

Introduction
The rapid growth of contactless payments and digital wallets in the Philippines has created new opportunities for financial inclusion and economic efficiency. However, this shift has also attracted the attention of cybercriminals who are actively exploiting Near Field Communication (NFC) technology to conduct fraud on a scale.
The Philippines has become one of the top regions affected by Chinese cybercriminals. Major underground shops managed by Chinese cybercriminals list the Philippines as one of the most impacted areas, based on the volume of compromised credit cards (CCs).
TransUnion Philippines has reported a significant increase in suspected digital fraud, with rates in the Philippines exceeding global averages. The Philippines suspected digital fraud rate stood at 13.4% in 2024 – 148% higher than the global rate of 5.4%. Over seven in every ten (74%) Filipinos reported being targeted by email, online, phone call or text messaging fraud recently. Among Filipinos who said they lost money due to fraud recently, the reported average loss exceeded 44,700 Philippine pesos (PHP). Damages to businesses are much more significant and difficult to estimate - potentially amounting to millions of PHP in losses.
Resecurity® estimates that the increase in cybercrime activity is proportional to malicious efforts by China targeting the Philippines and the Indo-Pacific region. Therefore, governments and financial institutions should accelerate their defenses to protect the financial system from foreign adversaries. Based on our assessment, as of Q2 2025, Dark Web activity originating from China targeting the Philippines increased by nearly 230%, doubling compared to the previous year. These statistics have been confirmed based on the volume of relevant communications within cybercrime communities, collected by Resecurity's global intelligence network from Chinese-speaking actors.
The scale of Chinese cybercrime is massive and, as of today, comprises at least several thousand independent actors and groups involved in fraud and other malicious activities. For example, the number of participants in major Chinese-speaking underground communities analyzed by our HUNTER team (threat intelligence and investigations) varied from 5,000 to over 20,000. Considering that cybercrime originating from China targeting other foreign countries is known to be tolerated by the state, it poses a major threat to the global financial system and requires significant attention from both the private and public sectors.
Resecurity®, a global leader in cyber threat intelligence, has observed an increase in the use of specialized tools that enable attackers to simulate legitimate contactless transactions using stolen card data. These activities, previously concentrated in other regions, are now affecting Southeast Asia, with indicators showing growing interest in the Philippine market.
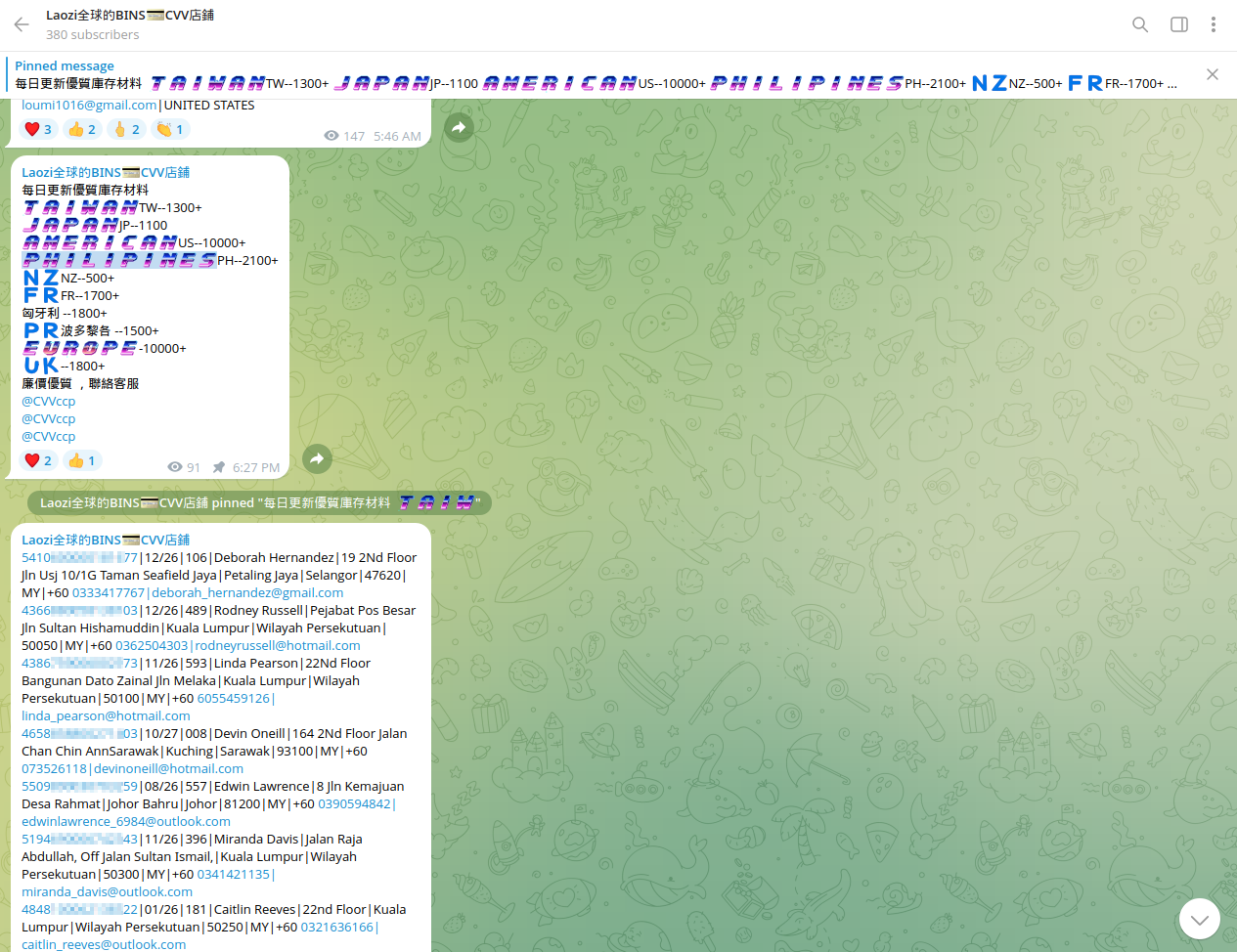
Besides the Philippines, the top regions targeted by Chinese cybercriminals also include Australia, Taiwan, Malaysia, New Zealand, Singapore, Thailand, Hong Kong, Korea, and Indonesia.
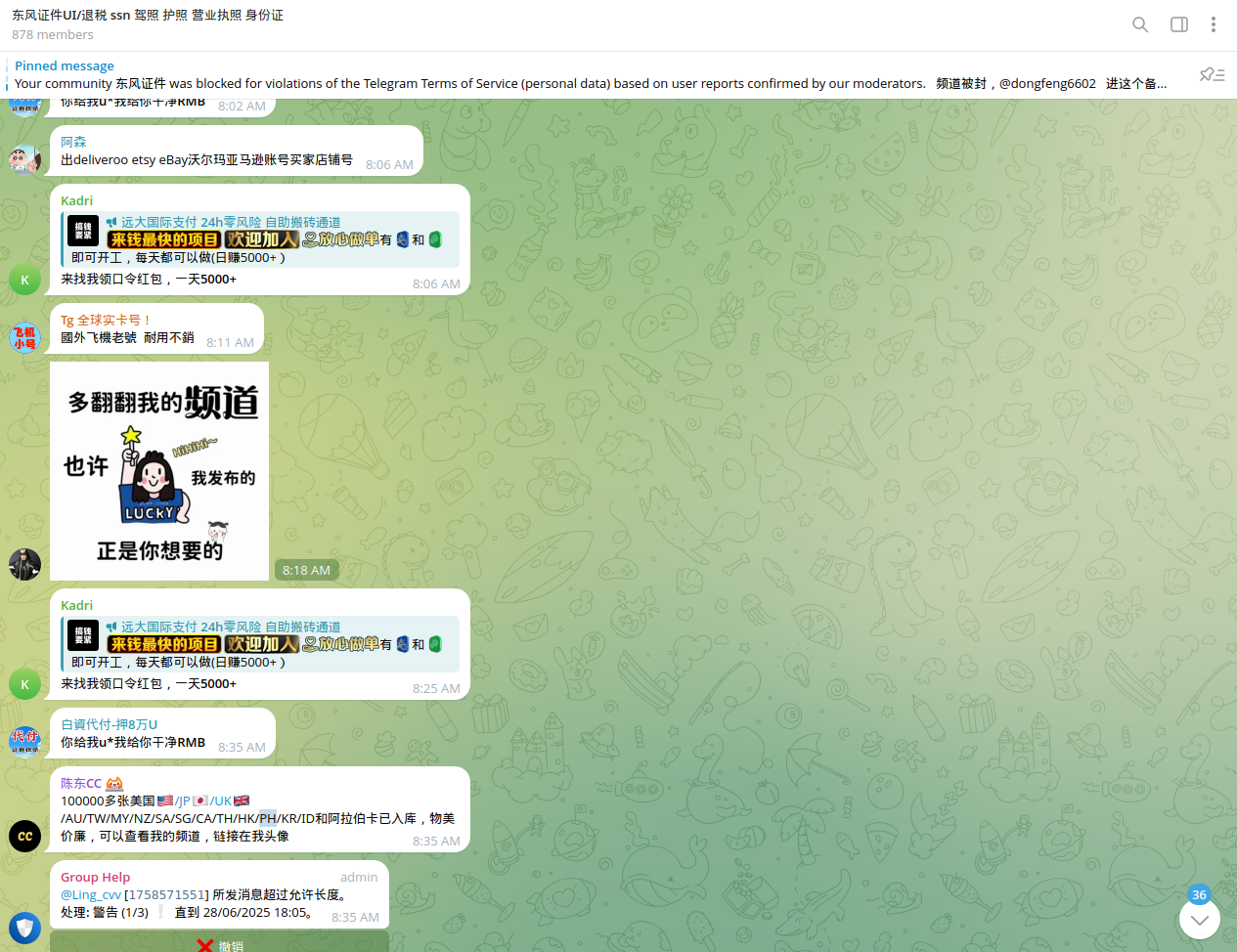
Resecurity also observed Chinese cybercriminals involved in NFC-enabled fraud actively targeting countries of the European Union, the US, the UK, Canada, and Mexico.
