Cybercriminals Transform Raspberry Pi into a Tool for Fraud and Anonymization: GEOBOX Discovery
Cyber Threat Intelligence


Resecurity identified a new solution advertised on the Dark Web – GEOBOX, a custom software, purpose-built for Raspberry Pi devices, representing an evolution in tooling for fraud and anonymization. Notably, the cybercriminals transformed widely used geek-favorite device into a 'plug-and-play' weapon for digital deception – enabling the operator to spoof GPS locations, emulate specific network and software settings, mimic settings of known Wi-Fi access points, as well as bypass anti-fraud filters.
The GEOBOX tool was first discovered during an investigation into an online banking theft involving a high-net-worth (HNW) client of a leading Fortune 100 financial institution. This discovery led to the acquisition of GEOBOX for more in-depth analysis. The malicious individuals utilized several GEOBOX devices, each connected to the Internet and strategically placed in various remote locations. These devices served as proxies, significantly enhancing their anonymity. This approach complicated the investigation and tracking process, especially since, by default, GEOBOX devices do not store any logs.
Resecurity envisions the tactics leveraging custom-made or modified devices like Raspberry Pi and other Internet-of-Things (IoTs) will be more actively used by bad actors, creating a new challenge for law enforcement internationally.
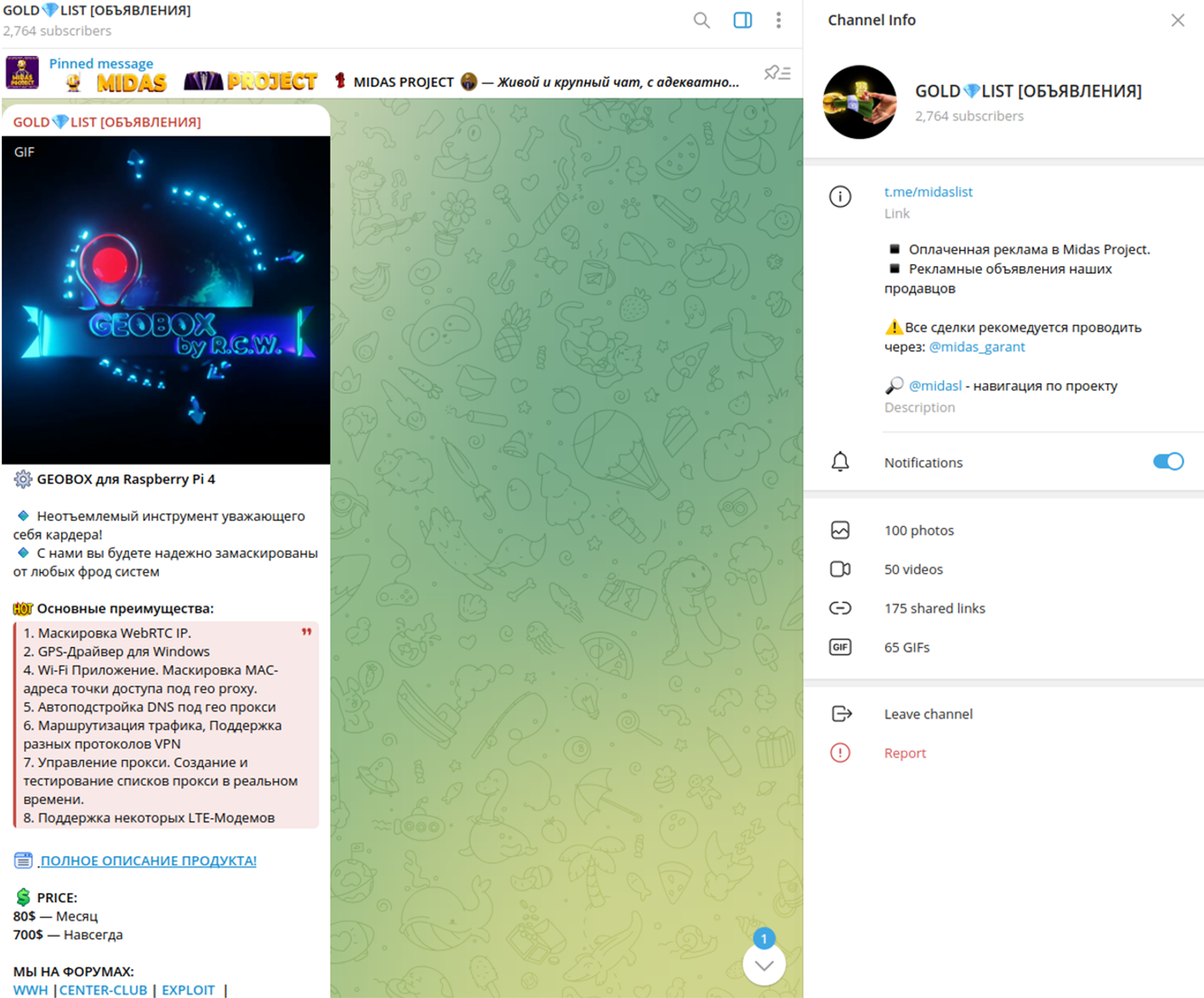
The package can be rented for a lifetime fee of $700 or a monthly rate of $80, payable in cryptocurrency. It is advertised on major underground forums, including Exploit, and is also promoted on Telegram.
