Solutions for Digital Risk Monitoring
Receive actionable risk intelligence about any significant changes to your security posture.
In-depth risk evaluation of the entire enterprise.
Early-warning security notifications.
Automated daily security posture reports.
Data is displayed on a convenient dashboard.
Time is our most valuable resource in cybersecurity. Leverage Risktm to automate your digital risk management and receive insight about any significant changes to your security posture due to Dark Web, data breach, compromised credentials, network infections and other security incidents.
In-depth risk evaluation throughout the entire enterprise ecosystem.
Monitor digital footprints of any size on a massive scale.
Proactively enabling strategic actions to improve security.
Capabilities of Digital Threat Monitoring
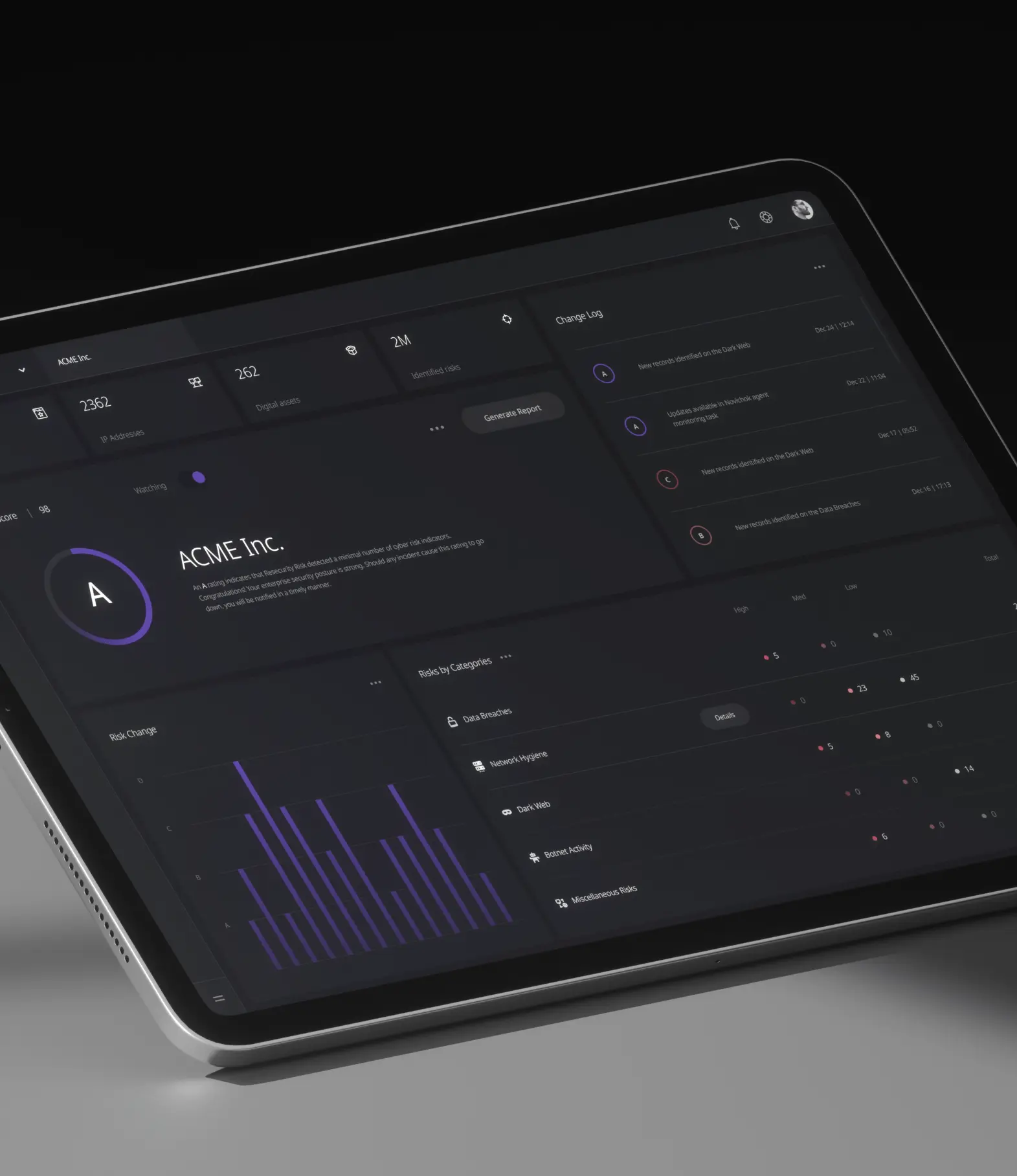
Your daily security score is rated based upon a summary of all risks for your monitored domains, IPs, networks, vulnerabilities, and cloud services. Actionable intelligence with immediate remediation is key to achieving a high security score.
