#OpIsrael, #FreePalestine And #OpSaudiArabia - How Cyber-Threat Actors Coordinate PSYOPS Campaigns with Kinetic Military Actions
Cyber Threat Landscape


The unprecedented scale of Palestinian militant group Hamas’ horrific strikes on Israel this past Saturday has shocked world leaders, business communities, and people across the globe. Hamas’ complex and meticulously plotted morning rampage coincided with the start of the Simchat Torah Jewish holiday.
Gaza militants used bulldozers, hang gliders, and motorbikes to slip past Israel’s high-tech iron wall and take various border towns and Jewish settlements by storm. Hamas fighters killed 700 Israelis and abducted dozens of soldiers and civilians, including women, children, and elderly people. These strikes also transpired just one day after the 50th anniversary of the surprise joint-attack staged by Egypt and Syria against Israel in 1973 that launched the historic Yom Kippur War.
Israel has responded to the carnage by formally declaring war on Hamas. Thus far, the Israeli military has struck more than 800 targets in Gaza, killing some 400 Palestinians, according to media reports. With some 130 Israelis reportedly being held hostage in Gaza, the majority of whom are civilians, the Israeli military is under extraordinary pressure to exercise caution in their counterstrikes against suspected Hamas targets.
Resecurity strongly opposes war irrespective of political agendas, religious motivations, or geoeconomic ambitions. We support all our colleagues, partners, and their families impacted by these tragic events. Resecurity hopes that a peaceful resolution to current Israeli-Palestinian hostilities is achieved as quickly as possible.
Yet, as Gaza has once again erupted into a full-blown war zone, cyberspace has also emerged as a theater of combat. Resecurity has identified malicious actors exploiting the conflict to weaponize psychological operations (PSYOPs) campaigns that appear to be interlinked with Hamas’ vicious, shock-and-awe offensive.
Resecurity identified these malign actors and their geopolitically coordinated PSYOP campaigns via the collection of cyber threat intelligence (CTI) from the Dark Web and multi-dimensional OSINT sources. The questions that emerge are: Who is behind this activity, and who is profiting from it? Determining the answers to these questions poses two significant riddles to the international Intelligence Community (IC).
PSYOPs are military-grade influence campaigns that adversaries weaponize to convey selective information and facts to manipulate public opinion. While some PSYOP conspirators completely fabricate narratives and amplify them through low-authority, but high-exposure accounts on social media, the majority beguile audiences through lies of omission.
Malicious actors exploiting this tactic will, for example, present one side of a geopolitical dispute, while withholding crucial context or omitting the full chain of causations or correlations that may have contributed to a disagreement. Overall, these orchestrated, reality-distortion campaigns are projected through memes, emotionally manipulative messaging, willfully malign influencers, and so-called ‘useful idiots.’
Today, psychologically exploitative narratives are amplified through fake accounts (bots), malicious influencers, ‘micro-influencers,’ and targeted social media communities where threat actors reason they can maximize the ‘network effect’ of their malign messaging. PSYOPs ultimately attack the collective mind of a specified generational demographic or social cohort with the aim of altering the behavior of governments and other institutional power centers.
In the context of the rapidly evolving war between Israel and Hamas, it is notable that some of this malign PSYOP activity began to accelerate the week before Palestinian militants struck. Threat actors operating under the guise of hacktivists launched the synergic, military PSYOP campaigns #OpIsrael and #FreePalestine on September 23, with the corresponding execution target date set for September 30.
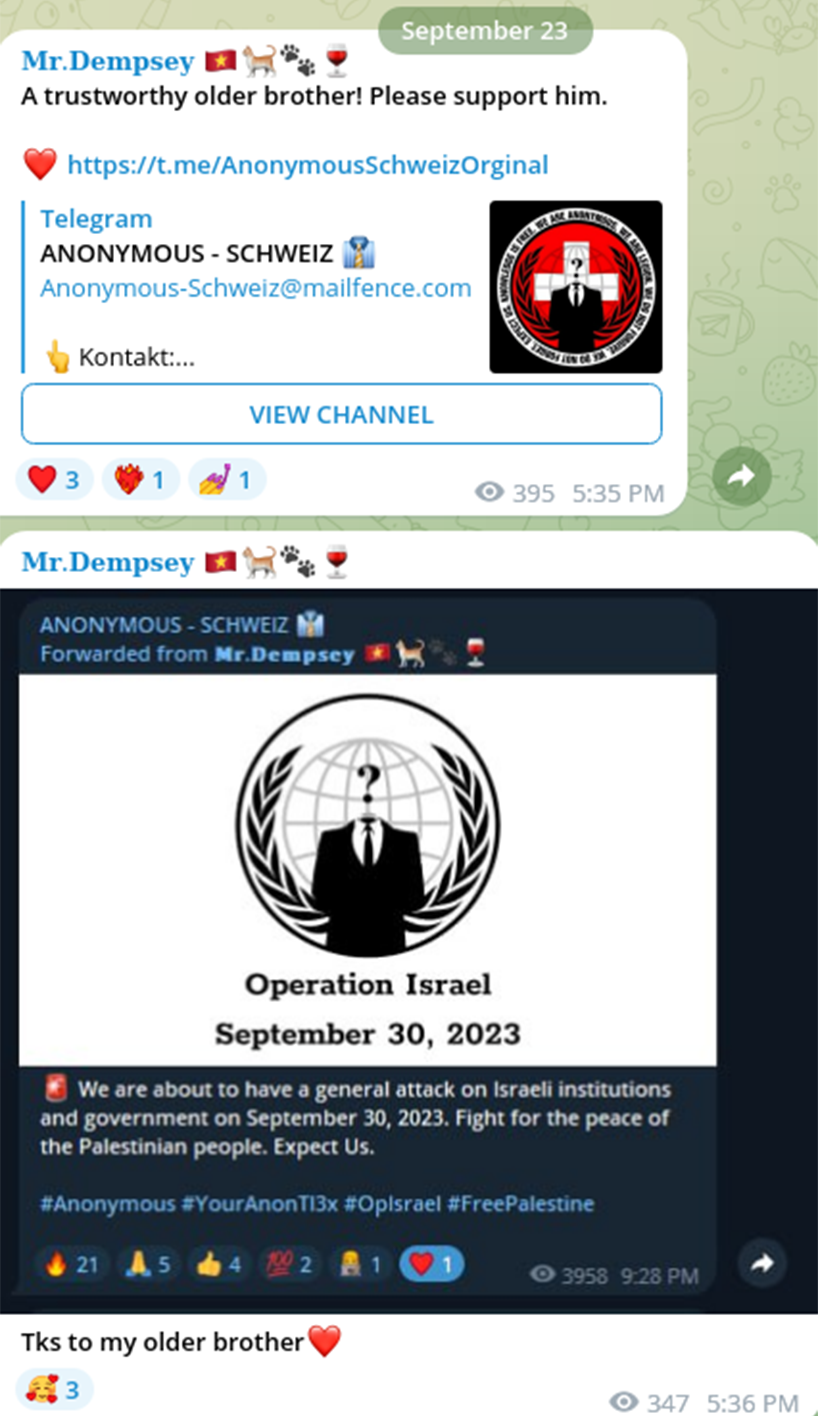
The actor using the alias, 'Mr.Dempsey,' identified himself as a "cybersecurity journalist". Mr. Dempsey began distributing narratives via the Telegram group, @YourAnonTl3x, which was created September 5. Messages posted in this TG channel were relayed to Twitter to encourage various hacktivist groups to join forces in cyberattacks against Israel. These hacktivist groups include:
- MysteriousTeamBangladesh
- Team_Insane_Pakistan
- EagleCyberCrew
- AnonGhostTeam
- HackerFactoryGroup
- K0lzSecTeam
- Stucxteam
- KhalifahCyberCrew
- VSO_Zone
It is very likely the actor expected a coalition in order to drive the campaign further. The efforts to influence other hacktivist groups failed, as none of them contributed with any meaningful attack afterwards.
