ShinyHunters Launches Data Leak Site: Trinity of Chaos Announces New Ransomware Victims
Cyber Threat Intelligence


The Trinity of Chaos, a ransomware collective presumably associated with Lapsus$, Scattered Spider, and ShinyHunters groups, launched a Data Leak Site (DLS) on the TOR network containing 39 companies impacted by the attacks. As detailed by Resecurity in our previous threat intelligence report, the group aims to continue its activities and has shifted toward a traditional ransomware modus operandi.
In fact, the group has not announced any new attacks but has released previously unavailable information about past successful attacks and shared samples of stolen data. Following previous Salesforce instances exploitation, the group released a message to the company threatening to release a massive number of records. The company downplayed these claims, stating that no new attacks or vulnerabilities had occurred. At the same time, it does not exclude the possibility that previous activity resulted in the compromise of customer instances at scale.
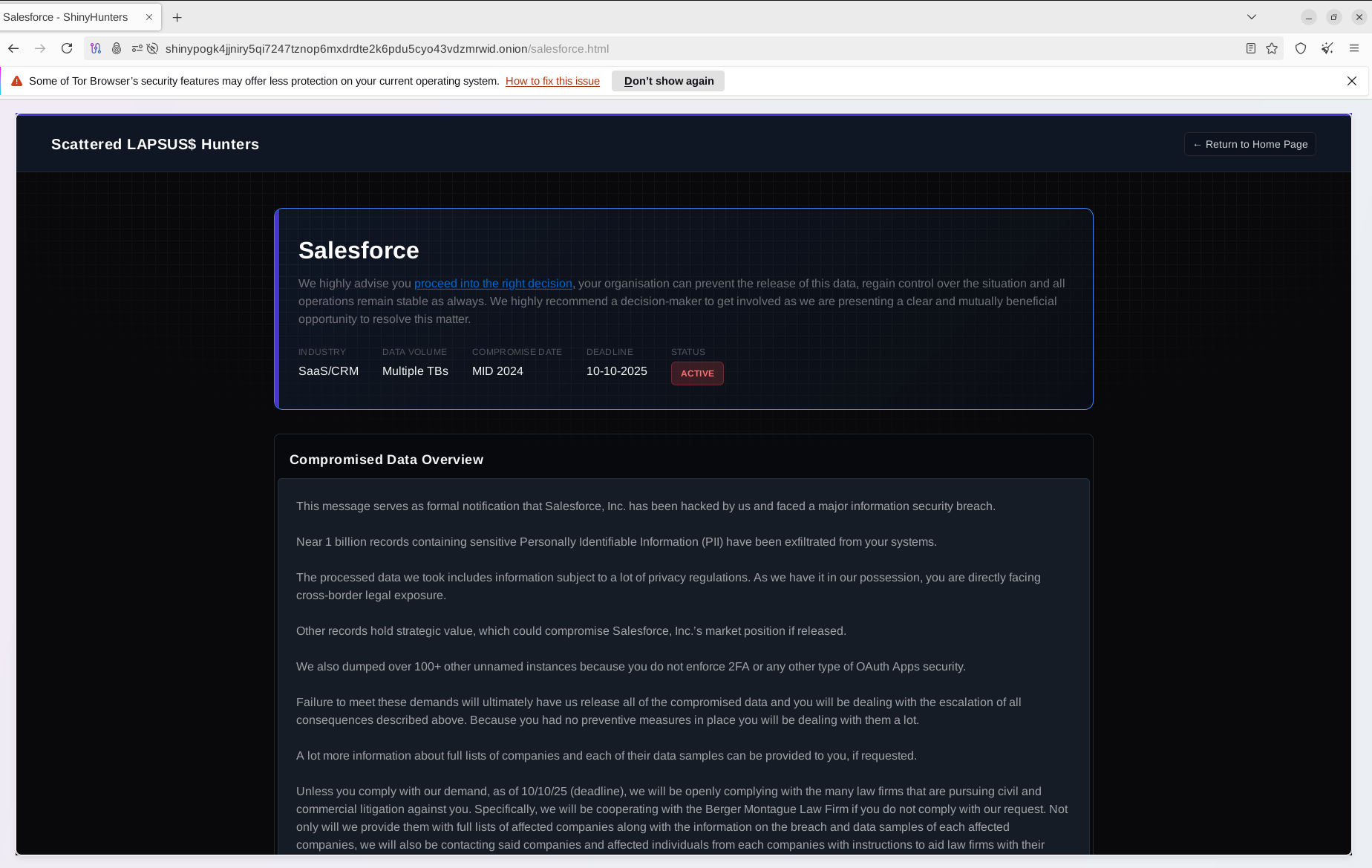
The threat actors stated they attempted to contact Salesforce earlier but were unable to negotiate terms to prevent disclosure. Similar to the tactics of other ransomware groups—for example, targeting EU-based victims to ensure compliance with GDPR—the group threatened to report evidence of the data breach to regulators, which could result in "criminal negligence charges" against the company.
In a polished marketing message, the "Scattered LAPSUS & Hunters" trio stated: "Specializing in high-value corporate data acquisition and strategic breach operations. Our expertise spans across automotive, financial, insurance, technological, telecommunications, ISPs, and numerous other sectors worldwide. We help you regain control." Interestingly, the group also mentioned that their operations began at least as early as 2019, which may indicate a high level of sophistication in their activities.
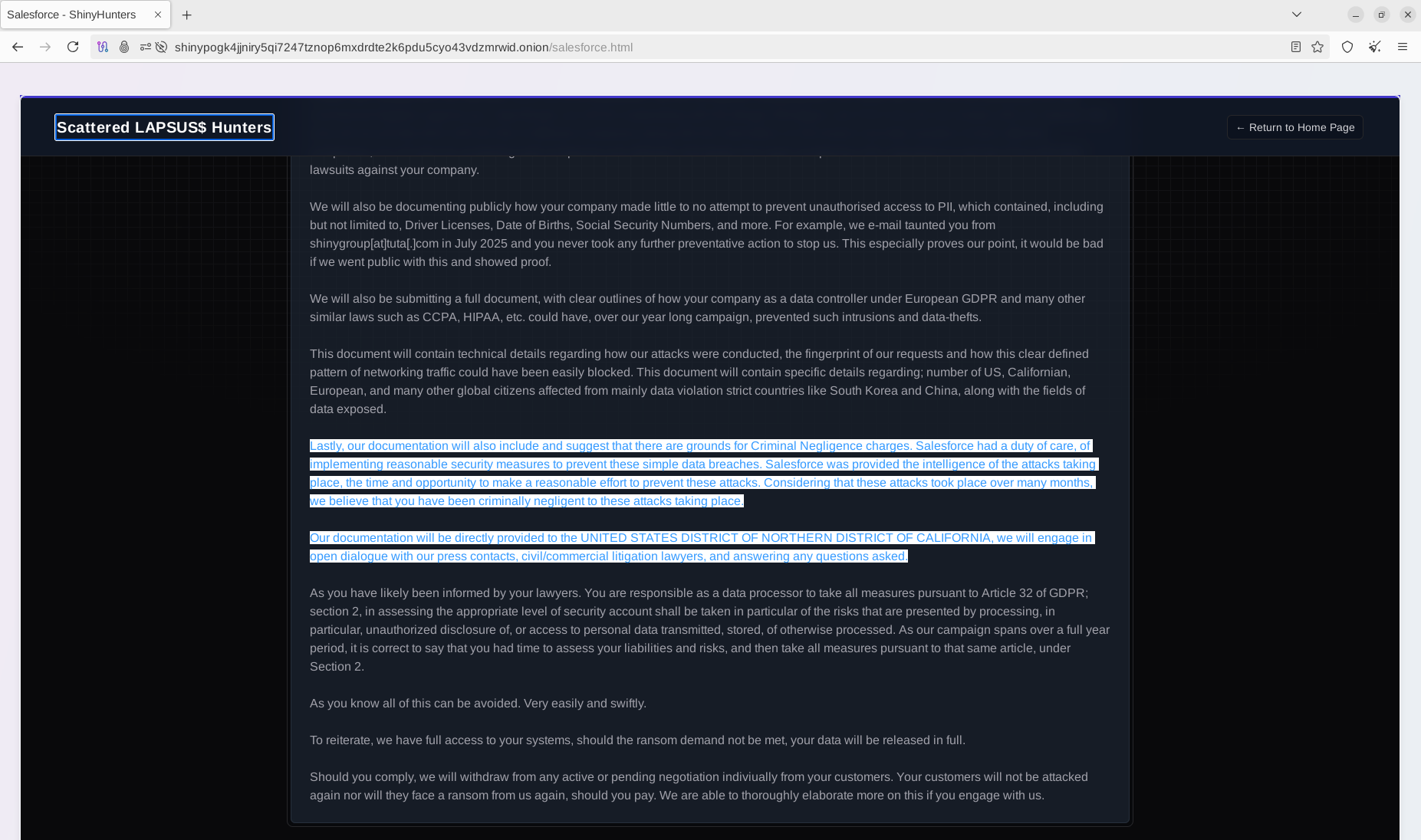
As the main point of contact, the actors provided their official email address, previously mentioned in several Dark Web communities and Telegram channels. Victims are advised to communicate using their official corporate (business) email addresses so that the trio can verify their identities and provide further instructions.
