Insider Threat Protection & Monitoring
Neutralize Insider Threats
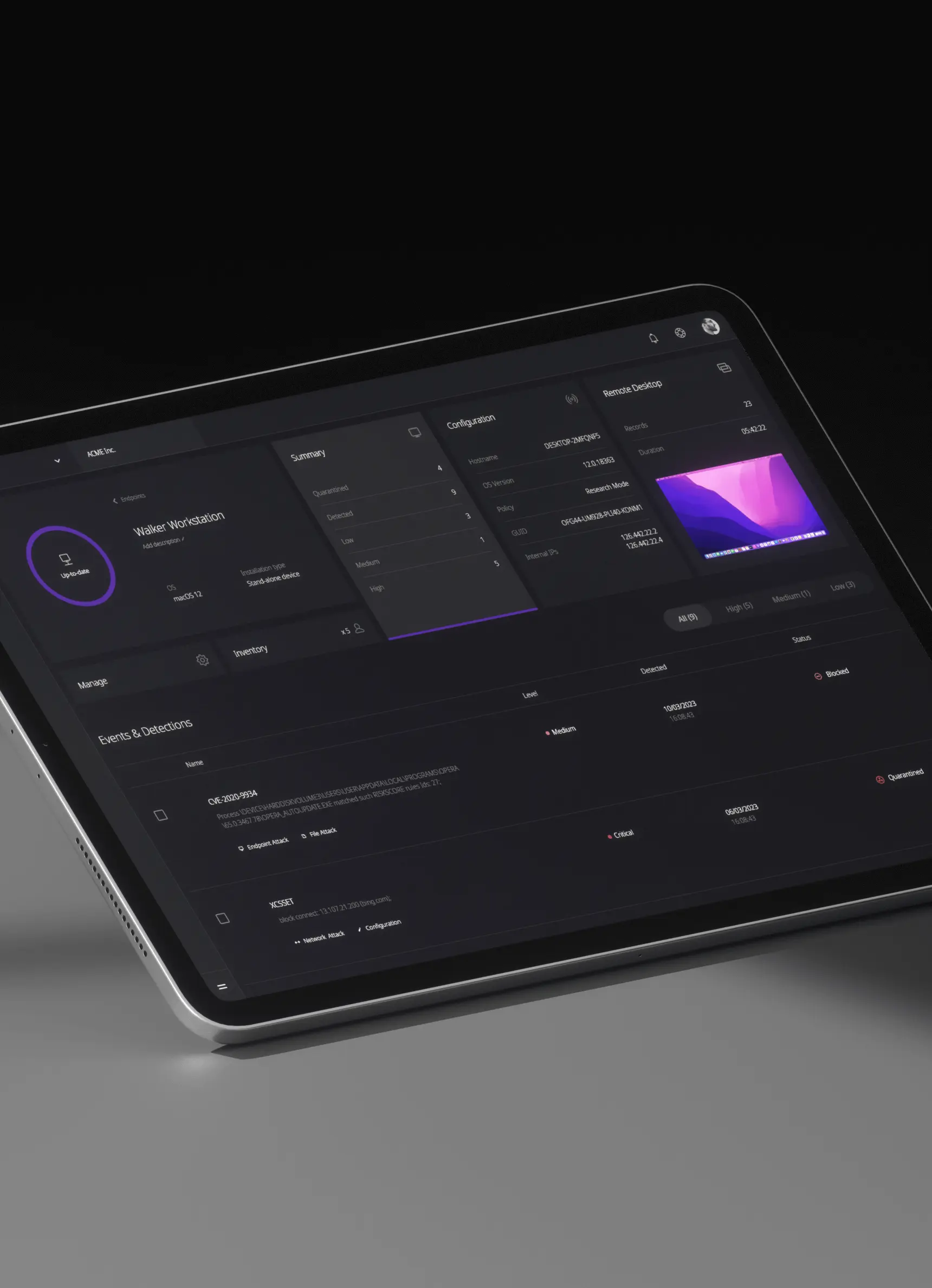
Resecurity’s nimble oversight software operates stealthily in the background of all applications displayed by employee-facing activity monitors and third-party applications.
The Insider Threat Protection & Monitoring application deploys rapidly, enabling frictionless installation and operationalization.
Resecurity harnesses AI and a robust library of known cybercriminal remote network access markers to rapidly detect the compromise of employee credentials by threat actors.
With the high-dimensional, and meticulously indexed user session and activity data, suspicious behavior can rapidly guide SOC and CERT investigators to active insider risks.
