Resecurity MirageX
AI-Powered Cyber Deception and Honeypot Platform
Turn Your Infrastructure into a Trap for Adversaries
Modern attackers are patient, stealthy, and highly adaptive. Traditional security tools are designed to block and alert, but they rarely reveal how attackers actually think, move, and operate inside a network.
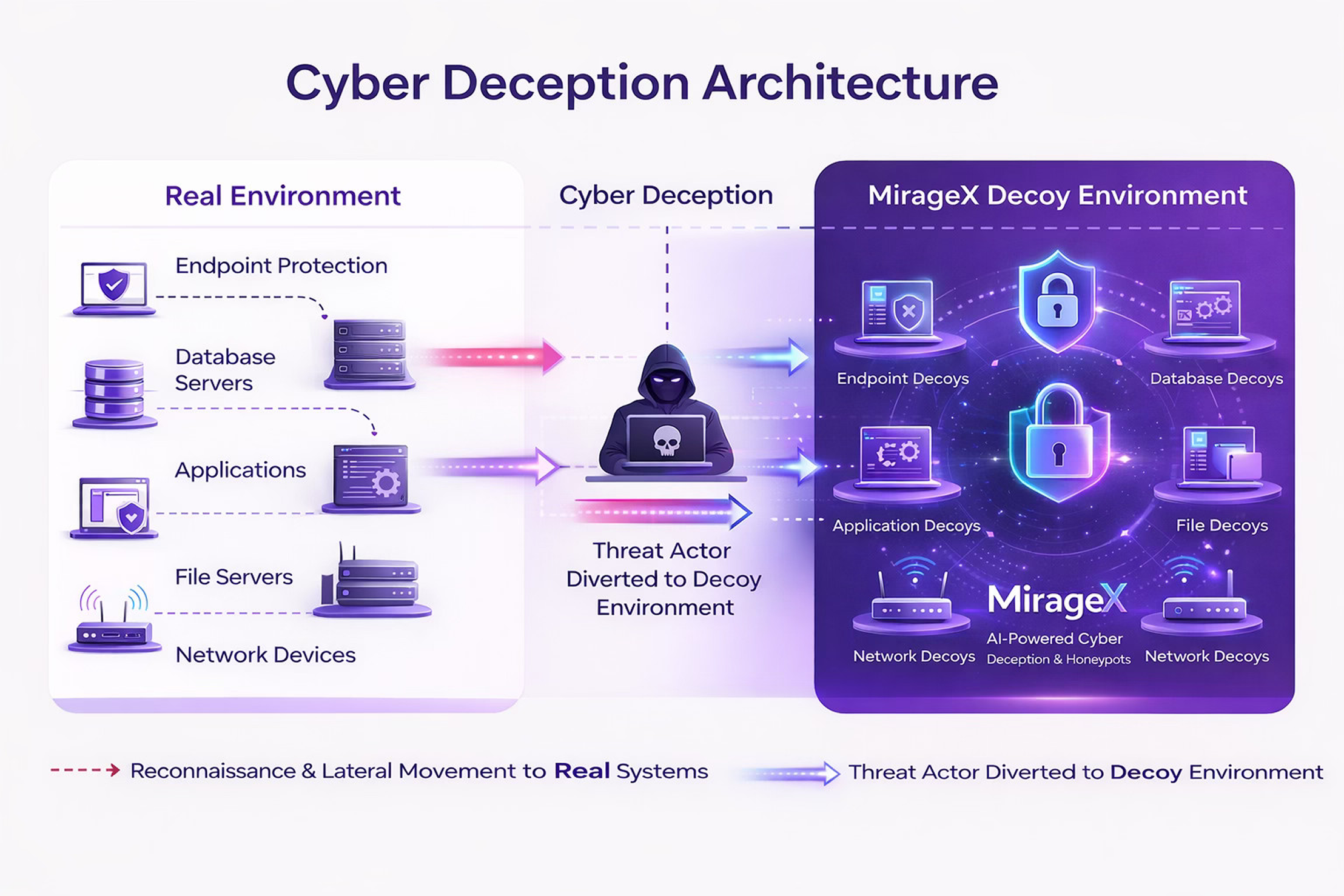
Resecurity MirageX is an advanced cyber deception and honeypot platform designed to expose adversaries by luring them into realistic decoy environments. By emulating enterprise infrastructure, applications, credentials, and network services, MirageX turns your environment into an active hunting ground where every attacker action is detected, recorded, and analyzed.
Instead of waiting for alerts, security teams gain direct visibility into attacker behavior in a controlled and isolated environment.
Cyber deception is a proactive security approach that uses decoys, traps, and simulated assets to mislead attackers and detect intrusions early. These assets look and behave like real production systems, but they are fully isolated and safe.
Any interaction with a deception asset is suspicious by definition. This makes cyber deception one of the most reliable ways to detect lateral movement, credential abuse, insider threats, and advanced persistent attackers.
MirageX extends this concept using artificial intelligence and threat intelligence to create high-fidelity environments that are nearly impossible for attackers to distinguish from real infrastructure.
-
Hyper-Realistic Infrastructure Emulation
MirageX deploys decoy servers, endpoints, databases, cloud services, and network devices that mirror your actual environment. Hostnames, operating systems, services, and configurations are designed to look authentic and operational.
-
Adaptive Deception Layer
The platform dynamically adjusts decoy assets based on attacker behavior and threat intelligence. As techniques evolve, MirageX adapts automatically to stay convincing and relevant.
-
Threat Actor Engagement and Trapping
MirageX attracts adversaries and keeps them engaged inside controlled environments. This allows security teams to observe their actions without risk to real business systems.
-
Automated Threat Hunting
Instead of waiting for alerts, MirageX continuously monitors attacker interactions with decoys to identify hidden threats, lateral movement, and insider activity.
-
Deep Attacker Telemetry and Forensics
Every command, connection, credential attempt, and movement is recorded. MirageX provides detailed insight into tactics, techniques, and procedures used by attackers.
-
Seamless Integration with Security Stack
MirageX integrates with SIEM, SOAR, EDR, NDR, and security analytics platforms to enrich alerts, accelerate investigations, and improve response workflows.
-
Deception Assets Deployment
Decoy systems, credentials, files, and services are deployed across the environment, including on-premise, cloud, and hybrid infrastructures.
-
Environment Emulation
Assets are configured to mimic real applications, network behavior, and user activity to appear fully legitimate.
-
Attacker Attraction
Threat actors discover and interact with deception assets during reconnaissance, lateral movement, or exploitation attempts.
-
Behavior Monitoring
MirageX captures every interaction in real time, including tools used, commands executed, and movement patterns.
-
Intelligence Generation
The platform analyzes attacker behavior using AI and threat intelligence to profile tactics and identify campaigns.
-
Response and Containment
Alerts are sent to security teams and integrated systems, enabling immediate investigation and response.
Traditional honeypots are static and easy to fingerprint. MirageX uses artificial intelligence to create living environments that change with the threat landscape.
-