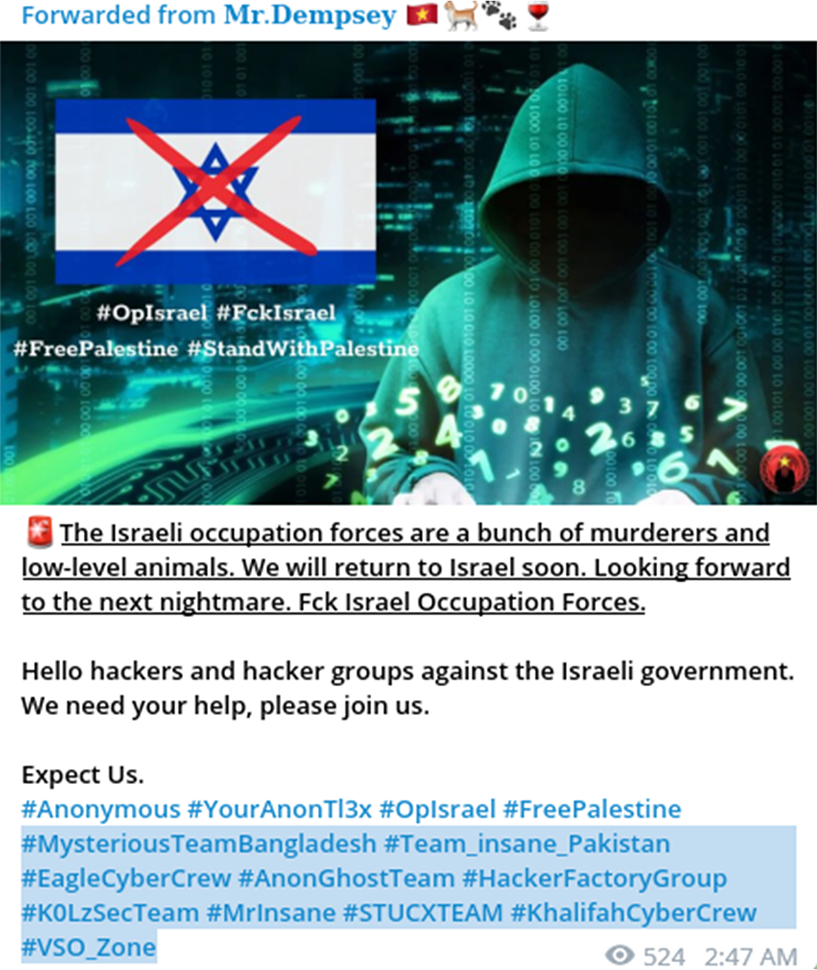
Later, the Mr.Dempsey account repeated the same PSYOP-amplification attempt on Facebook, expanding their recruitment campaign to include additional hacktivist groups operating out of Bangladesh, Malaysia, and Pakistan. It should be noted that all three countries are predominantly Muslim.
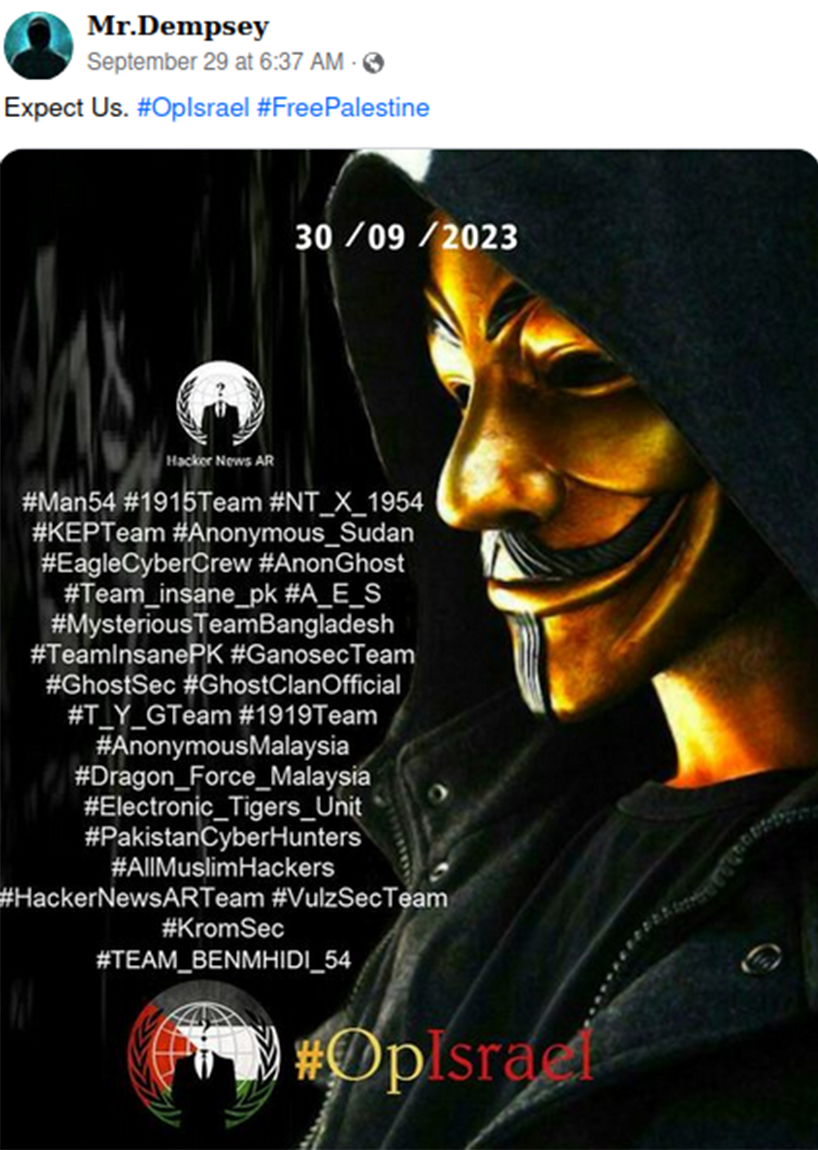
Prior to this activity, Mr.Demspey was involved in #OpIndia, a malign, crowd-sourced DDoS campaign that targeted government and financial institutions in India. The campaign was likely orchestrated with the help of other hacktivists, including independent actors recruited to perform website defacements and DDoS attacks.
