

Resecurity identified a new tool listed for sale on the Dark Web called TMChecker which is designed to attack remote-access services and popular e-commerce applications. This adversarial tool combines corporate access login (log) checking capabilities with a brute-force attack kit. The tool’s developer, a threat actor who goes by the handle “M762” on the XSS cybercrime forum, offers TMChecker on a monthly subscription basis for $200.
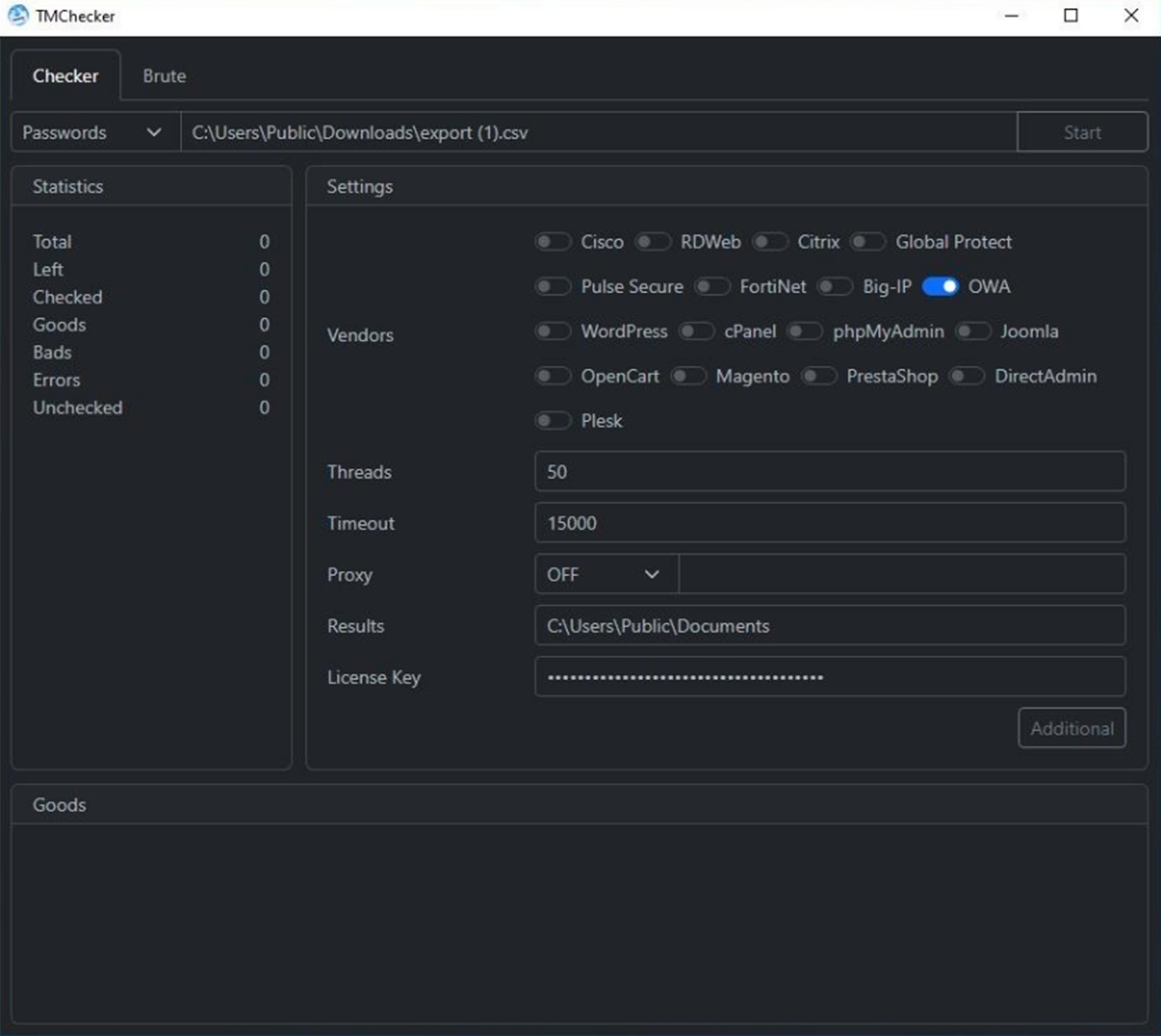
TMChecker is similar to tools like “ParanoidChecker,” which is designed to scan for compromised email and social media log data. But TMChecker is arguably more sophisticated, as it targets the corporate, remote access gateways that often serve as primary intrusion vectors for ransomware infections and other higher-level attacks. TMChecker supports 17 solutions to target VPN gateways, enterprise mail servers, database management tools, popular e-commerce and online-shop engines, hosting administration panels, and more. Below are the services that TMChecker actively targets:
- Cisco (VPN)
