

Introduction
ShinyHunters claimed to have exfiltrated over 160 million records from the National Credit Information Center (CIC) databases. This is a staggering number, given Vietnam’s population is under 102 million, indicating the dataset includes historical and possibly multiple records per individual. The CIC’s role as a centralized repository for Vietnam’s credit data made it a particularly attractive target, as breaching it exposed a single point of failure affecting nearly the entire population.
"Initial investigation indicated signs of unauthorised access aimed at stealing personal data, with the extent of the breach still being assessed," Vietnam's cybersecurity agency said in a statement late on Thursday.
The CIC is a government-owned, centralized credit information repository that plays a critical role in the financial system in Vietnam. It collects, maintains, and disseminates credit-related data from banks, financial institutions, insurance companies, and other lenders. The data includes loan amounts, repayment histories, and personal identification information. This information is essential for credit risk assessment, lending decisions, financial inclusion, and systemic risk management in the country.
ShinyHunters is one of the most prolific and notorious cybercriminal groups of the past five years, responsible for a series of high-profile data breaches that have impacted hundreds of millions of users and some of the world’s largest organizations—including the compromise of Microsoft’s GitHub account, AT&T, Ticketmaster, Santander, MathWay, Tokopedia, Wishbone, Wattpad, Pluto TV, Bonobos, Aditya Birla Fashion and Retail, Mashable, and the Legal Aid Agency (U.K. Ministry of Justice). Their operations have evolved from large-scale database thefts to sophisticated social engineering and cloud platform attacks.