On October 4, approximately 3 days prior to the Hamas attacks, Mr.Dempsey announced the launch of an anti-Saudi Arabia government initiative and related cyberattack campaign #OpSaudiArabia / #FreeSaudiArabia. This attack campaign sought to portray the Kingdom of Saudi Arabia (KSA) as an “unfair” country. The threat actor didn't specify any motive behind their desire to coordinate cyberattacks against the KSA at that stage.
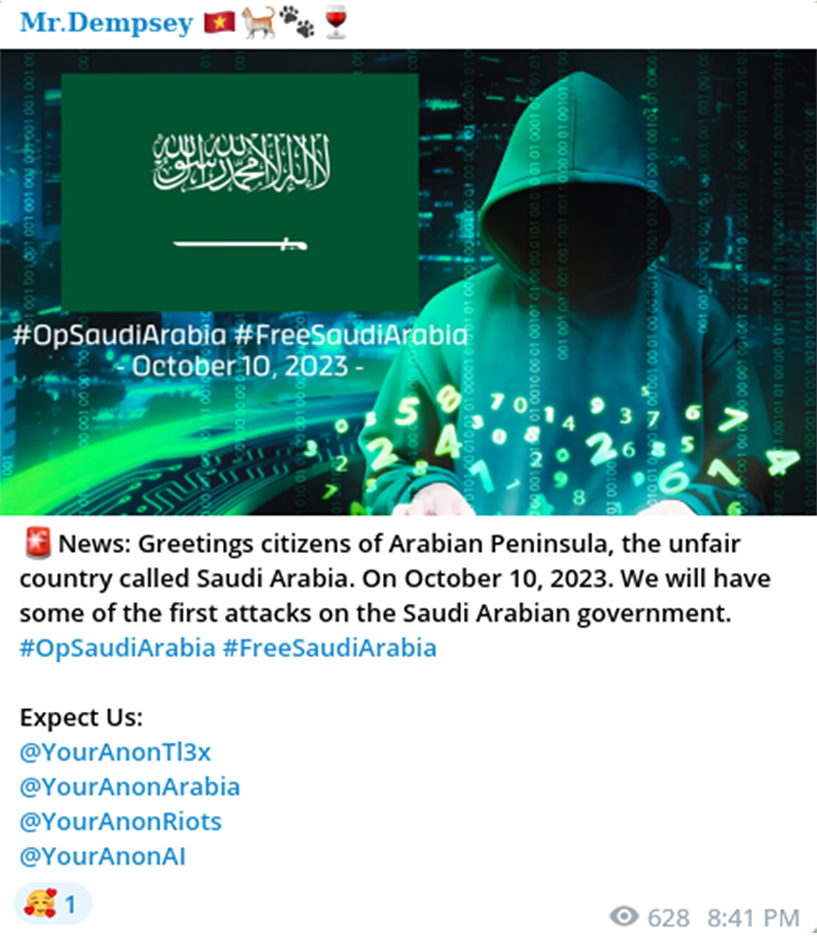
On October 6, Mr. Dempsey linked an alleged DDoS attack against the Saudi Arabian Public Transport Authority to their negative opinion about cooperation between Saudi Arabia and Israel. The threat actor posted screenshots, which purportedly displayed a successful "short-term" DDOS attack against the SAPTA. From this moment, the actor extensively began using the tags #OpIsrael and #FreePalestine in addition to the previous ones used. Mr.Dempsey’s goal was to amplify a targeted geopolitical narrative.
Mr.Dempsey also claimed Saudi Arabia's Ministry of Defense (MoD) as another DDoS attack victim. In reality, the attack didn't affect any critical systems or the network availability of MoD web resources. We can thus interpret this incident as an attempted "short-term" DDOS attack.
On the same day, Mr.Dempsey made several regionally divisive insinuations targeting KSA leadership. Resecurity assesses that Mr.Dempsey’s primary objective was not specifically related to successful DDoS campaigns. Instead, this threat actor was looking to manufacture and promote a distorted geopolitical narrative via social media and Telegram groups.
Mr.Dempsey also forwarded several postings published by hacktivist group Anonymous Sudan, who has promoted and engaged in similar narratives and campaigns. In the past, the group performed similar short-term DDoS attacks against a variety of government and private-sector resources to raise global awareness for the outbreak of war between the Sudanese Armed Forces and the paramilitary Rapid Support Forces.
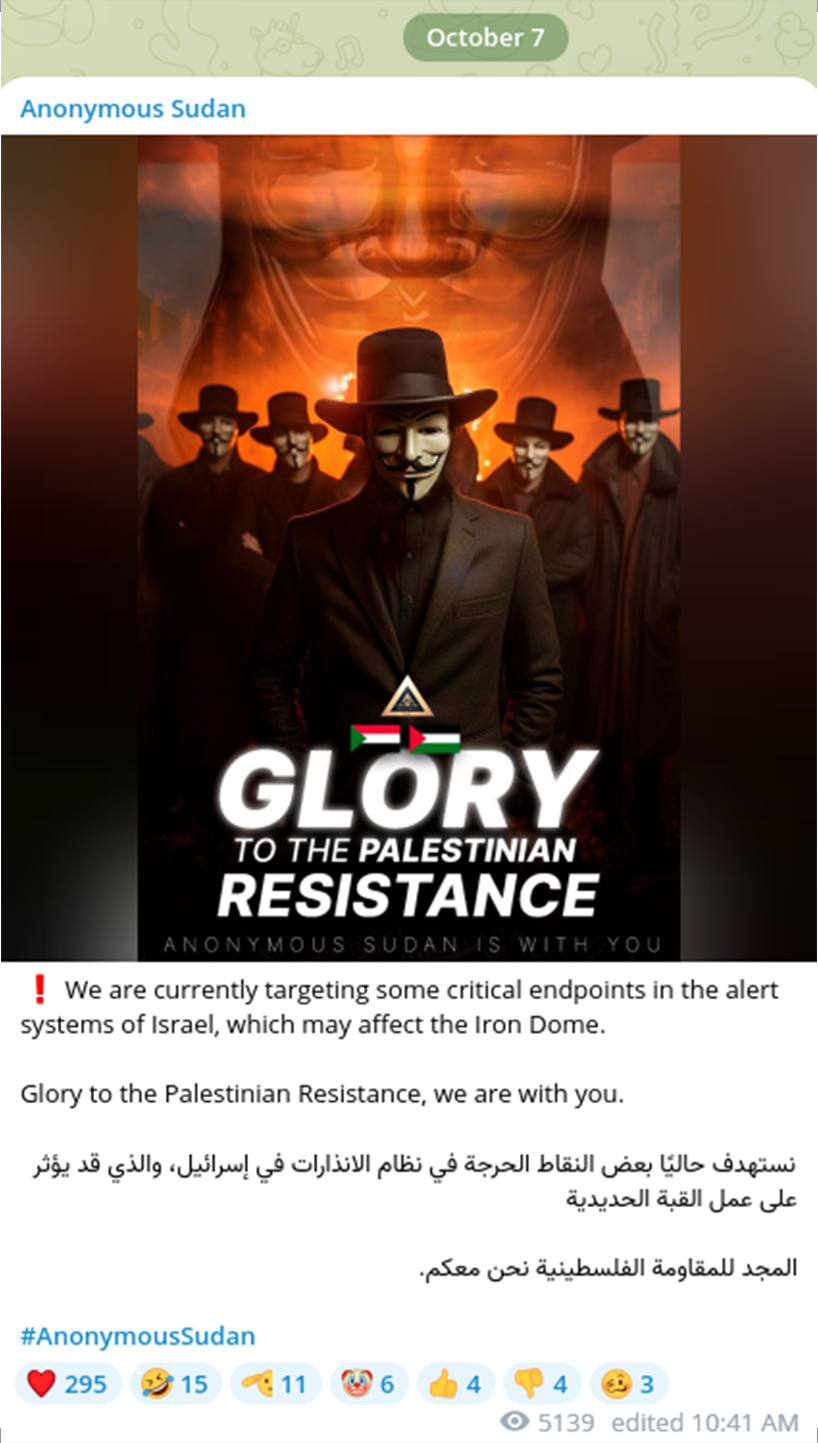
In their community chat group, Anonymous Sudan referenced the overhyped hacktivist group, Killnet, and accused the Israeli government of supporting Ukraine and betraying Russia. The statement was published in both Hebrew and Russian.