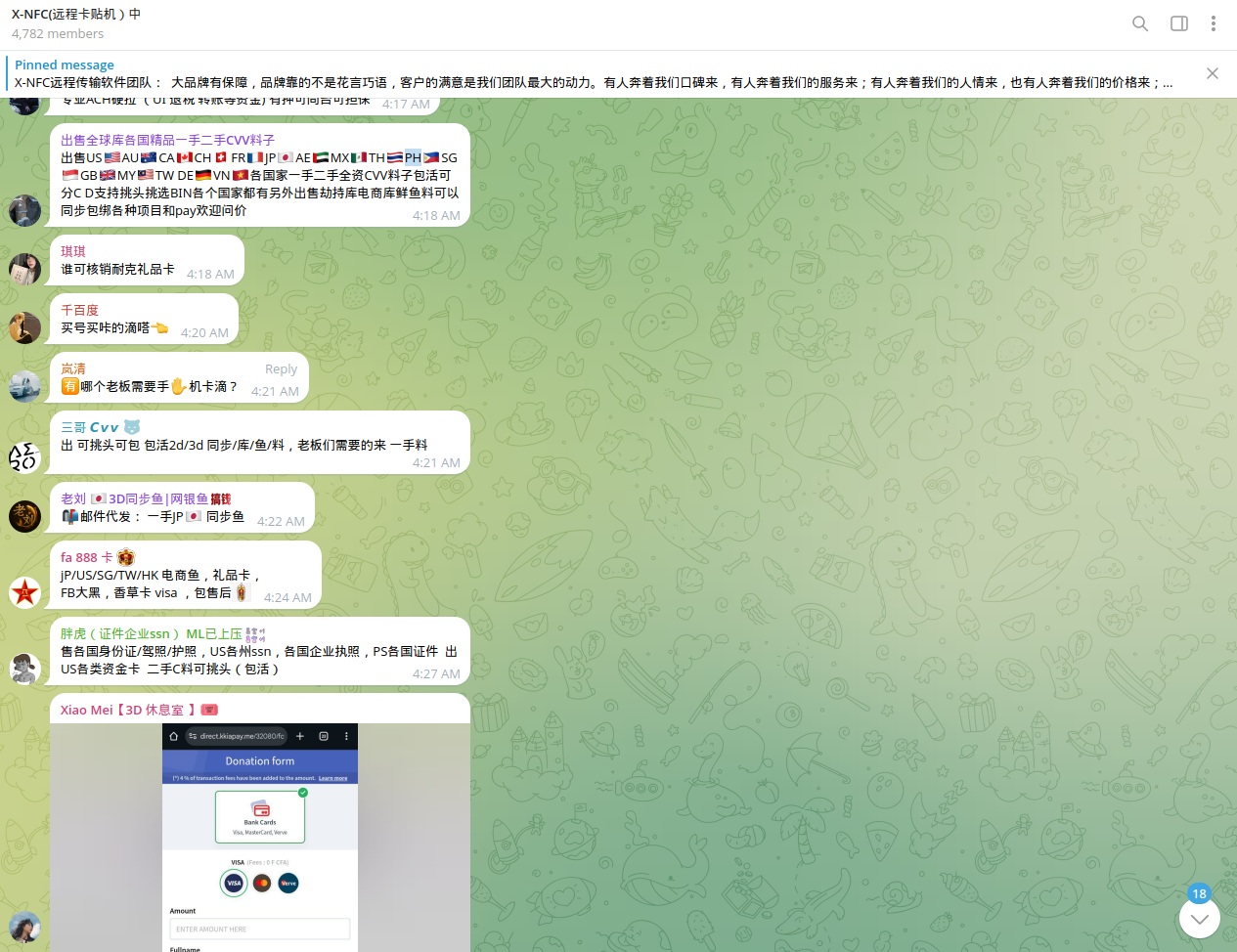
Our analysts identified numerous groups enabling cybercriminals to acquire compromised cards from those regions and also check whether they are valid or not, using micro-charges performed via fraudulent merchants set up by Chinese cybercriminals.
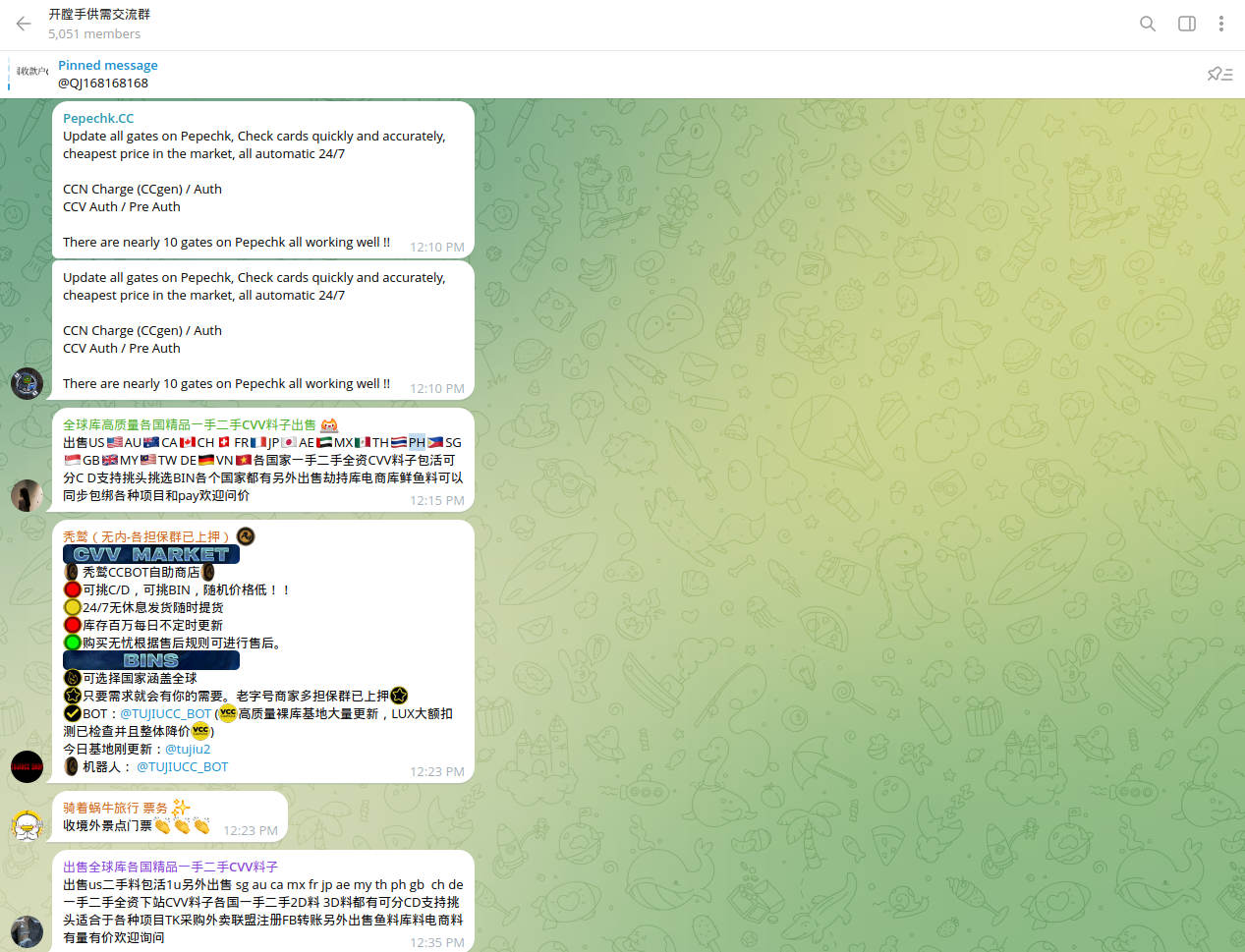
Most of these groups also have Telegram bots used to automate the sale of compromised payment data. In some cases, such bots are not easily identifiable, as information about them is shared within a close circle of actors, primarily Chinese-speaking, which may further complicate detection and timely response. Resecurity identified dozens of active Telegram bots managed by Chinese cybercriminals operating for a significant amount of time despite existing Terms and Conditions of the app - without flagging or blocking. This may indicate challenges in effective content moderation, fraud prevention, and compliance policies. Chinese cybercriminals are exploiting these aspects and moving cybercrime-related communications to Telegram, which seems to be a "safe option" for their OPSEC while physically residing in China. It is unlikely they want to risk communicating via domestic IMs such as WeChat or QQ to discuss cybercrime matters, but they feel relatively comfortable doing so via Telegram - a trend observed in Q1/Q2 2025. Example of such active Telegram bot called "Lita's Shop" is provided below:
Resecurity identified the Philippines as one of the main trending geographies targeted by Chinese cybercriminals - in terms of smishing activity and NFC fraud, the first enables Chinese cybercriminals to intercept large volumes of compromised payment data, which they later monetize via the Dark Web; the second allows them to use this data for actual fraud and money laundering. The majority of Chinese-managed underground shops and Telegram bots list the Philippines as one of the key regions with the highest volume of compromised credit cards.
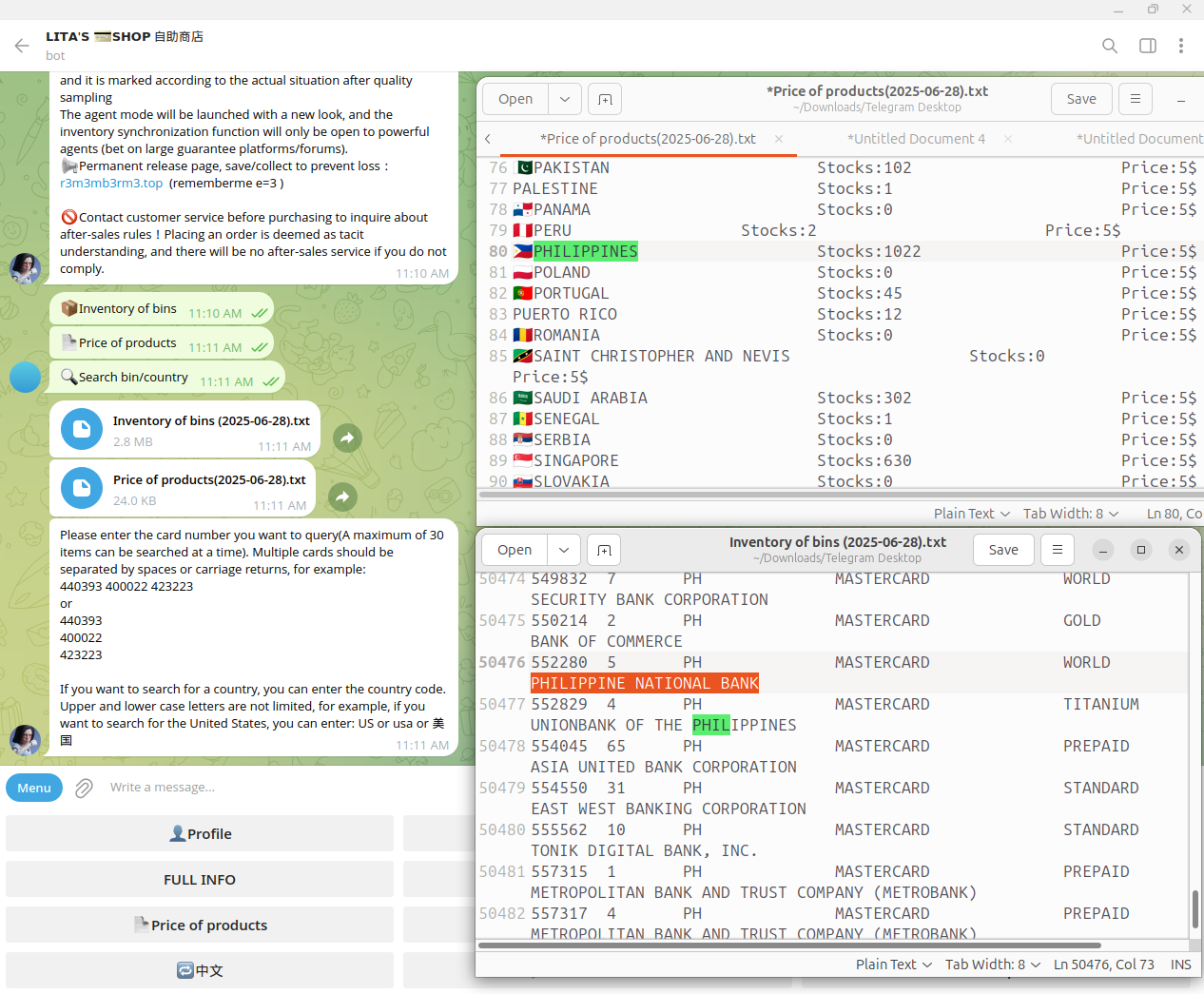
Telegram bots are automated and provide interactive navigation across various databases with stolen credit card information, organized by country and bank. Notably, some of the bots controlled by Chinese cybercriminals had substantial volumes of compromised payment data—potentially resulting in millions of dollars in losses.
