Misinformation and Hacktivist Campaigns Target the Philippines Amidst Rising Tensions with China
Cyber Threat Intelligence


Intro
The Philippines is one of 18 countries designated by the U.S. as a Major Non-NATO Ally (MNNA). The Philippines’ strategically vital location bordering the South China Sea (SCS) places it at growing risk of a military confrontation with China. Amidst a series of escalating clashes between Chinese and Philippine vessels in the SCS, China has recently asserted “indisputable sovereignty” over the maritime area that encompasses the Second Thomas Shoal. China’s bellicose actions and rhetoric in this area have infringed on the Philippines' “exclusive economic zone,” according to Philippine Foreign Minister Enrique Manalo. In this geopolitical backdrop, related malicious cyber activity is concurrently increasing. The Philippines is vital to U.S. national security interests in the Indo-Pacific region, which places the island country in the crosshairs of foreign cyber actors who are hostile to American influence in this geography. Threats targeting shipping supply chains are also rising, as the Philippines is located at the center of China’s, Japan’s, and Australia’s maritime trade routes. With its proximity to Taiwan and its central location bridging the SCS with the Pacific Ocean, the Philippines is a crucial U.S. ally. In the event of a major conflict with China, the island country would be a key military resupply point for Western forces. Additionally, in wartime, the Philippines could also serve as a key hub to control naval chokepoints in the SCS. The lasting alliance between the Philippines and the US was cemented by the Mutual Defense Treaty of 1951, which obligates each nation to aid the other in an attack by a third party.
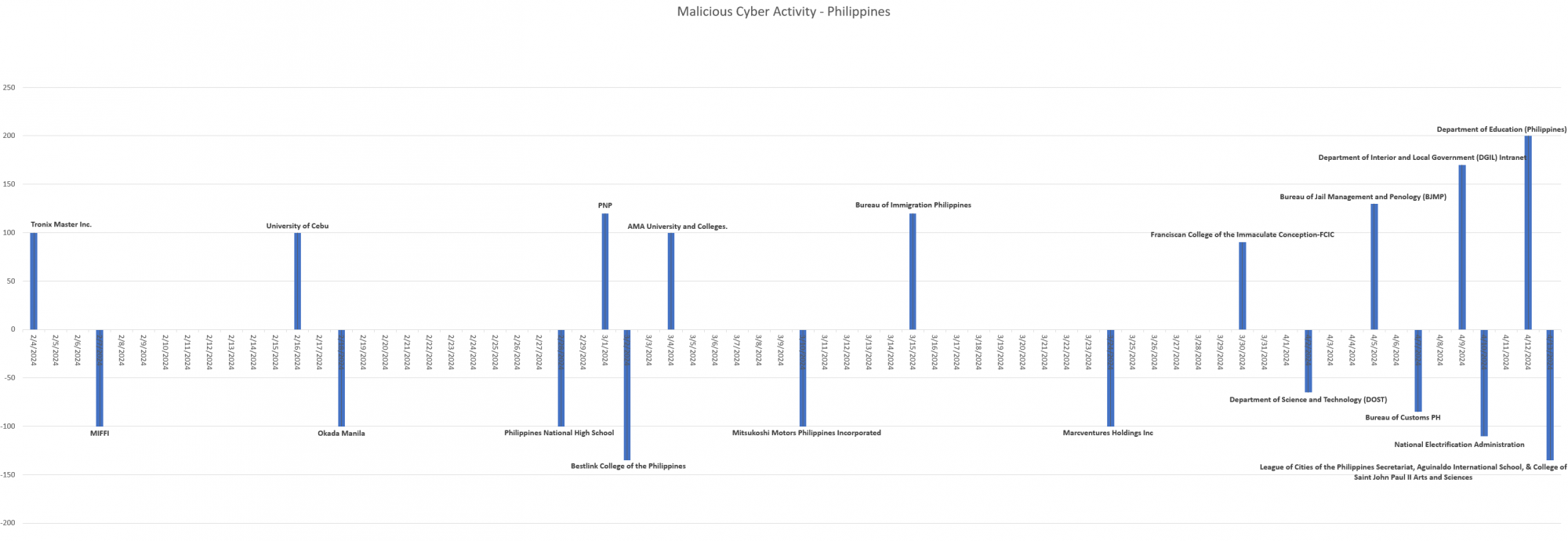
Amidst rising tensions with China in the SCS, Resecurity has observed a significant spike in malicious cyber activity targeting the Philippines in Q1 2024, increasing nearly 325% compared to the same period last year. The number of cyberattacks targeting the Philippines involving hacktivist groups and foreign misinformation campaigns has nearly tripled. In Q2 2024, this growth trajectory continues, with Resecurity observing multiple cyberattacks staged by previously unknown threat actors. These attacks are characterized by the intersection of ideological "hacktivist" motivations and nation-state-sponsored propaganda. One prolific example of this dynamic is the China-linked Mustang Panda group, which Resecurity observed using cyberspace to stage sophisticated information warfare campaigns. There is a thin line between cybercriminal activity (supported by the state) and nation-state actors engaging in malicious cyber activity. Leveraging hacktivist-related monikers allows threat actors to avoid attribution while creating the perception of homegrown social conflict online. This tactic is often combined with false-flag attacks originating under publicly known threat-actor profiles to keep a distance from the real intellectual authors of these malign campaigns.
Resecurity interprets this activity as pre-staging for broader malicious, foreign cyber-threat actor activity in the region, including cyber espionage and targeted attacks against government agencies and critical infrastructure.
Timeline
The Underground Scene
The underground ecosystem is quite diverse and unique. This adversarial universe involves multiple local and foreign threat groups known for past attacks against government agencies and major enterprises during local conflicts and military engagements.

One of the most notable groups in this ecosystem is Exodus Security. The group was founded on February 4, 2009. Initially, Exodus Security had a compact structure consisting exclusively of red-team (penetration-testing) specialists. However, the group became a high-profile hacktivist collective responsible for major cyberattacks against government agencies and enterprises in the Philippines and globally. On approximately February 15, 2024, the group started recruiting new members with experience in penetration testing and web-application hacking.

This past February, the group staged multiple targeted DDoS attacks. It leaked stolen data from targets in the Philippines and other countries, including the UK, France, Indonesia, Israel, and India. The group also announced several partnerships with other actors, including:
- Cyber Operation Alliance (COA)

- Robin Cyber Hood (RCH)

- Arab Anonymous

- Sylhet Gang-SG

There are some visible synergies between these groups as noted by their stated ideological motives, especially in the context of the ongoing Israel-Gaza conflict.
