

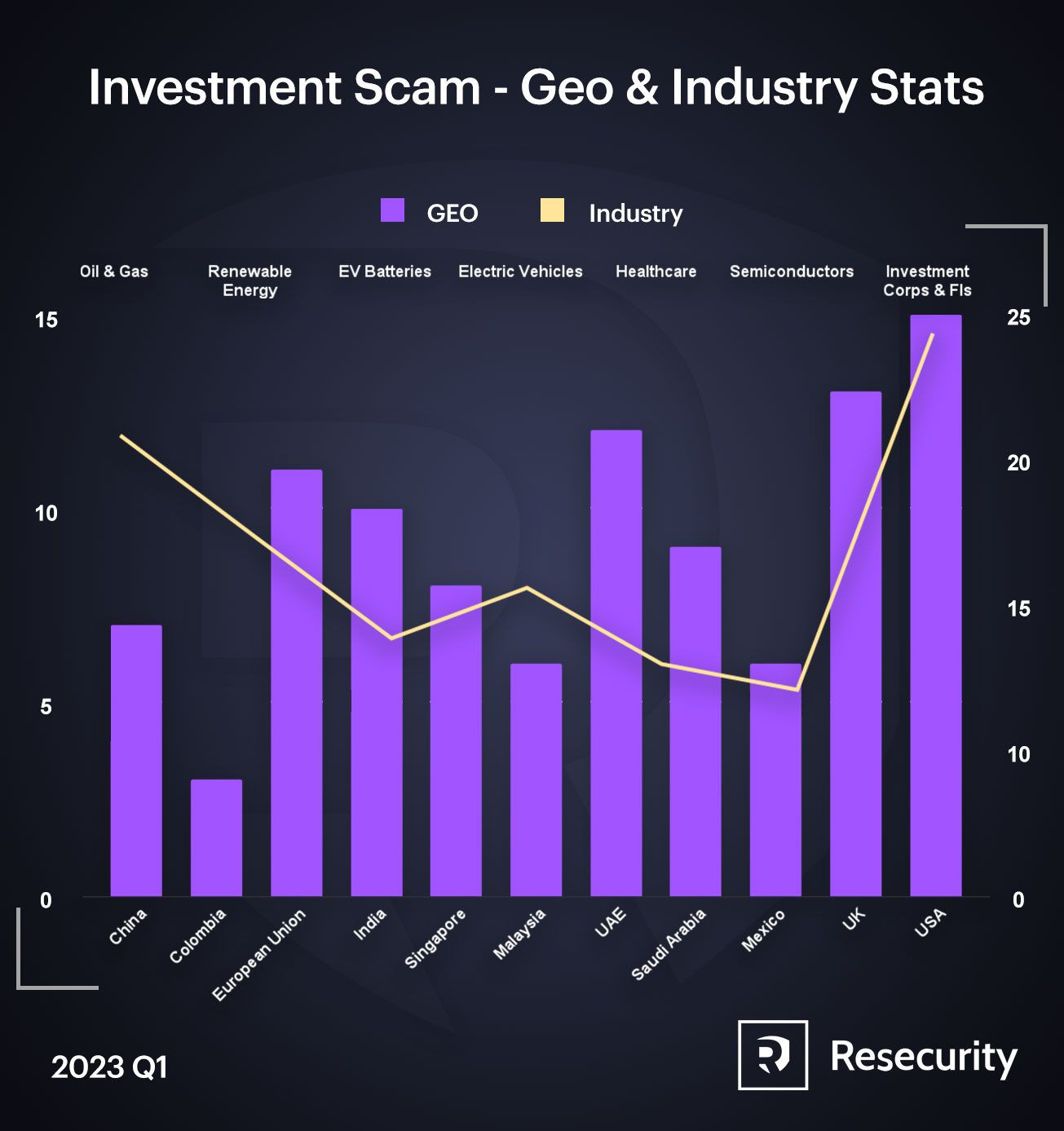
Resecurity identified one of the largest investment fraud networks by size and volume of operations created to defraud Internet users from China, Colombia, European Union, India, Singapore, Malaysia, United Arab Emirates, Saudi Arabia, Mexico, Australia, Canada, the U.S. including other regions. The bad actors operating as an organized crime syndicate developed a massive infrastructure to impersonate popular Fortune 100 corporations from the U.S and the U.K by using their brands and market reputation to trick consumers. The total damage from investment fraud including ponzi and pyramid schemes exceeds $5.8 billion in the U.S and over $77 worldwide (2022), with significant rapid growth at the start of Q1 2023. Investment fraud does serious damage to investors – beyond monetary losses. A FINRA survey points to health, marital and trust problems resulting from financial scams. Businesses experience significant damage in customer loyalty and brand reputation - in a long run negatively affecting sales and market profile.
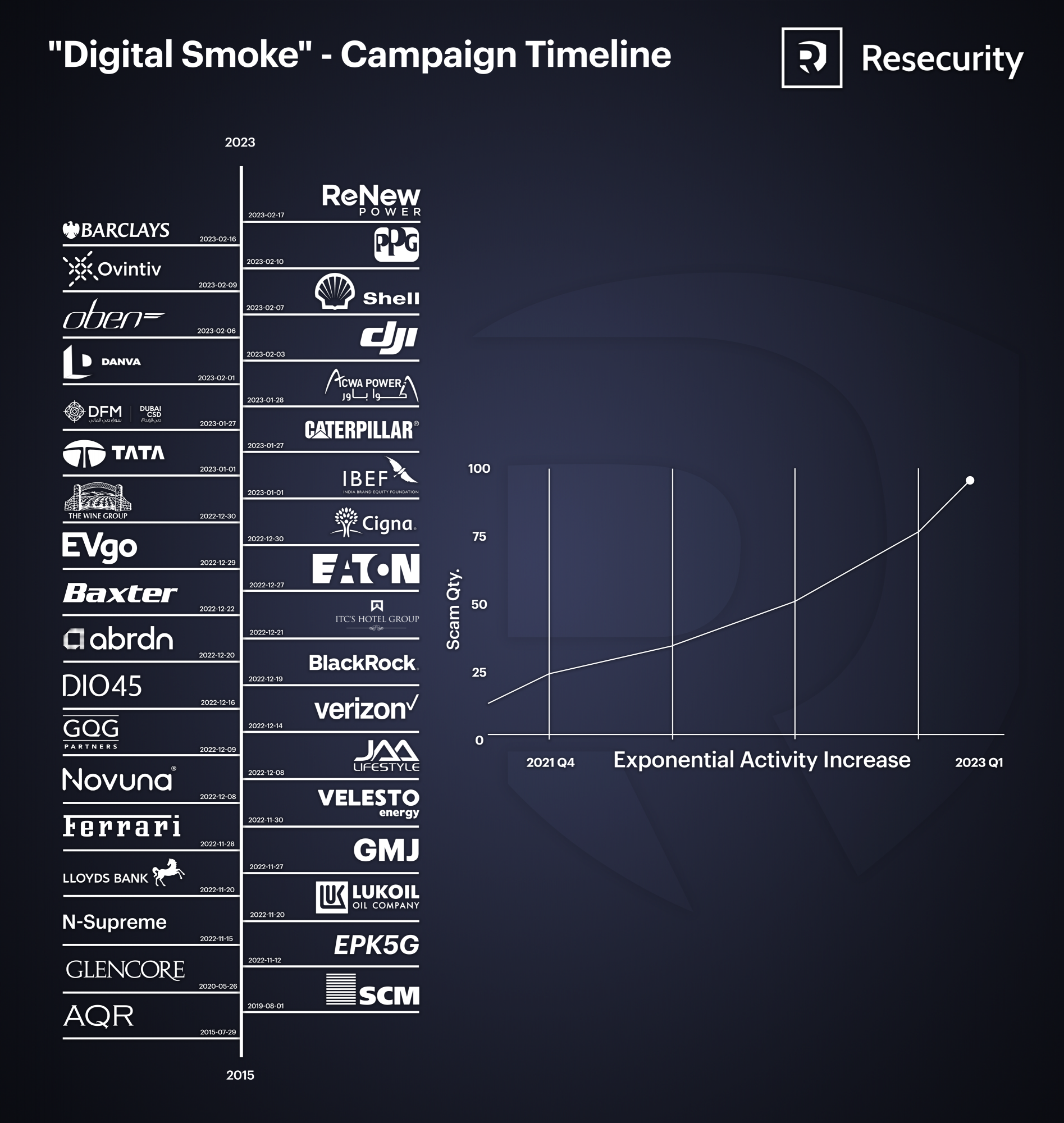
Notably, the bad actors have chosen high-demand investment areas to impersonate world-known brands including ABRDN (UK), Blackrock (US), Baxter Medical (US), Ferrari (Italy), ITC Hotels (India), Eaton Corporation (US/UK), Novuna Business Finance (UK), Tata (India), Valesto Oil (Malaysia), Lloyds Bank (UK). The majority of the identified fraudulent projects were related to financial services, oil & gas, renewable energy, EV batteries, electric vehicles, healthcare, semiconductors, and world-recognized investment corporations and funds with global presence.
The information about Digital Smoke along with identities of key actors has been timely shared with the Indian Cybercrime Coordination Center and the U.S. Law Enforcement in Q4 2022 which disrupted at the beginning of 2023.
‘Smoke and Mirrors’ of Modern Cyberspace
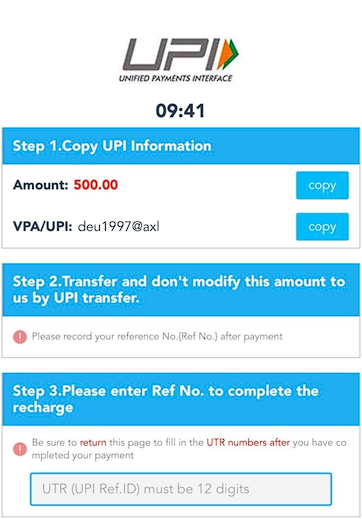
The criminal syndicate called Digital Smoke offered investment options in non-existing products and investment plans supposedly offered by the Fortune 100 corporations and state-owned entities. The bad actors have developed a large network of WEB-resources and related mobile applications hosted on bulletproof hosting providers, and jurisdictions not easily reachable for immediate take-downs – the total number of the identified hosts in December 2022 alone exceeded 350+ with thousands of domains used for ‘cloaking’ (Black SEO), hidden redirects and protection of the payment gateway used by fraudsters to collect payments from victims leveraging AliPay (China) and Unified Payments Interface (UPI) - an instant real-time payment system developed by National Payments Corporation of India, along with cryptocurrencies. Notably, combination of these methods enabled fraudsters to process funds with great flexibility – supporting Google Pay (GPay), PhonePe, Paytm, and major online-banking platforms.
Resecurity dubbed this group Digital Smoke, the name was chosen because of their sophisticated tactics used to entice victims hankering to earn good money online - the bad actors used the traditional HYIP approach: The victim is asked to deposit money with the option to withdrawal their funds anytime, mechanisms used by investment bankers and financial advisors to help make the victim feel comfortable investing in perspective markets and fixed income products. The group has also successfully combined ‘investment scam’ and ‘investment fraud’ models leveraging several scenarios to defraud victims:
- Investment Scam
Investment scam happens when bad actors try tricking you into investing money. They might want you to invest money in stocks, bonds, notes, commodities, or some plans to earn money online. Once the funds are sent to them – the victim won’t receive anything back. Some types of investment scams leverage sophisticated tactics to steal their victims’ money which typically ranges between a couple hundred to several thousand dollars. India is one of the most active participants for online trade and global payment systems, that's why the total damages from such activity may be estimated in millions. Like "exit scams" in the cryptocurrency world, after the victim deposited their funds, they wait for their payout but instead get their access blocked to the fake resource while the bad actors clean up loose ends, leaving the victim with nothing. Typically, the operator who initially invited the victims to register will announce how the project may experience some payout delays or got closed due to some unforeseen reasons.
- Investment Fraud
A pyramid scheme involves the collection of money from individuals at the bottom (new investors) to pay the initial investors at the top, with all emphasis on bringing in new members/investors and not on selling the product or service. It is possible, that some of the tricked investors will receive some payouts with the goal to get more money from the victims who may start believing into the legitimacy of such investment product.
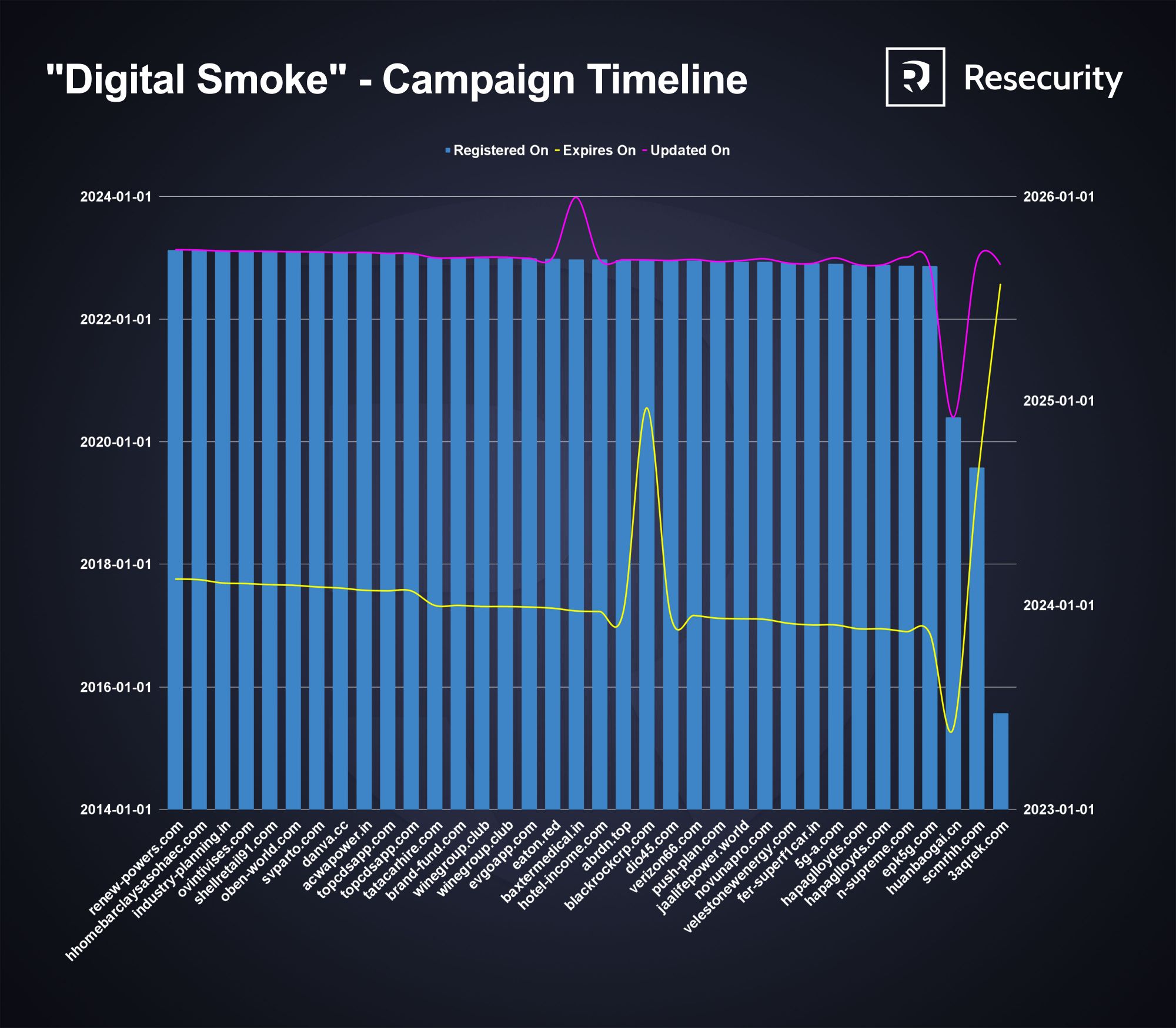
Notably, most domain names and hosting platforms used by cybercriminals were registered via Alibaba (China), however the actors were primarily targeting India.
Modus Operandi of Investment Scam
BlackRock
One of the first investment scam projects launched by Digital Smoke, who were identified by Resecurity was impersonating Blackrock, an American multi-national investment company based in New York City. Founded in 1988, initially as a risk management and fixed income institutional asset manager, BlackRock is the world's largest asset manager, with US$10 trillion in assets under management as of January 2022. The bad actors have registered multiple fake domain names with similar brand spelling and promoted them via social media and instant messengers to attract investments. One such domain has been registered around January 19, 2022 – blackrockcrp.com. Notably, the links planted by bad actors to register new victims contained a referral code tied to affiliates promoting the scam via Youtube and Whatsup IM.

Once the victim registers, the bad actors ask them to make a deposit by sending payment to an account registered in Indian:- Yes Bank (https://www.yesbank.in) via UPI payment:
Resecurity has extracted the payment details to analyze possible connections between accounts identified in other investment fraud projects.
| WHOIS Records for blackrockcrp.com | |
| Registrar Info:- |
|
| Name: | Hostinger, UAB |
| Whois Server: | whois.hostinger.com |
| Referral URL: | https://www.whois.hostinger.com/ |
| Status: | clientTransferProhibited https://www.icann.org/epp#clientTransferProhibited |
| Important Dates:- | |
| Expires On | 2023-12-19 |
| Registered On | 2023-12-19 |
| Updated On | 2022-12-19 |
| Name Servers :- | |
| ns1.dns-parking.com | 162.159.24.201 |
| ns2.dns-parking.com | 162.159.25.42 |
Abrdn
The bad actors impersonate Abrdn plc, formerly Standard Life Aberdeen plc, a United Kingdom-based global investment company headquartered in Edinburgh, Scotland. It is listed on the London Stock Exchange and is a constituent of the FTSE 100 – https://www.abrdn.com.
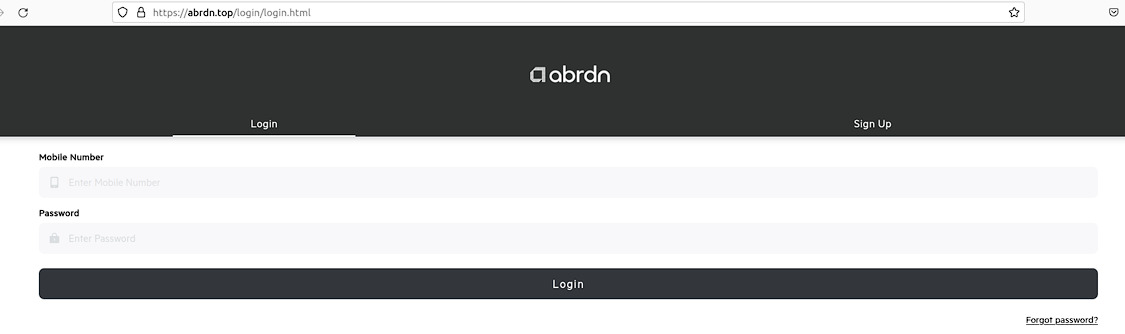
| URL | https://abrdn.top/?zf=3435 |
| Payment Methods: | UPI |
| Payment Details: | UPI ID: deu1997@axl |
| WHOIS Records for abrdn.top | |
| Registrar Info:- |
|
| Name: | Alibaba.com Singapore E-Commerce Private Limited |
| Whois Server: | whois.aliyun.com |
| Referral URL: | http://www.alibabacloud.com |
| Status: | ok |
| Important Dates:- | |
| Expires On | 2023-12-20 |
| Registered On | 2022-12-20 |
| Updated On | 2022-12-20 |
| Name Servers :- | |
| algin.ns.cloudflare.com | 173.245.59.61 |
| mckenzie.ns.cloudflare.com | 172.64.34.253 |
DJI
The global drone leader and inivator, DJI, has fallen victim to the Digital Smoke scammer syndicate. In the screenshot below, we can see the bad actors offering a range of rewards for different level tiers, daily check-ins, and referrals.

| WHOIS Records for svparto.com | |
| Registrar Info:- |
|
| Name: | Alibaba.com Singapore E-Commerce Private Limited |
| Whois Server: | grs-whois.hichina.com |
| Referral URL: | http://wanwang.aliyun.com |
| Status: | ok |
| Important Dates:- | |
| Expires On | 2024-02-03 |
| Registered On | 2023-02-03 |
| Updated On | 2023-02-05 |
| Name Servers :- | |
| ignat.ns.cloudflare.com | 108.162.195.19 |
| lia.ns.cloudflare.com | 108.162.192.185 |
Pseudo-Investments into Oil Markets
Velesto Oil

The bad actors impersonated Velesto Oil. VELESTO ENERGY BERHAD (“VEB”) is a Malaysia-based multinational provider of drilling for the upstream sector of the oil and gas industry.
The activity spike was registered during the Christmas and New Year's period, when online activity skyrocketed, and when both Internet users and financial institutions get overwhelmed with logistics and payments. The bad actors offered multiple areas of investments, one of which was in the energy sector. Around December 2022, a network of fake landing pages and associated mobile apps for Android devices impersonating Malaysian energy corporations launched, in the launch was a landing page and Android app for one of the major global energy providers.
The creative fraudsters offered victims the option to invest in new oil facilities as well as petroleum stations, which would be built by 2023/2024 and would provide a fixed income option - during year 1 and with bonus payments during year 2 and 3. It's worth noting, some of the language for this pretext was copied from existing investment programs, typically for entrepreneurs and franchises looking for new business opportunities in the oil and gas sector. This activity is not typical for cybercriminals and may clearly outline the differentiator of the Digital Smoke group. Their other scams were related to investments in mineral resources with a defined minimum sum of investment.
| WHOIS Records for velestonewenergy.com | |
| Registrar Info:- |
|
| Name: | DYNADOT, LLC |
| Whois Server: | Unknown |
| Referral URL: | dynadot.com |
| Status: | clientTransferProhibited |
| Important Dates:- | |
| Expires On | 2023-11-30 |
| Registered On | 2022-11-30 |
| Updated On | 2022-11-30 |
| Name Servers :- | |
| denver.ns.cloudflare.com | 108.162.195.196 |
| kristina.ns.cloudflare.com | 108.162.194.125 |
Shell

On the 13th February 2023, the bad actors have impersonated the very well known oil and petroleum giant Shell, they are offering a multitude of yield options with a registration link attached.