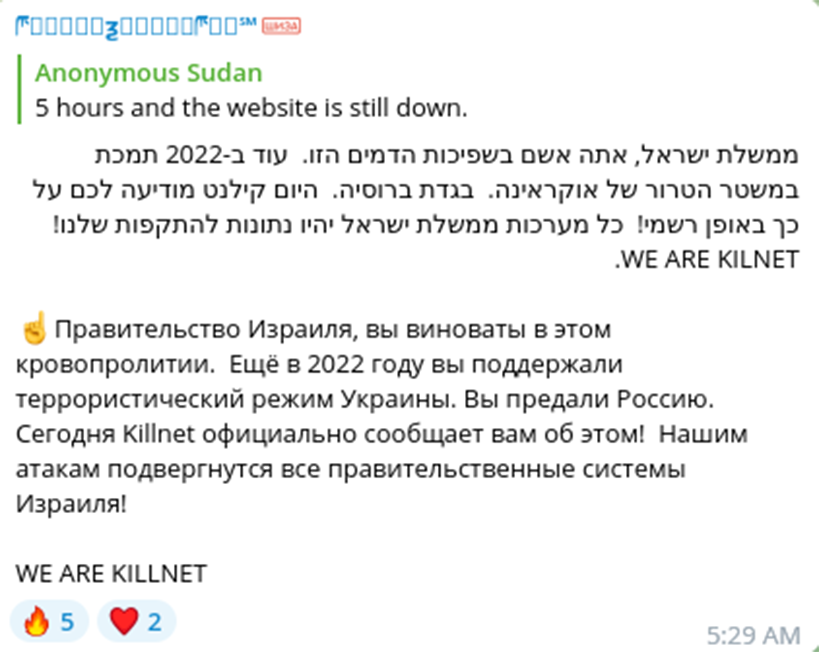
Interestingly, both Anonymous Sudan and Killnet use the same graphics with minor adjustments for the new pro-Palestinian campaign. These efforts may be jointly coordinated. Attributing this activity to a particular nation-state is complicated by the possibility of culprits operationalizing 'false flag’ tactics to sew confusion and frame sovereign actors that might seem the most obvious at first glance.

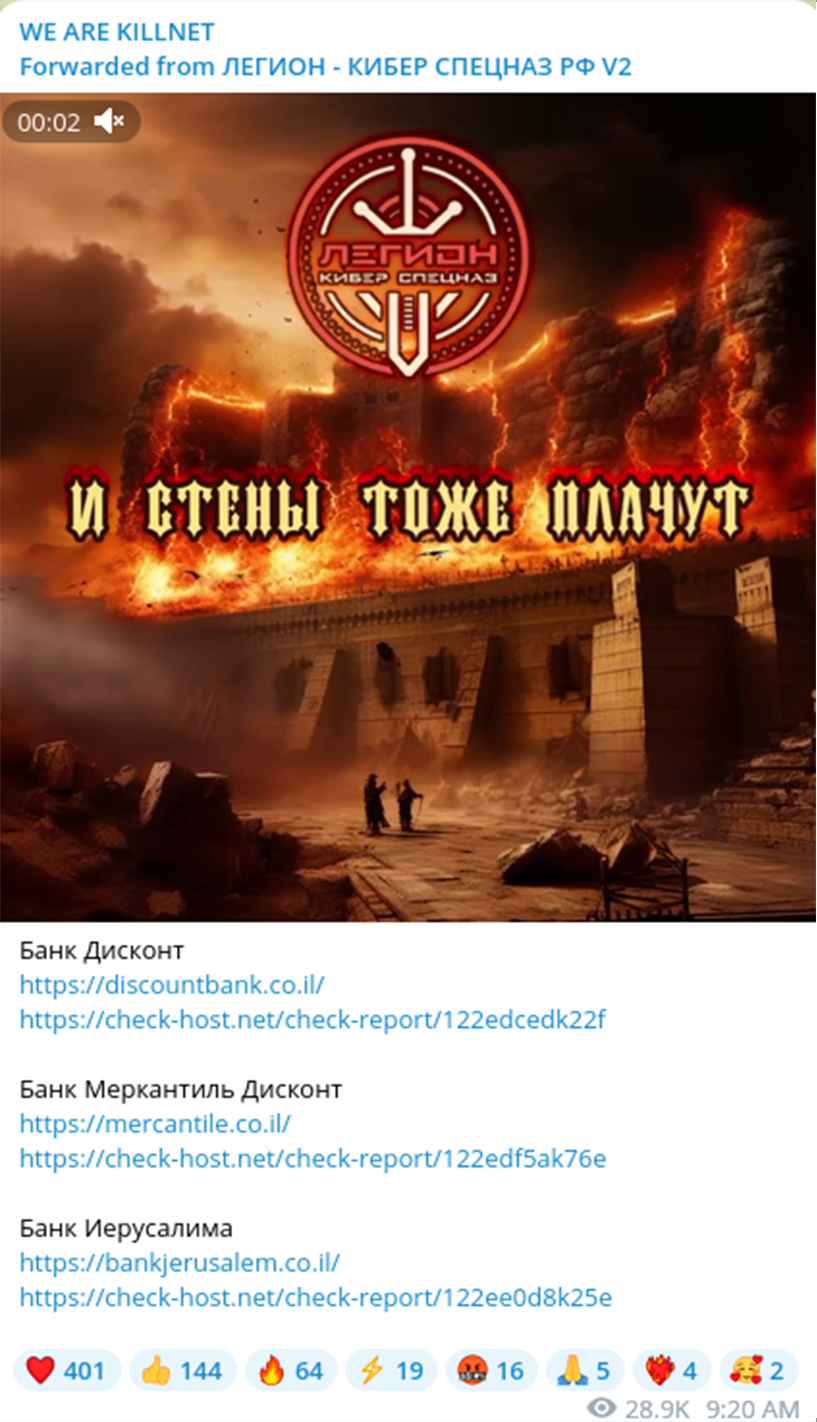
Following the Killnet announcement, another hacktivist group called Legion (Cyber Spetsnaz), which gained infamy for its successful cyberattacks against NATO and government resources in Ukraine, launched DDoS attacks against major financial institutions in Israel.
