

Cybercriminals continue to evolve their tactics, techniques, and procedures (TTPs) to defraud the customers of online banking, payment systems, advertising networks, and online marketplaces worldwide. Resecurity has observed a rising trend involving threat actors' increased use of specialized mobile Android OS device spoofing tools. These tools enable fraudsters to impersonate compromised account holders and bypass anti-fraud controls effectively.
Cybercriminals use these tools to access compromised accounts and impersonate legitimate customers by exploiting stolen cookie files, impersonating hyper-granular device identifiers, and utilizing fraud victims’ unique network settings.
Specialists from Resecurity’s HUNTER threat intelligence unit researched this rapidly emerging attack type to help fraud prevention teams build proper mitigation controls and better understand the ever-changing cybercriminal threat landscape.
While desktop-based antidetect browsers have been used by threat actors since at least 2014 to get around account bans and otherwise manipulate systems, the emergence of adversarial mobile OS-based tools represents a new frontier in cybercriminal innovation.
In Q1 of 2023, Resecurity identified a significant spike in interest from threat actors seeking this type of tool, and the emergence of new products on the Dark Web to satisfy the growing market demand. HUNTER researchers first mined intelligence about these tools from various underground communities, including XSS (the top Russian cybercriminal forum on the Dark Web) and several private Telegram groups that provide vetted members access to specialized attack kits frequently used for online banking theft and fraud.
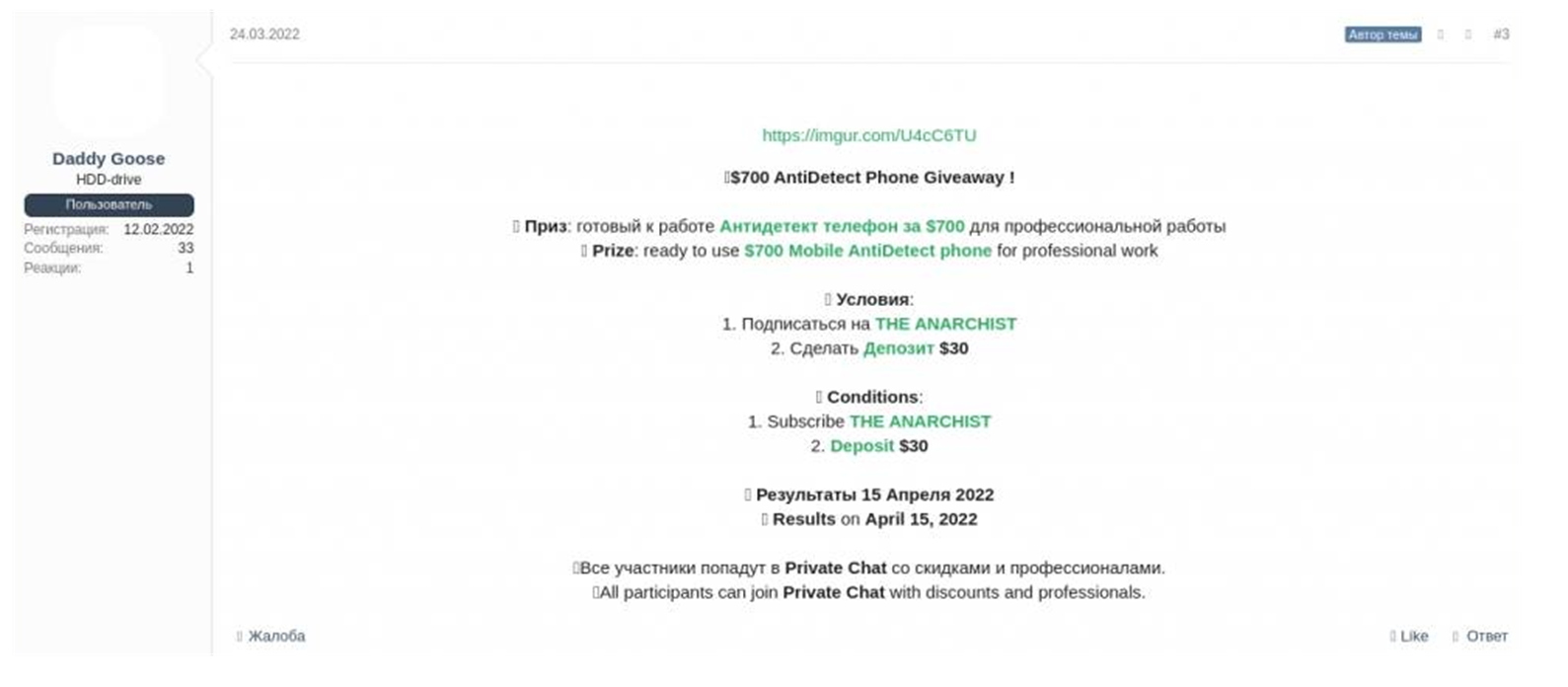
Tools sold in these communities include antidetect browsers, device fingerprint emulators, and spoofers. A device like a smartphone has a unique combination of hardware type, operating system (OS) version, software version, geolocation, screen size, language, etc., constituting its fingerprint. Threat actors use these attack kits to bypass anti-fraud controls based on these fingerprints on banking websites, e-commerce portals, and other online marketplaces. One prolific threat actor Resecurity analyst noted in this space is XSS forum member Daddy Goose. Resecurity observed this threat actor soliciting a mobile antidetect for $700. Following further interaction with Daddy Goose, HUNTER discovered that they provide a Swiss Army knife-like