Translation
More information:
- WebRTC IP masking.
- GPS-driver for Windows OS.
- Wi-Fi. Masquerading of hotspot MAC address for specific geolocation (based on the map of known hotspots)
- DNS configuration for specific geographical location (to avoid leaks).
- Support of various VPN protocols for routing.
- Flexible Proxy servers management.
- LTE modems support
Welcome!
PRICE:
$80 — Per Month
$700 — Forever
Internet-of-Things (IoTs) on the Service of Cybercriminals
Designed for anonymity and fraudulent activities, GEOBOX turns ordinary hardware into a potent weapon for digital deception. This development is particularly concerning given the widespread availability and low cost of Raspberry Pi devices, making advanced cyber tools more accessible to threat actors than ever before. In fact, the choice of Raspberry Pi is a good example of how cybercriminals may leverage Internet-connected portal devices for anonymization complicating investigation for law enforcement.


Easy to Setup
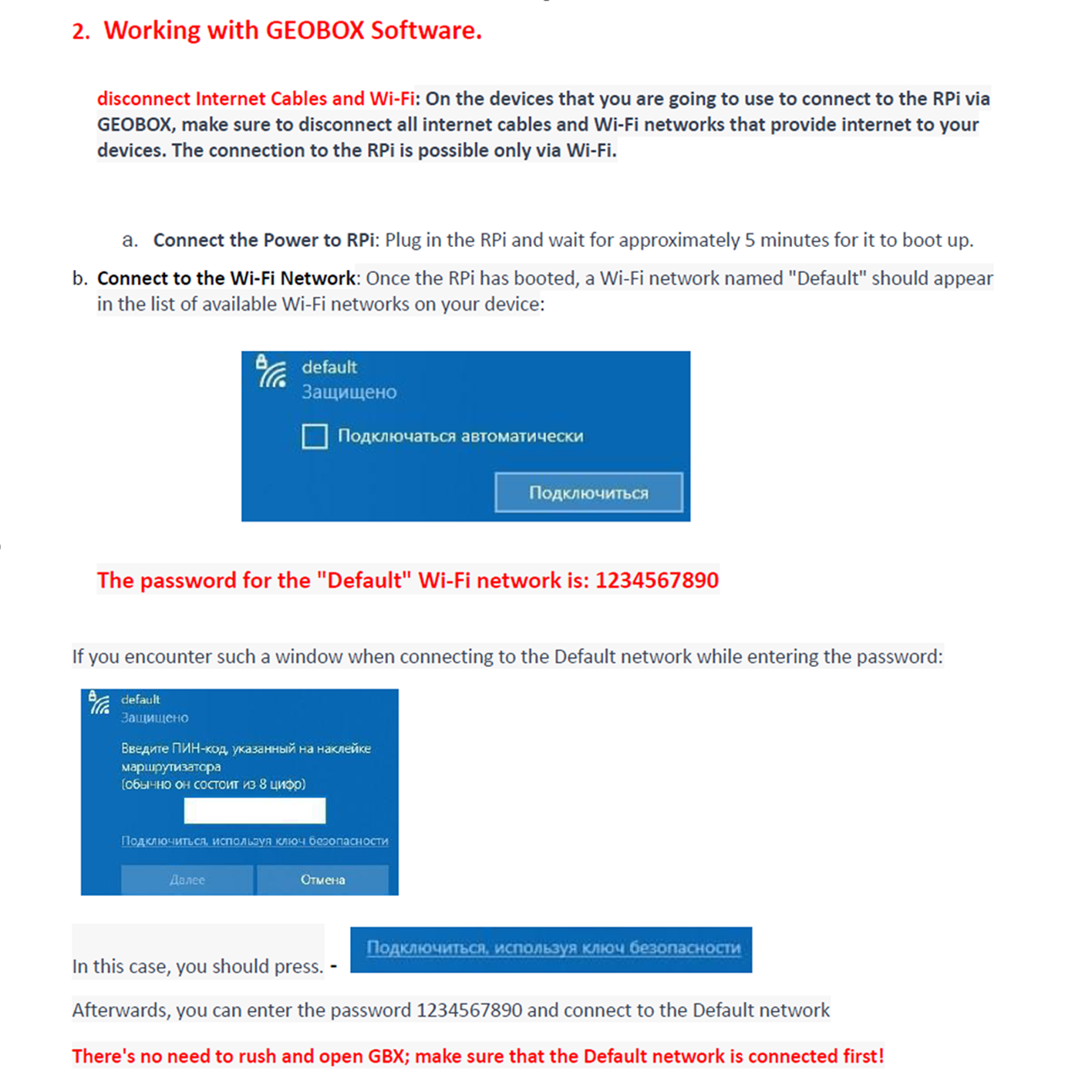
The setup process of this device has been made relatively simple, assuming GEOBOX is aiming this tool at a broad audience, they provide a user manual with clear, concise, and easy to follow instructions.
