Every industry-leading company has gone through mergers and acquisitions (M&A) at some point to acquire a competitor, expand into a new market, or gain access to intellectual property or technology. As M&A involves extensive risk for any company, how it is carried out can unlock or destroy millions of dollars in value.
Although M&A transactions often undergo screening, External CTI is not part of all M&A vetting or portfolio monitoring processes. However, CTI can answer critical questions that the acquiring company needs to know to determine the risks of acquiring or making a strategic investment.
Some of these questions include:
- Is the company experiencing a data breach, or has it experienced an undisclosed one in the past?
- Will the company experience a data breach in the future?
- Has the strategic IP of the company been leaked on the dark web?
- How does this company compare to the cybersecurity risk with its competitors and other companies evaluated by the M&A entity?
- Has a data breach or loss been detected that could cause regulatory issues (Such as the US Securities and Exchange Commission rule 7) or privacy concerns and materially affect the deal or pose a risk to the acquirer if the deal were finalized?
- Has the company been involved in an unknown or undeclared material breach, as defended by the recent SEC rule 7, that the company must disclose once known about? These identified issues may have a material impact on the value of a company. Additionally, the company may be financially, civilly, and legally liable if the SEC has not been notified of the material breach.
- Is the company at risk of insider threat from disgruntled employees offering company data or services on the dark web?
- Has the M&A entity or its supply chain been breached, or is a breach likely, which could result in leaked details about their M&A activities on the dark web?