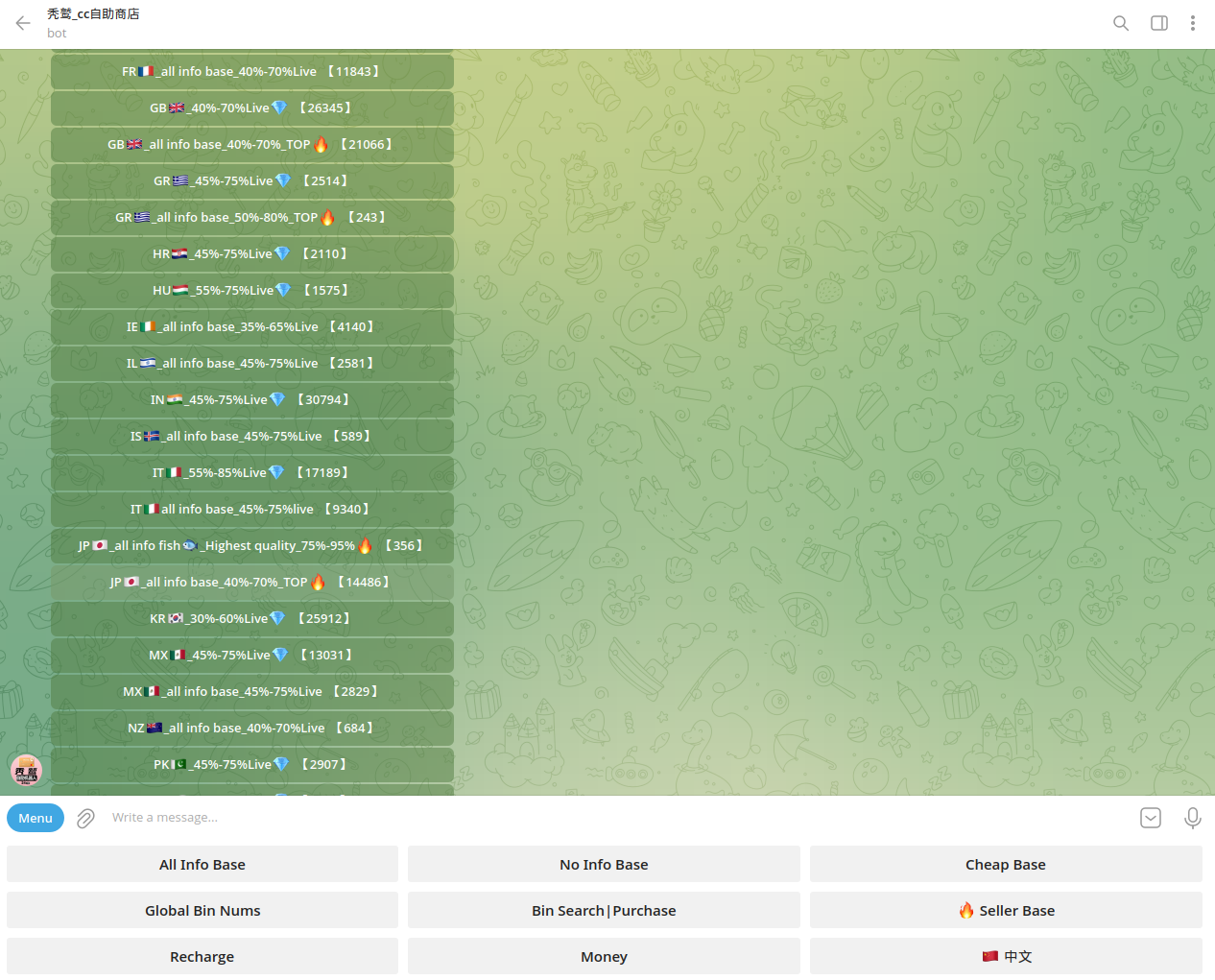
Notably, some of these bots are managed by well-organized syndicates involved in smishing, serving as a key source of compromised credit cards (CCs). On March 22, 2025, Resecurity identified a new smishing kit known as "Panda Shop," based on the same principles used by the Smishing Triad. Notably, the giant panda is a prominent and iconic symbol of China. It's recognized domestically and internationally as a symbol of the country, representing peace, friendship, and soft power. But in this case, it doesn’t seem to bring anything good besides financial losses to consumers. "Panda Shop" has multiple Telegram channels and interactive bots to automate service delivery.
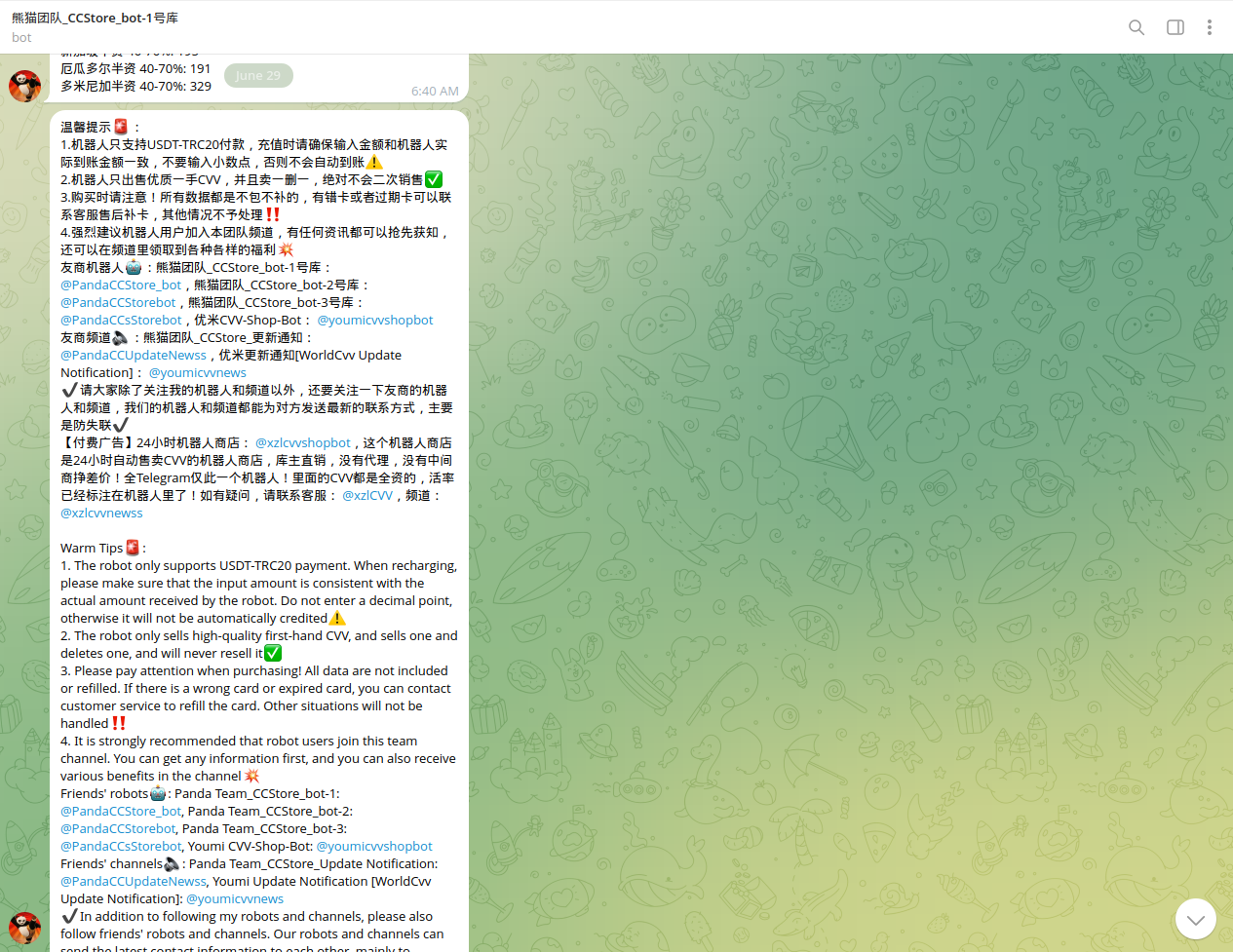
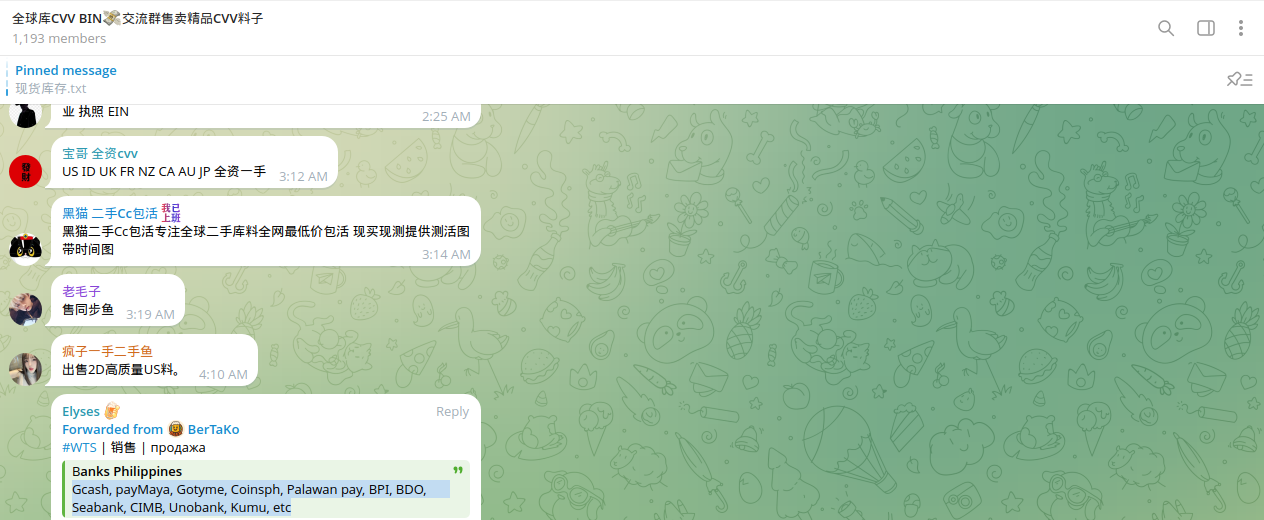
Resecurity also identified several new underground credit card shops managed by Chinese cybercriminals closely affiliated with groups involved in smishing and NFC-enabled carding, such as the Smishing Triad. Resecurity was the first company to identify the Smishing Triad, a group of Chinese cybercriminals targeting consumers across the globe. In August 2023, our team was able to identify their activity and locate the smishing kit they were using, successfully exploiting a vulnerability, which exposed the threat actors and their infrastructure. Since then, the group has become stealthier and upgraded its tooling, tactics, and procedures (TTPs). A group of this scale is not limited to just one threat actor; it has numerous associates with different roles, blurring its public profile. Such groups leverage a "Crime-as-a-Service" model, enabling other cybercriminals to use their smishing kit and scale their operations targeting consumers in different countries. For example, the "Hulk Vault" shop, managed by Chinese cybercriminals, has a presence on Telegram, the surface web, and the TOR network (Dark Web).