- RDWeb
- Citrix (VPN)
- GlobalProtect (VPN)
- Pulse Secure (VPN)
- FortiNet (VPN)
- Big-IP (VPN)
- OWA (Office 365 / Outlook)
- Wordpress (CMS)
- phpMyAdmin
- Joomla (CMS)
- OpenCart (e-commerce)
- Magento (e-commerce)
- PrestaShop (e-commerce)
- cPanel (Hosting Panel)
- DirectAdmin (hosting panel)
- Plesk (hosting panel)
- FTP
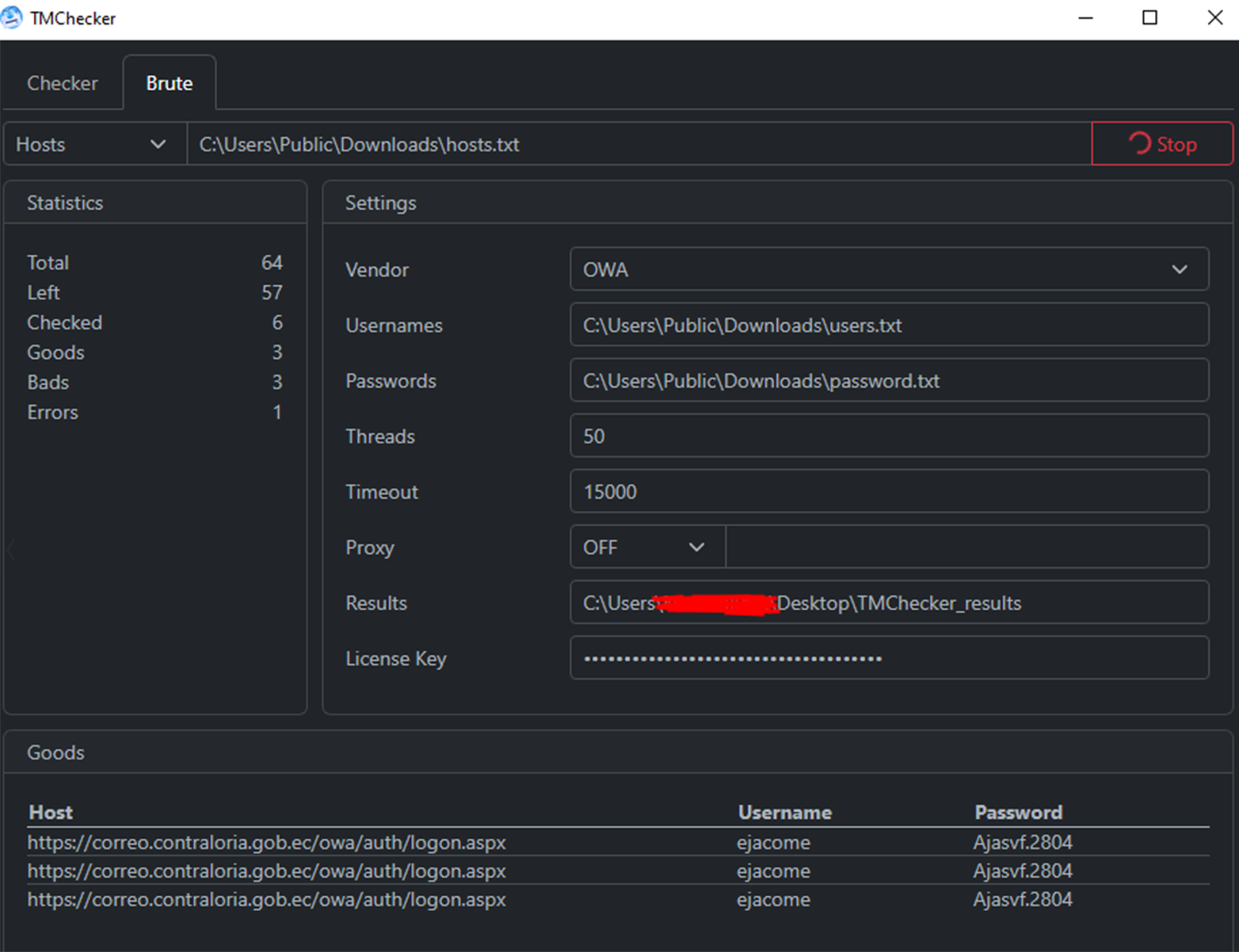
Multiple initial access brokers (IABs) and ransomware operators use this tool to check available compromised data for the presence of valid credentials to corporate VPN and e-mail accounts. For example, in one incident observed by Resecurity, threat actors used TMChecker to target the email server of a government organization (gob.ec) in Ecuador.
TMChecker’s black-hat developer, M762, runs a Telegram channel with over 3,270 subscribers. It’s unclear how many of these subscribers are paying customers, but the tool’s monthly subscription price combined with M762’s Telegram channel following helps give readers some idea about the profitability of this adversarial SaaS model.

Significance
