Iran-Linked Threat Actors Leak Visitors and Athletes' Data from Saudi Games
Cyber Threat Intelligence


Incident
Today (June 22, 2025) — the threat actors associated with the "Cyber Fattah" movement leaked thousands of records containing information about visitors and athletes from past Saudi Games, one of the major sports events in the Kingdom. The stolen data has been leaked in the form of SQL dumps - the actors gained unauthorized access to phpMyAdmin (backend) and exfiltrated stored records. Resecurity views this incident as part of a broader information operation (IO) carried out by Iran and its proxies for various objectives.
Based on our assessment, this is an example of Iran using data breaches as part of a larger anti-US, anti-Israel, and anti-Saudi propaganda activity in cyberspace, targeting major sports and social events. Due to the significant scale of the data breach and the precedent set by Iranian proxies attacking major sporting event, Resecurity is sharing the collected intelligence to raise awareness within the cybersecurity community and to equip stakeholders with actionable insights and risk mitigation strategies.
The leak was announced at 6:27 PM PST on Cyber Fattah's official Telegram channel, following the DDoS attacks on Truth Social, a popular social media network, after the U.S. conducted airstrikes on Iran’s nuclear sites.
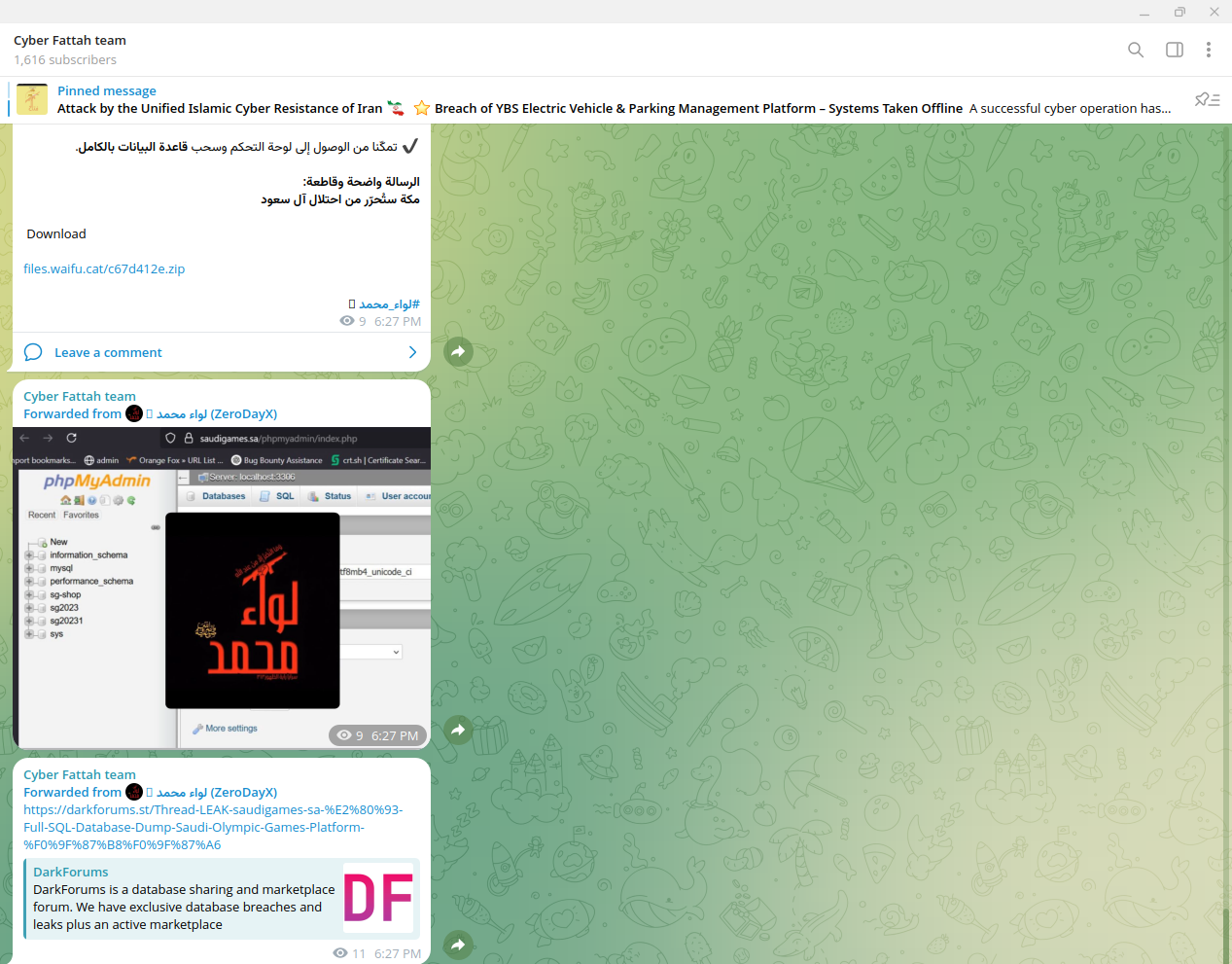
According to the official website of the event:
"the Saudi Games is the largest national sporting event held annually in the Kingdom. It is a multi-sport combined tournament featuring more than 53 sports, with over 6,000 athletes participating. The event contributes to achieving several goals of the Kingdom’s Vision 2030, including raising the quality of life through sports excellence, inspiring Saudi youth, and creating an emerging sports generation capable of representing the Kingdom in international sports forums by revealing and developing talents, and providing spaces and opportunities to practice all sports activities."
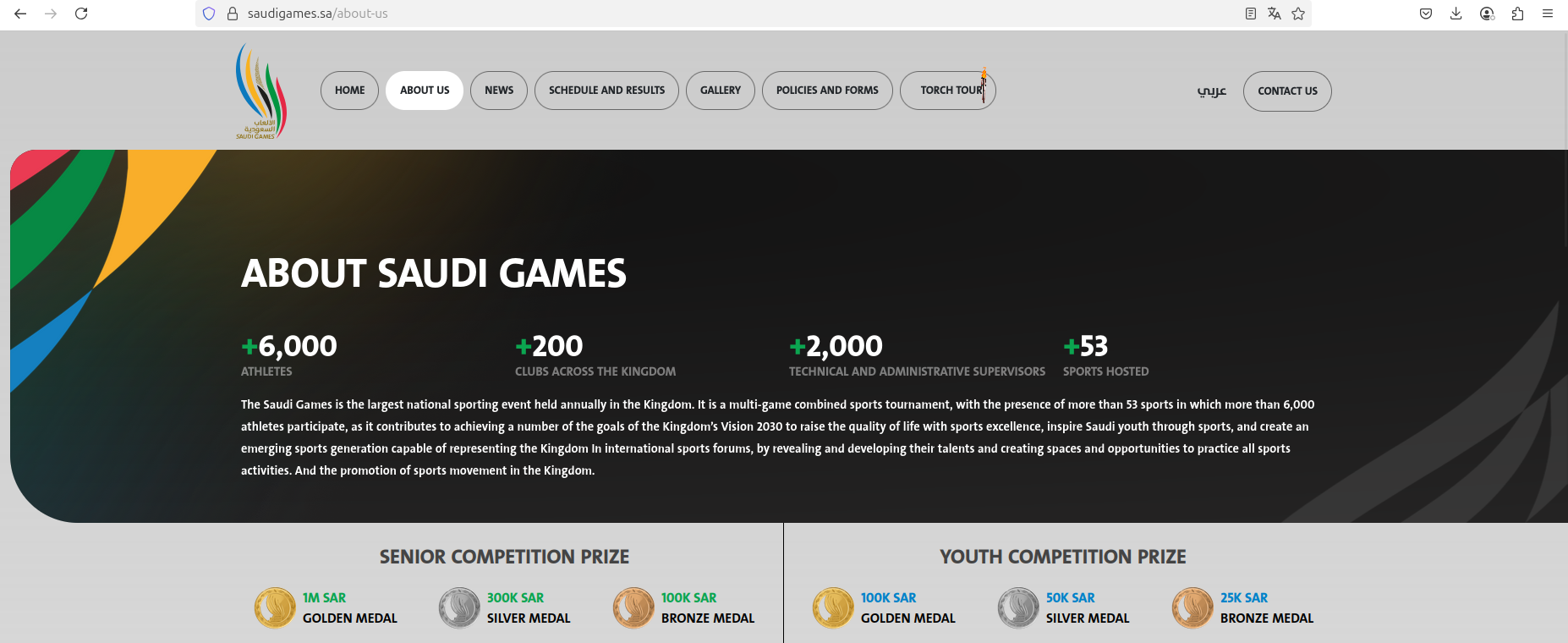
Notably, this incident is significant due to increasing Israel-Iran tensions, with threat actors aiming to capitalize on the important role of the Kingdom of Saudi Arabia and the United States in regional relationships and security. Several Hezbollah-linked, Hamas-linked, and pro-Iranian groups in Iraq also amplified the incident by integrating it with targeted propaganda activities via digital media channels.
Background
The data originates from a database presumably related to the Saudi Games 2024 official website, where visitors, athletes, and their teams register and share their personal information for further validation and activation of their profiles. The actors described the event as one of the largest in the region, massively followed locally, and officially launched by the Government of the Kingdom of Saudi Arabia to promote sports nationwide. It is likely that the choice of target was not random and was part of an information operation (IO) orchestrated by Iran to spread a narrative of insecurity.

