

Overview
APT41 is a highly sophisticated Chinese state-sponsored threat actor known for conducting both espionage and financially motivated cyberattacks. This group targets a wide range of sectors, including healthcare, telecom, software, and government entities across the globe. Unlike many threat groups, APT41 uniquely blends traditional cyber espionage with cybercrime tactics, deploying custom malware and ransomware in some attacks.
APT 41, also known by aliases such as BARIUM, Wicked Panda, and Brass Typhoon, is a prominent cyber threat group believed to be associated with the Chinese government. This group has been active since at least 2012 and is known for its dual focus on cyber espionage and financially motivated cybercrime.
APT41 was recently reported to be using Google Calendar for malware command-and-control on a government of Taiwan website. This research examines the delivery methods, technical details, recent activity, and key IOCs to help defenders identify and prevent similar attacks.
Resecurity is sharing additional technical information and indicators of compromise of APT41 activity to raise awareness of incident responders and cybersecurity professionals to combat threats originating from China.
Technical Details
1. Initial Infection and Delivery
APT41 launched this campaign using spear-phishing emails that directed victims to a ZIP archive hosted on a compromised government website.
The archive contained a Windows shortcut (LNK) file disguised as a PDF, along with several JPG images—two of which were actually malicious in nature.
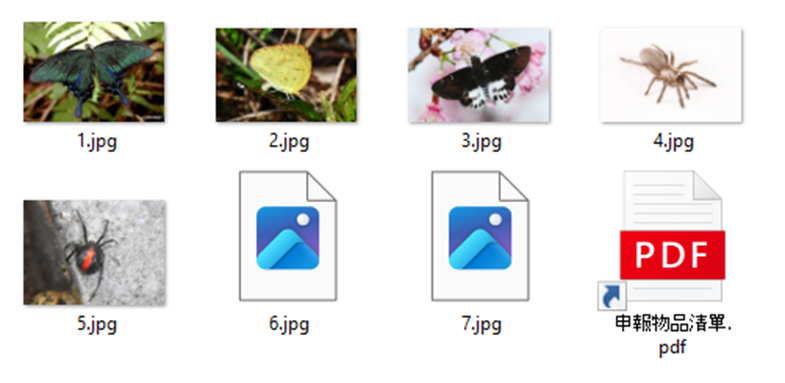
Inside the folder are what appear to be seven image files of arthropods, named “1.jpg” through “7.jpg.”
Notably, “6.jpg” and “7.jpg” are not genuine images—they are part of the malicious payload.
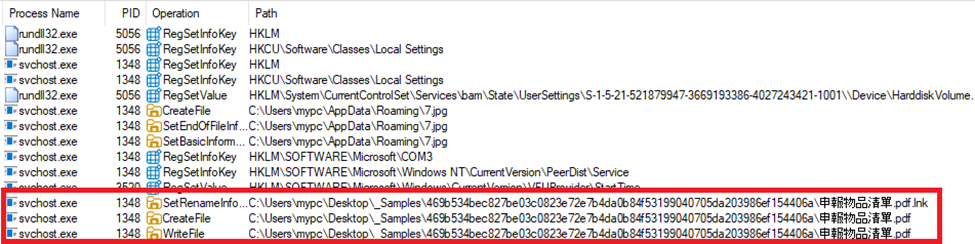
The infection chain begins when the victim opens the shortcut LNK file, which displays a decoy PDF stating that the listed species must be declared for export.


The shortcut then silently launches a stealthy malware known as ToughProgress.
The malware operates through three sequential modules, each designed for a specific function and equipped with various stealth and evasion techniques. These include in-memory execution, encryption, compression, process hollowing, control flow obfuscation, and the use of Google Calendar for command-and-control (C2) communications.
The three malicious components are:
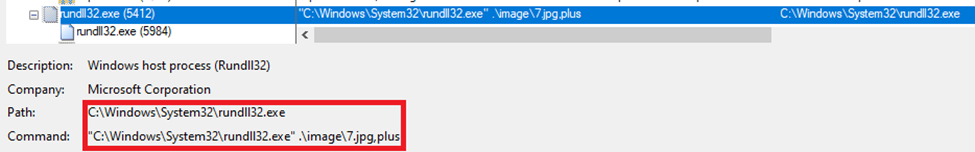
- PLUSDROP – decrypts 6.jpg and runs using Rundll32.exe.
- PLUSINJECT – Performs process hollowing by injecting the final payload into a legitimate svchost.exe process to evade detection.
- TOUGHPROGRESS – is then installed and begins communicating with attacker-controlled Google Calendar events, serving as a command-and-control (C2) channel.
2. Execution and Payload Deployment (PLUSDROP and PLUSINJECT)
Once Rundll32.exe has been launched successfully, it attempts to decrypt 6.jpg on the machine.