Organizations that purchase or merge with another entity inherit cybersecurity risks. Unfortunately, many companies do not conduct adequate cyber risk assessments to determine if a potential acquisition has been breached or if there are precursors of a breach available to the threat actor to breach the company if they elect to. This lack of exploration can increase the risks of inheriting compromised companies and their networks. In the fast-paced world of M&A, it can be increasingly more work to control cybersecurity risks. At the same time, information security departments may need more personnel and resources to mitigate discovered cyber threats.
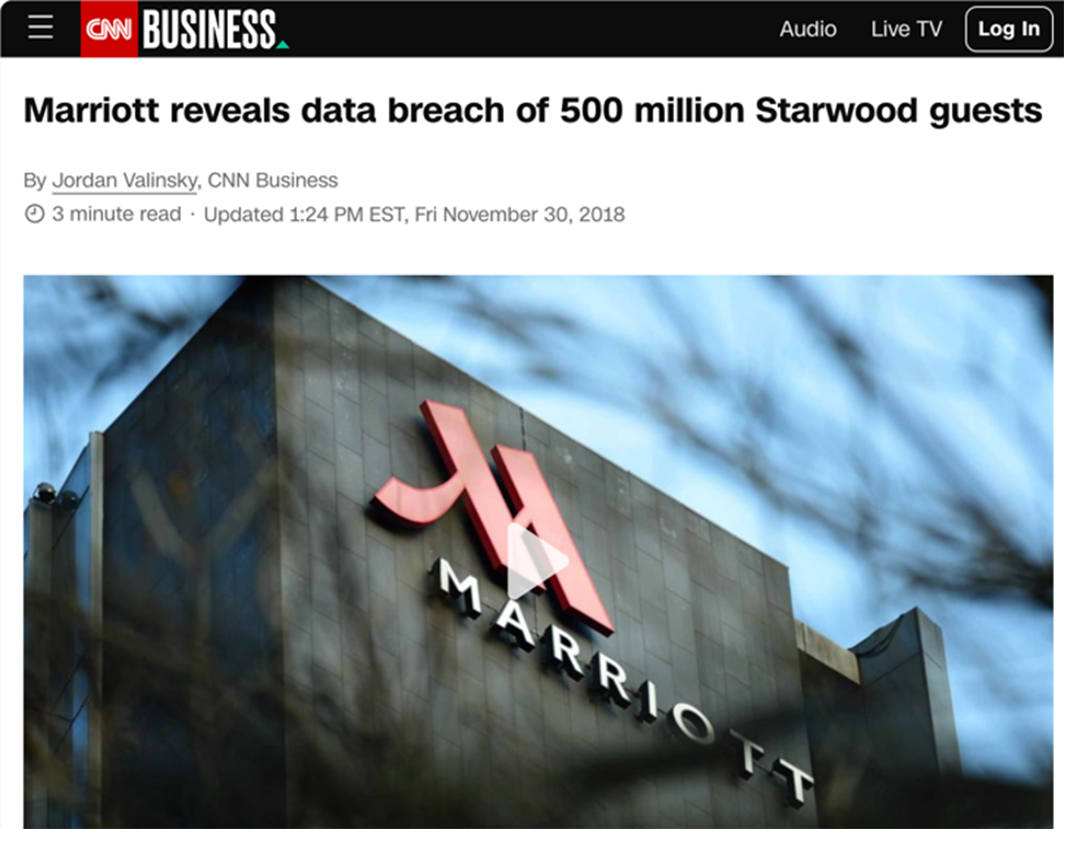
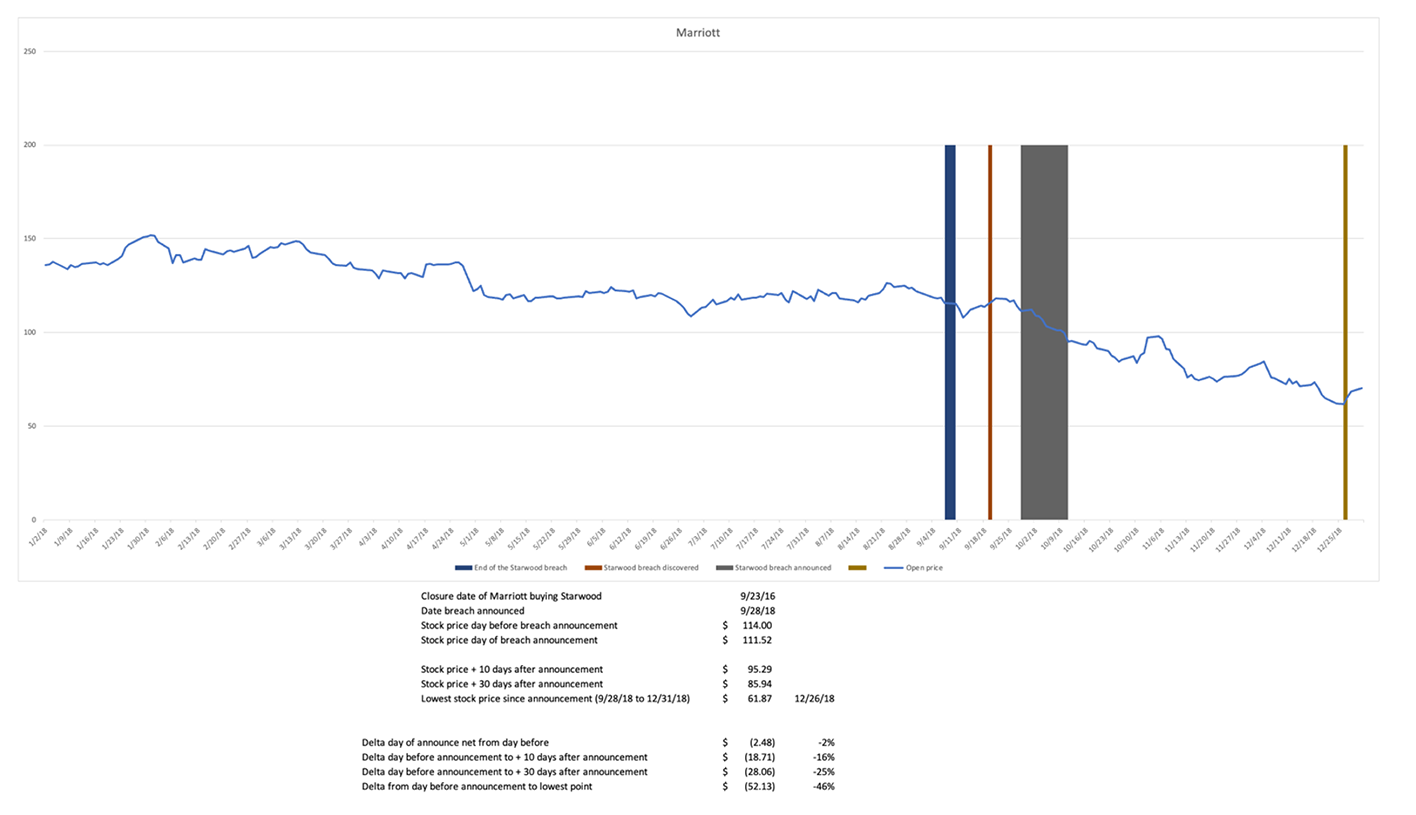
Many factors impact a company’s stock price. Without polling investors, it is unclear whether a stock's decline after a breach disclosure is due to correlation or causation. The Starwood breach was a significant unknown breach that existed before and after its purchase by Marriott. On the day Marriott announced the breach, its stock dropped 2%. In the ten trading days after the announcement, its stock dropped 16%. In the thirty days after the announcement, it dipped 25%. It was 89 days from the date the breach was announced and Marriott’s lowest close for the year, with a stock price drop of 46%.
During the M&A process, external consultants are often involved, depending on the deal's specifics. These consultants typically include investment banks, buying and selling agents, lawyers, auditors, etc. However, it is increasingly common to include CTI vendors as well. These vendors assess the security status of the company being considered for the deal and determine if there has been any breach or theft of valuable items by a known or unknown third party. This information is crucial as it can significantly impact the sale.
It is about more than just evaluating the M&A company. Threat actors more frequently target M&A organizations than typical businesses. Higher-end threat actors use proven and profitable business models such as industrial espionage and stock market manipulation, making breaching an M&A company very profitable. Therefore, M&A entities can benefit from CTI monitoring, such as what Resecurity offers, to safeguard themselves and the other entities involved in M&A activities. Additionally, it is essential to protect the confidential information the seller provides, as any leak could result in a seller's SEC rule 7 disclosure.
