Cybercriminals Target Brazil: 248,725 Exposed in CIEE One Data Breach
Cyber Threat Intelligence


Dark Web Data Broker
Yesterday, July 1, 2025 — the actor under the alias "888" published over 248,725 records containing sensitive PII stolen from CIEE (Centro de Integração Empresa-Escola). ONE CIEE is a personalized recruitment and selection service offered by CIEE Centro de Integração Empresa-Escola (Business-School Integration Center) for companies seeking candidates for internships and apprenticeship programs. It connects specialists and businesses, ranging from major international corporations to local entities in Brazil.
The service is widely used by top financial institutions in Brazil, as well as popular online platforms, energy, oil & gas, telecommunications, and technology providers. Why do threat actors target such services? Primarily, because they aggregate large amounts of sensitive PII collected for due diligence and recruitment processes, making them valuable targets for cybercriminals. Stolen data can be easily monetized on the Dark Web and used for further identity theft and financial fraud.
The actor has a credible reputation on the Dark Web, particularly for conducting large-scale data breaches. Additionally, on June 17, the actor published stolen data from MinasBet, a popular e-sports betting platform in Brazil, along with multiple other victim organizations operating in different verticals.
The profile of "888" has existed at least since 2024, when he was successfully targeting corporations, including Microsoft, BMW (Hong Kong), and others in the tech, freight, and oil & gas industries. This actor is known to be a "straight shooter," selling acquired databases exclusively due to his great reputation and a proven track record of leaks within the underground community.