The malware loads its path into memory using a dynamic string. It opens the file and reads its contents into a buffer. After reading, it applies an XOR-based decryption routine to the data. Once decrypted, the code treats the result as executable and runs it directly from memory. This allows the malware to hide its payload in a harmless-looking image and execute it without touching disk in its decoded form.

The malware then walks the list of loaded modules in memory by accessing the Process Environment Block (PEB). This is a common technique used to locate system DLLs without using API calls like GetModuleHandle, which could be monitored by security tools.
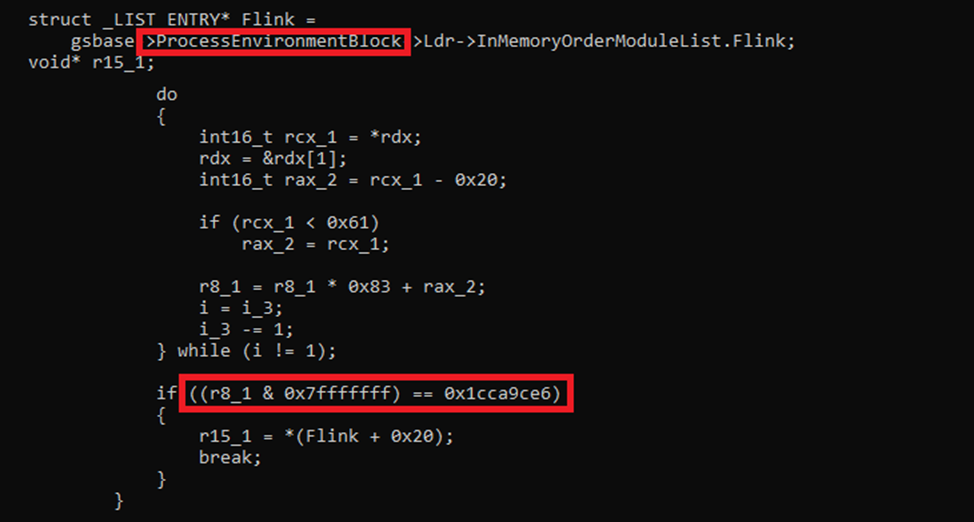
For each module, it retrieves the name and applies a custom hash function, which operates as follows:
- Converts characters to uppercase-like form (by subtracting 0x20).
- Skips non-printable characters.
- Applies a rolling hash:
Masks the result to 32 bits using 0x7FFFFFFF.
It then compares the result to the constant 0x1CCA9CE6:
When a match is found, the malware saves the module’s base address and injects the decrypted code into svchost.exe.
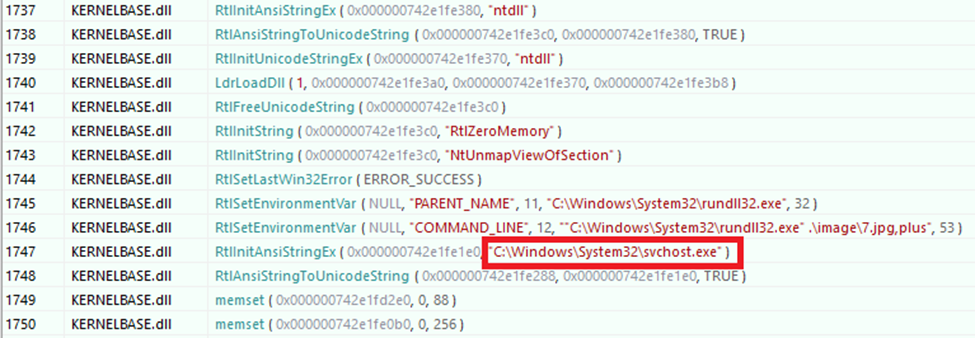