Cyber Threat Intelligence (CTI) for M&A
It is common for M&A companies to do CTI analysis during the M&A process. Most M&A companies outsource various aspects of determining the company’s cybersecurity posture to other companies, including a perimeter scan of the company’s network, scans of low-end cybercrime forums (TOR), and a review of the company’s source code. However, external threat intelligence can enhance this vetting by focusing on threats originating outside the company’s firewall and based on access to the surface web, the dark web (TOR), and Vetted / invite-only cybercrime communities. This allows for the following questions to be answered with high confidence:
- Is the company breached, and if so, by whom? What is their motivation? What data has been leaked?
- Are there precursors of a breach that a threat actor could use to breach the company if they elected to do so?
One size does not fit all: A CTI vendor must collaborate with customers to determine their needs and constraints. This will allow them to assist their customers in selecting the right combination of services to meet their requirements, including budget, timeframe, confidence, rules of engagement, and depth of insights.
Based on Resecurity’s internal analysis of discoverable breaches (not every breach can be identified through CTI), if CTI is limited to the surface web, less than 5% of companies that have been breached can be identified. If CTI is limited to the open web and the “dark web (TOR),” less than 25% of companies that have been breached will be identified (surface web (<5%) and dark web (TOR) (<20%)). For discoverable breaches to be discovered, they must include surface web and dark web, in addition to Vetted/invite-only cybercrime communities & P2P (> 75%).