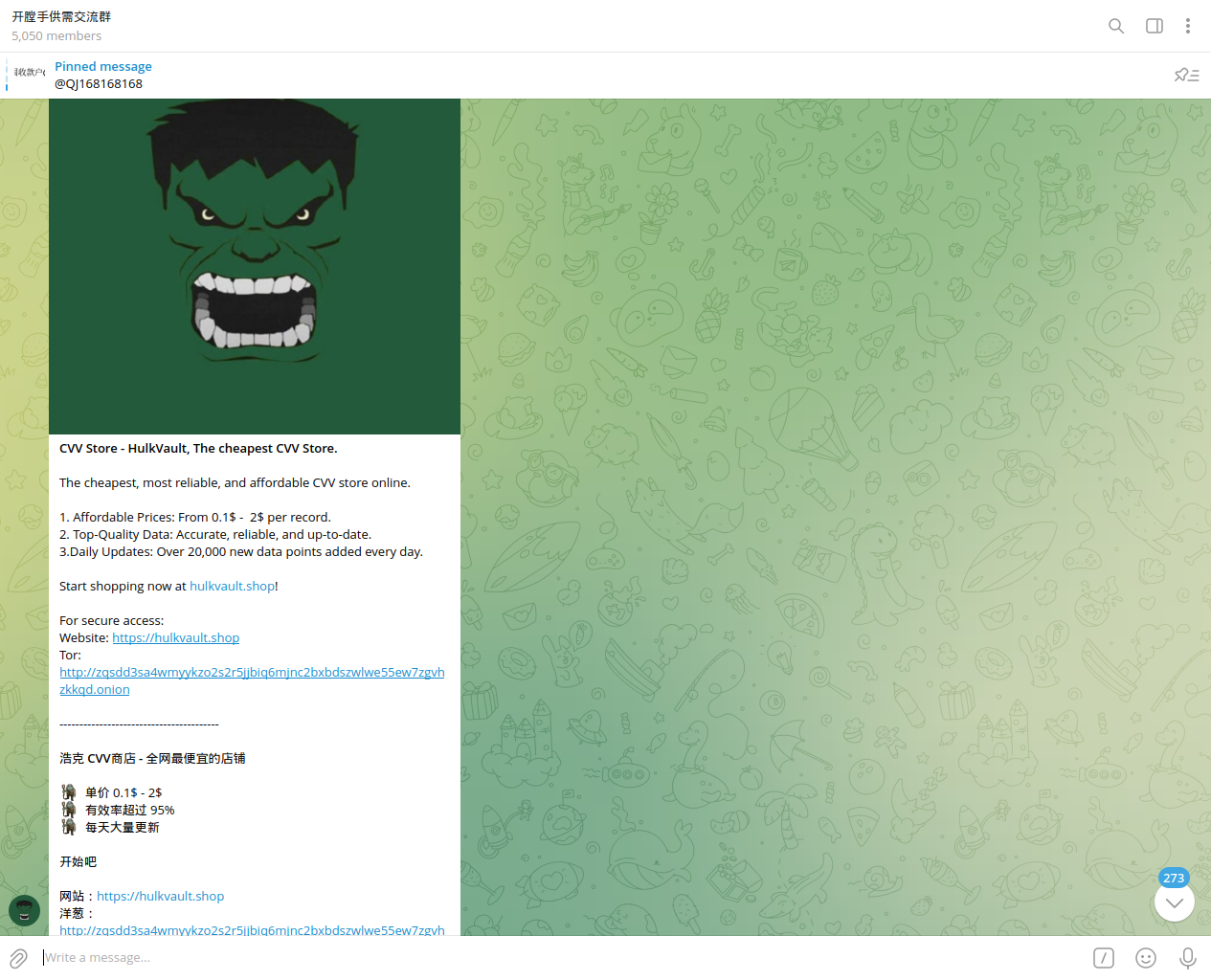
The Philippines was listed among the top 10 countries from which Chinese cybercriminals offer compromised credit cards. Some of the observed underground shops managed by Chinese cybercriminals have a substantial volume of compromised credit cards for sale - one of them had over 7,741 cards available.
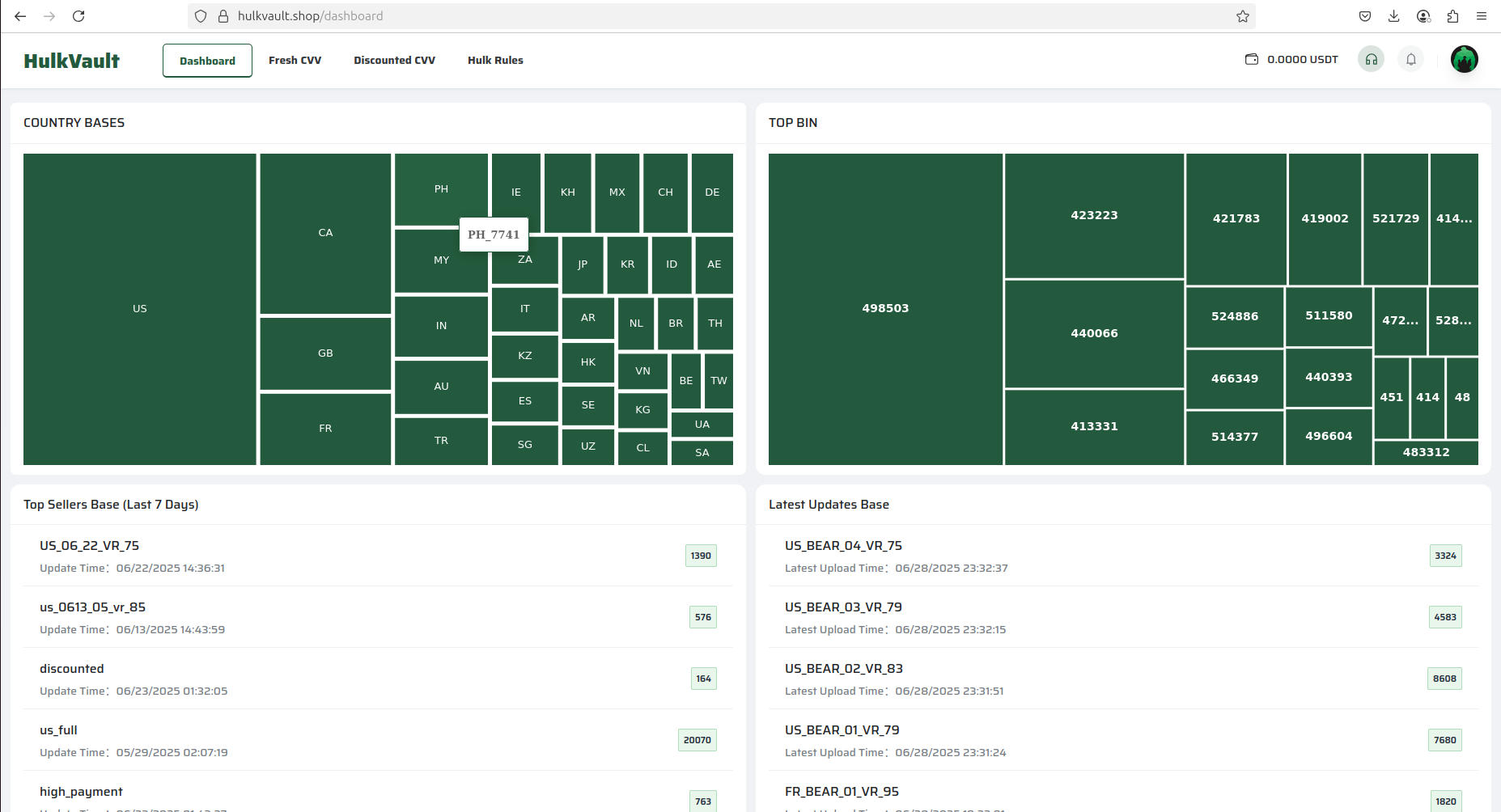
Considering the relatively inexpensive options for acquiring compromised credit cards by other cybercriminals - where the cost per card varies from cents to a few dollars - such activity could cause significant damage to the local economy and consumers.