combination of tools and modified components to perpetrate online identity fraud. These tools include a cookie manager, location spoofer, device fingerprint changes, and more. HUNTER found several similar offerings being solicited by other cybercriminal developers.
When covert HUNTER investigators asked members of the cybercriminal community whether mobile device emulators (like Bluestacks) are more effective than mobile antidetect software, black hat respondents noted that specialized antidetect tools have unique advantages that allow threat actors to remain incognito.
How Antidetects Work
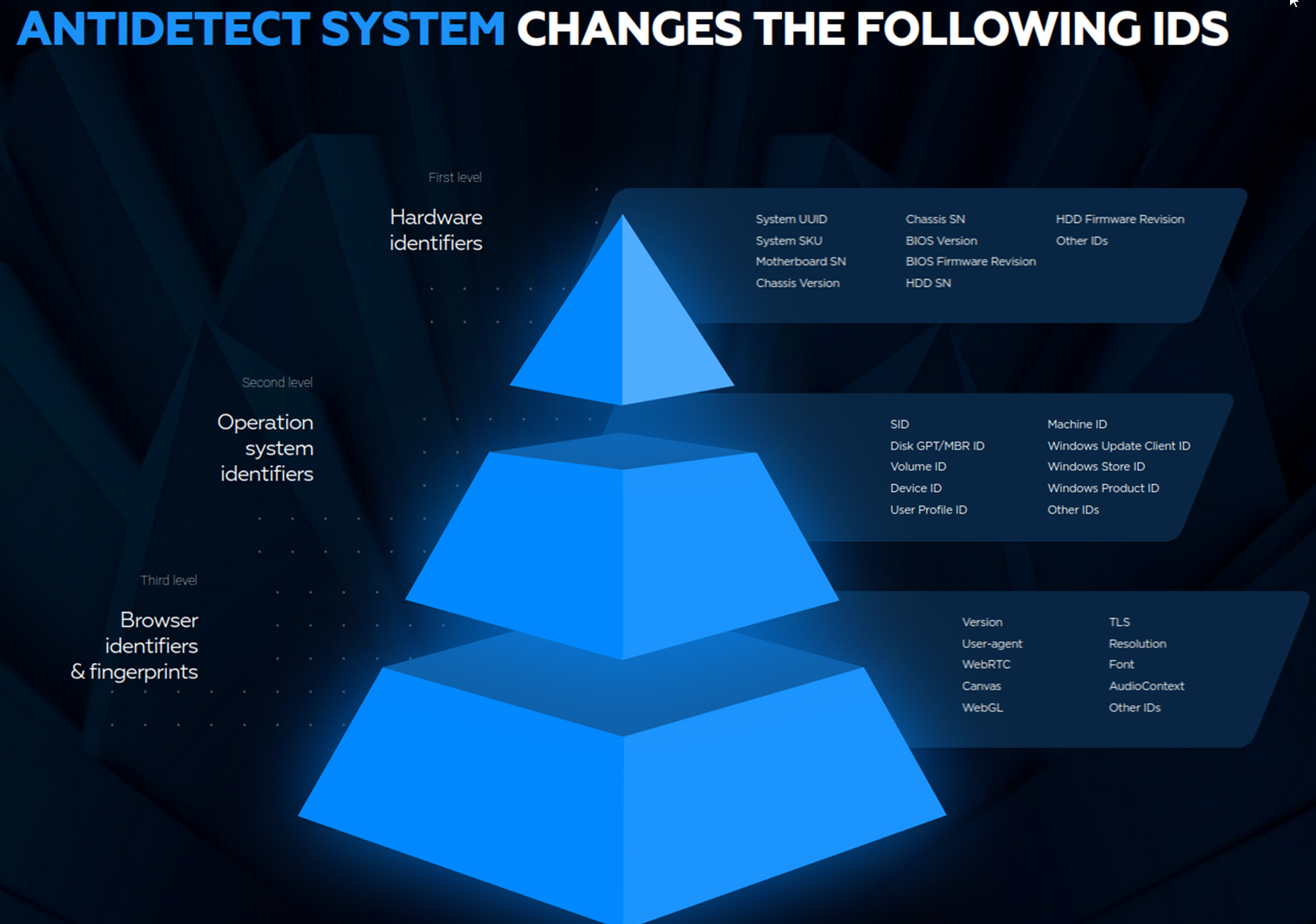
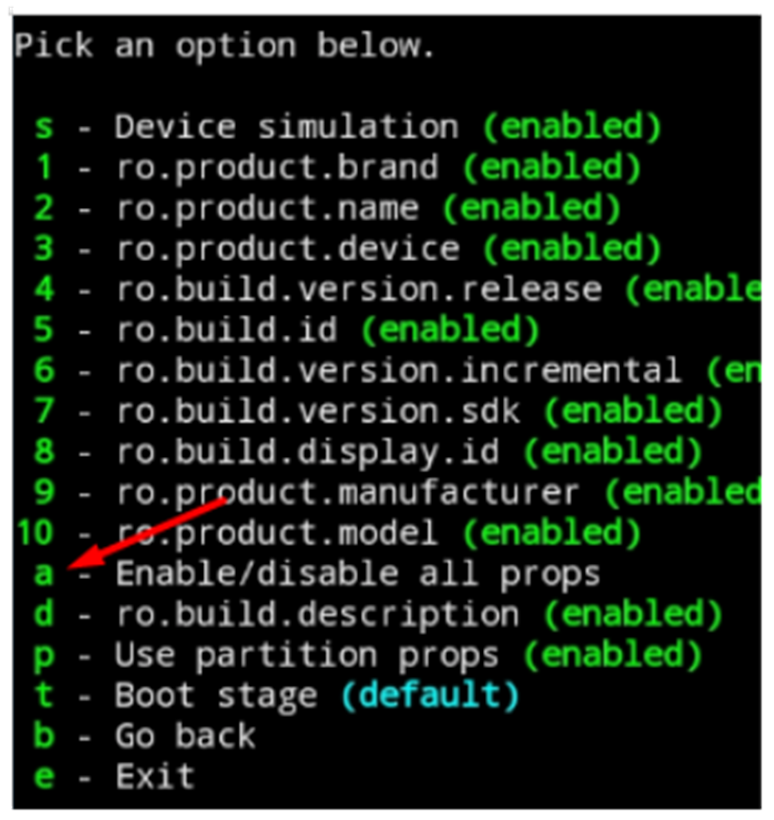
Some notable desktop-based antidetect systems that began to launch mobile-native offerings include Vektor T13, Antidetect 4 (Patreon), and others. Tools like Vektor T13, for example, provide strong customer support and continuous software updates to optimize the tool's effectiveness. Antidetects enable threat actors to change the data parameters that anti-fraud solutions scrape from the client side to fingerprint devices and authenticate the customer's identity. These parameters include hardware type, operating system (OS), and browser/software-related identities.