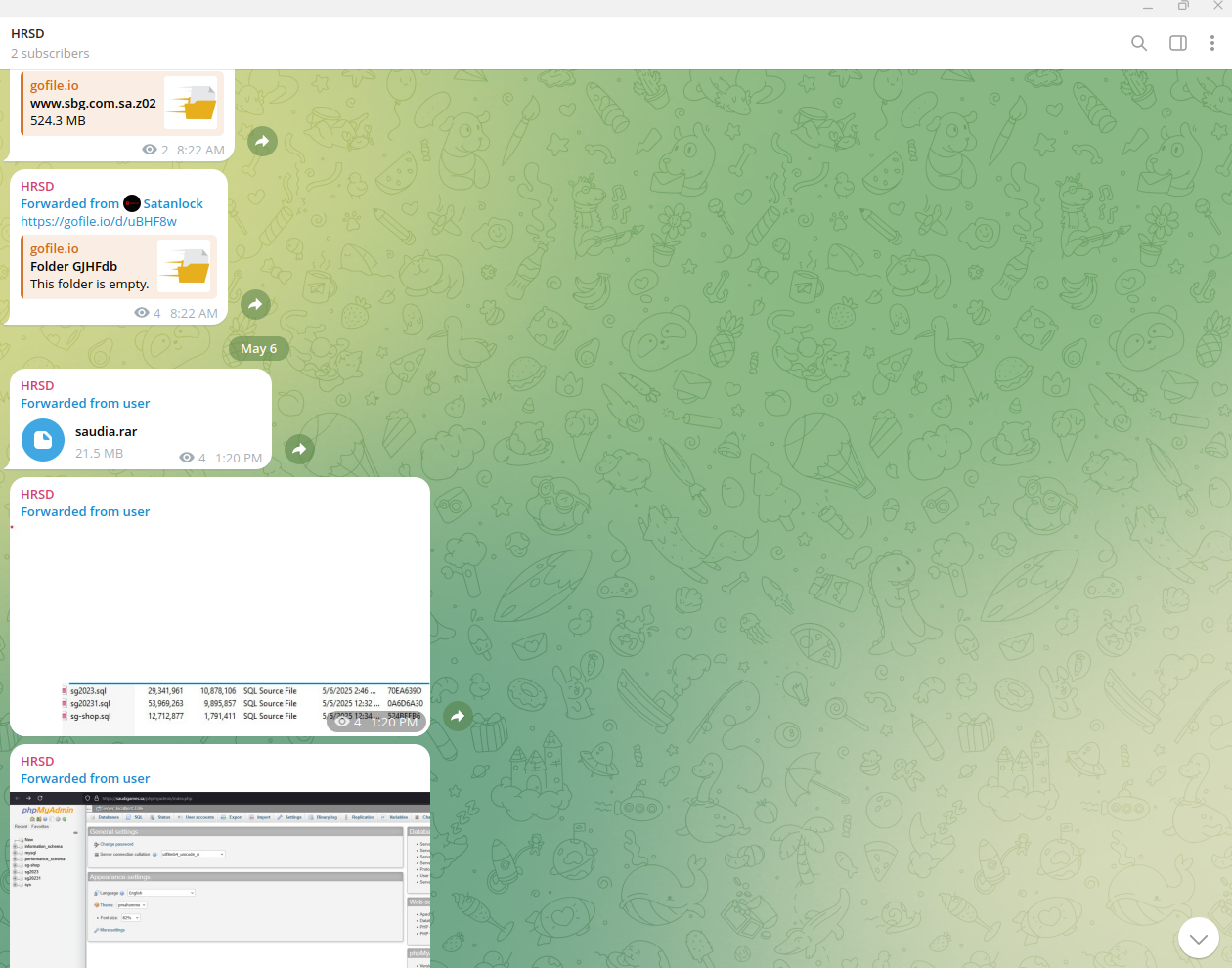
After the recent announcement on "Cyber Fattah" channels, the data was leaked in one of the prominent underground communities on the Dark Web. The actor, known by the moniker 'ZeroDayX'. His profile is a recent “burner profile” and contains only two posts, which confirms that it was likely created to promote and distribute the stolen data across the Dark Web. It is very common for the parties behind major data leaks to use a 'front' actor. or in this case a burner profile, to release the data, thereby obscuring attribution.
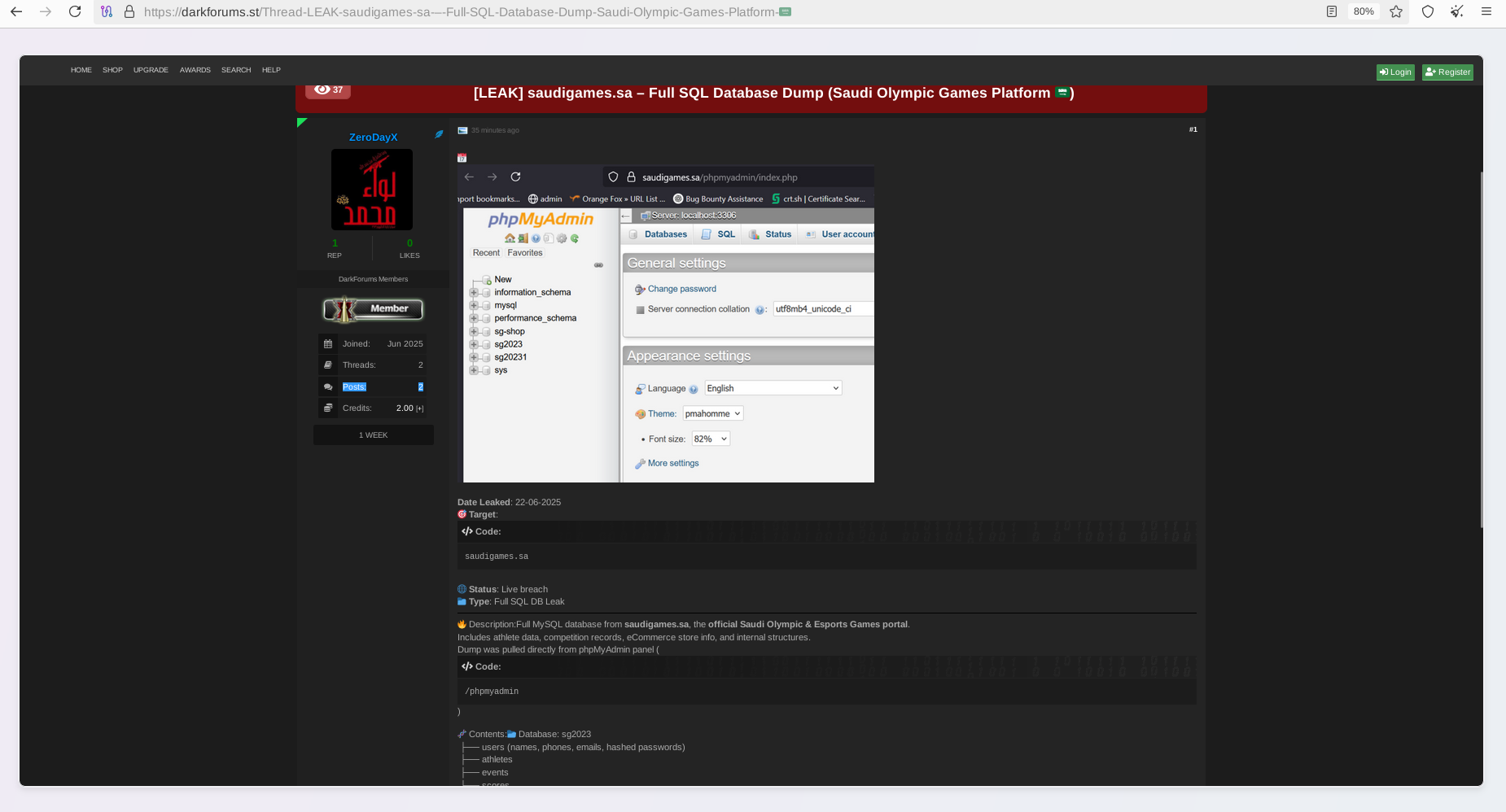
The leaked data contains multiple databases:

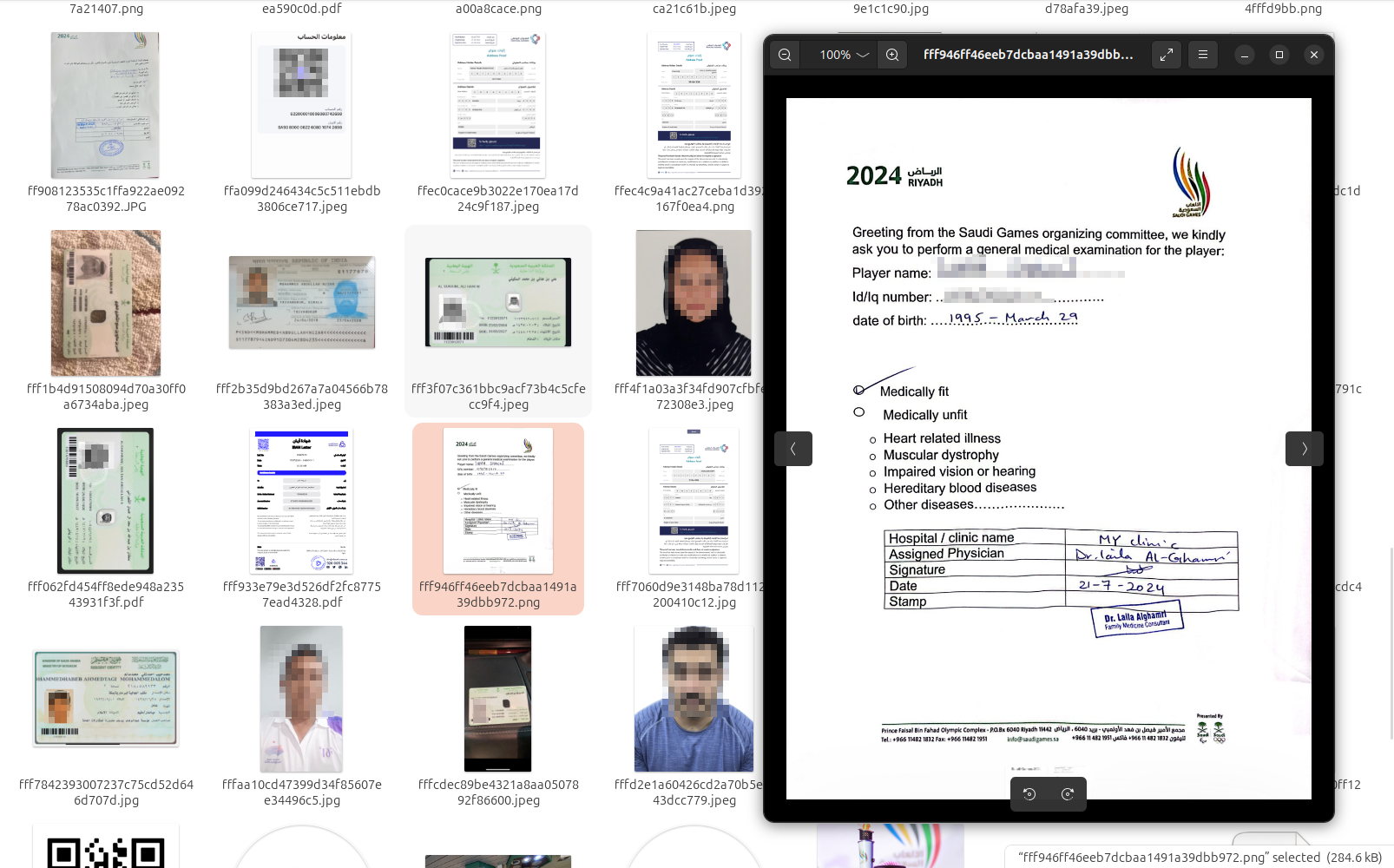
Notably, the first non-public claims about the compromise of Saudi Games began circulating on the Dark Web at the beginning of May 2025. Resecurity informed trusted law enforcement partners about this activity and shared artifacts obtained from one of the sources in Iran. The timestamp of the SQL dump creation suggests that a threat actor generated it on May 5, 2025.