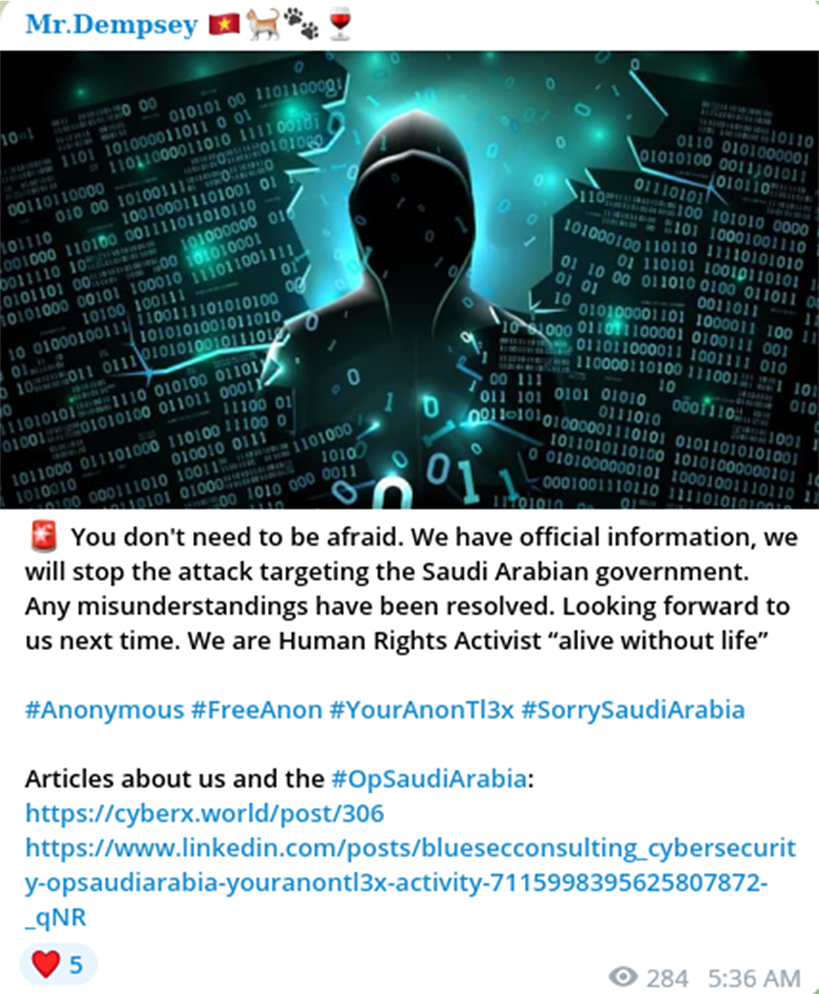
October 7, after a significant media narrative began to emerge, Mr.Dempsey made an announcement calling off attacks against Saudi Arabia.
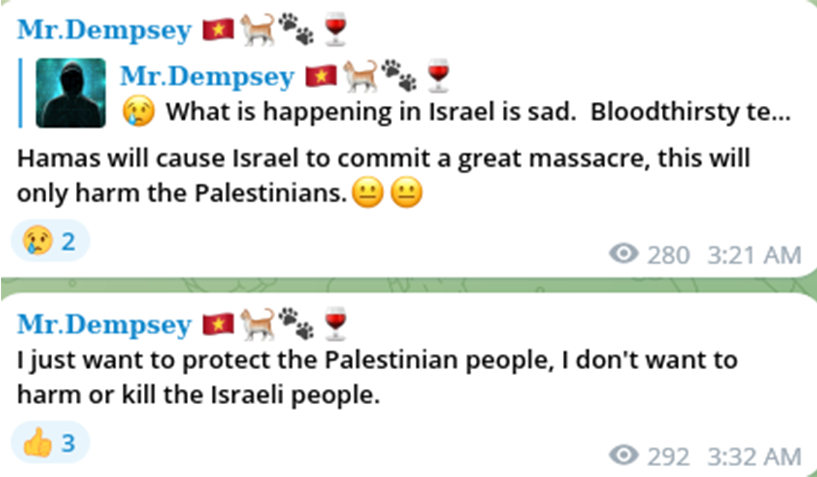
After the KSA media narrative flamed out, Mr.Demspey also 'exited' from one campaign involving the Gaza conflict.
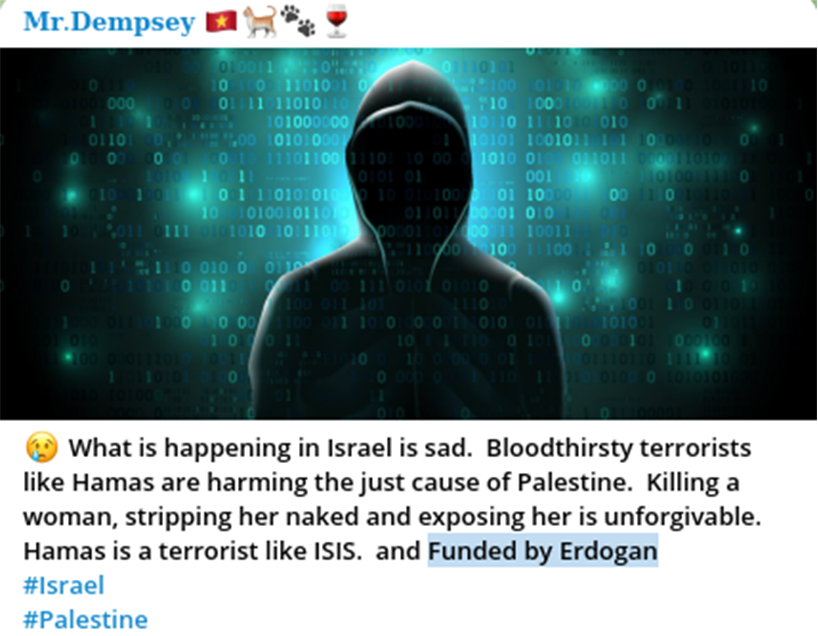
Prior to Mr.Dempsey’s apparent change of heart, they shifted their narrative by implicating Turkish President Recept Erdogan as a significant Hamas supporter. Resecurity assesses that Mr.Dempsey was likely probing his online audience’s responsiveness to contrasting geopolitical narratives to see which resonated most with them.