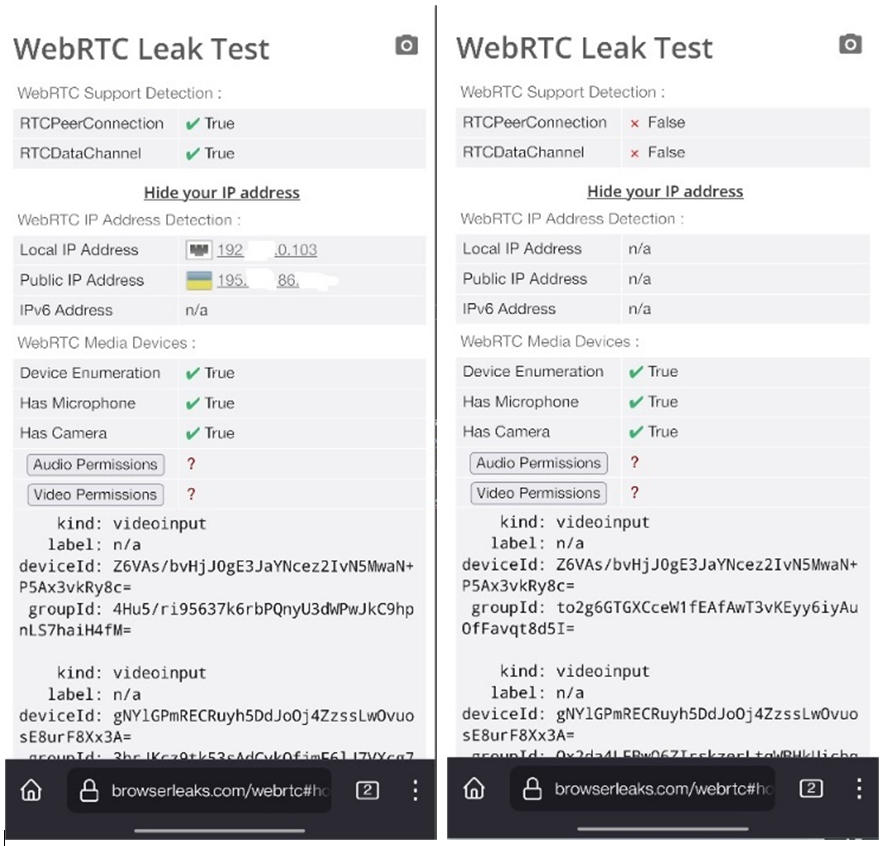
Some of these fingerprints are detailed in the image below. These identifiers are scraped using JavaScript, HTML5, WebRTC, and other technologies. Cybercriminal actors perpetually analyze the responsiveness of anti-fraud solutions to their attacks and modify their antidetect settings to parameters that enhance the odds of successful exploitation.
Notably, these tools also have mainstream use cases outside the Dark Web. Antidetect solutions have a variety of other legitimate applications, including affiliate marketing, social media management (SMM), and the automation of online activity using multiple profiles. One example of this type of legitimate software is the GoLogin tool, widely used by Internet marketing specialists. Concurrently, GoLogin is also promoted on unofficial web resources as an application that can be used to bypass anti-fraud systems.
Inevitably, cybercriminals exploit the functionality of tools like GoLogin to spoof fingerprints on desktop and mobile devices for malicious purposes. Financial institutions (FIs) and e-commerce providers should implement risk-based mitigation measures. As mobile-based antidetect tools become more widely adopted by the cybercriminal community, the number of banks, fintech, and online marketplaces bound to encounter increased fraud attacks from sophisticated threat actors operationalizing novel exploits of anti-fraud technologies increases.