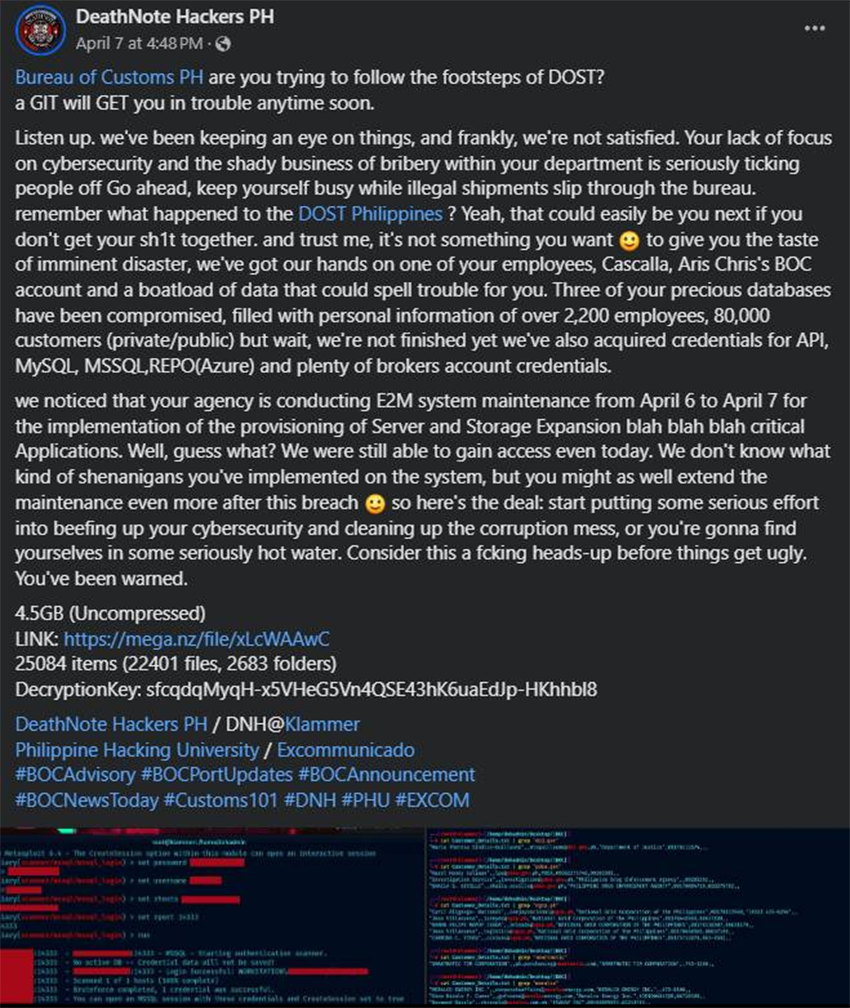
Another notable local group is DeathNote Hackers (Philippines). The group was likely responsible for a data leak from the Bureau of Customs under the flag of the #OPBOC campaign, which trended on social media and in notable hacktivist communities.
According to their WEB-site, the group emerged almost 15 years ago. Notably, the group transformed from a relatively small player into an active agitator of major cyber conflict. For example, the group actively supports Ukraine and defended their infrastructure in the ongoing conflict with Russia.

| Deathnote Hackers (DNH), formed 2015, but officially founded in 2016 by TATAY45. It initially started as a hacking tutorial page, where tricks and tips were shared. However, it quickly evolved into a hacking group when tatay45 acquired knowledge in unethical hacking, programming, and SEO. After discovering the international group "Lulzsec" and gaining inspiration from Lulzsec's Operation CODE:51, an operation focused on leaking any desired information, tatay45 initiated his own CODE:51. this operation primarily aimed at sharing leaked source codes. However, facing numerous challenges while working alone, tatay45 decided to establish a hacking group to facilitate his plans, leading to the birth of Deathnote-Hackers. based in Manila. by mid 2016 tatay45 started recruiting members consists of specializing in penetration testing, programming, engineers and humanitarians coming from multiple ex-members:Unirises,ZyberPh Developers,DeepWeb FAKK,Symbianize,XDA-Forums,phcorner and Anonymous Representatives coming from different parts of Manila(NCR) The group has been involved in numerous cyber-attacks,including a Distributed Denial of Service (DDOS) attack on Dragon Nest SEA, a game owned by Eyedentity Games. in 2015. the hacking group unleashed a ransomware attack on public forums. BleepingComputer first detected the ransomware in the wild on April 3rd, 2017. The group gained notoriety in the past for mocking and breaching systems of various local websites in the Philippines. the current leader, Klammer ex-member of GlobalSecurity Hackers, made her first appearance in late december 2016 as member of the group after attacking UP Diliman and Far Eastern University, click-jacking several students for a phishing campaign, on the same year klammer Appointed as the new leader after founder tatay45 decided to retire quietly. The group also targeted SM-Supermalls,DOST-pagasa,Vanguard International Semiconductor Corp.Pasig city's vaccine portal, Miami University and many more under new management. in 2022 DNH actively participated in Operation Russia and Ukraine during the cyber war, providing support to the Ukrainian side in the ongoing conflict. they played a crucial role in disrupting Russian cyberattacks and defending Ukrainian infrastructure working with anonymous member "LiteMods" from United states as well as operation japan,senegal. in 2018 issue facing accusations from a random group claiming DNH have hijacked the group-page of #PHU (Philippine Hacking University), a public facebook group dedicated to Filipino "inspired" Hacktivist, subsequent investigations revealed that Deathnote Hackers had no involvement in the incident, making them innocent. Currently, Deathnote Hackers remains an active and influential group in the Philippine's underground hacking scene or what they called "CW", constantly evolving their tactics and techniques to stay ahead of the curve. Their actions have sparked both criticism and praise, but their impact on the underground is undeniable. |
Notably, the notes left by actors also included references to other local hacktivist collectives, including
- Philippine Hacking University
The group promotes hacking activity as a form of protest.

- Excommunicado
This group removed their profiles.
One of the notable actors related to DNH (Philippines) uses the alias Klammer. The group distributed a dump of stolen data on April 9, 2024.
The leaked data referenced employees and private-sector individuals likely involved in logistics and the import/export business
Resecurity has contacted multiple victims in this dump to collect additional context about the possible origin of this leak.
