Cybercriminals Implemented Artificial Intelligence (AI) for Invoice Fraud
Cyber Threat Intelligence


Masterminds of Tech Excellence in the World of Cybercrime
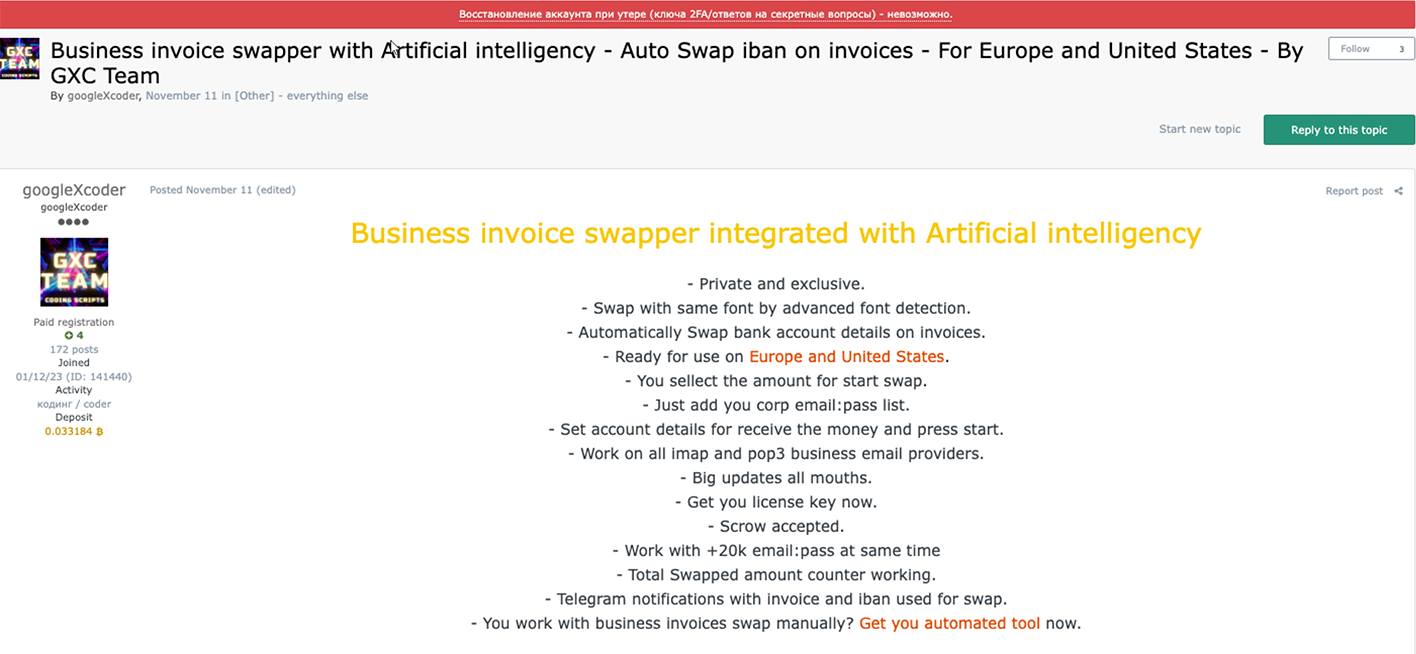
Resecurity has uncovered a cybercriminal group known as "GXC Team", which specializes in crafting tools for online banking theft, ecommerce fraud, and internet scams. Around November 11th, 2023, the group's leader, operating under the alias "googleXcoder", made multiple announcements on the Dark Web. These posts introduced a new tool that incorporates Artificial Intelligence (AI) for creating fraudulent invoices used for wire fraud and Business E-Mail Compromise (BEC) scams. According to a 2022 FBI IC3 report, BEC scams (such as invoice fraud) resulted in an average loss of over $120,000 per incident, inflicting a staggering financial toll of more than $2.4 billion on victim organizations. According to FinCEN advisory, criminals continue to exploit vulnerable business processes with business email compromise schemes – over $9 billion in possible losses affecting U.S. financial institutions and their customers since 2016.
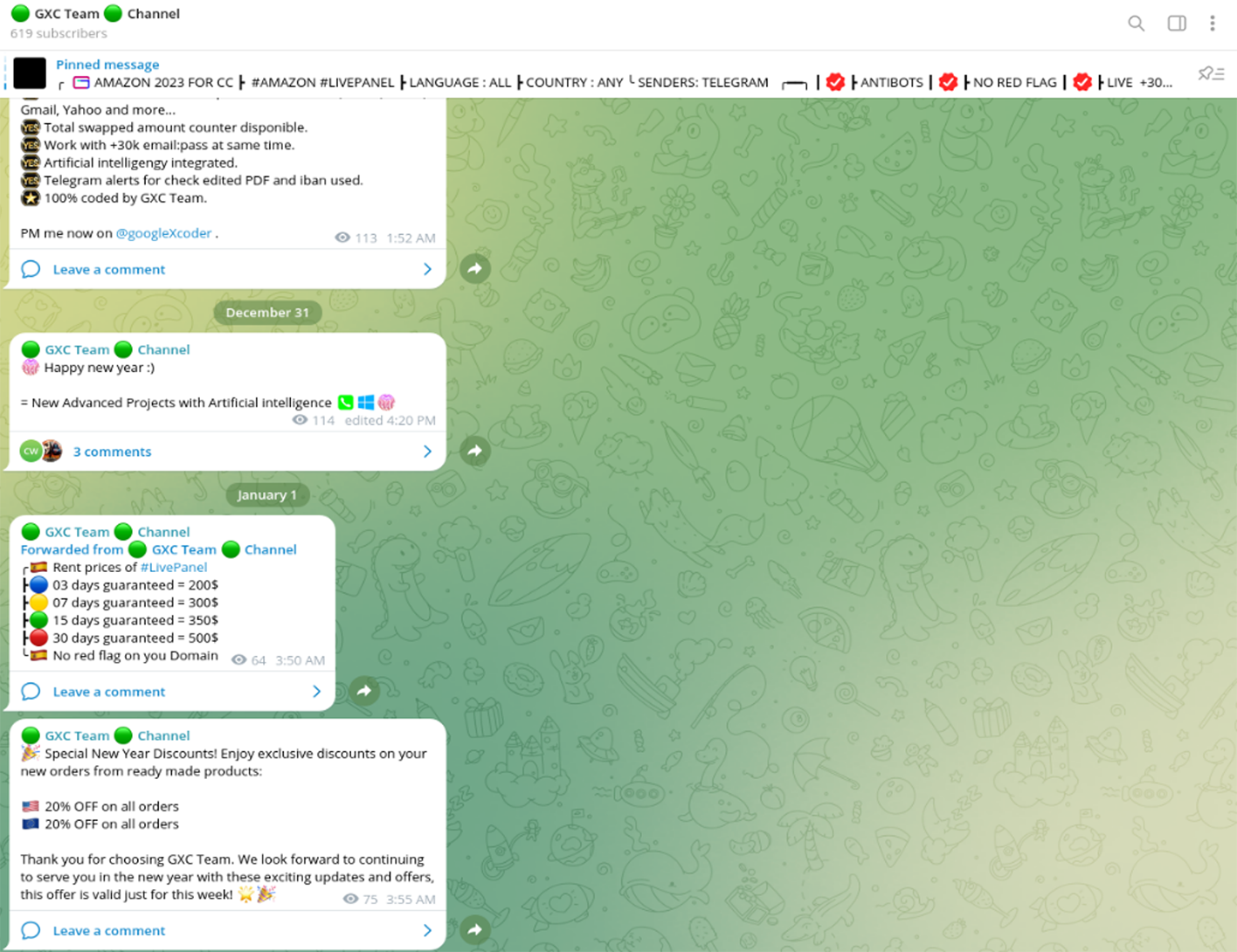
On New Year's Eve, the group announced significant price reductions, offering up to a 20% discount on their products available on the Dark Web.
The Deployment of AI for Malicious Purposes
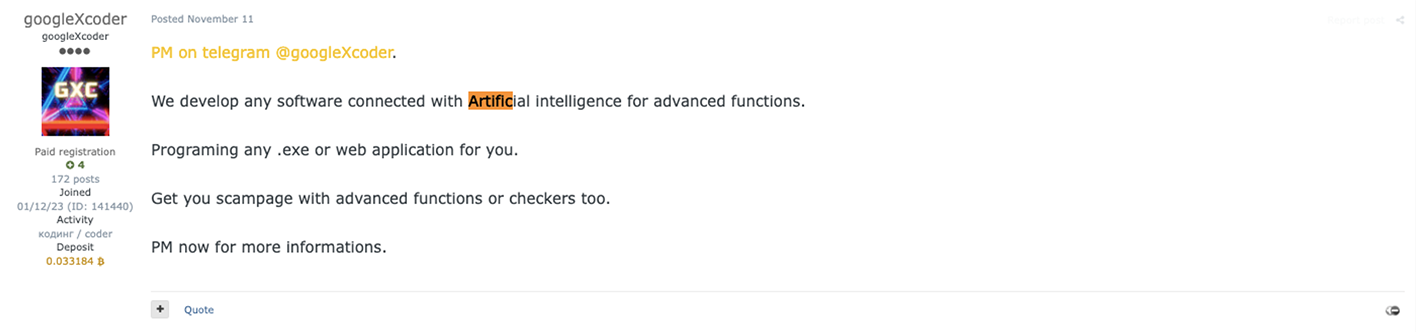
Threat actor "googleXcoder" placed multiple ads in renowned underground cybercriminal forums, including Exploit. The threat actor highlighted the potential for advanced functionalities that could be achieved by harnessing the capabilities of AI.
Undoubtedly, cybercriminals have recognized the immense potential of AI to enhance and expand their operations. But what specific advantages does AI offer them? Most notably, the emergence of AI-driven platforms like FraudGPT and WormGPT, which utilize Large Language Models (LLMs), has been a game-changer. These frameworks enable the creation and scaling of sophisticated Business Email Compromise (BEC) campaigns, and generation of content for "Money Mule" spam used in money laundering schemes, and the provision of pre-made malicious strategies and tools. Other use-cases being operationalized by threat actors include generative AI-powered deep fakes to further enhance the credibility of social-engineering attacks and online influence campaigns.
Additionally, four hackers were arrested in China and Inner Mongolia this past November for using ChatGPT to optimize the code of a ransomware binary they used in an attack against an unidentified company in Hangzhou. In this evolving and geopolitically volatile threat landscape, Resecurity is concerned that 2024 might be the year that adversaries launch an AI-enhanced, WannaCry-style ransomware campaign. In a recent, multi-vendor cybersecurity prediction report, one expert said that this troubling scenario would entail a ransomware variant retrofitted with an “autonomous agent that has sophisticated, context-based decision-making capabilities."
Business Invoice Swapper
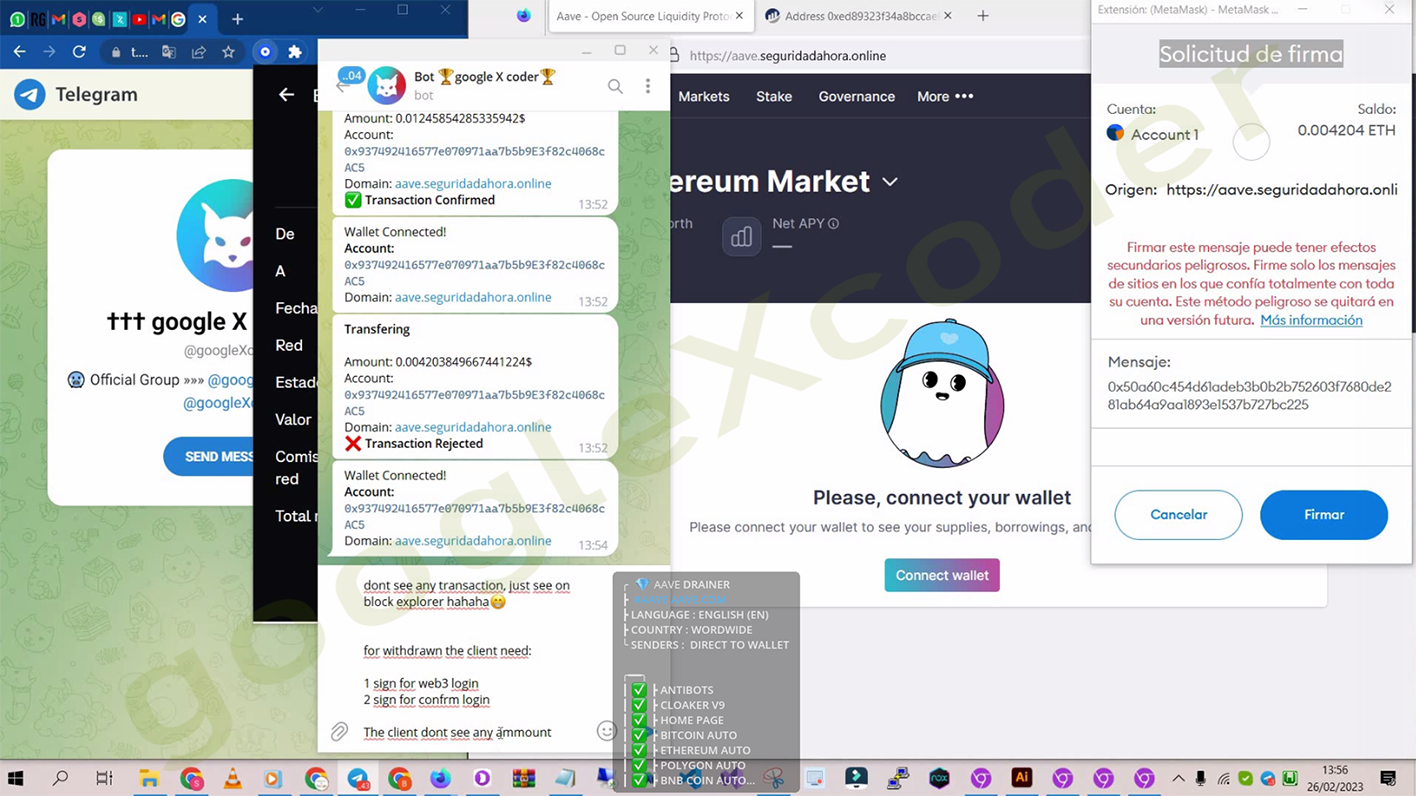
On December 30, 2023, GXC Team unveiled an updated version of their AI-powered tool, named "Business Invoice Swapper". This update was broadcasted through the official GXC Team’s official Telegram channel. The tool is being offered on a rental basis, with subscription plans starting from $2,000 per week, or alternatively, a one-time fee of $15,000 for unlimited access.