The actor associated with several other data breaches affecting the Kingdom was attempting to monetize stolen data from Saudi Games in a private capacity. It is possible that the mercenary or the actual actor linked to Iranian activities wanted to profit from it "on the side." Such behavior was previously observed by specialists from our HUNTER team (threat intelligence & investigations), who tracked actors from Iran.
Based on information collected from sources, these actors conducting attacks on behalf of foreign states are often not well paid; therefore, they seek alternative monetization methods, which involve certain risks if they are identified. Resecurity has established trusted contacts with several of these actors to acquire sensitive intelligence, helping organizations defend against planned attacks by Iran. As a result of Human Intelligence (HUMINT) engagement, Resecurity was able to acquire the complete data set. In contrast, the one leaked via a Dark Web forum recently was limited to text records.
What Has Been Leaked
The breach of such a scale contains a trove of sensitive data, ranging from personally identifiable information (PII) of visitors and athletes to International Bank Account Numbers (IBANs) and medical examination certificates shared with the event organizers.
- IT staff credentials
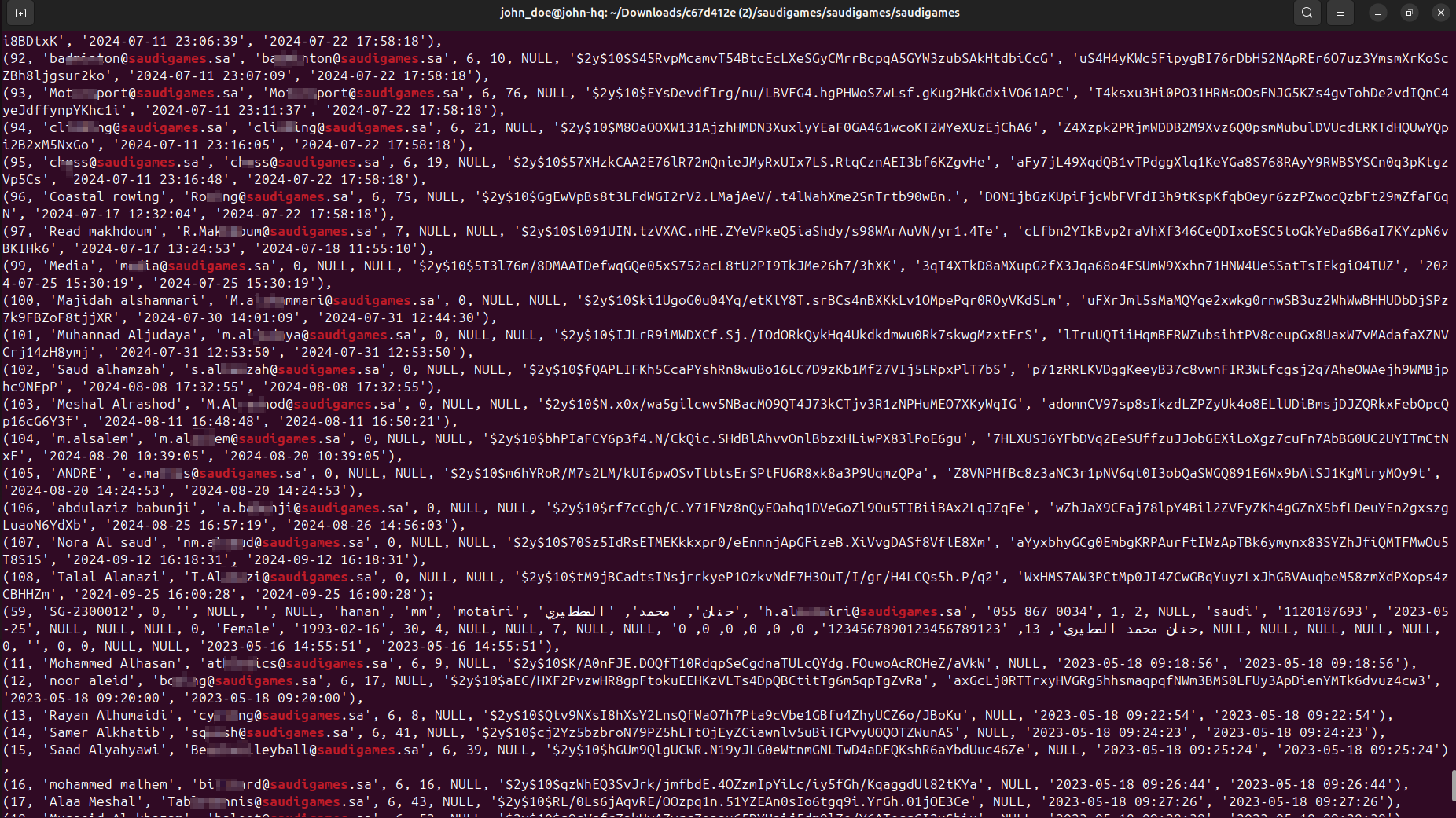
- government officials
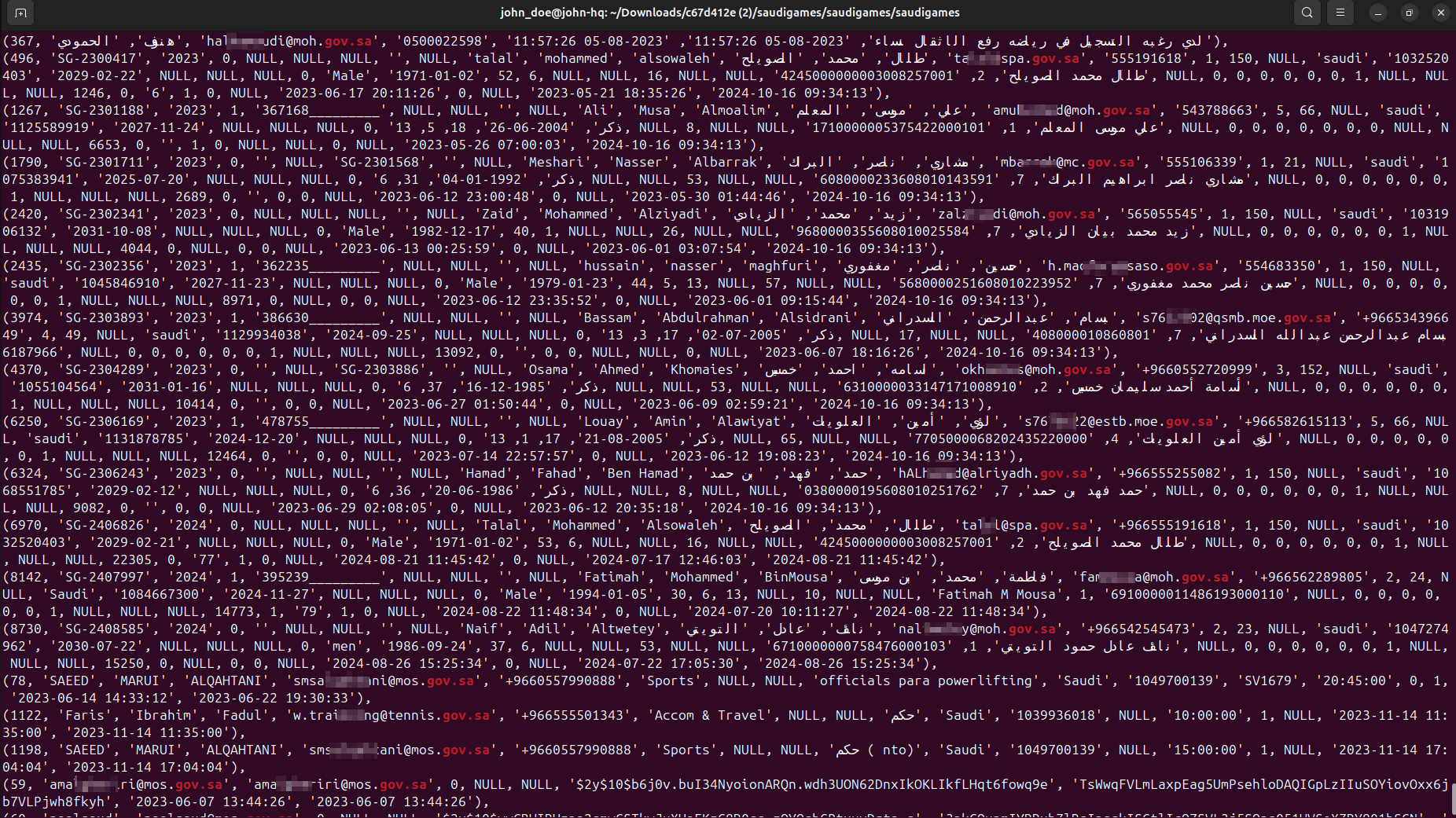
- athletes/visitors information
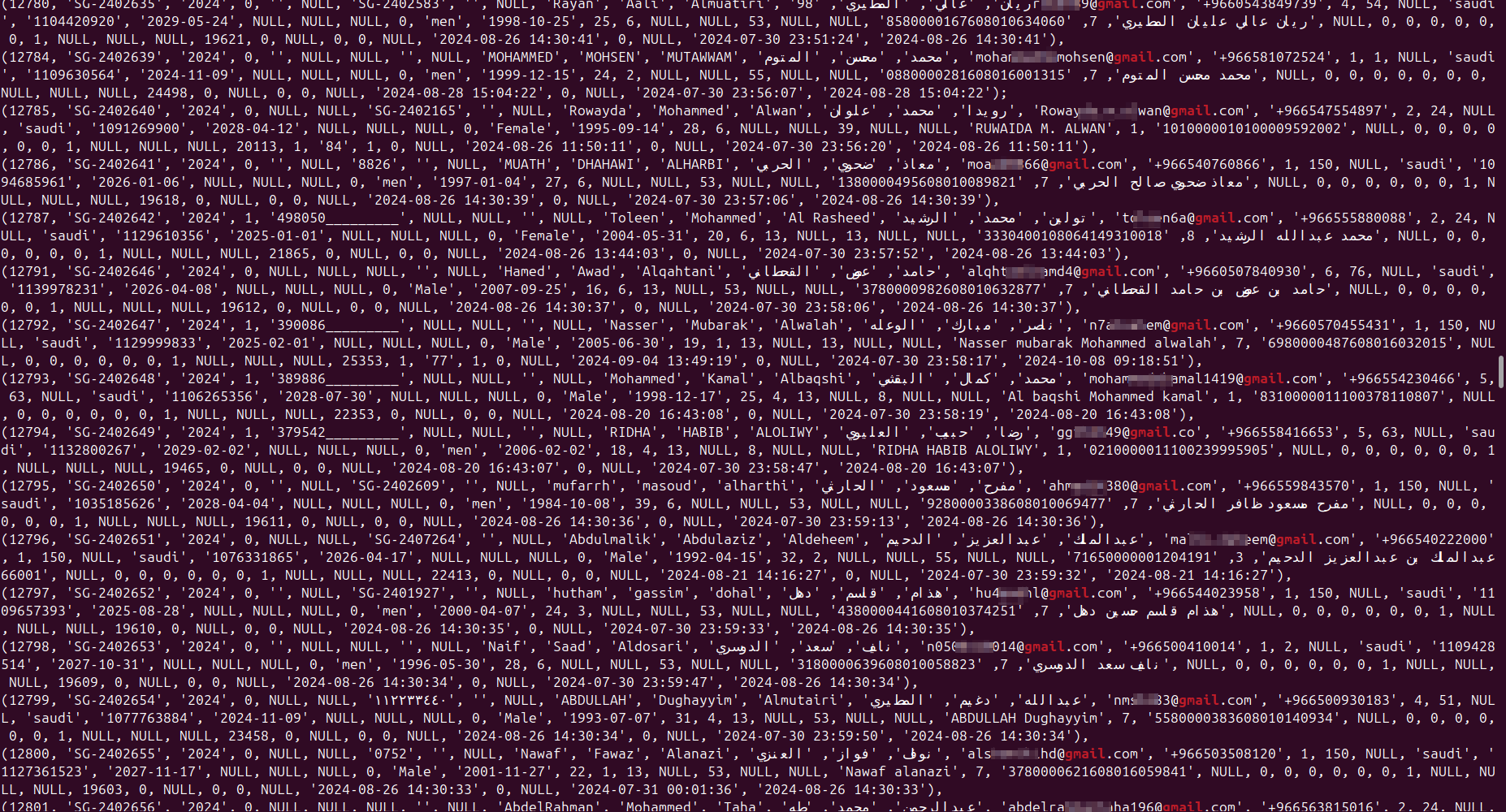
- passports and ID cards
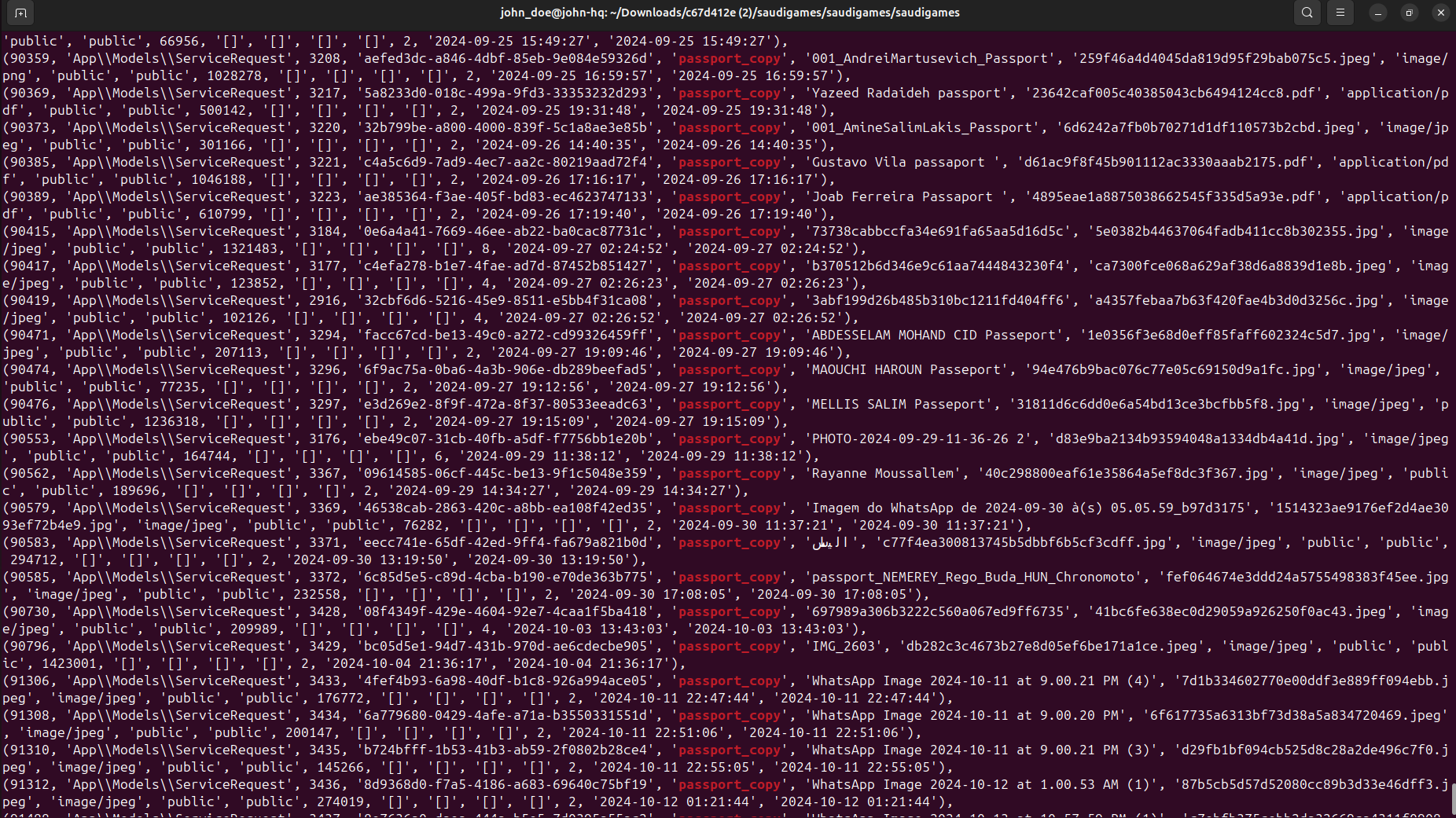
- bank statements, IBAN certificates and other records
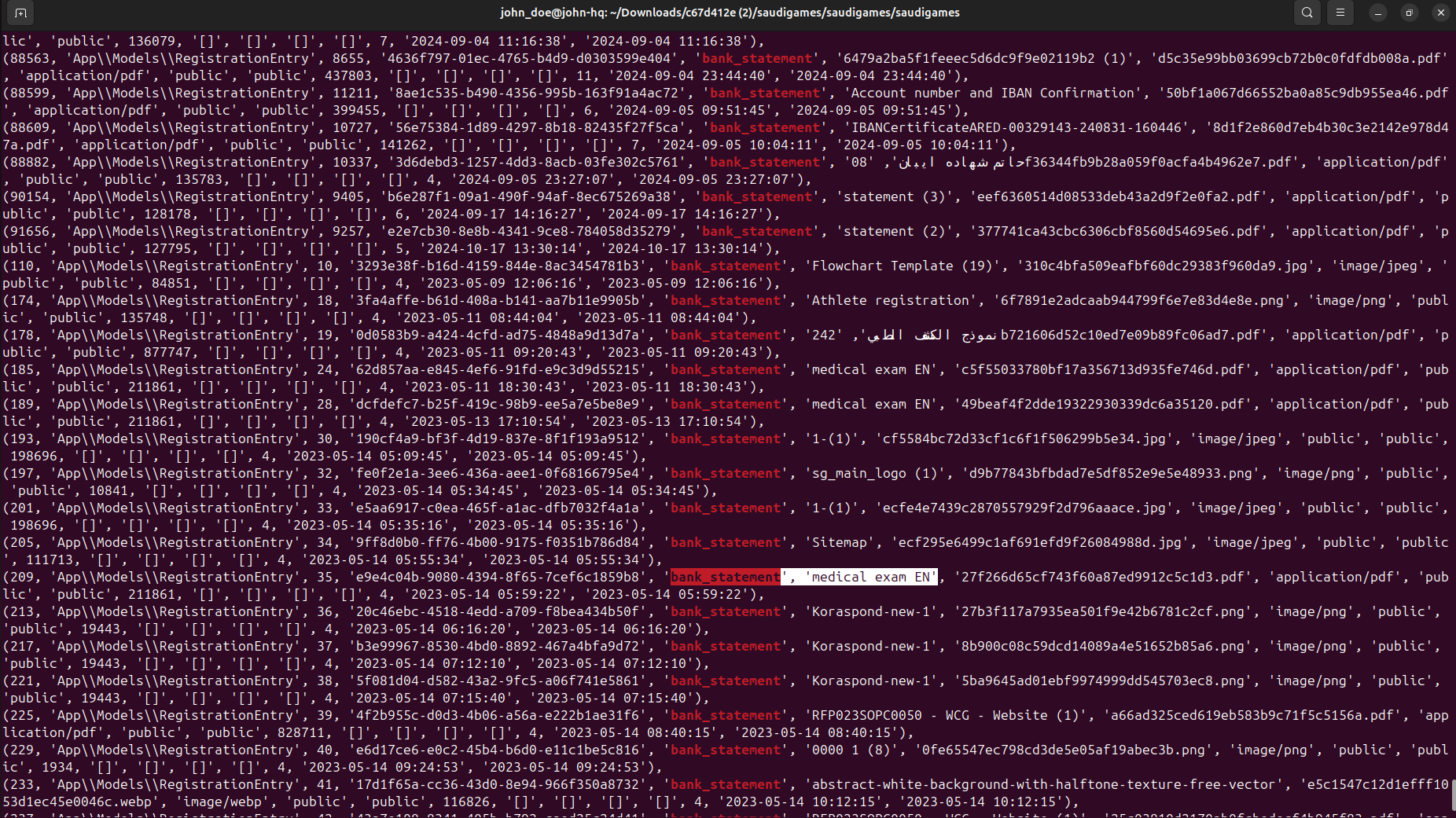
- medical forms
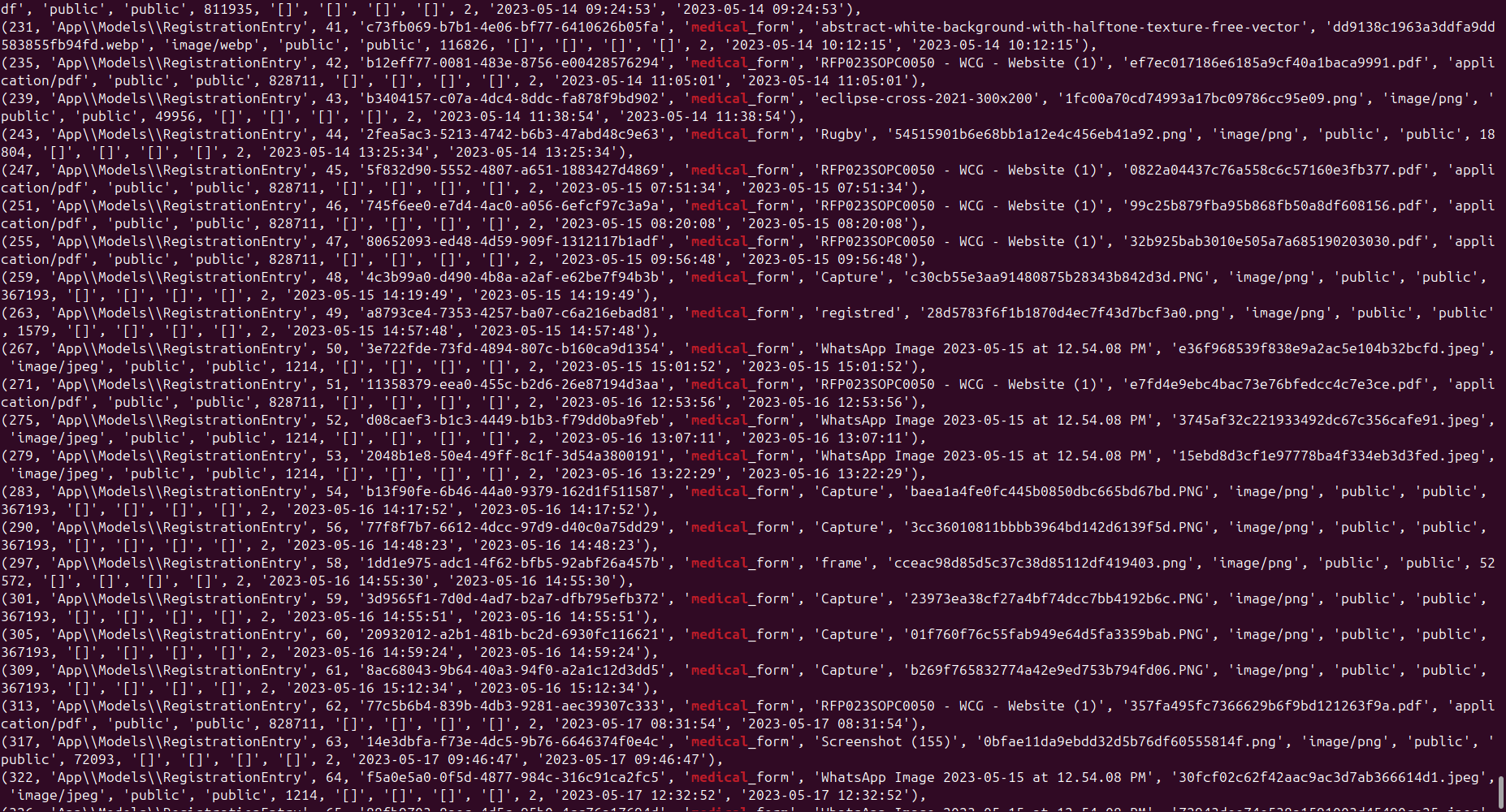
The most concerning issue is the insecure storage of personal documents in the form of scans, which have been targeted by threat actors. Cyber Fattah was able to exfiltrate thousands of sensitive documents related to Saudi citizens and foreigners visiting the Kingdom.