CyberMafia Philippines
The group strongly collaborates with DNH and Exodus Security. Around April 10, the group targeted the National Electrification Administration.

Philippine Cyber Alliance

The Philippine Cyber Alliance (PCA) bills itself as “the new generation of Filipino Hackers founded by various PH hacker groups since November 2022.” The group gained notoriety
last year for targeting eight Pakistani websites in a DDoS campaign, including various local news outlets and the president of Pakistan’s official website.
Bisaya Cyber Army

Bisaya Cyber Army has been active since 2022. They have been linked to 46 website defacements.
LizardSquad Philippines

The group is relatively new and remains a low key profile. Currently, they are recruiting new members.
Independent Actors and Mercenaries
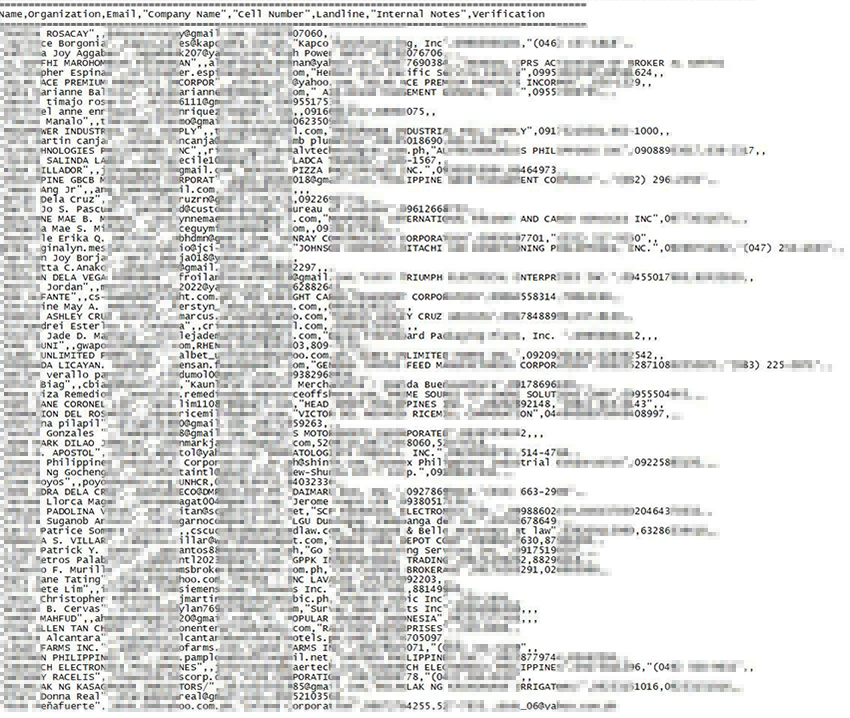
April 3, 2024 – A threat actor going by the alias "KryptonZambie" claimed over 152 gigabytes of stolen data from unnamed sources containing Philippine citizen identity cards. But are the threat actor’s claims true? The threat actor did not provide any additional context about the origin of or the motive behind the possible leak. This breach raised significant concerns for the Philippine cybersecurity community, which actively investigated the threat actor’s claims. Resecurity investigators performed a comprehensive, in-depth analysis of this leak, collaborating with local law enforcement organizations and threat-intelligence industry peers in the Philippines.
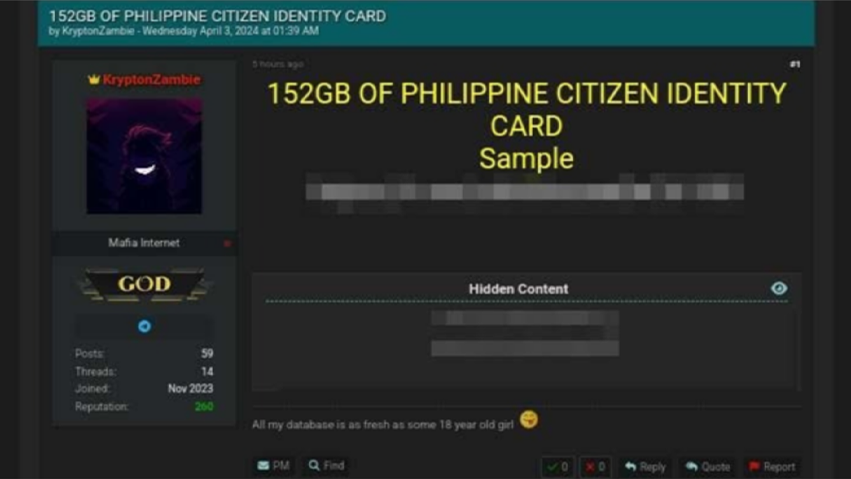
The post was initially released on Breach Forums, one of the premiere underground communities on the Dark Web. This threat actor had previously established a reputation on Breach Forums for posting various data leaks. Resecurity assesses that one of the primary motives of the threat actors behind this activity was to plant a fake narrative that could go viral on social media to target a broad number of citizens exposed to news of the leak.
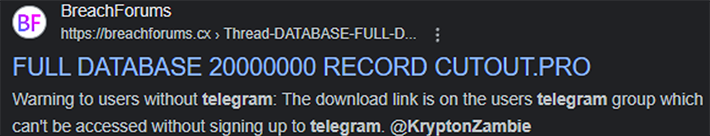
April 5, 2024, Breach Forum moderators moved KryptonZambie’s post to an unrelated section due to lack of context and evidence. Later, the moderators deleted the post from the forum, raising even more questions about this activity. In his post, the threat actor also left their Telegram contact information for further contacts to receive the data set, but it was also quickly deleted. The threat actor never responded to any messages Resecurity investigators sent to this account, and the account was deleted the same day the posting was published.
Any claims about major data leaks containing personally identifiable information (PII) are critical, as they may affect the country's population on a massive scale. This is why threat actors are able to generate a lot of attention from cybersecurity professionals and the media, the latter of which is looking for another sensationalist scoop.
Claims about large-scale data breaches undermine society's trust in institutions and information security, creating an underlying perception of distrust and insecurity. Secondly, misinformation campaigns also create chaos and aim to destabilize the government by providing misleading information. However, in many cases, with proper validation, fact-checking, and risk assessment, such claims often reveal that these disruptive narratives are misinformation. Foreign actors also widely use these tactics to stage psychological operations that damage the public’s perception of a particular country and its leadership. The claims about the data leak affecting citizens may be interpreted as an example of misinformation tactics, especially in the Philippines, as the region has strategic significance for U.S. security interests in the Indo-Pacific region.