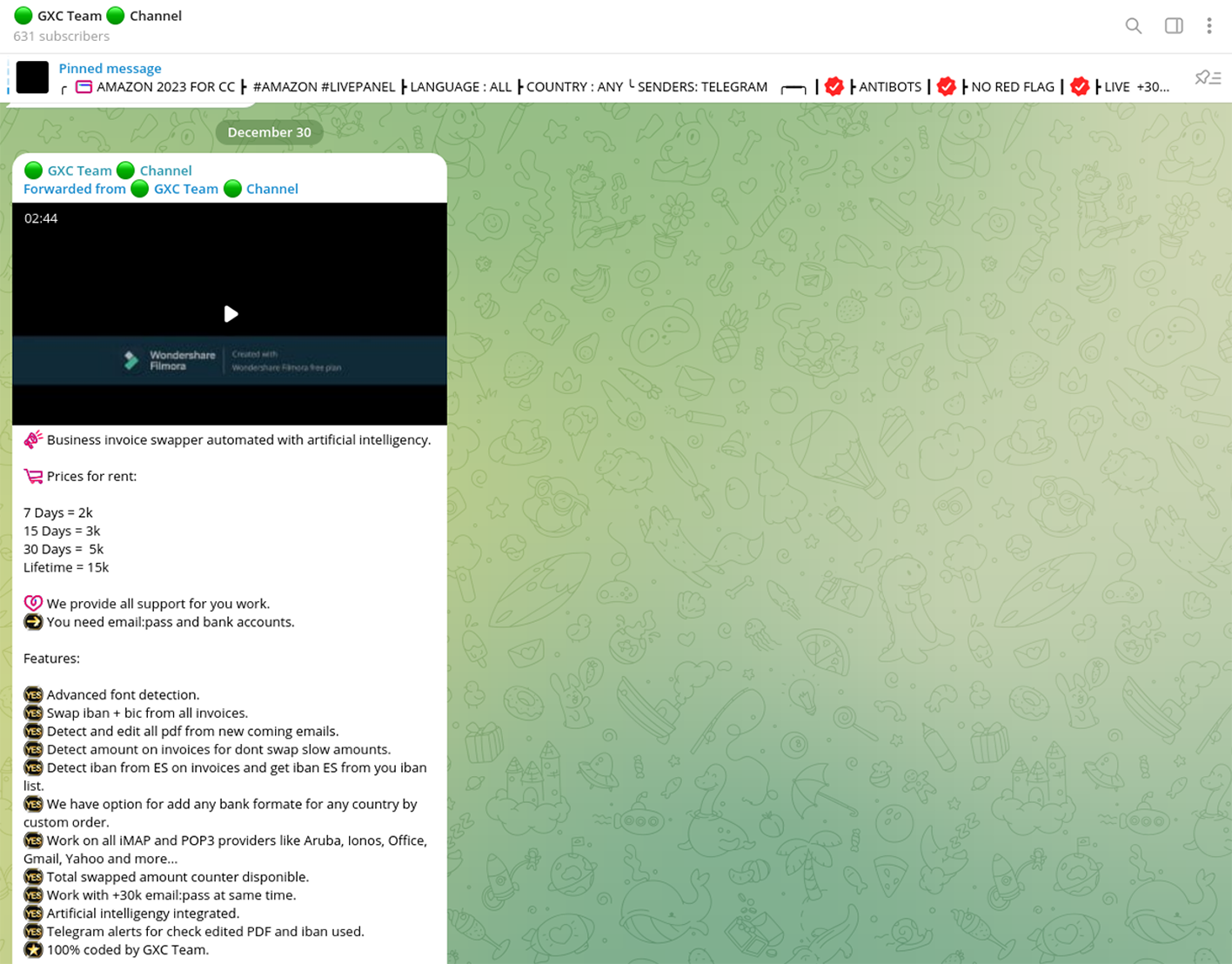
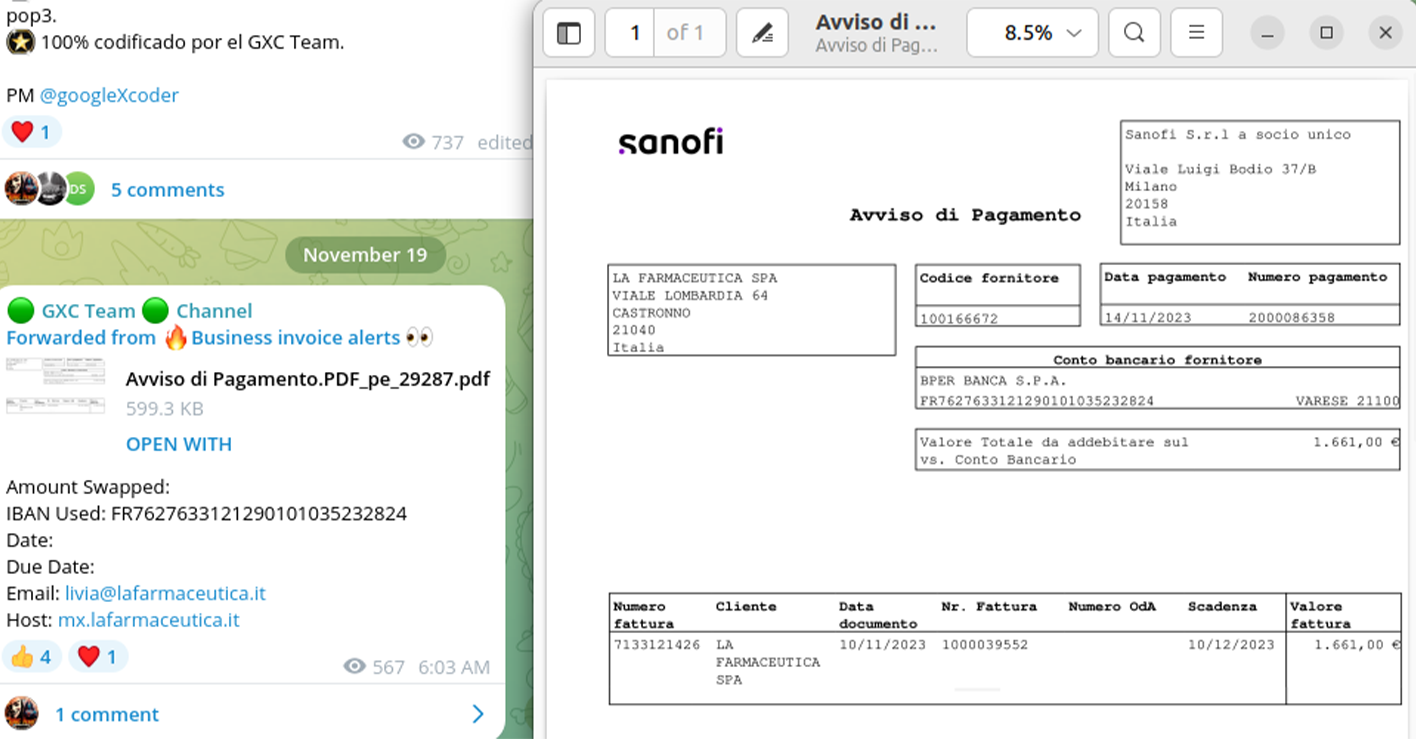
This tool employs proprietary algorithms to scrutinize compromised emails through POP3/IMAP4 protocols, identifying messages that either mention invoices or include attachments with payment details. Upon detection, the tool alters the banking information of the intended recipient (like the victim's supplier) to details specified by the perpetrator. The altered invoice is then either replaced in the original message or sent to a predetermined list of contacts. These methods are commonly employed in wire fraud and well-known bogus invoice scams. Often, accountants and staff in victimized companies do not thoroughly check invoices that appear familiar or nearly genuine, leading to unverified payments.
The tool's multi-language capability enables the automatic scanning of messages without any manual intervention, providing the actors with significant advantages.
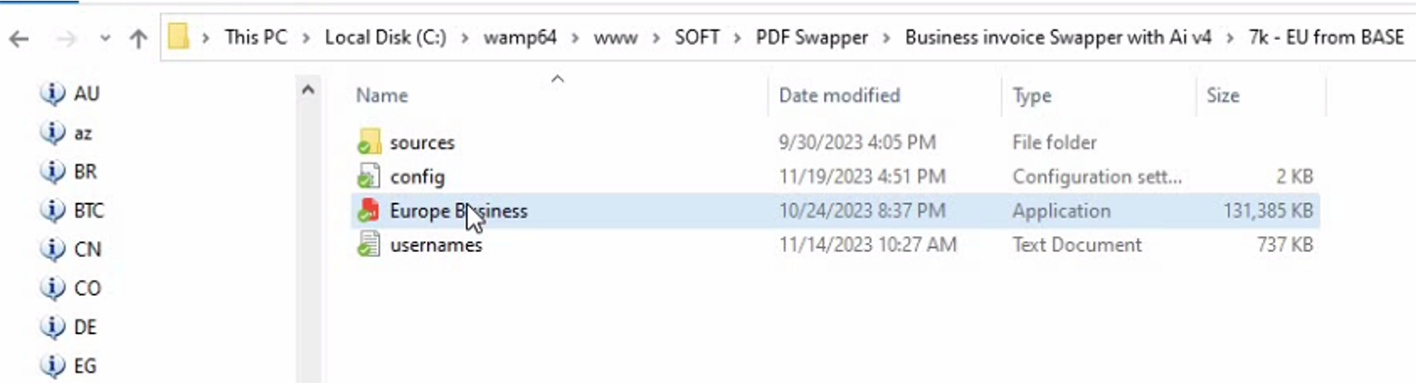
The tool's interface includes options to configure simple mail transfer protocol (SMTP) settings for sending out emails with the fabricated invoices it generates. Moreover, the tool includes a feature that sends reports to a designated Telegram channel, serving as an alternative to traditional command-and-control (C2C) communication. This functionality also extends to providing details about the generated invoices.
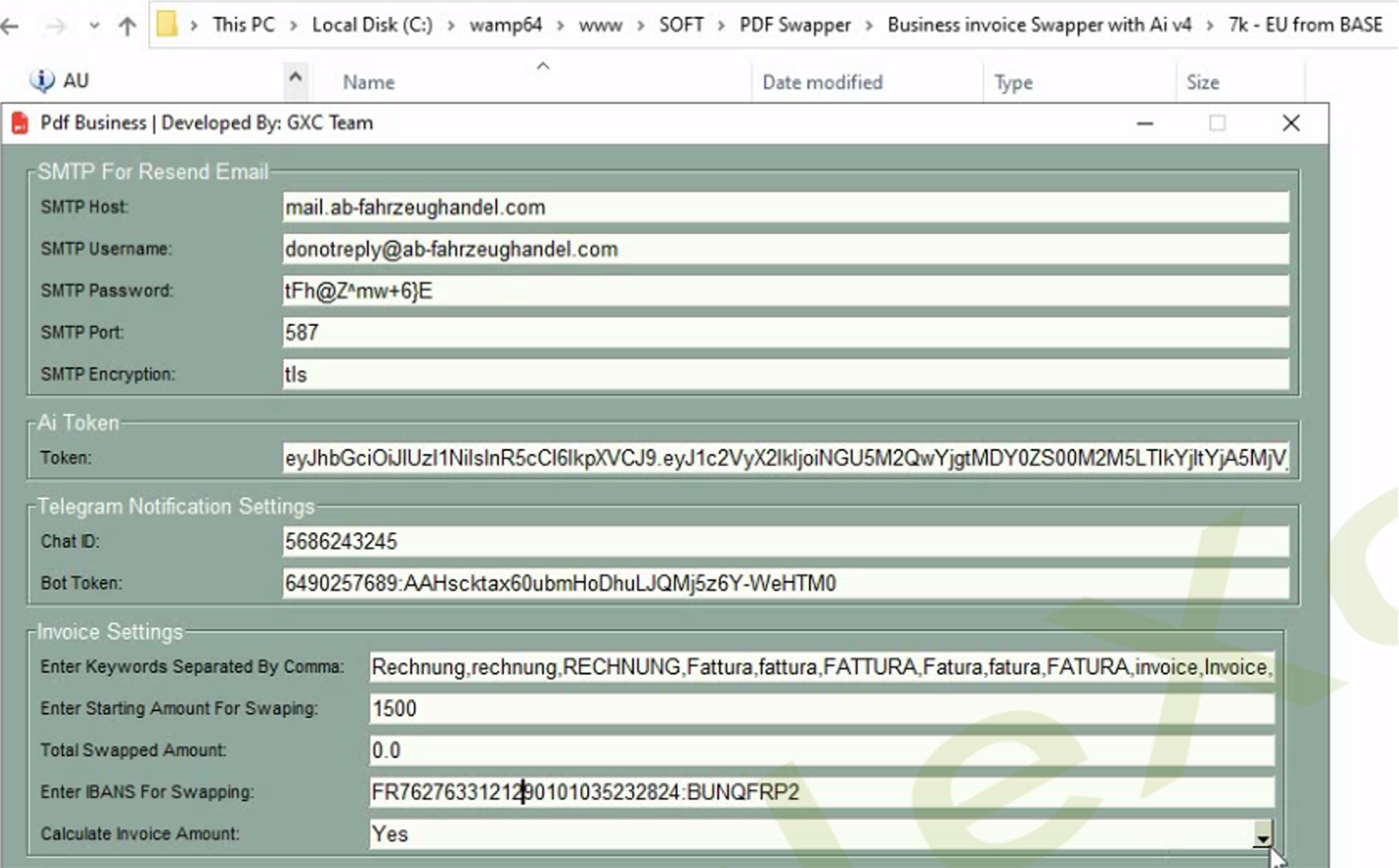
For the tool to function, the operator must input a list of compromised email accounts to be scanned. This process involves specifying the credentials, as well as the IBAN and BIC codes that will be used for the 'swapping' or spoofing process in the documents. It's noteworthy that most of the victim accounts identified were predominantly from the U.K. and various EU countries, including, but not limited to, Spain, France, Poland, Italy, Germany, Switzerland, among others.