Popular Desktop Antidetects
The following matrix lists some of the most popular desktop editions of antidetect software and includes each program’s icon, name, website, and description provided by each vendor.
| Logo | Name | Home URL | Description |
|---|---|---|---|
 |
AntBrowser | https://antbrowser.pro/en/ | According to the product description, this tool can “bypass the following: checks Fonts, CSS, Plugins, MimeTypes, Timezones, Canvas Fingerprint, WebGL Fingerprint, Audio Fingerprint, WebRTC, Firefox Leaks” |
 |
Lalicat | https://www.lalicat.com | According to the product description: “Customizable digital fingerprint data includes the browser version, system fonts, resolution, operating system, CPU class, language, WebGL, RAM, CPU, SSL, Media Device, Extensions, etc. The list is huge. Lalicat anti detect browser offers the option to configure all the collectable data and customize these data to make up your unique fingerprint, rendering any third-party website unable to collect user data. Users can also generate as many profiles as they want. Lalicat antidetect browser is an anti-detection platform that can simulate operating environments like Android phones. The mobile emulation feature of Lalicat antidetect browser is a key highlight of this browser. This function can simulate the touch screen to support the swipe function, allowing users to simulate the real behavior of a victim that browses the web on an Android device. This application also supports the simulation of other mobile device environments, including iPhone, iPad, and Microsoft Lumia.” |
 |
Aezakmi | https://aezakmi.run | According to the product description, “AEZAKMI is an antidetection browser that allows you to safely work with multi-accounts and traffic arbitrage. AEZAKMI can replace virtual machines and multiple computers, while remaining invisible to antifraud systems. You can discuss the technological effectiveness of your product as well as the results of testing multiple times. What good is it if users are banned and deanonymized in real-world situations? We provide demo access to 2 fingerprints after you register. In 5 clicks, create a new fingerprint. Access your fingerprints quickly from your desktop. Multiple fingerprints can be used simultaneously. Transfer fingerprint cookies to any AEZAKMI user to facilitate teamwork. Simultaneous work from multiple computers in one AEZAKMI Account.” In the blog for the tool, the authors state, “With the help of AEZAKMI Browser you can replace virtual machines or several computers with one program, remaining unnoticed by anti-fraud systems.” |
 |
ClonBrowser | https://www.clonbrowser.com | ClonBrowser is an antidetect fingerprint browser that enables “multi-account asset security operation.” According to the product description, “ClonBrowser allows users to create a separate browsing profile. Cookies, local storage, cache files, and other cache files are completely isolated and cannot leak between profiles. ClonBrowser allows users to do more with their account in a safe environment. Instead of using multiple desktop setups, ClonBrowser users can engage a virtual profile. Profile virtualization is executed via the creation of a browser configuration file. This is the equivalent of creating a virtual browser environment. Browser configuration files are isolated from local storage and cached files. They cannot leak information from one another, so cookies, local storage, and other cached files won't be affected. This ensures data security. This tool helps organizations better automate team operations and reduce manual labor requirements.” |
 |