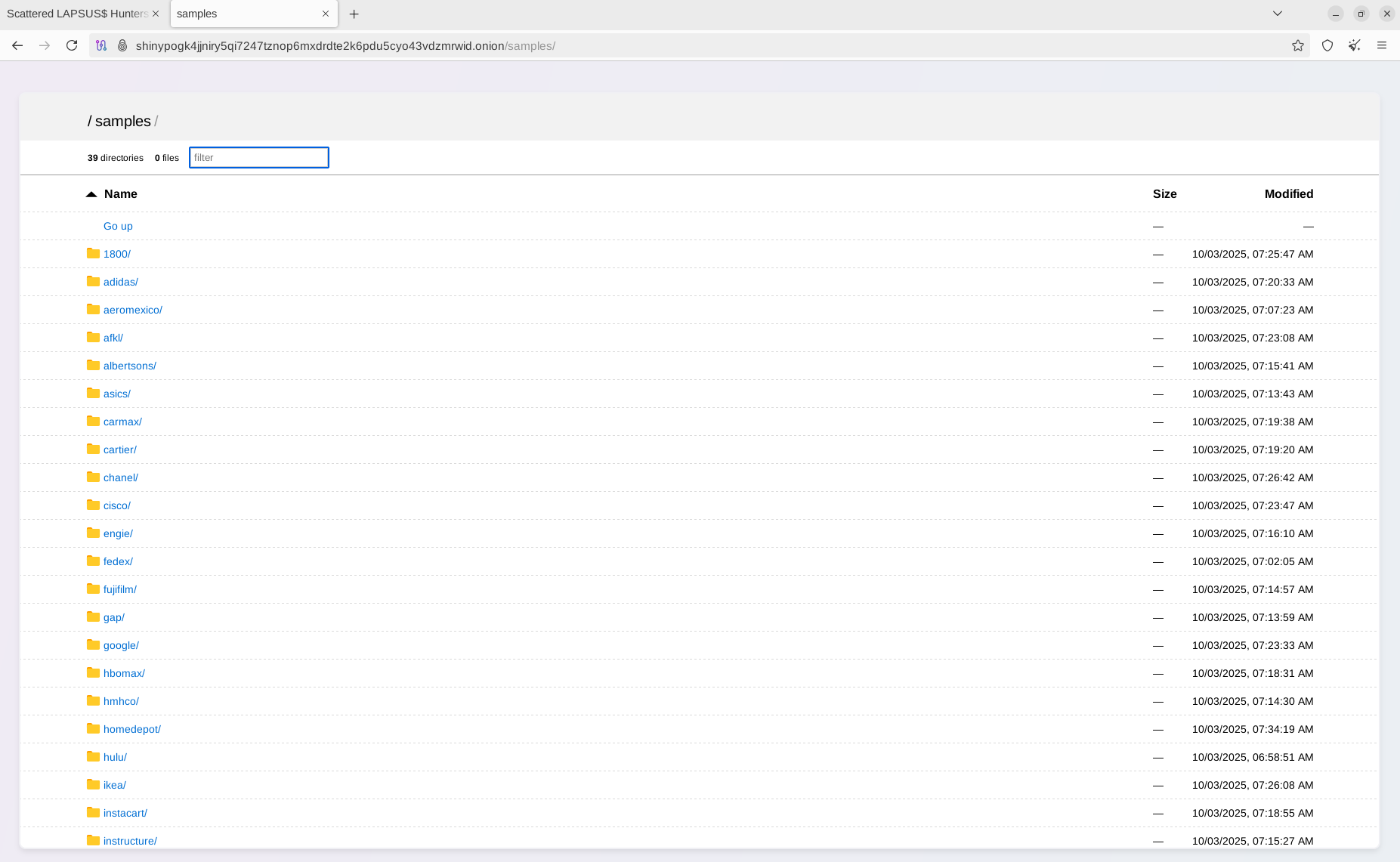
October 3, 2025, could be considered a bad day for many Fortune 100 companies, as some may face lawsuits from victims or at least inquiries into the root causes of the data leaks. Regardless of the most probable root cause - vulnerability in Salesloft’s Drift AI chat integration - the impacted customers may not distinguish this and could raise concerns about privacy violations within their jurisdictions. The following companies have been published on the Data Leak Site (DLS) today:
- Toyota Motor Corporation
- FedEx
- Disney/Hulu
- Republic Services
- UPS
- Aeromexico
- Home Depot
- Marriott
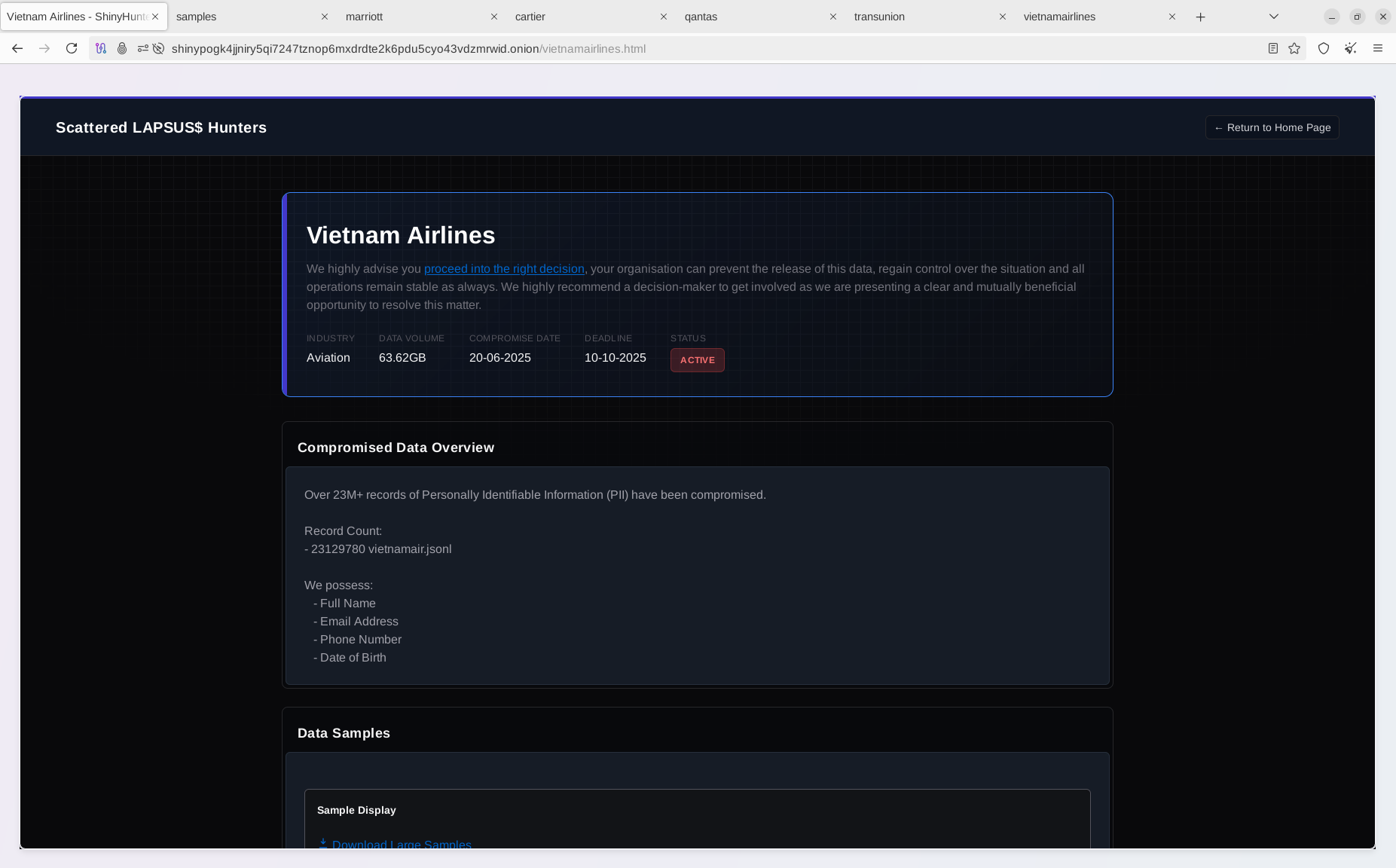
- Vietnam Airlines
- Walgreens
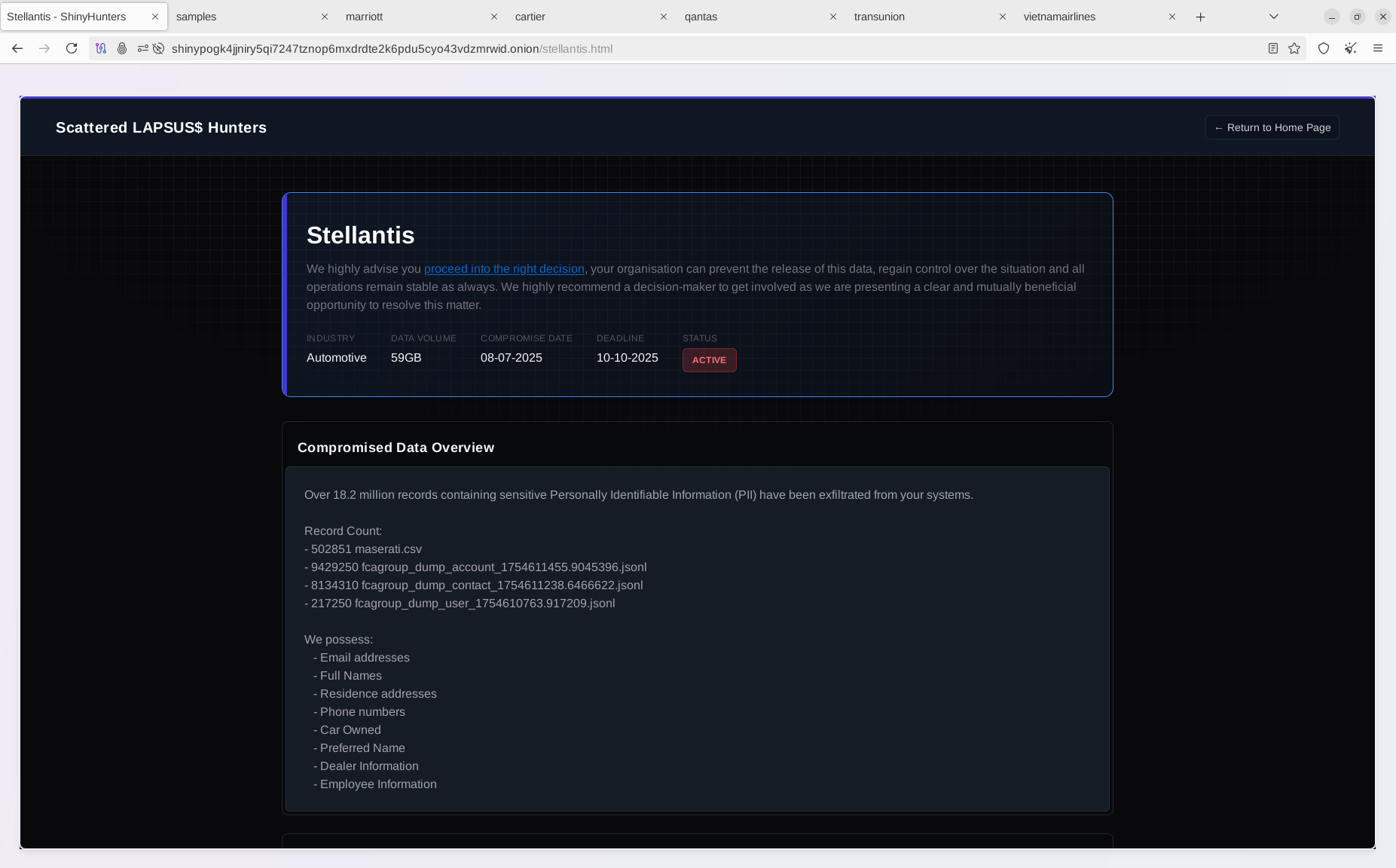
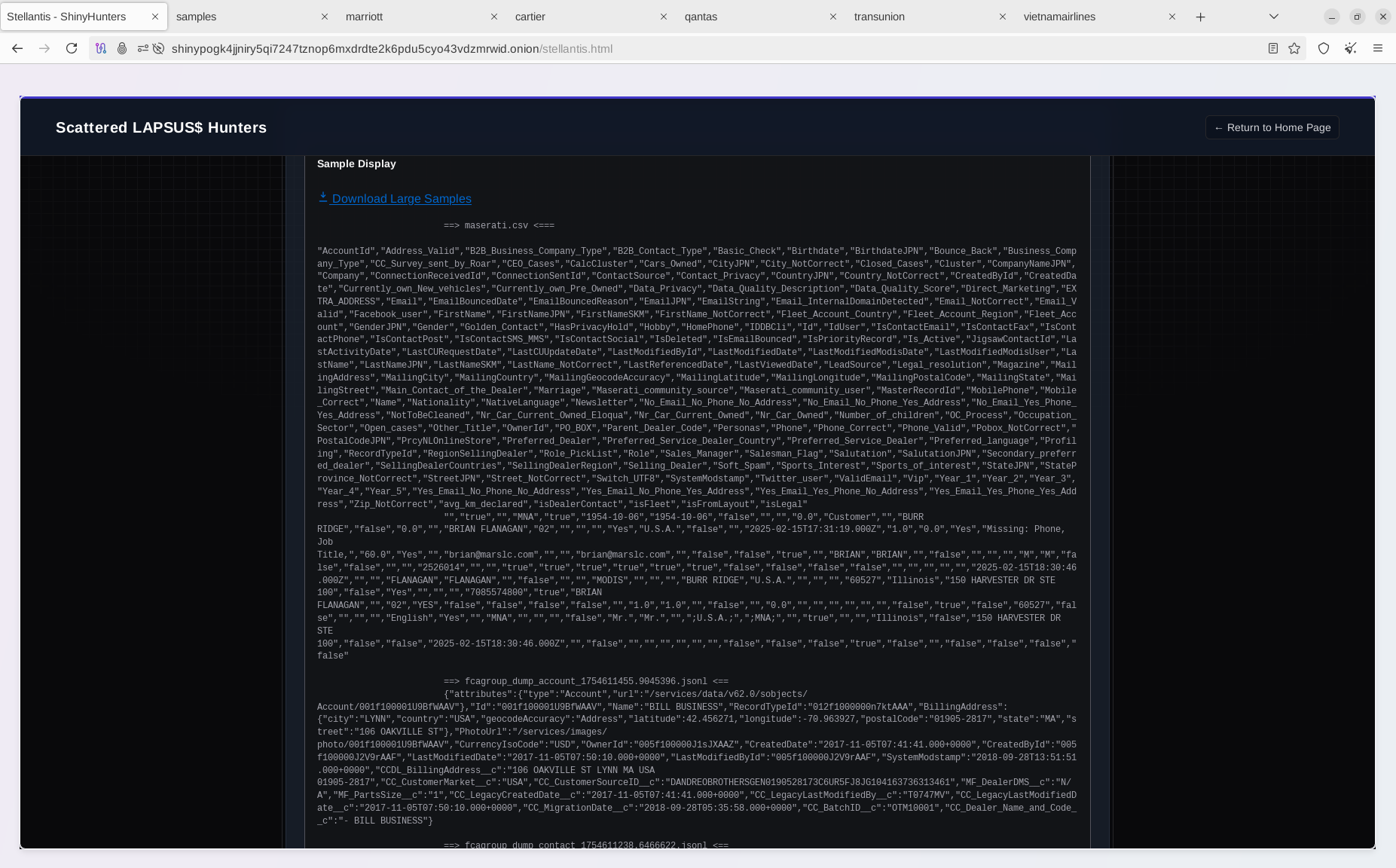
- Stellantis
- McDonald's
- KFC
- ASICS
- GAP
- HMH (HMHCO.COM)
- Fujifilm
- Instructure.com - Canvas
- Albertsons
- Engie Resources
- Instacart
- Petco
- Kering (Gucci, Balenciaga, Brioni, Alexander McQueen)
- Puma
- Cartier
- Adidas
- TripleA (aaa.com)
- Qantas Airways
- CarMax
- Saks Fifth Avenue
- 1-800 Accountant
- Air France & KLM
- Google Adsense
- CISCO
- Pandora.net
- TransUnion
- Chanel
- IKEA
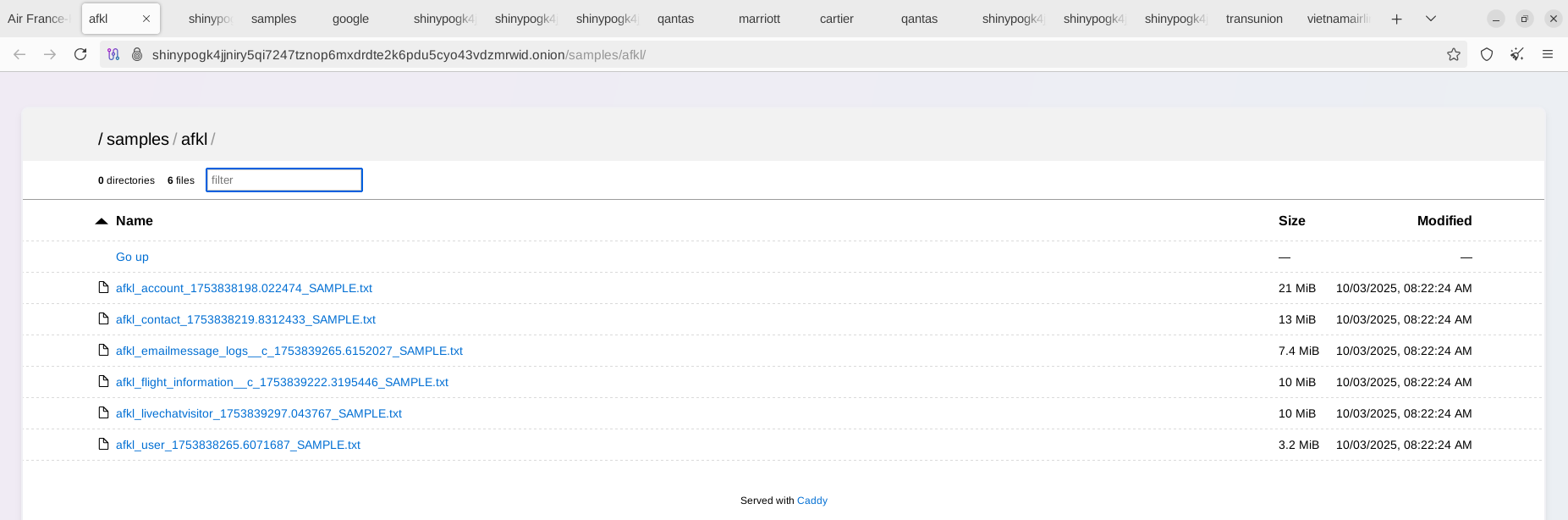