Preparing the MicroSD Card and Software
The user manual provides clear instructions on which SD card should be used to get optimal performance from their tool on the Raspberry Pi.
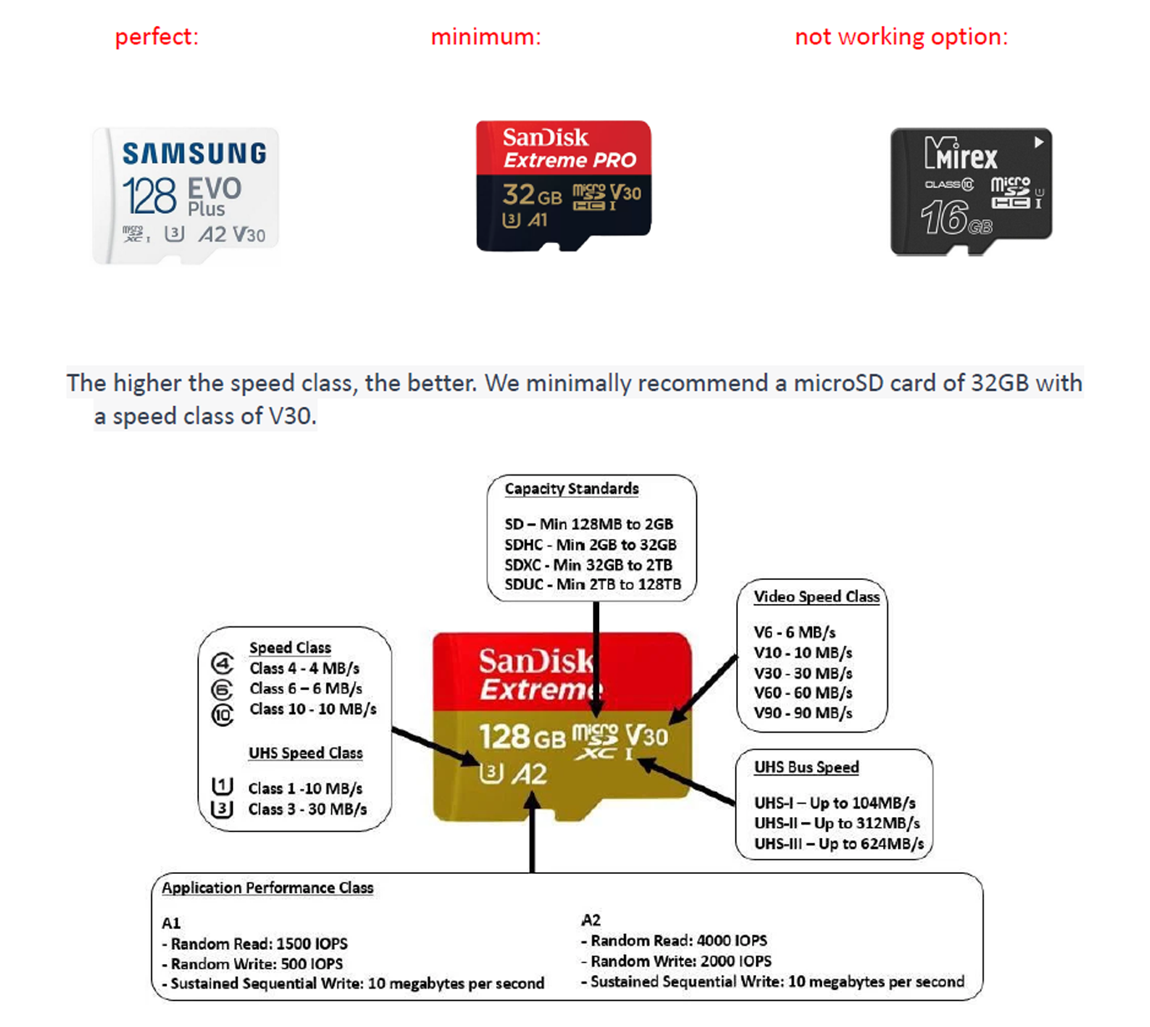
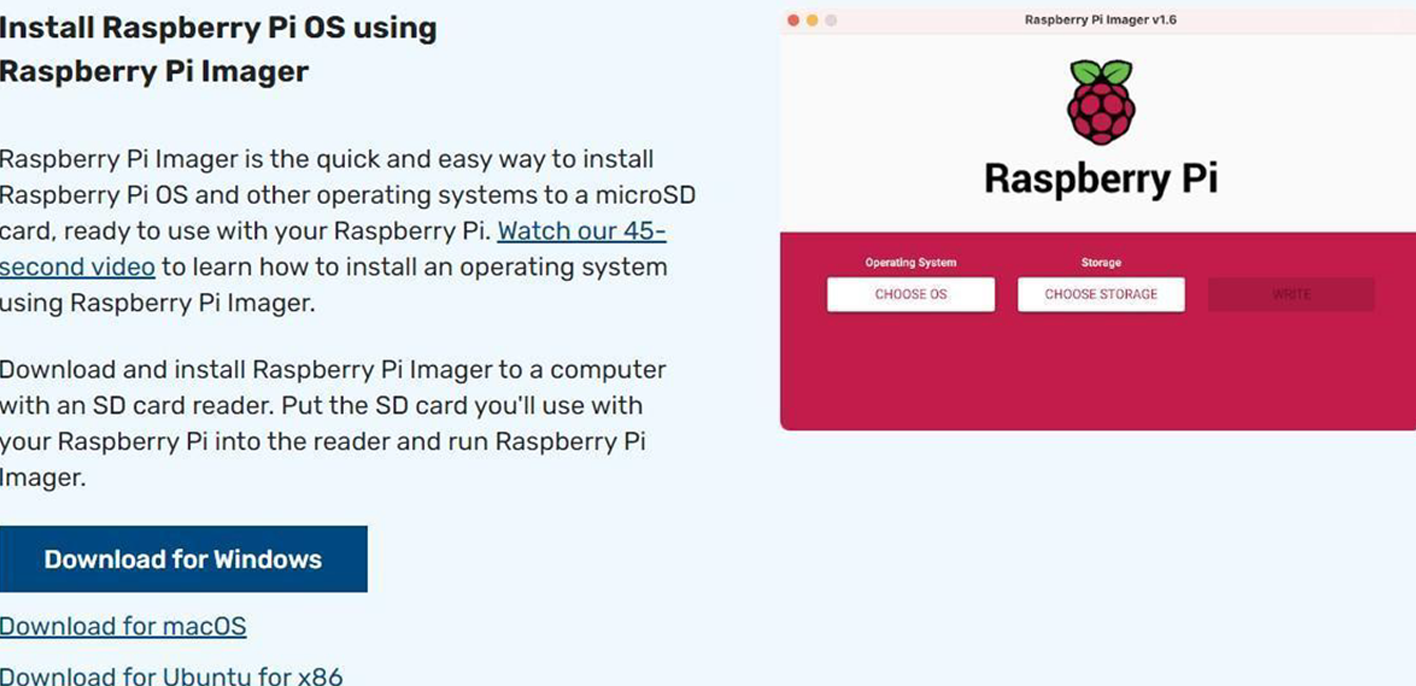
The manual also provides links to the official