We can see from the image above how the threat actors are enticing their victims with the news of a new oil fields, how four of wells are now producing and 2 are injecting. They do this to inspire trust and urgency.

| WHOIS Records for shellretail91.com | |
| Registrar Info:- |
|
| Name: | DYNADOT, LLC |
| Whois Server: | whois.dynadot.com |
| Referral URL: | dynadot.com |
| Status: | clientTransferProhibited |
| Important Dates:- | |
| Expires On | 2024-02-07 |
| Registered On | 2023-02-07 |
| Updated On | 2023-02-08 |
| Name Servers :- | |
| denver.ns.cloudflare.com | 108.162.195.196 |
| kristina.ns.cloudflare.com | 108.162.194.125 |
ReNew Power
On the 12th February, 2023, the bad actors launched a campaign to impersonated ReNew Power, India's largest renewable energry company, based in Gurgaon, Haryana.
Again, Digital Smoke utilized IM (Instant Messaging) to talk with their victims, they present their fraudulent investment scam details with enticing yields and promises.
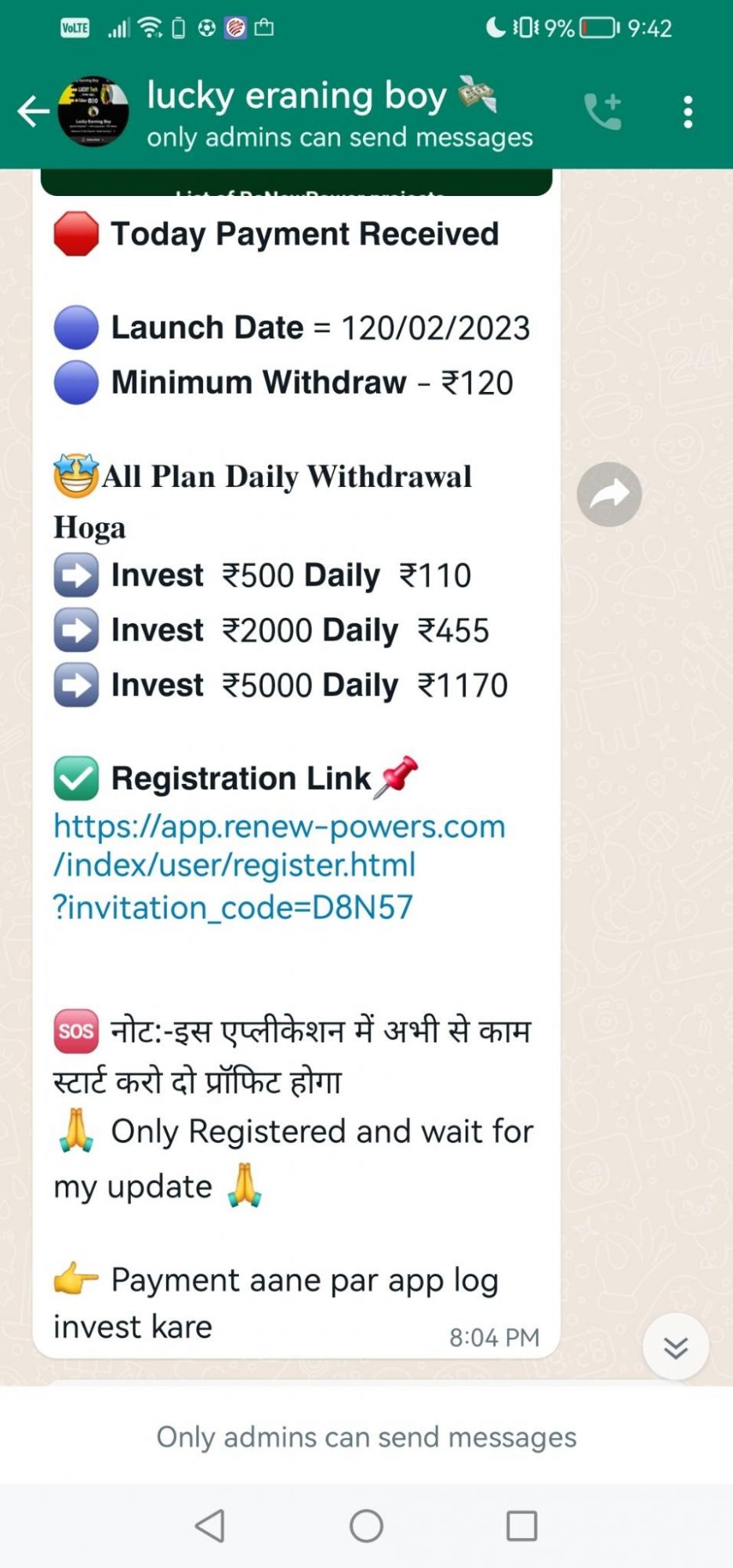
The victim reads over the IM message then taps on the "Registration Link", once the victim clicks the link, the victim is forwarded to the scammers fraudlent investment scam landing page seen below.

| WHOIS Records for renew-powers.com | |
| Registrar Info:- |
|
| Name: | DYNADOT, LLC |
| Whois Server: | Unknown |
| Referral URL: | dynadot.com |
| Status: | clientTransferProhibited |
| Important Dates:- | |
| Expires On | 2024-02-17 |
| Registered On | 2023-02-17 |
| Updated On | 2023-02-18 |
| Name Servers :- | |
| bowen.ns.cloudflare.com |
108.162.195.83 |
| tara.ns.cloudflare.com |
108.162.192.225 |
ACWA Power
Another fraudulent app detected launched by Digital Smoke in late January, 2023. ACWA Power is a developer, investor, co-owner and operator of a portfolio of power generation and desalinated water production plants. The scammers have used their good name and strong company image to entice their unsuspecting victims into parting with their money.

In the image above, we can see how the scammers utilize the same if not very similar structure to the other apps and scams they've built.
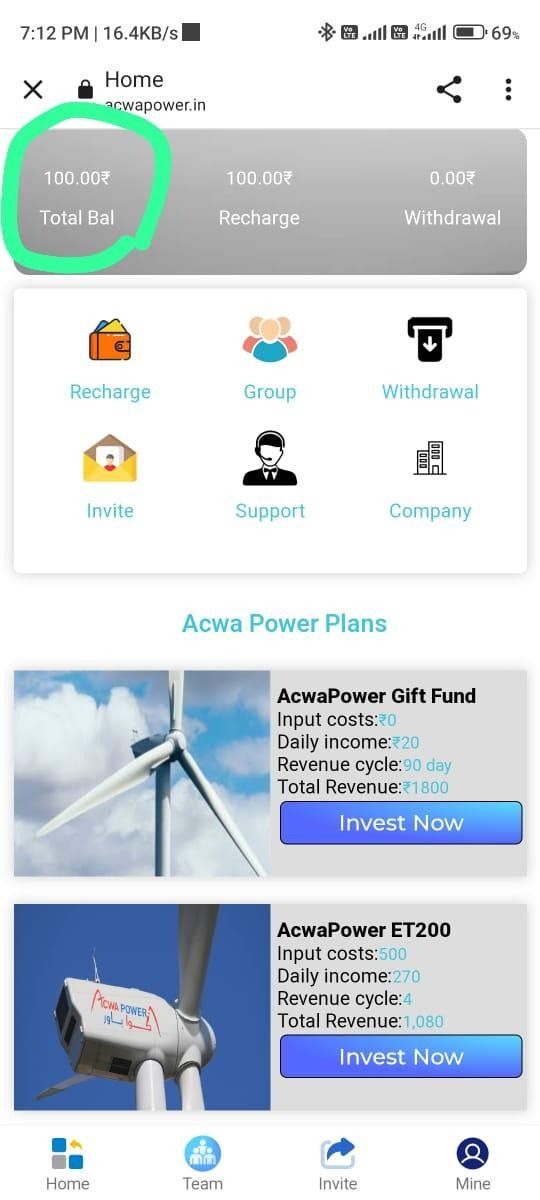
Example: https://acwapower[.]in/register/?r_code=mv4y3u
| WHOIS Records for acwapower.in | |
| Registrar Info:- |
|
| Name: | GoDaddy.com, LLC |
| Whois Server: | whois.godaddy.com |
| Referral URL: | http://www.godaddy.com/domains/search.aspx |
| Status: | clientUpdateProhibited |
| clientTransferProhibited | |
| clientDeleteProhibited | |
| clientRenewProhibited | |
| Important Dates:- | |
| Expires On | 2024-01-28 |
| Registered On | 2023-01-28 |
| Updated On | 2023-02-02 |
| Name Servers :- | |
| ns67.domaincontrol.com | 97.74.103.44 |
| ns68.domaincontrol.com | 173.201.71.44 |
Ovintiv
So lovingly on the 14th February, the Digital Smoke scamming syndicate impersonated the American conglomorate, Ovintiv. From the first image below, we can see how the scammers offer up a few different investment options to entice their victims