Adaptive Assets
Decoys adjust in real time based on attacker behavior, making them harder to detect and bypass.
-

Automated Profiling
AI analyzes attacker activity to identify tools, techniques, and possible attribution without manual effort.
-

Reduced False Positives
Machine learning helps distinguish legitimate activity from malicious behavior, improving signal quality.
-
Scalable Deployment
Deception assets can be deployed across large and distributed environments without manual configuration overhead.
-

Predictive Tactics
MirageX anticipates attacker moves and positions decoys to intercept advanced techniques before damage occurs.
-

Early Threat Detection
Attackers are identified at the first interaction with deception assets, often before reaching real systems.
-

Reduced Dwell Time
Intrusions are detected quickly, limiting the time attackers can remain hidden inside the environment.
-

Lower Risk to Production Systems
Attackers are diverted away from critical assets and into isolated decoy environments.
-

Deeper Attacker Insight
Security teams gain visibility into how adversaries operate, not just that they are present.
-

Stronger Incident Response
Real attacker telemetry improves investigation quality and speeds up containment.
-

Operational Efficiency
Automation reduces analyst workload and prioritizes real threats.
MirageX supports advanced detection and monitoring requirements across major frameworks, including:
-
NIST Cybersecurity Framework
-
ISO 27001
-
SOC 2
-
GDPR
-
CMMC and defense sector standards
By demonstrating proactive detection and advanced monitoring controls, MirageX strengthens audit posture and regulatory readiness.
Resecurity MirageX is not a standalone trap. It is a fully integrated part of the Resecurity cyber intelligence ecosystem. It combines:
-
Global threat intelligence
-
AI-driven analytics
-
Real-world adversary data
-
Enterprise-grade deception engineering
This allows organizations to move beyond passive defense and actively expose attackers before damage occurs. MirageX transforms your infrastructure from a target into a weapon against adversaries.

Los Angeles, CA 90071 Google Maps