Some of KryptonZambie's past targets were linked to India-- other postings contained primarily data recycled from previous data leaks published by ransomware groups and other threat actors. Interestingly, based on the historical Dark Web data indexed by Resecurity, some of the signatures used by the threat actor contained a reference to “Mercenary” (later, changed to another more abstract and neutral alias). It is possible the threat actor was purposely recruited or tasked to distribute unverified content against the Philippines by an unknown third party.
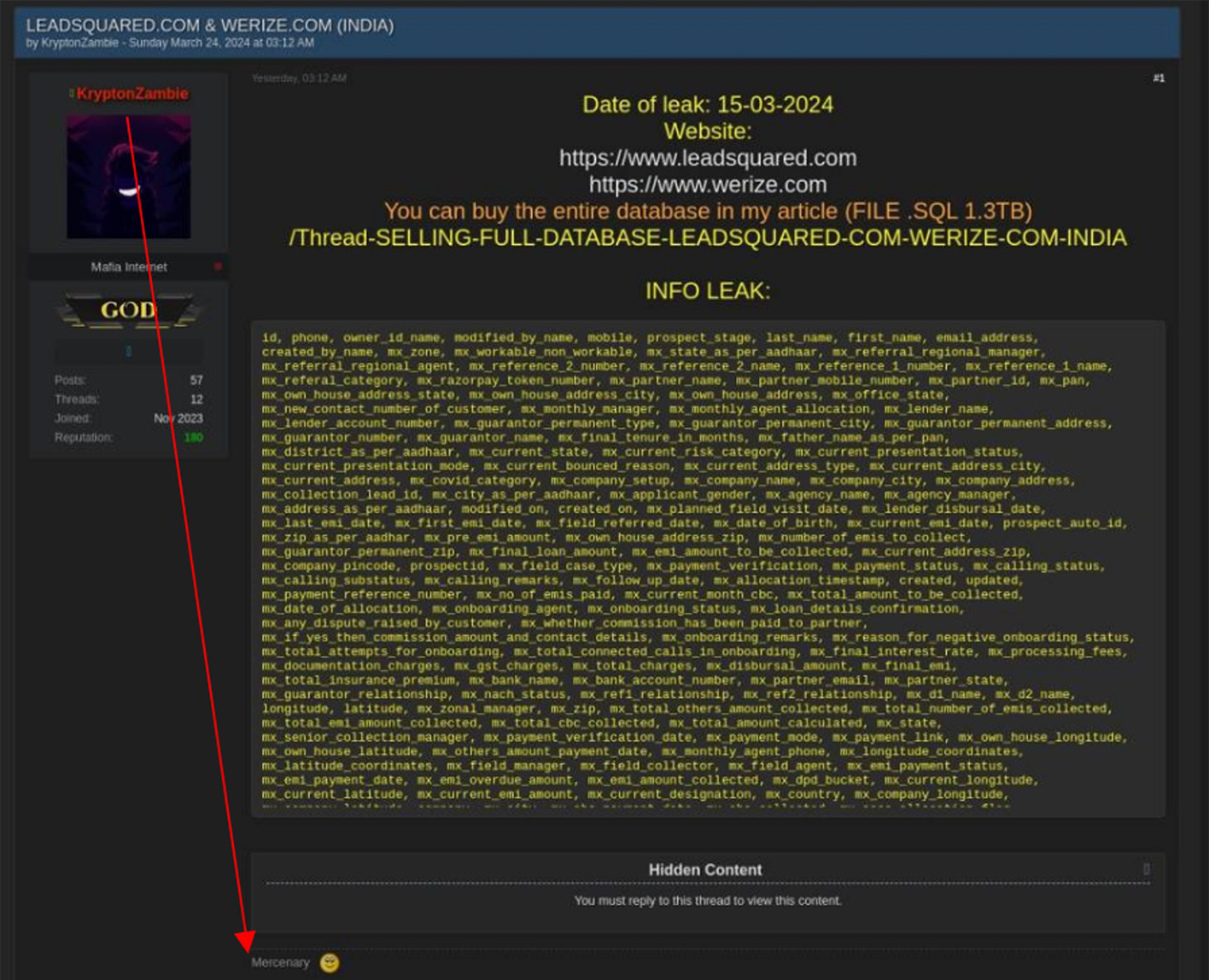
The threat actor doesn’t belong to any known cybercriminal collectives or ransomware groups and has an unknown profile. KryptonZambie likely purposely registered his moniker on Breach Forums to plant narratives about data breaches and build a reputation for future misinformation campaigns.
However, one of the most interesting features of KryptonZambie’s past activity is that some of this threat actor’s posts also overlapped with the activity of a ransomware group called RobinHouse, which has TOR and Telegram accounts. The actor may have a relationship with this group, ranging from initial access broker (IAB) to affiliate. Considering that this ransomware group's affiliate network is not well-known, KryptonZambie likely has a direct relationship with the group’s operators. This information may be used for further research and attribution.