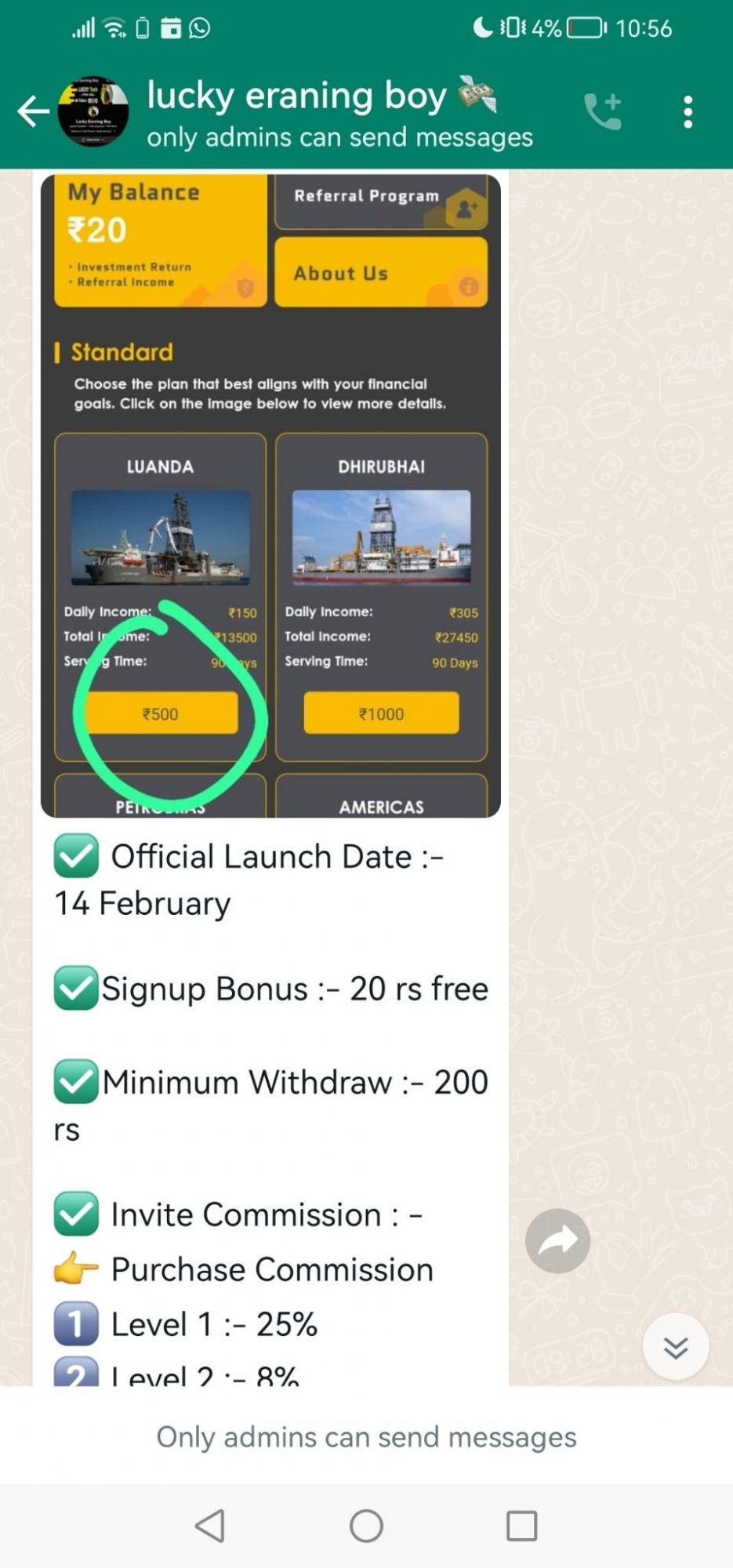
In the next screenshot, we can see the page the victum lands on where they're required to register before taking any further steps. Notice how the phone number GEO is pre set to India.
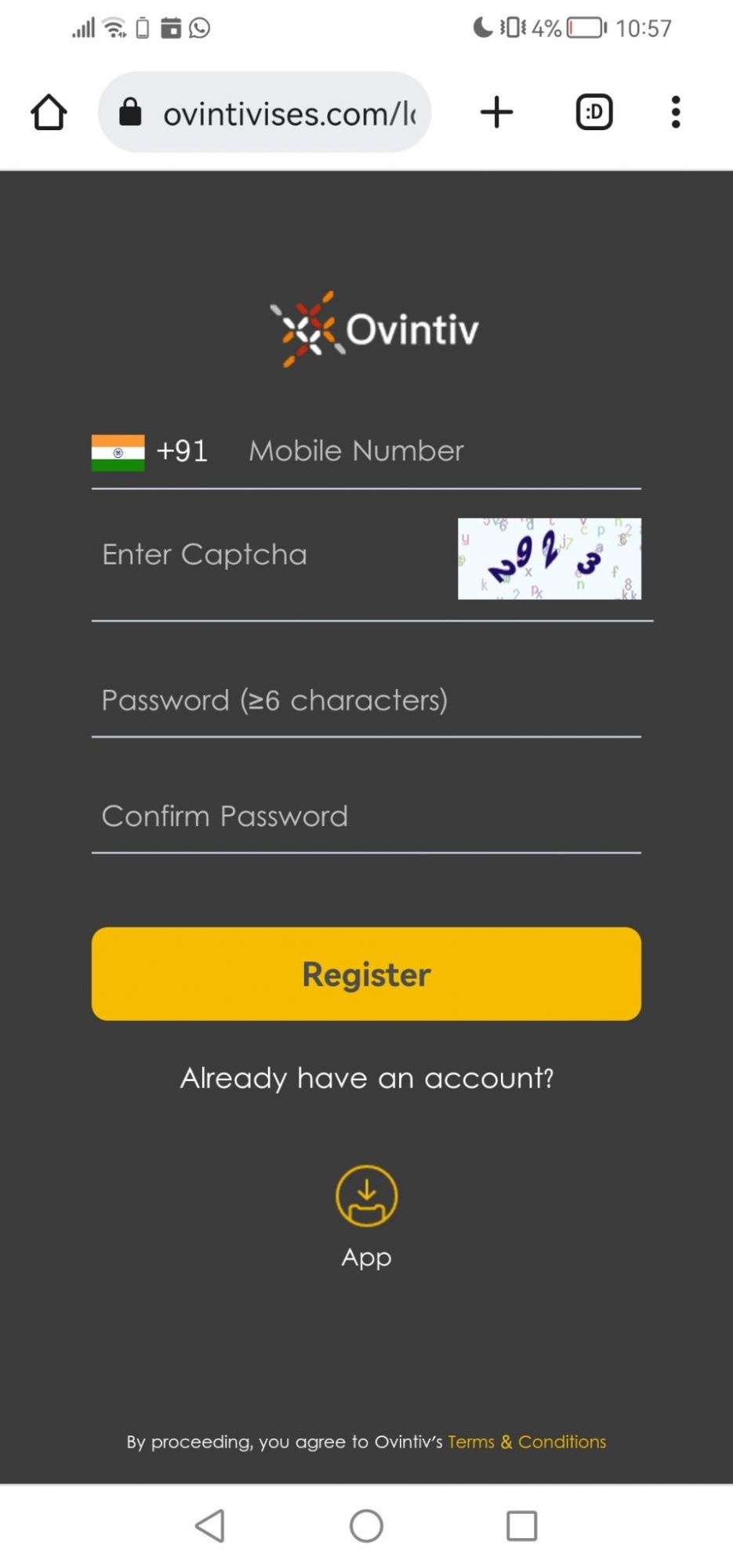
| WHOIS Records for ovintivises.com | |
| Registrar Info:- |
|
| Name: | Gname.com Pte. Ltd. |
| Whois Server: | whois.gname.com |
| Referral URL: | http://gname.com |
| Status: | clientTransferProhibited |
| Important Dates:- | |
| Expires On | 2024-02-09 |
| Registered On | 2023-02-09 |
| Updated On | 2023-02-09 |
| Name Servers :- | |
| mark.ns.cloudflare.com | 108.162.193.130 |
| shubhi.ns.cloudflare.com | 108.162.194.63 |
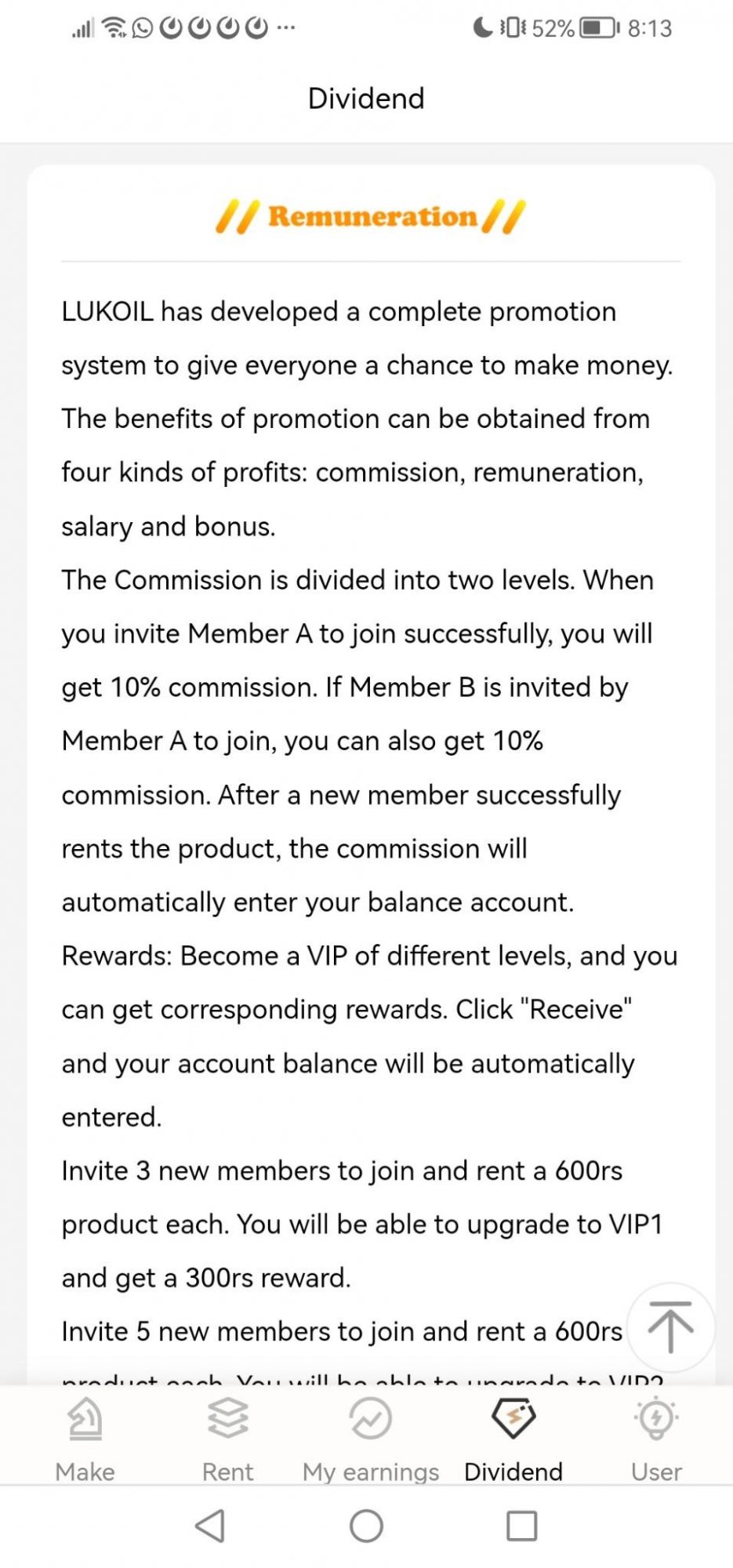
LukOil
On January 26th the syndicate launched the “Lukoil” scam campaign. Lukoil is a Russian oil company that Digital Smoke has used to generate interest in their victims. In the screenshot below, you can see how they hook their prospective victims by offering high returns based over a cycle of 365 days.
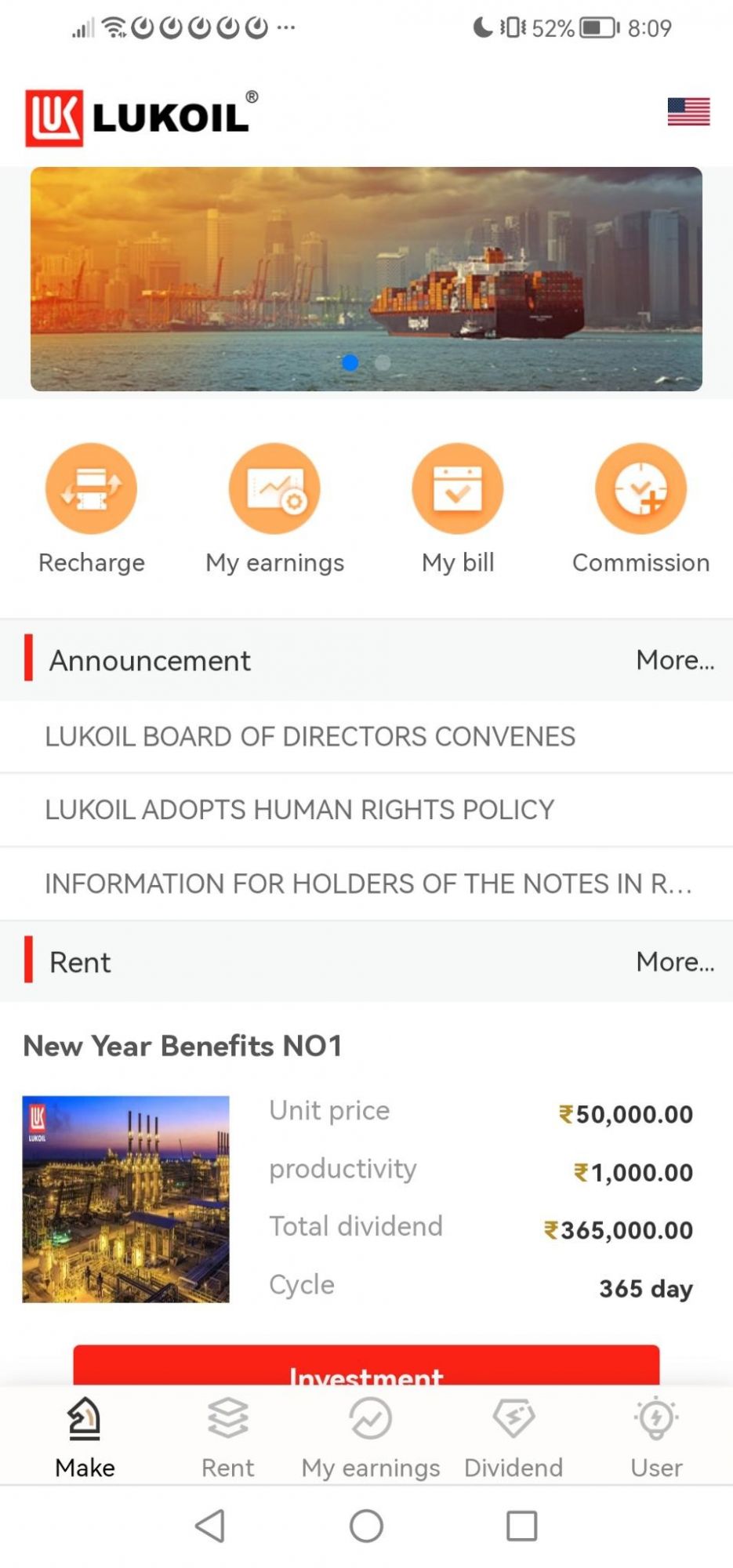
In the screenshot below you can see how the Digital Smoke syndicate are convincing their victims, they’re showing previous returns which appear to be paid already, in reality this is all fake and prepared material to fool the victims, they do this to install trust and FOMO (Fear Of Missing Out). Of course, non the wiser victims fall for this and endeavor to send them money, little do they know nothing will ever be returned to them.
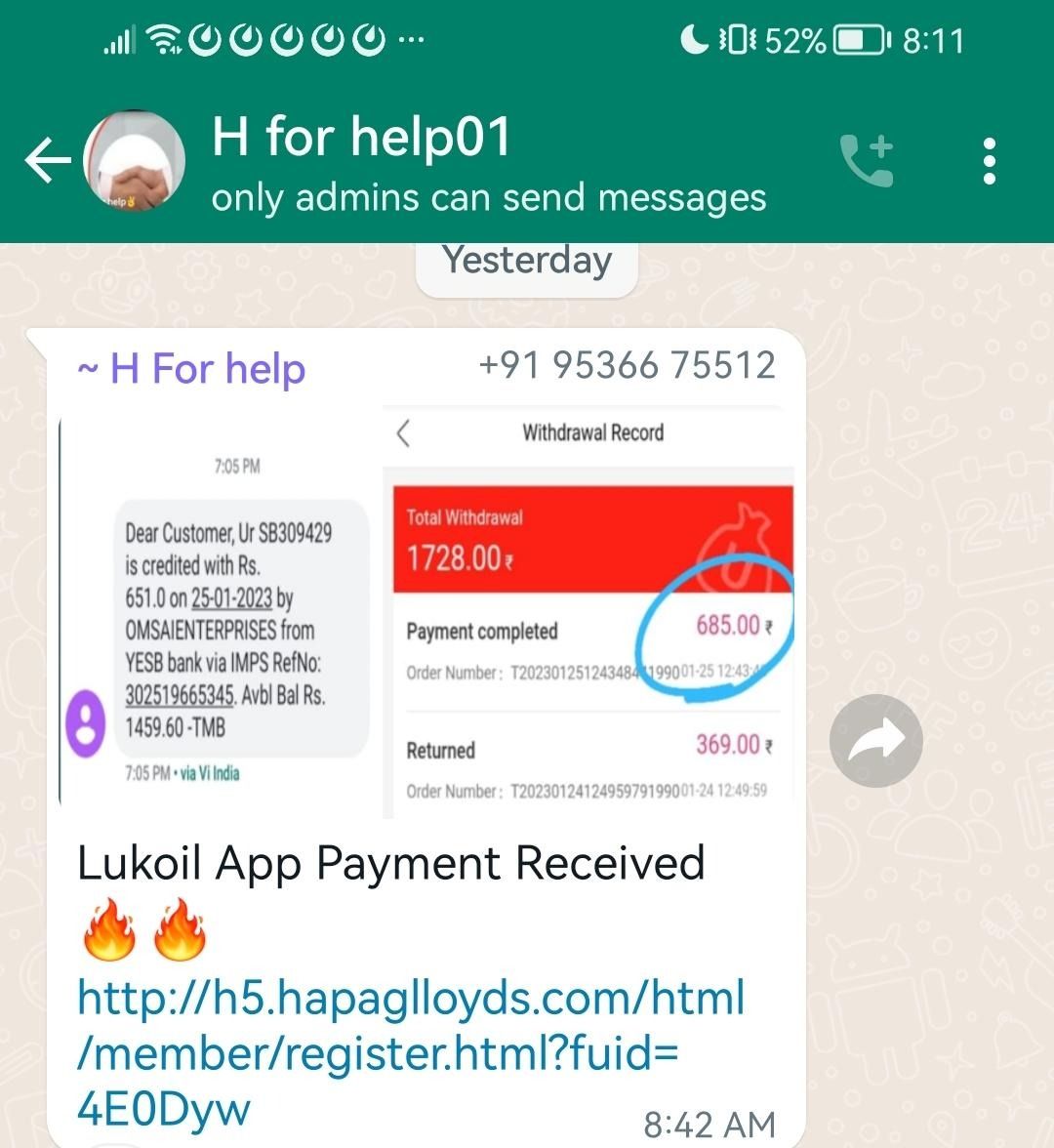
The fraudsters also designed a "legend" to trick their victims with a dividends model encouraging the invitation of more users into the fake investment platform.
| WHOIS Records for webh5.hapaglloyds.com | |
| Registrar Info:- |
|
| Name: | GoDaddy.com, LLC |
| Whois Server: | |
| Referral URL: | http://whois.godaddy.com |
| Status: | clientDeleteProhibited |
| clientRenewProhibited | |
| clientTransferProhibited | |
| clientUpdateProhibited | |
| Important Dates:- | |
| Expires On | 2023-11-20 |
| Registered On | 2022-11-30 |
| Updated On | 2022-11-30 |
| Name Servers :- | |
| ns33.domaincontrol.com | 97.74.106.17 |
| ns34.domaincontrol.com | 173.201.74.17 |
Glencore plc
Glencore plc is a Swiss multinational commodity trading and mining company with headquarters in Baar, Switzerland.
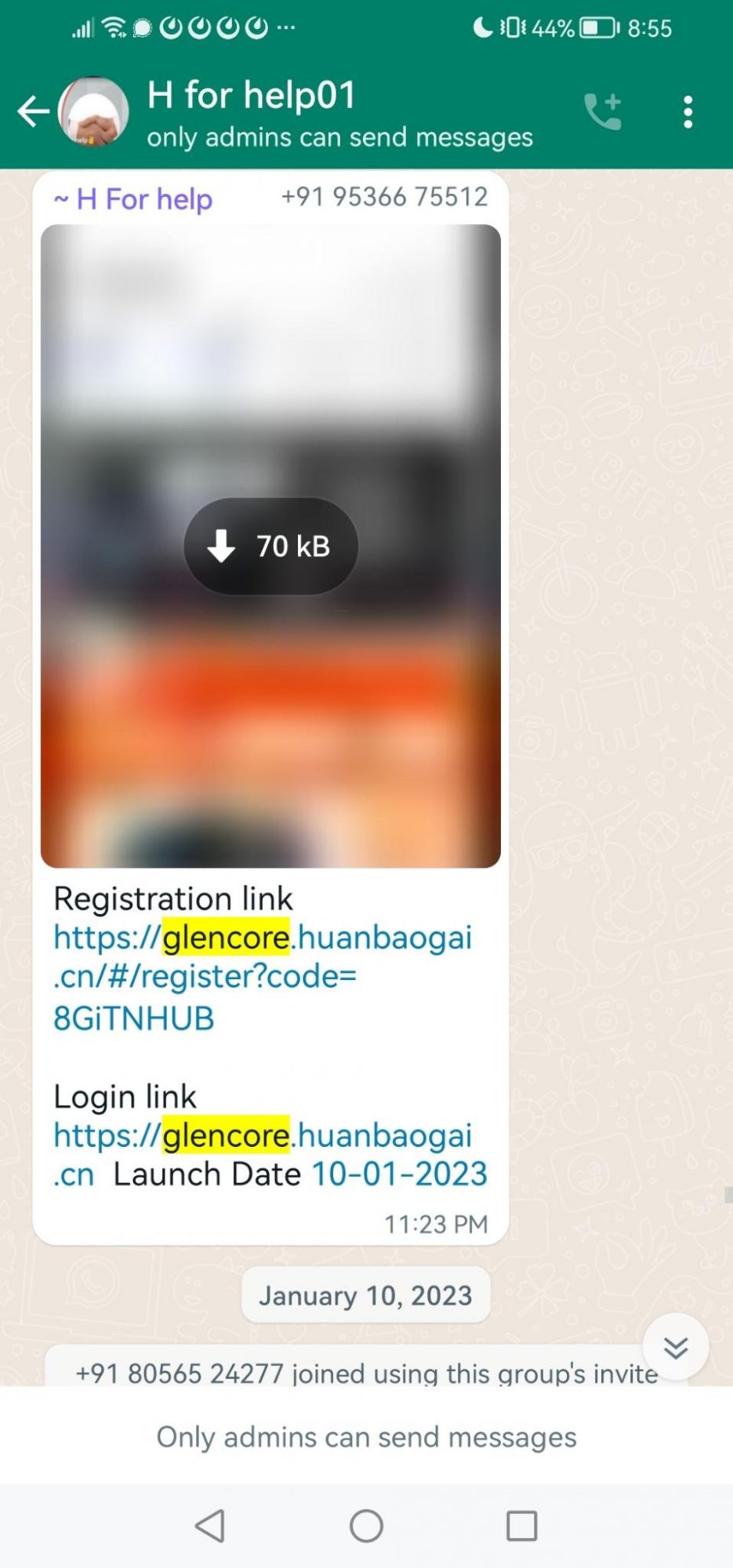
The bad actors launched the scam project around January 10th this year.
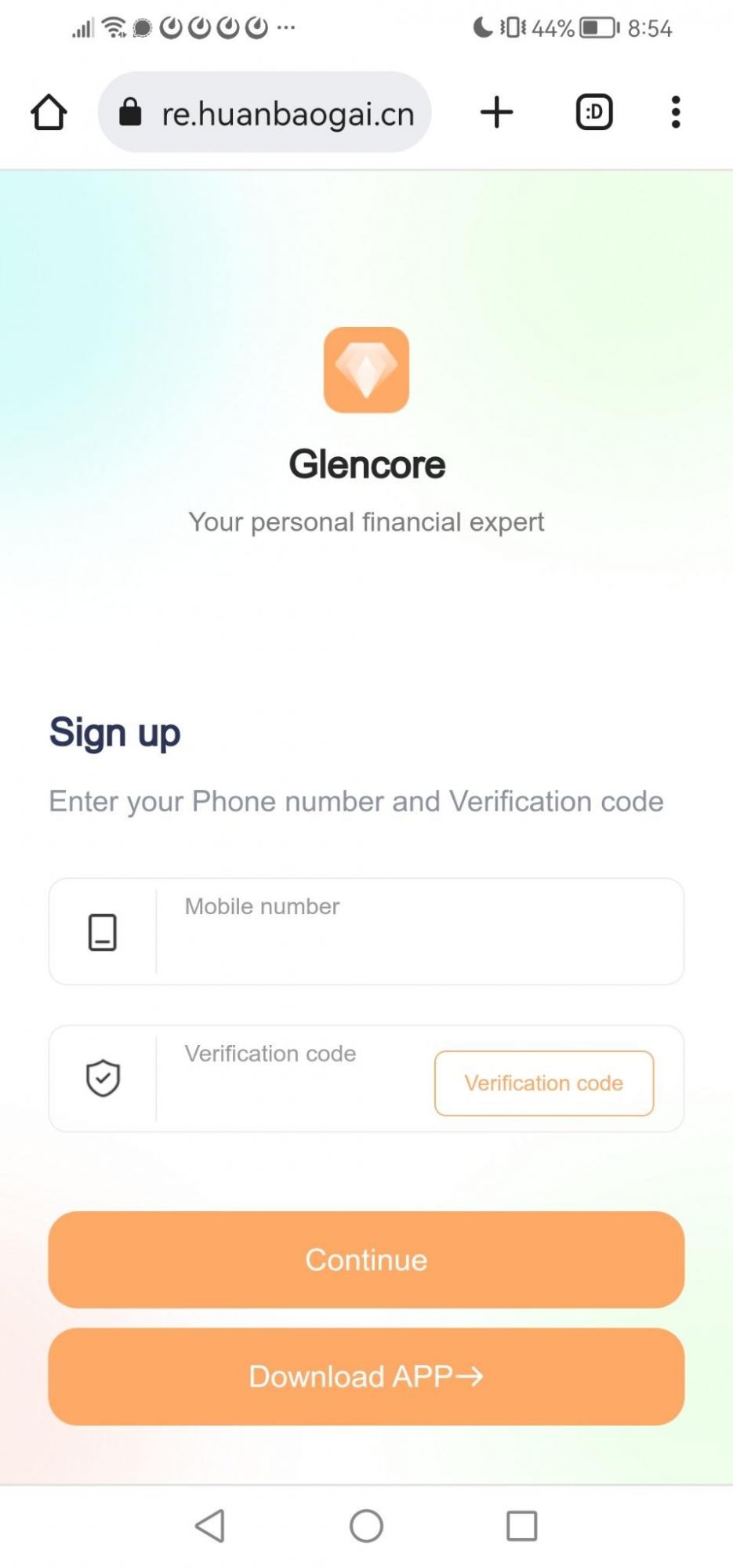
Notably, the resource was hosted in China, likely to delay further takedown by servicing victims from other countries including India.
Registration link: https://glencore.huanbaogai.cn/#/register?code=8GiTNHUB
Login link: https://glencore.huanbaogai.cn
Launch Date: 10-01-2023
The bad actors also designed 2 mobile apps, where iOS version was downloading from fake landing page impersonating Apple Store.