Resecurity characterizes "888" as a sophisticated underground data broker operating for profit (financially motivated), targeting public-facing services and applications. Notably, his previous activities overlap with those of notable actors such as IntelBroker, who the FBI recently indicted for monetizing stolen data on the Dark Web belonging to various corporations and government agencies.
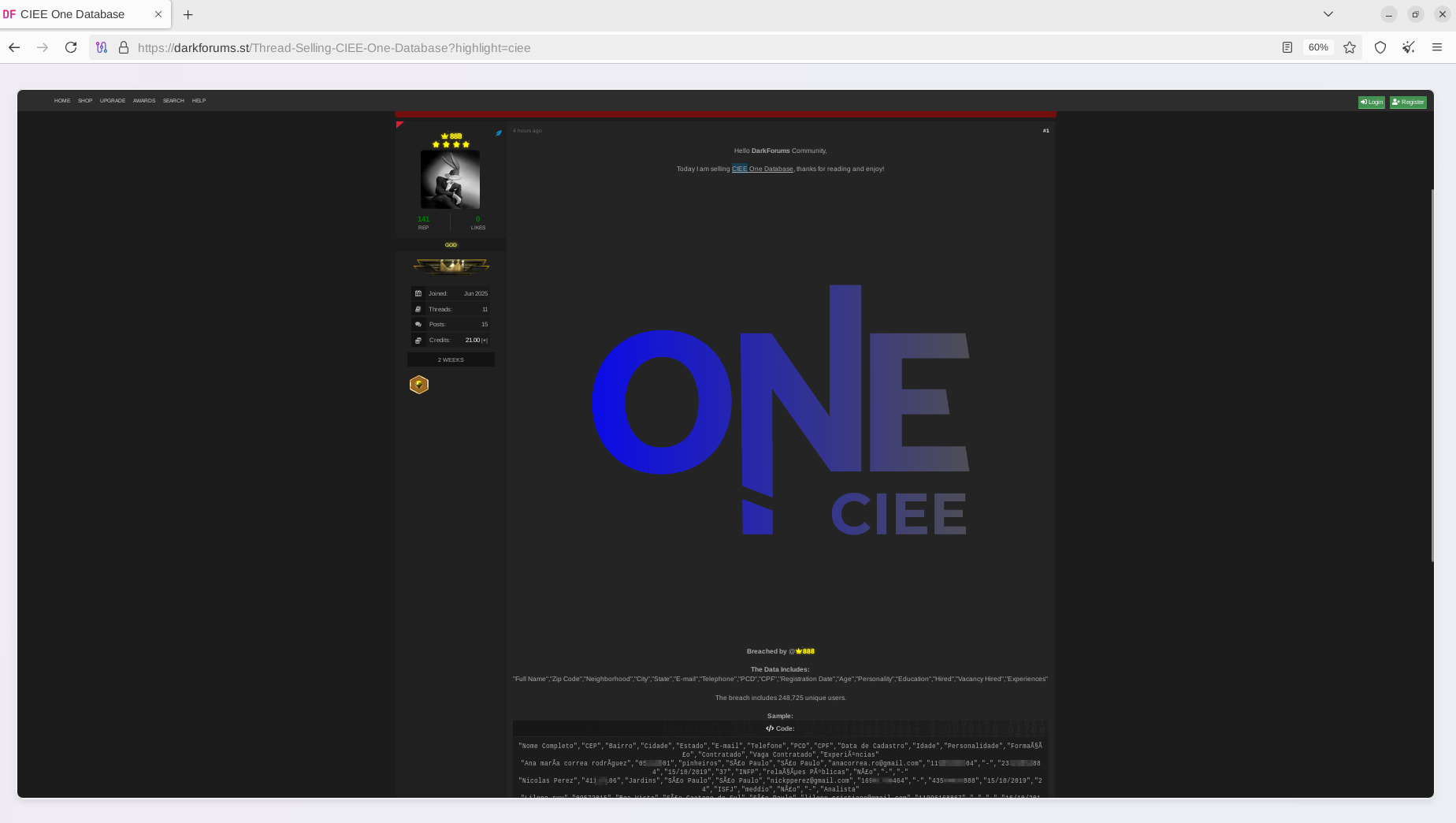
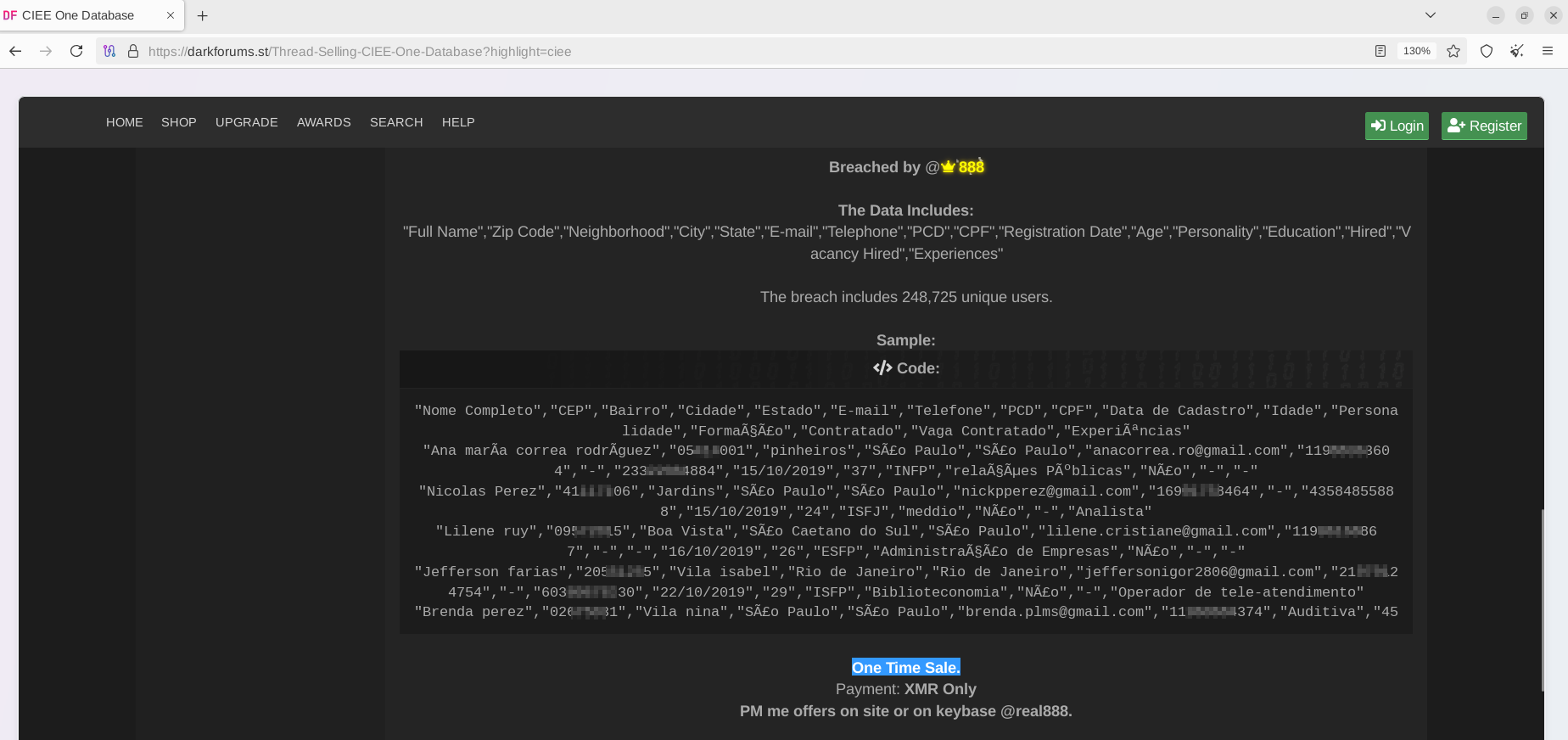
As proof, the actor has shared sample records containing personal data of Brazilian citizens. He did not clarify how this data was exfiltrated, but shared a substantial data set, which Resecurity has validated as authentic. Our team has contacted multiple victims identified among the affected individuals and received feedback that they were registered users at CIEE.
The actor prefers to be paid in XMR (Monero) (due to enhanced privacy) and has a history of successful dealings with other underground actors. Resecurity involved a Human Intelligence (HUMINT) team to acquire additional context from the actor and shared observed artifacts with our Red Team, aiming to identify possible points of compromise. Our team does not prefer to financially sponsor actors, as this could merely facilitate their activities. Instead, our specialists attempt to employ alternative methods to gather intelligence, disrupt their operations, and support victims.
Point of Compromise
After several hours of extensive research, our threat hunters identified possible points of compromise by probing exposed cloud buckets. Unfortunately, this vector remains very common and is widely exploitable by threat actors for data theft. This is due to a lack of protection for cloud services and inadequate configuration hardening.