This technique is called process hollowing, and here is why the malware operates this way:
- Avoids Suspicious Strings: Security tools scanning for keywords like "svchost.exe" or "kernel32.dll" won’t flag a hash.
- Obfuscation: Slows down analysts who must reverse-engineer the hash function and brute-force to discover the original string.
- Function Resolution: Allows the malware to dynamically resolve critical functions like LoadLibrary, VirtualAlloc, or even inject into trusted processes.
The malware then proceeds to target ntoskrnl.exe, the heart of the Windows operating system, in a calculated effort to map, analyze, and potentially manipulate critical sections of the system. This behavior is buried inside a function which initiates a complex sequence of memory operations, characteristic of advanced low-level persistence mechanisms.

The malware doesn't just inspect kernel memory — it actively locates and accesses internal structures in a stealthy, dynamic way. It performs pattern matching in the .text section to find non-exported kernel routines, maps physical memory to bypass standard protections, and uses driver-like memory handling to avoid detection. These techniques are designed to achieve advanced goals like privilege escalation and anti-forensics, making it particularly difficult for reverse engineers to analyze the malware.

3. Command and Control (C2 TOUGHPROGRESS)
What sets ToughProgress apart is its novel use of Google Calendar as a command-and-control (C2) mechanism. The malware communicates with an attacker-controlled Google Calendar by creating and modifying events to facilitate covert data exchange.
Upon installation, ToughProgress creates a calendar event back in 2023, embedding encrypted, exfiltrated data within the event’s description.
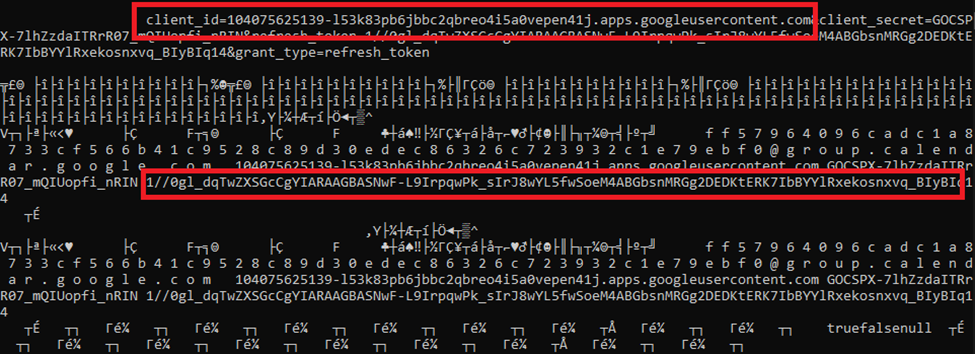
The attackers embed encrypted commands in calendar events. The malware retrieves these events, decrypts the commands, executes them on the infected Windows system, and then uploads the execution results into a new calendar event.
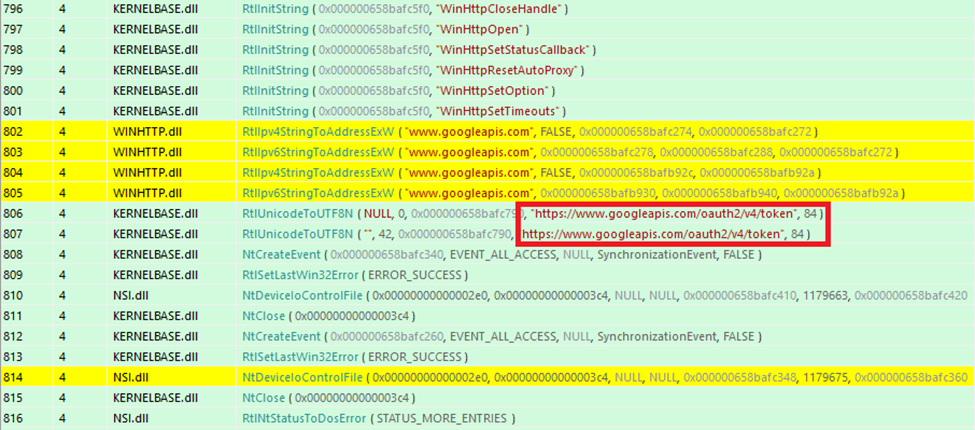
This process enables the threat actors to remotely collect the output, maintaining a stealthy communication channel.
To counter the TOUGHPROGRESS campaign, Google developed custom detection fingerprints to identify and remove malicious Google Calendar instances and disable attacker-controlled Workspace projects. Harmful domains and files associated with the threat were also added to Safe Browsing blocklists to enhance user protection.
Indicators of Compromise (IOCs)
File Hashes:
File Name |
SHA256 Hash |
MD5 Hash |
出境海關申報清單.zip |
469b534bec827be03c0823e72e7b4da0b84f5319904070 5da203986ef154406a |
876fb1b0275a653c4210aaf0 1c2698ec |
申報物品清單.pdf.lnk |
3b88b3efbdc86383ee9738c92026b8931ce1c13cd75cd1c da2fa302791c2c4fb |