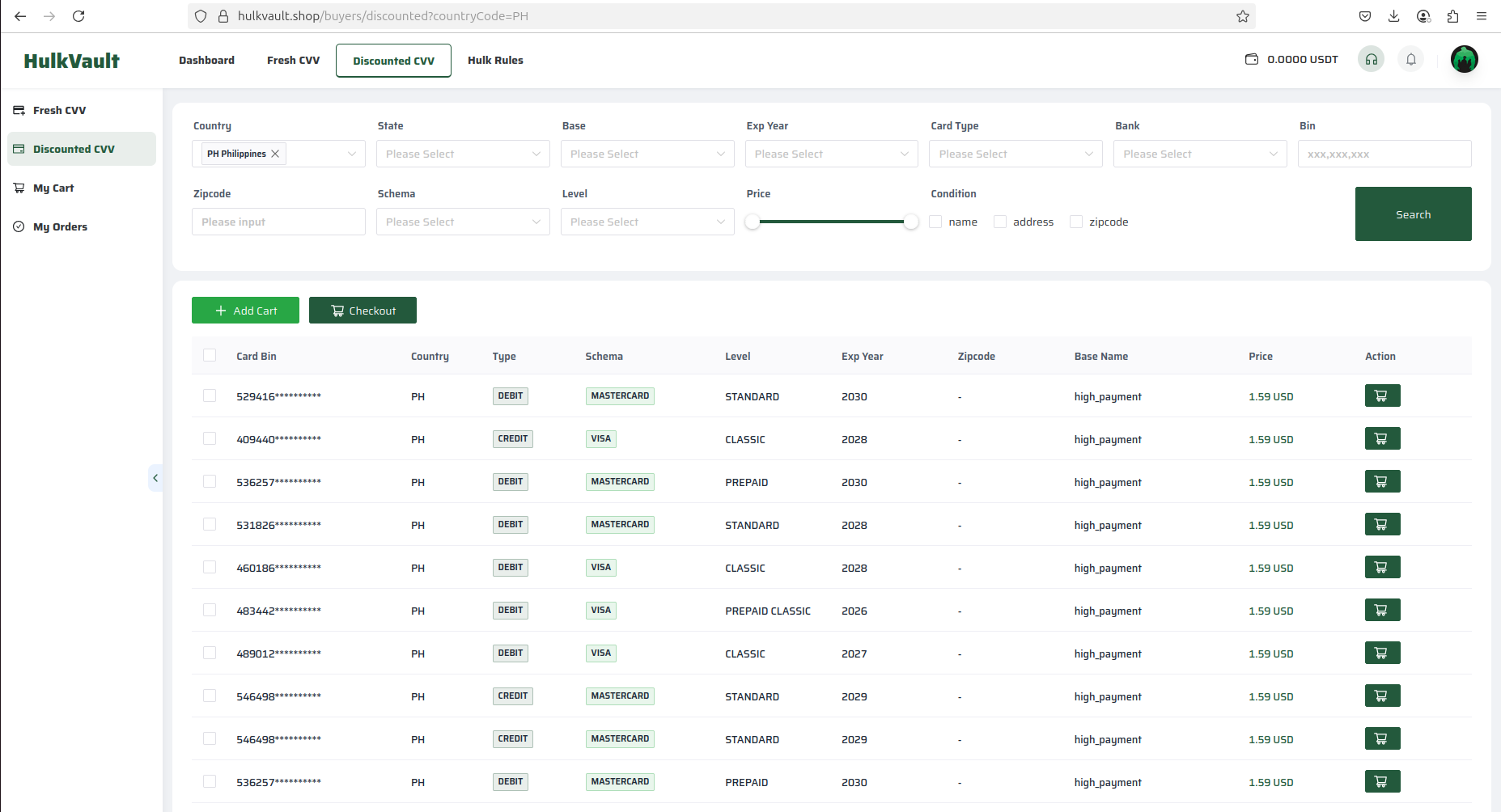
Another underground community frequently used by actors to acquire and check compromised credit cards had over 5,869 items available today.
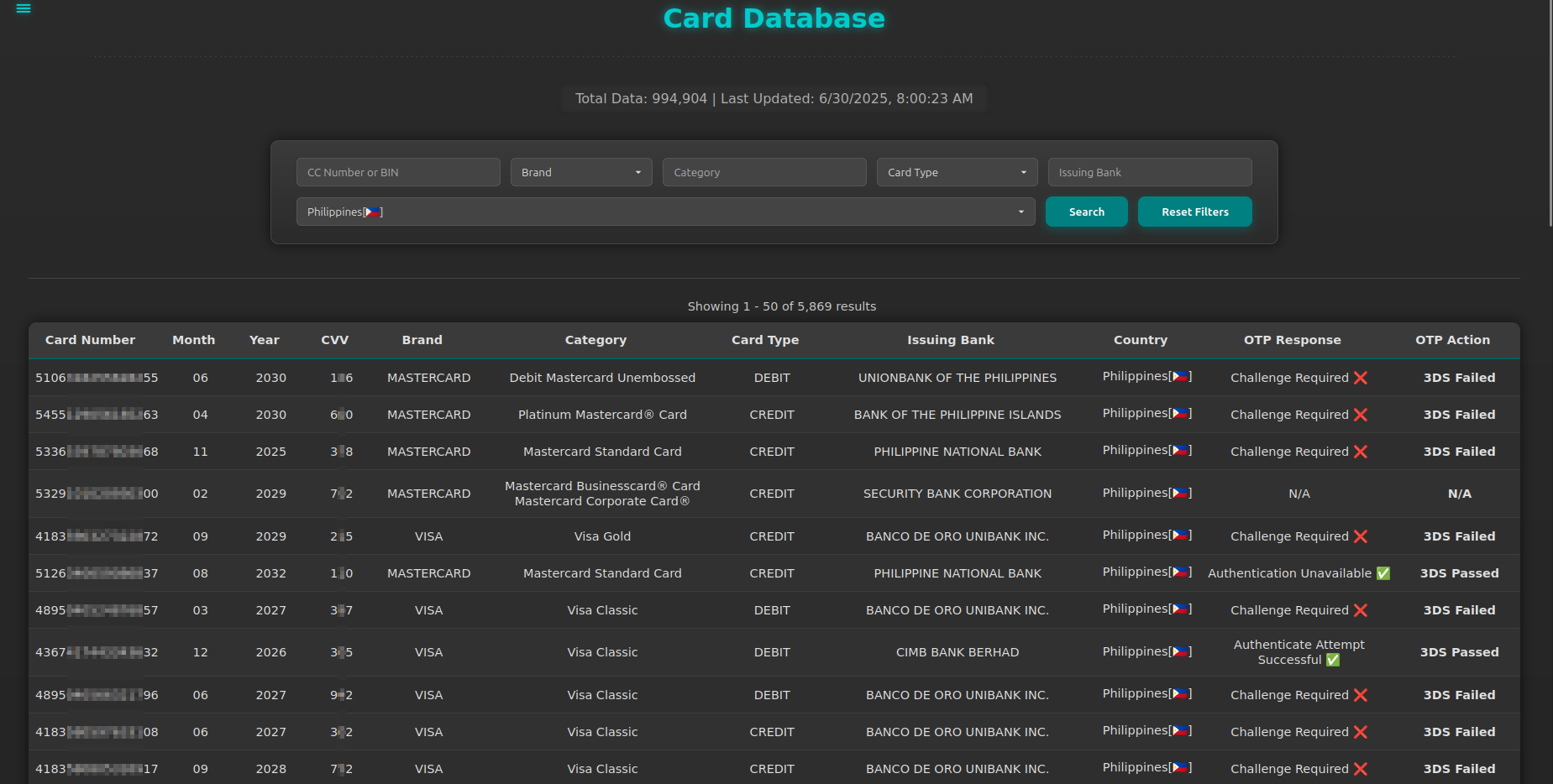
In total, we are talking about thousands of banking customers - victims of Chinese malicious activity.
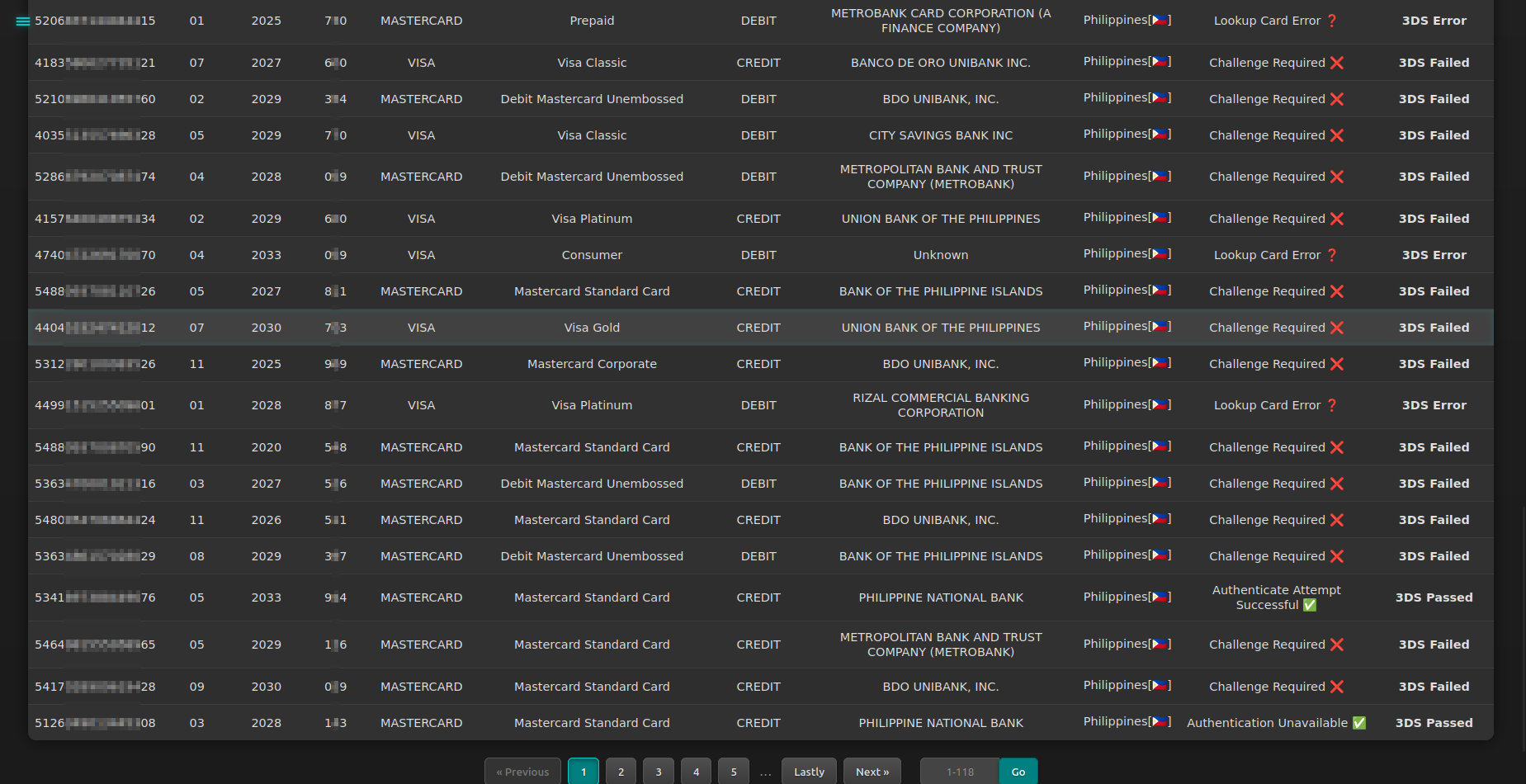
Targeting Major Payment Systems
Local payment systems in the Philippines are a key target for Chinese cybercriminals. First of all, these systems enable transactions for the majority of consumers, which is why they have become attractive avenues for fraud and money laundering. GCash, Maya Philippines (formerly PayMaya), GoTyme, and BDO (Banco De Oro) Mobile Pay are the most actively targeted systems by cybercriminals—based on the analysis of Dark Web communications.