For most of these companies, October 10 has been set as the deadline to negotiate in order to prevent further data publication. The notable update in this activity is the release of samples of stolen data, which may shed light on the past incidents.
The listing on the Data Leak Site (DLS) includes references to the most recent victims, including Stellantis, the automotive giant that disclosed a data breach affecting its North American customers a few weeks ago (September 21, 2025). This incident followed an attack on the British luxury carmaker Jaguar Land Rover, which severely disrupted its retail and production activities.
Notably, the majority of leaked data samples lack passwords but contain substantial amounts of PII data, which may confirm that the stolen records likely originate from the impacted Salesforce instances through vishing attacks and stolen OAuth tokens used for Salesloft’s Drift AI chat integration. This has prompted a recent flash warning issued by the FBI, outlining technical indicators that organizations should monitor to determine if attackers have infiltrated their Salesforce environments.
The actors also disclosed some of their past notable attacks, along with new data samples. For example, the attack against Vietnam Airlines was disclosed around November 7, 2023. At that time, an investigation confirmed that the attackers had been "lurking" within Vietnam Airlines' infrastructure for nearly three years. During this period, the group, operating under the alias "1973cn," which has not been publicly detailed, may also have been responsible for attacks at Noi Bai Airport and Tan Son Nhat Airport.
It is not yet clear whether the groups or their members are connected, but in the case of "Scattered LAPSUS$ Hunters," definitive evidence of stolen data has been shared. Interestingly, prior to this announcement, the group claimed to have exfiltrated over 160 million records from the National Credit Information Center (CIC) of Vietnam. Resecurity has provided additional details about that incident in a separate threat intelligence report.
Cybercriminals have shared evidence of successful data breaches involving airlines, including Air France and KLM. The leak of PII data in these incidents could be particularly damaging, especially within the European Union, where data protection regulations such as GDPR impose strict penalties for breaches involving personal information.
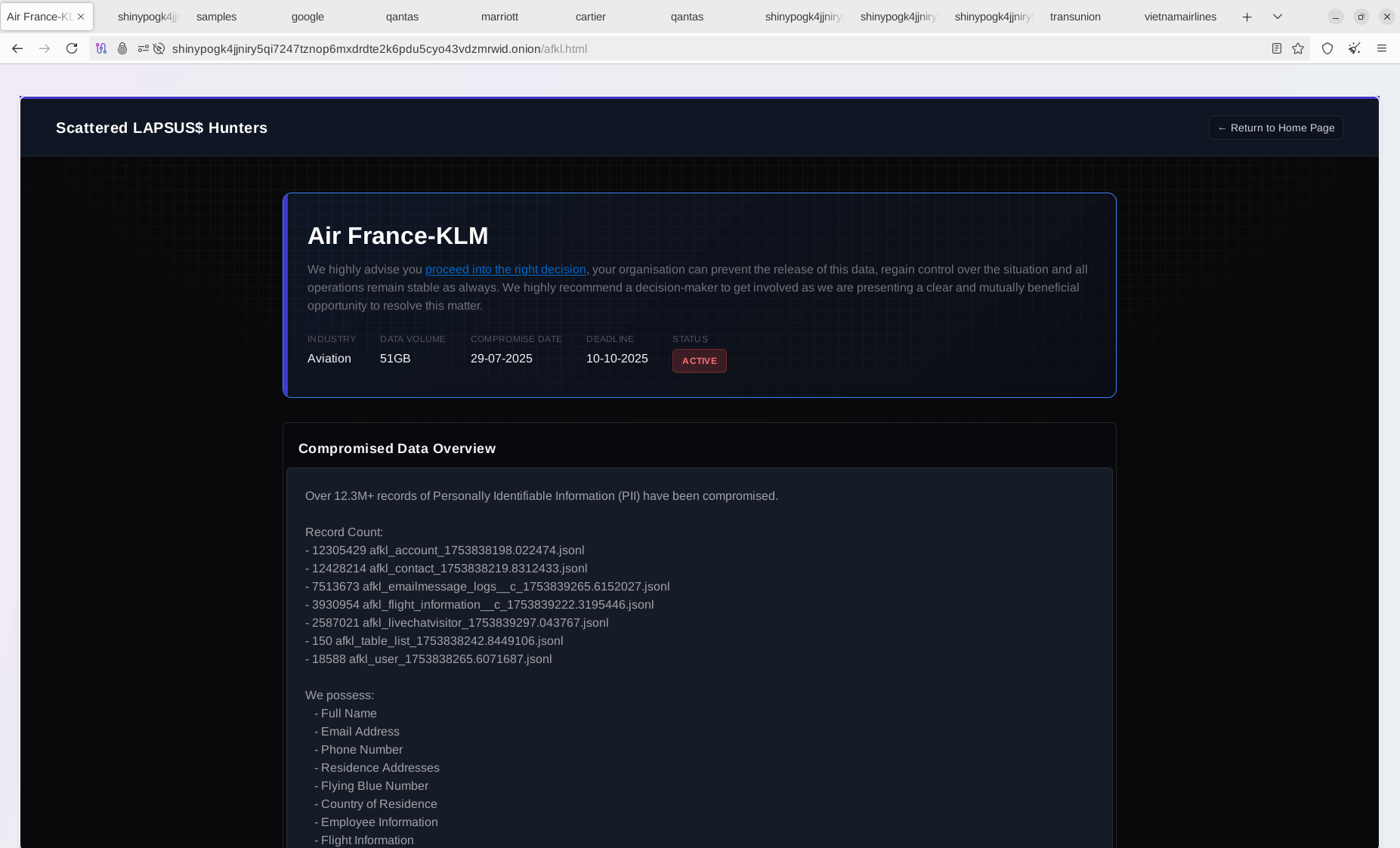
The stolen records have been validated by Resecurity; they contain sensitive passenger information, internal communications, references to loyalty points, and records of activity history.