Fake Apple Store download page to trick users on mobile devices:

| WHOIS Records for glencore.huanbaogai.cn | |
| Registrar Info:- |
|
| Name: | 杭州电商互联科技有限公司(原杭州创业互联科技有限公司) |
| Whois Server: | Unknown |
| Referral URL: | Unknown |
| Status: | Unknown |
| Important Dates:- | |
| Expires On | 2023-05-26 |
| Registered On | 2020-05-26 |
| Updated On | Unknown |
| Name Servers :- | |
| fute1.dns.com | Unknown |
| fute2.dns.com | Unknown |
Baxter Medical
The bad actors impersonated Baxter International Inc., an American multinational healthcare company with their headquarters in Deerfield, Illinois. The company primarily focuses on products to treat kidney disease, and other chronic and acute medical conditions – https://www.baxter.com.

| URL | http://www.baxtermedical.in/index/user/register/invite_code/1oc3w.html |
| Payment Methods: | UPI |
| Payment Details: | UPI ID: 777wasd@airtel |
| bklm777@airtel | |
| 777uponom@airtel | |
| uponom777@airtel |
| WHOIS Records for baxtermedical.in | |
| Registrar Info:- |
|
| Name: | Dynadot LLC |
| Whois Server: | Unknown |
| Referral URL: | http://www.dynadot.com |
| Status: | clientTransferProhibited |
| Important Dates:- | |
| Expires On | 2023-12-22 |
| Registered On | 2022-12-22 |
| Updated On | 2023-12-27 |
| Name Servers :- | |
| dawn.ns.cloudflare.com | |
| mcgrory.ns.cloudflare.com |
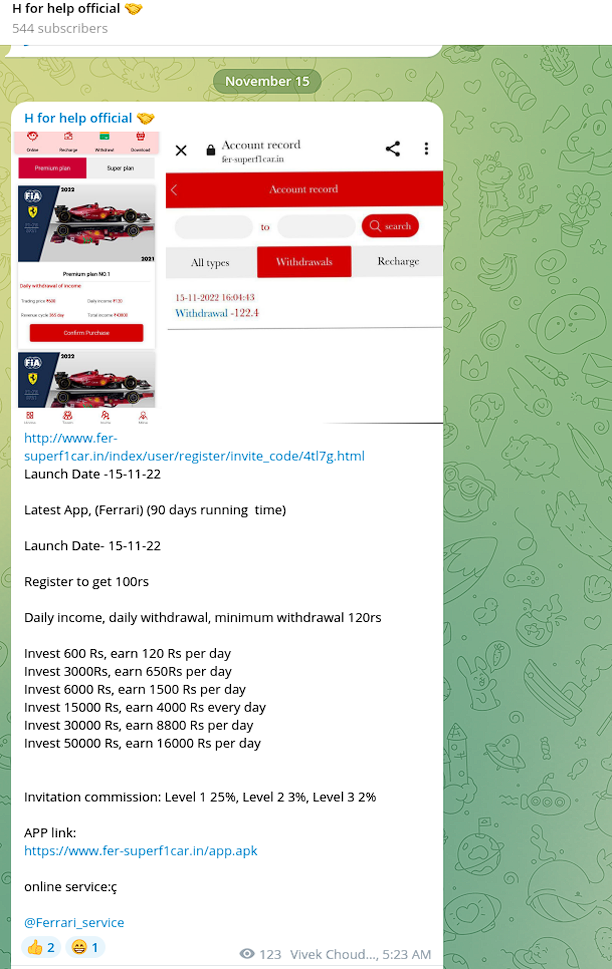
Ferrari
The bad actors impersonate Ferrari, an Italian luxury sports car manufacturer based in Maranello, Italy - https://t.me/hforhelp/58
Fake resource: http://www.fer-superf1car.in/index/user/register/invite_code/4tl7g.html
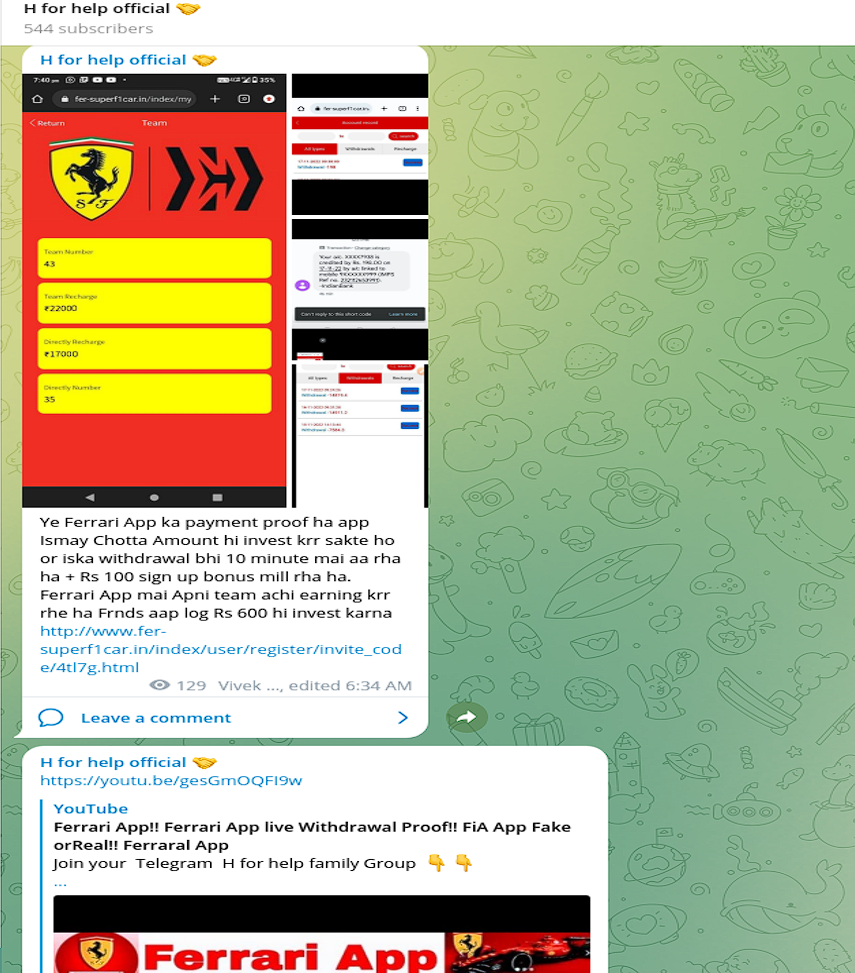
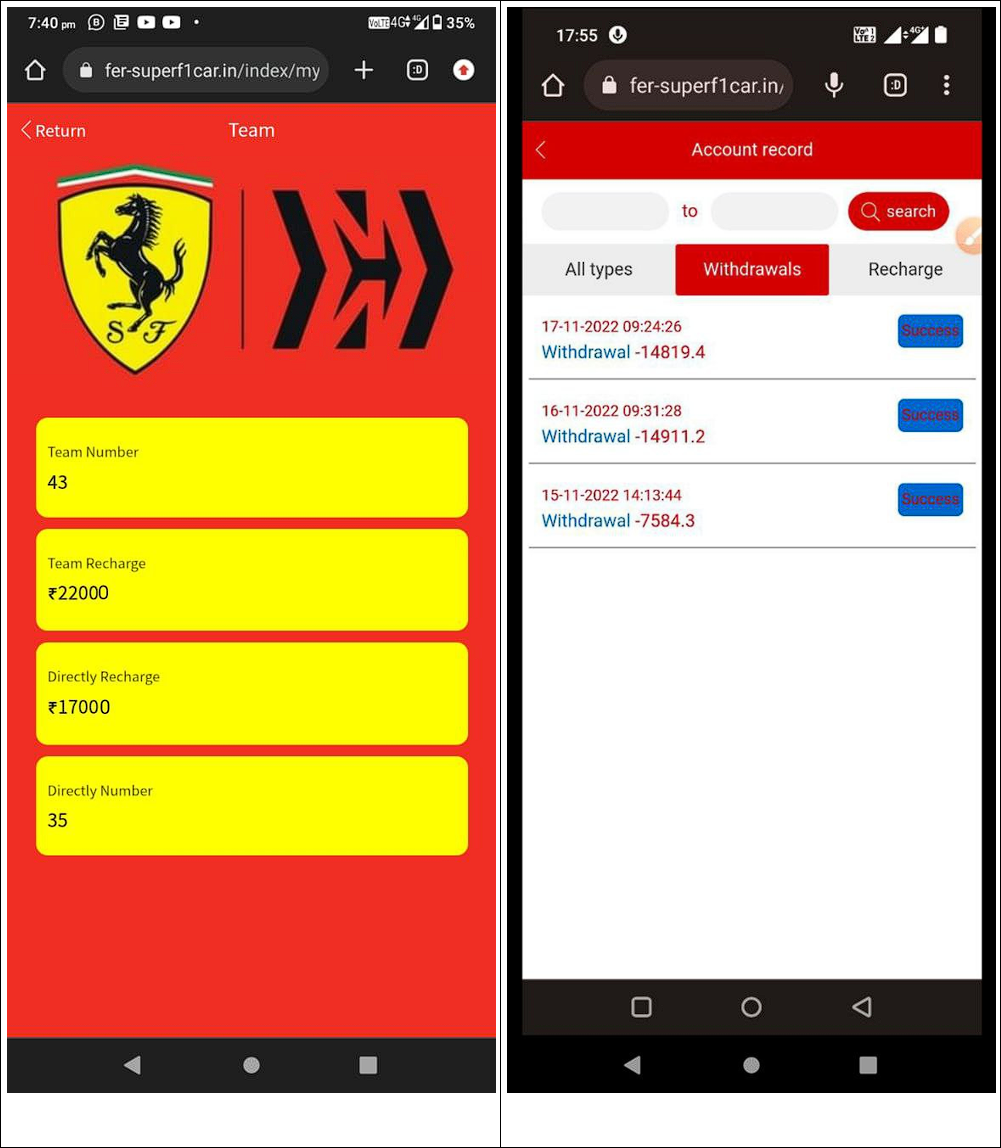
The fraudsters tricked victims to invest into non-existing products for commission:
| WHOIS Records for fer-superf1car.in | |
| Registrar Info:- |
|
| Name: | Dynadot LLC |
| Whois Server: | whois.aliyun.com |
| Referral URL: | http://www.dynadot.com |
| Status: | clientTransferProhibited |
| Important Dates:- | |
| Expires On | 2023-11-13 |
| Registered On | 2022-11-13 |
| Updated On | 2022-11-18 |
| Name Servers :- | |
| ashton.ns.cloudflare.com | 172.64.35.173 |
| june.ns.cloudflare.com | 173.245.58.176 |
GMJ Fund
The resource is also known as “GMJ Fund Power Bank”. The fraudsters use a fake certificate of incorporation from Nevada related to “GMJ Financial Holdings Limited”.
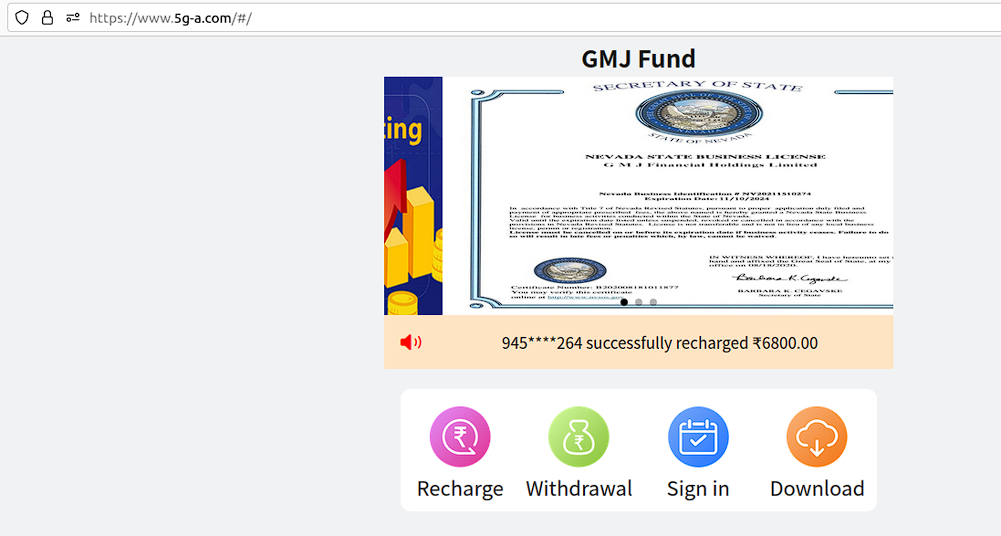
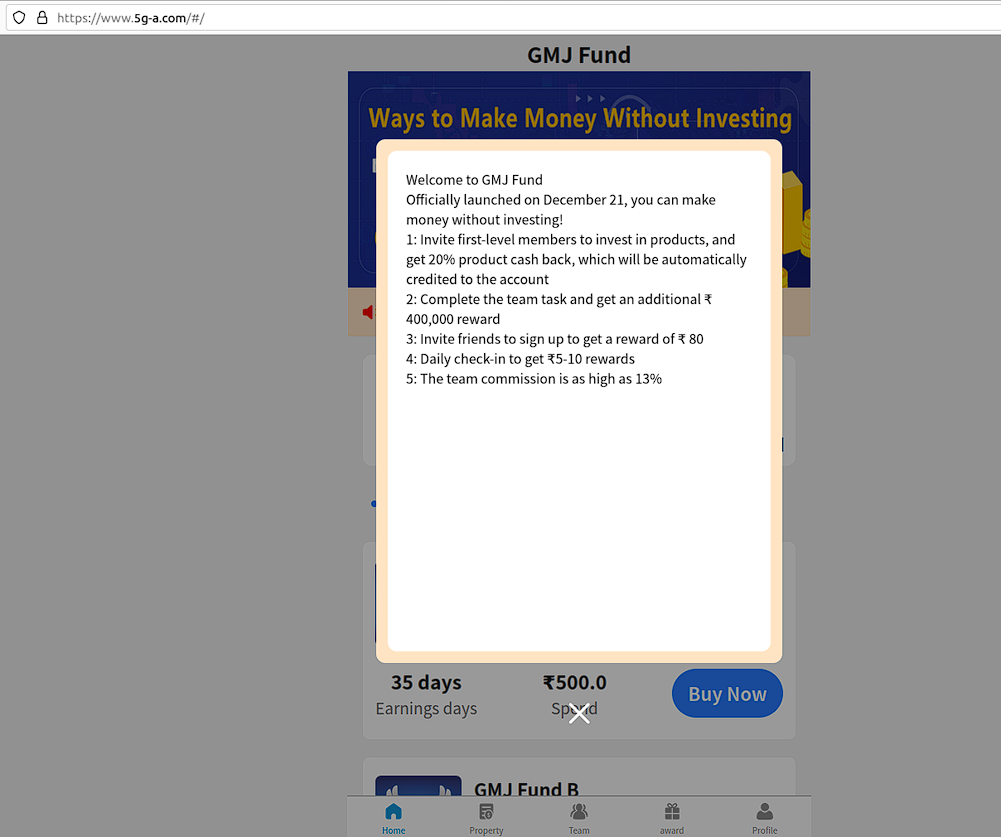
The bad actors offer various fake investment options designed to look like payment plans with fixed payout options:
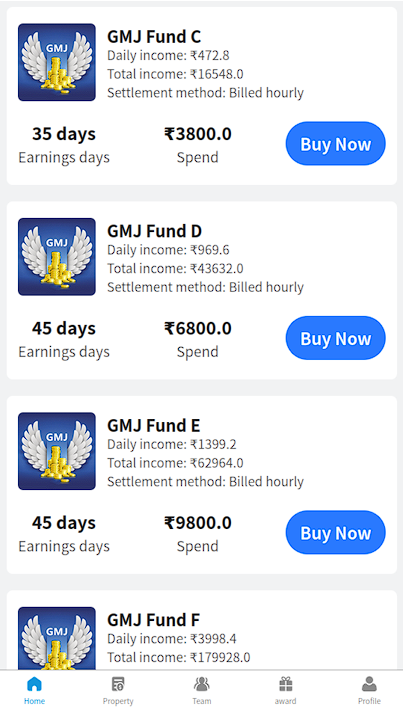
The resource also contain a URL to an Android-based mobile application which has over 10,000 downloads: https://play.google.com/store/apps/details?id=com.s1f55.af42ib
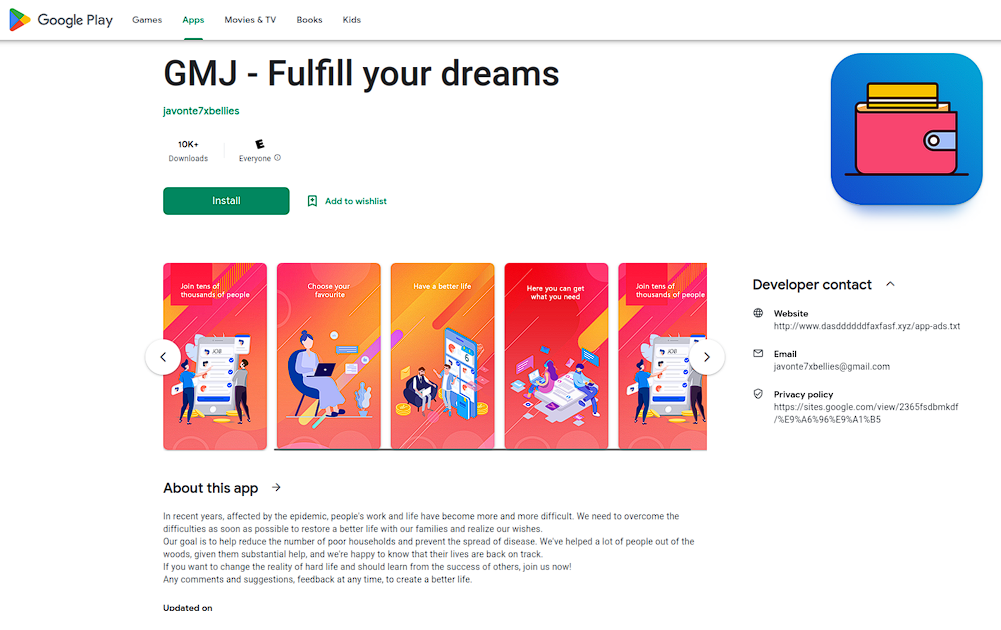
| Developer details: | javonte7xbellies@gmail.com |
| www.dasddddddfaxfasf.xyz/app-ads.txt | |
| https://sites.google.com/view/2365fsdbmkdf/%E9%A6%96%E9%A1%B5 | |
| The bad actors distribute the following invitation URL to register new victims: | https://www.5g-a.com/#/?invite_code=OUCzab0q |
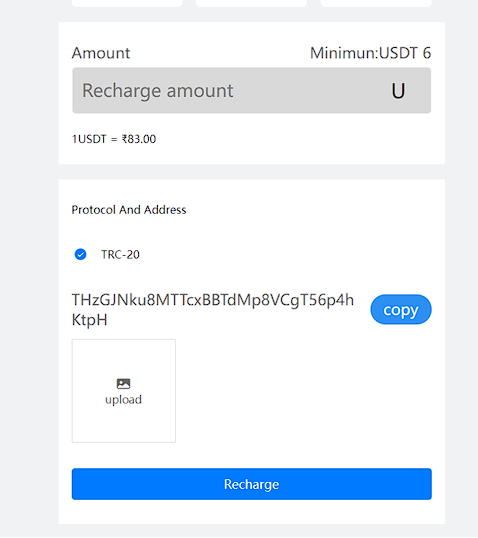
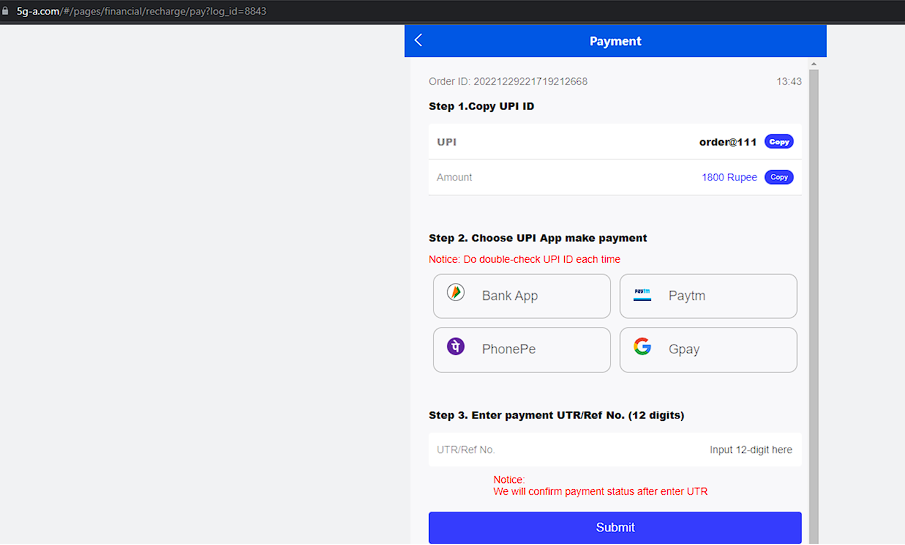
| Payment Methods: | UPI, USDT (TRC-20) |
| Payment Details: | |
| UPI ID: | order@111 |
| USDT Address (TRC-20): | THzGJNku8MTTcxBBTdMp8VCgT56p4hKtpH |
The bad actors asked their victims to make deposits via cryptocurrency:
Or alternatively, using UPI (Unified Payments Interface is an instant real-time payment system developed by National Payments Corporation of India), for e.g. to accounts like “order@111”:
| WHOIS Records for 5g-a.com | |
| Registrar Info:- |
|
| Name: | NameSilo, LLC |
| Whois Server: | whois.namesilo.com |
| Referral URL: | http://www.dynadot.com |
| Status: | clientTransferProhibited https://www.icann.org/epp#clientTransferProhibited |
| Important Dates:- | |
| Expires On | 2023-11-27 |
| Registered On | 2022-11-28 |
| Updated On | 2022-11-28 |
| Name Servers :- | |
| NS1.DNSOWL.COM | 162.159.26.136 |
| NS2.DNSOWL.COM | 162.159.27.130 |
| NS3.DNSOWL.COM | 162.159.27.98 |
ITC’s Hotel Group
The bad actors impersonate ITC Hotels Group - an Indian hotel chain, based out of Gurgaon. With over 100 hotels, it is India's fifth largest hotel chain. It is a part of the ITC Limited group of companies. It has a franchise agreement to operate most of its hotels as part of The Luxury Collection of Marriott International – https://www.itchotels.com.

| URL | http://www.hotel-income.com/index/user/register/invite_code/kuvj4.html |
| Payment Methods: | UPI |
| Payment Details: | UPI ID: gjki7375@fbl |
| hjcg57375@axisbank | |
| 777wasd@airtel (the same UPI ID was also found for Baxter Medical scam) |

| WHOIS Records for hotel-income.com | |
| Registrar Info:- | |
| Name: | DYNADOT LLC |
| Whois Server: | whois.dynadot.com |
| Referral URL: | http://www.dynadot.com |
| Status: | clientTransferProhibited |
| Important Dates:- | |
| Expires On | 2023-12-21 |
| Registered On | 2022-12-21 |
| Updated On | 2022-12-21 |
| Name Servers :- | |
| seth.ns.cloudflare.com | 172.64.33.142 |
| suzanne.ns.cloudflare.com | 172.64.34.87 |
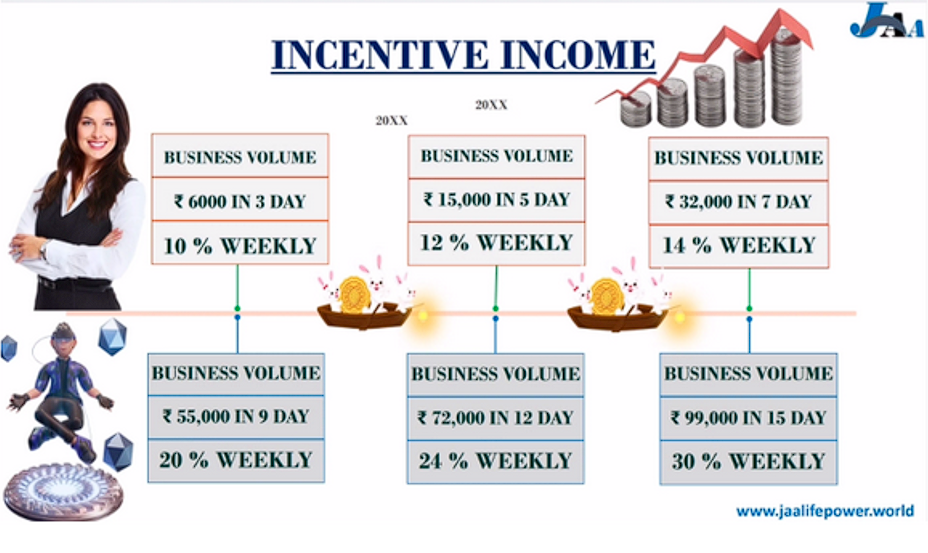
Jaalife Power
WEB-site:
http://jaalifepower.world/
The fraudsters impersonate a creative agency providing different services. In multiple sources this project is named as MLM (Pyramid Scheme) asking victims to deposit money for possible income. They ask the victim to deposit for joining as well and later invite other users.

https://freemlm.in/jaa-life-power-full-business-plan/

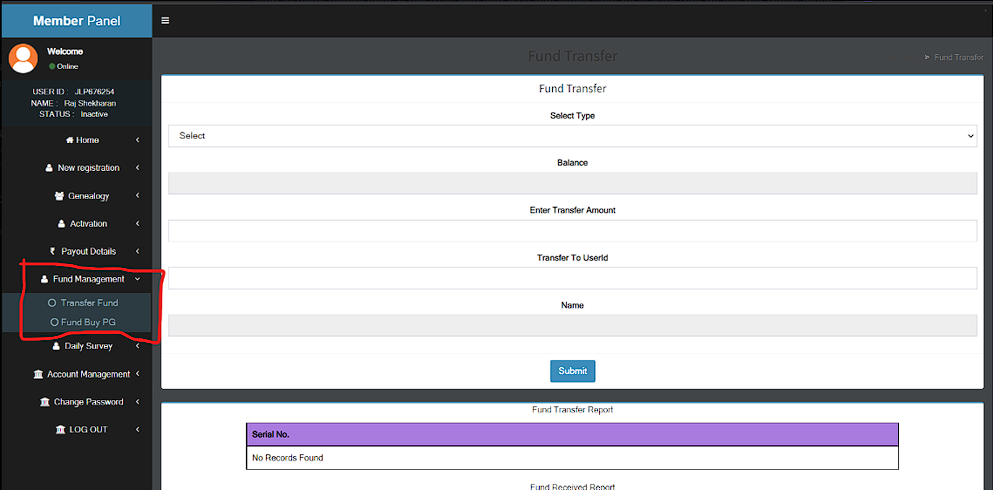
Once registered, the victim will see a panel to deposit money:
| WHOIS Records for jaalifepower.world | |
| Registrar Info:- | |
| Name: | GoDaddy.com, LLC |
| Whois Server: | whois.godaddy.com |
| Referral URL: | http://www.godaddy.com/domains/search.aspx?ci=8990 |
| Status: | clientDeleteProhibited https://icann.org/epp#clientDeleteProhibited clientRenewProhibited https://icann.org/epp#clientRenewProhibited clientTransferProhibited https://icann.org/epp#clientTransferProhibited clientUpdateProhibited https://icann.org/epp#clientUpdateProhibited |
| Important Dates:- | |
| Expires On | 2023-12-08 |
| Registered On | 2022-12-08 |
| Updated On | 2022-12-15 |
| Name Servers :- | |
| bradley.ns.cloudflare.com | 162.159.44.35 |
| tara.ns.cloudflare.com | 172.64.32.225 |
EVGo
The bad actors impersonate Evgo, an electric vehicle DC fast charging station network in the United States, with more than 850 charging locations as of August 2022. Official WEB-site: https://www.evgo.com. The company is incorporated in Los Angeles, California.

| WHOIS Records for evgoapp.com | |
| Registrar Info:- | |
| Name: | Alibaba Cloud Computing Ltd. d/b/a HiChina (www.net.cn) |
| Whois Server: | grs-whois.hichina.com |
| Referral URL: | http://wanwang.aliyun.com |
| Status: | ok https://icann.org/epp#ok |
| Important Dates:- | |
| Expires On | 2023-12-29 |
| Registered On | 2022-12-29 |
| Updated On | 2022-12-29 |
| Name Servers :- | |
| DNS17.HICHINA.COM | 39.96.153.60 |
| DNS18.HICHINA.COM | 47.118.199.198 |
Tata
The bad actors impersonate TAT, Indian multinational conglomerate headquartered in Mumbai.
URL: https://www.tatacarhire.com

| WHOIS Records for tatacarhire.com | |
| Registrar Info:- | |
| Name: | Gname.com Pte. Ltd. |
| Whois Server: | whois.gname.com |
| Referral URL: | www.gname.com |
| Status: | clientTransferProhibited https://icann.org/epp#clientTransferProhibited |
| Important Dates:- | |
| Expires On | 2024-01-01 |
| Registered On | 2023-01-01 |
| Updated On | 2023-01-01 |
| Name Servers :- | |
| DRAKE.NS.CLOUDFLARE.COM | 172.64.35.14 |
| KENIA.NS.CLOUDFLARE.COM | 162.159.38.93 |
GQG
The bad actors impersonate GQG, an independent asset management firm motivated by a commitment to broad-based employee ownership.
Official WEB-site: https://gqgpartners.com

Example:
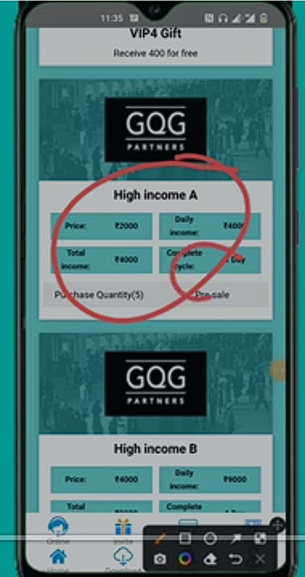
The landing page contains misleading information about investments into pre-IPO companies to earn some money (fixed income).
The bad actor published the URL with invitation code: https://www.push-plan[.]com/index/user/register/invite_code/xbo7k.html.
| WHOIS Records for push-plan.com | |
| Registrar Info:- | |
| Name: | DYNADOT LLC |
| Whois Server: | whois.dynadot.com |
| Referral URL: | http://www.dynadot.com |
| Status: | clientTransferProhibited |
| Important Dates:- | |
| Expires On | 2023-12-09 |
| Registered On | 2022-12-09 |
| Updated On | 2022-12-09 |
| Name Servers :- | |
| anuj.ns.cloudflare.com | 108.162.193.65 |
| laura.ns.cloudflare.com | 108.162.192.183 |
Novuna
The bad actors impersonate Novuna (https://www.novuna.co.uk), one of the leading UK-based financial companies.
The fraudulent app which is actively being promoted by bad actors is called Novuna (aka “Novuna Pro”). The bad actors describe it as the app for daily earning with opportunity of immediate funds withdrawal. They claim the user may request withdrawal anytime, but in fact, after the funds have been deposited – they will be never returned.Oben Electric
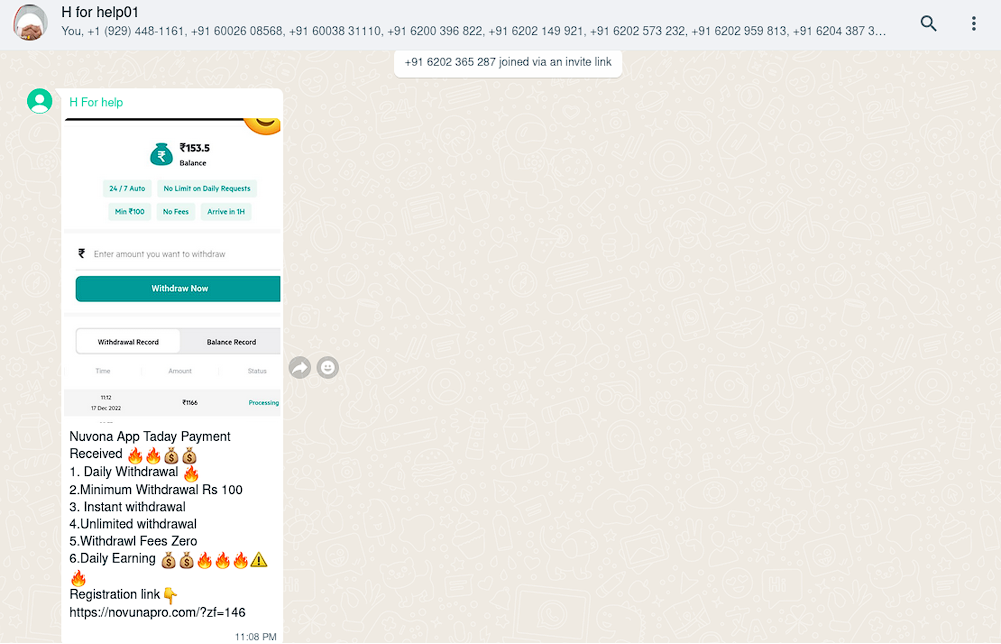
Similar to previous fake apps, the vicrtim will register via one of the invitation links such as https://novunapro[.]com/login/login/ref/146.html. Notably, in the footer of the WEB-site has a reference to Novuna Finance LTD (which we access as misleading).
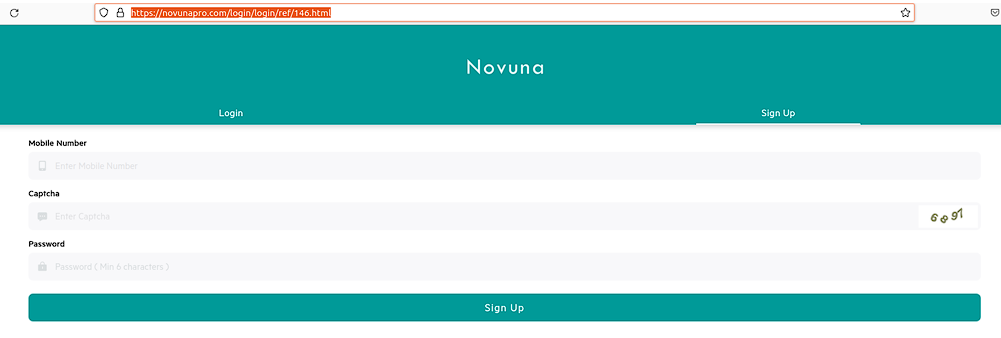
| WHOIS Records for novunapro.com | |
| Registrar Info:- |
|
| Name: | GoDaddy.com, LLC |
| Whois Server: | whois.godaddy.com |
| Referral URL: | https://www.godaddy.com/ |
| Status: | clientDeleteProhibited |
| clientRenewProhibited | |
| clientTransferProhibited | |
| clientUpdateProhibited | |
| Important Dates:- | |
| Expires On | 2023-12-07 |
| Registered On | 2022-12-08 |
| Updated On | 2022-12-26 |
| Name Servers :- | |
| ns67.domaincontrol.com | 97.74.103.44 |
| ns68.domaincontrol.com | 173.201.71.44 |
IBEF (India Brand Equity Foundation)
The bad actors impersonate India Brand Equity Foundation - a Trust established by the Department of Commerce, Ministry of Commerce and Industry, Government of India. https://www.ibef.org.