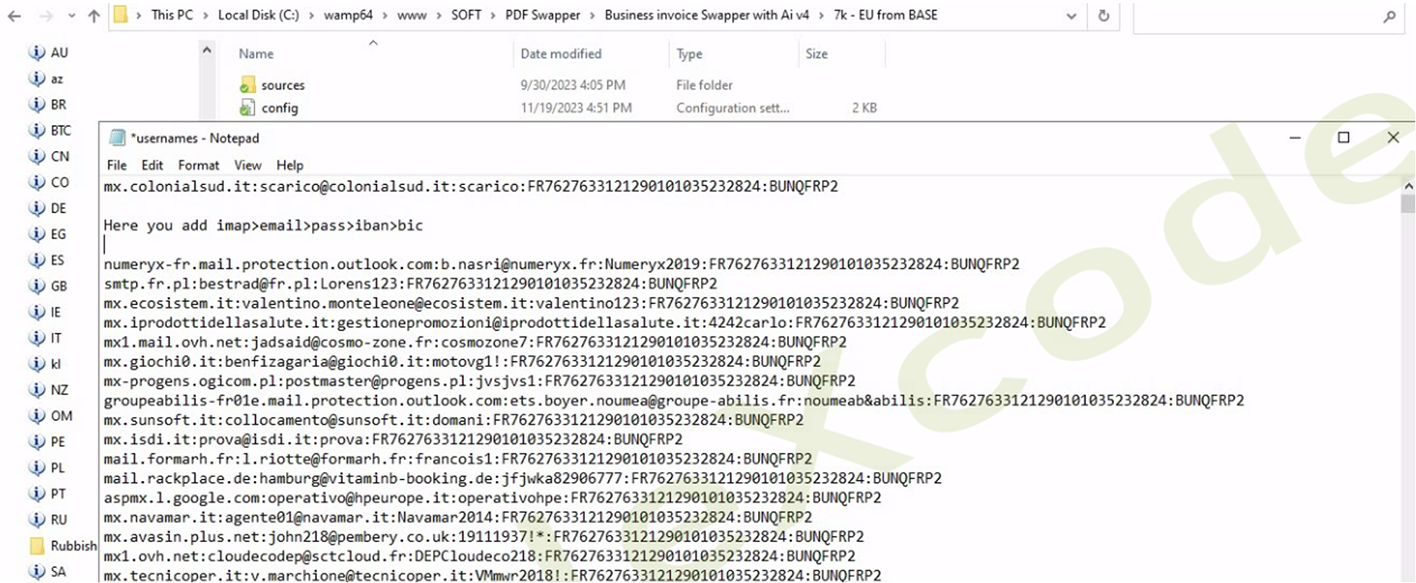
Once the list of victims is processed, the tool begins to scan each email account for any potential invoices. Its goal is to modify the recipient information in these invoices, replacing it with details specified by the malicious actor.
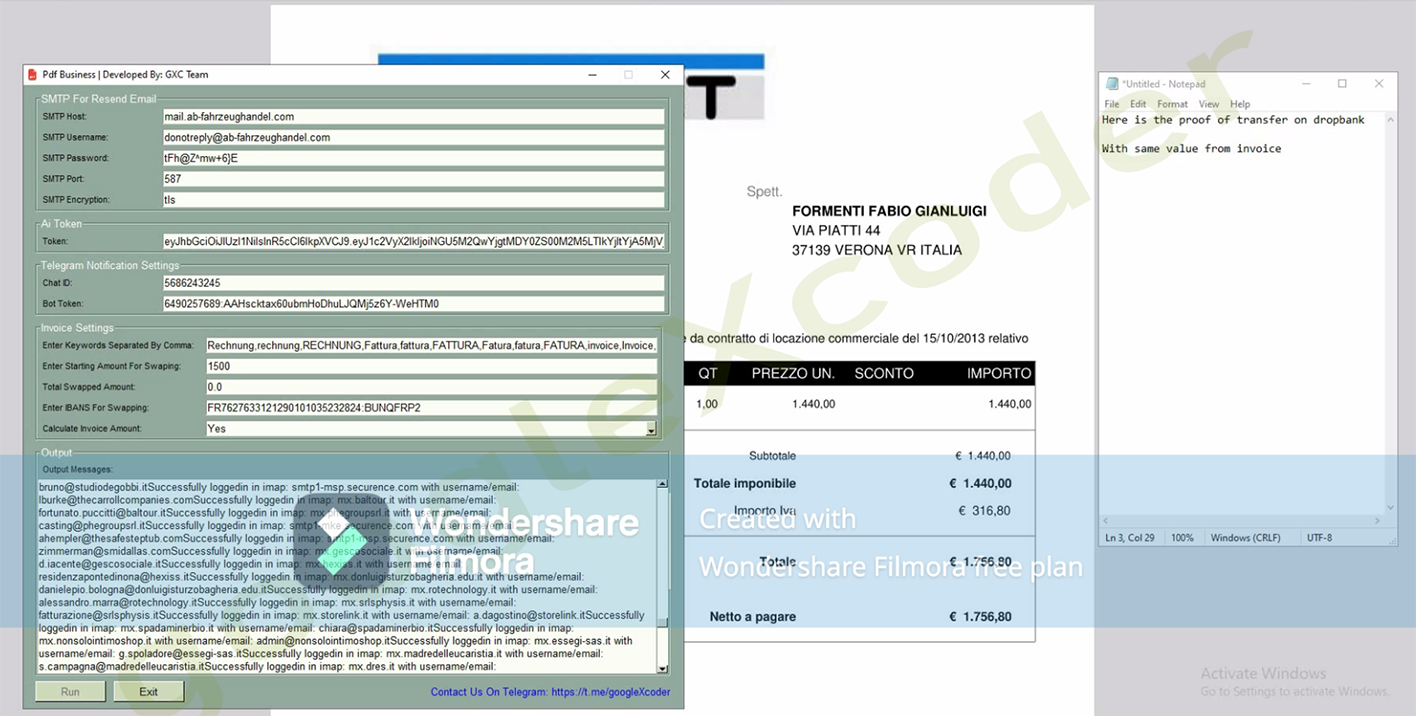
In this case, the creator of the tool effectively utilized AI for a specialized task – identifying invoices containing payment details. Additionally, the tool is equipped with multilingual support, enabling it to process and understand data in various languages, a crucial feature for handling invoices written in different languages.
Example of 'swapped' invoice:
Arsenal of Tools for Online-Fraud
Previously, the "GXC Team" gained notoriety for creating a wide array of online fraud tools, ranging from compromised payment data checkers to sophisticated phishing and smishing kits. They have been considered the masterminds in the illicit field of online-fraud tooling, as they have supplying fellow cybercriminals with a suite of ready-to-use tools designed to defraud innocent consumers globally. Additionally, GXC Team offers ongoing updates and technical support for conducting fraud. Presently, the tools crafted by the "GXC Team" are capable of targeting over 300 entities, including top financial institutions, government services, postal services, cryptocurrency platforms, payment networks, and major international online marketplaces.
Advanced Phishing Kits
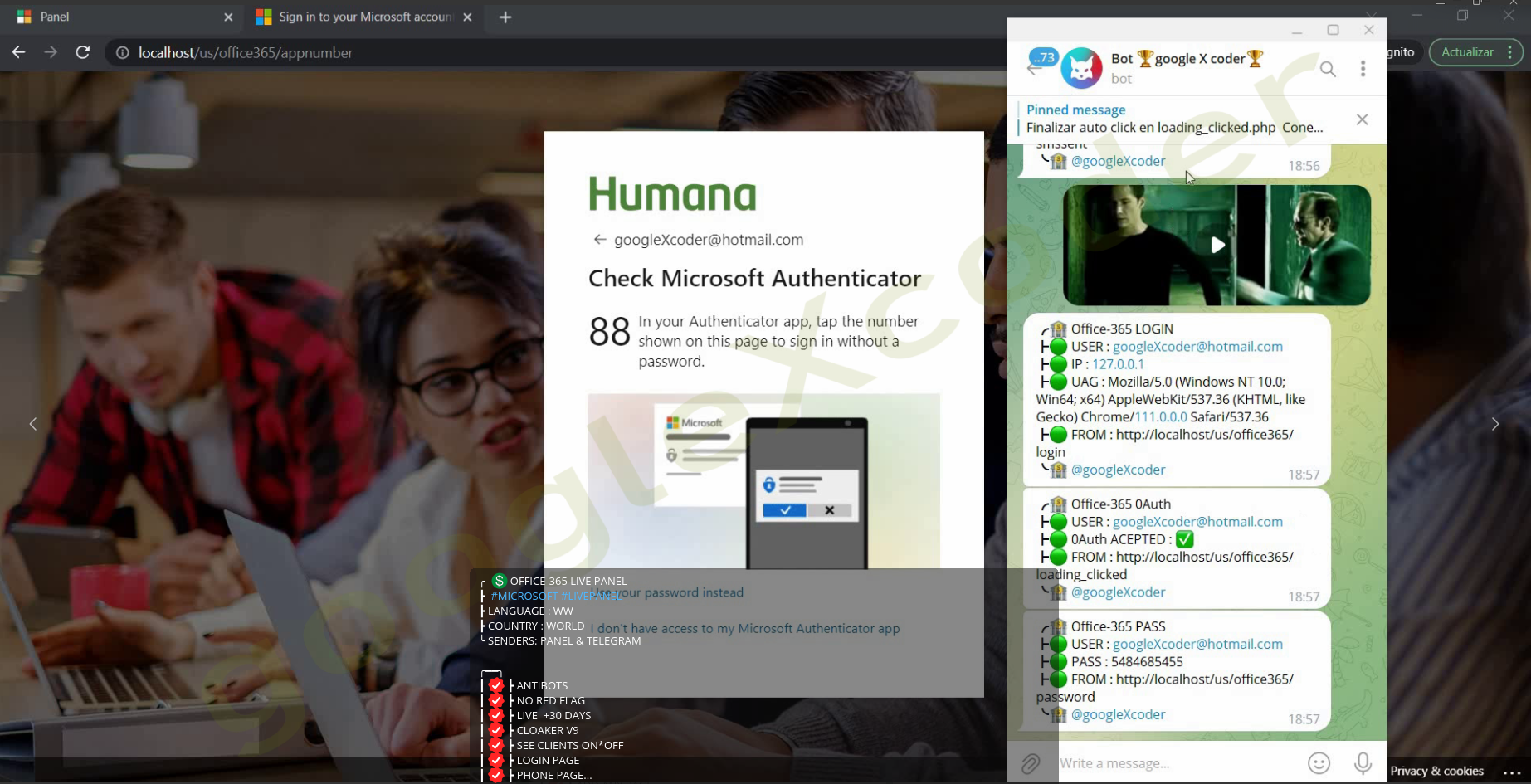
Among the initial offerings from the "GXC Team" was a sophisticated phishing kit designed for Office 365, equipped with support for two-factor authentication (2FA). This kit stands as one of their central products and is available for rent at a price of $999.
Notably, these threat actors targeted HUMANA, the fourth largest health insurance provider in the U.S, in a micro-targeted campaign leveraging this kit.
Attacks on Postal Services and Their Customers
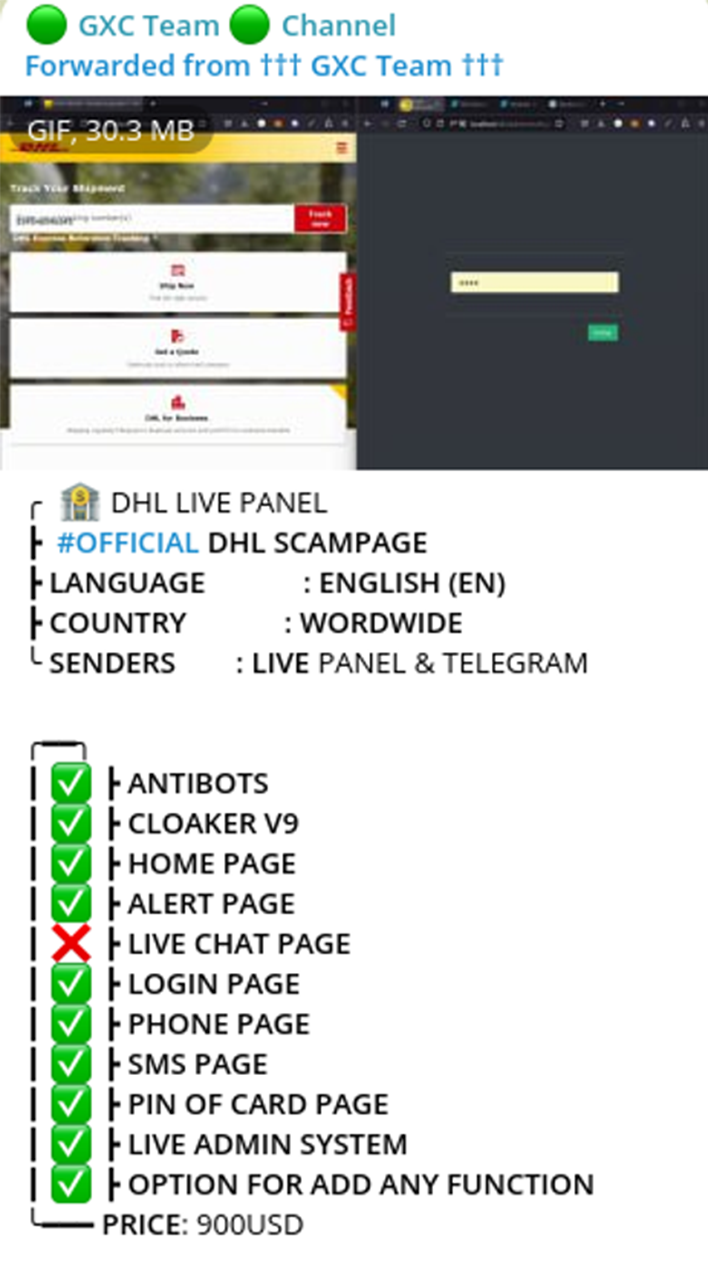
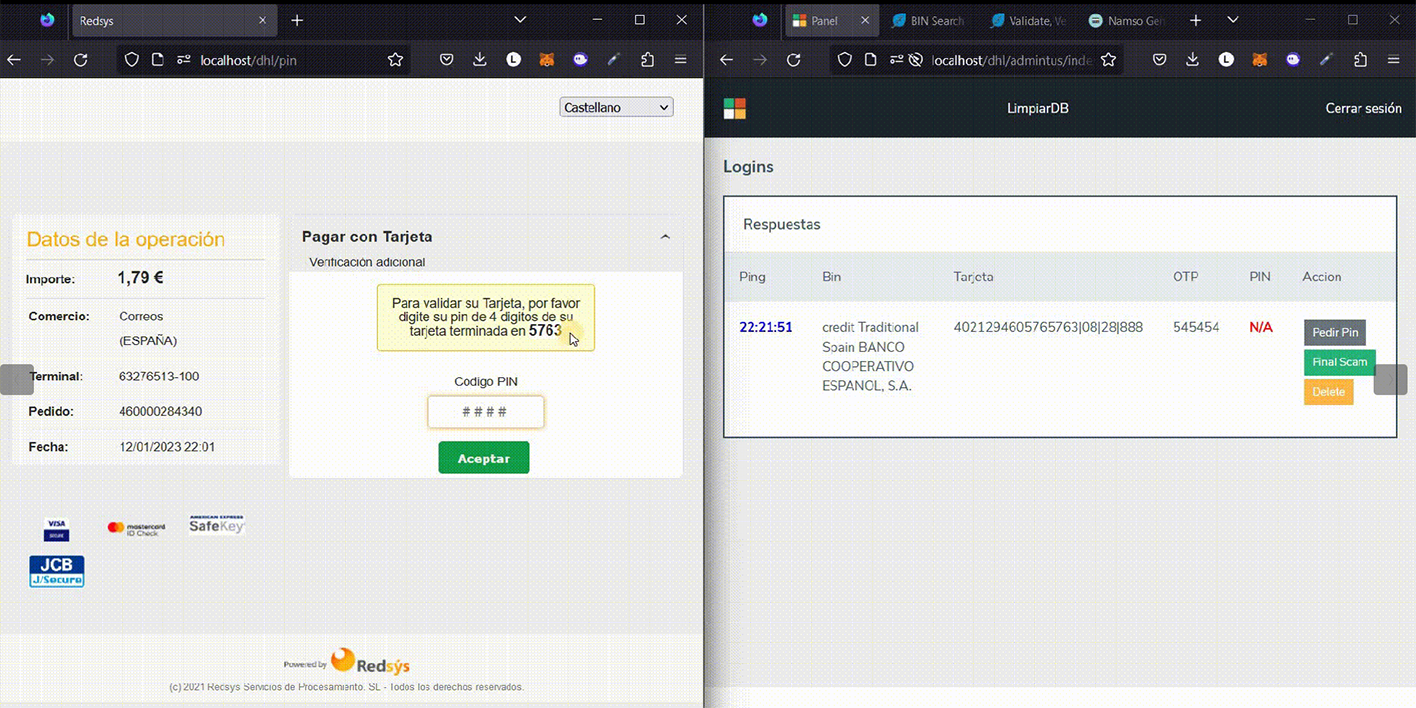
The range of tools developed by the GXC Team goes beyond just targeting email providers. They have also created kits aimed at defrauding customers of postal services, including DHL, Correos and An Post. Priced at $900, these kits have received favorable reviews and have drawn the attention of other cybercriminals.
