ARBS: Attack Response Breach Simulation
Operationalize Cyber Resilience Through Realistic Breach Simulation
Attack Response Breach Simulation (ARBS) is an advanced methodology for testing organizational response to cyber threats, under realistic, adversary-modeled conditions. It enables institutions to move beyond theoretical plans and assess real-time readiness at both technical and executive levels.
In today's threat landscape, the ability to respond to a cyberattack is as critical as prevention. ARBS allows institutions to evaluate how well their security operations, business continuity plans, and leadership protocols perform under pressure. It simulates targeted, adversary-driven scenarios that reveal procedural gaps, communication delays, and technical blind spots that traditional assessments often overlook.
ARBS is a controlled simulation of a cyber breach, designed to test an organization's ability to detect, escalate, contain, and recover from an incident. Unlike penetration tests or tabletop exercises, ARBS engages both technical and non-technical stakeholders in dynamic, cross-functional decision-making—mirroring the stress and uncertainty of a real-world crisis.
ARBS vs. Traditional Testing Approaches
Each ARBS engagement is designed using real-world threat intelligence and aligned to the organization's industry, regulatory environment, and risk posture. Scenarios are modeled after known tactics, techniques, and procedures (TTPs) observed in the wild—ranging from ransomware deployment to credential abuse and data exfiltration.
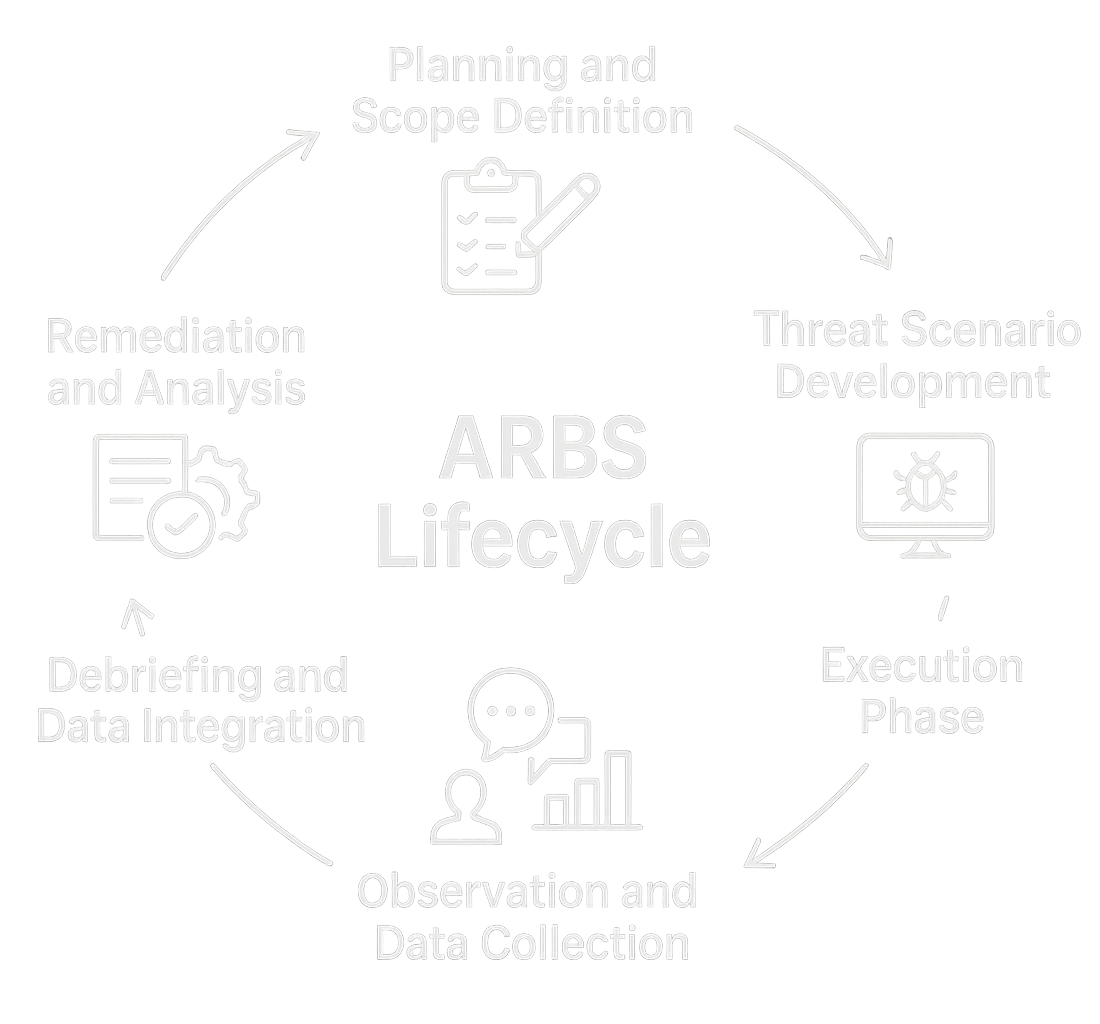
1. Planning and Scope Definition
Align objectives with risk priorities, regulatory frameworks, and operational boundaries.
2. Threat Scenario Development
Design realistic attack paths using current threat intelligence and relevant adversary profiles.
3. Execution Phase
Simulate attack vectors (e.g., phishing, lateral movement) in a secure, non-disruptive environment.
4. Observation and Data Collection
Monitor detection, escalation, containment, and communication workflows in real-time.
5. Debriefing and Analysis
Produce detailed findings, timeline reconstructions, and incident response maturity assessments.
6. Remediation and Policy Integration
Transform lessons learned into improved procedures, training, and risk governance.
For financial institutions in Saudi Arabia and the GCC, ARBS directly supports compliance with mandates like the SAMA Cybersecurity Framework, which requires periodic simulation of attack scenarios to validate detection and response readiness. ARBS also complements ISO 27035, NIST CSF, and DORA by providing measurable insights into incident response maturity.
Key Objectives ARBS Supports:
- Validation of incident detection, escalation, and containment procedures
- Board and executive-level incident playbook testing
- Evidence for auditors, regulators, and internal risk committees
- Integration of threat intelligence into response workflows
Beyond regulatory compliance, ARBS enables leadership to make informed decisions about where to invest in detection capabilities, process improvements, and cross-functional coordination. Outcomes are documented in actionable reporting, including:
- Timeline reconstruction of incident progression
- SOC and IR team response metrics
- Communication gap analysis (internal & external)
- Procedural recommendations for escalation and containment
- Executive and non-technical role engagement insights
The organizations best prepared for cyber incidents are those that regularly test, refine, and stress their response capabilities under simulated pressure. ARBS is not a one-off event, but part of a broader operational resilience strategy. It enables institutions to surface latent risks before adversaries exploit them—and to convert crisis into preparedness.
Keep up to date with the latest cybersecurity news and developments.
By subscribing, I understand and agree that my personal data will be collected and processed according to the Privacy and Cookies Policy

Los Angeles, CA 90071 Google Maps