It is also important to mention that the group has undergone certain transformations and is now operating under the umbrella of the "ShinyHunters-Lapsus-ScatteredSpider" conglomerate, uniting some of the best hacktivists of our time. The malicious cyber activity by these actors is often connected to Scattered Spider (also known as UNC3944, Octo Tempest, Storm-0875, LUCR-3), UNC6040, and UNC6395. In an interview arranged by DataBreaches.net, the actors stated, “It wasn’t a Scattered Spider type of hack … so ShinyHunters.” At the same time, it is also possible that other actors could reuse their aliases to capitalize on the "brand" they have built as a result of past successful attacks. Their Telegram channel is managed by multiple actors using references to the names of those groups.
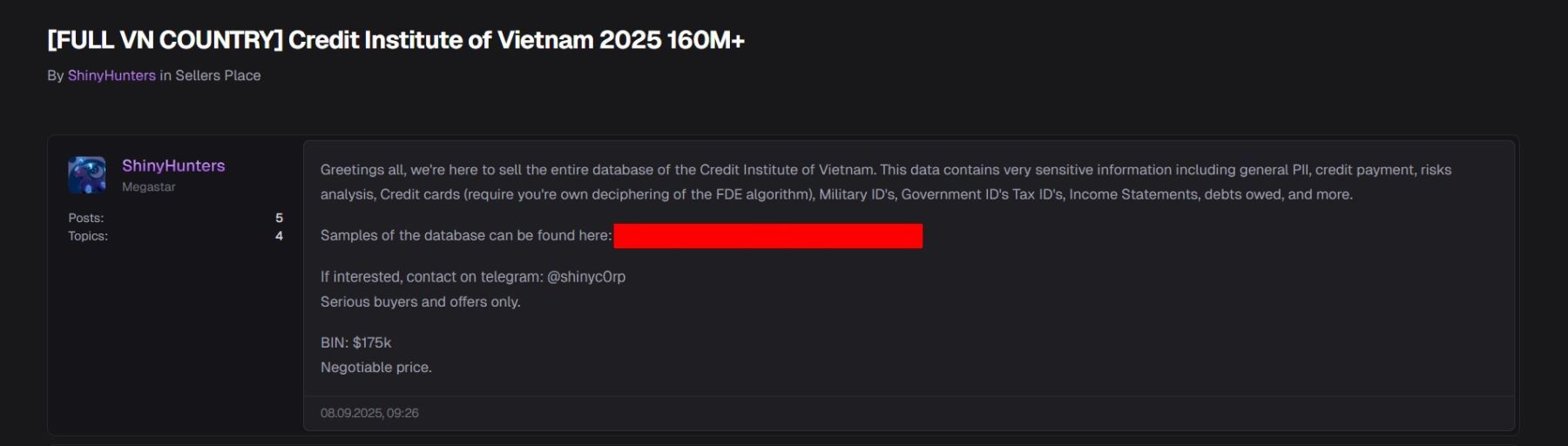
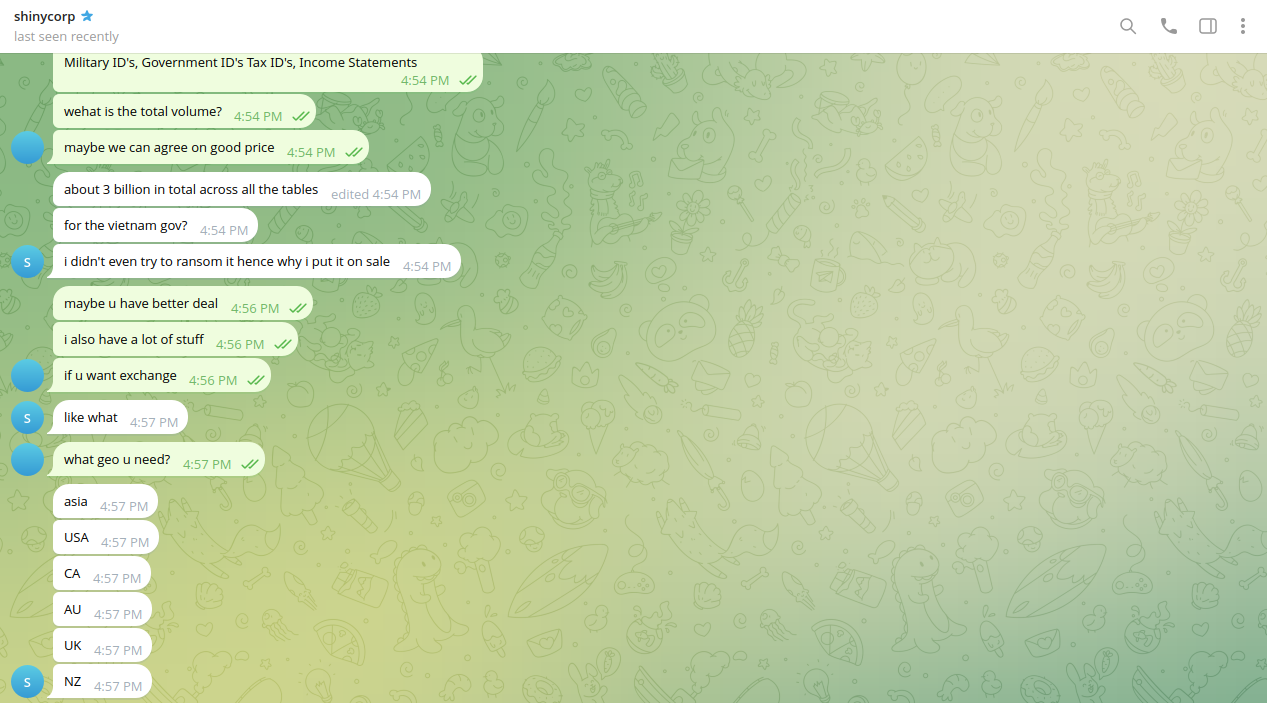
Resecurity has contacted ShinyHunters to learn more about the data for sale. According to the actors, they didn't try to extort the Vietnamese government, as it was unlikely they would expect to get paid. This is why they decided to monetize the stolen data on the Dark Web. Interestingly, in communications with our investigator, the actors outlined the possibility of exchanging data on other datasets, which could be of interest to the group. As a priority in terms of geographies, they mentioned the US, Canada, Australia, the UK, New Zealand, and Asia. ShinyHunters also shared that the total volume of records related to CIC may be over 3 billion.