This kit was among the first professionally designed toolsets capable of intercepting One-Time Passwords (OTP), a feature crucial for accessing compromised customer accounts and obtaining payment or credit-card information. These types of kits are commonly employed in 'smishing' campaigns by cybercriminals. Resecurity conducted an investigation into one such incident involving the Smishing Triad, a Chinese-speaking group that targets postal services and their customers globally as part of their fraudulent activities.
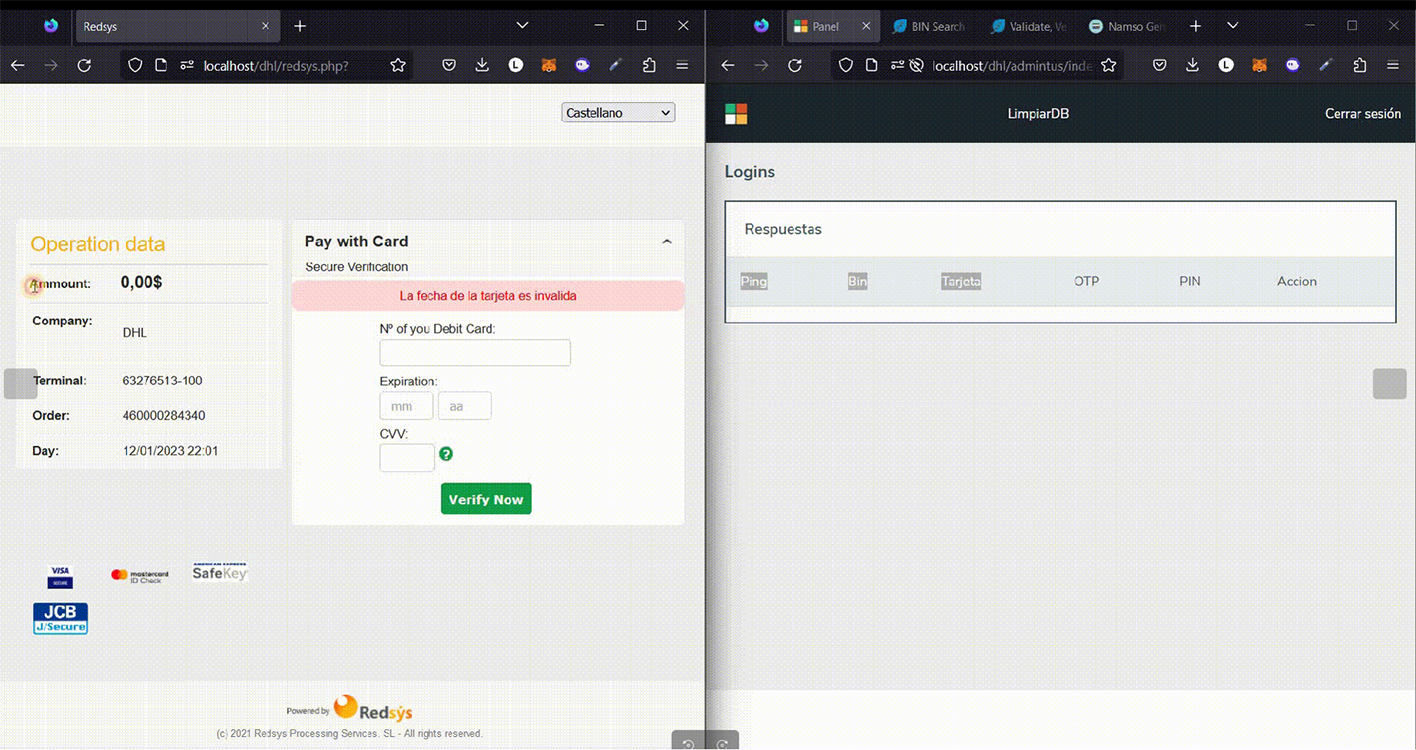
Victims of GXC-engineered forgeries encountered a convincingly designed interface mimicking DHL, available in several languages, including Spanish, enhancing the kit’s credibility.
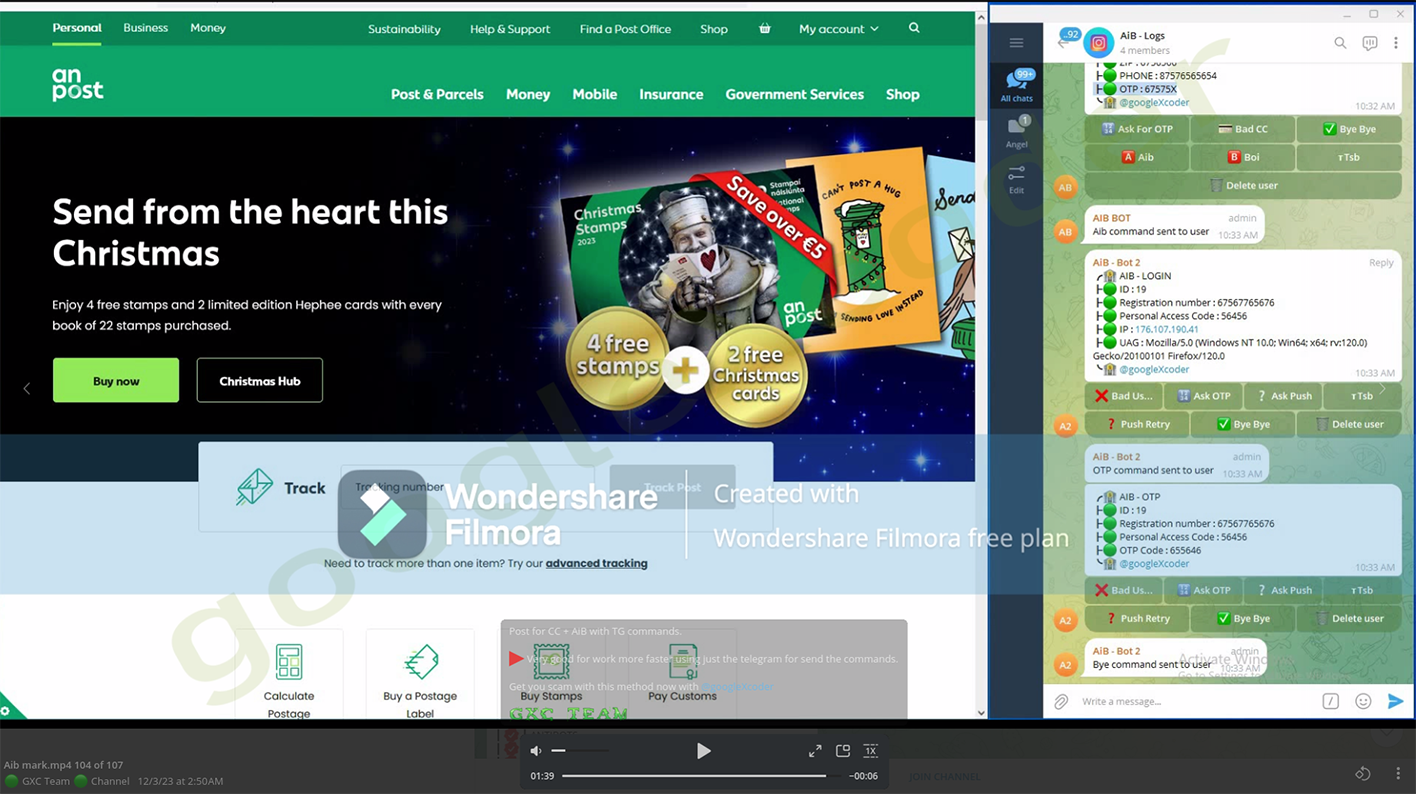
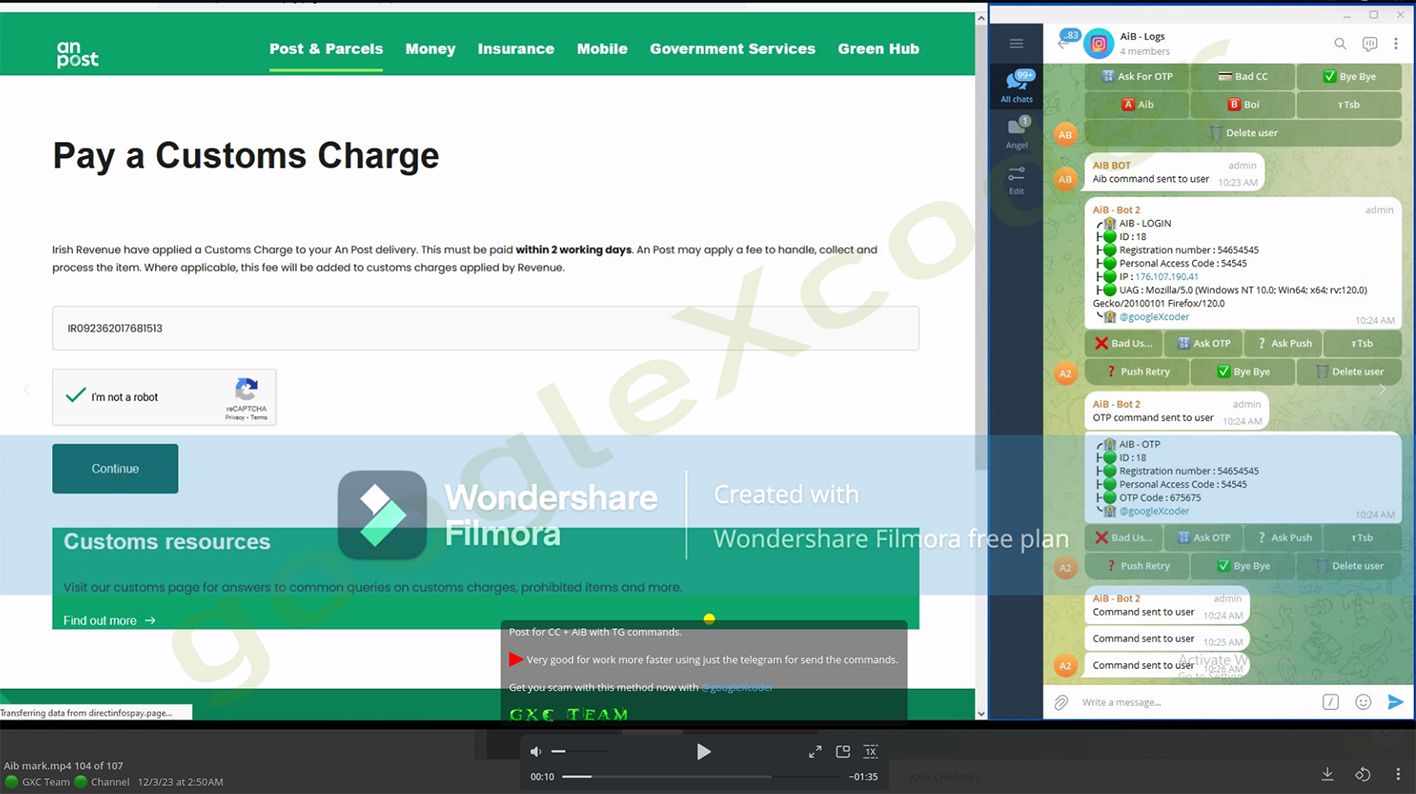
During the recent Christmas and New Year's Eve period, Resecurity observed a particularly vigorous campaign targeting An Post, the state-owned provider of postal services in Ireland.
Defrauding Millions for a Few Hundred
After targeting postal services and logistics providers, the actors shifted their focus to the banking sector. They released a phishing kit specifically designed for EVO Banco, S.A.U., a prominent Spanish bank headquartered in Madrid.
Video demonstration:
Spanish Language Fraud
Interestingly, a noticeable pattern emerged with a focus on Spanish language support. This was evident not only in the phishing kits but also in some of the postings made by the actors, which were written in Spanish.