Raspberry Pi website to download and install the OS using Raspberry Pi Imager.
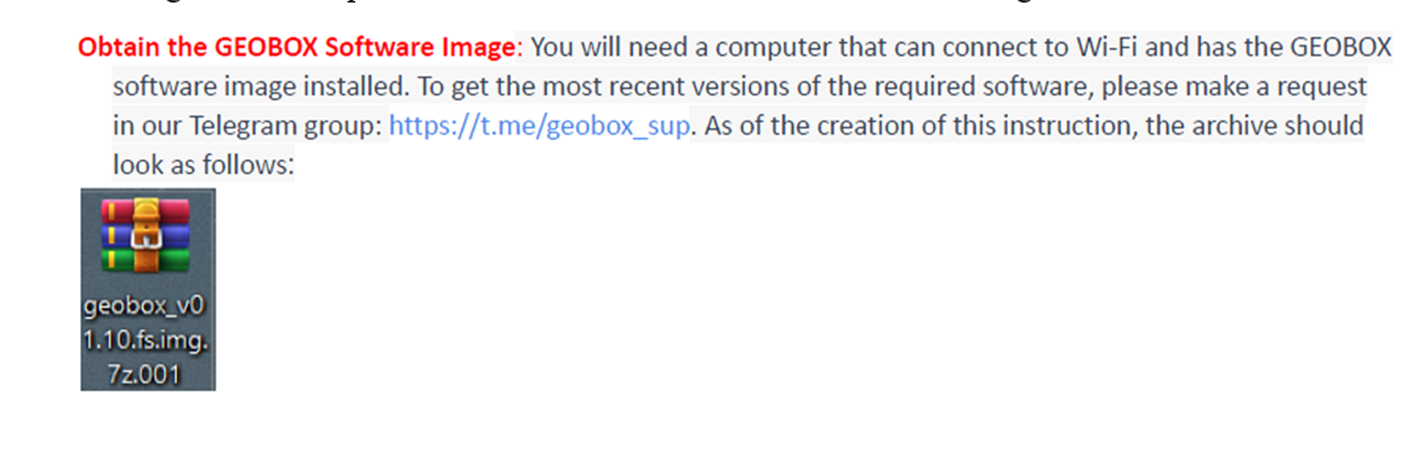
The manual goes on to explain how to obtain the GEOBOX Software Image
After completing the installation of the Raspberry Pi OS, the manual goes on in detail how to work with the GEOBOX software.