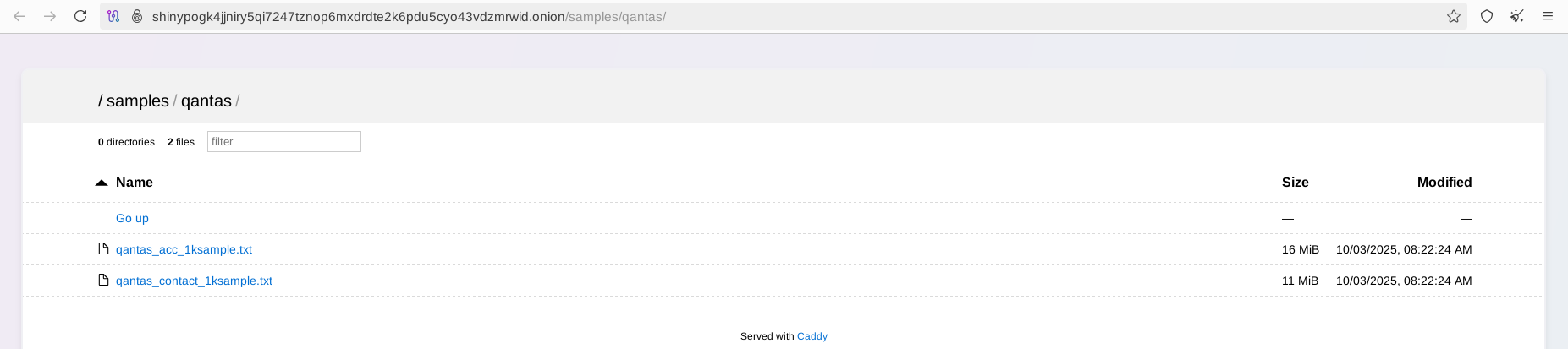
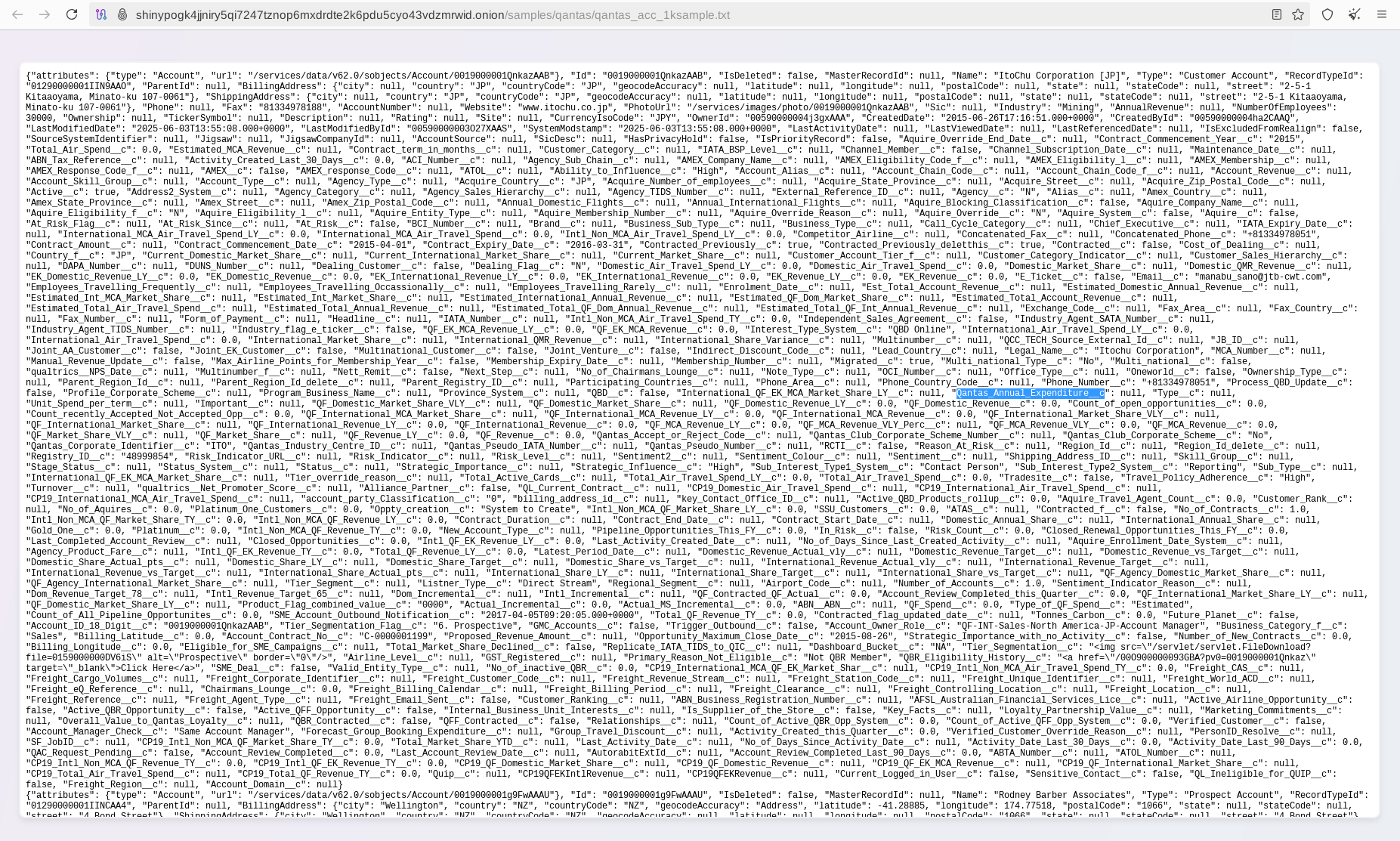
It is notable that the group was targeting major airlines worldwide and was successful in compromising some of the biggest brands. One of the first airlines attacked by the trio was Qantas (Australia), to which the actors also shared a substantial number of records as proof:
Resecurity observed similar data records when the airline was first extorted and received a warning via email. Subsequently, the company's management was fined for negligence in protecting customer data, but this did not resolve the issue of the stolen data, as cybercriminals continue to leverage and monetize it on the Dark Web.
This is also the first time the Trio has attributed their activity to the attack against Aeroméxico, one of the top airlines in Latin America.