It is the first time that ShinyHunters are targeting Vietnam. The group has a credible track record of leaks but has never previously attacked any organizations in Asia. Some of their attacks are done "for fun and profit," which is why the attack against Vietnam could be opportunistic and driven by interests in gaining access to Big Data stored in organizations like CIC.
Data Breach Scope
Data Types Exposed: According to descriptions shared by threat actors, the stolen data reportedly includes:
- Personally identifiable information (PII)
- Credit payment histories
- Risk analysis data
- Credit card information (some encrypted)
- Military, government, and tax IDs
- Income statements, debts, contact and employment information, and banking details
Resecurity was able to acquire samples of stolen data. Notably, multiple records include references to the leading financial institutions in Vietnam including but not limited to VietCredit, MB Bank, Ocean Bank, VPBank, Sacombank (Saigon Thuong Tin Commercial Joint Stock Bank), Agribank (Vietnam Bank for Agriculture and Rural Development). Our team was able to identify several victims and contact them for interviews. None of them received any notifications that their data had been breached in any fashion or form—raising some questions about the identity protection measures in place at the country level.
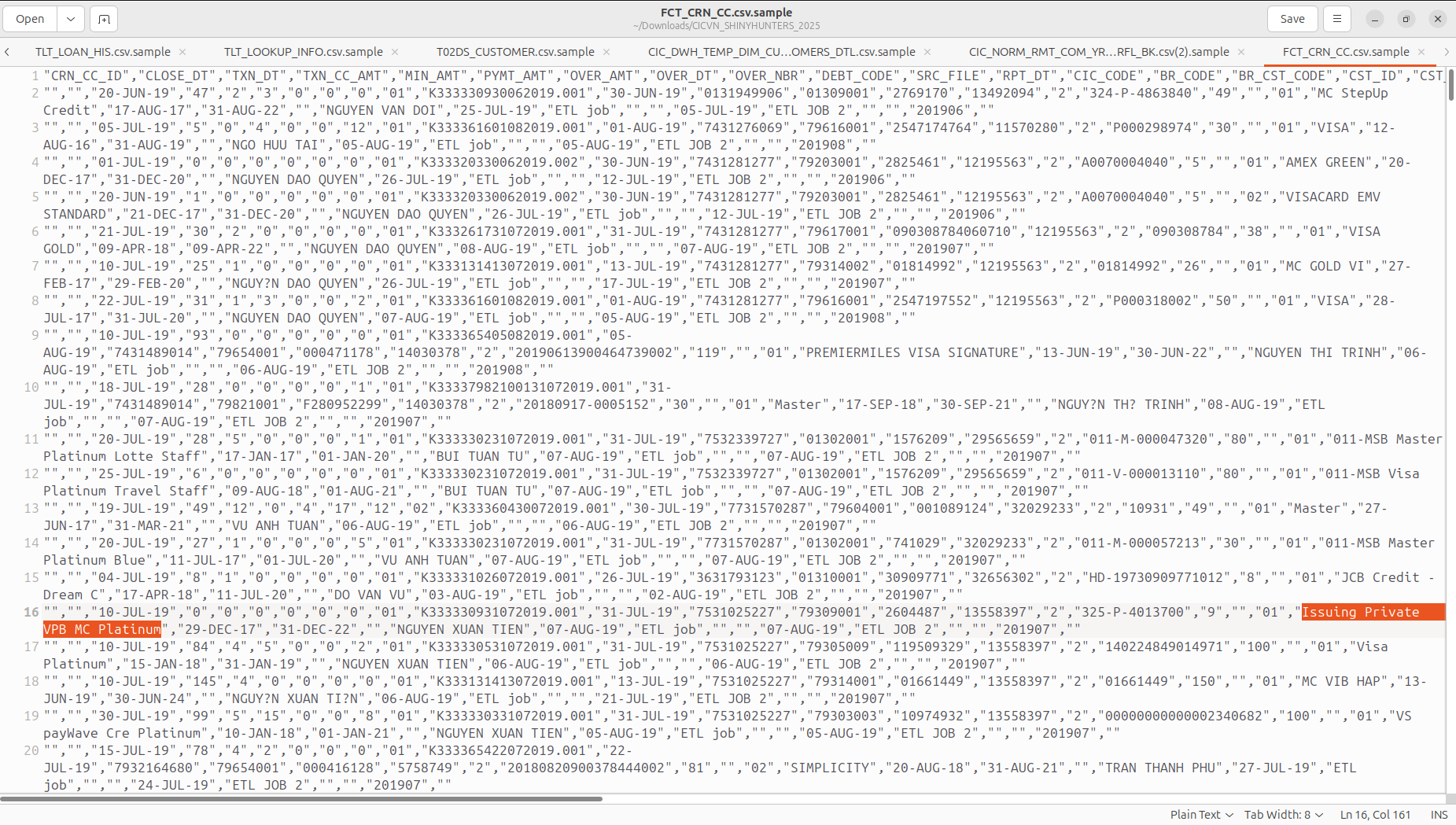
The data include historical records, which may give potential perpetrators substantial context about the victims.
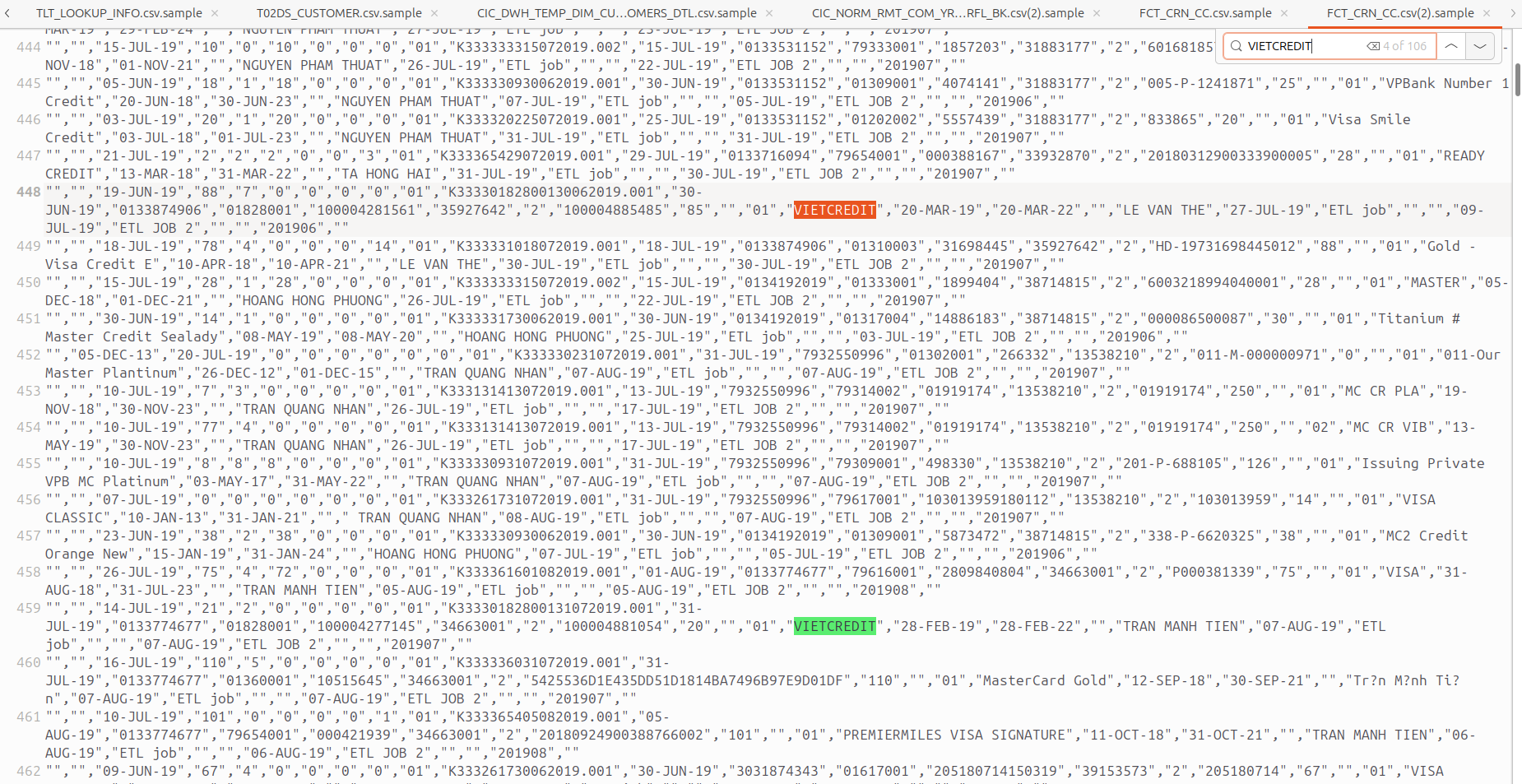
The data also references Citibank, the first U.S. financial institution licensed for branch opening and full branch establishment in Vietnam. No foreign banks or PII of individuals from countries other than Vietnam were identified in the acquired data set, as CIC is a local credit institution.