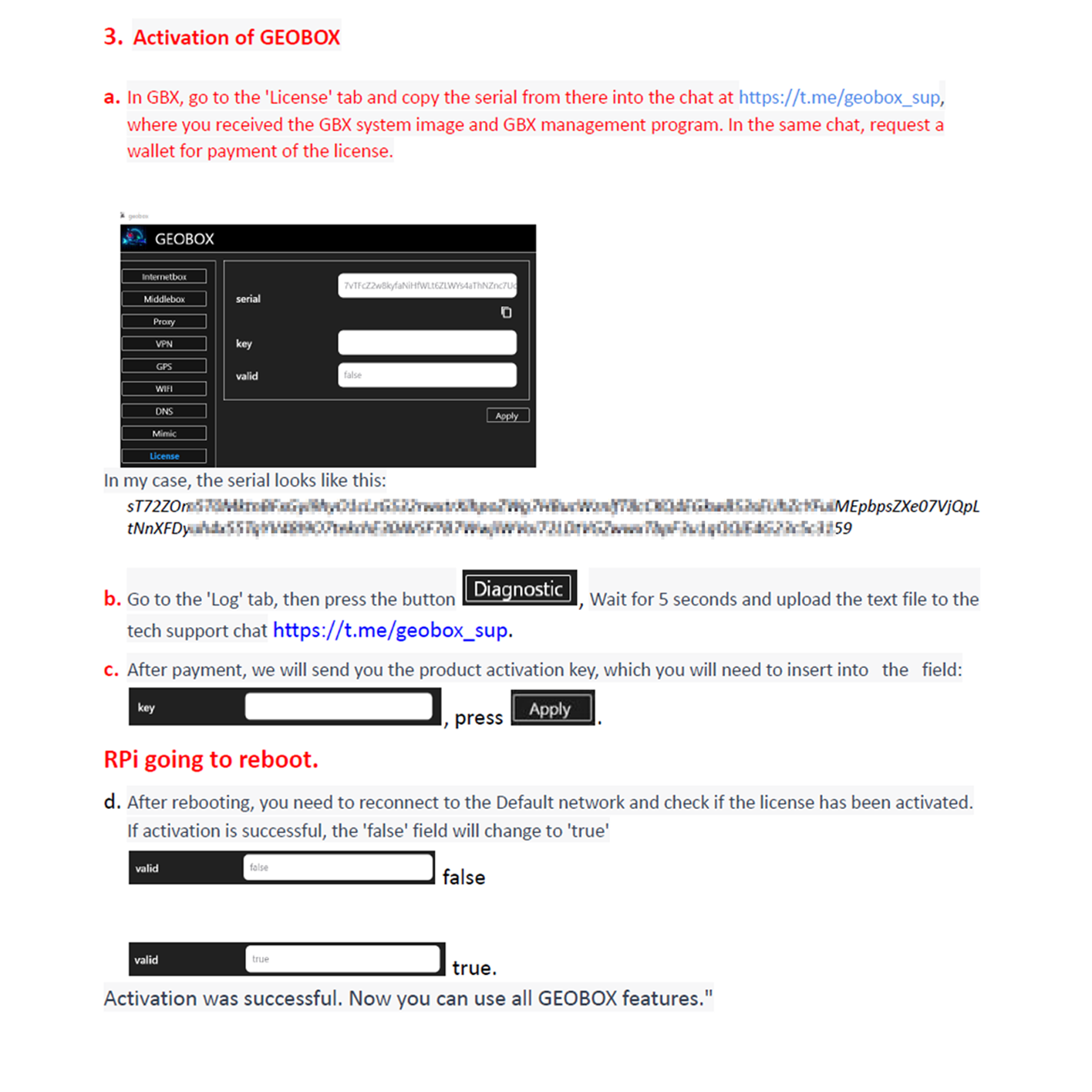
Once the user has installed the GEOBOX software, the article moves on to the activation procedure.