For example, the breach of Leadzen AI was published by the actor around March 29, 2024:
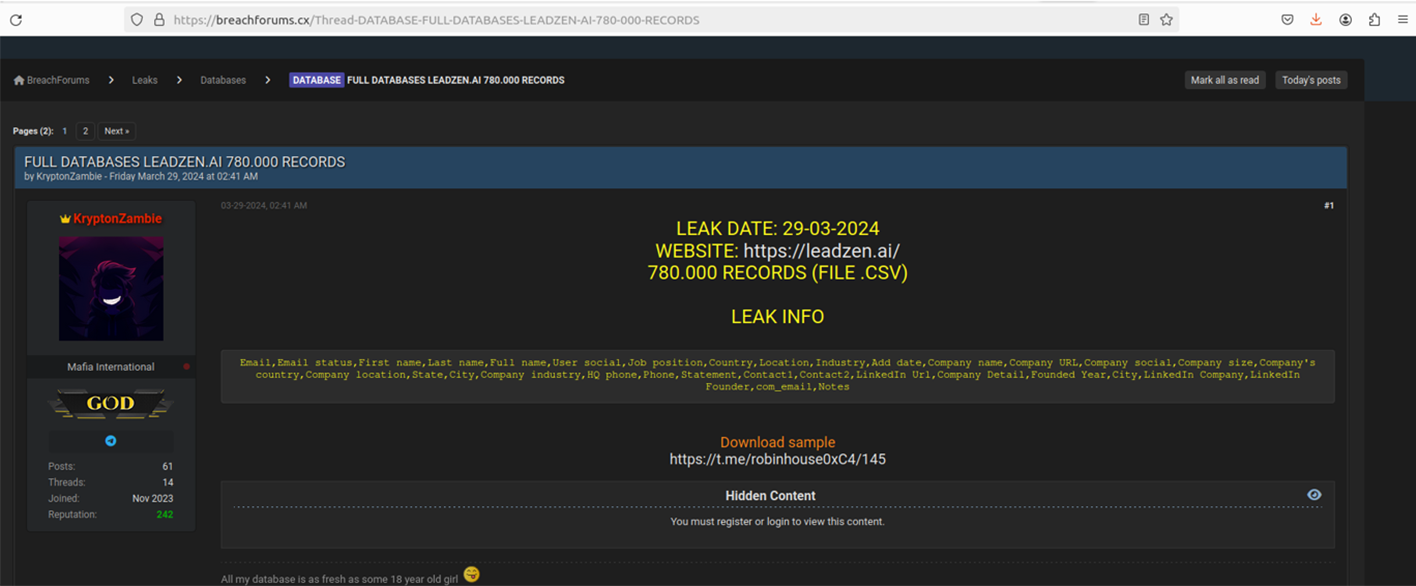
The same day, the same posting appeared on the RobinHouse Telegram group, where they published new victims:
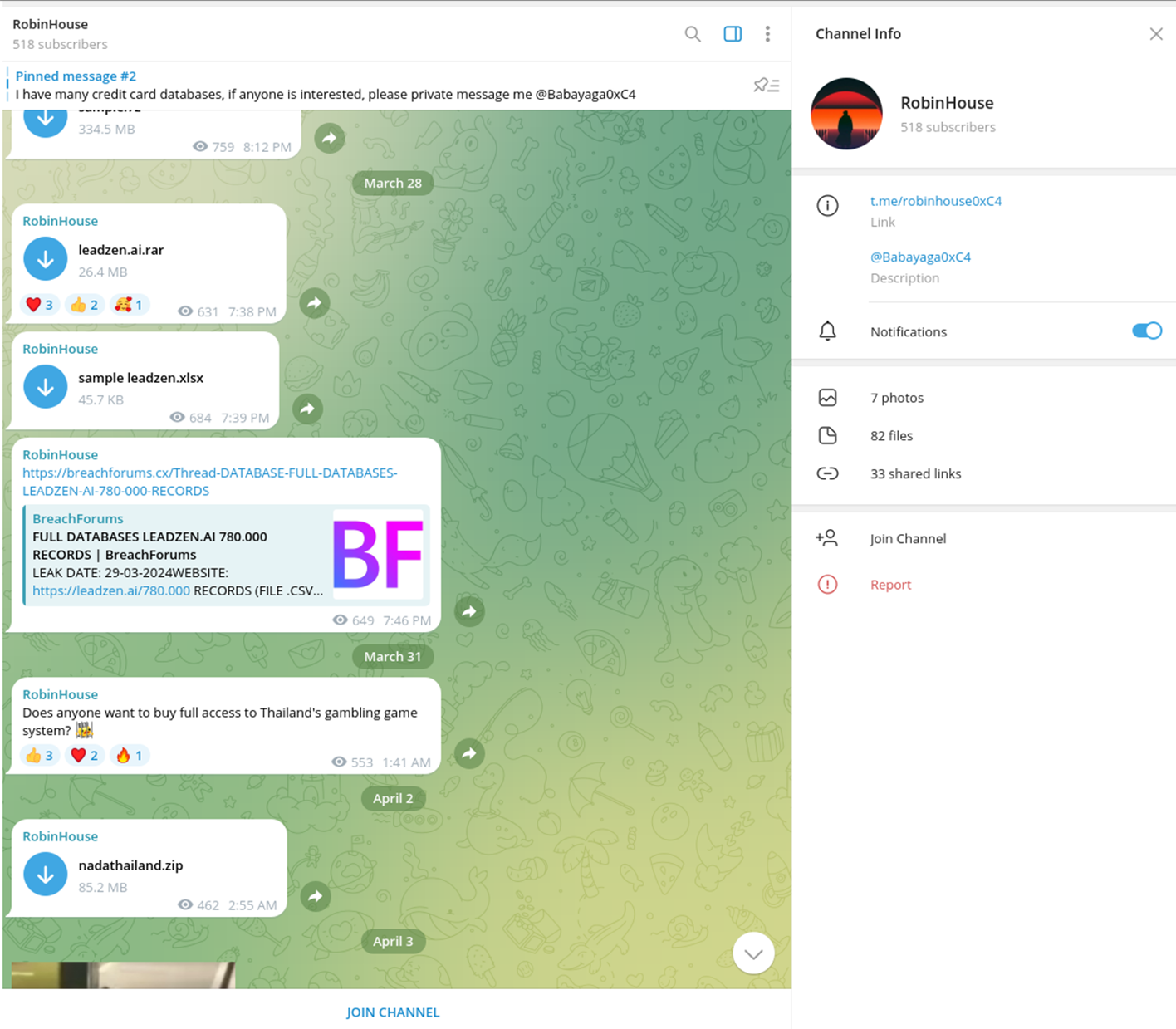
Given the overlap in the publication of Leadzen AI data, these posts appear connected and may be driven by the same threat actor or group. Another important detail is the partnership between Exodus Security Philippines and Robin Cyber Hood (RCH). Notably, an actor with an identical alias, Krypton Zambie, has a Vietnamese-language information security blog hosted on WordPress CMS, with the last posts dated 2021. It is possible the profile has been abandoned. Most postings are related to cybersecurity, penetration testing, and anonymization topics, which may confirm that the blog author engages in this activity.