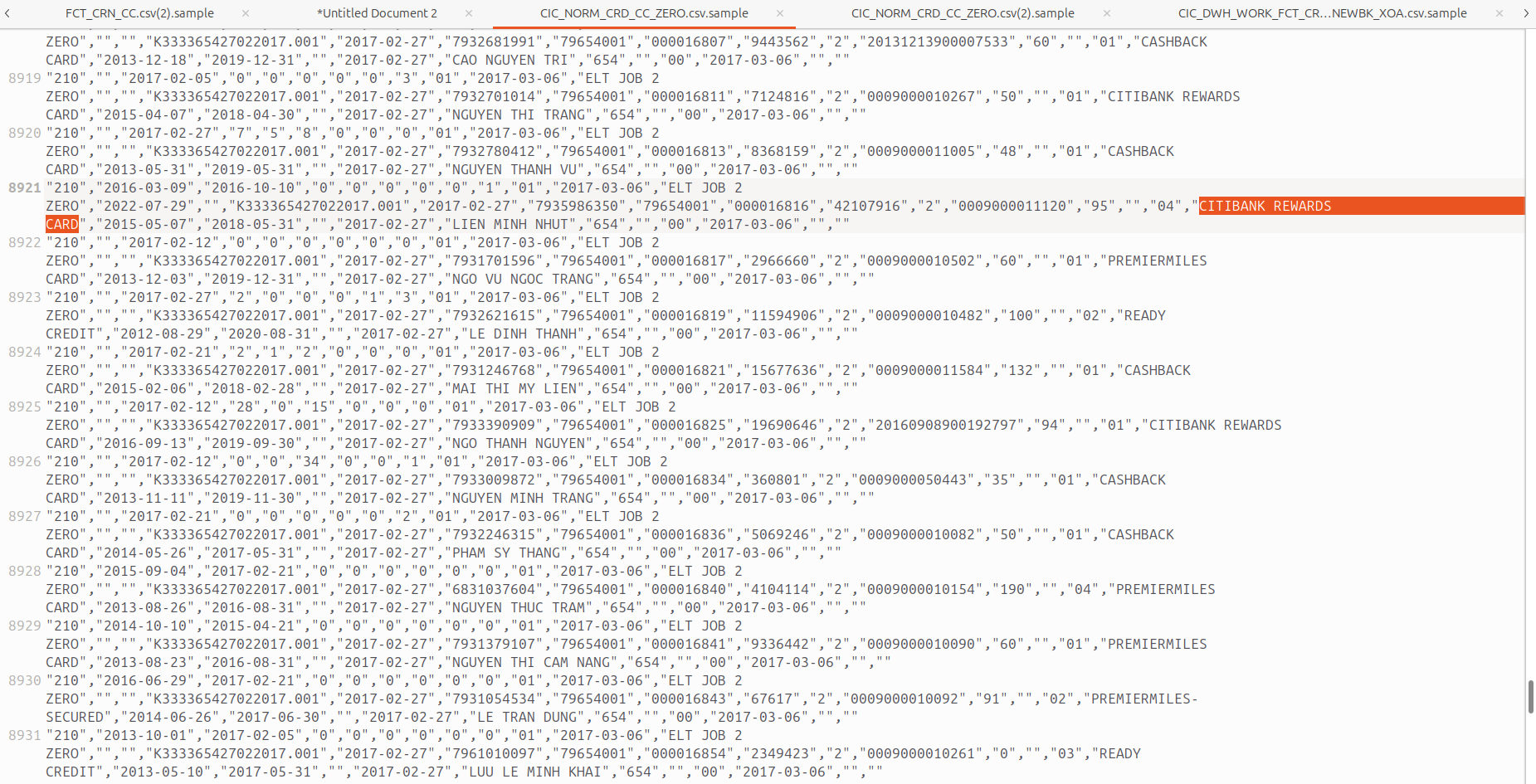
Besides historical data, several records with timestamps from 2025 were found. Among the most recent are several records dated February 2025. It is possible that there are records with even newer timestamps, but this can only be confirmed through independent verification and investigation with the affected party, which seems to be not very transparent about the incident.