The detailed user manual then goes on to explain how to connect to the internet, the functions of the GEOBOX and how to configure them.
GEOBOX Feature Set
- INTERNETBOX Tab: This section allows users to configure various internet connection types, including multiple VPN protocols such as L2TP, PPTP, L2TP-IPsec, Wireguard, SSTP, Zerotier, and OpenVPN. Users can create multiple VPN profiles and select the desired one for their activities.
- MIDDLEBOX Tab: Similar to the INTERNETBOX, the MIDDLEBOX tab offers additional VPN configuration options. It's designed to create a VPN tunnel within another VPN tunnel, adding an extra layer of anonymity.
- Proxy Tab: This function enables users to configure a proxy server for DNS, GPS, and Wi-Fi MAC address information. It also includes features for generating a Wi-Fi environment based on the geolocation of the proxy server, requiring specific Wi-Fi adapters with monitor/inject mode support.
- VPN Tab: This tab supports various VPN protocols and allows users to add VPN profiles by entering server and account information. Once a VPN profile is created, it can be selected for use in the INTERNETBOX or MIDDLEBOX.
- GPS Tab: In this tab, users can find installation files for a GPS emulator for Windows systems. This allows a device without a GPS receiver to receive coordinates from the selected proxy server.
- WI-FI Tab: Users can change the parameters of the Default network, including the network name, password, and location identifier for frequency settings.
- DNS Tab: GEOBOX automatically selects DNS servers based on the geolocation of the raised proxy or VPN. Users have the option to manually configure DNS settings for both VPN and proxy connections.
- Mimic Tab: This section displays the data received from the proxy server and the substituted data that the remote side sees, providing insights into how the GEOBOX is manipulating network information.
- System Tab: Provides system data about the Raspberry Pi, including IP addresses, the GEOBOX version, and other sensor data.
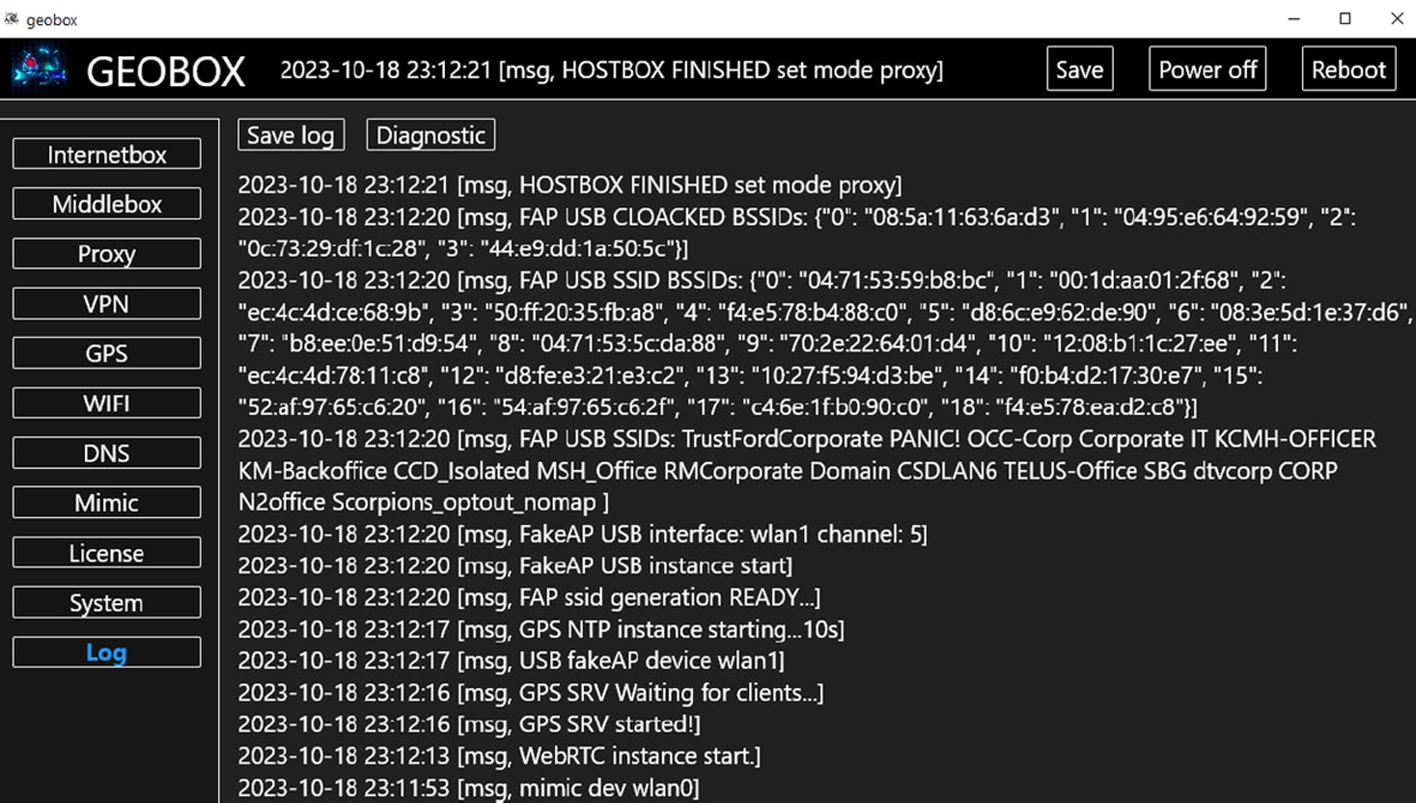
- Log Tab: Contains system events and logs for diagnostics and debugging. This tab is essential for troubleshooting and understanding the operation of GEOBOX.