Cloud bucket exposure - where cloud storage buckets (such as AWS S3, Google Cloud Storage, or Azure Blob Storage) are left misconfigured and accessible to unauthorized users - has become a very popular and significant attack vector for cybercriminals. The widespread adoption of cloud services drives this trend, as well as the frequency of misconfigurations and the valuable data often stored in these buckets. Cybercriminals utilize automated tools to scan for publicly accessible buckets, enabling them to identify and exploit misconfigurations at scale easily.
During a routine security assessment of cloud resources, a misconfigured Google Cloud Storage bucket (ciee-storage.storage.googleapis.com) belonging to CIEE was discovered to be publicly accessible. This configuration error exposed sensitive business and user data to the public Internet without authentication. The data within the bucket included over 364,000 files totaling approximately 28 GB in size. These files contained a significant amount of personal identifiable information (PII), financial documents, medical records, media files, and internal reports. Immediate containment and remediation actions should be initiated.
July 2, 2025 - Resecurity notified CERT.br regarding this matter and shared actionable intelligence about the identified vulnerability that led to cloud bucket data exposure.
Exposed Bucket Overview
Bucket Name: ciee-storage.storage.googleapis.com
• Purpose: General-purpose storage for business operations.
• Misconfiguration: Public read access was enabled, allowing any user to list and download files.
• Risk Level: High
Bucket Statistics:
• Total Files: 364,942
• Total Size: ~28 GB
An investigation of the contents revealed the following breakdown:
• Profile Pictures
◦ Quantity: 281,912
◦ Format: JPEG/PNG
◦ Description: User profile images submitted for account creation or verification.
• Vacancy Videos
◦ Quantity: ~8,000
◦ Format: MP4/MOV
◦ Description: Job application video submissions by users.
• Curriculum Vitae (CVs)
◦ Quantity: ~40,000
◦ Format: PDF/JPEG
◦ Description: User resumes uploaded for job applications.