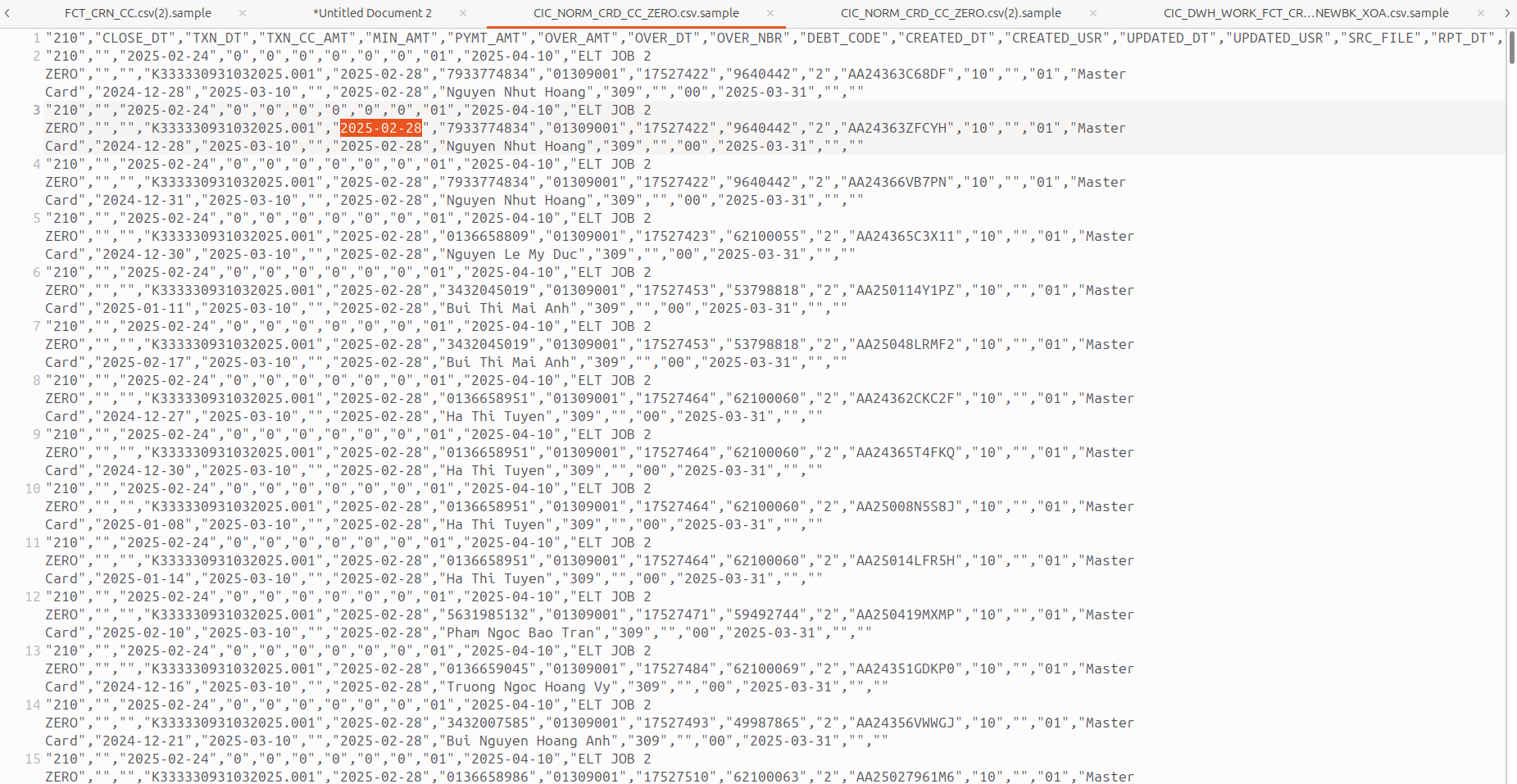
According to local experts in Vietnam, organizations like CIC do not store actual credit card (CC) data in plaintext. At the same time, numerous records containing detailed PII have been identified - including names, emails, phones, identifiers, references to financial institutions, records describing balances and their latest updates, and credit information. Resecurity has reached out to over 100 victims randomly selected from the acquired data set for comments via email - while the data was confirmed to be authentic, its source remains unclear.
Cybercriminals seek such data to orchestrate fraudulent activities via phishing, social engineering, and identity theft scenarios, impersonating individuals and businesses. However, nation-state actors and foreign intelligence services also use this data for espionage and gathering intelligence about targets of interest. One potential buyer of such data from ShinyHunters could be a nation-state, possessing the budget and capability to leverage this information at scale to target an entire country.
Resecurity has analyzed the possible structure of tables related to the exfiltrated database. It contains prefixes such as "CIC," which are likely pointing to the source of the compromise.
CIC_DWH_DIM_KHPN_DB.csv
CIC_DWH_FCT_CICB_QLNX_SLKH_MONTH_BAD.csv
CIC_DWH_FCT_CICB_TEMP_CRD.csv
CIC_DWH_FCT_TTP_LN_DEBT_TOP_PPS_TMP.csv
CIC_DWH_TEMP_DIM_CUSTOMERS_DTL.csv
CIC_DWH_WORK_DWH_CRD_TXN_CREDITCARD_MAX.csv
CIC_DWH_WORK_FCT_CRN_CC_NEWBK_XOA.csv
CIC_NORM_CIF_COMPANY_BK20231124.csv
CIC_NORM_CIF_IDV_BRANCH_HIS.csv
CIC_NORM_CIF_IDV_DIF.csv
CIC_NORM_CIF_IDV_DOC_HIS.csv
CIC_NORM_CK_CST_BR_LOST.csv
CIC_NORM_COMPARE_FCT_CREDITCARD.csv