65da1a9026cf171a5a7779b c5ee45fb1 |
6.jpg |
50124174a4ac0d65bf8b6fd66f538829d1589edc73aa7cf3 6502e57aa5513360 |
1ca609e207edb211c8b9566 ef35043b6 |
7.jpg |
151257e9dfda476cdafd9983266ad3255104d72a66f9265 caa8417a5fe1df5d7 |
2ec4eeeabb8f6c2970dcbffd cdbd60e3 |
C2 Domains:
- word[.]msapp[.]workers[.]dev
- cloud[.]msapp[.]workers[.]dev
- term-restore-satisfied-hence[.]trycloudflare[.]com
- ways-sms-pmc-shareholders[.]trycloudflare[.]com
- resource[.]infinityfreeapp[.]com
- pubs[.]infinityfreeapp[.]com
MITRE ATT&CK Mapping
Tactic |
Technique ID |
Technique Name |
Details from Report |
Initial Access |
T1566.001 |
Phishing: Spearphishing Attachment |
Spear-phishing emails with ZIP archives. |
T1190 |
Exploit Public-Facing Application |
ZIP hosted on a compromised government website. |
|
Execution |
T1204.002 |
User Execution: Malicious File |
Victim clicks LNK file disguised as PDF. |
T1059.003 |
Command and Scripting Interpreter: Windows Command Shell |
Uses Rundll32.exe to launch PLUSDROP. |
|
Defense Evasion |
T1140 |
Deobfuscate/Decode Files or Information |
XOR-decrypts image files (6.jpg and 7.jpg). |
T1027.002 |
Obfuscated Files or Information: Software Packing |
Compressed/encrypted payload in images. |
|
T1055.012 |
Process Injection: Process Hollowing |
Injects into svchost.exe using PLUSINJECT. |
|
T1027 |
Obfuscated Files or Information |
Uses dynamic string generation, hashing, and obfuscation. |
|
T1218.011 |
Signed Binary Proxy Execution: Rundll32 |
Executes PLUSDROP via Rundll32.exe. |
|
Privilege Escalation |
T1068 |
Exploitation for Privilege Escalation |
Potential exploitation of ntoskrnl.exe, indicates Low-level access. |
T1543.003 |
Create or Modify System Process: Windows Service |
May manipulate services via injected svchost. |
|
Discovery |
T1082 |
System Information Discovery |
Likely step post-infection (common, though not explicit). |
T1057 |
Process Discovery |
Used for identifying target processes to inject into. |
|
Collection |
T1119 |
Automated Collection |
Collects and sends execution results via Google Calendar. |
Command and Control |
T1102.003 |
Web Service: One-Way Communication |
Uses Google Calendar for C2. |
T1568.002 |
Dynamic Resolution: Domain Generation Algorithms |
Uses domains like *.workers.dev and *.trycloudflare.com. |
|
T1090.003 |
Proxy: Multi-hop Proxy |
Uses public-facing domains for proxying traffic. |
|
Exfiltration |
T1041 |
Exfiltration Over C2 Channel |
Sends encrypted execution results back via Google Calendar events. |
Conclusion
APT41 is among the most versatile and dangerous threat actors globally, combining sophisticated state-sponsored tactics with criminal intent. Their use of custom malware, supply chain attacks, and hybrid objectives makes them a persistent threat across industries.