Key takeaways:
CTI offers threat intelligence services to entities involved in M&A to reduce their risks. Some CTI vendors provide services to entities involved in M&A. The scope and scale of these options are scaled up and down to meet the individual customer’s and engagement's needs and budget:
Offering: One-time: Summary report
Timing: Normally less than a week.
Used for: Used during the development of companies for acquisition to help prioritize companies based on their risk.
Deliverable: Summary report of the likelihood that the company is, or likely will be, breached.
- Typically, 1-2 pages.
- Optionally, identify initial areas of risk discovered from external CTI besides items related to a potential breach.
- Can compare the risk of the target company being breached with other specific customers.
- Provides areas of concern and areas of future research.
Offering: One-time managed service: In-depth
Timing: Normally less than three weeks.
They are often used during the due diligence or earlier based on the acquirer's requirements.
Deliverable: A more detailed report of the artifacts discovered during the one-time summary report.
- Typically, 5-10+ pages.
- Duration based on the requirements per customer and engagement.
- Optionally, identify additional areas of risk discovered.
- Provide areas of concern that could be addressed through additional research.
- Research can focus on areas of concern raised in the summary report.
One-time managed service: Mitigation
Timing: Varies and can be done pro- or post-acquisition.
Used for: Aid the victim in mitigating the breach and ejecting the threat actors from their network.
Deliverable: Collaborate with the affected company to assist them in identifying and addressing known threats. Additionally, evaluate the effectiveness of the implemented solutions.