The emergence of TMChecker coincides with the stratospheric rise of human-operated ransomware attacks, according to recent Microsoft research. Coverage of this report in The Record noted that “human-operated attacks typically involve the active abuse of remote monitoring and management tools that allow hackers to leave behind less evidence — as opposed to automated attacks that are delivered through malicious phishing documents.” Published in October of last year, this Microsoft report found that human-operated attacks had more than tripled since September 2022.
Threat intelligence experts anticipate this trend to increase in 2024 as individual ransomware actors try to “maximize their returns by working for a range of gangs,” according to The Record. Obviously, the recent law enforcement takedowns that disrupted and dismantled the LockBit 3.0 and BlackCat/ALPHV ransomware-as-a-service (RaaS) operations, two of the most prolific threat actor groups tracked over the last two years, have altered this threat trajectory in ways that are not yet clear. It should be noted, however, that many in the cybersecurity and cybercrime communities anticipate that ALPHV will rebrand and reemerge like other notorious RaaS syndicates that have been shut down by law enforcement operations in the past.
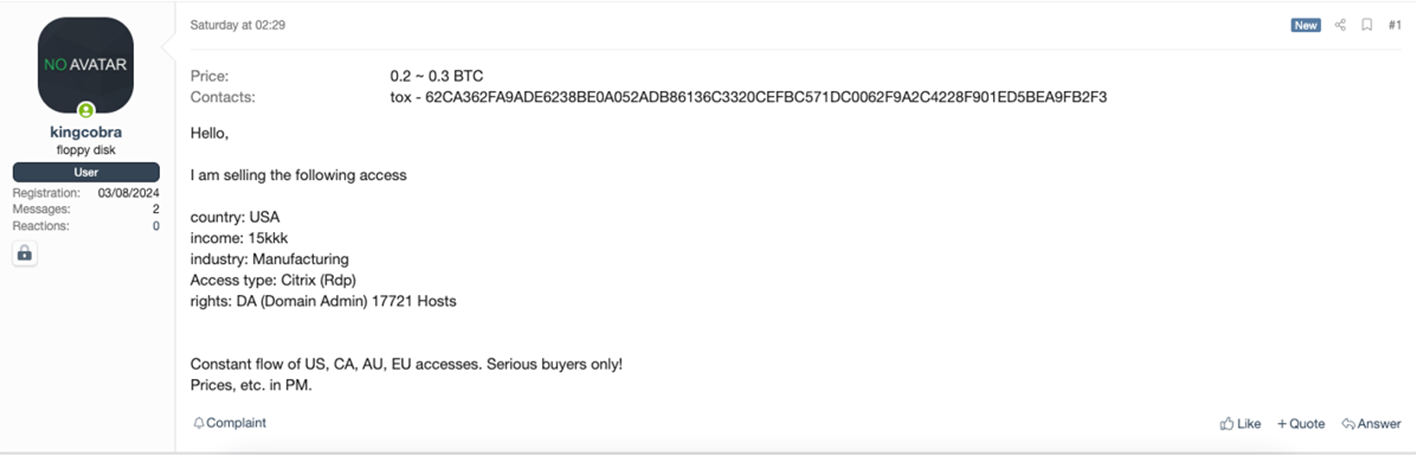
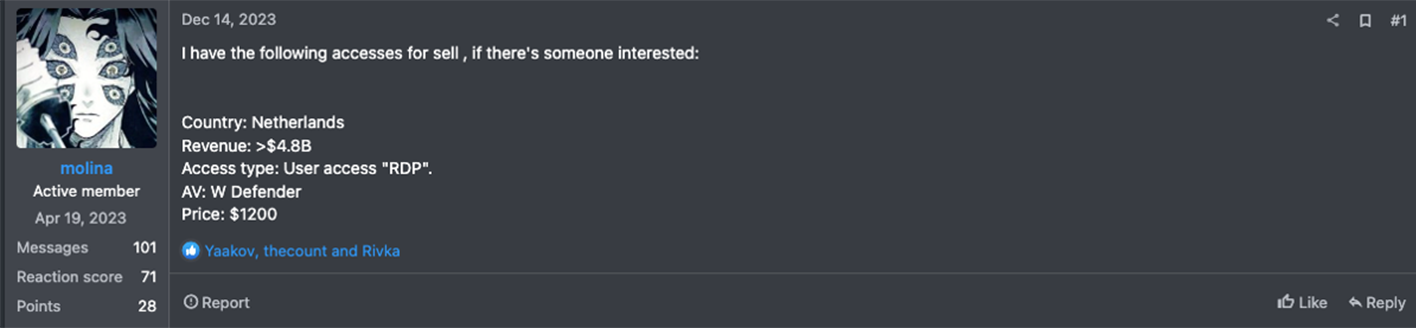
Regardless, remote desktop protocols (RDPs), VPNs, and personal devices remain prime targets for ransomware attackers. Among external services, Microsoft found that adversaries primarily leveraged unsecured RDPs and VPNs. “Threat actors attacking valid accounts, where the attacker somehow gained legitimate account credentials, were most often able to log in via Citrix,” according to Microsoft. Below is a sampling of Dark Web posts listed by various IABs that illustrate the popularity of remote-access gateways with cybercriminals. As the reader can tell from these listings, the cost of remote access can range from $500 to $20,000 on the Dark Web. Even at the lowest end, this price schedule exceeds two months’ TMChecker subscription costs.