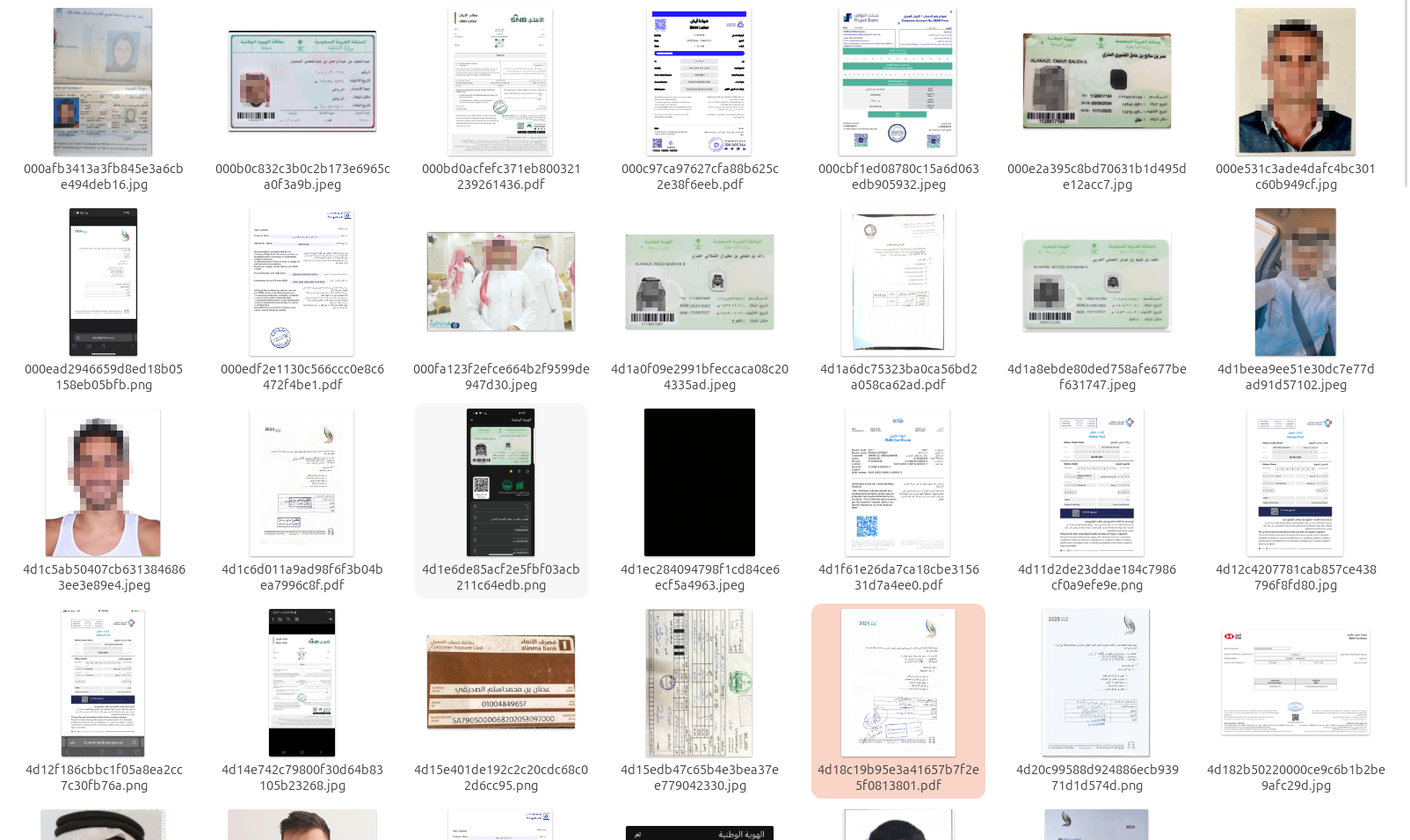
The artifacts observed in the leak confirm references to Saudi Games.
Cyber Fattah: Origins and Identity
The activities of Cyber Fattah align with a broader trend of hacktivism in the Middle East, where groups frequently engage in cyber warfare as a form of activism. In some cases, it is complicated to differentiate between activities that are state-supported, state-sponsored, tolerated by the state, or purely conducted due to hacktivism. Based on recent developments, the activities of hacktivists and the narratives promoted by Iran are overlapping, as they are based on a common ideology and propaganda.
For example:
- Pro-Iranian hacktivist groups have launched coordinated attacks on Israeli military and government targets.
- Other groups, such as Anonymous, have also conducted operations in support of the Palestinian cause, including attacks on Israeli websites during conflicts in Gaza.
- Iranian state media resources amplified these events by technically directing actors to conduct cyber-attacks and other forms of malicious activity.
From another perspective, with the start of the Israel-Iran conflict, the group has accelerated its activities, specifically targeting Israel, the Kingdom of Saudi Arabia, and the United States. Iran extensively employs malicious cyber activities within targeted information operations (IO) to sow chaos across the region.
Iran's propaganda against Saudi Arabia is primarily driven by their competition for regional dominance, including the following key aspects:
- Both nations vie for influence across the Middle East
- Iran supports Shia militias in various countries
- Saudi Arabia is seen as a threat to Iran's regional ambitions
A major driver of anti-US propaganda stems from disputes over Iran's nuclear program, as well as support for Israel and Saudi Arabia.
The group is also calling itself "Iranian Cyber Team," and it has a significant track record of attacks against Israeli and Western web resources and government agencies.
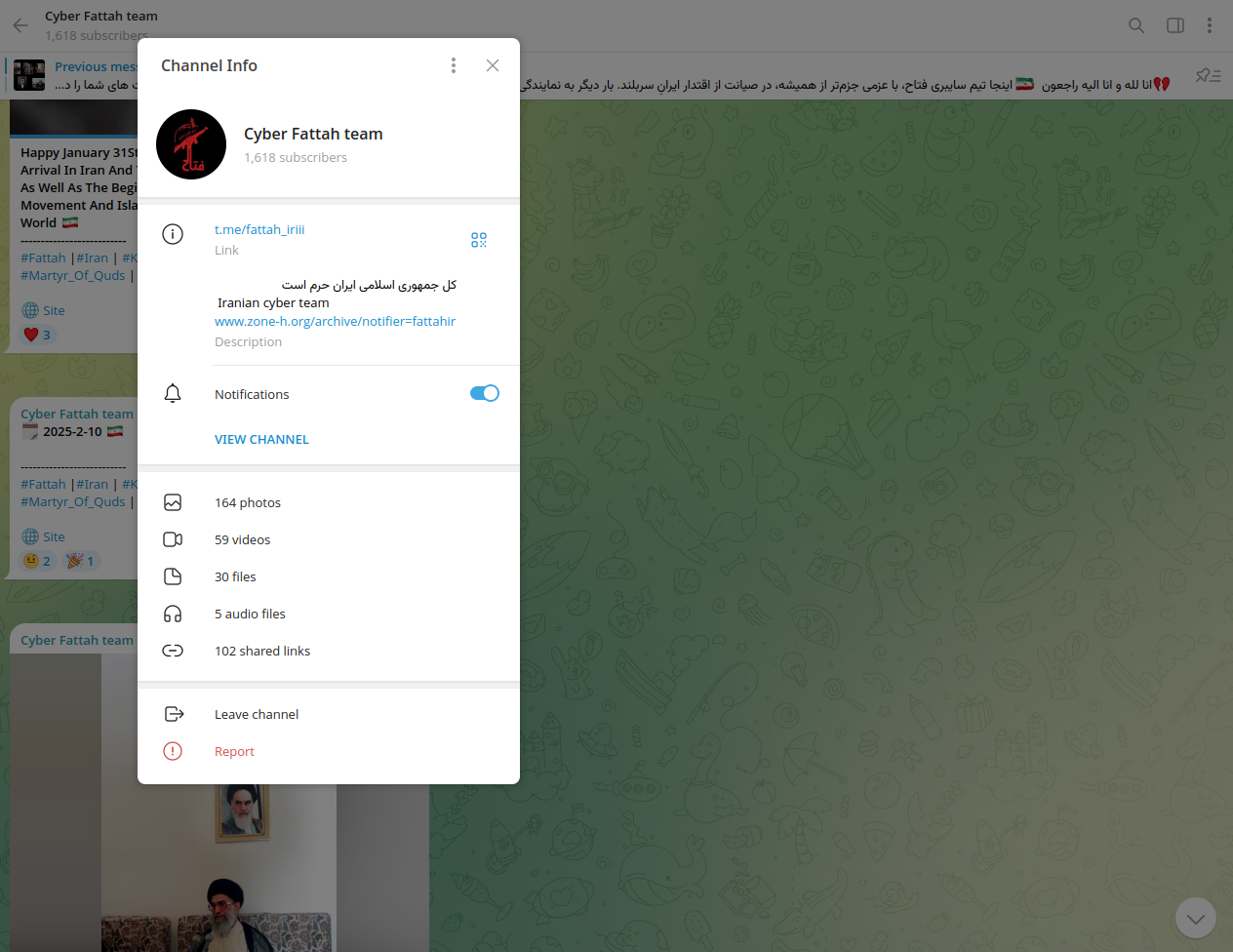
The group has close collaboration with other threat actors known as:
• 313 Team (@xX313XxTeam)
• LulzSec Black (رابط التليغرام) (https://t.me/+mC1MrRnDp5FjNmQ0)
• Cyber Islamic Resistance (@Mhwear98)
Cyber Fattah is also a member of the so-called "Holy League" - a conglomerate of hacktivists targeting Israel. In the past, Cyber Fattah has conducted cyber-attacks against an Israeli solar energy company, with the assistance of the so-called Iranian and Lebanese Islamic Cyber Resistance battalions.