The pandemic caused a shift to remote work, increasing enterprises' attack surface and exposing them to various risks. Resecurity's Insider Threat Protection & Monitoring platform can help by detecting compromised accounts, monitoring all activity in real-time, and recording sessions before and after incidents. The platform offers advanced content based DLP and user behavior analytics, allowing firms to rapidly disrupt suspected malicious or high-risk user behavior.
With supervisory tools such as session logging, keystroke recording, system activity logging, and computer vision, Resecurity provides a holistic view of user-generated content and anomalies in credentialed user behavior. The platform deploys rapidly, interoperable across cloud-based IT systems, and offers agile incident response capabilities. The solution combines DLP, user behavior analytics, and session recording to deliver unparalleled insight and intervention capabilities.
Highlighting these IT comorbidities, Cybersecurity policy research center Ponemon Institute reported that insider threat incidents have risen 44% over the last two years. Additionally, the cost per incident increased by more than one-third, totaling over $15 million. Broadly speaking, insider threats are willfully malicious or accidental employee behaviors that jeopardize an employer’s digital, physical, human, vendor, or brand assets.
These threats manifest in the form of network privilege abuse, unauthorized data exfiltration, corporate sabotage, IT sloppiness, workplace incivility, and more. With some 87% of firms now relying on their employee’s capacity to access mobile business applications from their personal smartphones, companies urgently need a security solution that factors all stages of the insider-threat cycle to effectively mitigate risks. Resecurity’s Insider Threat Protection & Monitoring suite can help neutralize malicious insider threats before they wreak havoc on organizations.
-
Monitoring & recording employee activity provides the real-time intelligence required to preemptively detect risk and then protect your organization before any records are compromised.
-
Eliminating Regulatory Fines by utilizing Resecurity’s Insider Threat Protection & Monitoring solution increases organization reputation and reduces unwanted costly overheads.
-
By utilizing the power of Insider Threat Detection & Monitoring, private organization data will no longer be leaked or stolen by insider threats.
-
Receiving early-warning notifications of insider activity allows your organization to rapidly respond to situations and prevent data breaches before they happen.
-
As remote work environments continue to flourish, so do the cybersecurity threats. By using Insider Threat Protection & Monitoring, you can monitor and secure your employees remotely as if they were on premise.
Enterprises face the daunting challenge of defending against advanced attacks that seek to exploit unknown vulnerabilities. Early detection and warnings are crucial for effective threat mitigation.
Intuitive controls, centralized interface, and automatic analysis provide real-time visibility into network traffic and user activity, enabling rapid incident response. Incident analysis provides contextual information for forensic analysis, while cryptographic security ensures the protection of sensitive data.
Our solution offers all these features, which enables organizations to protect critical assets and defend against a vast array of threats.
Resecurity’s nimble oversight software operates stealthily in the background of all applications displayed by employee-facing activity monitors and third-party applications. User and session data logged by the application is automatically saved and intuitively indexed and in enriched text, audio, and video formats. This indexing enables lightweight storage and streamlines reporting.
Resecurity’s nimble oversight software operates stealthily in the background of all applications displayed by employee-facing activity monitors and third-party applications. User and session data logged by the application is automatically saved and intuitively indexed and in enriched text, audio, and video formats. This indexing enables lightweight storage and streamlines reporting.
Insider Threat Protection & Monitoring is interoperable across the full-spectrum of cloud-based enterprise IT systems, seamlessly integrating with a broad universe of SaaS applications and network clients. The application deploys rapidly, enabling frictionless installation and operationalization.
With the high-dimensional, and meticulously indexed user session and activity data logged by the application, superior contextual insight into detected suspicious behavior can rapidly guide SOC and CERT investigators to active insider risks and willfully malicious employee threats.
Firms can enhance their detection of insider threats by leveraging Resecurity’s robust suite of IT oversight-enhancing technologies. These supervisory tools include session logging, key stroke recording, the documentation of all user-generated text, system activity logging, computer vision, audio logging, and the recognition of anomalies in credentialed user behavior.
Detection engines issue alerts, gather evidence, and generate notifications for users flagged for enhanced monitoring.
Resecurity continuously identifies, authenticates, tracks, controls, and manages access for permissioned users any time they are engaging with a firm’s IT system, connected workplace device, or network infrastructure.
User access is managed according to internally established network rules permissioned for employees by the enterprise.
Harnessing continuous access management and threat detection technologies enables firms to rapidly disrupt suspected malicious, negligent, or high-risk user behavior and neutralize potentially adversarial insiders before they cause harm.
Keep up to date with the latest cybersecurity news and developments.
By subscribing, I understand and agree that my personal data will be collected and processed according to the Privacy and Cookies Policy

Los Angeles, CA 90071 Google Maps