• CSV Files (Candidate Records)
◦ Quantity: 285
◦ Format: CSV
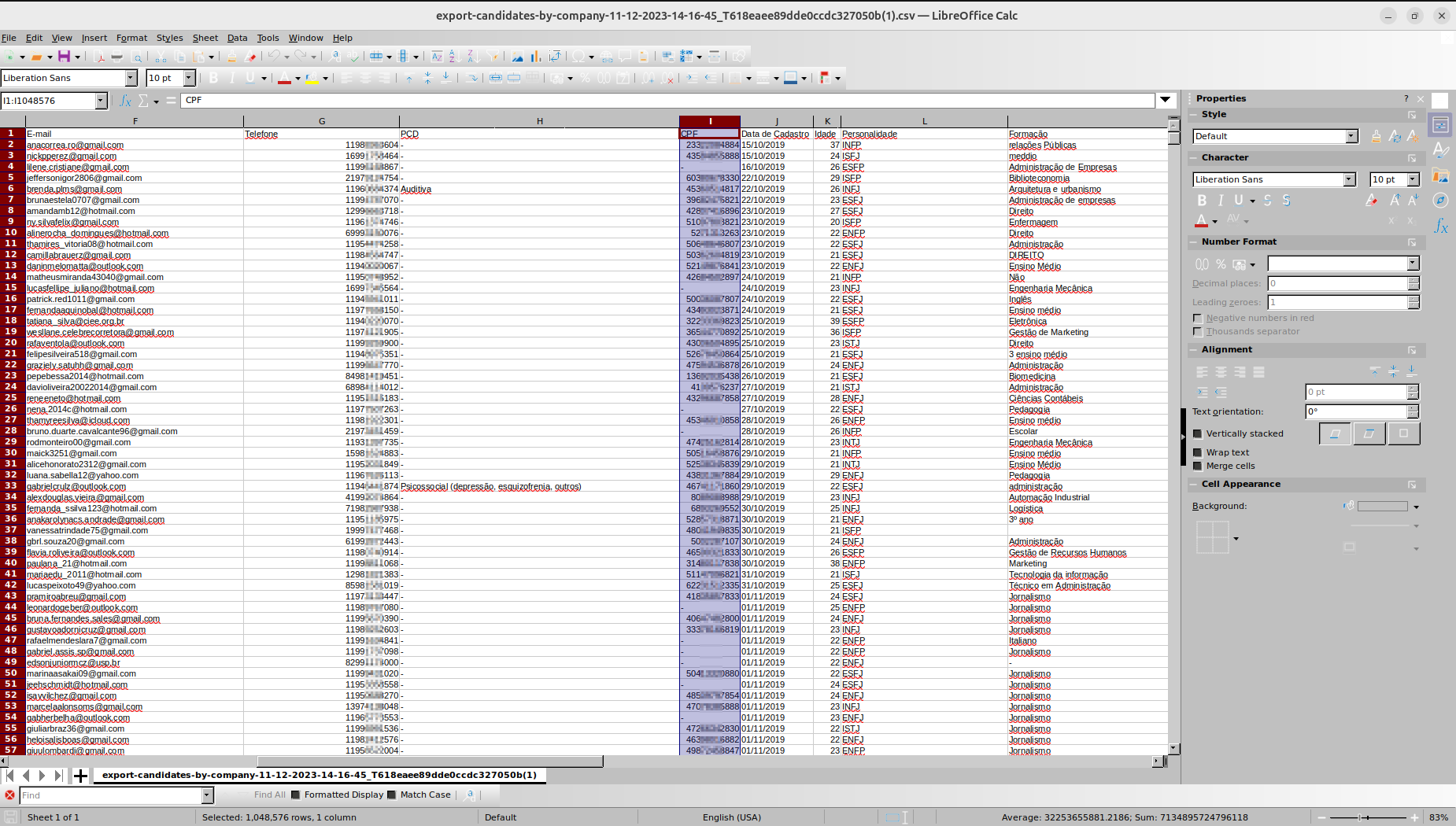
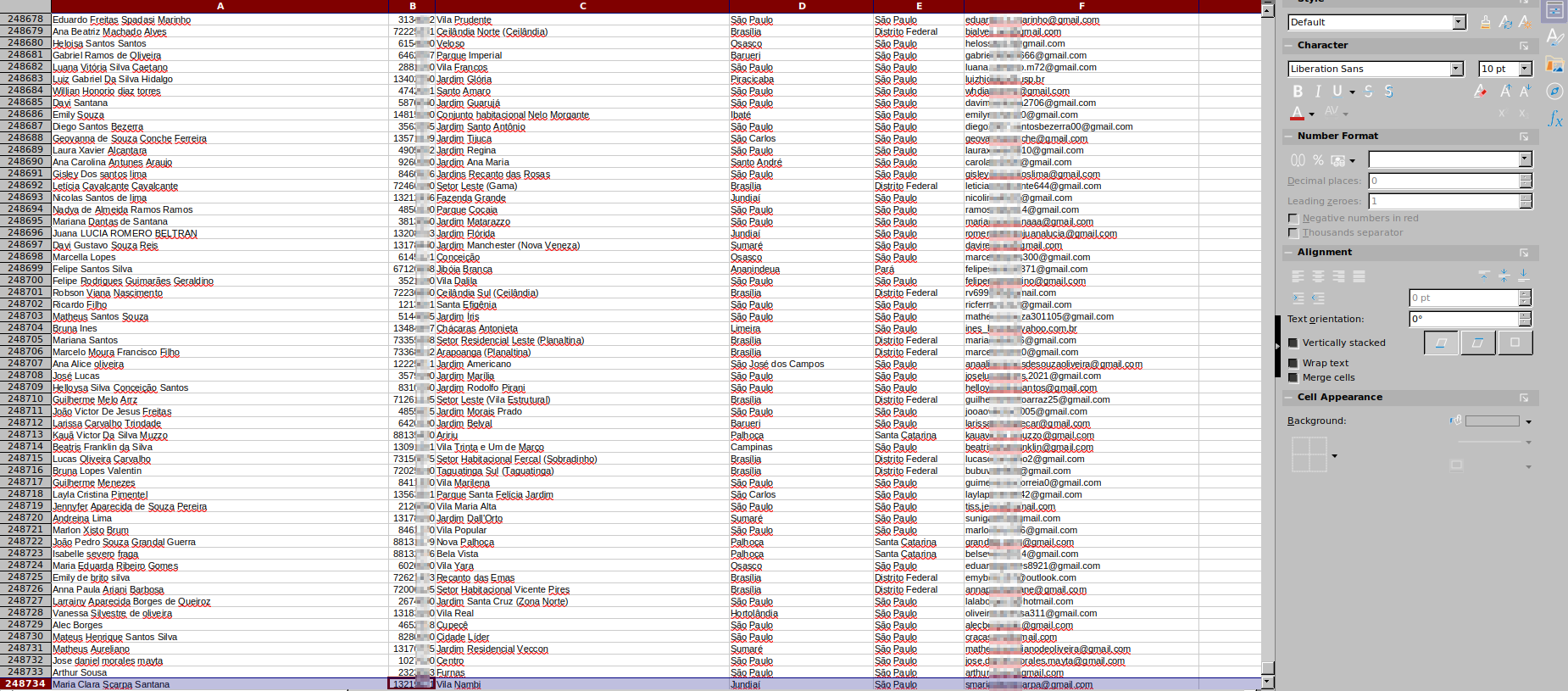
◦ Description: Each file contains ~300,000 candidate records with the following fields:
• Nome Completo, CEP, Bairro, Cidade, Estado, E-mail, Telefone, PCD, CPF, Data de Cadastro, Idade, Personalidade, Formação, Contratado, Vaga Contratado, Experiências
• Medical Reports
◦ Quantity: 2,838
◦ Format: PDF
◦ Description: Includes private medical evaluations and reports linked to job applications.
• Excel Documents
◦ Quantity: 264
◦ Format: XLSX
◦ Description: Internal tracking sheets, analytics, candidate lists, and operational data.
What Has Been Breached?
After several hours of extensive research, our threat hunters identified possible points of compromise by probing exposed cloud buckets. Unfortunately, this vector remains very common and widely exploitable by threat actors for data theft, due to a lack of protection for cloud services and inadequate configuration hardening.
After the initial assessment, the central aspect of the data breach involved the disclosure of PII, including the CPF identifier, also known as Cadastro de Pessoas Físicas, which is the Brazilian individual taxpayer number.