Notably, both GCash and Maya support NFC. They offer NFC-enabled payment terminals for merchants and have integrated NFC into their cards for tap-to-pay functionality. Other systems do not support NFC yet but provide QR payments as an alternative for contactless payments.
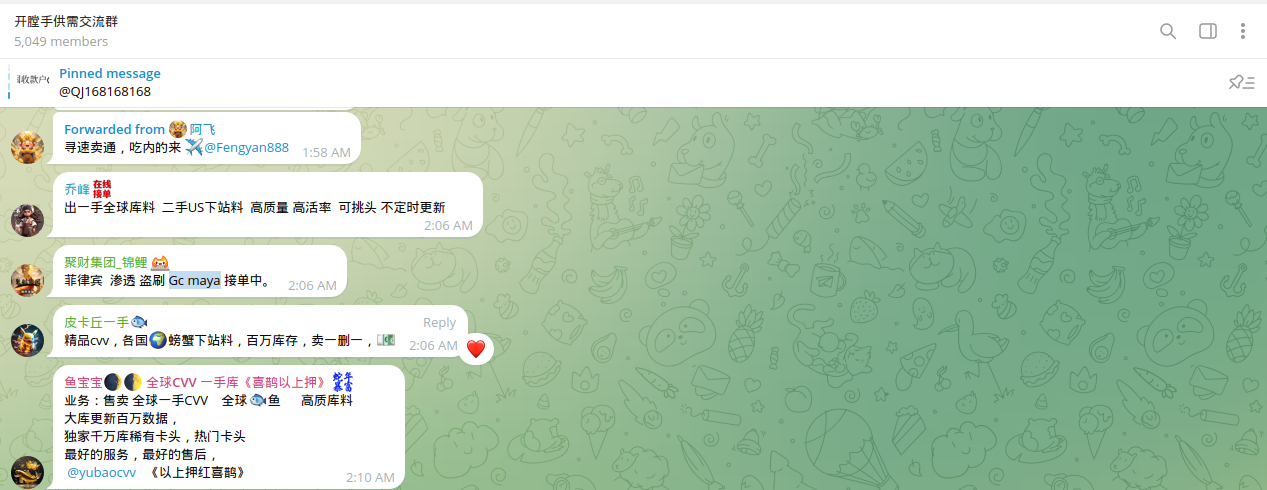
The precursors to targeting these systems had been previously flagged by local industry professionals, but fraud attempts did not stop and only increased with the rapid digitization and implementation of new technologies such as NFC.
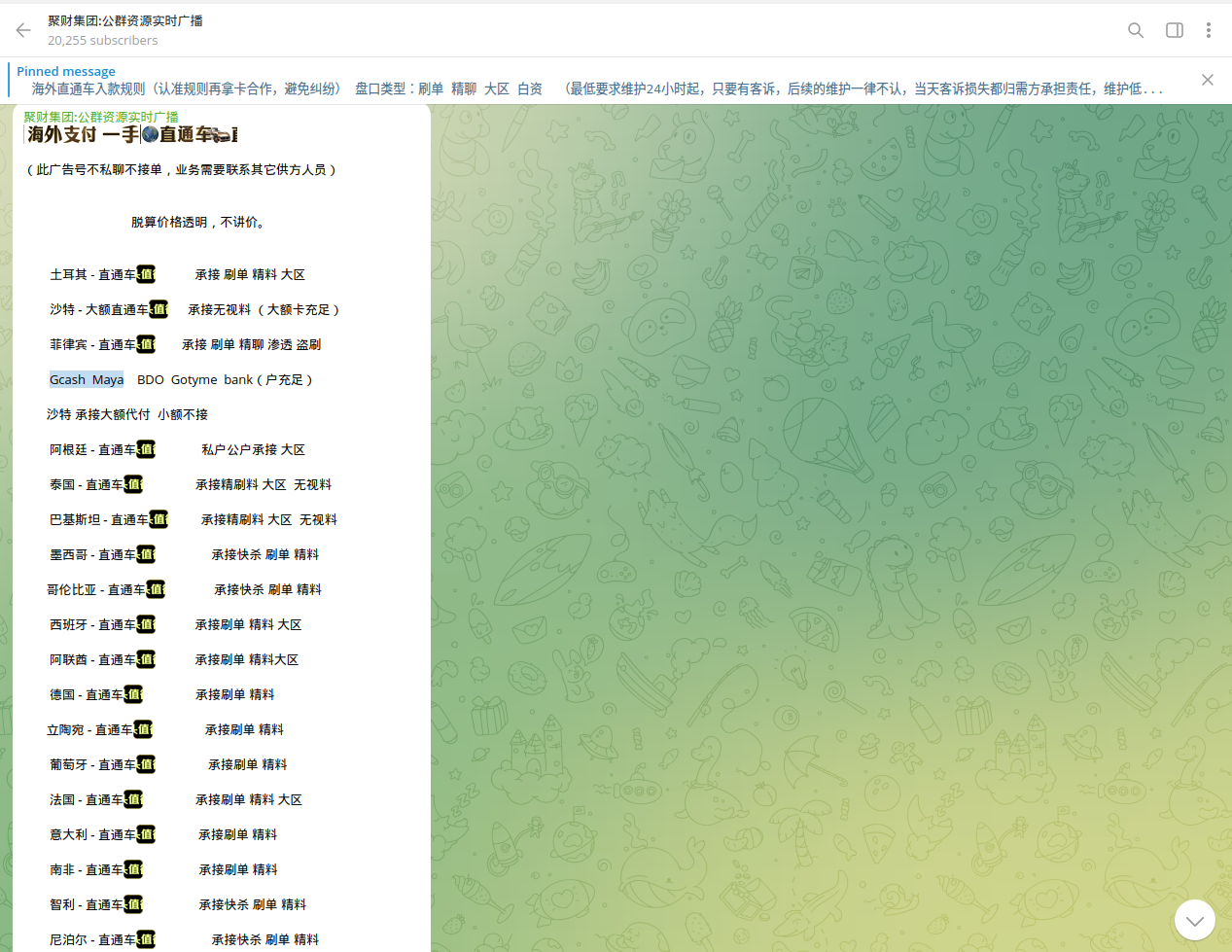
An interesting pattern was identified where Chinese cybercriminals partner with local organized crime in the Philippines to facilitate fraud. Multiple communications were also detected between Dark Web actors selling or acquiring accounts for further fraud and money laundering.
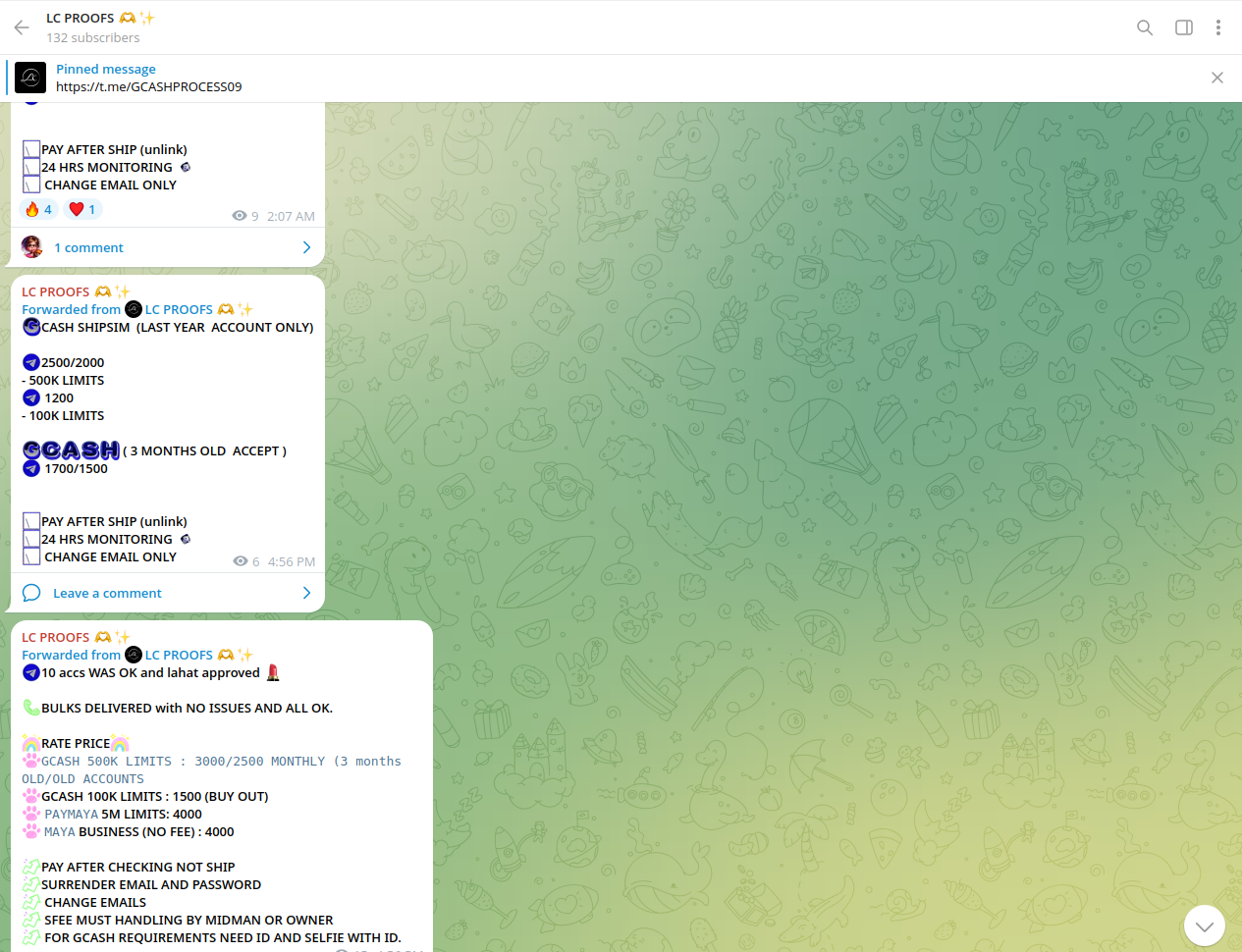
Chinese cybercriminals seek cooperation with locals in the Philippines to recruit money mules - tasking them with opening accounts for further illegal cashout operations or the re-distribution of stolen funds. Building money laundering chains is a key aspect of such cooperation.