| URL | http://www.brand-fund.com/ |
| Payment Methods: | UPI |
| Payment Details: | BHARATPE09911192471@yesbankltd |
| BHARATPE09910705614@yesbankltd | |
| saienterprise438@upi | |
| ek2061@freecharge |
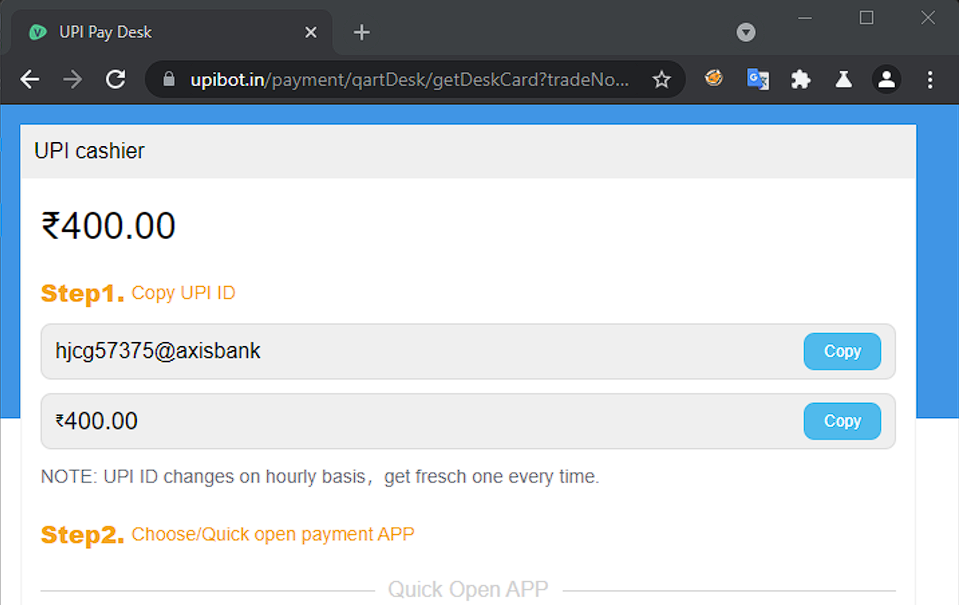
| WHOIS Records for brand-fund.com | |
| Registrar Info:- | |
| Name: | DYNADOT LLC |
| Whois Server: | whois.dynadot.com |
| Referral URL: | http://www.dynadot.com |
| Status: | clientTransferProhibited |
| Important Dates:- | |
| Expires On | 2024-01-01 |
| Registered On | 2023-01-01 |
| Updated On | 2023-01-01 |
| Name Servers :- | |
| seth.ns.cloudflare.com | 172.64.33.142 |
| suzanne.ns.cloudflare.com | 172.64.34.87 |
The scams below require registration from Indian phone number (only).
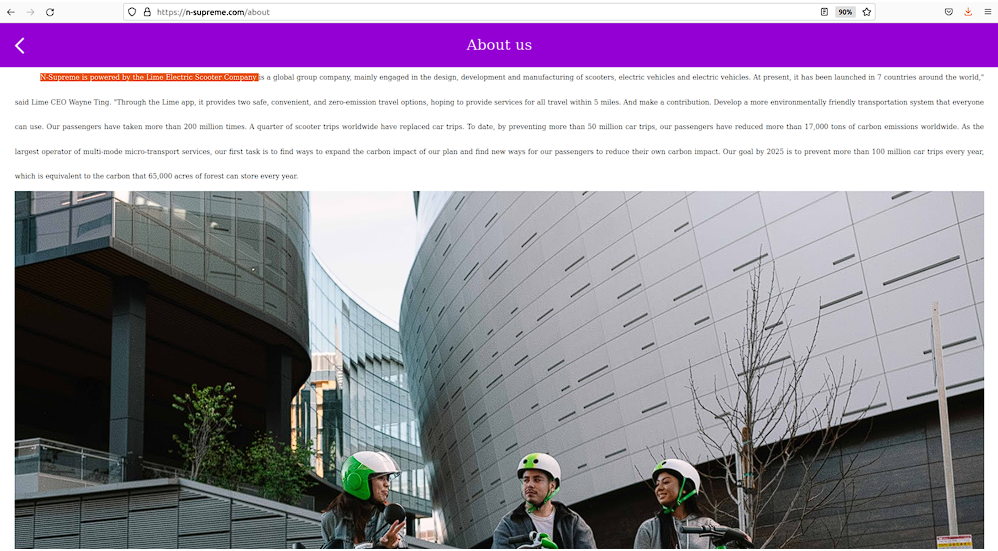
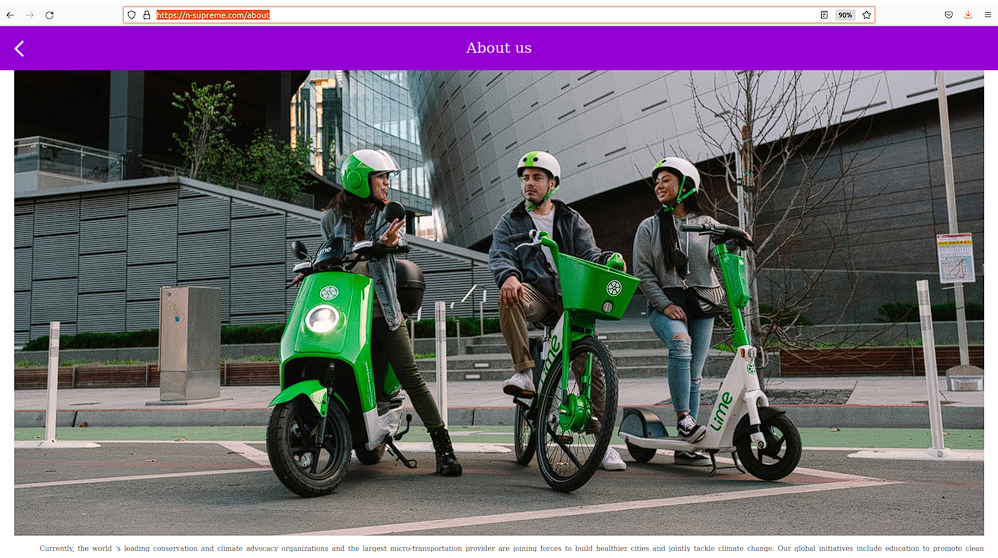
N-Supreme
The fraudulent WEB-site impersonates an “earning platform” which claims to have connections to Lime (an electric scooters company) also known as Neutron Holdings, Inc., doing business under the name Lime, formerly LimeBike, is a transportation company based in San Francisco, California.
The bad actors request payment for sign-up and then later deposit funds to earn money online.
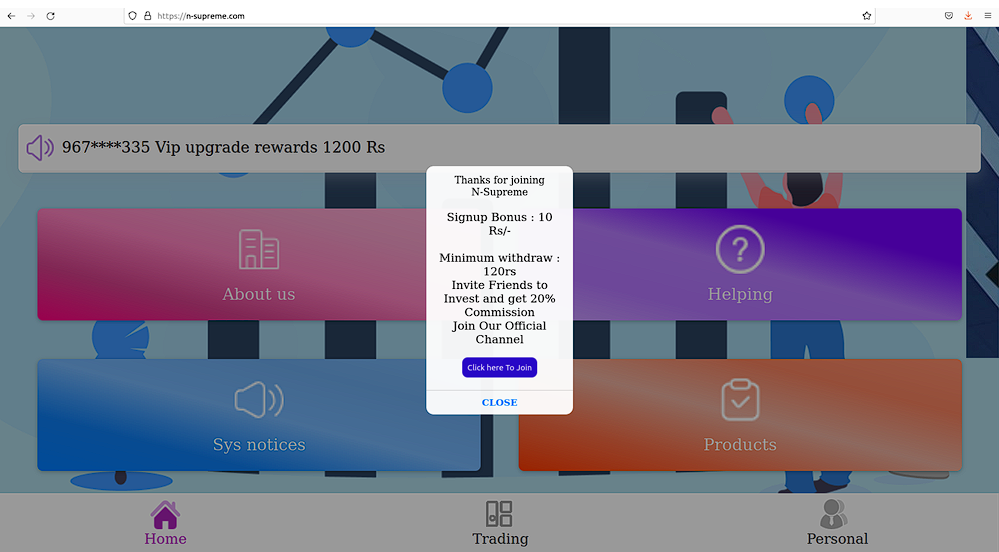
| WHOIS Records for n-supreme.com | |
| Registrar Info:- | |
| Name: | GoDaddy.com, LLC |
| Whois Server: | whois.godaddy.com |
| Referral URL: | http://www.dynadot.com |
| Status: | clientDeleteProhibited https://icann.org/epp#clientDeleteProhibited clientRenewProhibited https://icann.org/epp#clientRenewProhibited clientTransferProhibited https://icann.org/epp#clientTransferProhibited clientUpdateProhibited https://icann.org/epp#clientUpdateProhibited |
| Important Dates:- | |
| Expires On | 2023-11-15 |
| Registered On | 2022-11-15 |
| Updated On | 2023-01-04 |
| Name Servers :- | |
| NS1.SECURECLOUDDNS.NET | 3.109.90.179 |
| NS2.SECURECLOUDDNS.NET | 3.109.90.179 |
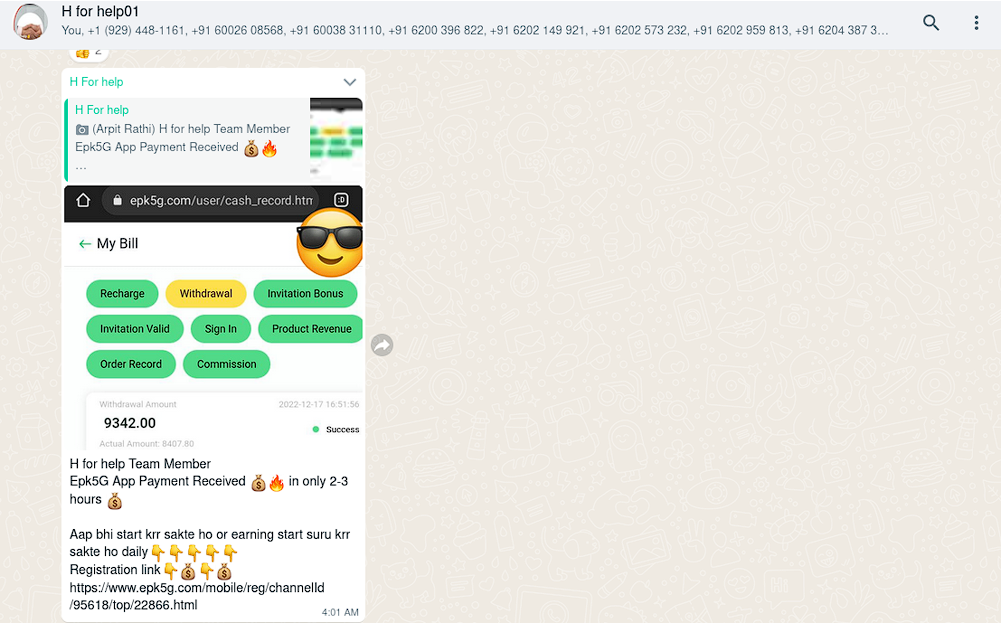
EPK5G
Another fraudulent app, EPK5G. In order to motivate victims to register, the bad actors are demonstrating fake examples where some other users got successfully paid and received their earnings from the platform. In fact, none of those payments exist.
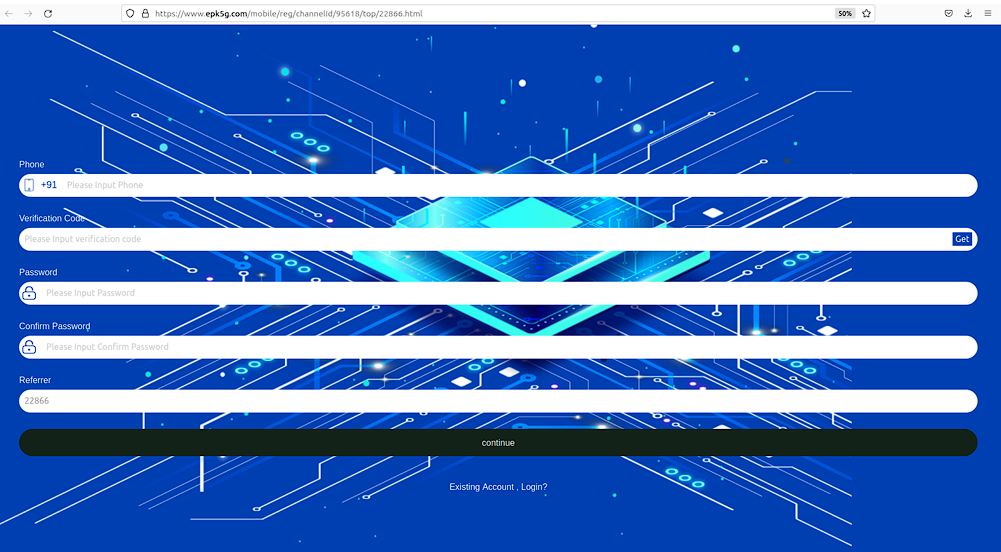
The actors use the following invitation link to register new victims, which is available only when accessing from mobile device. The landing page doesn’t have any logo or references to any other pages besides registration with pre-defined phone code (+91):
Example:
https://www.epk5g[.]com/mobile/reg/channelId/95618/top/22866.html
| WHOIS Records for epk5g.com | |
| Registrar Info:- |
|
| Name: | Amazon Registrar, Inc. |
| Whois Server: | registrar.amazon.com/whois |
| Referral URL: | amazonregistry.com/ |
| Status: | ok |
| Important Dates:- | |
| Expires On | 2023-11-12 |
| Registered On | 2022-11-12 |
| Updated On | 2022-11-12 |
| Name Servers :- | |
| ns-1401.awsdns-47.org | 205.251.197.121 |
| ns-1903.awsdns-45.co.uk | 205.251.199.111 |
| ns-266.awsdns-33.com | 205.251.193.10 |
| ns-789.awsdns-34.net | 205.251.195.21 |
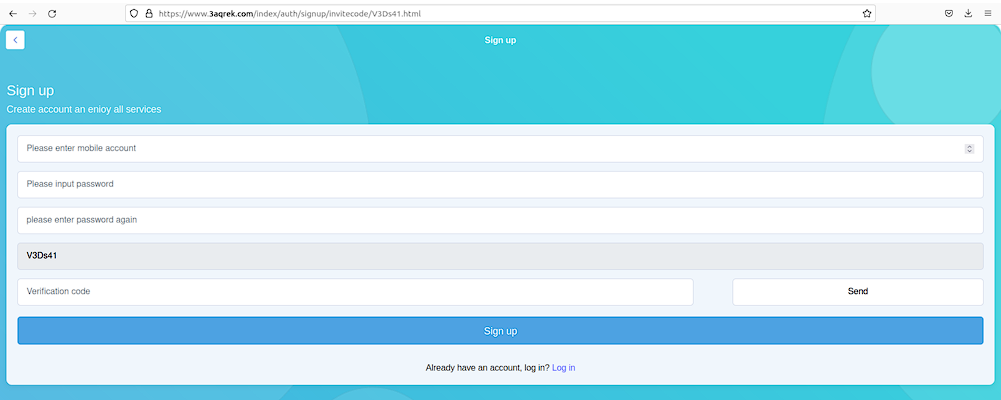
AQR
Another fraudulent app promoted by bad actors is called AQR.

Example:
https://www.3aqrek[.]com/index/auth/signup/invitecode/V3Ds41.html
| WHOIS Records for 3aqrek.com | |
| Registrar Info:- |
|
| Name: | ALIBABA.COM SINGAPORE E-COMMERCE PRIVATE LIMITED |
| Whois Server: | whois.aliyun.com |
| Referral URL: | https://www.alibabacloud.com/domain |
| Status: | ok |
| Important Dates:- | |
| Expires On | 2025-07-29 |
| Registered On | 2015-07-29 |
| Updated On | 2022-11-20 |
| Name Servers :- | |
| ns7.alidns.com | 120.76.107.47 |
ns8.alidns.com
|
120.76.107.48 |
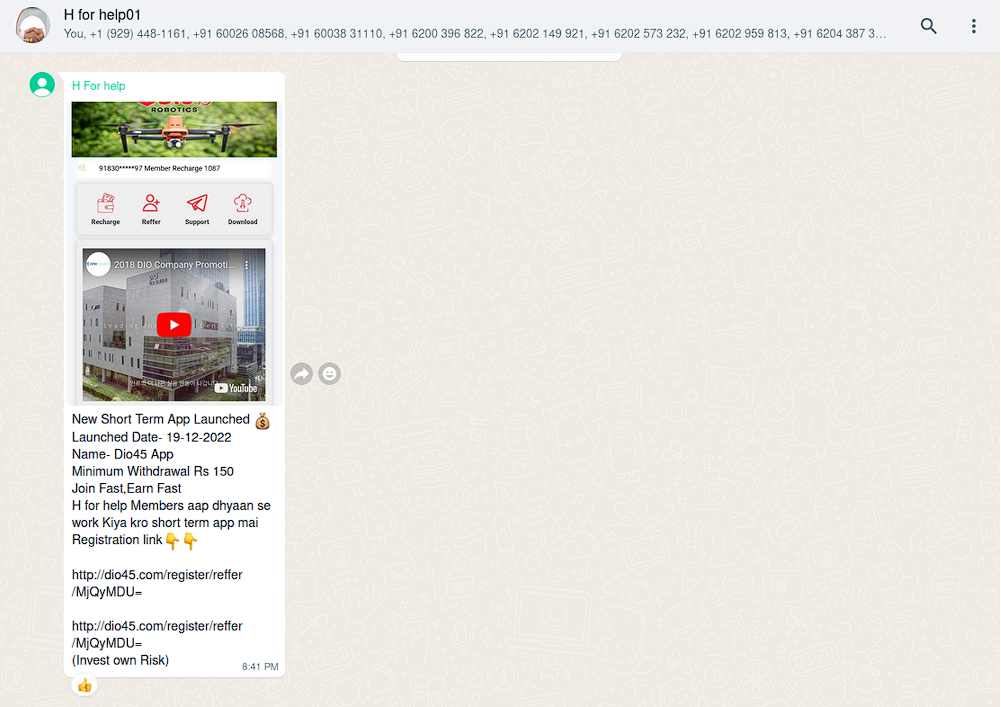
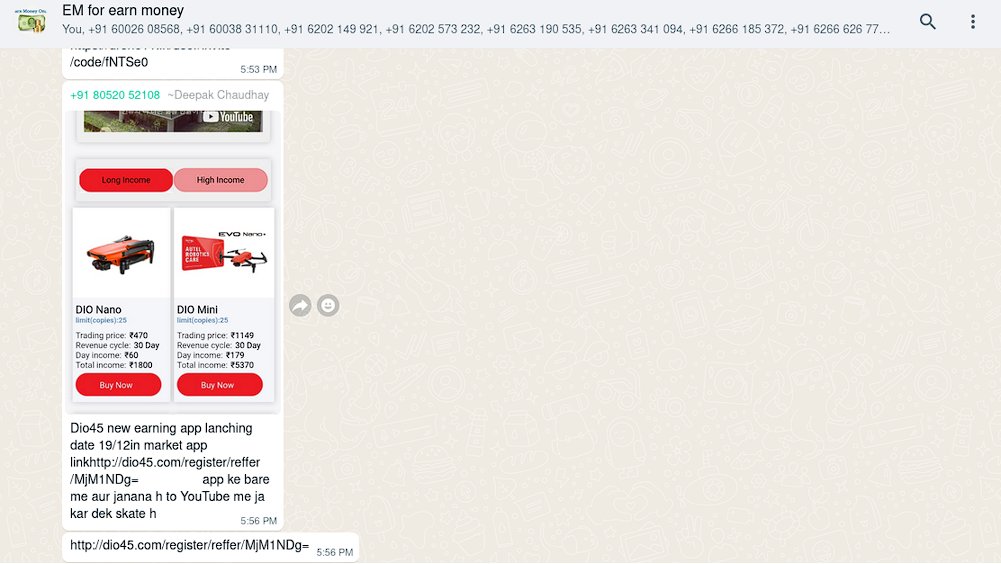
DIO45
Another fraudulent app is called DIO45:
Example:
http://dio45[.]com/register/reffer/MjQyMDU=