The reason behind the emphasis on Spanish-language marketing push remains unclear. It's uncertain whether this focus was due to a team member's Hispanic background or if the Spanish-speaking victim demographic was particularly lucrative for the perpetrators at that time. One explanation may be that threat actors were deliberately targeting Spain, as phishing kits were developed for several leading Spanish banks, including ABANCA, Banca March, Banco de Sabadell, Grupo Caja Rural, Unicaja Banco SA, Caixa Enginyers, Banco Mediolanum, Laboral Kutxa, Eurocaja Dynamic, BBVA, and Santander. The geo-targeting Spain aligns with broader regional trends that have seen the European country become one of the leading recipients of “remote online attacks in the world,” according to 2023 vendor reports.
Beyond Spain, the most recent edition of the United Nation’s International Telecommunication Union, published in 2021, found that Latin America is the least prepared region in the world for cyberattacks. Broadly, this trend is due to rapid digitization and smartphone adoption over the last decade – regional developments that have far exceeded the pace of security integration. In fact, recent vendor research found that three of the top-10 most cyber-insecure countries in the world are in the the LatAm region: Honduras, Nicaragua, and Venezuela. It should also be noted that many Spanish banks have large operating footprints in the LatAM region. Therefore, GXC Team may be casting a wide net in the Spanish-speaking world and purposing their kits and sales strategies to capitalize on geo-specific cybercrime trends.
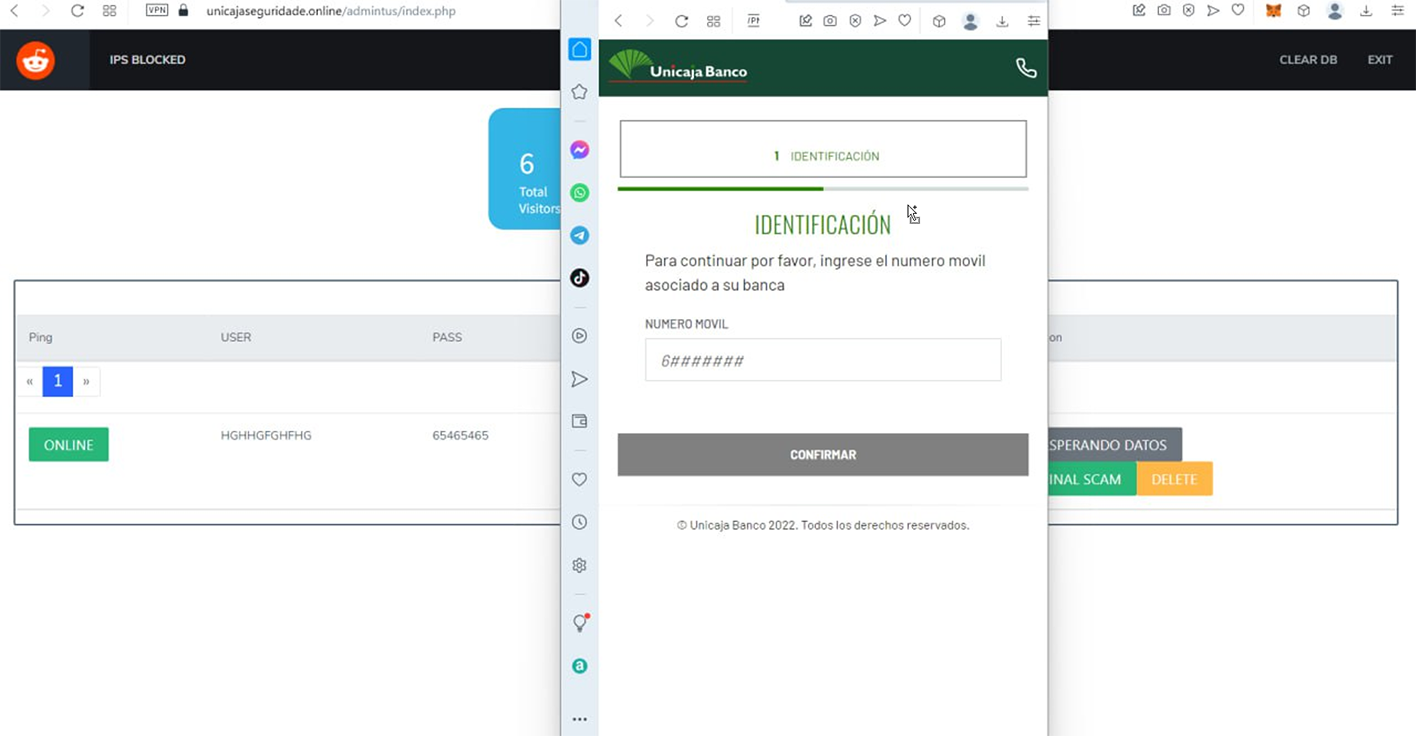
2FA/OTP Interception via Fake Mobile Banking Apps
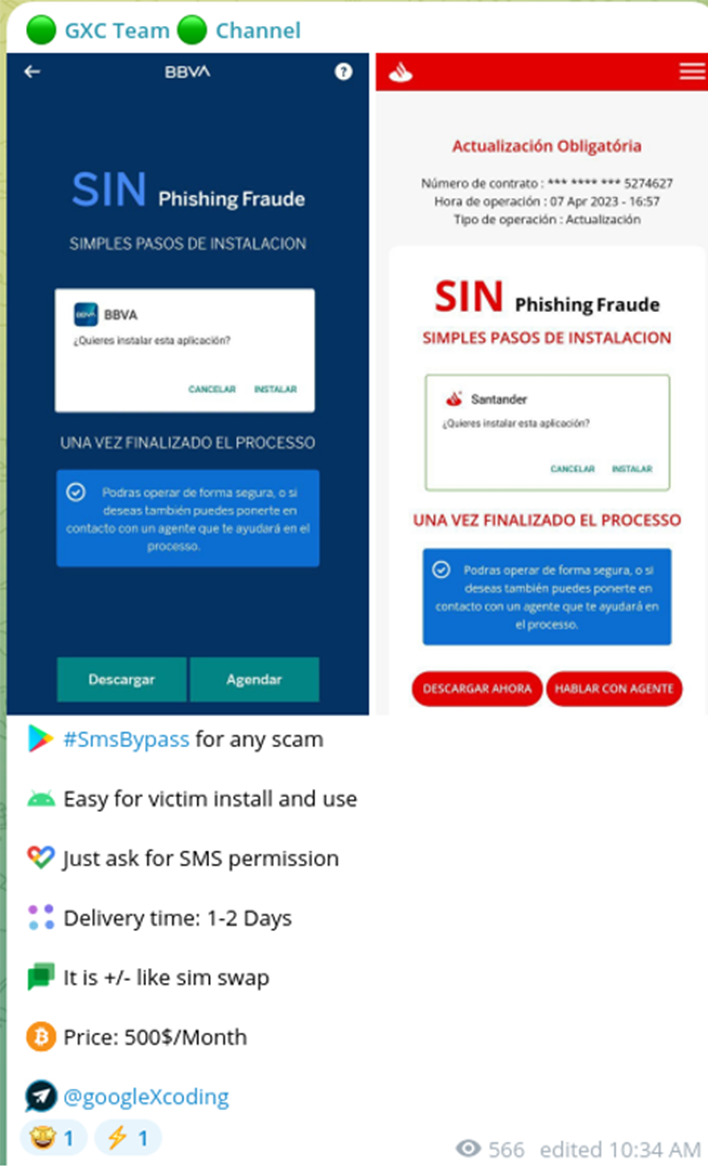
In a novel approach to circumvent two-factor authentication (2FA), the threat actors crafted malicious Android code that mimics official mobile banking applications. Victims are tricked into installing this fake app under the guise of confirming their OTP (One-Time Password), which is then intercepted and transmitted to a command-and-control (C2C) server managed by the attacker. The necessary login credentials for online banking systems are previously harvested through a phishing kit. Once the OTP is intercepted, the malicious actor can access the victim's banking account, utilizing geographically relevant residential proxies to facilitate this unauthorized access.
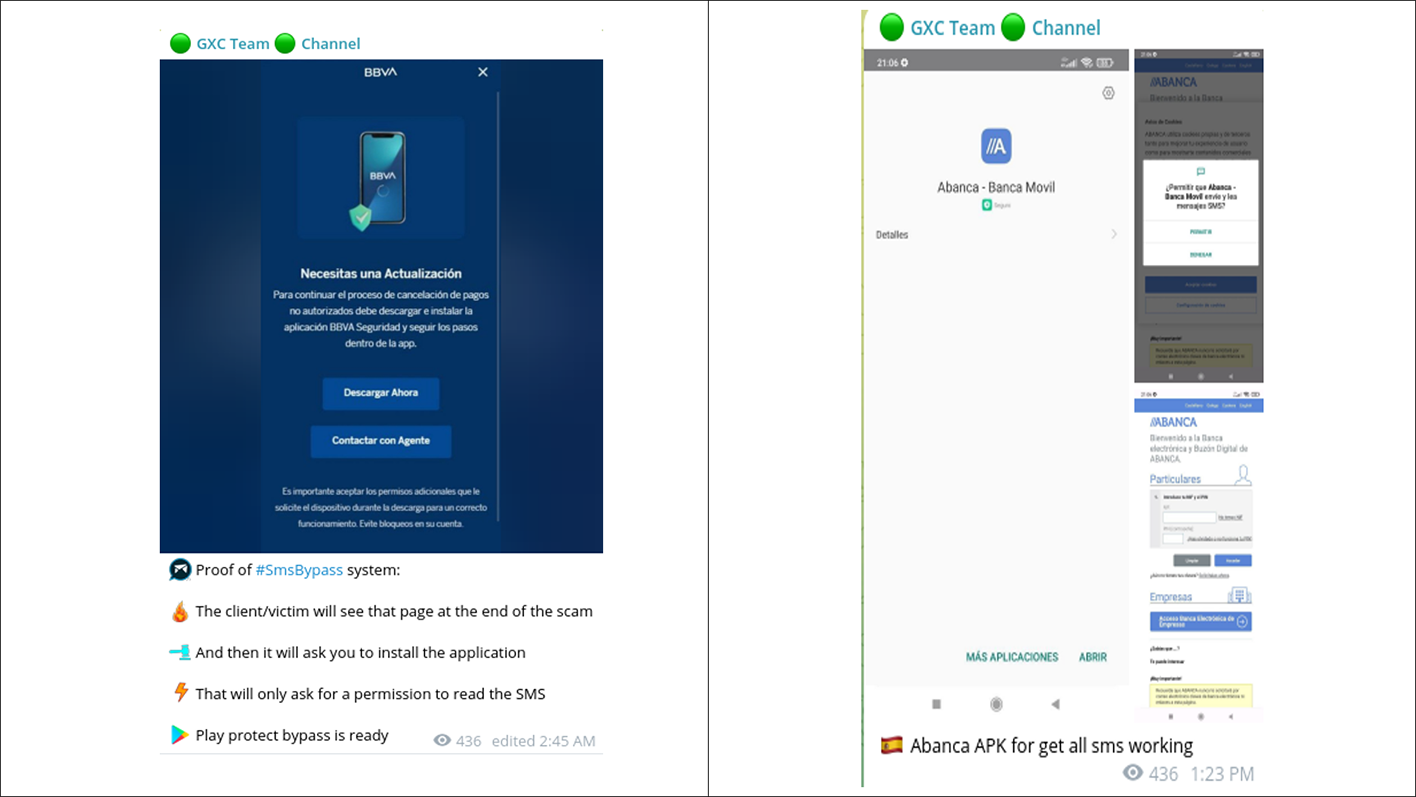
This system, designed to bypass two-factor authentication, has been implemented by threat actors across multiple services. The scheme has also been successfully tested and utilized by other malicious actors in their operations.
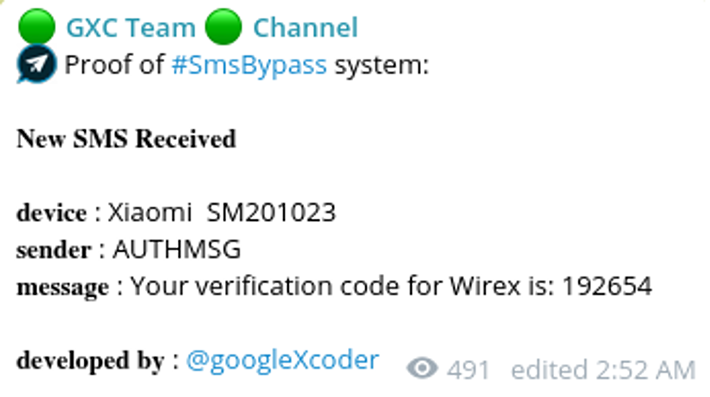
In one of their videos, the actors showcased their ability to successfully circumvent Google Protect, demonstrating the effectiveness of their methods. It is highly likely that these malicious actors achieved their goals by exploiting stolen Google Developer digital certificates, which are readily available for sale on the Dark Web. Alternatively, they may have used programming techniques that do not trigger significant behavior-based alerts. Notably, the fake mobile apps they developed predominantly masqueraded as legitimate financial institutions, illicitly using the branding of these trusted organizations for their fraudulent activities.
Moving beyond targeting banks, the GXC Team also developed a phishing kit tailored for Coinbase users. Priced at $900, this kit was specifically aimed at customers, again in Spain, expanding the group's focus to include cryptocurrency platforms.
Moving beyond targeting banks, the GXC Team also developed a phishing kit tailored for Coinbase users. Priced at $900, this kit was specifically aimed at customers, again in Spain, expanding the group's focus to include cryptocurrency platforms.
The phishing kit developed for Coinbase was notably effective and included the feature of sending notifications via Telegram. In addition to Coinbase, the "GXC Team" crafted and released tailored phishing kits for other prominent cryptocurrency trading platforms, including Binance, AAVE, DAO Maker, and DYDX Exchange. DAO Maker, representing Decentralized Autonomous Organization, is renowned as a leading launchpad and incubator for new cryptocurrencies and non-fungible tokens (NFTs). These digital assets are particularly attractive to cybercriminals due to the near impossibility for victims to recover them once they are stolen.
A notable advantage of these phishing kits is their capability for an automatic "silent send" function. This feature enables the direct transfer of stolen funds to a wallet preselected by the attacker as soon as the victim falls prey to the phishing attempt. This functionality is particularly effective for pilfering funds from web-based wallets and various cryptocurrencies held in the accounts, including Bitcoin, Ethereum, Polygon, and BNB. This stealthy and automated transfer mechanism significantly enhances the efficacy of these phishing operations.