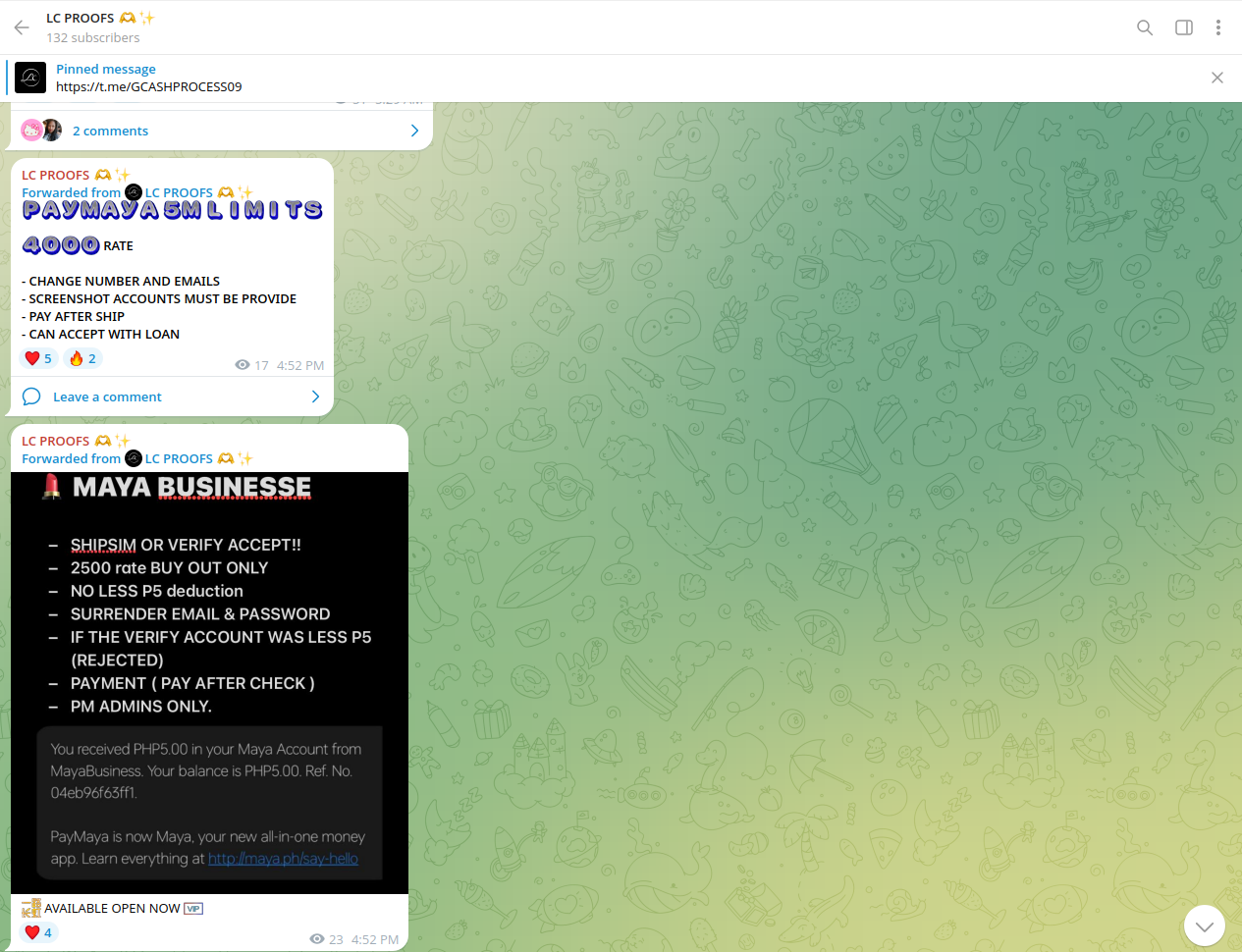
Along with GCash and Maya, accounts of local digital banks, neobanks, and e-wallets are another high-demand category for Chinese cybercriminals.
Considering the intersection between e-wallets and NFC, Resecurity expects Chinese cybercriminals to focus on these technologies in the near future.
How NFC Fraud Works
NFC technology allows users to make contactless payments using a card or mobile device. Threat actors have begun abusing this technology by leveraging Host Card Emulation (HCE), a method that allows a smartphone to act as a payment card.
With tools such as Z-NFC, X-NFC, SuperCard X, Track2NFC, attackers can clone stolen card data and perform unauthorized transactions using NFC-enabled devices. These tools are widely available in underground forums and private messaging groups. The resulting fraud is difficult to detect, as the transactions appear to originate from trusted, authenticated devices. In markets like the Philippines, where contactless payment usage is rising and low-value transactions often bypass PIN verification, such attacks are harder to trace and stop in real time.
Resecurity’s analysis highlights that Southeast Asia has become a testing ground for NFC fraud, with groups targeting regional banks and financial service providers.
While the Philippines is not explicitly named in public underground communications, several indicators point to increasing risk:
• Widespread use of mobile wallets and NFC-based services, including GCash, Maya, and banking apps.
• Expansion of contactless POS infrastructure, particularly among small and medium-sized enterprises.
• Inconsistent onboarding and due diligence practices for merchants and terminal distributors.
• Increased chatter in dark web communities referencing Filipino-issued card data and tools for use in the region.
These factors suggest that attackers are actively exploring vulnerabilities in the Philippine payment ecosystem.
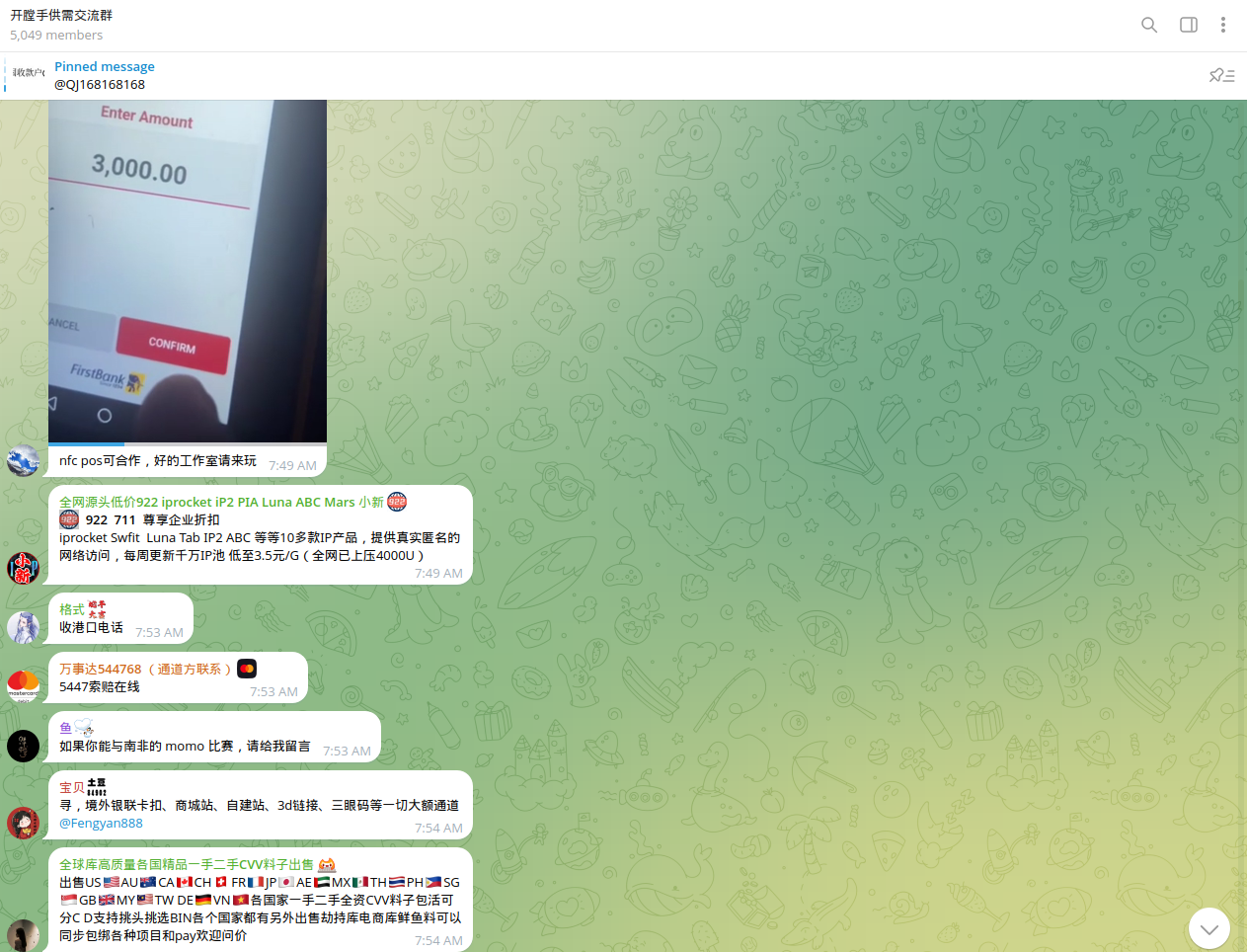
POS Terminals Used to Launder Funds
Another key trend observed by Resecurity is the use of NFC-enabled POS terminals to process transactions with stolen payment data. These terminals are often registered under fake businesses or individuals who were recruited, sometimes unknowingly, as money mules.