MultiLogin | https://multilogin.com | According to the product description, this tool can “Stop account bans and get rid of unreliable masking solutions. Stable virtual browser profiles with native browser fingerprints are possible using stable, customizable browser profiles. You can research competitors, verify ads and automate manual tasks on platforms such as Google, Facebook, eBay and Amazon. MultiLogin makes it possible to do the impossible. MultiLogin allows you to quickly create virtual browser profiles. Each profile appears as a separate device with its own storage and fingerprints. These are just a few of the many reasons MultiLogin has been embraced by entrepreneurs all over the globe. MultiLogin allows you to choose between Chromium- or Firefox-based browsers. Both have regularly updated cores for better undetectability. Stealthfox is built on the Firefox engine. This browser was the first to challenge browser fingerprinting. MultiLogin’s customizable capabilities make it far more reliable that Mozilla’s leaky multi-account containers.” |
 |
Sphere | https://sphere.tenebris.cc | According to the product description, “The browser supports protection and fingerprint substitution (GPU. Audio. Canvas. Fonts. Fonts. ClientRects. Ubercookies). These systems automatically change for each new identity. Sphere protects you from any attempt to identify your computer's configuration. Sphere works in an off-the-record mode. All files and data are kept in RAM until the software is closed. It is impossible to access information about visited sites or activities within them, even if spying software (viruses) is installed on the computer. You can easily replace your IP address with software such as TOR. Multi-flow SOCKS or SSH connections are available for users who don’t trust an onion network.” |
 |
GoLogin | https://gologin.com | According to the product description, this tool is an “Anti-detect browser for multi-accounting. The GoLogin antidetect browser is also available for popular platforms such as Windows, macOS, and Linux. Multiple browser profiles can be created and managed on websites. Configure each parameter in your fingerprint. There are currently more than 50 connection characteristics. Each browser profile is stored in its own cloud, which provides privacy and anonymity. A convenient ecosystem for teamwork. You can share profiles and proxies with your team members and assign rights to them. Hackers, governments, and corporations all know what anonymity means and can track your Internet identity.” |
 |
Incognition | https://incogniton.com | According to the product description, this tool offers, “Unlimited virtual profiles can be managed for multi-account management. Secure and anonymous Ideal for individuals and teams.” “All data from browser profiles are securely stored in an online database. You can also store your data on your device. You can create team members with different logins and give them specific permissions. With a structured overview, you can access multiple internet browsers from the same application. Emulation of human typing to quickly fill out website forms. To save time, automate browser operations with Selenium and Puppeteer. Bulk creator allows you to create multiple browser profiles with just a few clicks.” |
 |
VMMask | https://vmmask.net | According to the product description, this tool offers, “Centralized management of e-commerce/social media/advertising/independent website accounts through virtual fingerprint browser technology, with unrestricted access to all major websites/platforms. The software includes a built-in login area matching mechanism that not only keeps the user’s login region stable, but also matches the corresponding time, language, latitude, longitude, and other relevant information based on the user’s login location.” |
 |
Dolphin{anty} | https://anty.dolphin.ru.com/en/ | According to the product description, with this tool, “You can work with hundreds of profiles from one device. Each profile is a unique browser fingerprint that has its own web environment. Cookies, cache, and other parameters are all completely independent of each other. Modern antidetectors require not only high-quality substitutions but also easy team interaction, tracking the status of accounts, notes, and proxy.” |
 |