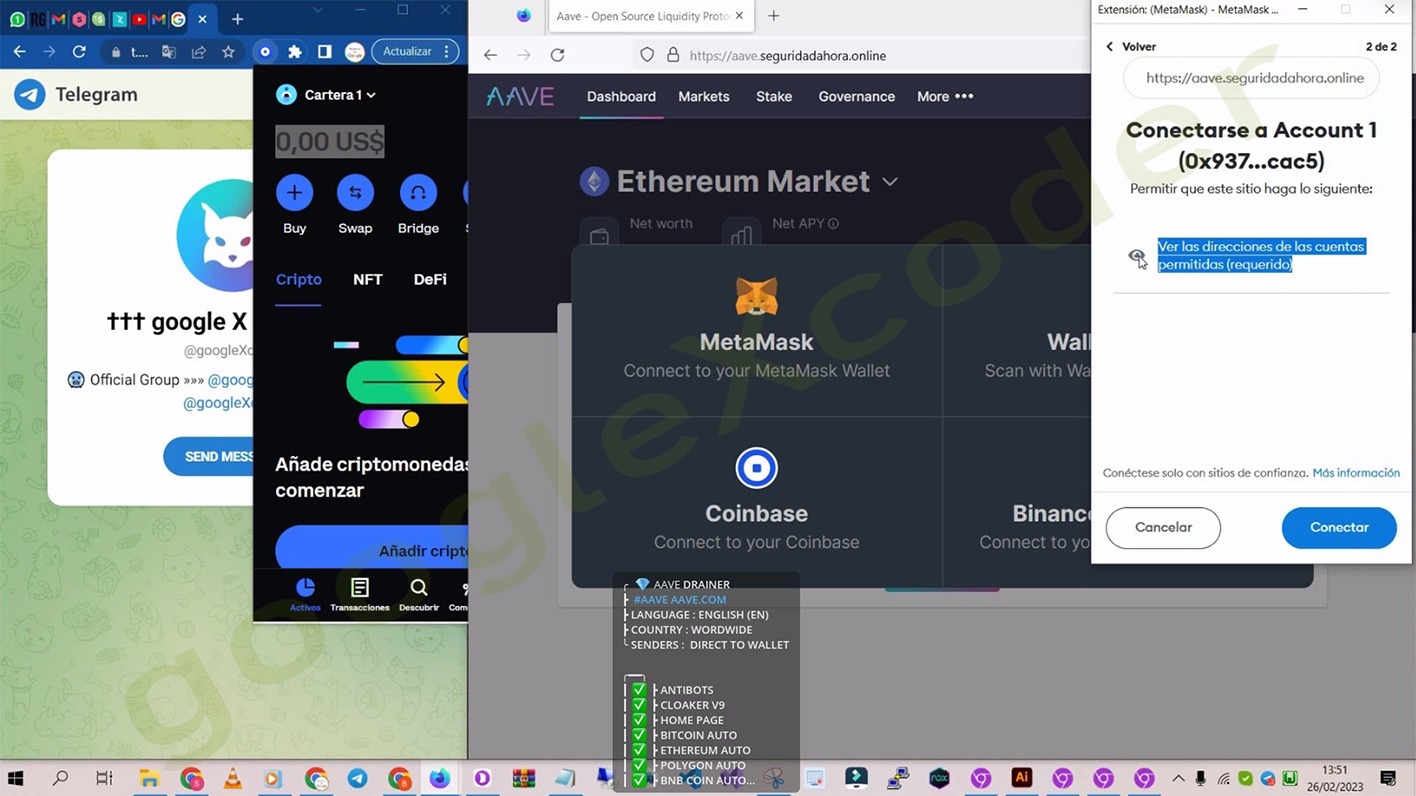
The record of successful transactions executed through this system is configured to be sent directly via Telegram, providing the attackers with real-time updates on their illicit activities.
Video demonstration:
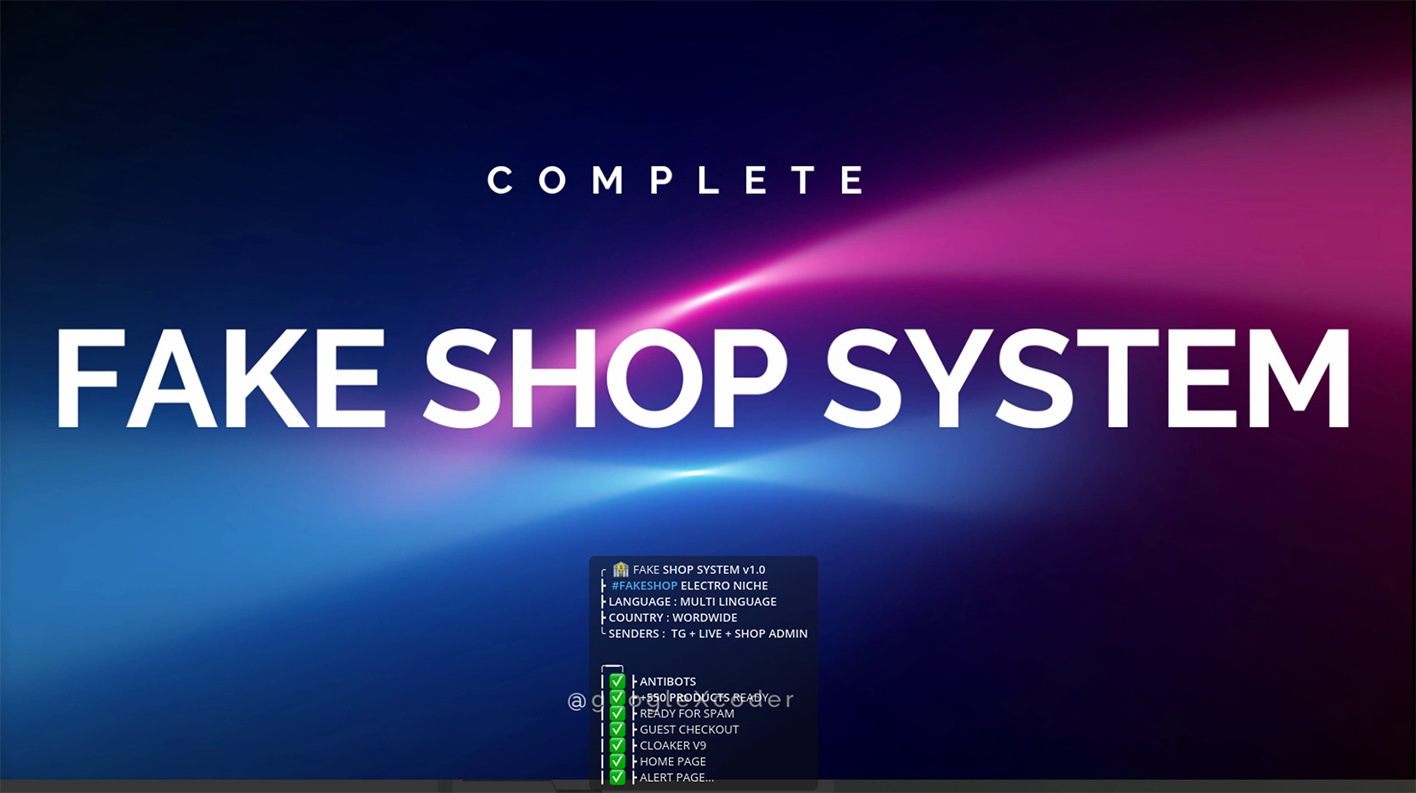
Fake Shop System 4.0
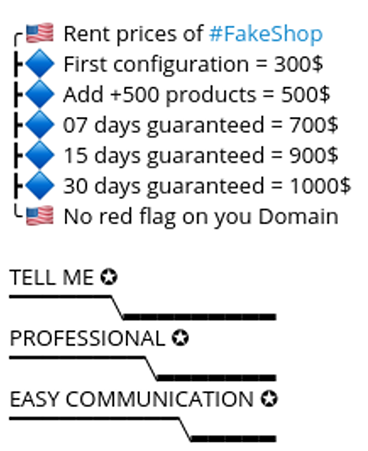
Early in February, the GXC Team introduced an entirely new category of tools: a fake online-shop system, priced at $4,000. This system comes pre-loaded with over 400 products, meticulously curated to appear authentic, thereby requiring only a domain name registration from the operator to imitate well-known brands. The primary focus of this fake shop is on electronic goods, strategically targeting a customer base with significant spending power.
Additionally, for an extra charge, the group offered bespoke customization options and flexible rental terms for this fake online shop, catering to the specific preferences of their clients.
The kit came equipped with features for credit card (CC) and OTP interception via SMS. The toolset also included the capability for interactive notifications through Telegram, enhancing its functionality and user experience.
One of the initial counterfeit shops created by this kit was modeled after Mi Electro, a popular chain of electronic stores in Spain, and K-Tuin, an Apple Premium Reseller located in Madrid, Spain, showcasing the kit's ability to convincingly replicate established retail businesses.
The malicious actors populated their fake online shops with a wide array of non-existent electronic products. These shops were powered by a comprehensive Content Management System (CMS) akin to Shopify, enabling them to manage inventory, adjust product prices, and modify item descriptions seamlessly.
Video demonstration:
As part of their ongoing development, the threat actors integrated a system for generating fake reviews, likely utilizing existing GPT engines. This system could produce extensive, authentic-looking text that resembled positive customer feedback on specific products.
Additionally, the tools they developed included the capability to monitor a victim's activity on the fake web page almost in real-time, further enhancing the effectiveness of their fraudulent scheme.
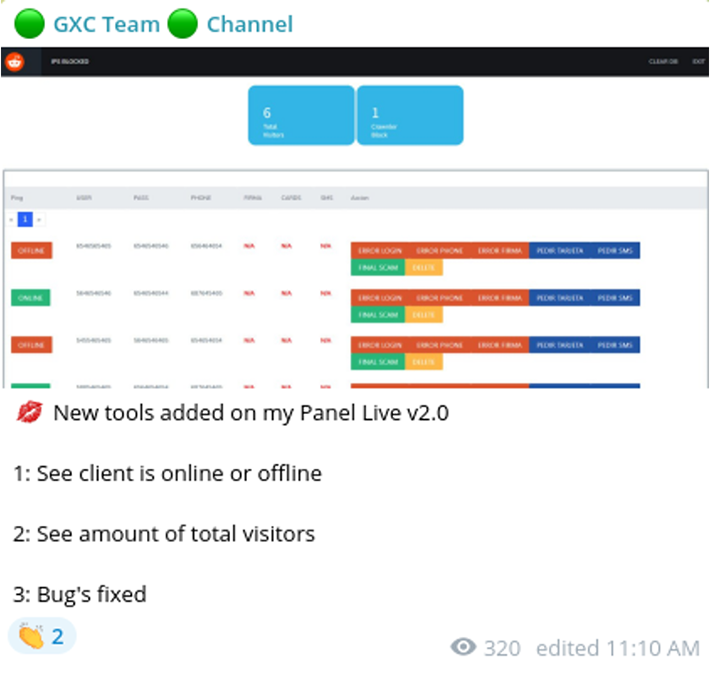
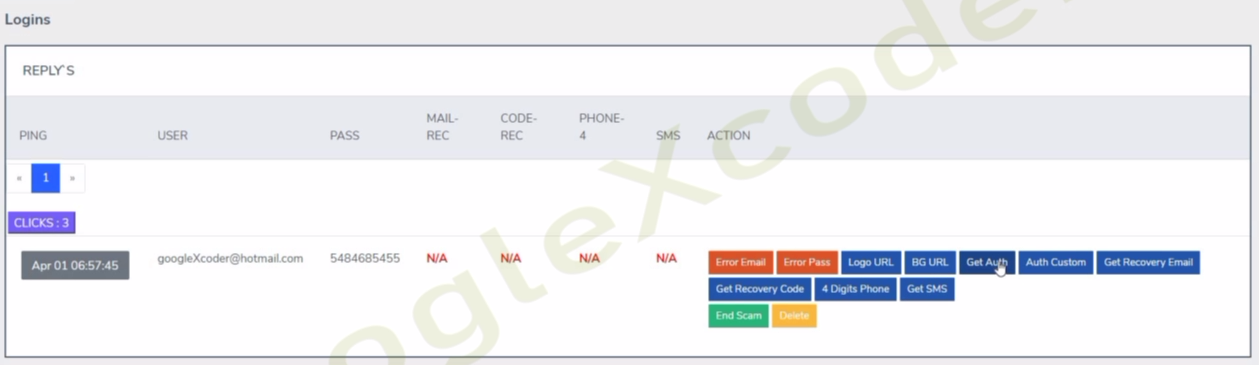
Being able to see the victim in close to real-time enables the threat actors to interact with the person browsing the phishing kit by sending various commands available via the kit’s administrative panel:
- Logo URL
- BG URL
- Get Auth
- Auth Custom
- Get Recovery Email
- Get Recovery Code
- 4 Digits Phone
- Get SMS
- End Scam
For example, the "Get SMS" command compels the victim to input their OTP (SMS) directly into the phishing kit. Upon interception, threat actors can then bypass the 2FA check and proceed with their malicious activities.
The attackers continually update their range of customized shops and services to include interfaces resembling well-known platforms like Airbnb, Amazon. These updates not only enhanced the visual authenticity of the shops but also introduced additional features to improve their functionality and deceptiveness.
The fake shops were designed to support a variety of payment methods and systems, providing a facade of legitimacy to their operations. The malicious actors would then employ "money mules" to receive funds from their victims, further complicating the tracking of illicit financial transactions.
The threat actors also released a phishing kit designed to mimic Amazon, which could be sold separately from fake shop.
In addition to their fake shop engine, the group also developed several pre-made fake shops that mimicked Chrono24, one of the leading marketplaces for luxury watches. These ready-to-use shops allowed for quick deployment in their fraudulent operations, further diversifying their targets and schemes.