CIC_NORM_CRD_CC_ZERO.csv
CIC_NORM_FIN_FINANCIAL_DTL_TT200.csv
CIC_NORM_FIN_FINANCIAL_HIS.csv
CIC_NORM_M2_NORM_CRN_CTR_PS_CT_W_DEL.csv
CIC_NORM_M2_NORM_OVER_BAL_11_K32_DEL.csv
CIC_NORM_RMT_COM_YR_PRFL_BK.csv
CIC_NORM_TBL_C06PL12.csv
CIC_NORM_TBL_C06PL12_MATCH.csv
CIC_NORM_TBL_C06PL12_MATCH_FINAL.csv
CIC_USERS_HD285_THE.csv
CIC_USERS_HTLT_HOITIN_OFFLINE.csv
CIC_USERS_PPT_SN_PHAPLY_LOG.csv
CIC_USERS_TBLGIAODICHCAPTIN2407.csv
CIC_USERS_TBLGIAODICHCAPTIN_HIS.csv
CIC_USERS_TBLHOADON2011_LS.csv
CIC_USERS_TBLKTTC_CHOTSOLIEU.csv
CIC_USERS_TBLTONGHOPSP_DVSUDUNG_BK.csv
CIC_USERS_VAMC2.csv
CIC_XHTD_CRD_TXN_CREDITCARD_TN_TMP.csv
CIC_XHTD_TBLXHDN_BC_DANHMUC_CT.csv
CIC_XHTD_TBLXHDN_NN_201709.csv
CIF_COM_BRANCH.csv
CIF_COM_BRANCH_HIS.csv
CIF_COMPANY.csv
CIF_CUSTOMERS_TT02.csv
CIF_IDV_BRANCH.csv
CIF_INDIVIDUAL.csv
CIF_INDIVIDUAL_HIS.csv
CIF_NN_CHUNG.csv
CRD_SUPP_CREDITCARD.csv
CRD_TXN_CREDITCARD_1.csv
D2_BCTC_BC009.csv
DIM_CUSTOMER.csv
DWH_LOD_TXN_CONTRACT_MAX.csv
FCT_CREDITCARD_BK20220920.csv
FCT_CRN_CC.csv
FCT_CST_BAL_DTL.csv
FCT_TTP_LN_BAL_BAD_DEBT.csv
FCT_TTP_LN_BAL_CARD.csv
FCT_TXN_CREDITCARD.csv
HTLT_HOITIN.csv
NORM_CREDITCARD.csv
T02DS_CUSTOMER.csv
T02G_IN_BALANCE.csv
T02G_RPT02.csv
T02G_TRE_BALANCE.csv
TBL_C06PL12.csv
TBL_C06PL12_DOT6.csv
TBL_CDTN_HOITIN.csv
TBLTEMP_TH1_204_07012024.csv
TBL_TN_SEABANK_FIX_TMP.csv
TBLXHDN_BC_DANHMUC_CT.csv
TLT_LEGAL.csv
TLT_LOAN_HIS.csv
TLT_LOOKUP_INFO.csv
Notably, the records contain information not only about consumers, but also about business entities in Vietnam.
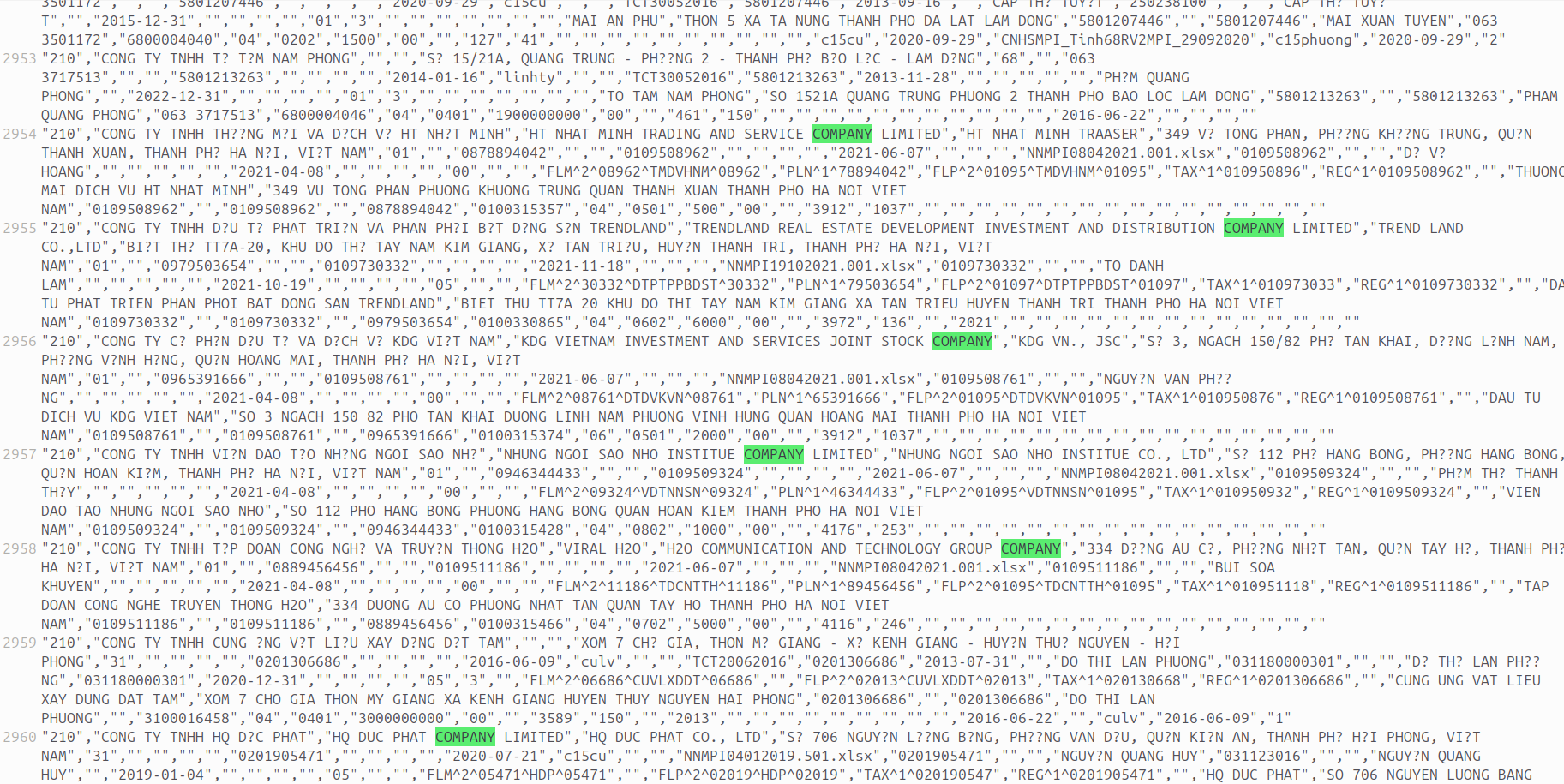
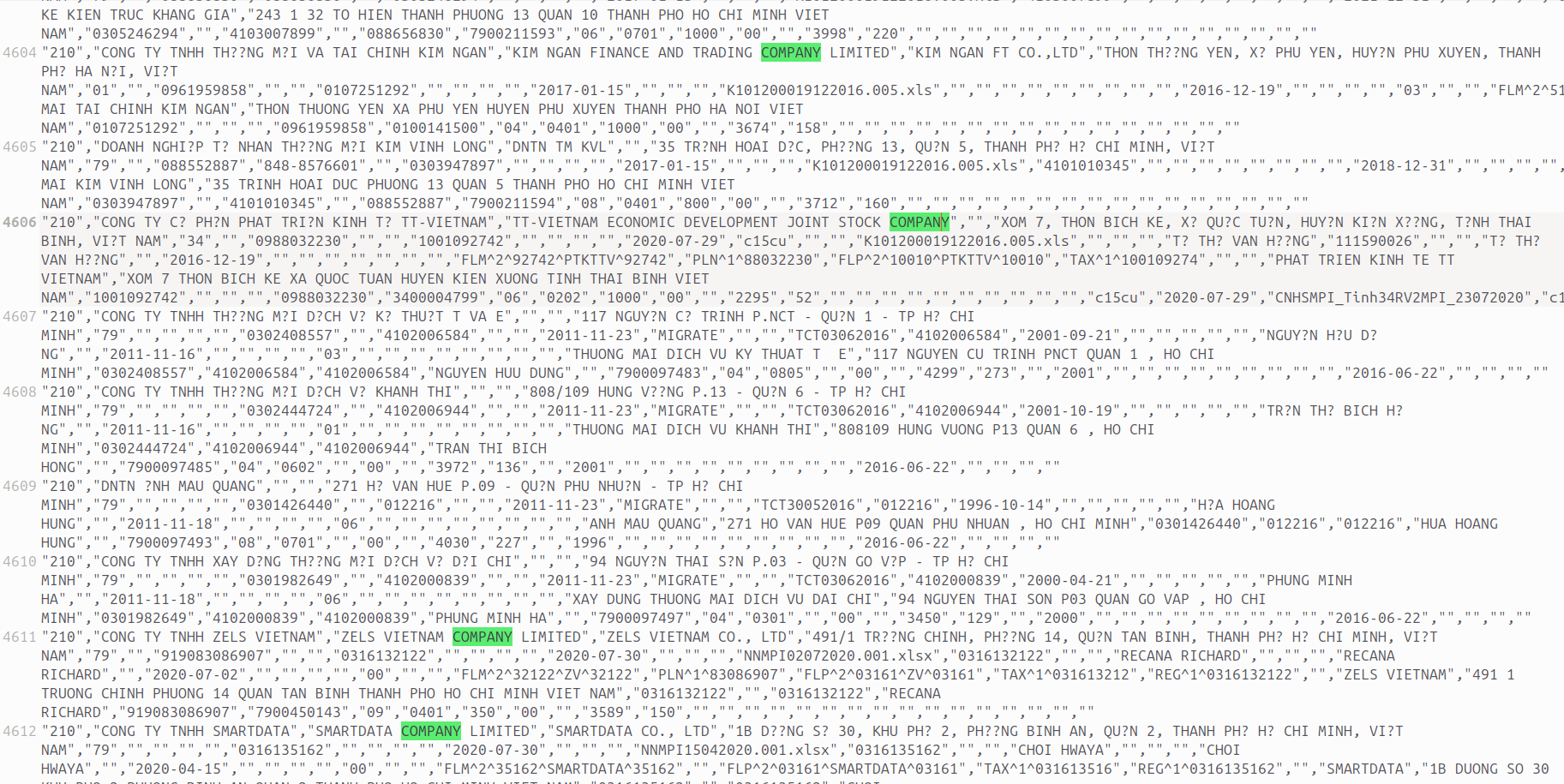
Resecurity has also acquired multiple records outside the public domain for further analysis and ongoing protection of our customers in Vietnam and the ASEAN region.