Red Teaming
Timing: Varies and can be done pro- or post-acquisition.
Used for: Aid the victim or the acquirer in identifying and mitigating likely avenues of a potential breach(es) and software and hardware vulnerabilities.
Deliverable Vulnerability assessment and penetration testing. To include strategic intelligence, including IoC, endpoint, and vulnerabilities.
Managed engagement
Timing: Varies. Duration based on the requirements per customer and engagement.
Used for: To help any parties learn more about the threat and the efficacy of the mitigations put into place.
Deliverable: Provide ongoing research to support the mitigation of identified threats.
Ongoing portfolio monitoring
Timing: Ongoing with the cadence of the reports defined by the customer.
Used for: Identify new threats that emerge in their existing portfolio.
Deliverable: Ongoing monitoring of a portfolio of companies managed by an M&A entity.
- Monthly report with alerts for emerging threats.
- Provides an updated list of areas of concern, areas of future research, and mitigations.
Conclusion
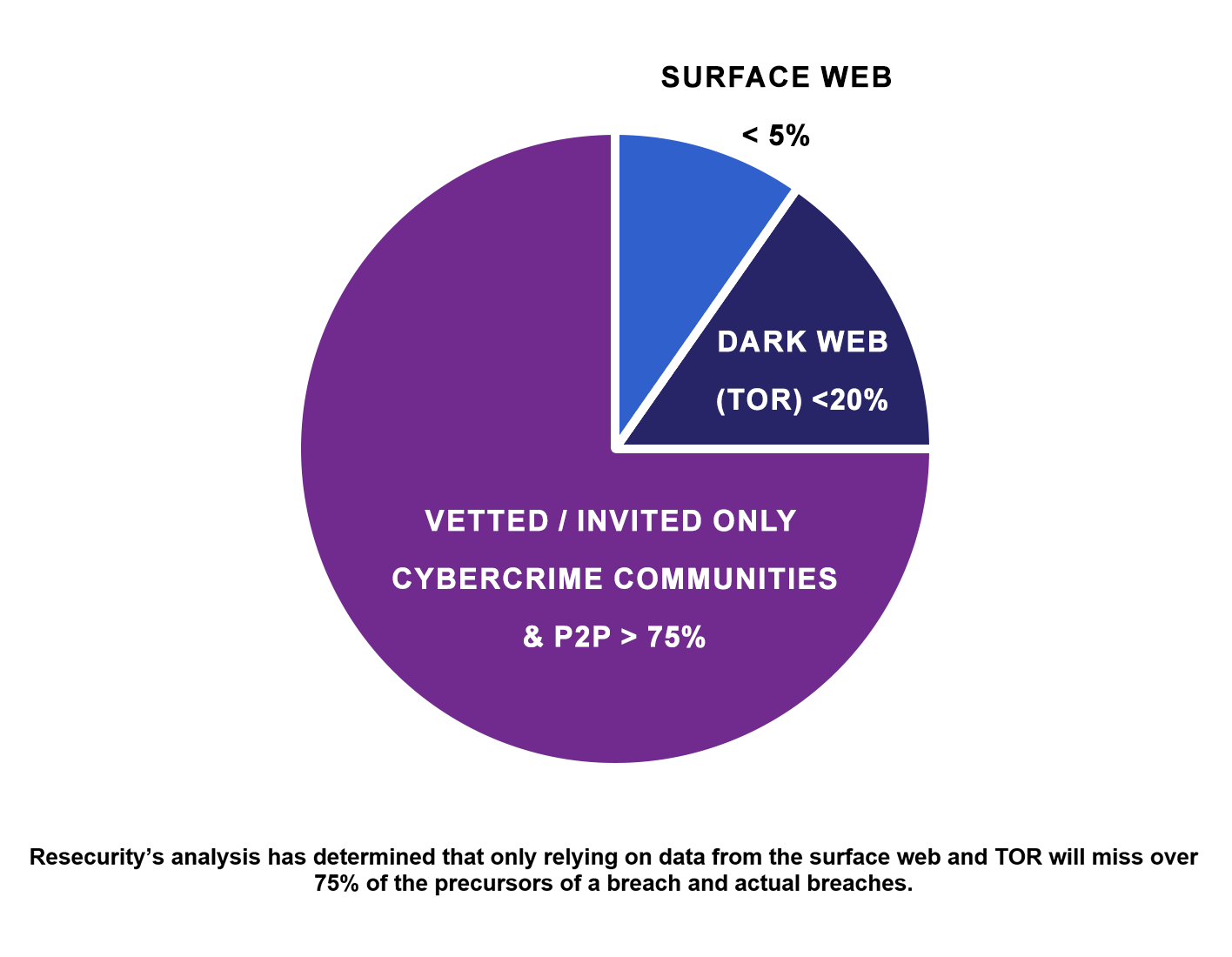
As part of the M&A vetting process, the acquirer is expected to evaluate the source code for misused open-source code, unknown vulnerabilities, and a pen test of the entity's network. Some will go deeper and rely on a CTI vendor for a deeper scan. However, they usually rely on vendors who can only access TOR and the surface web, which gives their clients incomplete visibility and will often miss material issues they are concerned about. Often missing more notable events than they discover. However, an in-depth CTI for an M&A effort can answer critical questions that the acquiring company needs to know to determine the risks of acquiring or making a strategic investment.