VMLogin | https://www.vmlogin.us | According to the product description, “VMLogin allows you to create a separate browsing profile. Cookies, local storage, cache files, and other cache files are completely isolated and cannot leak between profiles. VMLogin Anti-Detect Browser allows you to replace multiple computers with virtual profiles and login to multiple accounts from one place. It offers 100% security isolation, real fingerprint protection and prevention of information loss. It is suitable for eCommerce, social marketing, and affiliate advertising. VMLogin can automate any repetitive task. VMLogin can be automated using the Selenium web driver. You can also use a third-party visual automation constructor such as Browser Automation Studio.” |
 |
IndigoBrowser | https://indigobrowser.com | According to the product description, “Antidetect allows for safe and comfortable work with all antifraud systems. This tool is essential for affiliates. It can be used to launch advertising campaigns, create accounts for uploading applications, and launch advertising campaigns. Unique database of prints that can be adapted and continuously updated. Reliability and success in passing digital fingerprint checks on most anti-fraud software. You can create your own team by issuing access rights to each member. You can also track their status and track their profiles. Advanced browser emulator for Android mobile devices. You can immediately begin working without any additional settings. Indigo is the only antidetect that can be used with both Chrome and Firefox. Mimic is a browser that uses browser identity protection technology, based on Chrome.” |
 |
SessionBox | https://sessionbox.io | According to the product description, SessionBox’s “Workstation protects your privacy by allowing you to manage browser fingerprints across all sessions. It is easy to get started without any complicated configuration. SessionBox Workstation, a desktop application, unlocks new possibilities for multi-account management. Your SessionBox sessions will now act as separate browser profiles. SessionBox Workstation uses session isolation, fingerprint management, and proxy cloaking to allow you to use multiple accounts without being detected. To protect your identity, you can set up proxy accounts. SessionBox Workstation supports many proxy providers and automatically adjusts system properties (like language and timezone) to your active proxy.” |
 |
Octo Browser | https://octobrowser.net | According to the product description, “Octo Browser passes popular checkers like Pixels and BrowserLeaks. Reduce identification risks and account overlap. When working with eCommerce and affiliate marketing, be aware of the potential for account loss. You can combine your profiles using tags to quickly access different account types. You can export, clone, and transfer ready profiles with all associated information individually or in bulk.” |
 |
MoreLogin | https://www.morelogin.com | According to the product description, “MoreLogin provides an Antidetect Browser that you can use to create multiple browser fingerprints. These new browser fingerprints don't overlap, so websites don't ban your account, which is great for performing various tasks on the internet.” |
 |
Undetectable | https://undetectable.io | According to the product description, Undetectable is an “Antidetection browser that makes it easy to conduct safe and efficient online activities. Virtual machines are no longer necessary, and you don't need to purchase new hardware. You can browse the web with lightning-fast speeds. Undetectable browser is available to almost all online businesses. Multi-accounts on Social Media are easy to use. Manage unlimited online accounts. Manage high volume contextual and targeted advertising. Undetectable makes it easy to switch between multiple advertising accounts with remarkable efficiency. Undetectable lets you register multiple accounts and manage them all from one location, regardless of your bonus hunting profile.” |
 |