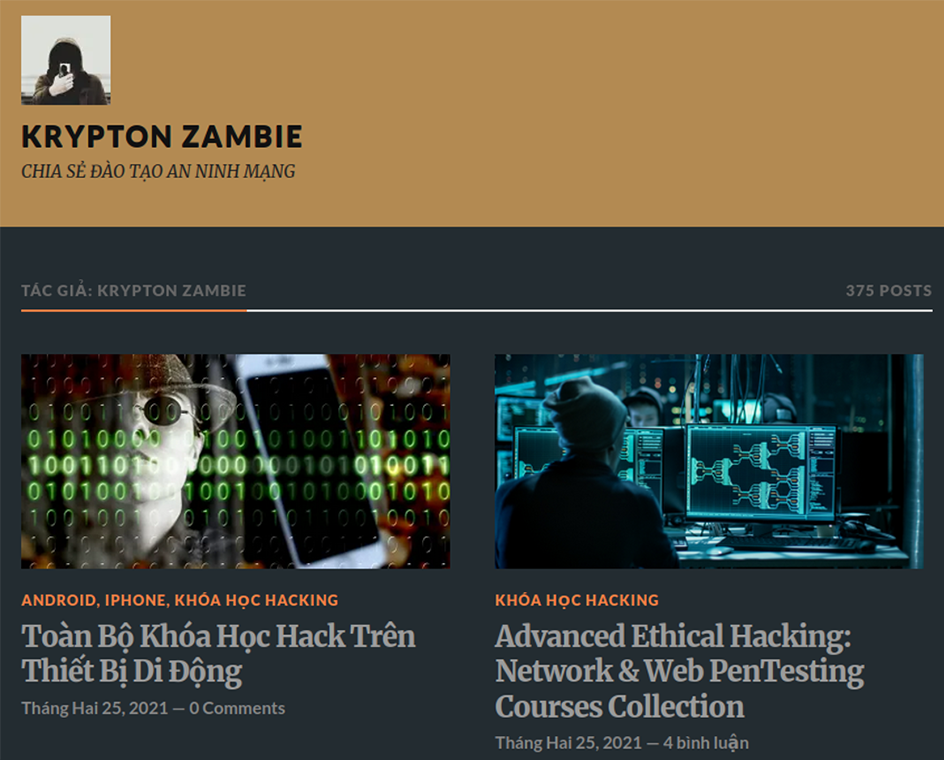
Multiple postings were related to exploiting vulnerabilities in applications such as RFI, LFI, and SQL injections. The actor seems familiar with malicious code, AV/EDR bypass, attacks against databases, and vulnerability exploitation.
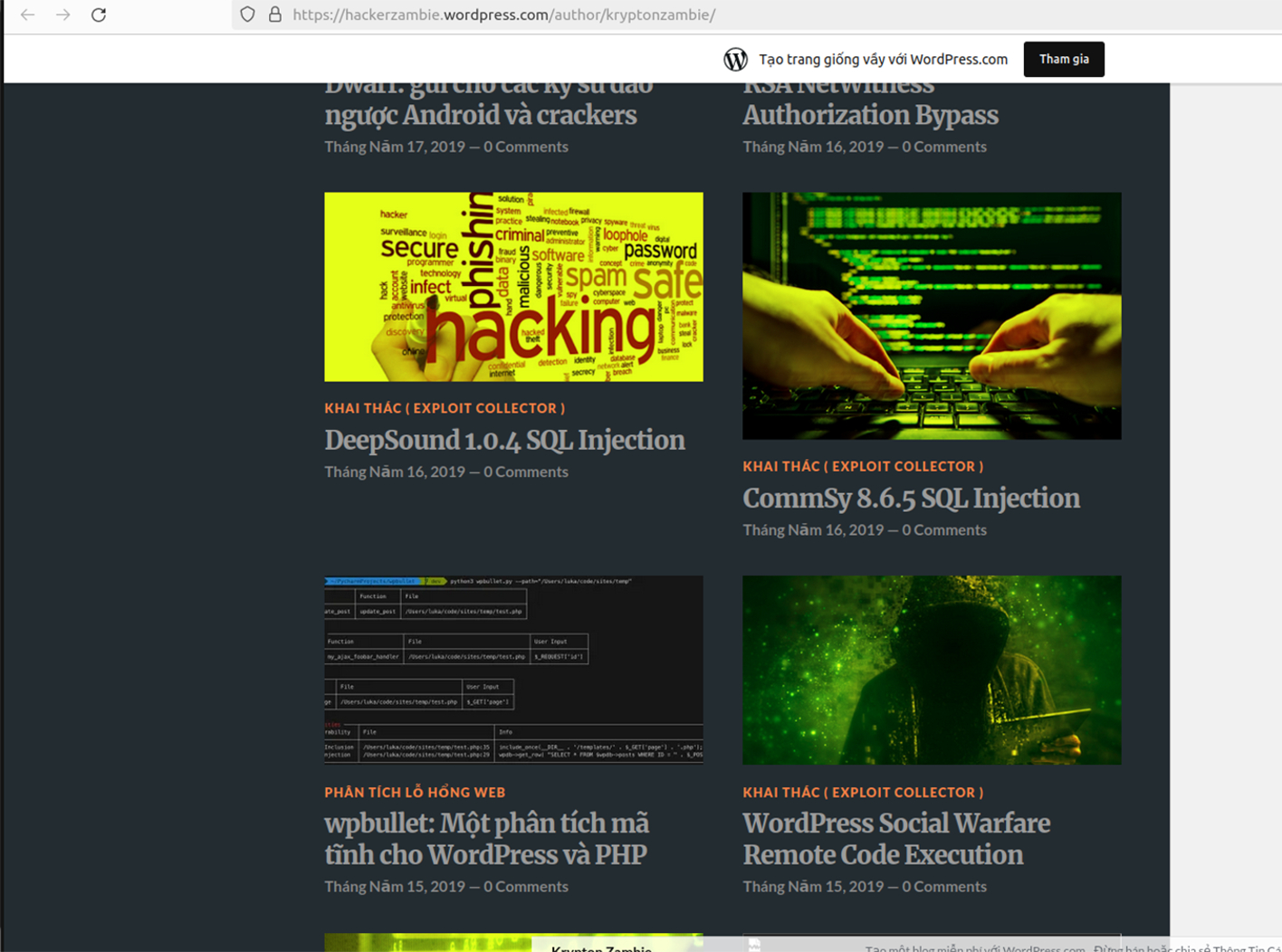
Based on these details, Resecurity assumes that the threat actor who planted fake narratives about the theft of Philippine citizens' data may be the same individual who used the Krypton Zambie alias starting in 2020/2021. Another possible theory is that some threat actor could be re-using this alias. Additionally, the WordPress blogger’s stated interests in hacking and exploiting web application vulnerabilities suggest the personas behind the blog and the Breach Forums post are the same threat actor.