What Is the Value and Risk of the Stolen Data?
Dark Web Value: Stolen data from credit bureaus is among the most valuable on the dark web. Full identity profiles (“Fullz”) can sell for $10–$100+ per profile, credit card details for $5–$120 per card, and government IDs for hundreds to thousands of dollars each.
Criminal Uses: The data can be used for identity theft, financial fraud (such as opening new accounts or taking out loans), phishing, social engineering, and even corporate espionage if business or government data is included.
Long-Term Impact: The comprehensive nature of the breach means the data will likely remain valuable and dangerous for years, increasing the risk of ongoing fraud and privacy violations for affected individuals.
Of course, geography is an important factor affecting the price, and in the context of Vietnam, these figures would be much lower. Likely, the actors interested in buying data from Vietnam would prefer to acquire it in bulk; therefore, the pricing would be individual. The offered price of $175,000 seems reasonable considering the substantial number of records included. Such data can be used in fraudulent campaigns against both consumers and businesses.
The Root Cause
Exploit Used: ShinyHunters claimed to exploit an "n-day" vulnerability (a known but unpatched flaw) in end-of-life software used by the CIC. Because the software was no longer supported, no security patches were available, leaving the system especially vulnerable.
No Ransom Demand: Unlike many ransomware attacks, ShinyHunters did not attempt to extort the CIC. Instead, they listed the data for sale on a hacking forum, providing a large sample as proof.
Why Did ShinyHunters Attack the CIC?