The same actor (Deepak Chaudhay) is posting this information:
| WHOIS Records for dio45.com | |
| Registrar Info:- |
|
| Name: | ALIBABA.COM SINGAPORE E-COMMERCE PRIVATE LIMITED |
| Whois Server: | whois.aliyun.com |
| Referral URL: | https://www.alibabacloud.com/domain |
| Status: | ok |
| Important Dates:- | |
| Expires On | 2023-12-16 |
| Registered On | 2022-12-16 |
| Updated On | 2022-12-16 |
| Name Servers :- | |
| ns7.alidns.com | 120.76.107.47 |
| ns8.alidns.com | 120.76.107.48 |
SCM
Another fraudulent app is called SCM:
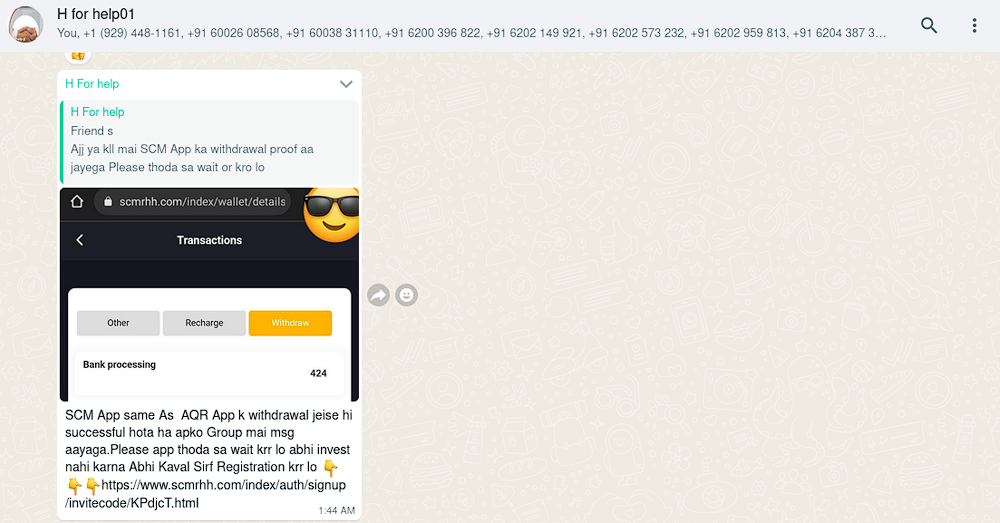
Example:
https://www.scmrhh[.]com/index/auth/signup/invitecode/KPdjcT.html
https://www.alibabacloud.com/domain
| WHOIS Records for scmrhh.com | |
| Registrar Info:- | |
| Name: | ALIBABA.COM SINGAPORE E-COMMERCE PRIVATE LIMITED |
| Whois Server: | |
| Referral URL: | amazonregistry.com |
| Status: | clientDeleteProhibited |
| clientRenewProhibited | |
| clientTransferProhibited | |
| clientUpdateProhibited | |
| Important Dates:- | |
| Expires On | 2024-08-01 |
| Registered On | 2019-08-01 |
| Updated On | 2022-12-13 |
| Name Servers :- | |
| sterling.ns.cloudflare.com | 108.162.195.143 |
| val.ns.cloudflare.com | 108.162.192.234 |
Lloyds
Another fraudulent app, Lloyds:
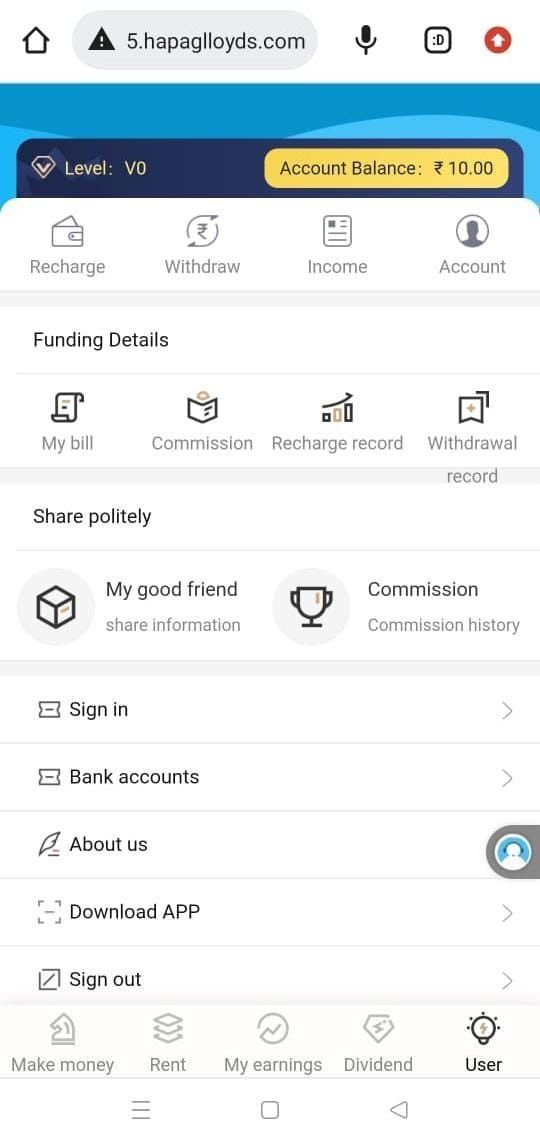
Example: http://h5.hapaglloyds[.]com/html/member/register.html?fuid=4E0Dyw
| WHOIS Records for hapaglloyds.com | |
| Registrar Info:- |
|
| Name: | GoDaddy.com, LLC |
| Whois Server: | whois.godaddy.com |
| Referral URL: | http://www.godaddy.com/domains/search.aspx |
| Status: | clientDeleteProhibited |
| clientRenewProhibited | |
| clientTransferProhibited | |
| clientUpdateProhibited | |
| Important Dates:- | |
| Expires On | 2023-11-20 |
| Registered On | 2022-11-20 |
| Updated On | 2022-11-20 |
| Name Servers :- | |
| ns33.domaincontrol.com | 120.76.107.47 |
| ns34.domaincontrol.com | 120.76.107.48 |
Dubai Central Securities Depository
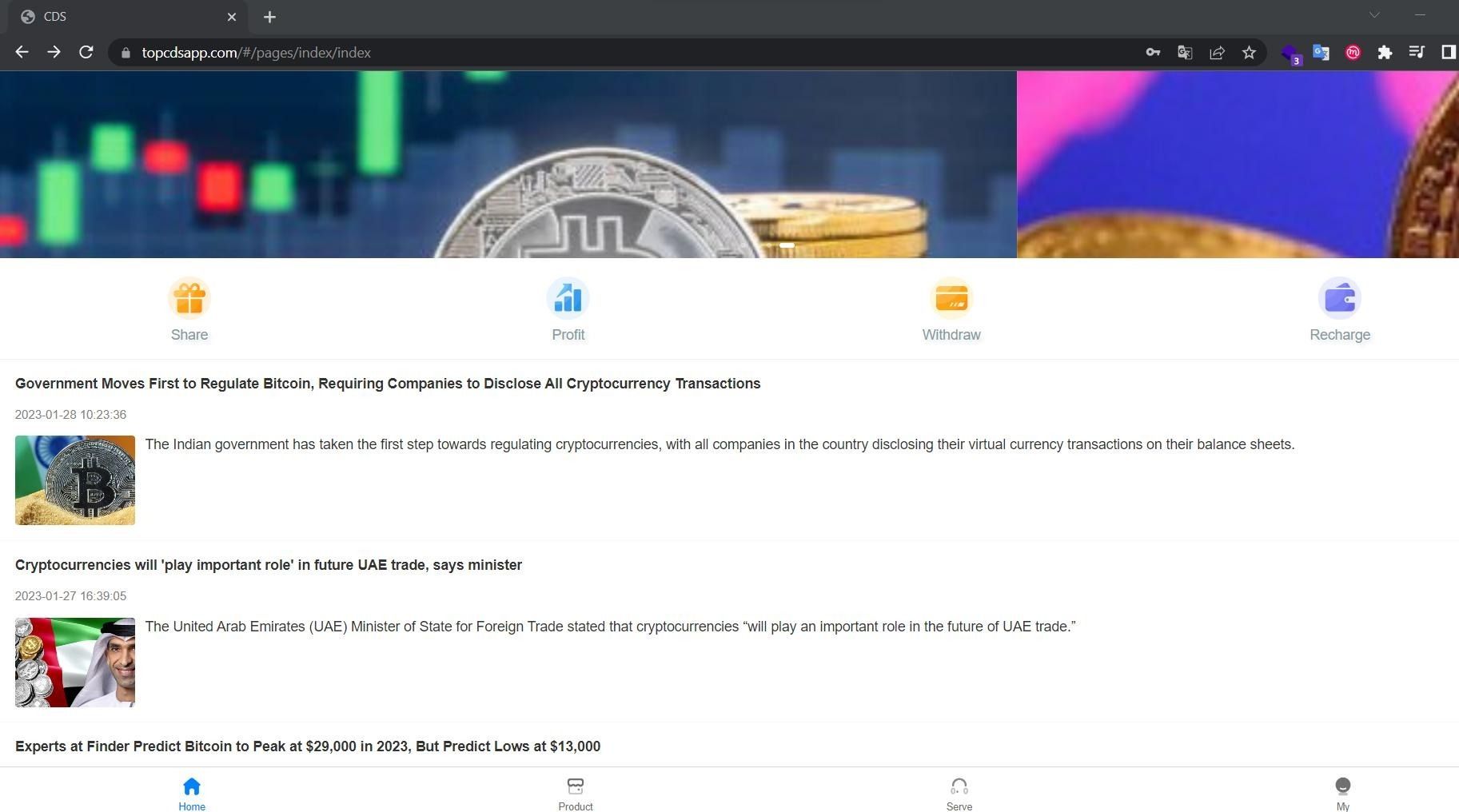
The fraud syndicate wasted no time in the first month of 2023, their latest scam launched on January 28th. Notably, this operation is impersonating the UAE government, with a focus on their minister Mr. Thani Al Zeyoudi with hopes to appear more legitimate. Their goal is to use their tactics and previous experience gathered from multiple past operations to defraud their targets in the UAE.
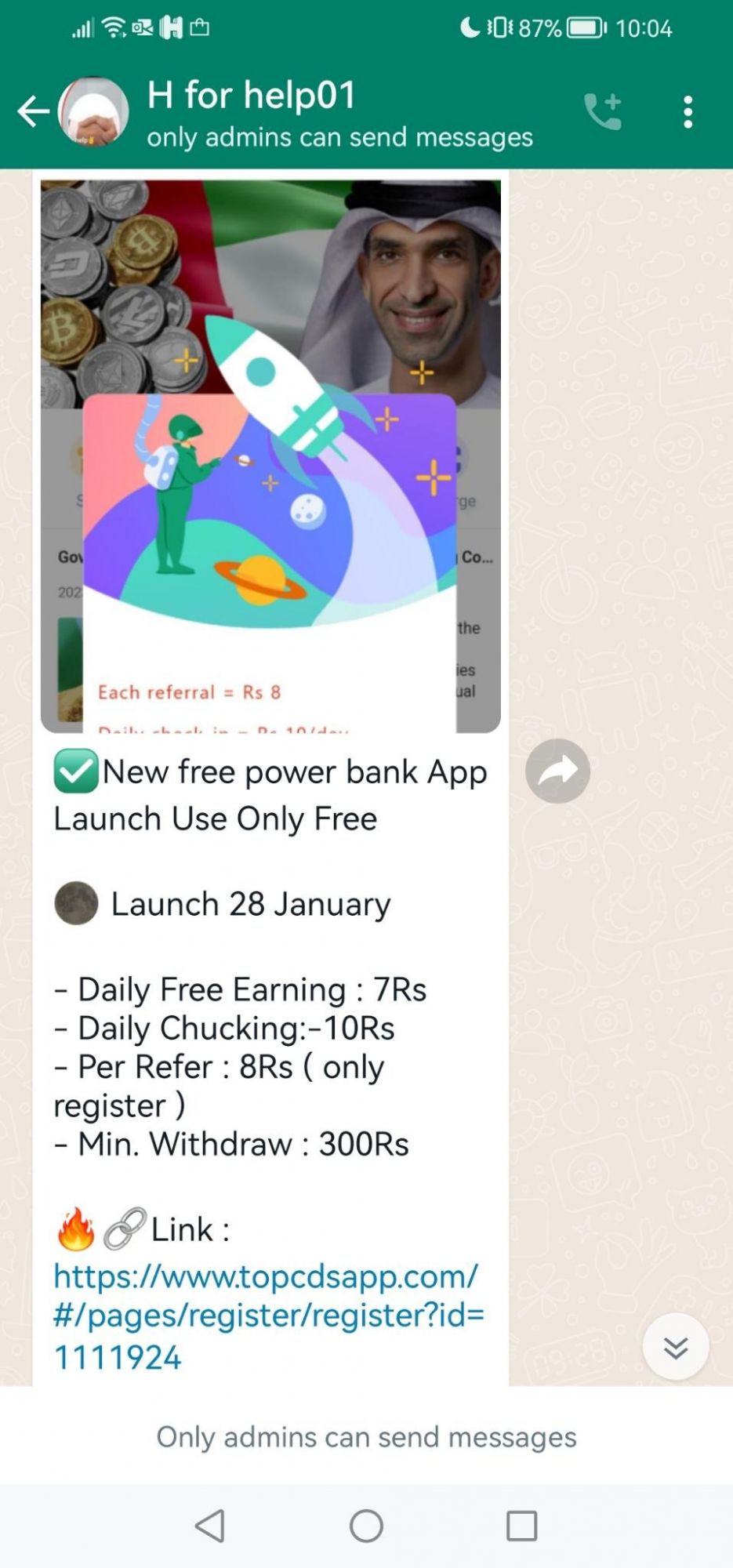
Example: https://www.topcdsapp.com/#/pages/register/register?id=1111924
| WHOIS Records for topcdsapp.com | |
| Registrar Info:- |
|
| Name: | Alibaba Cloud Computing Ltd. d/b/a HiChina (www.net.cn) |
| Whois Server: | |
| Referral URL: | www.net.cn |
| Status: | ok |
| Important Dates:- | |
| Expires On | 2024-01-27 |
| Registered On | 2023-01-27 |
| Updated On | 2023-01-27 |
| Name Servers :- | |
| andy.ns.cloudflare.com | 104.21.32.16 |
| nina.ns.cloudflare.com | 172.67.182.68 |
Caterpillar(CAT)
Following on from their previous launch, Digital Smoke expanded their operation on the 30th January, but this time impersonating the Caterpillar (CAT) company.
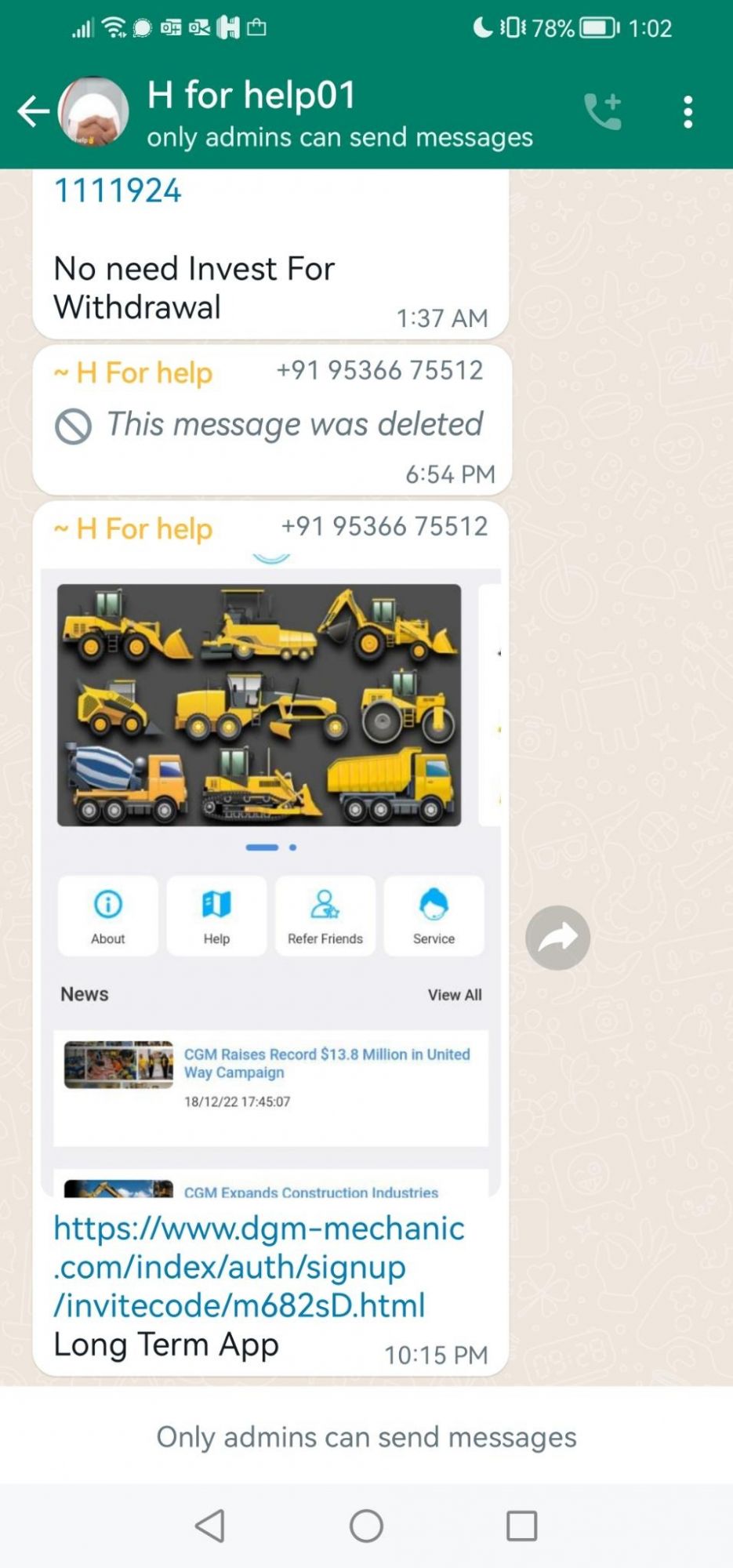
Example: https://dgm-mechanic.com/index/message/article/id/155.html
| WHOIS Records for topcdsapp.com | |
| Registrar Info:- |
|
| Name: | ALIBABA.COM SINGAPORE E-COMMERCE PRIVATE LIMITED |
| Whois Server: | grs-whois.aliyun.com |
| Referral URL: | |
| Status: | ok |
| Important Dates:- | |
| Expires On | 2024-01-27 |
| Registered On | 2023-01-27 |
| Updated On | 2023-01-27 |
| Name Servers :- | |
| ns7.alidns.com | 120.76.107.47 |
| ns8.alidns.com | 120.76.107.48 |
Danva Group
Yet another company target by the scammers, Danva Group - the Danva Group provide multiple solutions such as Real Estate, Construction, Investment & Development, Simming Pools, Restaurants, and Schools. In the screen shot below you can see the scam, it has the same format as the others above. Danva Groups official website is https://danvagroup.com/
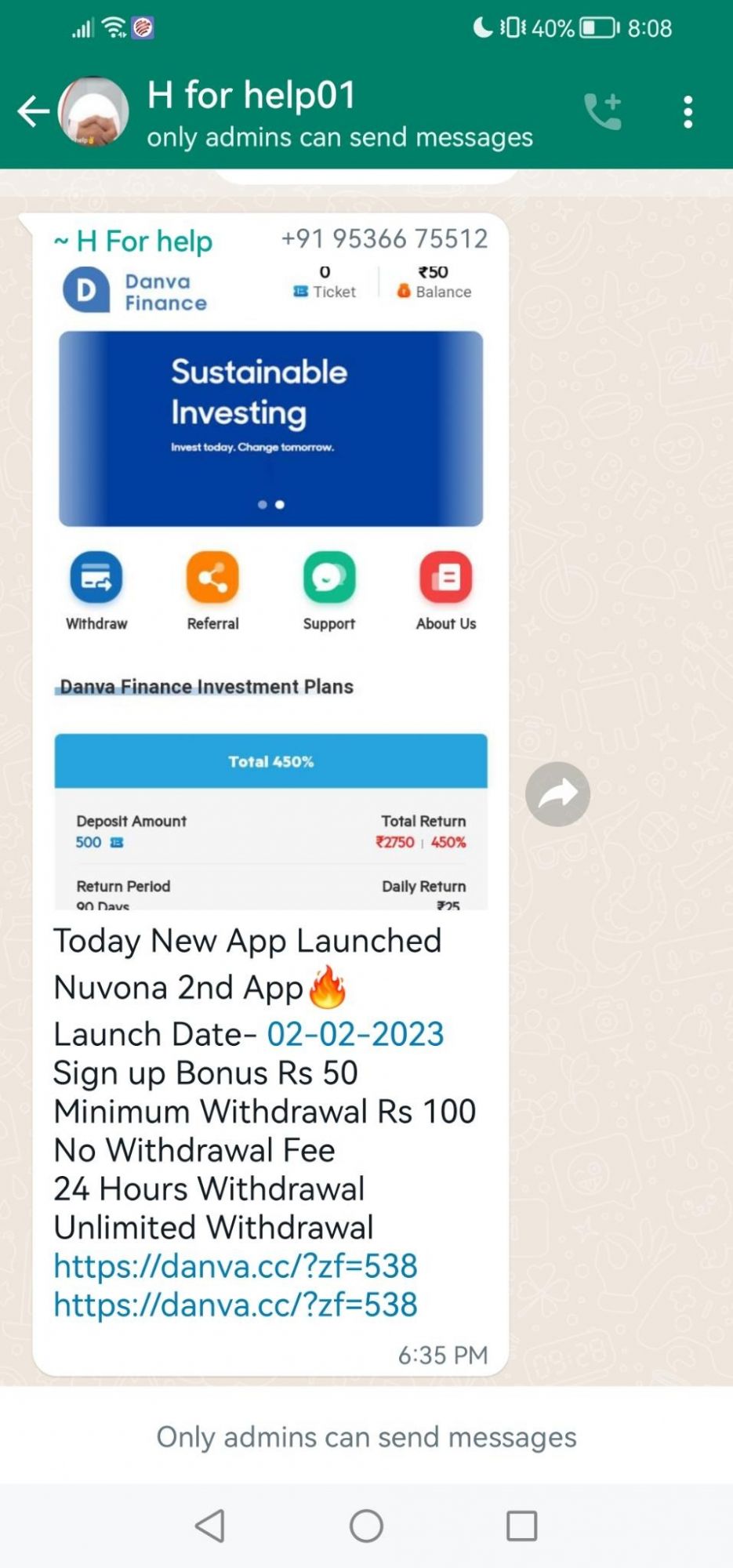
Example: https://danva.cc/
| WHOIS Records for danva.cc | |
| Registrar Info:- |
|
| Name: | ALIBABA.COM SINGAPORE E-COMMERCE PRIVATE LIMITED |
| Whois Server: | https://whois.aliyun.com/whois/whoisForm |
| Referral URL: | https://www.alibabacloud.com/domain |
| Status: | ok |
| Important Dates:- | |
| Expires On | 2024-02-01 |
| Registered On | 2023-02-01 |
| Updated On | 2023-02-01 |
| Name Servers :- | |
| collins.ns.cloudflare.com | 108.162.194.226 |
| jim.ns.cloudflare.com | 108.162.193.225 |
The Wine Group
These fraudsters are continuing to impersonate popular retailers, here is ther latest scam. This time they have taken it upon themselves to impersonate "The Wine Group", an American company founded in 1981, and based in Livermore, California.
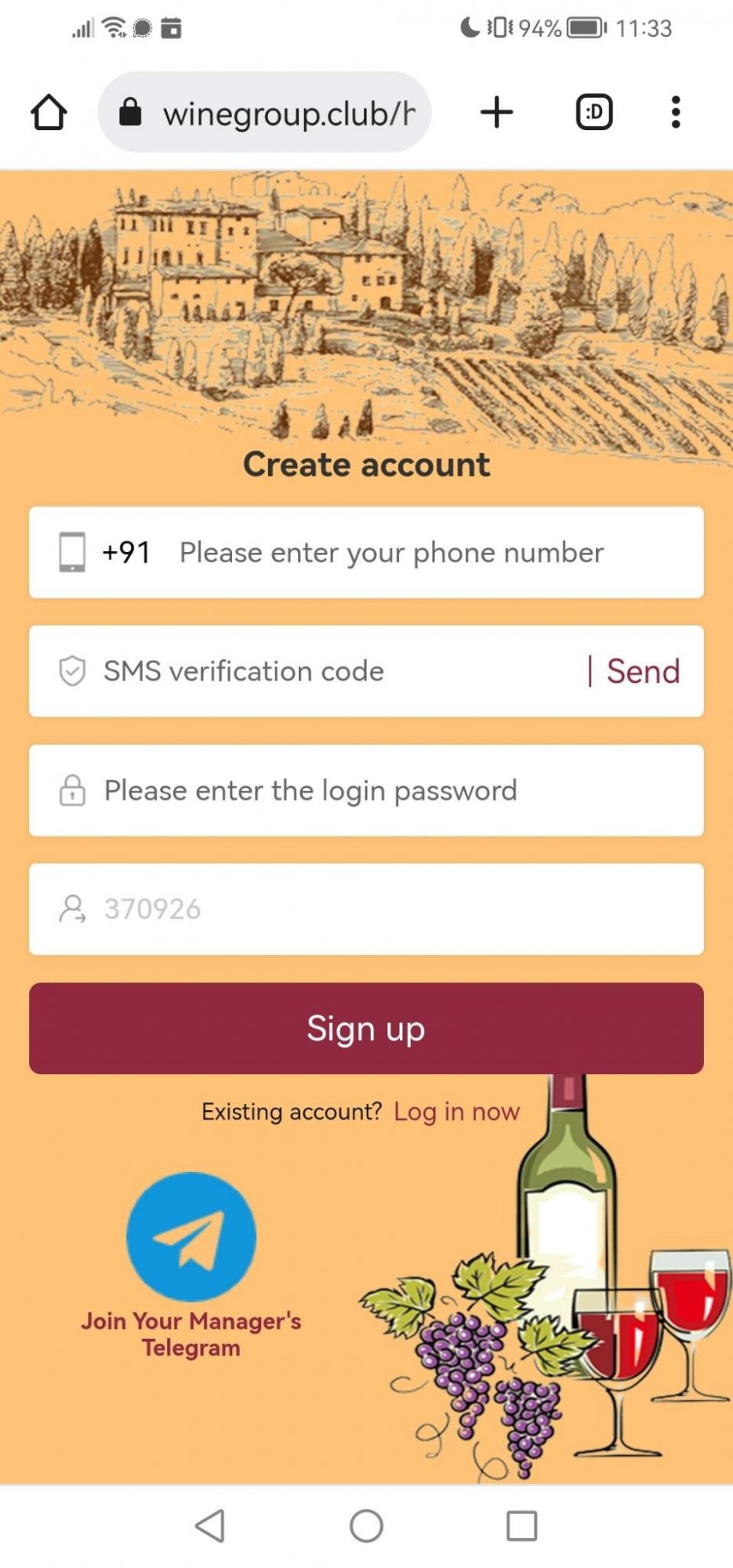
The identified Telegram group has over 9k members at the time of writing this report. The fraudsters have successfully positioned them selves in such a way, they have a members community with personal assistance being available upon request via the Telegram group.