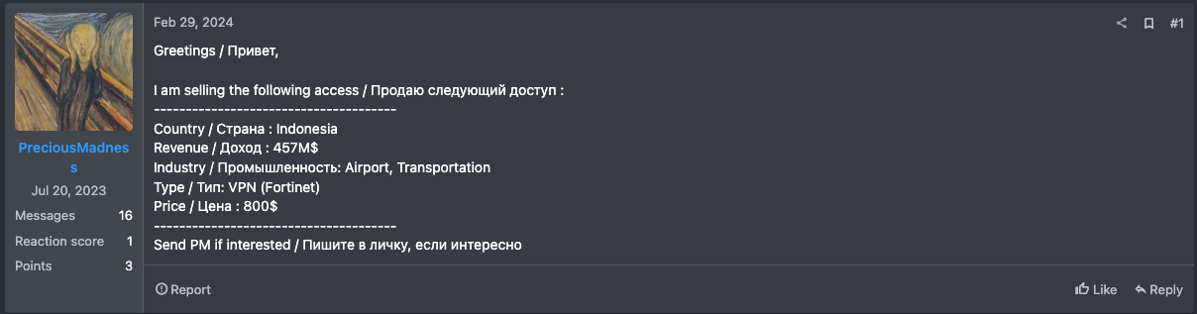
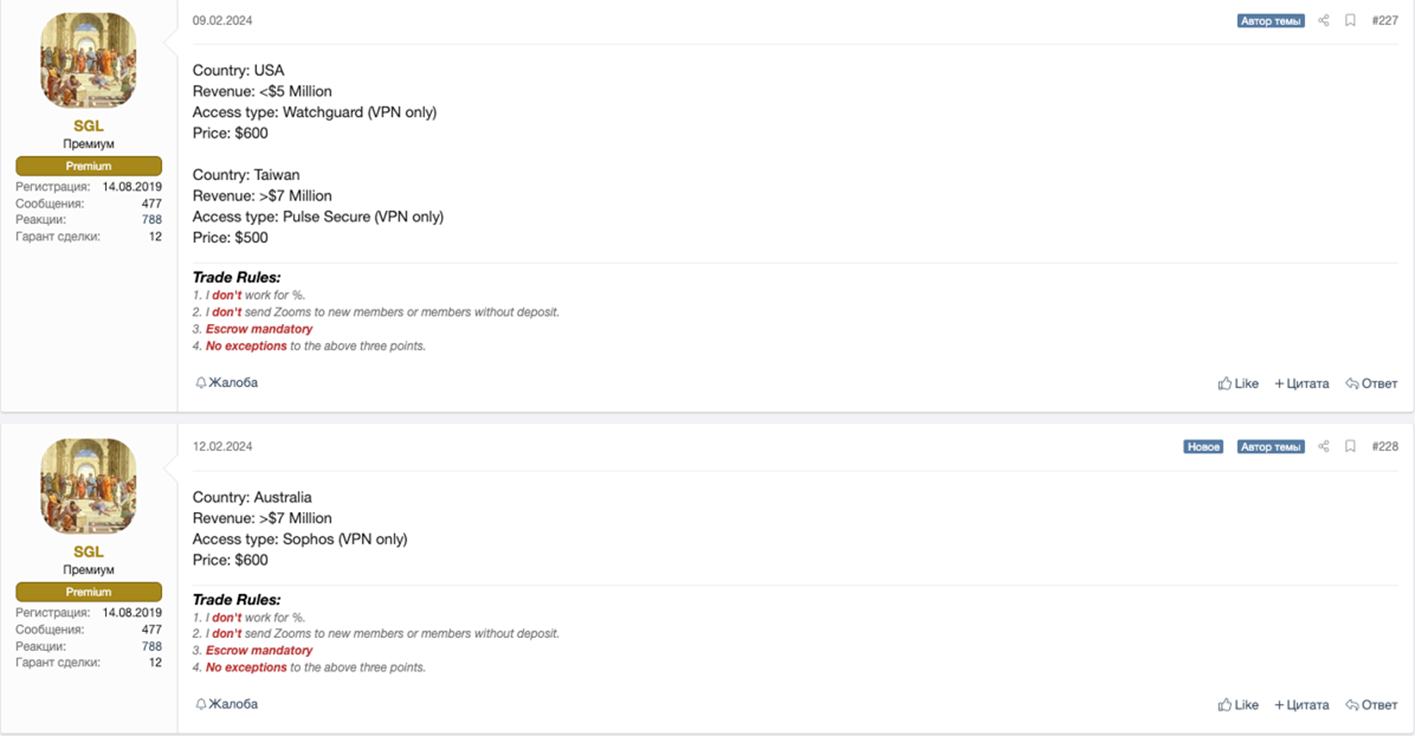
In February, incident responders observed this human-centric attack typology in a mass-exploitation campaign targeting an authentication-bypass vulnerability in ConnectWise’s ScreenConnect remote-support tool. A Dark Reading report covering this breach noted that hundreds of IABs and cybercrime gangs had “started pouncing on the bugs to set up shop inside various endpoints, with the intent of selling that access to ransomware groups.” Resecurity observed related signals of this activity on XSS and other Dark Web communities.