This approach is similar to the ‘A/B testing’ method used in traditional marketing campaigns, which helps brands identify the most effective form of consumer messaging. The sentiment of Mr.Dempsey’s posts has also changed from being anti-Israel to one of anti-hostility and remorse as it pertains to the rapidly escalating Gaza conflict.
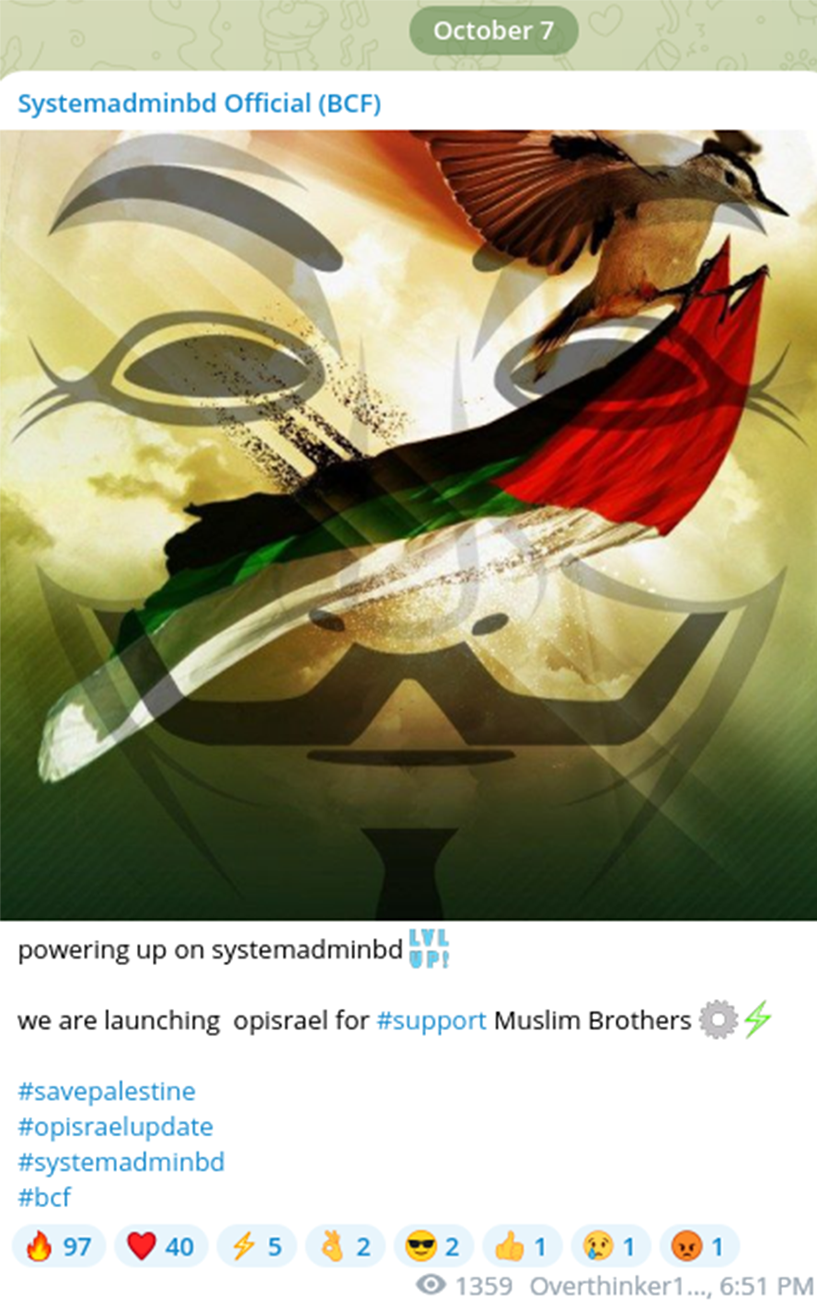
Based on Resecurity’s analysis of other Telegram groups that Mr.Dempsey interacted with, HUNTER (HUMINT) investigators identified additional actors collaborating with #OpIsrael and #FreePalestine propogandists. These threat actors call themselves ‘Systemadminbd Spy Agents’ and likely originate from Bangladesh. Bangladesh is a predominantly Muslim country with nearly 90% of the population identifying as such.
Systemadminbd Spy Agents used the following symbol on their official profile page(s) and for various website defacements:

The group announced the launch of a cyberattack against Israeli web resources accompanied by the tags #SavePalestine and #OpIsraelUpdate.