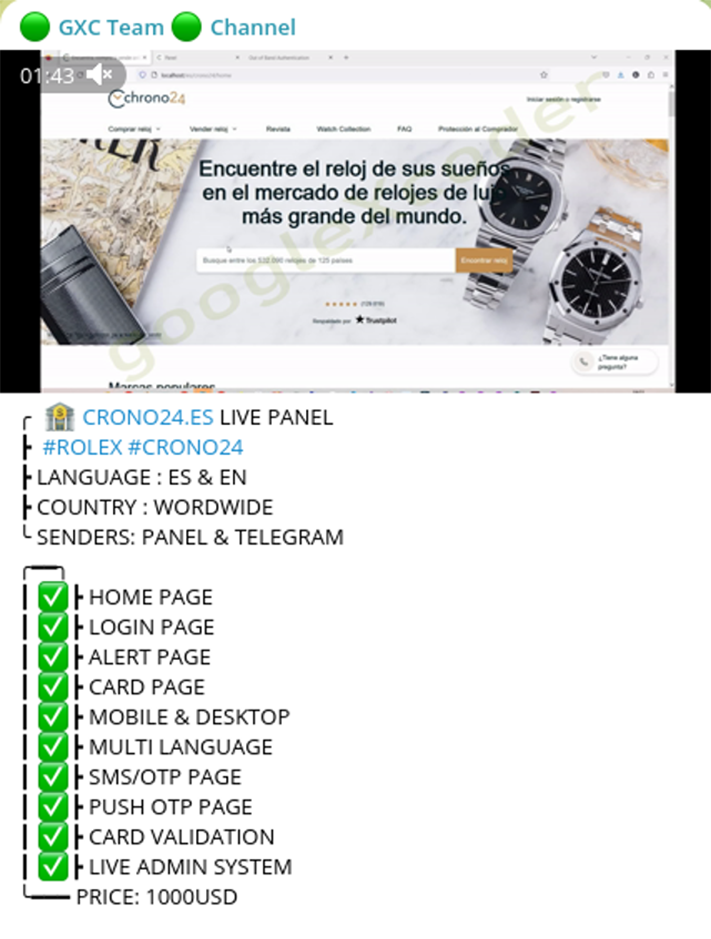
Video demonstration:
Apart from their focus on Amazon and Walmart, the group also crafted a phishing kit tailored for Sumup. Sumup offers point-of-sale hardware and software solutions for businesses to accept various payment methods. By targeting Sumup, the actors expanded their reach to include businesses that rely on this payment processing service.
In their future plans, the team intends to release multiple phishing kits targeting leading banks in the UK and the European Union. These banks include ING in the Netherlands, Santander Consumer Bank (Deutschland), Deutsche Bank, Postbank, DKB AG (Das kann Bank), and BBBank eG (formerly Badische Beamtenbank), a German cooperative bank. This expansion indicates their readiness to further exploit financial institutions across different regions.
In addition to traditional banks, the group also set their sights on N26, a German neobank headquartered in Berlin. The cybercriminals devised a phishing kit centered around the delivery of an email confirmation letter. Victims would receive an email that appeared to be sent from N26, prompting them to validate their customer information. This approach allowed them to target users of modern, digital banking services.
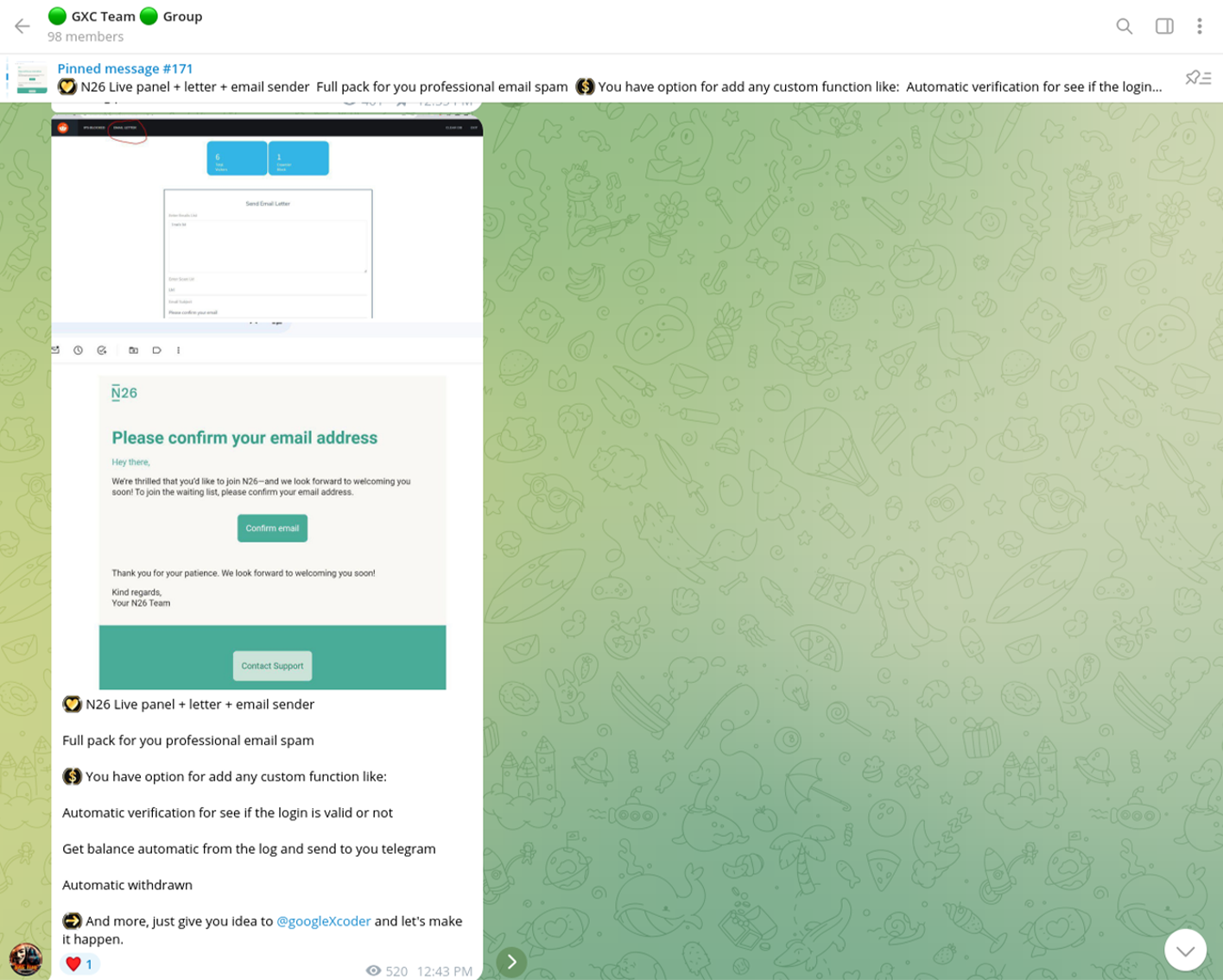
The group's activities extend beyond Dutch and German banking customers. GXC Team also launched a new phishing kit aimed at Halifax, a British banking brand that operates as a trading division of Bank of Scotland, which is in turn a wholly owned subsidiary of Lloyds Banking Group. This expansion into the British banking sector demonstrates their intent to target a wider range of financial institutions.
The GXC Team also offers a specialized category of tools: compromised data checkers. These tools were used by cybercriminals to identify clients of various online services, highlighting their versatility in assisting malicious actors across different types of cybercriminal activities.
Bunq Checker
The tool allowed to cross-check customers of Bunq, a popular digital bank.
Amazon Checker
One of the tools provided by the GXC Team enabled users to cross-check a list of phone numbers to determine if they were associated with Amazon accounts. This capability was particularly useful for cybercriminals planning mobile phishing campaigns, often referred to as "smishing." By identifying potential Amazon customers, threat actors could send malicious iMessages or SMS messages to these individuals. Notably, the threat actors highlighted that one effective tactic for such campaigns was to leverage traffic sent from compromised or defrauded Google Ads accounts, which allows for precise targeting.
The tool didn't require any unique setup and demonstrated efficient performance.
AMEX Checker
One of GXC Team’s earlier tools was designed to expedite the identification of valid American Express (AMEX) customers by leveraging stolen email data. This tool, known as the "AmericanExpress Checker," scanned email messages, identified potential AMEX-related content, and assessed whether the email recipient could be a registered AMEX user. This information was then used for various nefarious purposes, including payment fraud and identity theft. Threat actors could gain access to victims' AMEX accounts and attempt unauthorized transactions using stolen identity and password data.
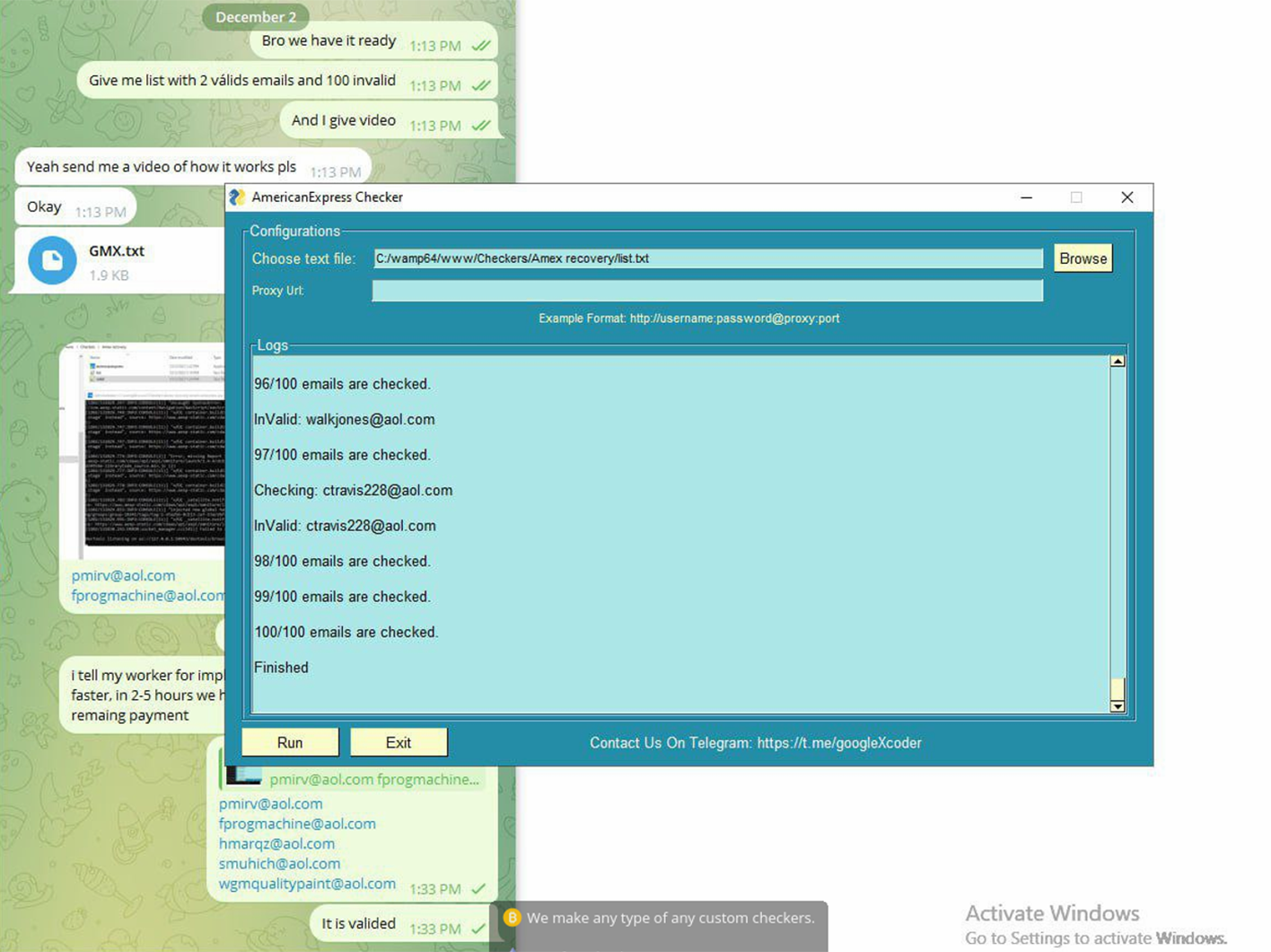
The GXC Team also developed a range of other tools, including multiple phishing kits that featured customized templates aimed at targeting customers of prominent payment systems, cryptocurrency providers, and banks. These kits were designed to facilitate cybercriminals in their efforts to deceive and defraud individuals and organizations within the financial sector.
Attacks against e-government
GXC Team has also created several kits designed to pilfer identity information from Australian and Spanish citizens through the use of fake government websites. In the case of Australia, the actors impersonated the "my.gov.au" portal, luring victims into providing their personal information. This tactic underscores their commitment to identity theft and the exploitation of unsuspecting individuals through deceptive means online.
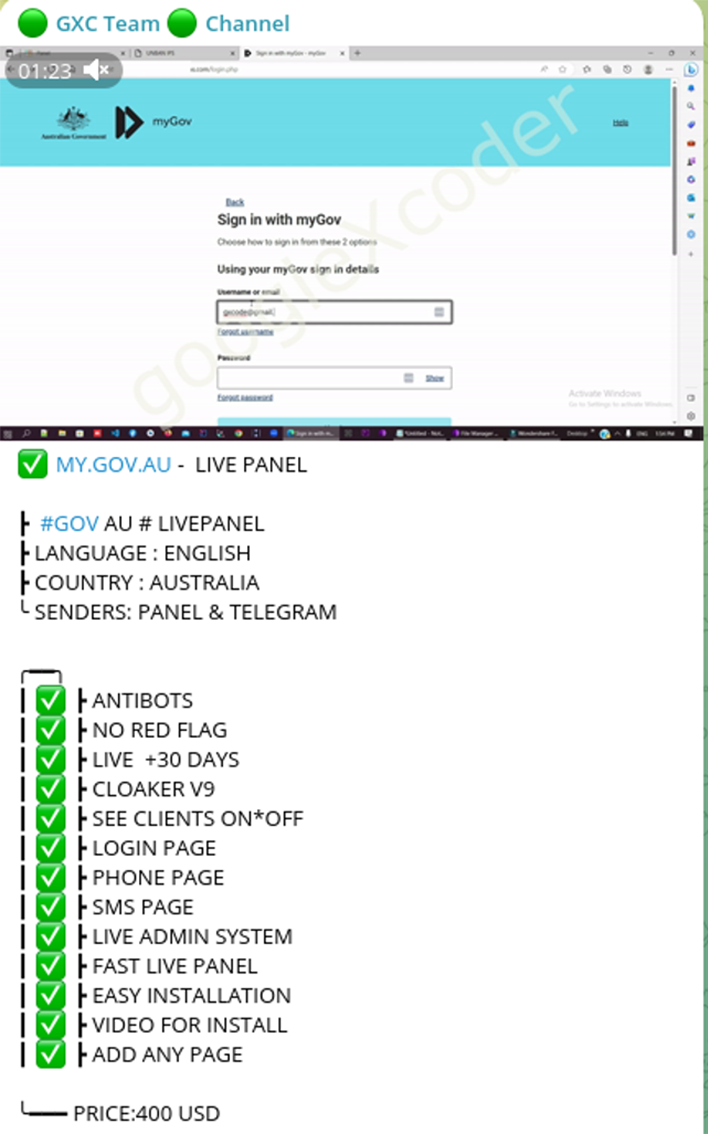
Video demonstration:
In the case of Spain, GXC Team created a fake landing page that impersonated one of the "gob.es" websites This fake page claimed to support payments through multiple banks, all with the aim of gaining the victim's trust by presenting content that appeared to originate from an official government site. This approach was used to deceive individuals into sharing sensitive information with malicious actors.