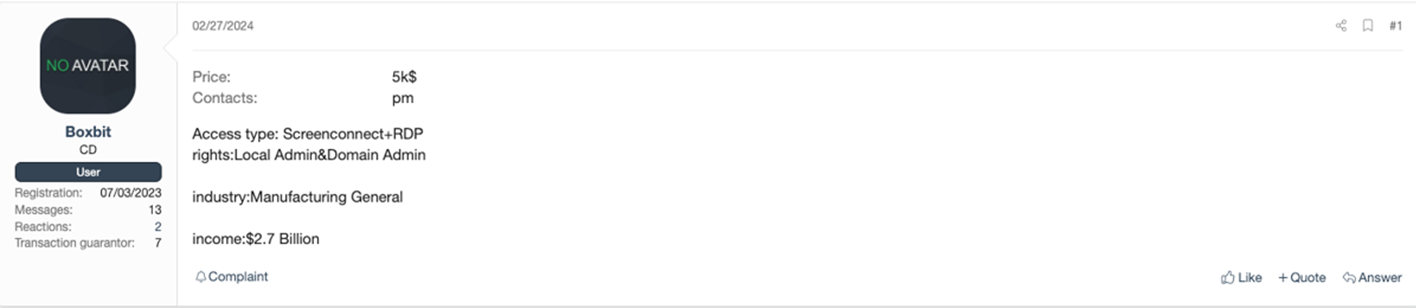
The concurrent rise of TMChecker is thus significant because it substantially lowers the cost barriers to entry for threat actors looking to obtain high-impact corporate access either for primary exploitation or for sale to other adversaries on the secondary market. Armed with these remote access credentials, threat actors can more easily grab a foothold in corporate networks and gain persistence to the extent that the initial breach remains undetected – until attackers find an opportune time to strike, that is. This dynamic has become a particularly high-level threat in mergers and acquisitions (M&A). A 2022 Wall Street Journal report warned that midmarket acquisition targets for private equity and venture capital firms were being increasingly targeted by ransomware attackers, for example.
This growing trend is particularly noteworthy as M&A activity in the PE sector is anticipated to bounce back strong in 2024 following last year’s slump. While methods of compromise vary, remote-access gateways remain readily exploitable nodes in M&A infection chains. The recent Change Healthcare breach is a bulge-bracket example of this strategic M&A cyberattack cycle. As reported by SC Media, the February “breach of Change Healthcare that disrupted pharmacies nationwide was the result of an exploit of two ConnectWise vulnerabilities affecting the remote access app ScreenConnect.” Change Healthcare is a recently acquired payment-cycle management unit of UnitedHealth Group.
The subsidiary, which UHG acquired for $8 billion in 2022 after winning a year-long federal antitrust lawsuit filed by the Department of Justice, “often serves as a backend services provider for various healthcare insurance providers in the U.S.,” according to TechTarget. As a result of the ransomware attack, millions of Americans were unable to fill their prescriptions, as health insurance billing systems were taken offline. The ALPHV RaaS syndicate claimed credit for the breach and allegedly scammed the affiliate who personally executed the attack on Change Healthcare out of a $22 million bitcoin ransom payout that the subsidiary made to them. After this purported “exit scam,” ALPHV announced that they were selling their malicious source code and shutting down their RaaS operation for good.
