Compromise Assessment
Identify Hidden Threats Before They Emerge
A Compromise Assessment (CA) is a proactive cybersecurity service designed to detect threats that have bypassed traditional security defenses. Unlike incident response, which reacts to confirmed breaches, this assessment is a preemptive investigation aimed at identifying ongoing or past intrusions, dormant malware, unauthorized access, and indicators of compromise (IOCs) already present in your digital environment.
Resecurity's Compromise Assessment provides a comprehensive, intelligence-led evaluation of your organization's security posture across endpoints, network traffic, cloud systems, and identity management — without disrupting operations. Whether you're evaluating third-party risk, undergoing leadership transitions, or strengthening cyber resilience, CA brings clarity to the blind spots often overlooked by conventional security tools.
Organizations benefit most from a Compromise Assessment in the following scenarios:
- Post-incident validation – Confirm complete remediation and ensure no residual threats remain.
- Routine cybersecurity hygiene – Perform periodic evaluations of security effectiveness.
- Mergers, acquisitions, or leadership changes – Assess risks introduced by organizational transitions.
- Insider threat investigations – Detect unauthorized access or misuse by internal actors.
- Suspicious activity – Investigate signs of phishing, credential abuse, or unknown malware.
- Regulatory compliance – Support audits and meet governance or legal requirements.
| Assessment Area | Purpose |
|---|---|
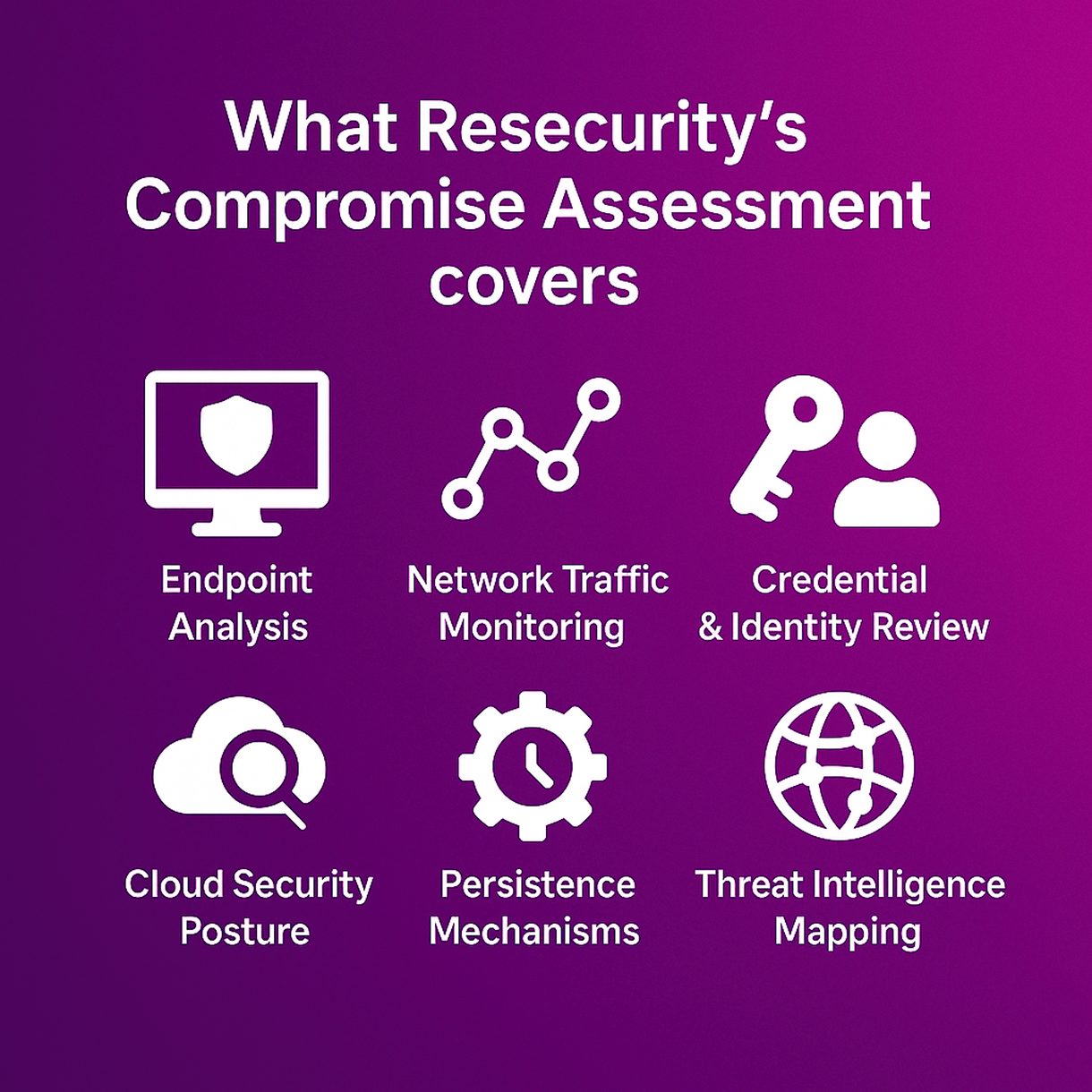
| Endpoint Analysis | Identify malware, keyloggers, and unauthorized access on user and server systems. |
| Network Traffic Monitoring | Detect lateral movement, unusual communication, and signs of command-and-control activity. |
| Credential & Identity Review | Uncover credential misuse, identity theft, and compromised user behavior. |
| Cloud Security Posture | Assess SaaS and cloud environments for misconfigurations or unauthorized access. |
| Persistence Mechanisms | Detect implants, scheduled tasks, registry modifications, and stealthy backdoors. |
| Threat Intelligence Mapping | Correlate internal findings with global threat intelligence and adversary tactics. |
Resecurity combines technology, threat intelligence, and human expertise to deliver a thorough assessment with minimal business impact:
1. Non-Intrusive Data Collection
Lightweight agents and forensic methods gather telemetry from endpoints, logs, and cloud services without affecting performance.
2. Behavioral and Anomaly Analytics
Machine learning models surface suspicious deviations in user, system, and network behavior.
3. Threat Intelligence Correlation
Findings are matched against Resecurity's global threat datasets and dark web reconnaissance for high-confidence detection.
4. Expert-Led Threat Hunting
Skilled analysts manually inspect evidence to validate compromises, identify root causes, and eliminate false positives.
5. Executive Reporting & Mitigation Guidance
Receive detailed technical reports, executive summaries, and actionable recommendations for remediation and risk reduction.
- Detect advanced threats missed by EDR, SIEM, or antivirus tools
- Minimize attacker dwell time and reduce potential damage
- Validate your third-party, vendor, and supply chain cybersecurity posture
- Enhance internal security controls and improve readiness
- Support regulatory and audit requirements with evidence-backed assessments
- Gain confidence and assurance for executives, board members, and regulators
Resecurity's Compromise Assessment is trusted by organizations worldwide to uncover the truth behind suspicious activity, reduce cyber risk, and strengthen security posture. Our methodology blends global threat intelligence with hands-on expertise, delivering visibility and clarity across your enterprise infrastructure.
Keep up to date with the latest cybersecurity news and developments.
By subscribing, I understand and agree that my personal data will be collected and processed according to the Privacy and Cookies Policy

Los Angeles, CA 90071 Google Maps