Example: https://www.winegroup.club/h5/register?icode=370926
| WHOIS Records for winegroup.club | |
| Registrar Info:- |
|
| Name: | GoDaddy.com, LLC |
| Whois Server: | whois.godaddy.com |
| Referral URL: | https://www.godaddy.com/ |
| Status: | clientTransferProhibited |
| clientRenewProhibited | |
| clientDeleteProhibited | |
| clientUpdateProhibited | |
| Important Dates:- | |
| Expires On | 2023-12-30 |
| Registered On | 2022-12-30 |
| Updated On | 2023-01-04 |
| Name Servers :- | |
| ns07.domaincontrol.com | 97.74.103.4 |
| ns08.domaincontrol.com | 173.201.71.4 |
Cigna
The fraudsters continue their scamming, this time they impersonate a company called Cigna. Cigna is an insurance company offering insurance for a wide array of verticies.
Example: https://www.winegroup.club/h5/register?icode=370926
| WHOIS Records for winegroup.club | |
| Registrar Info:- |
|
| Name: | GoDaddy.com, LLC |
| Whois Server: | whois.godaddy.com |
| Referral URL: | https://www.godaddy.com/ |
| Status: | clientTransferProhibited |
| clientRenewProhibited | |
| clientDeleteProhibited | |
| clientUpdateProhibited | |
| Important Dates:- | |
| Expires On | 2023-12-30 |
| Registered On | 2022-12-30 |
| Updated On | 2023-01-04 |
| Name Servers :- | |
| ns07.domaincontrol.com | 97.74.103.4 |
| ns08.domaincontrol.com | 173.201.71.4 |
At this stage in our report, we would like to bring to your attention that some of the identified domains have used generic names or names with no relation to the brands they impersonate, however their scams have been designed to involve companies illegally. That being said, traditional tactics (brand protection firms scanning domains to detect those with similar spelling) used to detect them are no longer as effective as they once were, making the detection of the scams much more complicated. This is why Resecurity introduced Computer Vision to analyze images on the page thus detecting brands illegally used by threat actors without relying on the domain name and its reputation.
PPG
On the 11th Feb 2023, the syndicate expanded their operation with their impersonation of PPG Industries, Inc.. PPG is an American Fortune 500 company and global supplier of paints, coatings, and speciality materials. PPG operates in more than 70 countries around the bloge. By revenue PPG is the largest coatings company in the world.
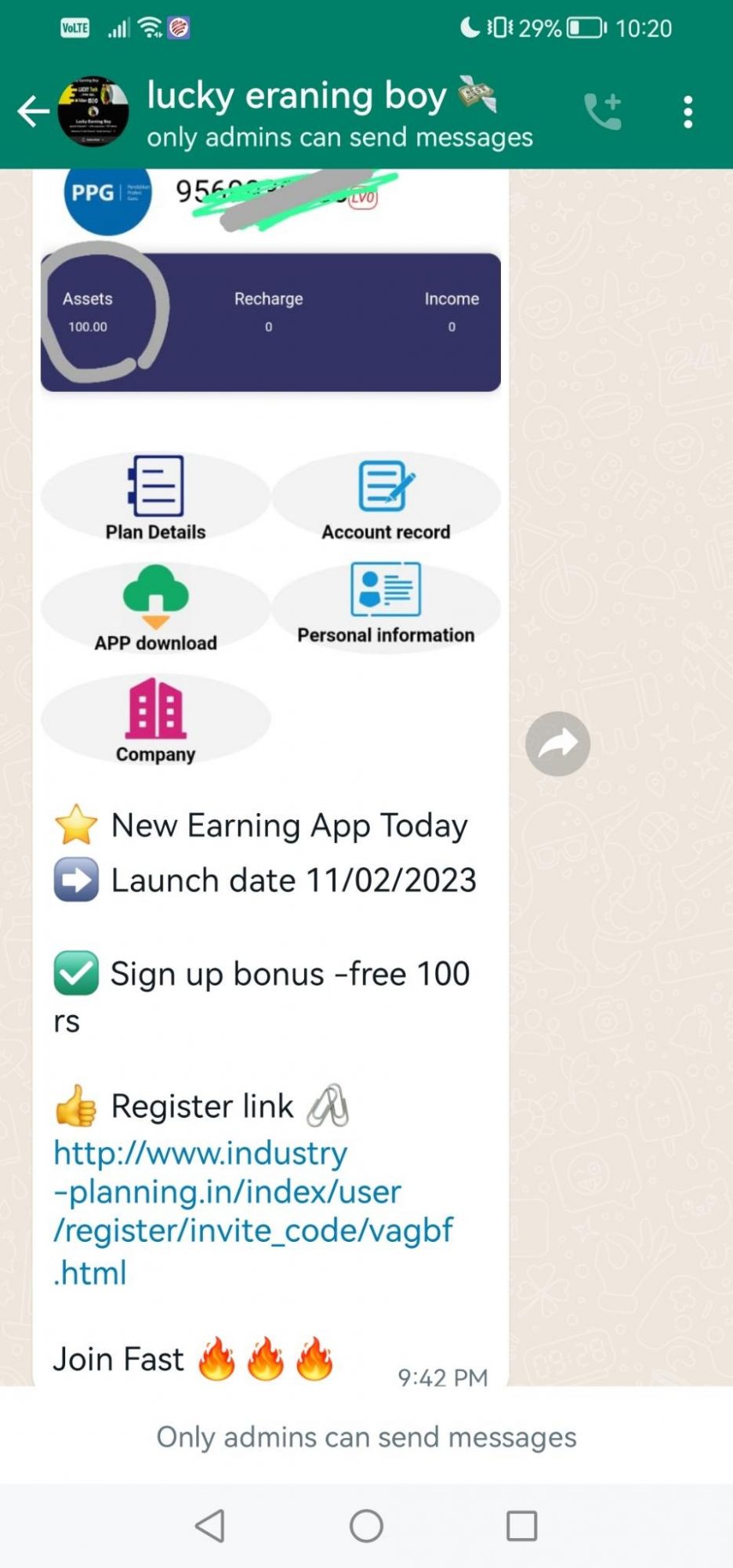
Example: https://www.industry-planning.in/index/user/register/invite_code/vagbf.html
| WHOIS Records for industry-planning.in | |
| Registrar Info:- |
|
| Name: | Dynadot LLC |
| Whois Server: | https://www.dynadot.com/domain/whois |
| Referral URL: | |
| Status: | clientTransferProhibited |
| addPeriod | |
| Important Dates:- | |
| Expires On | 2024-02-10 |
| Registered On | 2023-02-10 |
| Updated On | 2023-02-10 |
| Name Servers :- | |
| laura.ns.cloudflare.com | 08.162.192.183 |
| anuj.ns.cloudflare.com | 108.162.193.65 |
Verizon
Another scam app detected, this time impersonating Verizon - a telecommunication conglomerate based in America. Digital Smoke have used the Verizon reputation and name to enhance their scamming performance, it was launched on the 15th February 2023.
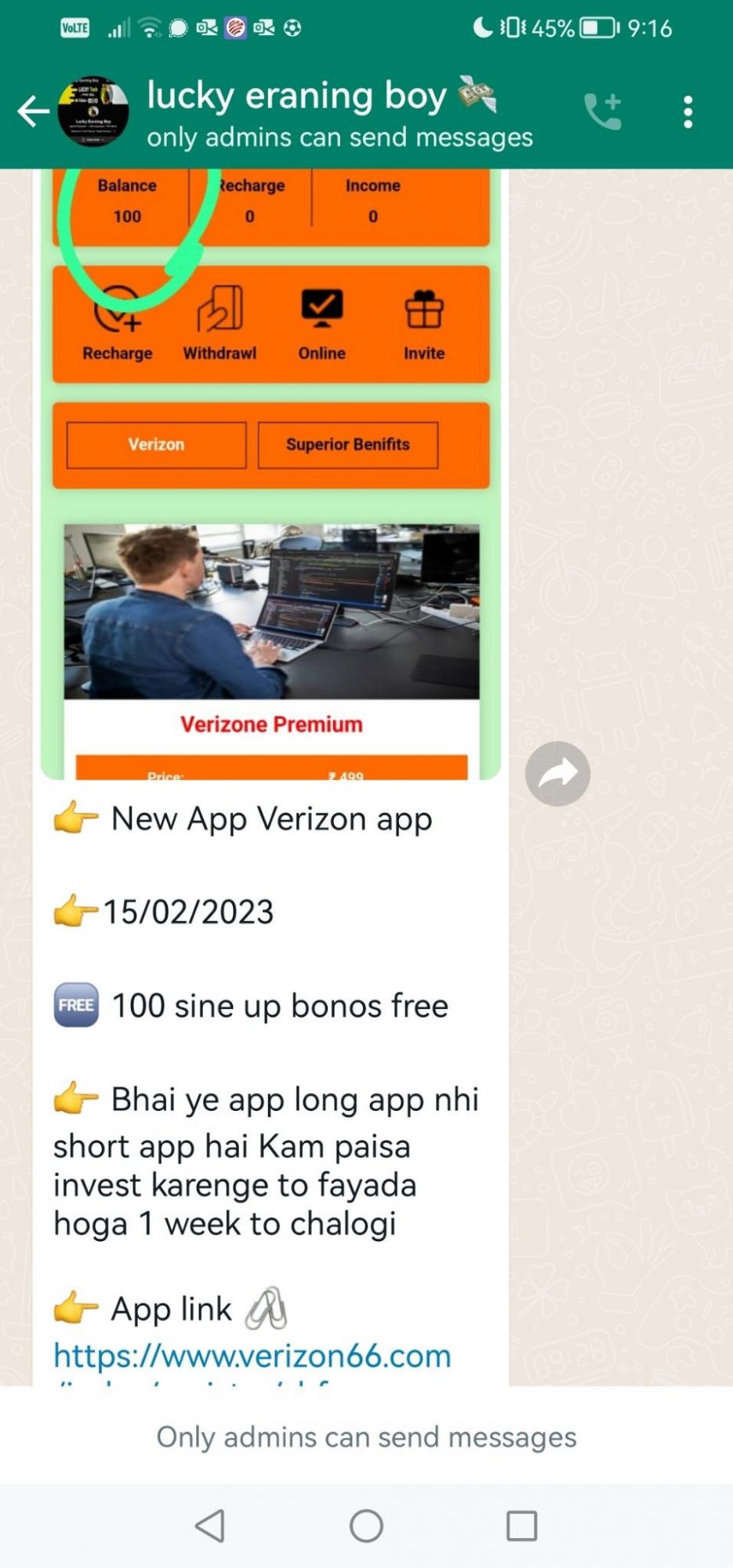
The screenshot below is of the panel the vicims are presented, we can see here how the bad actors present daily income values designed to entice their victims
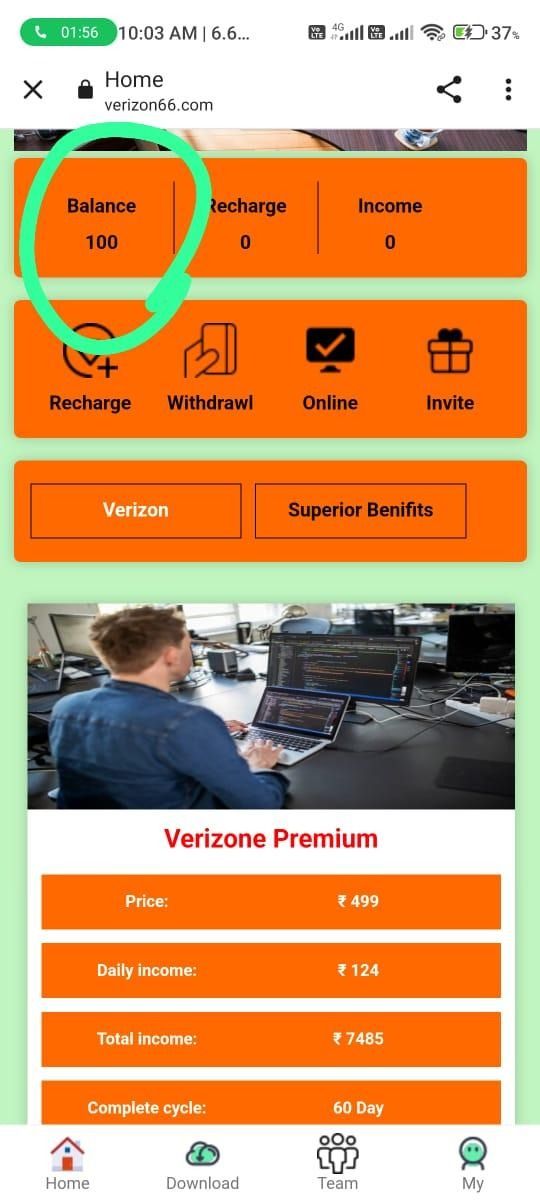
Example: https://www.verizon66[.]com/index/register/zhfcy
| WHOIS Records for verizon66.com | |
| Registrar Info:- |
|
| Name: | BigRock Solutions Ltd |
| Whois Server: | Whois.bigrock.com |
| Referral URL: | https://www.bigrock.com |
| Status: | clientTransferProhibited |
| Important Dates:- | |
| Expires On | 2023-12-14 |
| Registered On | 2022-12-14 |
| Updated On | 2022-12-22 |
| Name Servers :- | |
| ezra.ns.cloudflare.com | 108.162.195.15 |
| martha.ns.cloudflare.com | 108.162.194.142 |
Eaton
On the 27th December, 2023, Digital Smoke turned their attention to Eaton Corporation plc, an American-Irish multinational power management company with 2021 sales of $19.63 billion, founded in the United States with global headquarters in Dublin, Ireland but have multiple offices in the U.S. including EATON Aerospace
In the below screen shot we can see how the fraudsters present their "investment opportunity".
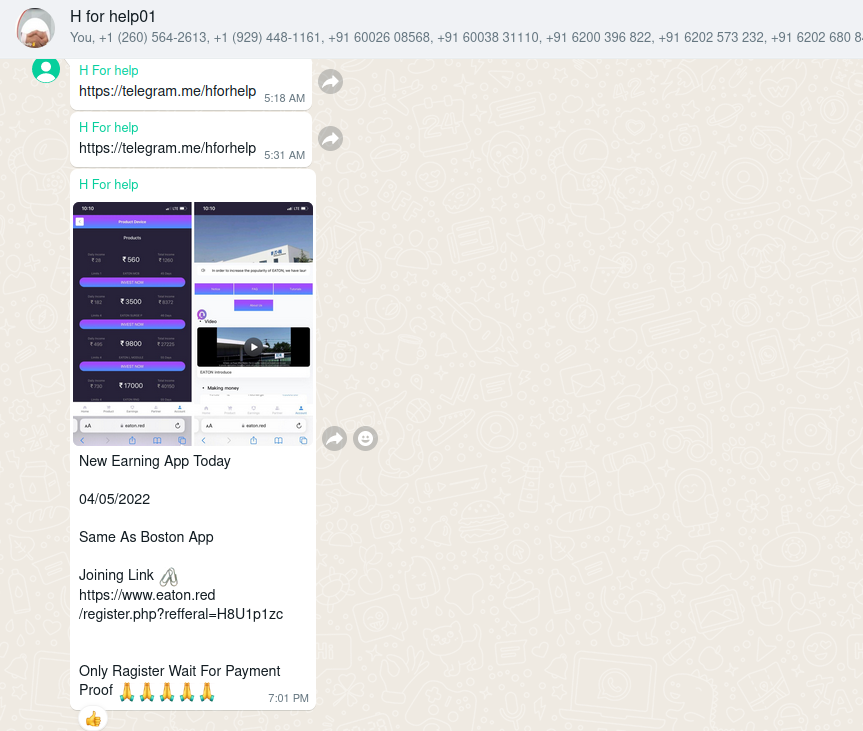
Like the other campaigns Digital Smoke has launched, the victim is spoken to via chat (in the above screenshot) and invited to join via a "refferal" link. The victim is directed to their landing page that impersonates the Eaton company, offering enticing returns on non exisiting investment opportunities, and again Digital Smoke presents them in teirs, to ensure they maximize their theft.
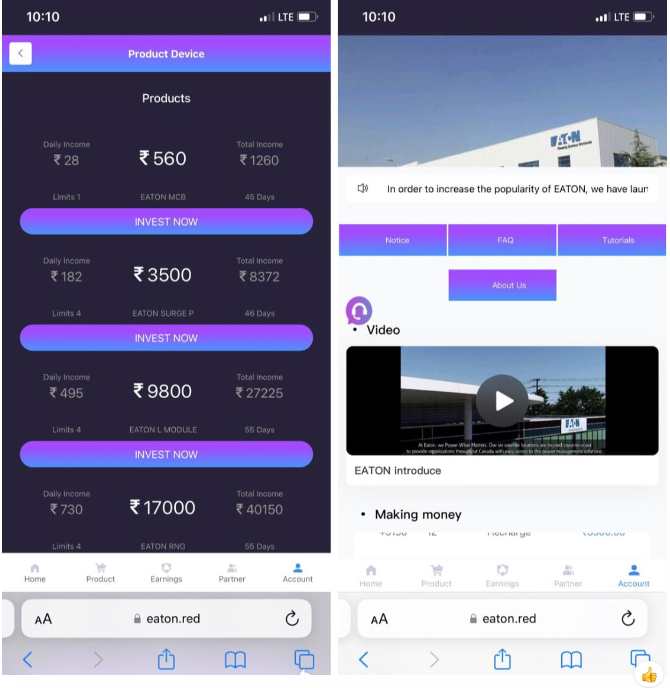
Example: https://www.eaton.red/register.php?/refferal=H8U1p1zc
| WHOIS Records for eaton.red | |
| Registrar Info:- |
|
| Name: | PDR Ltd. d/b/a PublicDomainRegistry.com |
| Whois Server: | whois.PublicDomainRegistry.com |
| Referral URL: | http://www.PublicDomainRegistry.com |
| Status: | clientTransferProhibited |
| Important Dates:- | |
| Expires On | 2023-12-27 |
| Registered On | 2022-12-27 |
| Updated On | 2023-01-01 |
| Name Servers :- | |
| andy.ns.cloudflare.com | 108.162.193.101 |
| dora.ns.cloudflare.com | 108.162.192.108 |
Oben Electric
Following on from their previous launch, Digital Smoke expanded their operation on the 30th January, but this time impersonating the Oben Electric company.
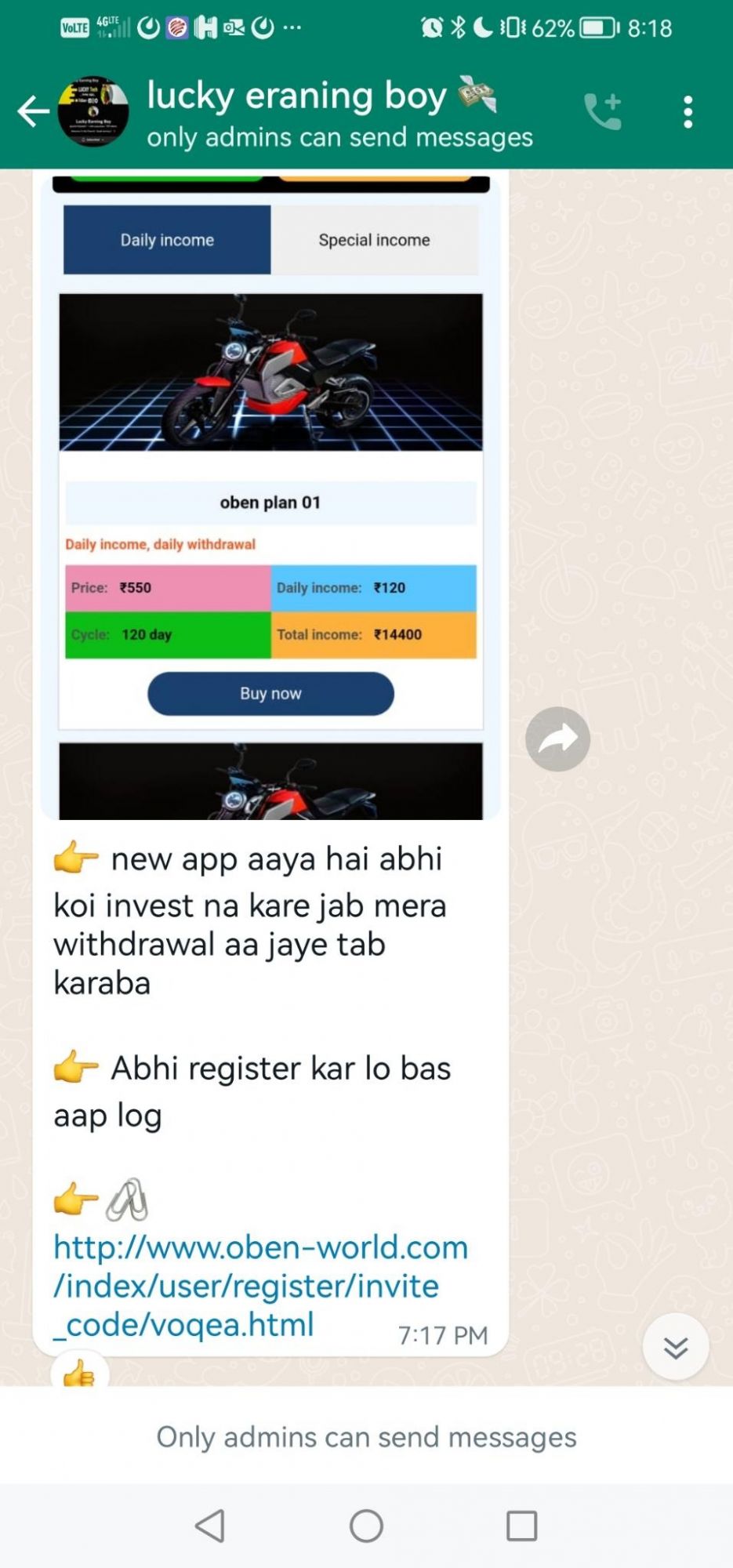
Below we can see the page presented to the victims after clicking on the linke in the above image, notice how they entice their victims with different plan tiers consisting of figures that are simply too good to be true.
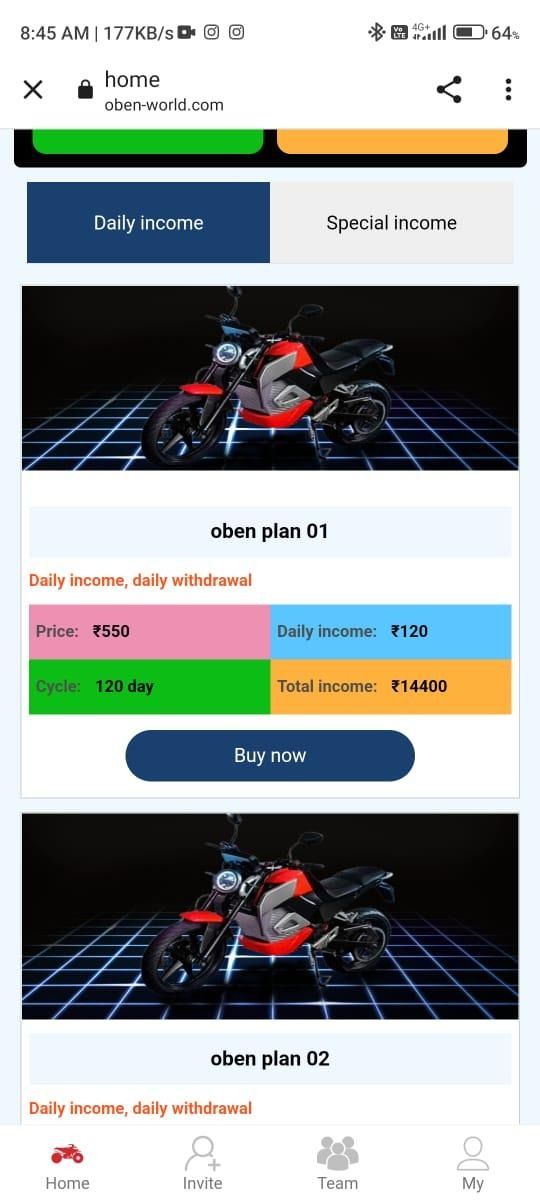
Example: http://www.oben-world.com/index/user/register/invite_code/voqea.html
| WHOIS Records for oben-world.com | |
| Registrar Info:- |
|
| Name: | DYNADOT, LLC |
| Whois Server: | whois.dynadot.com |
| Referral URL: | http://www.dynadot.com |
| Status: | clientTransferProhibited |
| Important Dates:- | |
| Expires On | 2024-02-06 |
| Registered On | 2023-02-06 |
| Updated On | 2023-02-06 |
| Name Servers :- | |
| christian.ns.cloudflare.com | 108.162.195.247 |
| stevie.ns.cloudflare.com | 108.162.194.106 |
Barclays
Digital Smoke have set their sights on Barclays from the UK, below we can see some example screenshots of what the fraudsters present and how the victims are meant to interact with their scam campaign.