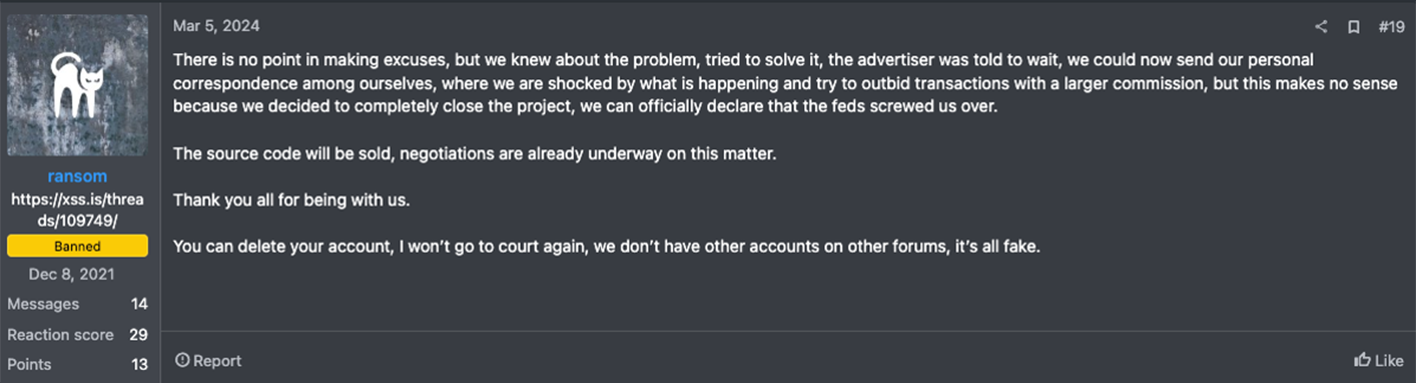
The key question that arises from the game-changing convenience of TMChecker’s SaaS model is how many organizations are unaware that they have been compromised via tooling of this nature while attackers achieve increasing persistence in their networks? Ultimately, as the barriers to obtaining in-demand remote access for corporate networks decrease, it becomes much easier for less sophisticated or financially resourced threat actors to conduct destructive ransomware attacks and other malicious campaigns.
In a threat landscape marked by diminishing hurdles to acquiring illicit remote access, the corresponding breach costs for the enterprise sector – as delineated by the combined expenses for incident response, operational disruption, reputational damage, and potential litigation by customers and business partners – could swell into the billions. To put the cost-benefit proposition of TMChecker and similar tools in perspective, consider that $200 a month in cybercriminal spend can potentially reap millions of dollars in dividends to ransomware attackers for each company they successfully breach.
At the same time, the global average cost of a data breach set each compromised organization back $4.45 million in 2023, according to IBM’s latest Cost of a Data Breach report. TMChecker has further amplified the enterprise attack surface by exponentially increasing the risk of remote-access-enabled breaches while more victims remain oblivious to the ongoing exploitation of their VPN and RDP gateways.
Conclusion
In a modern threat landscape marked by proliferating human-operated ransomware attacks that favor the compromise of VPN, RDP, and other remote gateways, the emergence of TMChecker and similar tools represents a major threat to organizations. This hybrid brute-force and log-scanning attack kit substantially lowers the barriers to entry for novice threat actors who may otherwise lack the financial resources or connections to purchase higher-value VPN and RDP access offerings on the Dark Web.
Given the recent ascent of groups like Scattered Spider, a group of 20something, non-ransom native sim-swappers who rapidly evolved into marquee ALPHV affiliates last Summer, defenders should take TMChecker’s malicious potential seriously. The tool’s SaaS-friendly user model makes it trivial for less experienced attackers to obtain access to highly coveted remote gateways. In the hands of more experienced threat actors, TMChecker and similar tools introduce added convenience and streamlining of adversarial operations.
With Ernst & Young projecting corporate M&A and PE deal flow to both rebound by over 10% this year, TMChecker also serves as a powerful supplement to growing threat-actor reconnaissance of midmarket acquisition targets. The confluence of the prevailing corporate M&A market with rising cyberattack trends targeting remote corporate gateways and midmarket firms that are ripe for acquisition compels the private sector to enhance its cyber-due diligence processes.
To this end, Resecurity's RISKTM platform can assist strategic acquirers in mitigating the risk of a post-acquisition breach disaster like the one that impacted Change Healthcare and its corporate parent, UHG. By harnessing the power of Resecurity’s leap-ahead cyber threat intelligence (CTI) capabilities, corporate acquirers can more confidently visualize M&A targets’ exposures to remote-access intrusions enabled by TMChecker and other Dark Web conduits.