Video demonstration:
Conclusion
The use of AI in cybercrime is not a novel concept. Variations of AI have previously been employed for various malicious purposes, such as spamming, where neural networks are weaponized to evade anti-spam filters. Adversarial neural networks (ANNs) used in spam campaigns often manifest as Markov Chains, for example. Additionally, AI has been leveraged in areas like Black Hat SEO, where advanced actors use ANNs to create deceptive web content.
According to Resecurity’s HUNTER (HUMINT) Unit’s assessment, the most promising areas for applying AI in cybercrime include:
- Content generation for malicious and fraudulent purposes, with the goal of optimizing human resources and scaling operations.
- Recognition of specific objects and targets through text processing and document analysis.
- Decision-making and automation of cybercriminal operations.
- Utilizing AI-driven bots for advanced social engineering techniques.
- Analyzing and scoring potential victims, studying their behavior, and detecting patterns for more effective targeting and exploitation.
- Bypass of anti-fraud filters and cybersecurity controls (for e.g. using Deep Fakes and AI-generated artifacts).
- Influence and interference campaigns where AI will be used for emotional sentiment analysis, targeting activity and actual engagement with the audience (for e.g. in social media networks and alternative digital channels).
These observations highlight the evolving and expanding role of AI in cybercrime, posing significant challenges to cybersecurity efforts.
References:
- The double-edged sword of artificial intelligence in cybersecurity
https://www.weforum.org/agenda/2023/10/the-double-edged-sword-of-artificial-intelligence-in-cybersec... - Inside the FBI: Defending Against AI Threats
https://www.fbi.gov/audio-repository/inside-the-fbi-defending-against-the-ai-threat-072823.mp3/view - FBI warns of adversaries using AI in influence campaigns, cyberattacks
https://therecord.media/fbi-artificial-intelligence-ai-briefing - Hackers are using AI to create vicious malware, says FBI
https://www.digitaltrends.com/computing/hackers-using-ai-chatgpt-to-create-malware/ - Implementation and Evaluation of a Deep Neural Network for Spam Detection: An Empirical Study of Accuracy and Efficiency
https://link.springer.com/chapter/10.1007/978-3-031-43056-5_28
- Convolutional Neural Networks for Image Spam Detection
https://arxiv.org/pdf/2204.01710.pdf
- Hiding Malware inside a model of a neural network
https://securityaffairs.com/120558/malware/hiding-malware-model-neural-network.html - FinCEN - Updated Advisory on Email Compromise Fraud Schemes Targeting Vulnerable Business Processes
https://www.fincen.gov/sites/default/files/advisory/2019-07-16/Updated%20BEC%20Advisory%20FINAL%2050...
Indicators of Compromise (IOCs):
Resecurity has compiled the following Indicators of Compromise (IOCs) associated with mail servers that were presumably exploited by the "GXC Team" in November 2023 to distribute malicious content through their AI-powered tool, known as the "Business Invoice Swapper". It's important to note that these bad actors targeted multiple organizations in Estonia, Hungary, Italy, France, Denmark, Russia, Portugal, Spain, Ukraine, and China, with the intention of conducting business email compromise (BEC) attacks by spoofing attachments, leading to large-scale invoice fraud.
The provided list of acquired artifacts can aid network defenders and incident responders in gaining deeper insights into the malicious activities carried out by the "GXC Team". However, it's crucial to exercise caution when dealing with these artifacts, as they include compromised email accounts and related domain names, which can pose a significant challenge for mitigation efforts due to the involvement of third-party cyber risk factors that are often beyond the recipient's control.
Abused E-mail Accounts:
scarico@colonialsud[.]it
b.nasri@numeryx[.]fr
bestrad@fr[.]pl
valentino[.]monteleone@ecosistem[.]it
gestionepromozioni@iprodottidellasalute[.]it
jadsaid@cosmo-zone[.]fr
benfizagaria@giochi0[.]it
postmaster@progens[.]pl
ets[.]boyer[.]noumea@groupe-abilis[.]fr
collocamento@sunsoft[.]it
prova@isdi[.]it
l.riotte@formarh[.]fr
hamburg@vitaminb-booking[.]de
operativo@hpeurope[.]it
agente01@navamar[.]it
john218@pembery[.]co[.]uk
cloudecodep@sctcloud[.]fr
v.marchione@tecnicoper[.]it
v.lamantia@diocesipa[.]it
jansons@btv[.]lv
servizisociali@comune[.]atripalda[.]av[.]it
h.manthey@tischlerei-manthey[.]de
maxwellhale75wezaxu@azmailz[.]com
p.adnot@media-pac[.]fr
salazarhedrick73orwuwq@azmailz[.]com
merlin@cpsi-france[.]fr
16li4gcq@chasefreedomactivate[.]com
kat@rustiquetreasures[.]com
talimuhe@aliyun[.]com
protostar@email[.]ua
zhangyilei@netease[.]com
turtlegurl29@1nsyncfan[.]com
josembarreiro@jazzfree[.]com
gonzalo-nowak@carpetcleaningbirmingham[.]biz
emerson246@eudorawebmail[.]com
sunxueyi88@aliyun[.]com
medve1976@t-email[.]hu
mu@suhtlus[.]ee
berrype16@onmail[.]com
xploretv[.]38598315730@a1net[.]hr
vania[.]norte@portugalmail[.]pt
amy2009@aliyun[.]com
apel_sin@tyt[.]by
jimmy_cortez7482@andreagilardi[.]me
pintacril@orange[.]es
krokro1@i[.]ua
nursandi@multireka[.]com
karesz@tatu18[.]hu
jacqueline[.]regalado1491@andreagilardi[.]me
lngajip@immergis[.]cm
post@sti[.]as
onetkikaku@mbp[.]nifty[.]com
archaclin@melodysouvenir[.]com
oliveraagesen85budwzo@azmailz[.]com
andre74@wooow[.]it
wec02slk@chasefreedomactivate[.]com
englandmead94zmkvku@azmail[.]com
volkof@sampo[.]ru
inetmi2@email[.]ua
dreamweavers1@universe[.]com
elwood_guerra17@theparryscope[.]com
bruce.grandi45@theparryscope[.]com
karina-hovell7514@andreagilardi[.]me
contact@annuairedubienetre[.]com
proyectocnt@montevideo[.]com[.]uy
tarmo3@hot[.]ee
zoltan[.]darabos@compu-consult[.]hu
billyjow@melodysouvenir[.]com
max.reid@db5[.]co[.]uk
zipfer@uralweb[.]ru
susser@davidbowie[.]com
marie-france@masseyeff[.]com
tmf56@execpc[.]com
austin_1@aliyun[.]com
mkubat@prijedor[.]com
contact@meyzaud[.]com
webmaster@heteromorphic[.]com
forbesallen15wtirkq@azmailz[.]com
ravas@poczta[.]pl
johan@jokinen[.]dk
danniluo@aliyun[.]com
tonitenis@orange[.]es
akrouf[.]rachid@issmi[.]fr
nessa@lds[.]net[.]ua
nannettecordell9194@andreagilardi[.]me
alex.licanin@vip[.]hr
home@wimmer-juelich[.]de
djtp.panay@gandokscorp[.]com
andreasfiedler@alice-dsi[.]de
engingeadummaa@ramireschat[.]com
zilianr@aliyun[.]com
p.ballarini@tecnicoper[.]it
serviceeconomique@consulat-algerie[.]ch
yoann@genito[.]ch
tommoller@klbn[.]dk
ettli1@jtbank[.]ch
ursini.a@liceoeuropeo[.]it
g.avola@cgilragusa[.]it
giuseppe.buscemi@insupport[.]it
jruzickajruzicka111@jtbank[.]ch
max_ros@rossellalima[.]it
nicola.pulvirenti@keypartner[.]it
sonia@cozydesign[.]it
v.barry@bge-limousin[.]fr
d.petronelli@tecnicoper[.]it
contact@ameliemoreau[.]fr
samuel@solutice[.]fr
bryan@imprinted concrete[.]co[.]uk
contact@publicspirit-cooperation[.]fr
orientacampus@smartlabstudio[.]it
krisskallaste1998@suhtlus[.]ee
paolo.filoscia@fidiricambi[.]it
m.lunghi@tecnicoper[.]it
nbazzucchi@eagleprojects[.]it
jruzicka@jtbank[.]ch
fax.sepa@tecnoaccisesrl[.]it
contact@creation-jardin-gassin[.]fr
risorse@converger[.]it
vmarini@magnaflow[.]it
artzet@leslutins[.]fr
hardware@worldevent[.]it
gmadgwick@johnryan[.]co[.]uk
contact@smpfi[.]fr
benjaminhick@diediebe[.]be
c1357etc@dmobile-etc[.] fr
azvezdina48@jtbank[.]ch
olmalerservice@brnet[.]dk
taniwha@visir[.]it
miamiimmobiliare@istitutoplateja[.]it
scanner@ireneviaggi[.]it
711john@pembery[.]co[.]uk
erwan@180c[.]fr
sales@firstsignsandlabels[.]co[.]uk
domenico@lanzidei[.]it
martina@perettimedica[.]it
cooper@couffina[.]fr
r.rubino@trapanicalcio[.]it
hrovatin888@xnet[.]it
daniela[.]tornatore@milanoteamvolley[.]it
fratelcarlo@confenfrancesco[.]it
piper@radiopiper[.]it
segreteria@islotto[.]it
marketting@artigianaplast[.]it
sales@netupsrl[.]it
postmaster@aben-moha[.]fr
southfleet@patlaw[.]co[.]uk
amministrazione@telelazionord[.]it
rosalbamonaco@sudpress[.]it
maurizio@liberrima[.]it
progettazione@lightandmore[.]it
daprile536@geopistoia[.]it
partner@smarthouseabruzzo[.]it
sandra@studiocavicchia[.]it
camille.delouvrier@innersense[.]fr
lab.audio@nuovasirel[.]it
guidop@lifegate[.]it
60293@zns-kiel[.]de
scansione@studiocivilisti[.]it
simonedonato@blubayspa[.]it
assistenza@luluu[.]it
atroubat@fiscalea[.]fr
antimo.petito@uniroma5[.]it
a.malacario@tecnicoper[.]it
richieste@consultingassistance[.]it
vittoria.n@caritasdiocesana[.]it
agenovese@agenovese[.]it
fares.zeghnani@gueststar[.]fr
ordini@nielsen2[.]it
f.cesare@sincrono[.]it
orietta@doriapamphilj[.]it
jruzicka121@jtbank[.]ch
iocisono@pleiadisrl[.]it
filomenarigione@circolovega[.]It
a.molinari@onconsulting[.]ch
contact@parisack[.]fr
lpalasi29@groupedyn[.]fr
611-john@pembery[.]co[.]uk
postmaster@cid[.]be
torkild@mollertaagaard[.]dk
andrea.longo@dolcinonnavincenza[.]it
claudine.boccard@cosmosoft[.]fr
Mail Exchange (MX) Records:
mx[.]sincrono[.]it
mx[.]doriapamphilj[.]it
mail[.]jtbank[.]ch
mx[.]pleiadisrl[.]it
mx[.]circolovega[.]it
mai13[.]scanscope[.]net
mx[.]t-online[.]hu
mx[.]generic-isp[.]com
mx[.]avasin[.]plus[.]net
mx2[.]dandomain[.]dk
mx[.]dolcinonnavincenza[.]it
mx1[.]cosmosoft[.]fr
mx[.]onmail[.]com
mail-mx[.]xnet[.]hr
a[.]mx[.]portugalmail[.]pt
mx2[.]mail[.]aliyun[.]com
mx[.]generic-isp[.]com
inc[.]wanadoo[.]es
mx13[.]i[.]ua
srv68[.]niagahoster[.]com
mx[.]nuovasirel[.]it
mail[.]lifegate[.]it
mail[.]zns-kiel[.]de
mx[.]studiocivilisti[.]it
mx[.]blubayspa[.]it
mx[.]luluu[.]it
fiscalea-fr[.]mail[.]protection[.]outlook[.]com
mx[.]uniroma5[.]it
mx[.]tecnicoper[.]it
mx[.]consultingassistance[.]it
mx[.]caritasdiocesana[.]it
mx[.]agenovese[.]it
mx[.]nielsen2[.]it
mx[.]telelazionord[.]it
mx[.]liberrima[.]it
mx[.]lightandmore[.]it
mx[.]geopistoia[.]it
mx[.]smarthouseabruzzo[.]it
mx[.]studiocavicchia[.]it
mx1[.]dcube-resource[.]be
mx[.]tecnicoper[.]it
mail[.]jtbank[.]ch
mta-gw[.]infomaniak[.]ch
mta-gw[.]infomaniak[.]ch
mx[.]danskkabeltv[.]dk
mx[.]liceoeuropeo[.]it
mx[.]cgilragusa[.]it
mx[.]insupport[.]it
mail[.]jtbank[.]ch
mx[.]danskkabeltv[.]dk
mx[.]visir[.]it
mx[.]fidiricambi[.]it
mx[.]tecnicoper[.]it
mx[.]istitutoplateja[.]it
mx[.]ireneviaggi[.]it
mx[.]avasin[.]plus[.]net
firstsignsandlabels-co-uk[.]mail[.]protection[.]outlook[.]com
smtp-in[.]panservice[.]it
mx[.]perettimedica[.]it
mx[.]trapanicalcio[.]it
mtal[.]spin[.]it
mx[.]milanoteamvolley[.]it
mx[.]confrancesco[.]it
mx[.]radiopiper[.]it
mx[.]artigianaplast[.]it
mx[.]netupsrl[.]it
mx[.]tecnoaccisesrl[.]it
mx[.]converger[.]it
mx[.]magnaflow[.]it