- Unparalleled risk management
- Actionable intelligence that makes a difference
Refine and enrich datapoints to understand where weaknesses and vulnerabilities in your digital assets are. Changes and updates are sent through notifications via reports or e-mail as new data is discovered.

Identify external threats based upon high-quality intelligence aggregated from over 20,000 public and closed sources.
Risk vectors
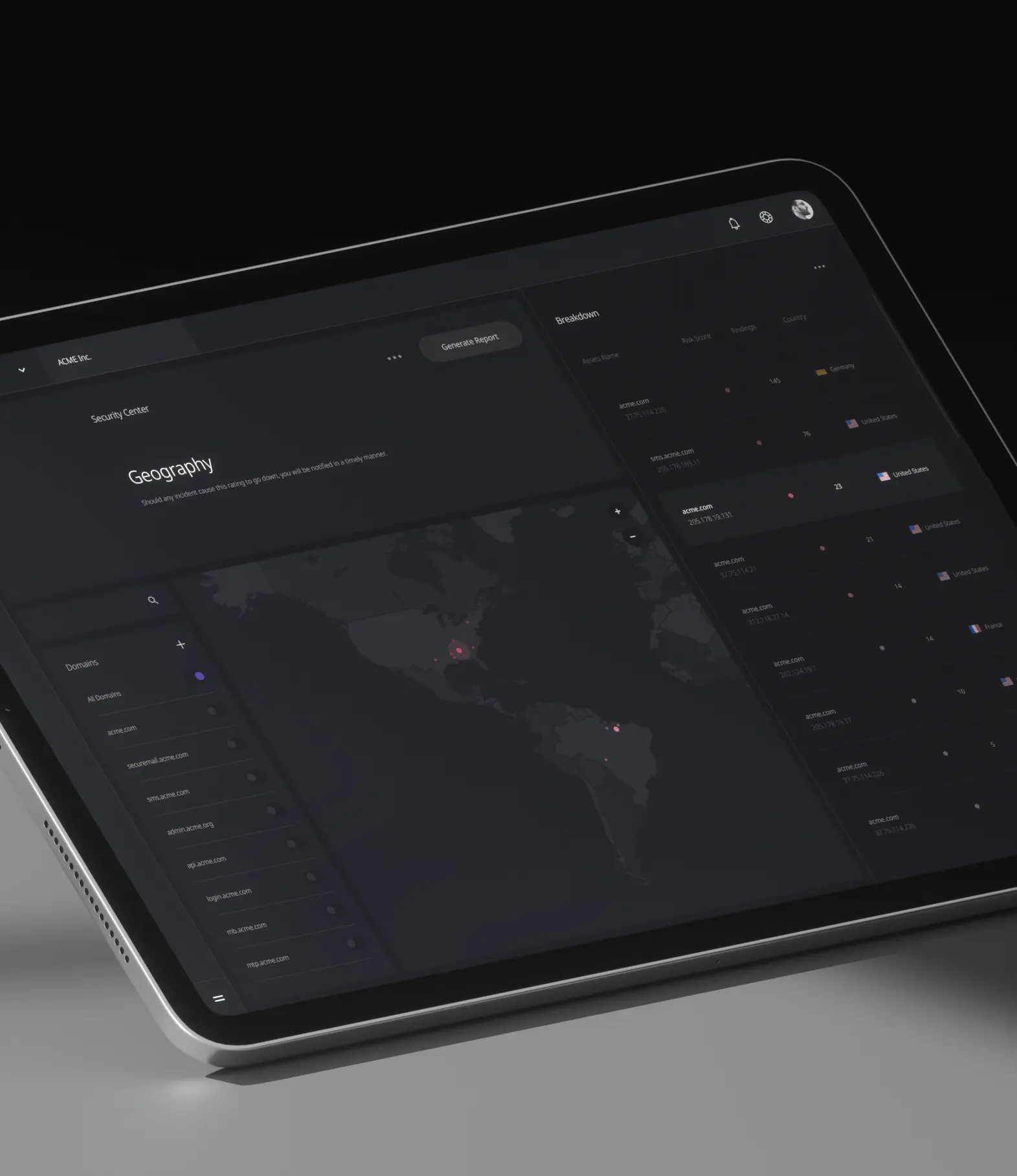
Our geo-location capability delivers contextual information identifying low, medium and high-risk areas for managing your infrastructure, network resources and other company assets.
Keep up to date with the latest cybersecurity news and developments.
By subscribing, I understand and agree that my personal data will be collected and processed according to the Privacy and Cookies Policy

Los Angeles, CA 90071 Google Maps