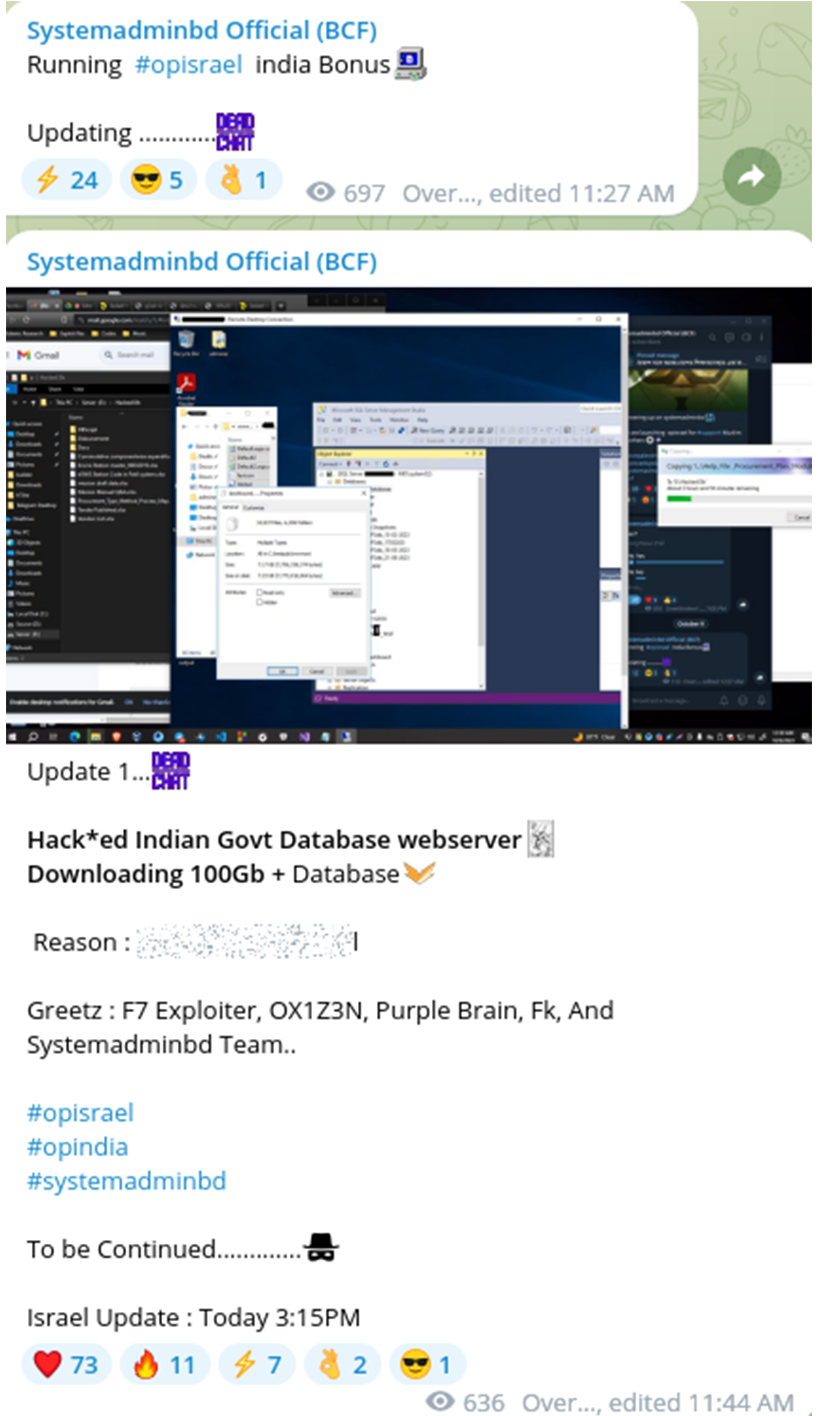
Notably, these threat actors also discussed targeting organizations in India. Other hacktivist groups also joined Systemadminbd Spy Agents proposed, India-focused cyberattack campaign.
Around April 15, 2023, Systemadminbd Spy Agents claimed to leak data from the Mossad, Israel’s national intelligence agency. This claim proved to be false. In reality, the leaked archive contained samples of data stolen from multiple private-sector organizations. Victims exposed in this leak included an aerospace and defense contractor with an office in the U.S. and a company that produces portable power and energy management systems.

While Systemadminbd Spy Agents’ Mossad leak turned out be a dud, Blackfield, a higher-credibility threat actor, recently solicited access to a data leak on the Russian Anonymous Market Place (RAMP) cybercriminal forum that purports to expose the private information of hundreds of Israel Defense Forces soldiers and some Shabak (Shin Bet – Israel Security Agency) members.
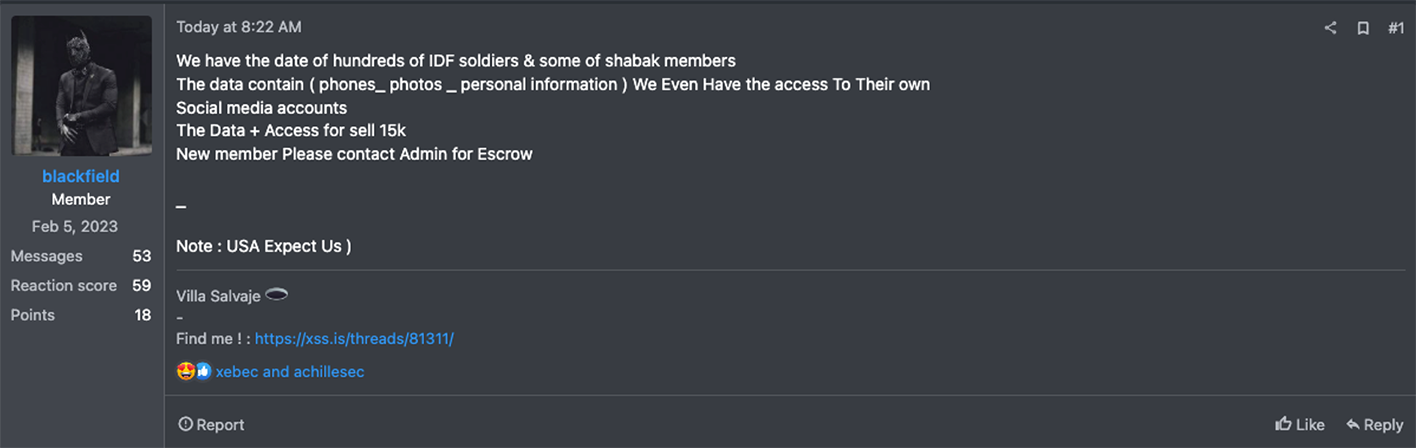
While this threat actor has typically been associated with cybercrime and selling access, it is interesting that they end their post with the following: “Note USA Expect Us.” The phrase, “expect us,” has effectively been trademarked by the Anonymous hacktivist collective.
However, the fact that the threat actor concludes that line with a closed-loop parentheses, which is often used colloquially to signify a ‘smiley face’ in Russian and CIS digital parlance, obviously indicates they are not aligned with pro-Western hacktivist causes.
Another variant of psychological warfare noted by Resecurity analysts was the impersonation of high-authority Israeli news organizations. In this case, threat actors impersonated the official Telegram of Yedioth Ahronoth (Latest News), Israel’s largest paid newspaper in terms of sales and circulation.
While the real Ynetnews Telegram channel counts 316,257 subscribers and posts exclusively in Hebrew, the malicious account only registers 8,623 followers and spreads anti-Israel propaganda in English.
In the above post, dated October 10, the threat actor managing the fake Yediot News TG channel promotes a narrative accusing “Zionist immigrants” of dropping “forbidden white phosphorous bombs on the Palestinian people.” Obviously, referring to Israelis as Zionist immigrants inherently discredits the concept of Jewish statehood.