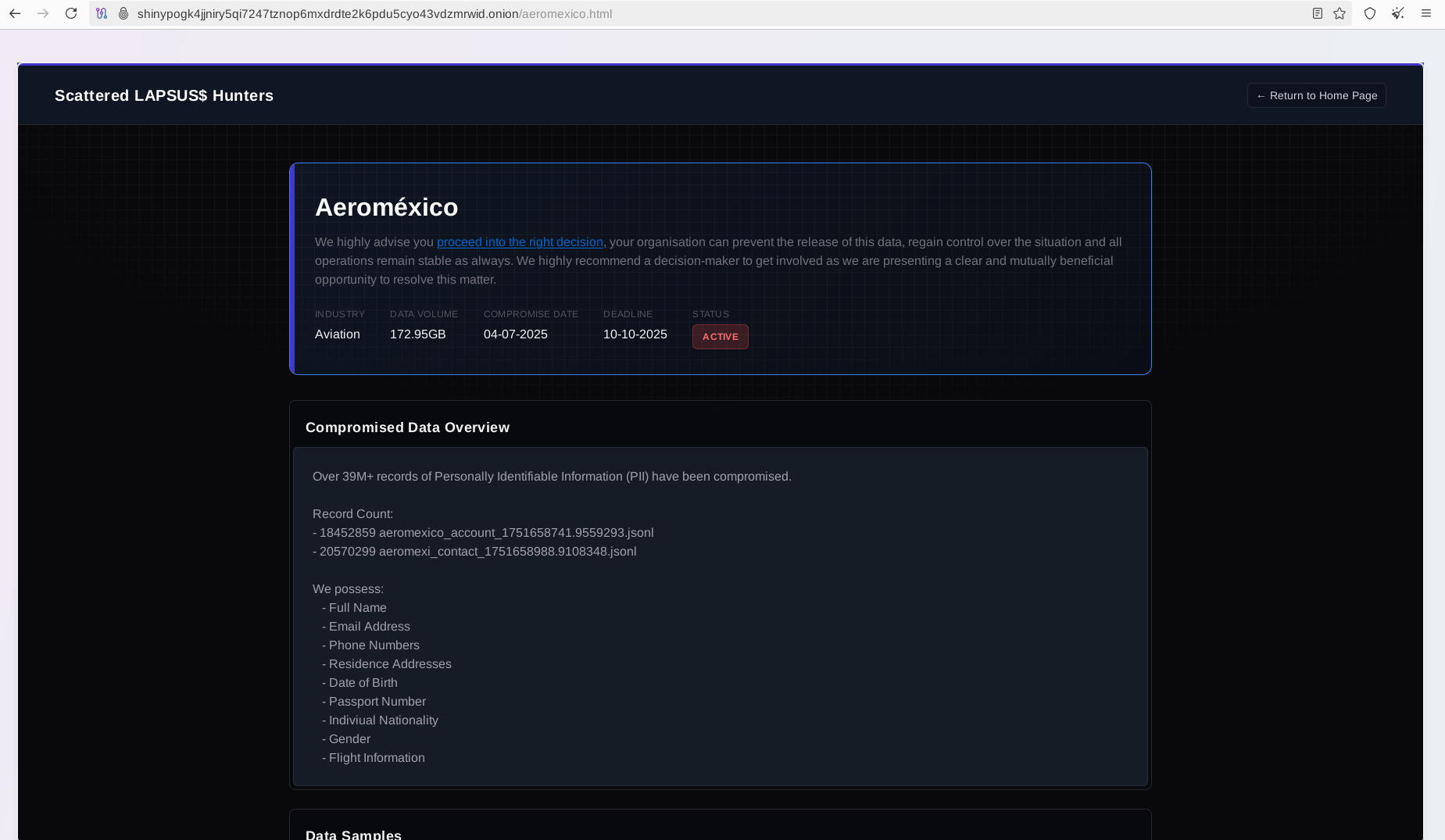
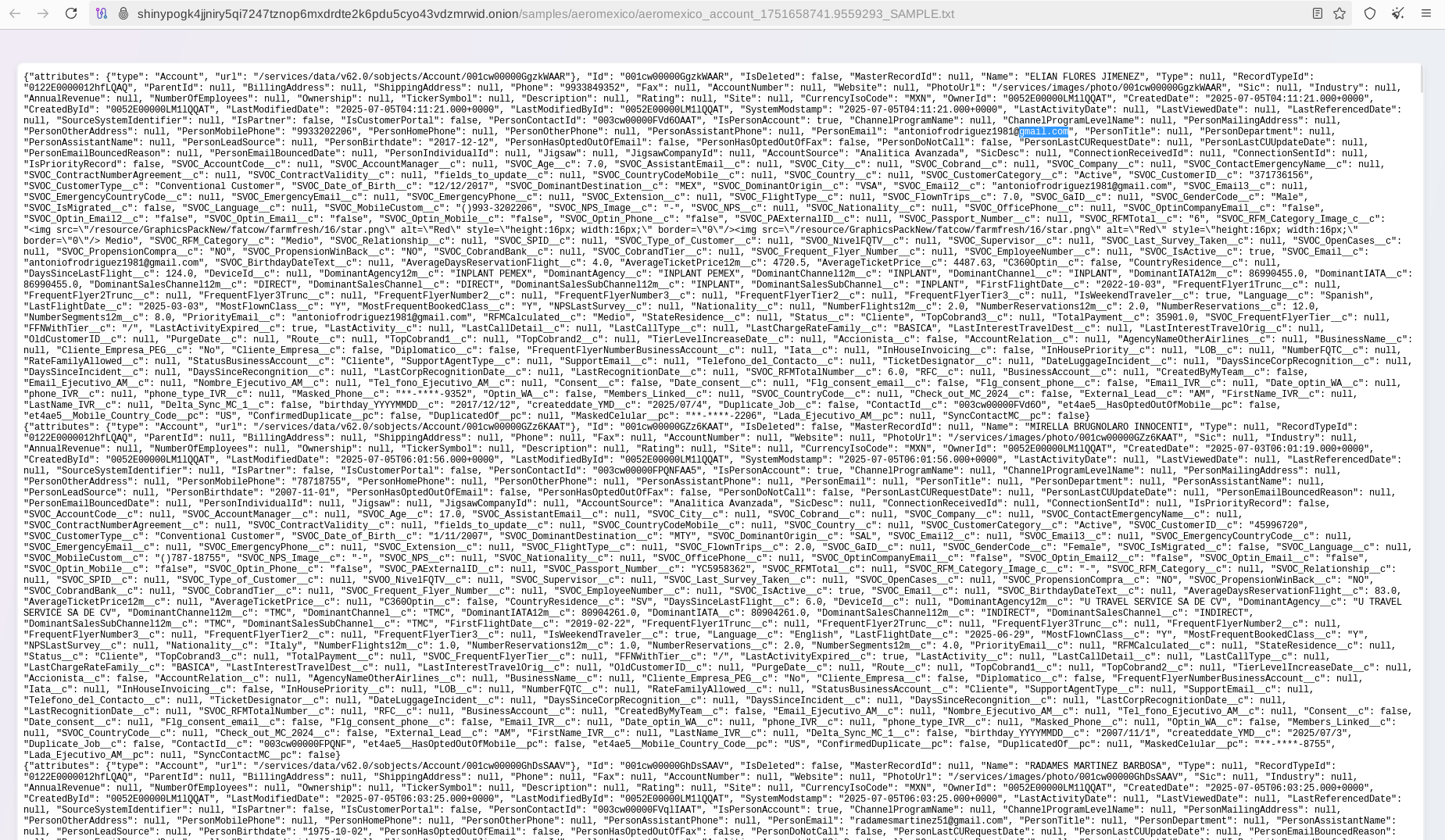
The breach, dated July 4, 2025, was likely related to Salesforce exploitation based on the observed records. The actors claim to have exfiltrated over 39 million records containing PII and have shared a substantial sample:
What is truly new is the publication of data related to technology giants like Cisco and Google. Although the full scope of the breach remains unclear, the actors have shared multiple records referencing potentially impacted customers. Notably, they have indicated possible breach dates of June 30, 2025, and July 23, 2025. It is unlikely that the entire organizations are affected; rather, the breach probably involves a specific service or customer-specific platform, such as Salesforce, similar to other incidents carried out by the same threat actors.