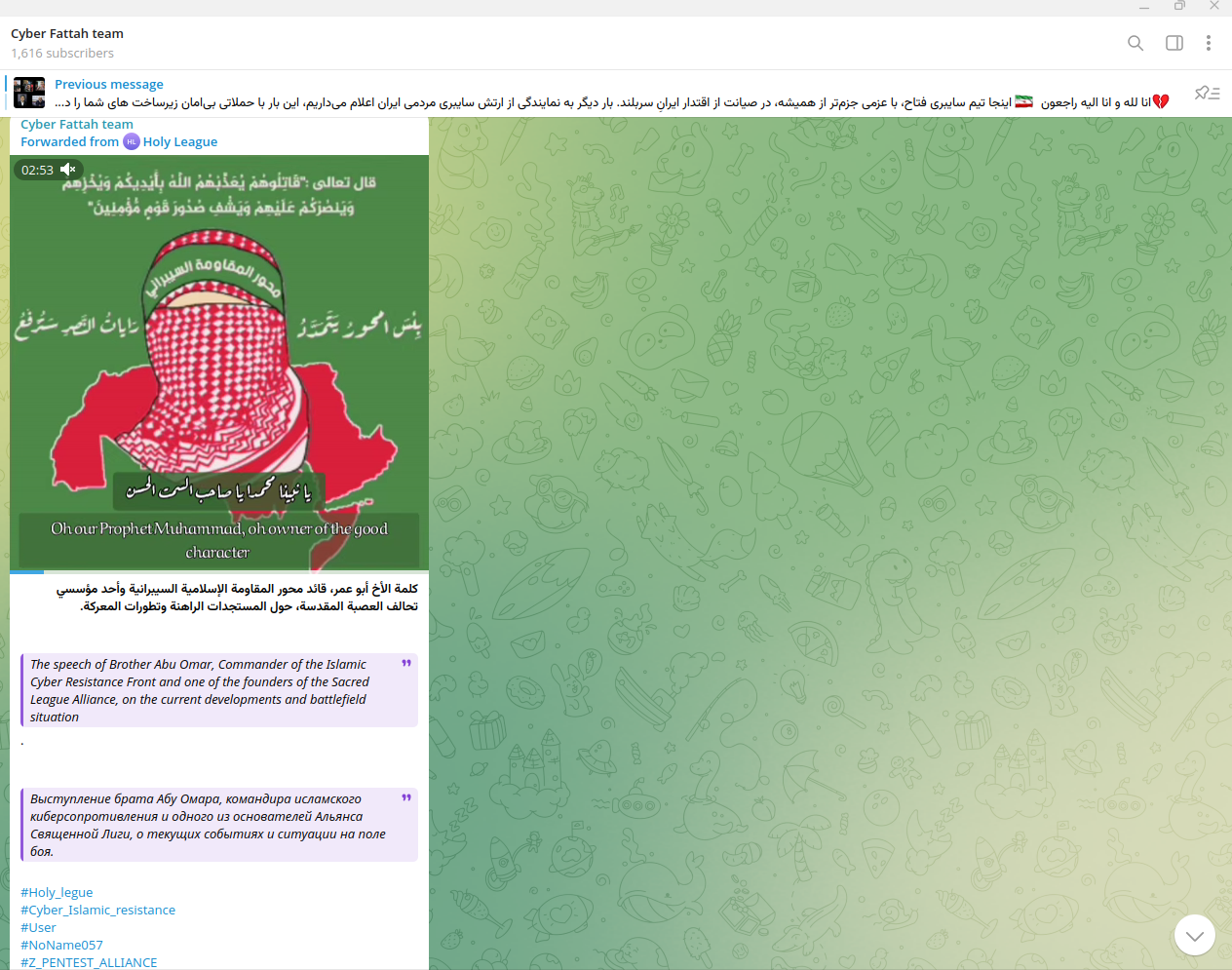
May 18, 2025 - The "Holy League" cyber alliance announced the declaration of affiliated "cyber units" to target Ukraine and Israel.
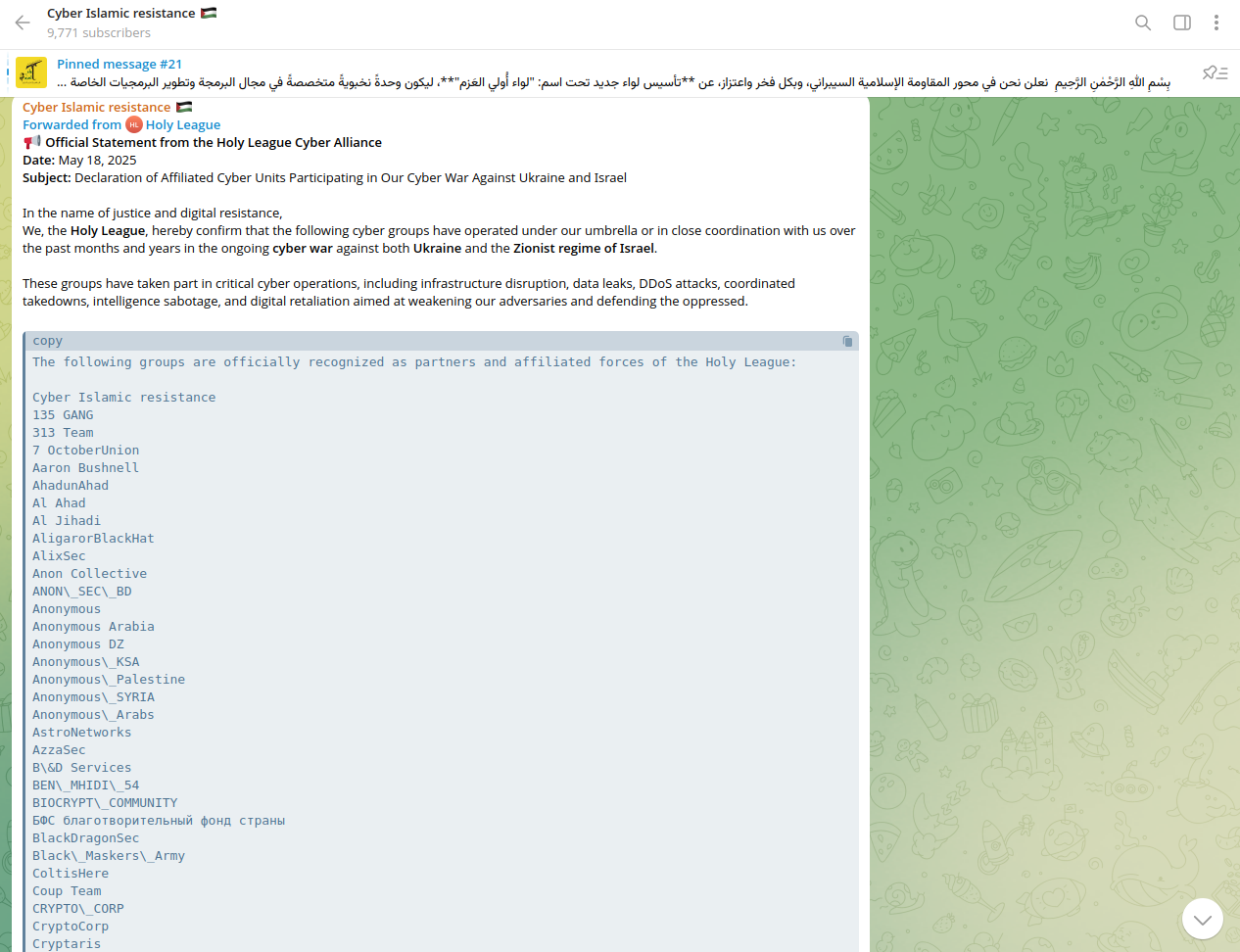
Earlier, the group announced cooperation with CyberVolk, a non-Arabic-speaking hacktivist group, known to target NATO countries.
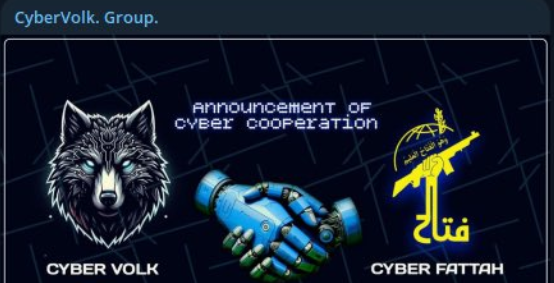
Notably, some of their defacements contain reference to "Liwaa Mohammad", whom we associated with 'ZeroDayX' moniker.
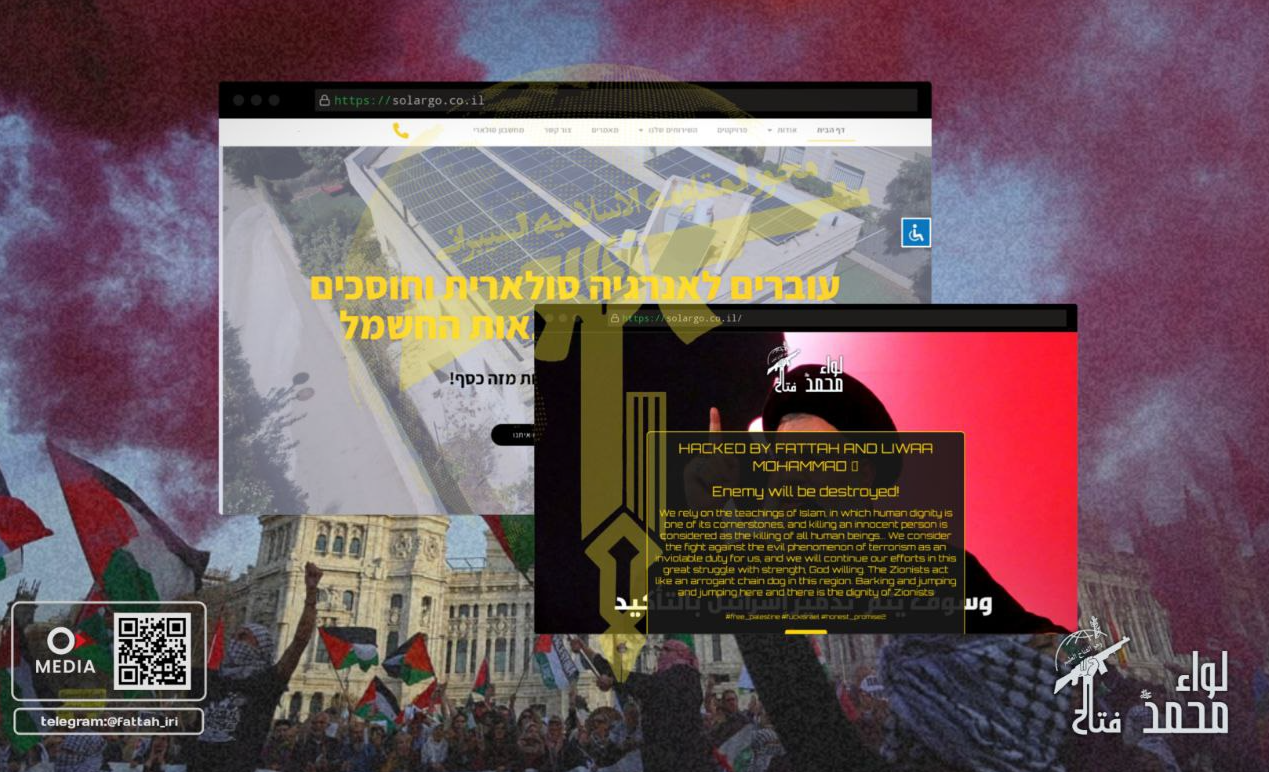
Defacements by the same actor prior to 2025 included images of Hassan Nasrallah, the former secretary-general of Hezbollah.