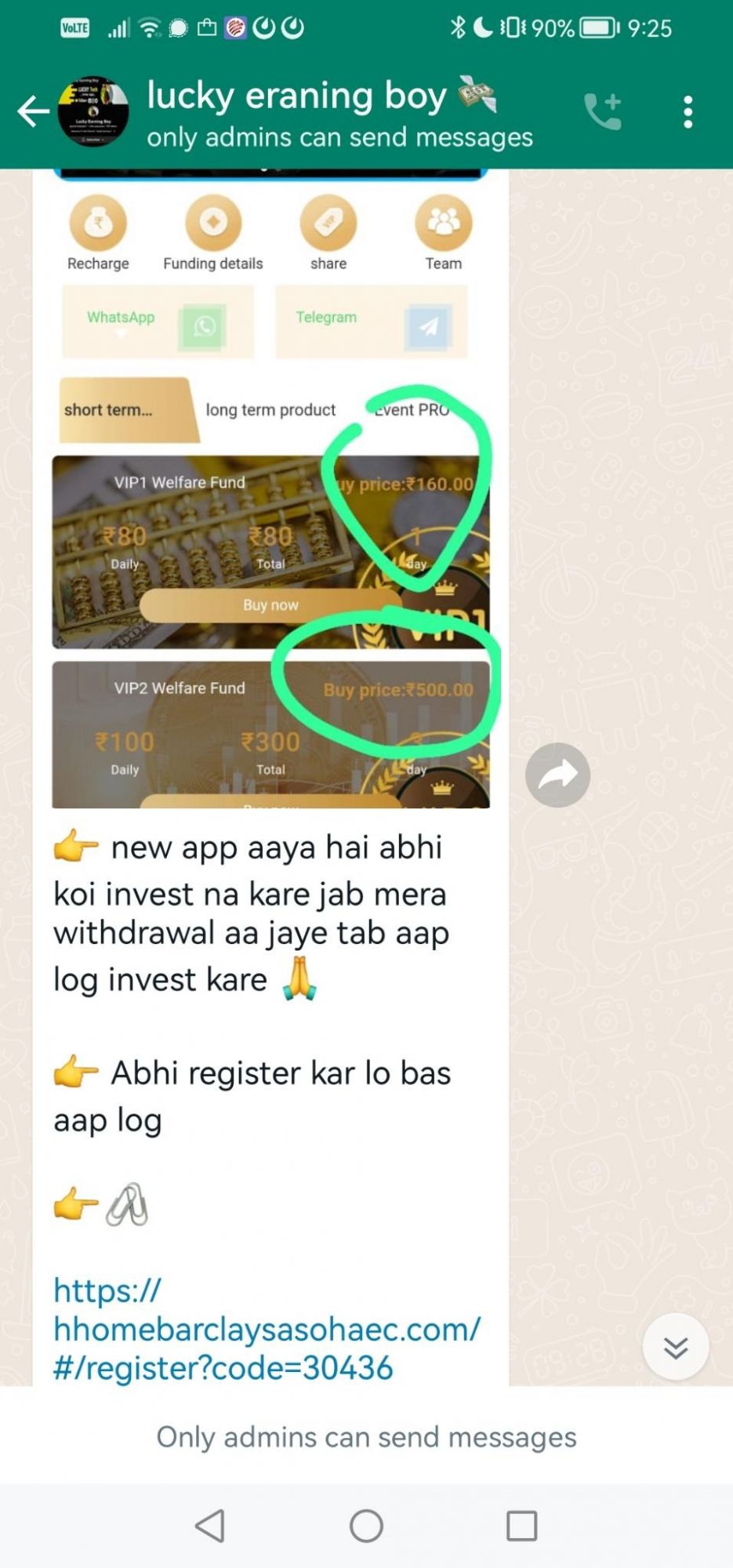
In the below screenshot, we can see the platform presented to the victims after clicking the link in the top screenshot. Once again, there are enticing fractles such tiers using the words "VIP" to help make their victims feel special / safe and "Daily" which is used to encourage the victim into progressing forward with the fraudlent investment, of course never to revcieve anything in return.
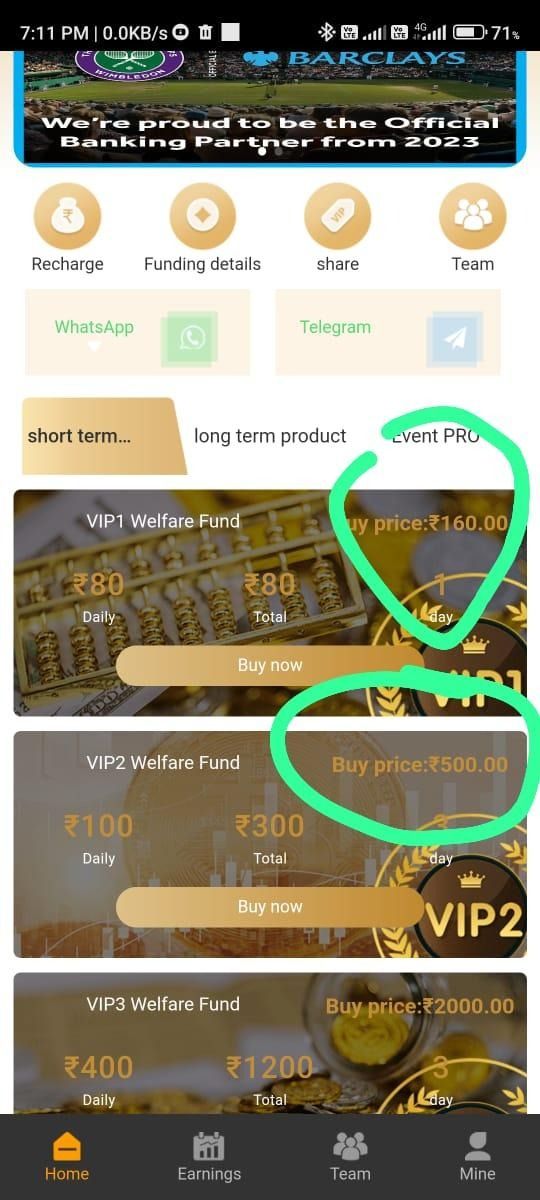
Example: https://hhomebarclaysasohaec.com/#/register?code=30436
| WHOIS Records for hhomebarclaysasohaec.com | |
| Registrar Info:- |
|
| Name: | Web Commerce Communications Limited dba WebNic.cc |
| Whois Server: | whois.webnic.cc |
| Referral URL: | http://www.webnic.cc |
| Status: | ok |
| Important Dates:- | |
| Expires On | 2024-02-16 |
| Registered On | 2023-02-16 |
| Updated On | 2023-02-16 |
| Name Servers :- | |
| ns1.hndnsv1.com | 154.38.115.217 |
| ns2.hndnsv1.com | 154.38.115.216 |
List of Companies & Domains Used by Digital Smoke
| Impersonated Companies | Domain Used | Registered On | Expires On | Updated On |
| ReNew Power | renew-powers.com | 2023-02-17 | 2024-02-17 | 2023-02-18 |
| Barclays | hhomebarclaysasohaec.com | 2023-02-16 | 2024-02-16 | 2023-02-16 |
| Shell | shellretail91.com | 2023-02-07 | 2024-02-07 | 2023-02-08 |
| DJI | svparto.com | 2023-02-03 | 2024-02-03 | 2023-02-05 |
| PPG | industry-planning.in | 2023-02-10 | 2024-02-10 | 2023-02-10 |
| Ovintiv | ovintivises.com | 2023-02-09 | 2024-02-09 | 2023-02-09 |
| Oben Electric | oben-world.com | 2023-02-06 | 2024-02-06 | 2023-02-06 |
| Danva | danva.cc | 2023-02-01 | 2024-02-01 | 2023-02-01 |
| Acwa | acwapower.in | 2023-01-28 | 2024-01-28 | 2023-02-02 |
| Dubai Central Securities Depository | topcdsapp.com | 2023-01-27 | 2024-01-27 | 2023-01-27 |
| Catapilar | topcdsapp.com | 2023-01-27 | 2024-01-27 | 2023-01-27 |
| Tata | tatacarhire.com | 2023-01-01 | 2024-01-01 | 2023-01-01 |
| IBEF | brand-fund.com | 2023-01-01 | 2024-01-01 | 2023-01-01 |
| The Wine Group | winegroup.club | 2022-12-30 | 2023-12-30 | 2023-01-04 |
| Cigna | winegroup.club | 2022-12-30 | 2023-12-30 | 2023-01-04 |
| EVGo | evgoapp.com | 2022-12-29 | 2023-12-29 | 2022-12-29 |
| Eaton | eaton.red | 2022-12-27 | 2023-12-27 | 2023-01-01 |
| Baxter Medical | baxtermedical.in | 2022-12-22 | 2023-12-22 | 2023-12-27 |
| ITC's Hotel Group | hotel-income.com | 2022-12-21 | 2023-12-21 | 2022-12-21 |
| ABRDN | abrdn.top | 2022-12-20 | 2023-12-20 | 2022-12-20 |
| BlackRock | blackrockcrp.com | 2022-12-19 | 2024-12-19 | 2022-12-19 |
| DIO45 | dio45.com | 2022-12-16 | 2023-12-16 | 2022-12-16 |
| Verizon | verizon66.com | 2022-12-14 | 2023-12-14 | 2022-12-22 |
| GQG | push-plan.com | 2022-12-09 | 2023-12-09 | 2022-12-09 |
| Jaalife Power | jaalifepower.world | 2022-12-08 | 2023-12-08 | 2022-12-15 |
| Novuna | novunapro.com | 2022-12-08 | 2023-12-07 | 2022-12-26 |
| Velesto Oil | velestonewenergy.com | 2022-11-30 | 2023-11-30 | 2022-11-30 |
| Ferrari | fer-superf1car.in | 2022-11-28 | 2023-11-27 | 2022-11-28 |
| GMJ Fund | 5g-a.com | 2022-11-27 | 2023-11-27 | 2022-12-31 |
| Lloyds | hapaglloyds.com | 2022-11-20 | 2023-11-20 | 2022-11-20 |
| LukOil | hapaglloyds.com | 2022-11-20 | 2023-11-20 | 2022-11-20 |
| N-Supreme | n-supreme.com | 2022-11-15 | 2023-11-15 | 2023-01-04 |
| EPK5G | epk5g.com | 2022-11-12 | 2023-11-12 | 2022-11-12 |
| Glencore plc | huanbaogai.cn | 2020-05-26 | 2023-05-26 | 2020-05-26 |
| SCM | scmrhh.com | 2019-08-01 | 2024-08-01 | 2022-12-13 |
| AQR | 3aqrek.com | 2015-07-29 | 2025-07-29 | 2022-11-20 |
Money Laundering in the Heart of Investment Scams
The victim should install a mobile app or is registered on the landing page to receive payment instructions. To minimize leaks, the bad actor’s issue special invitation codes and one-time URLs which remain available only for a limited period of time. These tactics help them protect their network from cybersecurity researchers and law enforcement agencies for a significant amount of time. Once the victim is registered, the automated system provides them several options for payment including UPI, AliPay and cryptocurrencies. Notably, the fraudsters primarily leveraged Card-to-Card (C2C) payments for when the victim should pay to the scammers account, other users are likely tricked by the bad actors by becoming unsuspecting money mules. Notably, most payments were in Indian rupees (by default), with option to convert currency. In some cases, the victim’s registration to the initial scam pages have been limited to Indian phone numbers only. Multiple 'money mule' accounts have been identified in course of the Digital Smoke investigation in Axis Bank, FBL, Airtel Payments Bank, Yes Bank Limited, Union Bank of India, IFDC First Bank Limited and other financial institutions.
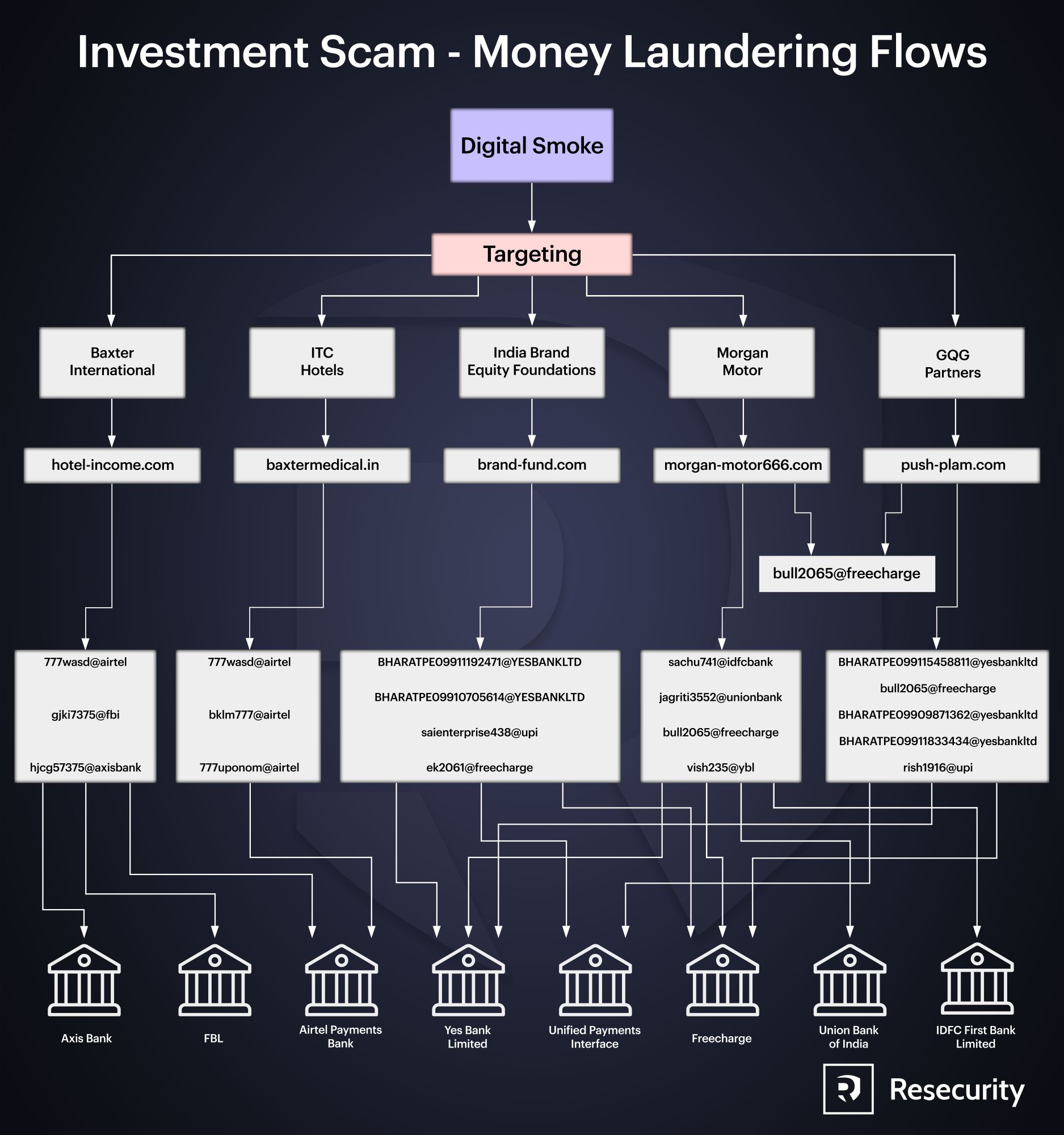
Besides the energy sector, fraudsters were especially active at impersonating well established organizations and world recognized brands of major investment corporations such as Blackrock, GMF and India Brand Equity Foundation. By abusing such large brands, the fraudsters aim to exploit people's trust and loyalty - as not many users check what or who is behind what they see online. Most of the traffic sent to the fake resources came from Whatsapp and other social media networks - which is where the fraudsters and their associates were promoting it.
Ironically, fraudsters used the disclaimer from a well-known investment program related to risks and liability, this in turn helped persuade and coach the victims into believing their scam was a legitimate investment product. Unfortunately, only after some time, angry victims in multiple countries realized they got scammed. Some of the victims interviewed by Resecurity mentioned how before they received some payouts, and because of this they never could have imagined they joined a scam network. These tactics are purposely used to coach the victims into depositing more and more funds - with each new deposit the fraudsters were also increasing the level of minimal deposit.
Significance
The Digital Smoke case is somewhat remarkable and may confirm how investment scams have now become more sophisticated than before. Fraudsters are investing large amounts of effort and time to prepare high-quality resources which look almost identical to their well-known investment product counterparts - in the case of Digital Smoke, for each investment scam they ran, they also created a separate mobile app with a unique design.
Notably, legitimate businesses who were impersonated also suffered serious damages, both reputationally and from a customer loyalty perspective - that's why an effective and ongoing brand protection system is one of the must-have solutions to minimize the negative side effects of such scams. Business leaders should consider monitoring the exposure of their brands online including but not limited to social media, mobile marketplaces, and instant messaging services.
Digital Smoke has clearly demonstrated how bad actors leverage cross-border payments and various jurisdictions to complicate further investigation and identification of victims. The investment fraudsters leverage this weakness to blur the origin of the activity as well as distribute payment flows by multiple merchants and money mules located in different countries.
Based on the arranged communications with law enforcement, the complexity was highlighted while responding to such incidents in a timely manner which also complicated the recovery of stolen funds. This process requires strong international collaboration by law enforcement, financial institutions, and the private sector where Resecurity applies significant contributions by providing actionable intelligence and criminal referrals to support further investigation.
How To Report Investment Fraud Checklist
Reporting an investment fraud case to law enforcement is important to begin the recovery process, ensure the responsible parties are investigated, which in turn will help prevent further damage to other individuals.
Local Law Enforcement — Contact any local law enforcement office to file a police report.
District Attorney — Contact your local District Attorney's Office.
Attorney General — Contact your state's Attorney General's Consumer Protection unit and the prosecution unit to report the fraud.
Federal Law Enforcement — Contact your local FBI Field Office or submit an online tip at http://tips.fbi.gov.
Here are a few steps to get you started on the right path.
1. Create an investment fraud file. Start by collecting all relevant documentation concerning the fraud in one file that's kept in a secure location. The file should include a contact sheet of the perpetrator's name, mail and email addresses, telephone numbers and website address. Also include the fraudster's purported regulatory registration numbers, if they were provided to you, and a timeline of events, which may span many years. Your file should include the police report, if any, and any call notes or relevant documentation about the fraud. And add one more important piece of information: your most recent credit report from all three credit reporting companies.
2. Know your rights. Federal and, in some cases, state law give rights to victims of crime. Learn about your rights to better protect yourself. On the federal level, the U.S. Department of Justice (DOJ) provides information on victim rights and financial fraud. In addition, check out the DOJ's Office for Victims of Crime's (OVC) brochure, What You Can Do If You Are a Victim of Crime, which provides an overview of crime victim rights, and where you can get help.
On the state level, check with your state Attorney General, whose contact information is available at www.naag.org.The North American Securities Administrators Association publishes a helpful “Investor Bill of Rights.”
3. Report fraud to regulators. National, federal and state regulatory agencies for investment products and professionals may be able to help. You may benefit from reporting the investment fraud to as many agencies as apply.
- U.S. Securities and Exchange Commission: (800) SEC-0330 or file a complaint.
- FINRA: (844) 57-HELPS or file a tip.
- North American Securities Administrators Association: (202) 737-0900 or www.nasaa.org.
- National Association of Insurance Commissioners: report fraud or file a complaint to your state Commissioner.
- National Futures Association: (312) 781-1467 or file a complaint.
- U.S. Commodity Futures Trading Commission: (866) 366-2382 or file a tip or complaint.
- Internet Crime Complaint Center (a partnership between the FBI and the National White Collar Crime Center): www.ic3.gov.
It may also be helpful to file a report with the Federal Trade Commission (FTC), by contacting the FTC's Complaint Assistant at: (877) FTC-HELP or go to https://reportfraud.ftc.gov/. Lodging a complaint will enter the fraud into the Consumer Sentinel Network so that law enforcement can stop ongoing fraud and track these crimes. This process, however, will not initiate a criminal investigation of your case.
4. Report the fraud to law enforcement. Reporting the investment fraud to law enforcement is important to begin the recovery process, ensure the responsible parties are investigated, and prevent further damage to other individuals.
- Local Law Enforcement—Contact any local law enforcement office to file a police report.
- District Attorney—Contact your local District Attorney's Office.
- Attorney General—Contact your state's Attorney General's Consumer Protection unit and the prosecution unit to report the fraud.
- Federal Law Enforcement—Contact your local FBI Field Office or submit an online tip at http://tips.fbi.gov.
5. Consider your options. It can be difficult to recover assets lost to fraud or other scenarios in which an investor has experienced a problem with an investment. But there are legitimate ways to attempt recovery (you must be logged in to view this page). In most cases, you can do so on your own—at little or no cost.
6. Follow Up. Review the steps you've taken and follow up after 30 days with any law enforcement agencies or organizations that serve victims.
Here's a final sobering reality. If you have been already been a victim of investment fraud, you are more likely to be re-targeted, perhaps for a different investment fraud. Be on your guard. You can learn more about spotting the red flags of fraud by going to the Avoid Fraud section of FINRA.org/investors.