On June 4, 2025, Google disclosed that one of their corporate Salesforce instances had been impacted by activity attributed to UNC6040. Google responded to the incident, conducted an impact analysis, and initiated mitigation measures. At that time, the company did not specify which exact product or service might be affected. However, based on the most recent publication on DLS by the actors, the issue could be related to Google AdWords and its end users.
In the observed data sets, the group has leaked information pertaining to multiple potential customers, as well as various records related to Google AdWords, digital media planners, and advertising partners from different regions around the world.
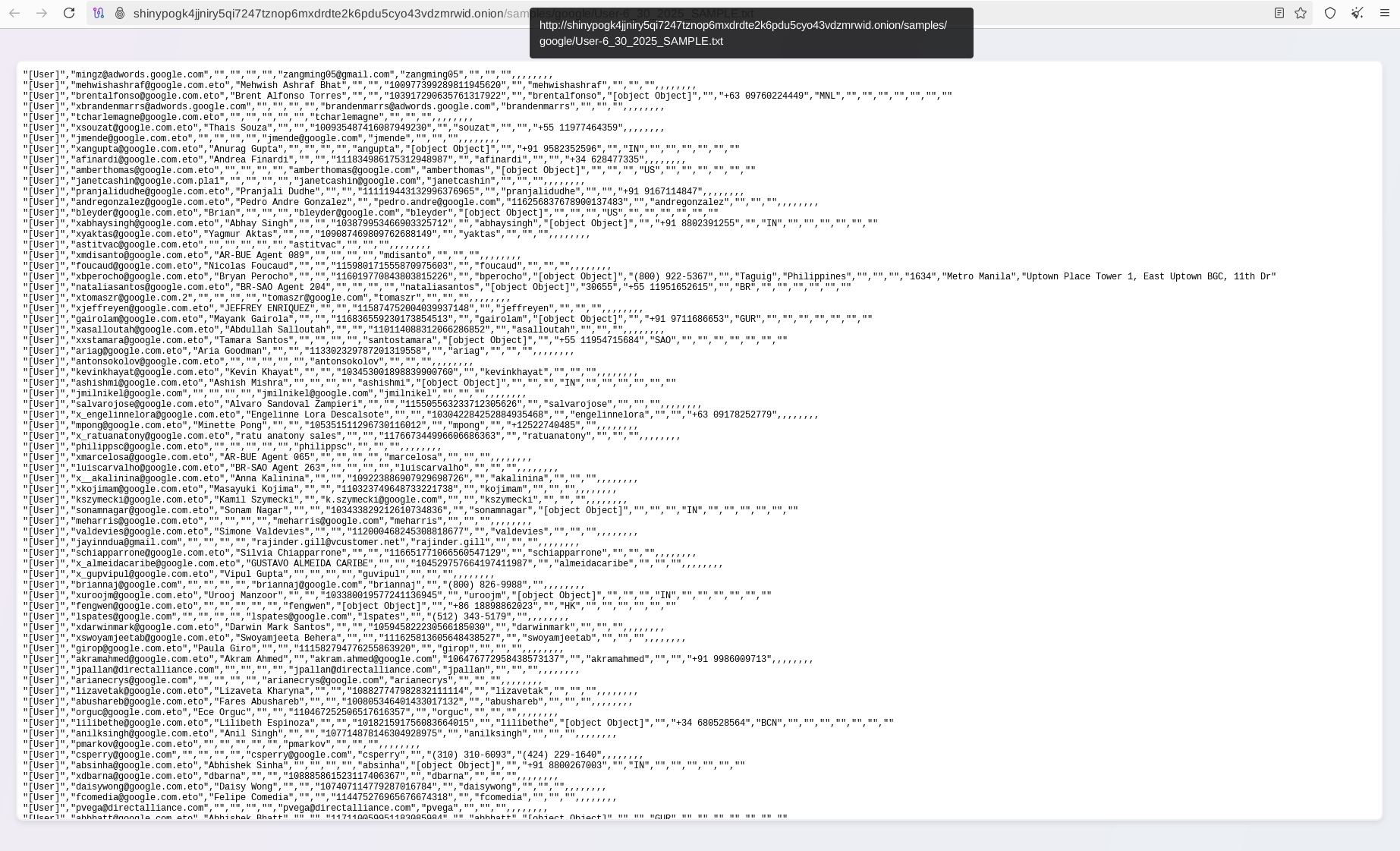
Resecurity has identified a large number of digital media partners and third-party advertising agencies within the data set, which may confirm a possible connection to Google AdWords, a widely used platform for organizing digital marketing campaigns.
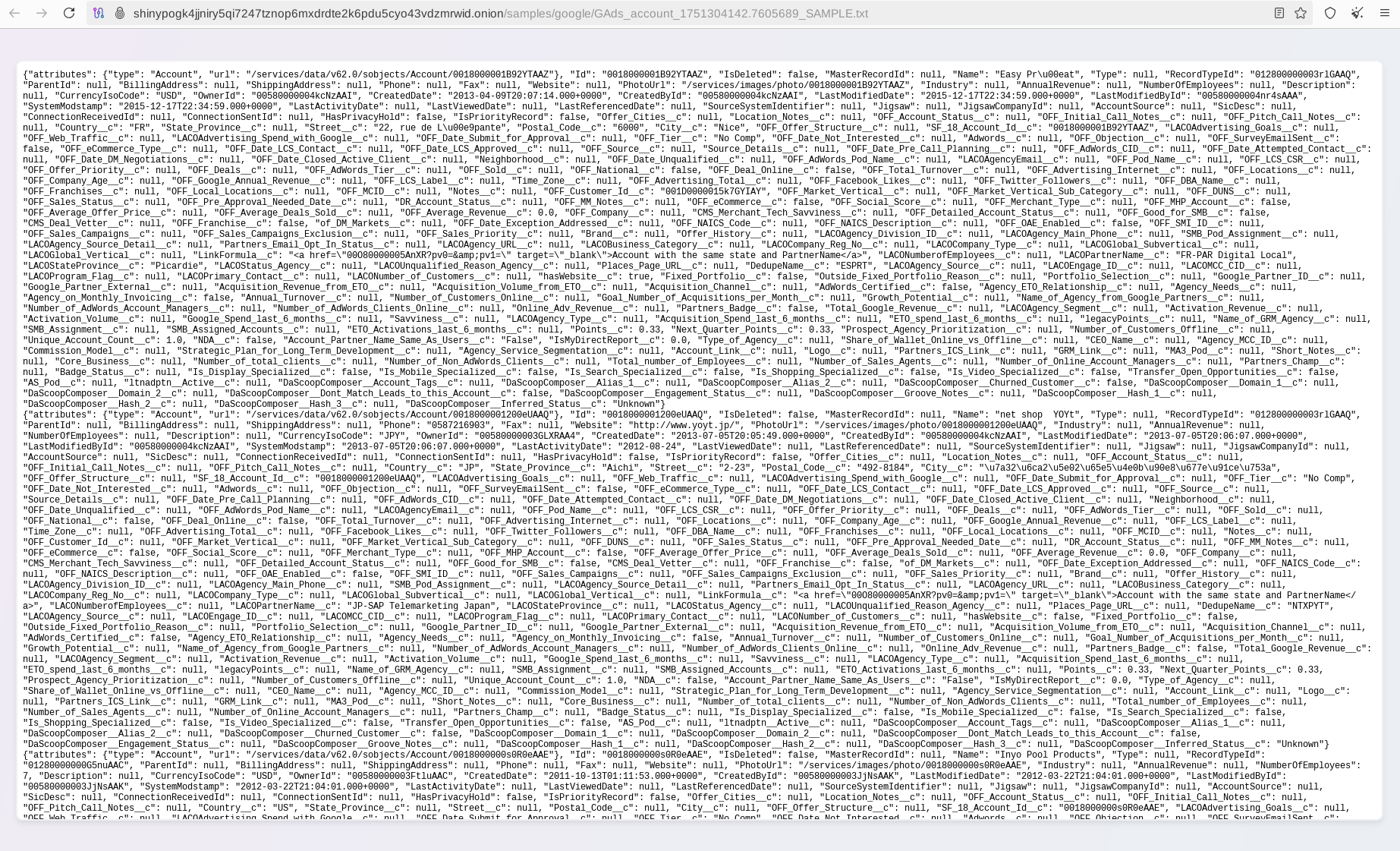
In the case of Cisco, the situation appears to be more straightforward, as the stolen records clearly originate from Salesforce and contain references to their customers as well as employees.