The actor has also been seen in several groups with pro-Hezbollah ideology, having a significant presence in Lebanon.

Multiple episodes of anti-Israeli and anti-Saudi propaganda were observed, during which actors aim to spread misleading information to amplify geopolitical events.
Multiple postings by Cyber Fattah actively support the Supreme Leader of Iran, Khamenei, and promote an anti-Israel agenda.
The new propaganda content released by them also targets Donald Trump, the President of the US.
This incident by Cyber Fattah may indicate an interesting shift from Israel-centric malicious activity toward a broader focus on anti-US and anti-Saudi messaging. Likely, such maneuvers are aligned with psychological operations conducted by Iran to spread propaganda and malicious narratives.
Sports Events - The Next Target?
Indirectly, the threat actors sent a concerning message, potentially targeting major sports events worldwide.
Hackers are increasingly targeting major sports events due to a combination of financial, political, and strategic motivations. These events present unique vulnerabilities and opportunities for cybercriminals and state-sponsored actors. Below are the key reasons why hackers focus on such events:
1. Financial Gain
Valuable Data: Major sports events involve vast amounts of sensitive data, including personal information of athletes, teams, and spectators, as well as financial transactions. Cybercriminals can steal and sell this data on the dark web or use it for identity theft and fraud.
Ransomware Attacks: Hackers often deploy ransomware to encrypt critical systems, such as ticketing platforms, stadium operations, or broadcasting networks, demanding large sums of money to restore access. For example, ransomware attacks have previously disrupted sports organizations, including encrypting IT systems and affecting stadium operations.
Ticket Scams: Cybercriminals target ticketing systems to steal payment information or sell fake tickets, exploiting the high demand for event access.
2. Political and Geopolitical Motivations
State-Sponsored Espionage: Nation-states may target international sporting events for espionage or sabotage. For instance, during the 2018 Winter Olympics, state-linked hackers launched disruptive cyberattacks aimed at sabotaging the event.
Geopolitical Messaging: Events like the Olympics or FIFA World Cup are high-profile platforms that can be exploited to send political messages or retaliate against perceived adversaries. For example, Russian hackers targeted the World Anti-Doping Agency (WADA) after Russian athletes were banned from the Olympics.
3. Disruption and Sabotage
Operational Disruption: Hackers may aim to disrupt the smooth functioning of events by targeting critical infrastructure, such as turnstiles, CCTV systems, or broadcasting networks. This can lead to event delays or cancellations, causing reputational damage to organizers.
Distributed Denial of Service (DDoS) Attacks: DDoS attacks can overwhelm event-related websites or streaming platforms, disrupting ticket sales, live broadcasts, or online betting systems.
4. Exploiting the Digital Surface
Interconnected Systems: Modern sports events rely heavily on interconnected digital systems, including IoT devices, payment systems, and broadcasting networks. A single misconfigured device or weak password can provide hackers with an entry point to compromise the entire network.
Emerging Technologies: As technologies like 5G and biometric tracking become more integrated into sports events, they create new vulnerabilities that hackers can exploit.
5. Targeting High-Profile Individuals
Athletes and Teams: Hackers may target athletes, coaches, or teams to steal sensitive data, such as performance metrics, medical records, or proprietary strategies. This information can be used for blackmail, extortion, or to gain a competitive advantage.
Sponsors and Advertisers: High-profile sponsors and advertisers associated with major events are also lucrative targets for cybercriminals, as they handle significant financial transactions and sensitive marketing data.
Significance
The hack of a major sports competition is significant for several reasons, as it can have wide-ranging implications across multiple domains, including cybersecurity, sports integrity, and global audiences.
No date has yet been confirmed for the Saudi Games 2025, but the Kingdom is hosting a variety of major sports events that attract audiences from all over the world including:
- Islamic Solidarity Games
A multi-sport event held every four years by the Islamic Solidarity Sports Association (ISSA)
- Esports World Cup 2025
One of the major e-gaming international competitions
- 2026 Gulf Cup
The Kingdom will host the upcoming global soccer tournament
Hosting the Olympics in 2036 is one of the national targets and priorities for Saudi Arabia. Likely, threat actors attempted to interfere with efforts of the country and abuse the reputation of the Kingdom of Saudi Arabia by conducting a targeted cyberattack on the Saudi Games.
Mitigation Measures
Resecurity recommends implementing Digital Identity Protection solution to safeguard consumers and businesses. Recognizing the escalating cyber threats in the Middle East, Resecurity's IDP solution is poised to play a pivotal role in safeguarding the digital identities of Saudi citizens.
In a significant stride towards fortifying the cybersecurity landscape in the Middle East, Resecurity proudly introduced its state-of-the-art Digital Identity Protection (IDP) solution at the prestigious Black Hat Middle East & Africa conference.
This strategic move aligns with Resecurity's commitment to creating a safer digital society and empowering individuals and businesses in the region to counteract cyber threats effectively.
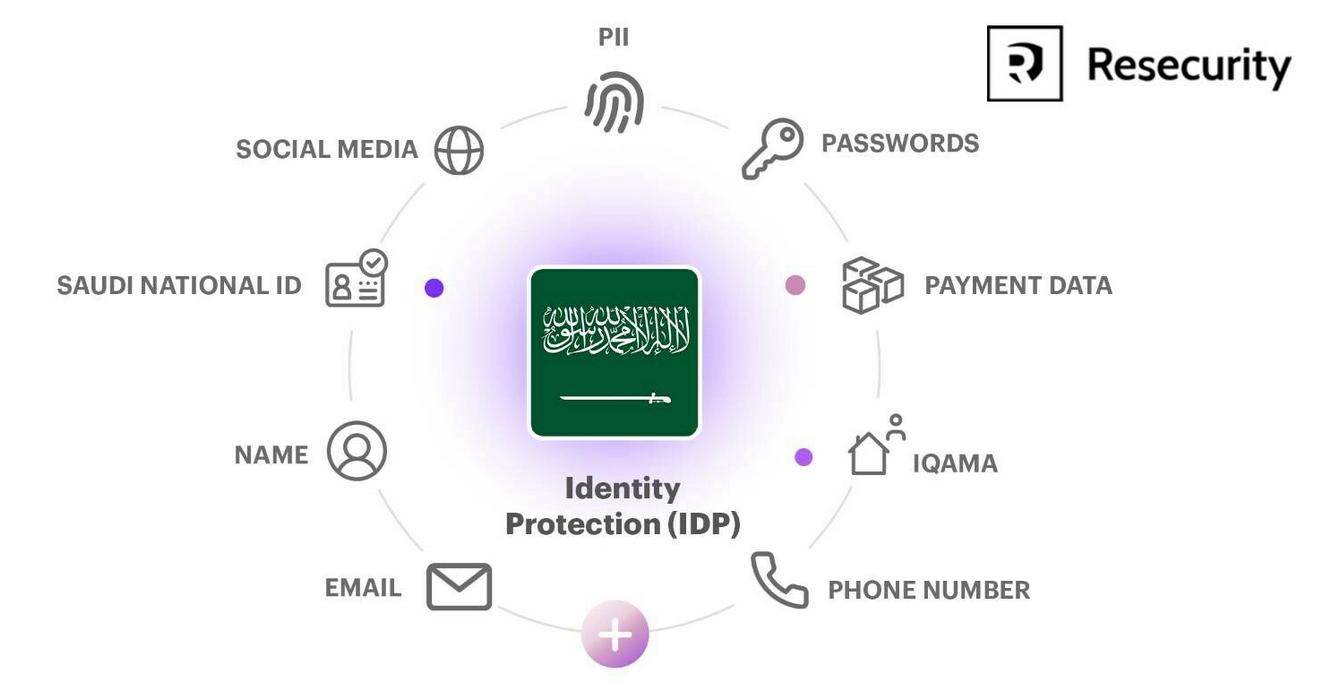
The IDP service provides a comprehensive defense mechanism, enabling individuals and enterprises to proactively monitor and receive early-warning notifications to protect their accounts and personal data.
Cyber Threat Intelligence (CTI) by Resecurity empowers organizations to proactively safeguard against breaches and attacks stemming from leaked personally identifiable information (PII) of employees, vendors, or customers. Utilizing its Context™ and Risk™ platforms, Resecurity scans the surface, deep, and dark web for compromised data, delivering real-time alerts and actionable insights when sensitive information or leaked credentials are identified. The application of predictive analytics and indicators of compromise (IoCs) enables early threat detection, allowing firms to respond swiftly and prevent breaches.
In addition to detection capabilities, Resecurity offers support for incident response, risk management, and threat mitigation. Its CTI services provide comprehensive intelligence reports to assist in containment and remediation efforts, while the HUNTER™ framework facilitates continuous, customized threat hunting within the illicit online community. These resources also support the evaluation of third-party and supply chain risks, ensuring a broader protective net around the organization’s ecosystem. By integrating advanced analytics, monitoring threat actors, and providing timely intelligence, Resecurity helps companies identify and mitigate vulnerabilities, thereby strengthening their cybersecurity posture against risks associated with leaked PII.