Misinformation and Data Breaches
The timing of these data leaks was not random. For example, at about the same time (April 4, 2024), Philippine government organization, the Department of Science and Technology (DoST), became a victim of a cyberattack. Likely, the threat actors were coordinating this activity in the scope of the broader misinformation campaign, mixing some valid cyber events with fake ones. The combination of real and fake cyberattacks is a common tactics used by threat actors in staging their misinformation campaigns. The threat actor going by the alias “ph1ns” and using the email address ph1ns@proton.me published the following message following the cyberattack against DoST:
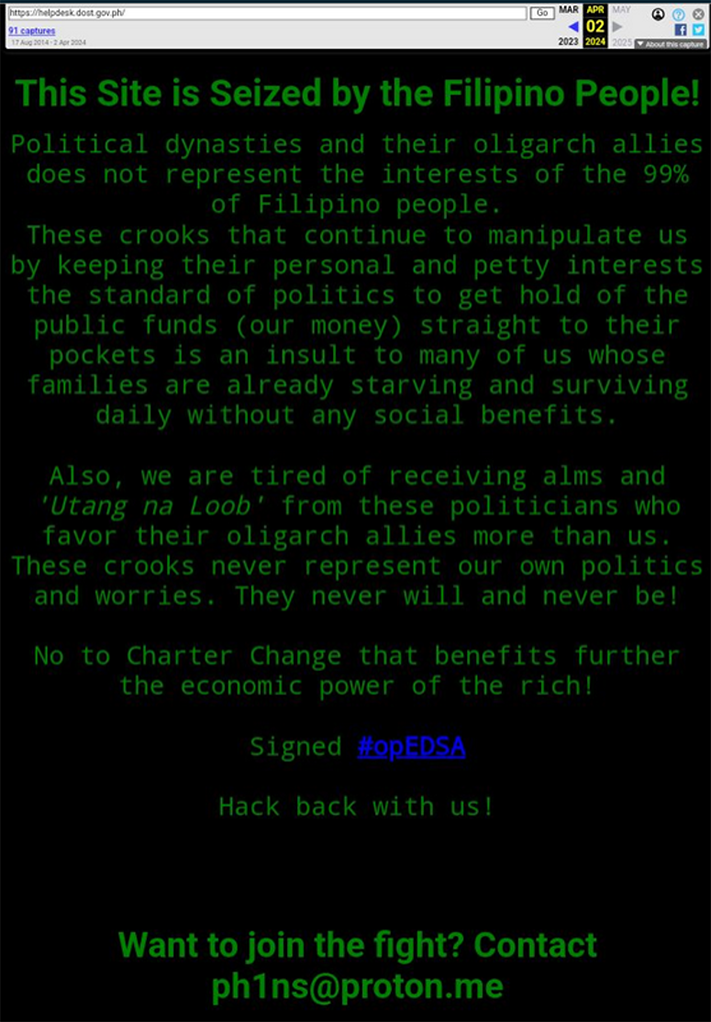
In addition, the actor has distributed the following PR message:
Hack back EDSA: End the Destructful Time of Political Dynasties Forever! Time and time again, ordinary people are always betrayed and manipulated by the affluent class in society. However, there are moments in time when such abuse is suspended by the ordinary people themselves. In contemporary Filipino history, the testament to such an event was the EDSA People Power in February 1986. It was a weeklong uprising that marked the end of a two decade-long dictatorship of Ferdinand Marcos Sr. But the victory of the people was not long-lasting. It was betrayed by none other than the affluent class. They are the same class that was once allied with the Marcos dictatorship but quickly jumped ship after the overheating discontent was strongly felt by the ordinary people. The momentary vibrant power of ordinary people who practiced their politics during the uprising suddenly spiraled down towards their depoliticization in the events to come. Once again, the affluent class firmly holds the practice of politics exclusively to themselves. Unsurprisingly, despite the poor social infrastructures, environmental destruction, mental health decline, unemployment, and unimaginable growing poverty that ordinary people have to endure every day; the politics of the time are personal squabbles between competing affluent political families. Recently, Baste Duterte, the son of the former President and strongman from Davao, and the incumbent President, who is also a son of a former strongman, were both throwing personal insults at each other. This is just one among many cases of such low-quality politics in the country. Their political squabbles are mostly tied to securing their power and authority to government funds and, thus, keeping their personal interests secure. These affluent political families are