- Zerotier Configuration: Detailed instructions are provided for setting up Zerotier, a method to bypass VPN restrictions using a specific network ID.
Technical Insights
GEOBOX transforms Raspberry Pi devices into sophisticated tools for anonymization and fraud. This device, equipped with custom firmware/software, is specifically designed for the Raspberry Pi 4 Model B. It requires at least 4 GB of RAM, but an 8 GB version is recommended for optimal performance.
The device's functionality is diverse, allowing for various forms of digital manipulation and disguise. Key features include the ability to use WebRTC IP for discreet online communication and GPS spoofing to simulate different geographical locations, which is particularly valuable for activities that require geolocation manipulation. Furthermore, the GEOBOX can mask Wi-Fi MAC addresses, making the user's network activity more difficult to trace.
Installation and operation are user-friendly. The device connects to the internet through either an Ethernet cable or a USB modem, and settings can be managed via a Wi-Fi network named "Default." GEOBOX's software offers a range of tabs including INTERNETBOX, MIDDLEBOX, Proxy, VPN, and Wi-Fi, each providing specific functionalities like proxy server configuration, VPN connectivity, and altering Wi-Fi network parameters.
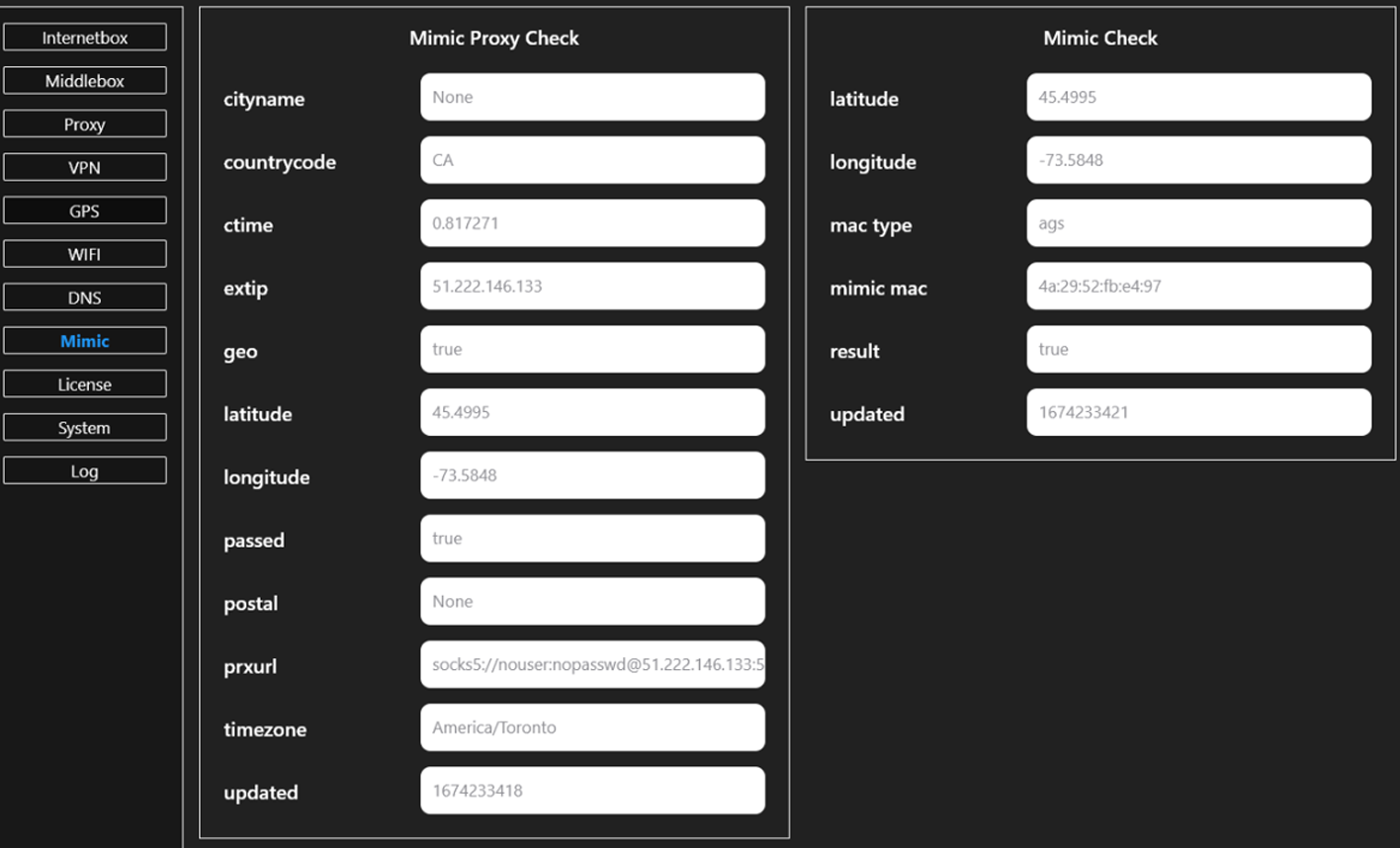
This array of features positions GEOBOX as a powerful tool for maintaining anonymity online and engaging in fraudulent activities, posing significant challenges to cybersecurity.