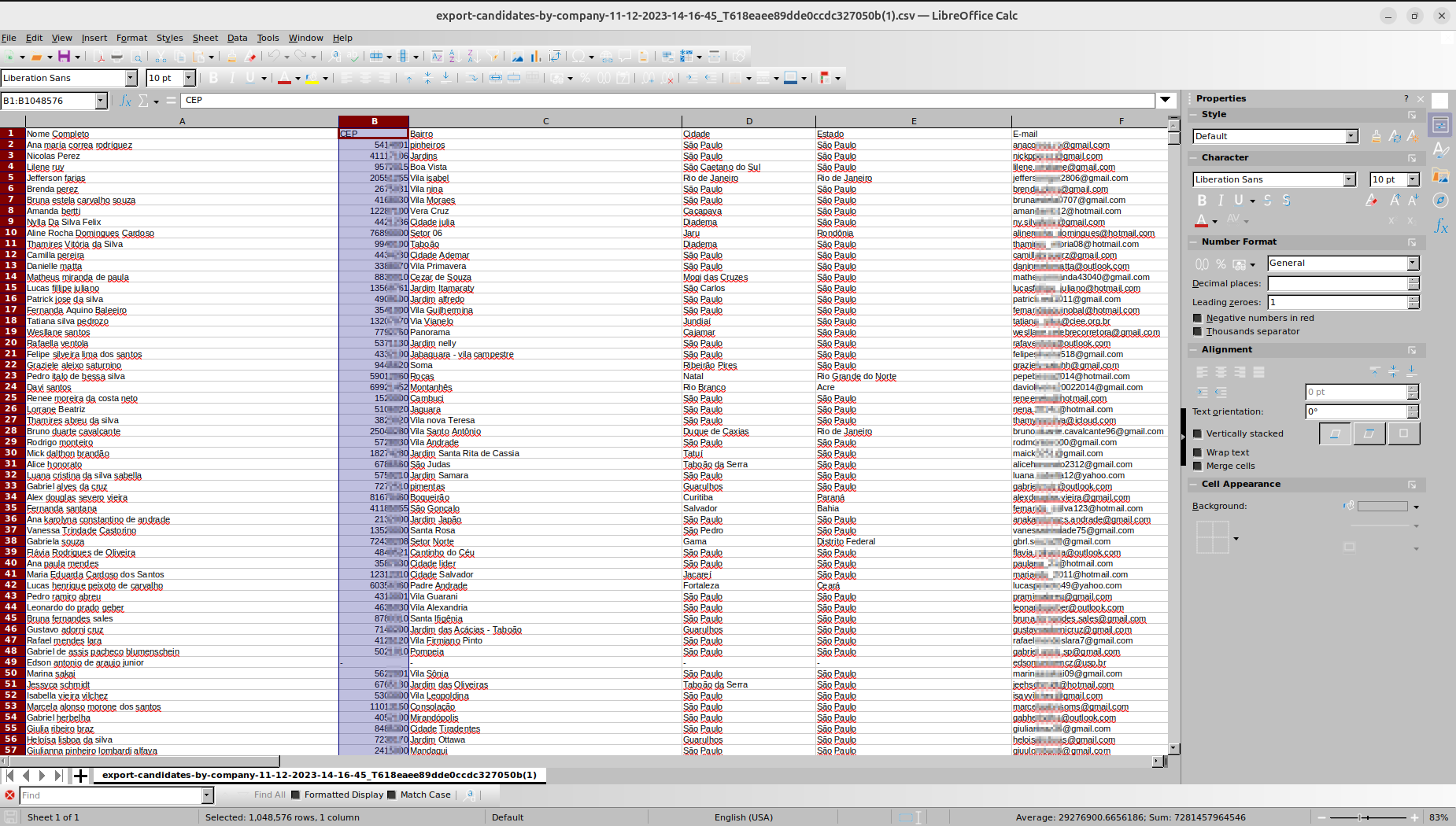
The data was stored in CSV format and was being updated—likely with new registrations received via the CCIE platform. As of July 2, 2025, the issue had not been contained, allowing the threat actor to continue collecting exposed PII.
Resecurity acquired the exposed records and shared them with the data protection authority in Brazil to inform victims about the risks to their privacy.