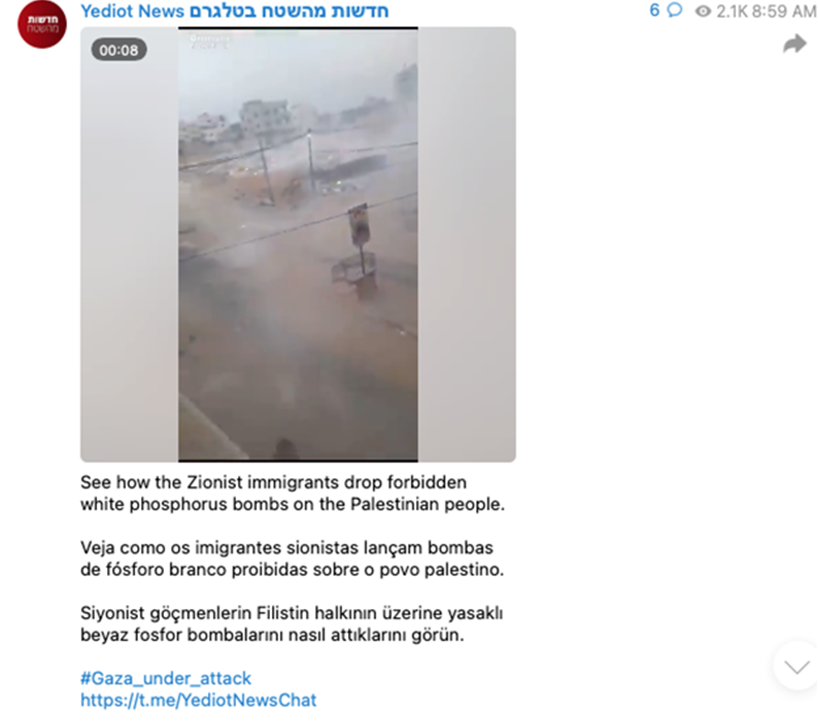
Also, Israel’s use of banned phosphorous munitions remains an unverified allegation, despite the circulation of videos that can easily be manipulated with modern digital tools. More broadly, this messaging is conveyed in three languages, English, Portuguese, and Turkish. Notably, the white phosphorous bombing-campaign narrative can be traced back to an October 9th story published in Iranian media outlet PressTV.
The Iranian nexus of the messaging in the fake Yediot News channel is also visible in the Telegram post below. Here, the channel is promoting a speech by the Secretary General of Lebanon’s Hezbollah. Although Hezbollah boasts a strong presence in Lebanon, their strongest base of state-sponsored support comes from Iran.
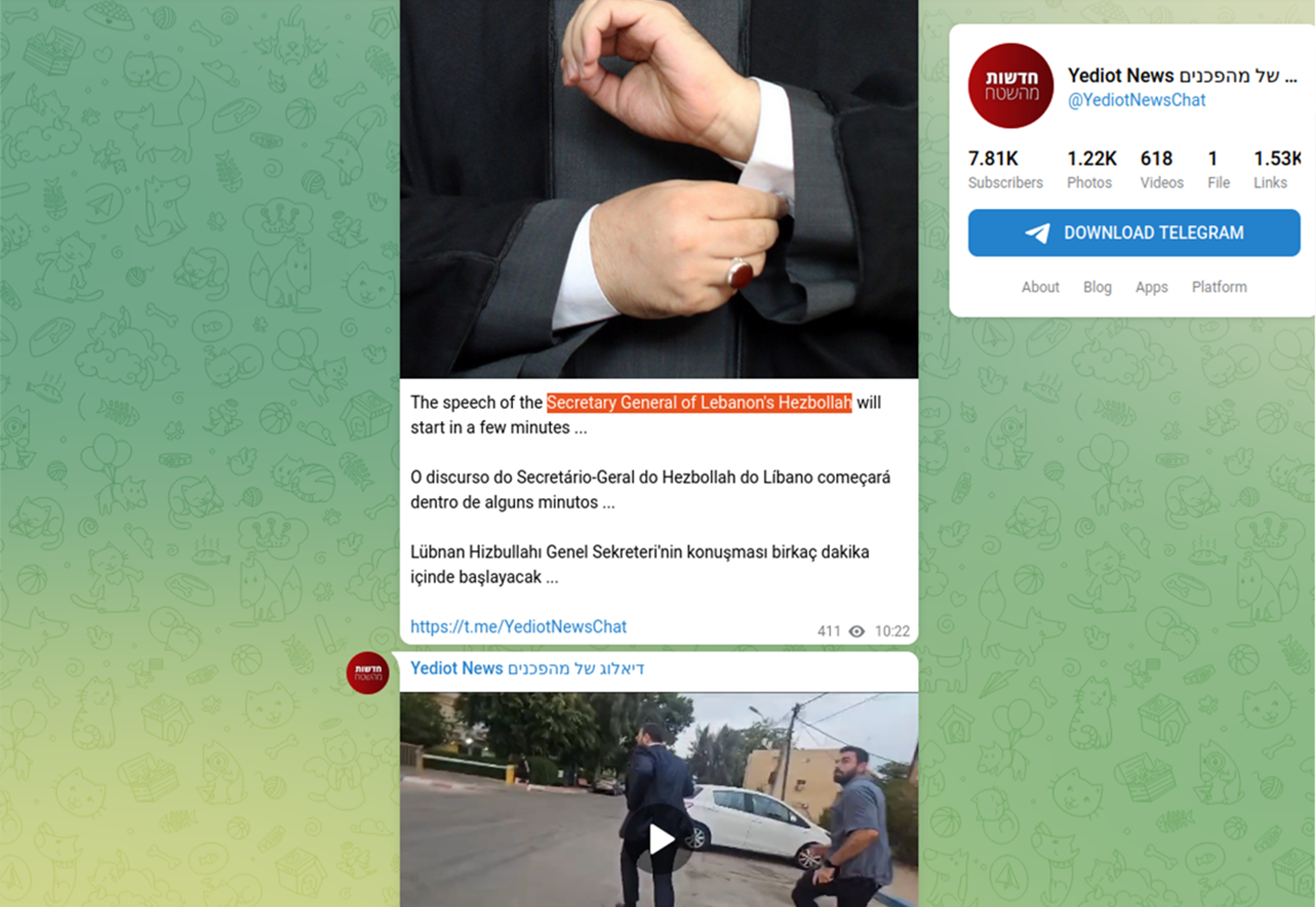
The identified Telegram channel promoted propaganda against Israeli population using per-defined narratives.
Ultimately, the impersonation of official media channels on Telegram is just a modern messaging tactic to conduct conventional military PSYOPs and alter the enemy's state of mind through non-combative means (such as distribution of leaflets offline or specific publications online).
Besides these ongoing PSYOPs, threat researchers have recently observed several Israel-related data breaches and targeted network intrusions. For example, Microsoft linked a Gaza-based threat actor tracked as Storm-1133 to a series of attacks aimed at private organizations in Israel earlier this month.
Conclusion:
- Current Israel-Palestine tensions involve similar patterns of malicious cyber-and-information warfare, which were also observed during the Ukraine-Russia war, as well as the Sudan war;
- The actors involved in malicious cyber-activity during major geopolitical conflicts aim to conduct sophisticated psychological operations (PSYOPs) to amplify a particular narrative via easily accessible digital media channels, rather than performing actual cyberattacks;
- Cyberspace reflects modern geopolitics. Cyber-threat actors leverage psychological tactics, techniques, and procedures (TTPs) oriented towards disinformation and influence campaigns to impact public opinion regarding geopolitical events and military conflicts.