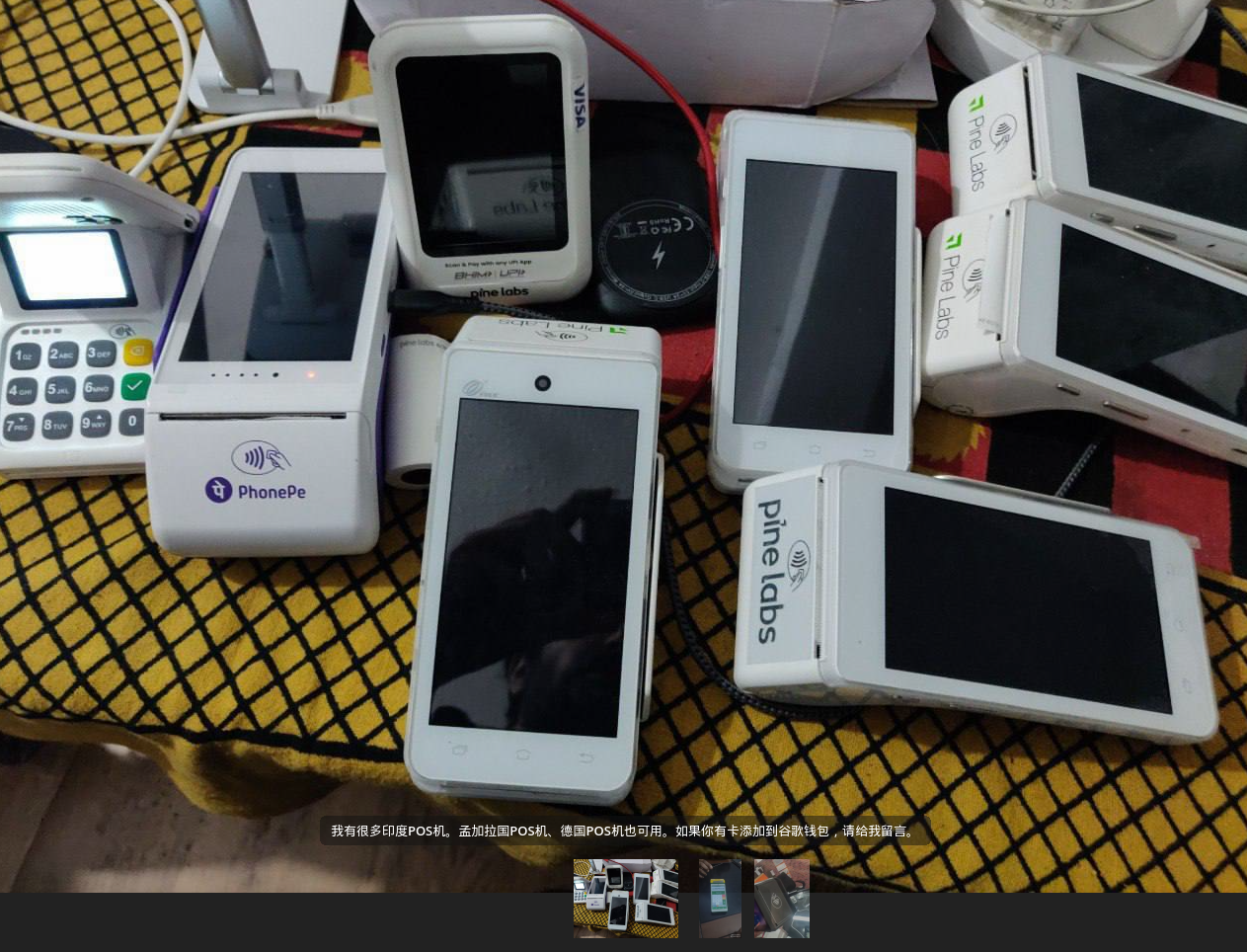
Once activated, the terminals are used to withdraw funds by simulating legitimate retail transactions.
In many cases, the terminals are pre-configured with malicious software and sold online with eSIM connectivity. This allows them to operate independently from any specific location. Resecurity estimates that such terminals can facilitate between $25,000 and $80,000 USD per day in fraudulent payments, depending on the merchant profile and transaction limits.
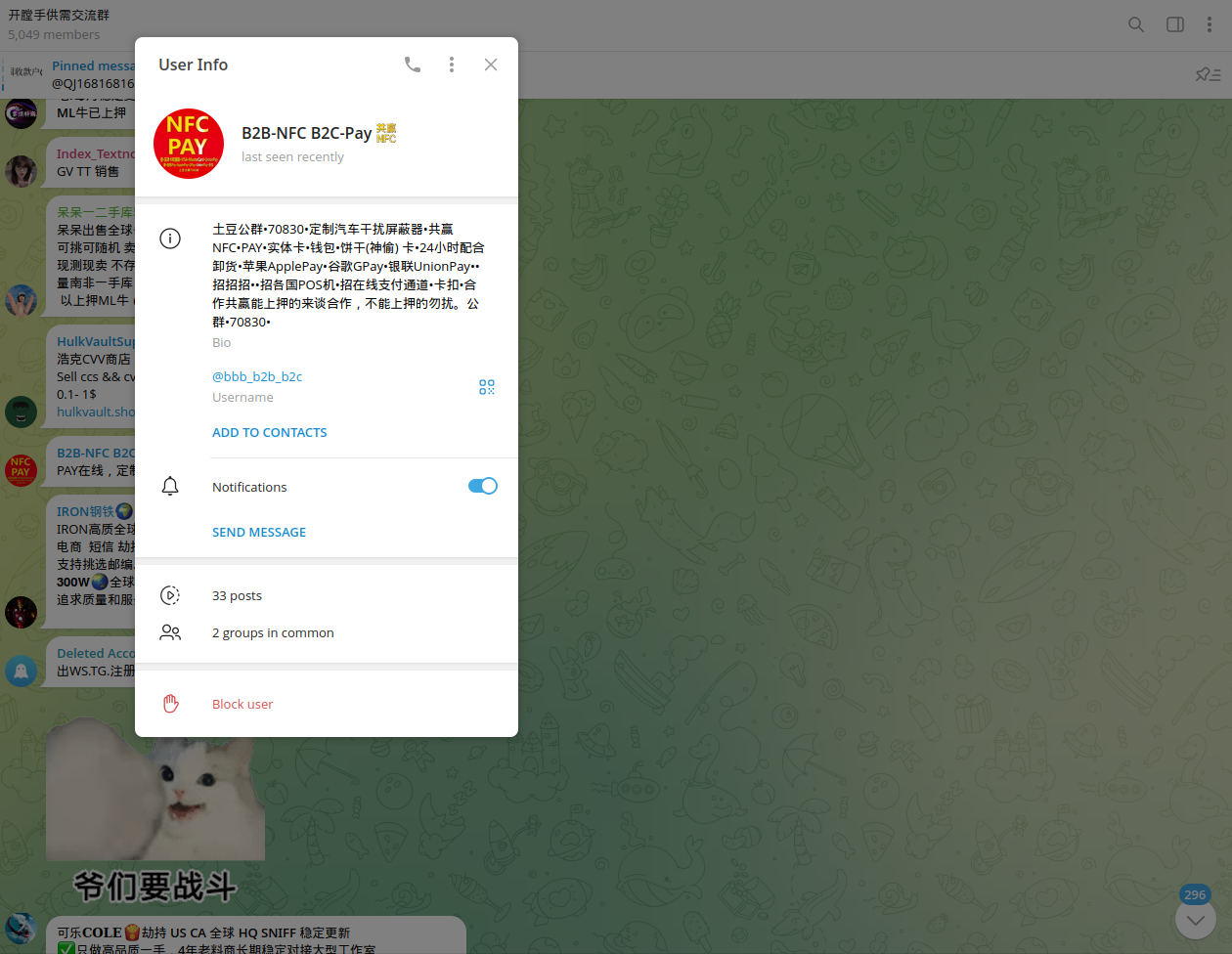
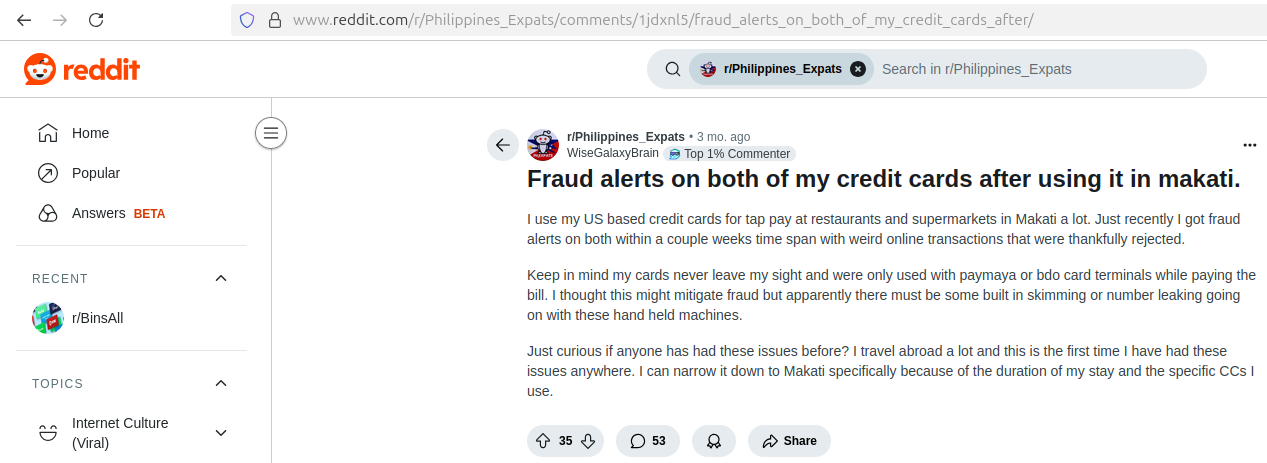
This type of laundering infrastructure is especially dangerous because it blends into legitimate financial flows, making detection more complex. It is common for such POS terminals to be deployed in restaurant chains, where visitors may not suspect any wrongdoing by staff. Chinese cybercriminals are recruiting insiders for fraudulent purposes, sharing commissions with them from illegally processed (stolen) funds. For example, multiple fraud reports have recently been observed referencing local restaurants and retail outlets with NFC-enabled POS terminals:
Recommendations for Financial Institutions and Regulators
Given the pace at which contactless technology is being adopted, it is essential for financial institutions, regulators, and service providers in the Philippines to take proactive steps to prevent misuse.
Key recommendations include:
• Strengthen merchant onboarding procedures for POS devices, with a focus on geolocation validation, industry classification, and transaction monitoring.
• Deploy behavioral analytics and anomaly detection to identify suspicious activity in tap-and-go payments, especially repeated low-value transactions.
• Expand public-private collaboration, including intelligence sharing with the Bangko Sentral ng Pilipinas (BSP), Cybercrime Investigation and Coordinating Center (CICC), and financial institutions.
• Enhance dark web monitoring capabilities to track emerging threats, cloned card data, and merchant abuse related to local institutions.
• Improve consumer education around NFC wallet security, unauthorized device pairing, and card data protection.
These measures can help close existing gaps and reduce exposure to emerging fraud schemes.
Conclusion
The evolution of NFC-enabled fraud represents a growing challenge for the Philippine financial sector. As attackers continue to develop new tools and tactics, institutions must adopt a more intelligence-driven approach to payment security.
Resecurity is actively supporting organizations in the region with tools for threat detection, fraud prevention, and digital risk monitoring. By identifying threats early and improving coordination between stakeholders, the Philippines can strengthen its defenses and maintain confidence in its digital payment infrastructure.