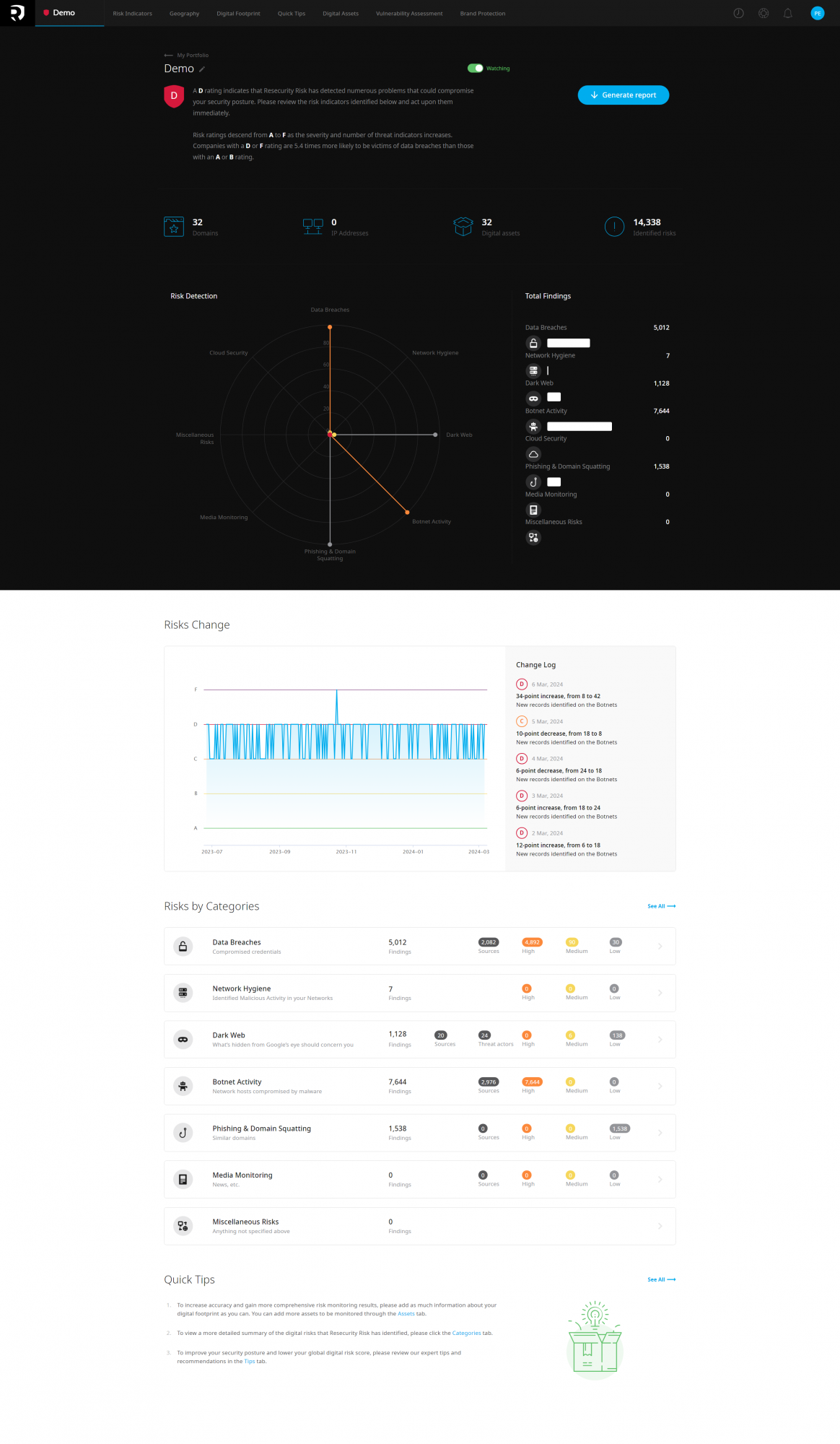
Evaluate Resecurity's RISKTM
To enhance the effectiveness of Mergers and Acquisitions (M&A) and third-party risk assessments, it is highly recommended to evaluate Resecurity's RISKTM platform. This innovative solution offers comprehensive digital risk monitoring, crucial for identifying and managing potential cybersecurity threats and vulnerabilities in real-time.
By integrating Resecurity's RISKTM into the M&A process, organizations can gain a deeper insight into the digital landscape of potential partners or acquisition targets, ensuring a more informed decision-making process and safeguarding against inheriting hidden cybersecurity risks.
In today's digital-centric world, adopting a proactive strategy is key to preserving the integrity and ensuring the success of M&A deals. This approach is crucial for navigating the complex cyber landscape and securing the true value of transactions.
Resecurity is successfully protecting major Fortune 100 corporations worldwide and publicly-traded companies from emerging cybersecurity threats. Please, contact our team for cyber risk assessment and advisory regarding possible M&A deals in order to evaluate potential challenges associated with planned transactions.