also backed by local oligarchies and competing imperialist countries (US vs. China). Together, they keep the deception alive to secure their personal wealth and interests at the expense of the ordinary people\'s well-being and the health of our planet. None of these squabbling affluent families represent the interests of ordinary people. But can ordinary people change the course of the future away from the destructive reign of the affluent class? One has to take a leap of faith to find the answer. And that faith lies in the spirit of EDSA People Power and similar experiences of power from ordinary people around the world. By keeping this spirit alive, we aim to reclaim what should rightfully be ours and finally suspend the destructive reign of the affluent class forever. Stop the Time of the Elite Class! Attack where it hurts, bitlock their infrastructures! |
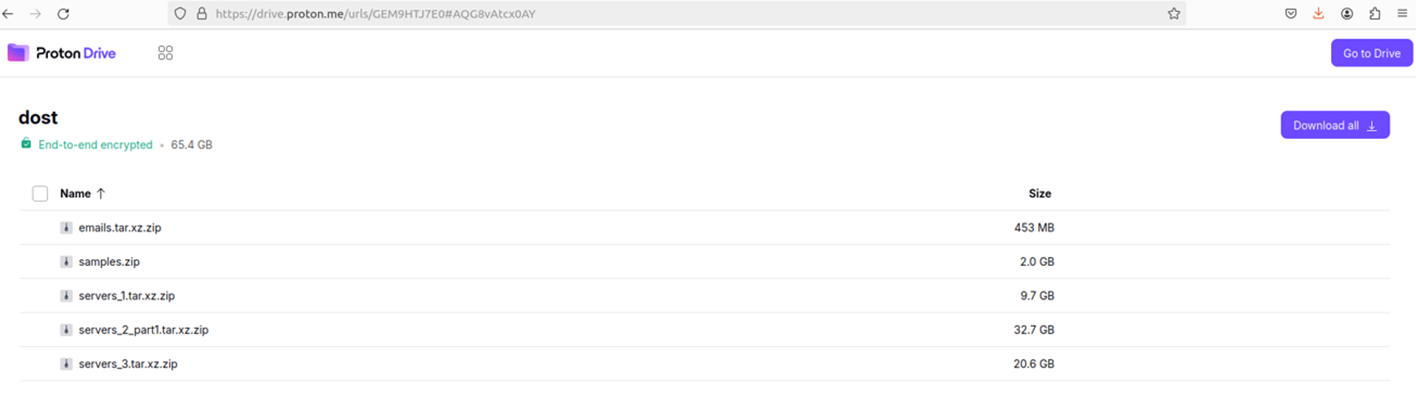
Stolen data from DoST has been uploaded and later shared with ProtonDrive:
Like the previous actor, ph1ns also has an account at Breach forums:
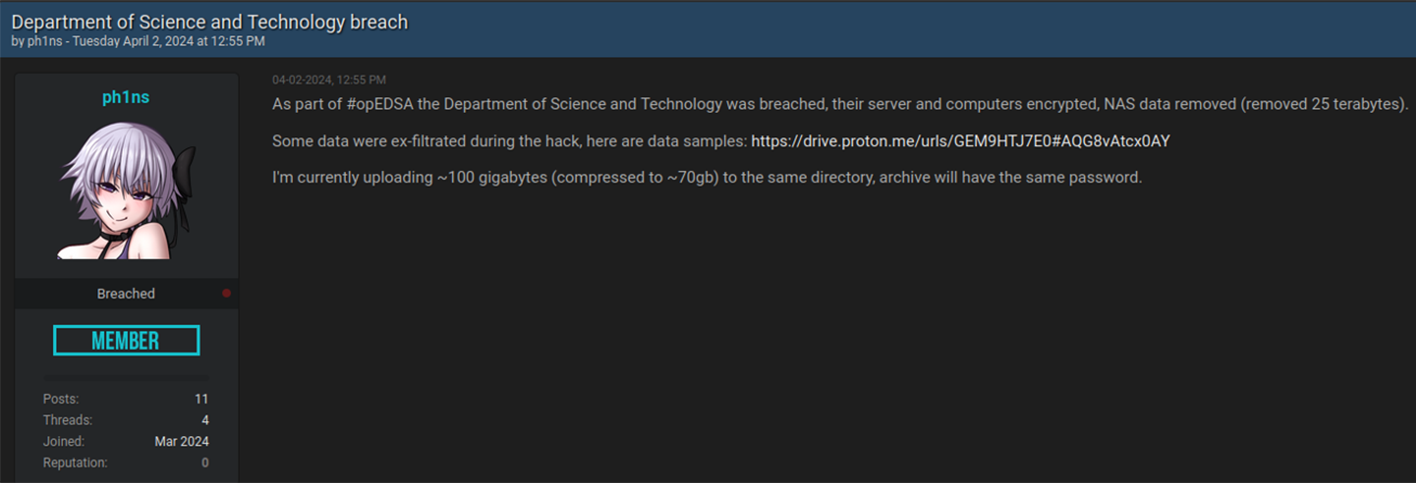
The dump was password protected:

Due to similarities in their tactics, Krypton Zambie's and ,ph1ns’s activities may be coordinated by the same group targeting the Philippines.
In the backdrop of rising regional tensions with China, these misinformation tactics could be part of a broader cyber-targeting conspiracy focused on the Philippines. Multiple reports (most recently from April 6) highlighted the activity of so-called “trolls” on social media and other digital channels, spreading misinformation about the Philippines. Spreading misinformation about fake data breaches generates uncertainty in society, so it should be vigorously investigated and prosecuted.
Example:
Notably, hacktivists from Exodus Security Philippines have released a statement about these fake narratives.
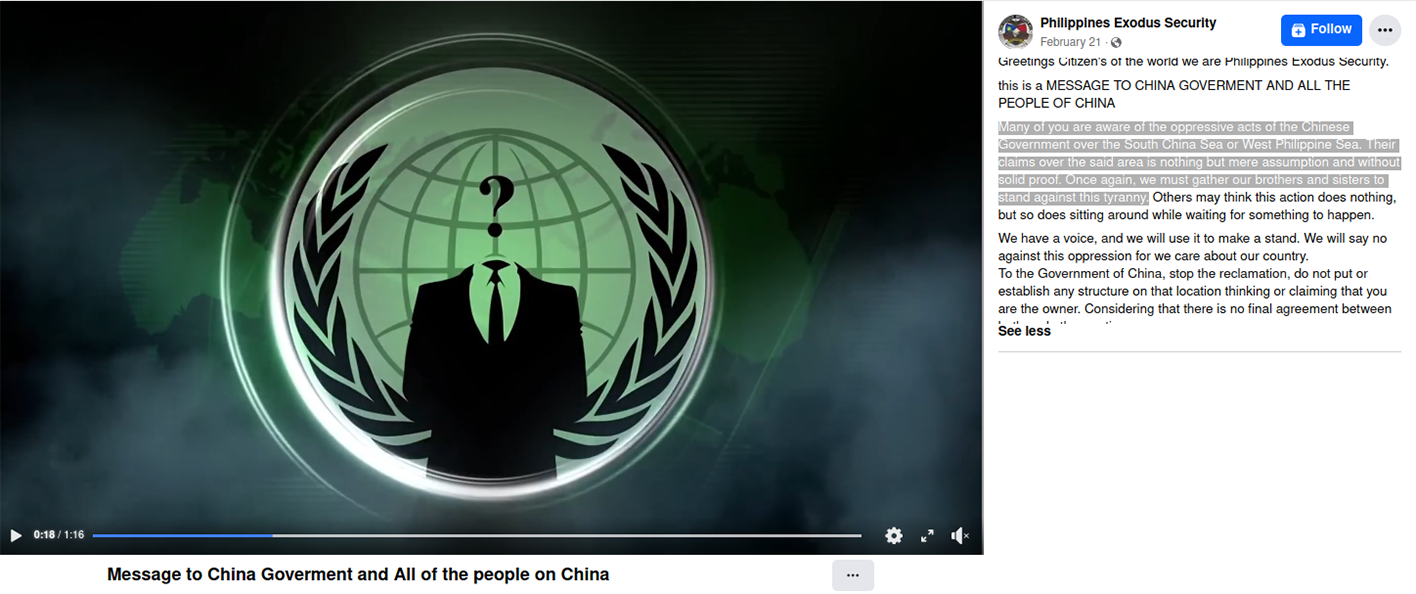
Greetings Citizen's of the world we are Philippines Exodus Security. this is a MESSAGE TO CHINA GOVERMENT AND ALL THE PEOPLE OF CHINA |
Conclusion
The cyberattacks and information warfare campaigns targeting the Philippines had an enthusiastic reception in local hacktivist communities. These campaigns incorporated political attacks and fomented protest activity against the Philippine government. Considering the Philippines' strategic significance in the Indo-Pacific, foreign actors interested in destabilizing civil society may support such activity.
References
- Philippines wards off cyber-attacks from China-based hackers
- DICT says DOST hack possible ransomware, ‘hacktivism’ attack