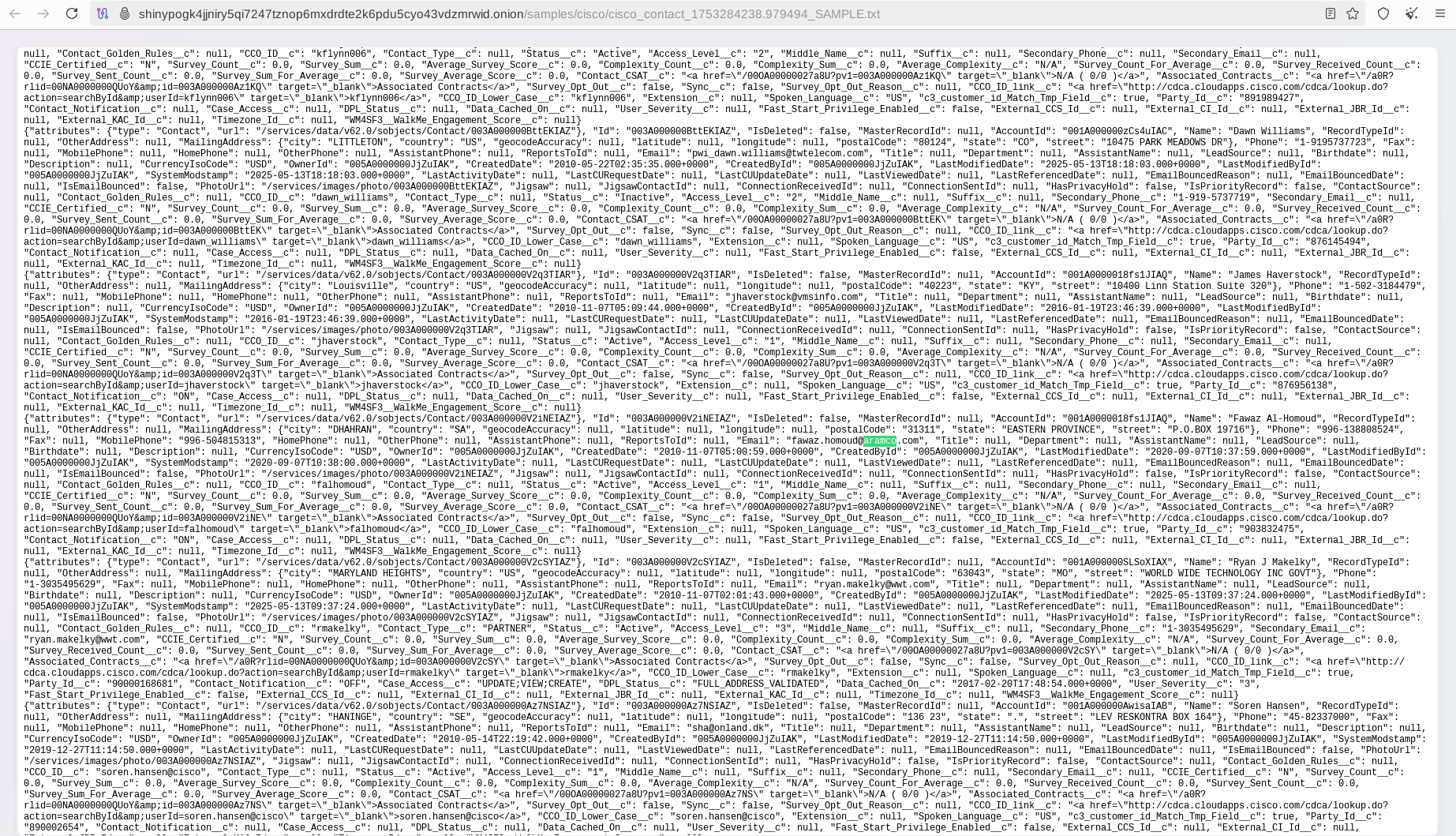
Such information may be valuable to other malicious actors planning new attacks, as insights into customer-vendor relationships can be effectively leveraged for social engineering and advanced phishing campaigns.

The data set also contains multiple records related to employees of law enforcement, military and federal agencies, likely involved in the procurement or configuration of Cisco products, including personnel from the FBI, DHS, DISA, IRS, NASA. In addition to the U.S.-based agencies, the data set includes records related to the Ministry of Defense of Australia, multiple government agencies in India, and other foreign public sector organizations. Interestingly, the launch of the Data Leak Site (DLS) overlaps with the period of the U.S. government shutdown, which affected federal agencies, including law enforcement. Industry experts have expressed concerns that this timing may impact their ability to work effectively and respond to national security threats including cybercrime-related.
After multiple bans, the group also re-launched a Telegram channel, calling it "SLSH 6.0 Part 3." The group claims to have updated the Data Leak Site (DLS) after October 10 in the event of non-payment. According to them, the new DLS will feature over 1.5 billion records, with the following statistics:
- "total_records": 1,563,633,235
- "company": 760
- "object_counts":
- "Account": 254,127,054
- "Contact": 579,042,146
- "Opportunity": 171,625,743
- "User": 59,900,417
- "Case": 458,044,533
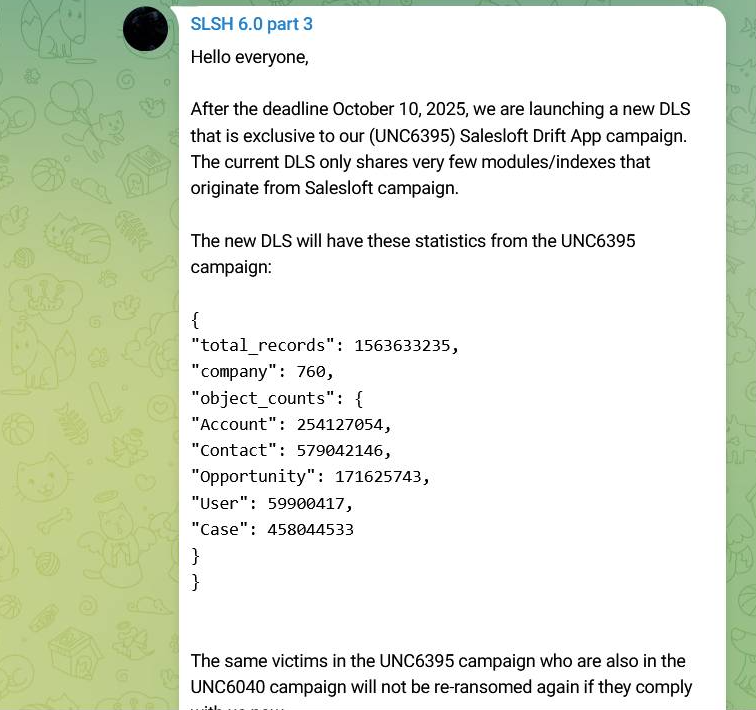
The notorious ransomware collective indicated that the victims originate from previous campaigns, including UNC6395 (related to Salesforce / Salesloft Drift App exploitation) and UNC6040. They also promised not to "re-ransom" the victims if there is cooperation.
What is expected if the stolen data is leaked? Cybercriminals may exploit it for malicious purposes on a large scale, including in harmful artificial intelligence (AI) applications. By having context about the affected victims and their industries, threat actors could perform data mining to extract valuable insights and correlate victim data sets with other available information. This could lead to sophisticated social engineering schemes, advanced phishing campaigns, and identity theft, especially targeting large enterprises and government sectors.
Resecurity's HUNTER team has also observed a possible DDoS attack against the new Data Leak Site (DLS), which may indicate that the impacted parties are attempting to prevent the publication of leaked data.