Possible Motives
Financially Motivated: Cybersecurity experts overwhelmingly agree that ShinyHunters’ primary motivation is financial profit. The group has a long history of targeting organizations with valuable data that can be monetized on underground markets.
Value of Data: The type of data held by the CIC—comprehensive credit reports, PII, financial records, and government IDs—is extremely valuable on the dark web. Such data enables identity theft, financial fraud, and can be resold in bulk to other criminals.
No Political or Ideological Motive: There is no evidence that the attack was politically or ideologically motivated. ShinyHunters’ previous attacks have not shown a pattern of targeting based on geopolitical tensions, but rather on the potential for lucrative data theft.
Contextual Factors
Geopolitical and Financial Instability: The timing of the attack coincided with heightened global and regional geopolitical tensions and financial instability. Such periods often see a spike in cyberattacks, as institutions are more vulnerable and attackers seek to capitalize on the chaos.
Centralized Target: The CIC’s role as a centralized repository for Vietnam’s credit data made it a particularly attractive target, as breaching it exposed a single point of failure affecting nearly the entire population.
Incident Response
The CIC, in collaboration with national cybersecurity agencies and major state-owned technology partners, launched a task force to investigate the breach, secure systems, and identify vulnerabilities.
Vietnamese authorities and the CIC publicly acknowledged the breach and confirmed that an investigation was underway. They stated that, as of their announcement, there was no operational damage and that credit information services remained functional.
Authorities launched an official investigation to determine the full extent of the breach. The Department of Cybersecurity, along with major state-owned technology partners such as Viettel, VNPT, and NCS, was mobilized to assess the scope of the incident and to identify the vulnerabilities exploited by the attackers. The national cyberresponse team was also activated to take emergency measures and to coordinate the response.
So far, no disruption or damage has been caused, and credit services remain fully operational, CIC said in the letter. CIC representatives did not immediately respond to a request for comment. At the same time, nobody clarified how exactly the data was leaked on the Dark Web or took action to prevent it. It is clear that the incident had nothing to do with the disruption of CIC's operations but was focused on data theft. The national cyberresponse team is taking emergency measures to deal with the incident, the government said to local media. Authorities are working with the central bank and other agencies to contain the breach and secure the systems of the credit center.
In a recent announcement, a cybersecurity breach at the National Credit Information Center (CIC) was confirmed by the Vietnam Cyber Emergency Response Center (VNCERT), with initial investigations pointing to a criminal cyberattack aimed at stealing personal data. According to Vietnam News, VNCERT has issued a strict warning to all individuals and organizations, urging them not to download, share, or exploit any leaked data. Violations will be handled in accordance with Vietnam’s data protection and cybersecurity laws. Unfortunately, it cannot prevent cybercriminals from such activity, as the data has already been leaked and become available.
Yesterday, the State Bank of Vietnam (SBV) issued a statement to reassure clients following a data breach at the National Credit Information Centre (CIC). SBV confirmed that CIC is one of four organizations authorized to provide credit information services in Vietnam, and the credit data it collects does not include bank account numbers, account balances, savings books, payment accounts, debit or credit card numbers, CVV/CVC codes, or clients’ transaction histories.
Unfortunately, other types of PII are likely to be impacted by the breach and could still be used by fraudsters. In its statement, the central bank emphasized that commercial banks’ IT systems continue to operate safely and stably, ensuring the protection of clients’ assets and information. It also regularly directs financial institutions to strengthen security measures, comply with legal regulations on IT safety, and safeguard customers’ rights.
According to Reuters, investment bank JPMorgan said in a note to investors on Friday the incident could lead to higher costs for banks to improve cybersecurity and was a potential risk to deposit flows, but maintained its recommendation to stay invested in Vietnamese banks "barring a widespread impact or further incidents".
Significance
In a 2024 cybersecurity report, Vietnamese military-run telecommunication firm Viettel said data leakage in Vietnam had surged sharply, with 14.5 million leaked accounts accounting for 12% of the global total.
Cybersecurity professionals consider breaches of national credit bureaus to be "worst-case scenarios" due to the sensitivity and centrality of the data involved. Experts emphasize that such incidents can have cascading effects, including increased risk of identity theft, financial fraud, and systemic instability. When compared to other major breaches—such as those at Equifax (2017, 147 million records), Experian Brazil (2020, 220 million records), - the CIC breach stands out for its scale and the critical role of the institution in the national financial infrastructure in Vietnam. The average cost of a data breach in the finance sector is $5.9 million, with additional costs from lawsuits, regulatory fines, and loss of market value.
ShinyHunters is recognized as one of the most prolific and dangerous cybercrime groups, responsible for numerous high-profile breaches affecting hundreds of millions of users worldwide. Their attacks are characterized by technical sophistication, rapid monetization of stolen data, and a willingness to escalate to extortion and public leaks. The group’s involvement in the CIC breach further underscores the significance and potential impact of the incident.
References
- Vietnam’s national credit registration and reporting agency hacked; most of the population affected
https://databreaches.net/2025/09/08/vietnams-national-credit-registration-and-reporting-agency-hacke...
- Vietnam warns of major data theft after credit center hacked
https://www.bloomberg.com/news/articles/2025-09-12/vietnam-says-national-credit-center-hacked-warns-...
- Vietnam probes suspected cyberattack on its national credit information database
https://www.businesstimes.com.sg/international/asean/vietnam-probes-suspected-cyberattack-its-nation...
- VNCERT khuyến cáo người dân nâng cao cảnh giác trước tội phạm mạng
https://vietnamnet-vn.translate.goog/trung-tam-thong-tin-tin-dung-quoc-gia-bi-hacker-tan-cong-244165...