Implications for Cybersecurity
The emergence of GEOBOX introduces new complexities in the realm of cybersecurity. It underscores the necessity for robust digital risk monitoring and endpoint protection strategies. The situation demands not only enhanced detection capabilities but also a concerted effort from cybersecurity entities worldwide to share intelligence and resources.
Spectrum of Potential Cybercrimes
- Cyber Attacks Coordination:
Ideal for orchestrating complex cyber offensives, including state-sponsored attacks or corporate espionage. - Dark Web Market Operations:
Empowers operators of illicit online markets in their anonymous sale of illegal goods. - Sophisticated Financial Frauds:
Enhances capabilities for committing identity theft and credit card fraud under the veil of anonymity. - Circumvention of Government Censorship:
Facilitates bypassing state-imposed content restrictions and surveillance. - Anonymized Malware Distribution:
Aids in the anonymous spread of malware and ransomware, complicating traceability. - Credential Stuffing Campaigns:
Streamlines automated attacks on digital accounts for mass data breaches. - Creation of Disinformation Campaigns:
Enables creating and managing multiple fake online personas for spreading misinformation. - Surveillance Evasion in Authoritarian Regimes:
Assists individuals in authoritarian regimes to evade digital surveillance. - Content Piracy and Geo-Restriction Bypassing:
Allows illegal access and distribution of geo-restricted digital content. - Network Security Testing:
Less malicious but potentially problematic for testing networks’ vulnerabilities to such anonymization tools.
Multiple individuals were found using GEOBOX to create customized accounts on well-known online platforms such as Google and Amazon.:
GEOBOX provides cybercriminals with the ability to fake their geographical location down to specific coordinates, which can be manually set. This is accomplished through a specially designed driver that mimics a GPS device. In this case, the individual set their location using GEOBOX and successfully bypassed location verification checks on websites like Whoer.net and browserleaks.com.
Challenge for Law Enforcement – Tracing the Cybercriminal IoTs
In one of the scenarios observed by Resecurity, the bad actor was using GEOBOX in combination with two LTE-based wireless modems, proxyfying connections via multiple chains of SOCKS and PROXY servers. Such model provides bad actor enhanced anonymization, especially, in case of remote connection via device where the bad actor is not physically present. Leveraging several devices deployed in various locations using this model may create a significant challenge in tracing cybercriminal using it.
It was also observed very short duration of sessions by some actors – understanding principles of lawful interception technologies. Once the malicious action has been conducted – they either wipe the device or destroy it physically, and move it to other locations, including those providing free public Wi-Fi access.
Conclusion
The ease of access to GEOBOX raises significant concerns within the cybersecurity community about its potential for widespread adoption among various threat actors. This development necessitates a heightened level of vigilance and underscores the importance of global cooperation in the fight against these increasingly accessible and sophisticated cyber threats.
The detection of GEOBOX by Resecurity is a stark reminder of the continuously evolving cyber threat landscape. It highlights the sophistication of modern cybercriminals and the importance of staying one step ahead. In a world where digital security is paramount, the vigilance and expertise of organizations like Resecurity and their HUNTER unit are invaluable assets in our collective cybersecurity endeavors.
In the face of this discovery, Resecurity stands at the forefront of the battle against cybercrime. Our commitment to providing advanced cybersecurity solutions, including managed threat detection and intelligence services, is crucial in combating threats like GEOBOX. By closely collaborating with law enforcement and the cybersecurity community, Resecurity plays a pivotal role in shaping a safer digital future.