A comprehensive assessment revealed much broader implications resulting from this data breach compared to those initially outlined by the actor. Likely, he aimed to protect the data available to him and monetize only a portion of it. Once Resecurity identified the point of compromise, it became clear that, in addition to text records, the actor could also have obtained scans of personal documents, including medical reports, which are critical to users’ privacy.
Resecurity identified several other buckets storing sensitive imagery and video information with citizens' documents and biometrics (face):
https://storage.googleapis.com/ciee-storage/production/public/users/medical-reports/6722806cfc3a5215...
https://storage.googleapis.com/ciee-storage/production/public/users/medical-reports/615b1bd3fa71fe00...
https://storage.googleapis.com/ciee-storage/production/public/users/curriculums/61a9176ebdf4c1001cb9...
https://storage.googleapis.com/ciee-storage/production/public/users/medical-reports/5eb084f60e594100...
Data breaches of such scale are especially damaging and challenging to mitigate, as they combine personal data with actual documents and medical information, which victims cannot easily change or "erase." While contact information, such as phone numbers and email addresses, can be updated relatively easily. To further exacerbate the damage, biometrics and medical data are highly sensitive categories that greatly affect victims’ privacy.

Resecurity promptly alerted the affected parties and shared additional artifacts to determine the scope of the data breach and to formulate recommendations on how to contain it promptly. The acquired records have also been ingested and disseminated by our Digital Identity Protection platform to alert businesses and consumers about the risk of data leaks.
Privacy, Security and Business Impact
Privacy Implications:
• Massive PII Exposure: Thousands of individuals' personally identifiable information is now publicly accessible, which will be used in future frauds, including identity theft and impersonation.
• Sensitive information can be used for extortion.
Security Implications:
• Massive PII Exposure: Personally identifiable information of millions of individuals was publicly accessible. To be used in future attacks.
• Sensitive Health Data Disclosure: Exposure of medical reports introduces additional compliance risks.
• Credential Leakage: Presence of configuration files may expose system credentials.
• Reconnaissance Support: Adversaries could use internal data structure to tailor attacks.
Business Risks:
• Regulatory Violations: The exposure may violate LGPD (Lei Geral de Proteção de Dados) and potentially international data protection laws.
• Reputational Harm: Users may lose trust in the platform’s ability to safeguard their information.
• Financial Liabilities: Significant potential for fines and penalties, plus breach notification and mitigation costs.
Conclusion
This incident underscores the critical need for vigilant security monitoring, proactive access management, and comprehensive cloud security governance. The scale and sensitivity of the exposed data require a thorough post-incident review and ongoing improvements to infrastructure management to prevent recurrence.
Cloud bucket exposure is not only a popular attack vector for cybercriminals but also one of the most persistent and damaging. The combination of frequent misconfigurations, ease of discovery, and the high value of data stored in cloud buckets makes this a favored target for attackers. Organizations must prioritize secure configuration, regular audits, and robust access controls to mitigate this risk.
This report also shows, as another example, that even though breaches happen through technology and insider threats, a similarly common reason is improper access control. Threat actors continue to exploit all three, resulting in the same outcome: the IP of companies and the PII of users being obtained by threat actors to victimize them.
Resecurity recommends that businesses conduct VAPT (Vulnerability Assessment and Penetration Testing) and perform ongoing cyber threat intelligence (CTI) gathering to detect potential targeting by cybercriminals at an early stage, before a data breach can cause substantial damage.
Vulnerabilities that lead to personal data leakage can result in significant regulatory penalties under the Lei Geral de Proteção de Dados (LGPD) act. Failure to comply with LGPD may lead to administrative sanctions by Brazil’s data protection authority (ANPD), including fines of up to 2% of a company's revenue in Brazil, capped at R$50 million per infraction. In addition to regulatory risks, Brazil continues to experience high levels of cybercrime, including data breaches and ransomware attacks. This makes compliance with LGPD not only a legal obligation but also a critical cybersecurity concern.
By delivering cutting-edge threat intelligence and compliance automation, combined with on-the-ground expertise, Resecurity empowers organizations to confidently meet LGPD standards. In doing so, it helps build a safer, more trusted digital future for individuals, companies, and the public sector in Brazil. As Brazil continues to strengthen its position as a regional tech leader, Resecurity is proud to contribute to the country’s data protection ecosystem and support its mission to protect citizens' rights in the digital age.