LinkenSphere | https://ls.tenebris.cc | According to the product description, “This software allows you to investigate complex antifraud system vulnerabilities. It is based on complex structures such as Fraudscore and MinFraud, SiftScience and ThreatMetrix. The browser has protection and substitution systems for prints (GPU. Audio. Canvas. Plugins. Fonts. ClientRects. Ubercookies). Linken Sphere will protect you against any attempts to identify your hardware configuration. The browser doesn't just prevent their acquisition, but it also provides the correct information, creating a unique user profile that you can use as often as necessary. The browser allows you to create parameters quickly and qualitatively for each session. It also offers the most comprehensive options for setting up configurations.” |
 |
Kameleo | https://kameleo.io | According to the product description, “For complete anonymity, change your IP address and browser fingerprint every time you open a browser. Easy profile management. Kameleo makes it easy to share saved browser profiles with your colleagues. It's now easier than ever to change the fingerprint of your mobile device or proxy connection. Our Selenium Stealth WebDriver allows you to create hundreds of profiles and keep them safe. Our market-leading solution allows you to change the browser fingerprint of each browser that you use on your computer. Kameleo will make websites assume that these browsers have been opened from different locations and devices. After you're done, you can save your profiles into files and share them to your team. With just a few lines code, you can create hundreds of virtual browser profiles using the Kameleo Local API. You can manage them with your favorite automation frameworks like Selenium, Puppeteer or Playwright. Notably, one of the few projects having Android version. Kameleo Mobile Browser allows you to create unlimited Android and iOS profiles that you can operate from your Android device or emulate them from your PC.” |
The Mobile Threat Environment
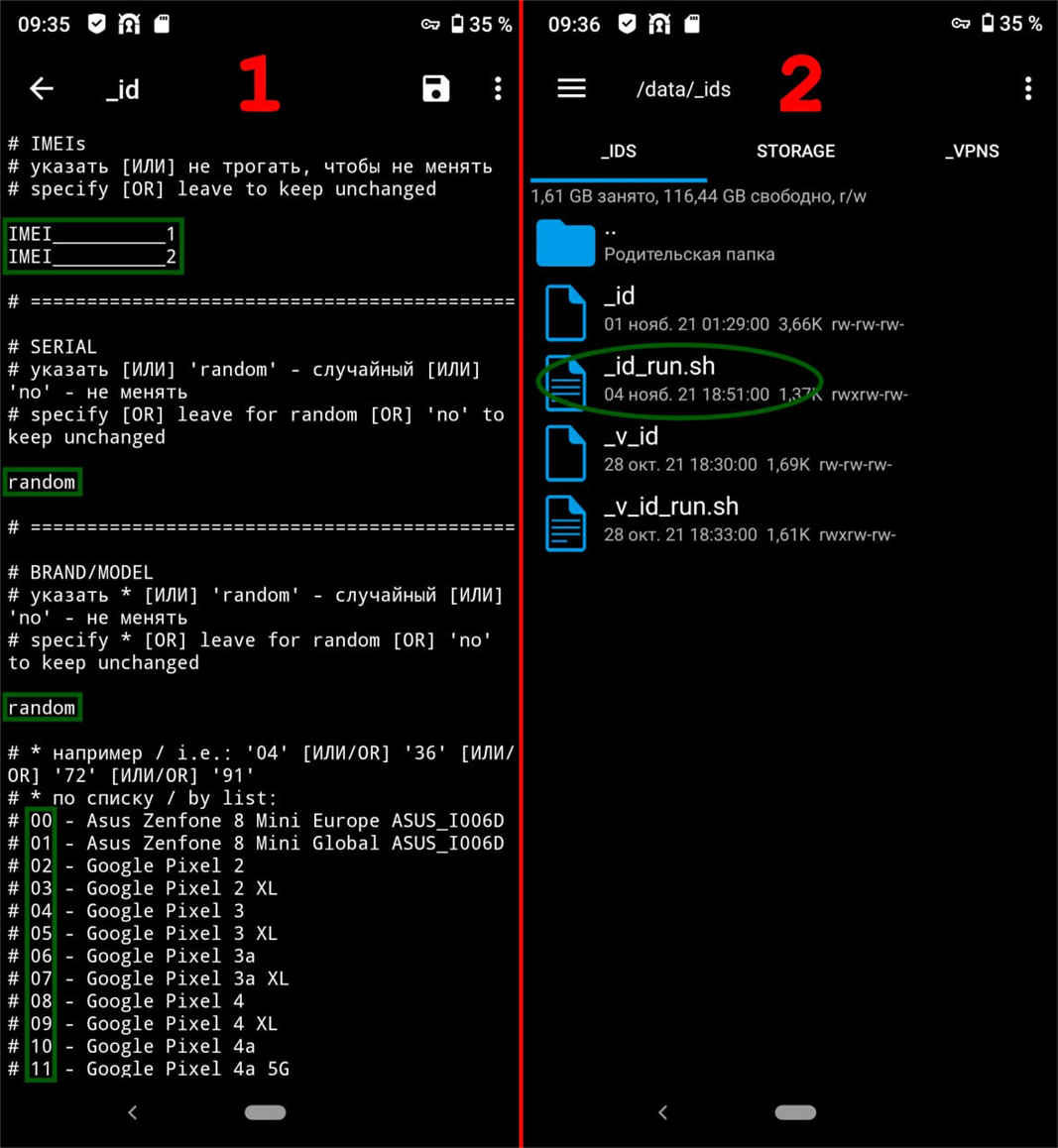
Resecurity identified the emergence of new antidetects on the Dark Web capable of spoofing mobile device fingerprints and other software and network parameters typically analyzed by anti-fraud systems. Based on our assessment, most of these mobile antidetect exploit kits are designed for One Plus and Xiaomi Redmi devices. The growing adoption of these tools dovetails with the explosion of mobile malware, with at least 200,000 new malicious variants discovered last year.
Given the rise of mobile-based credential theft and data exploitation by threat actors, mobile antidetects empower fraudsters to circumvent weak fraud controls that attempt to protect users from banking or to perform other financial transactions via smartphones. Some notable modern mobile malware strains include TimpDoor and Clientor. These exploits allow threat actors to install a proxy server on the device. This enables scammers to use the victim’s IP addresses when, for example, accessing the victim’s online banking accounts. Alternately, some of these mobile banking trojans can set up a virtual network computing (VNC) connection with full remote-control management of the victim’s smartphone.
Based on incidents of online-banking theft that have impacted Fortune 500 FIs, these tactics are already the established “modus operandi” of sophisticated cybercriminals. In these cases, mobile malware is playing an increasingly significant role.
Mobile Antidetect by “Enclave Service”
One emerging antidetect solution is “Enclave Service,” a Dark Web service with a good reputation among cybercriminals that provides tools for identity spoofing and anti-fraud bypass. Initially, Enclave Service specialized in identity theft and document-faking services on the Dark Web, assisting other actors to pass Know Your Customer (KYC) verification on popular online banking sites and other financial portals. This threat actor frequently promotes their product on the STYX Innovation Marketplace.
The starting price for the Enclave mobile antidetect tool is $500, with additional costs varying based on the level of customization required by the client. Notably, this vendor provides limited public information about themselves and prefers to deal privately with established Dark Web clients.
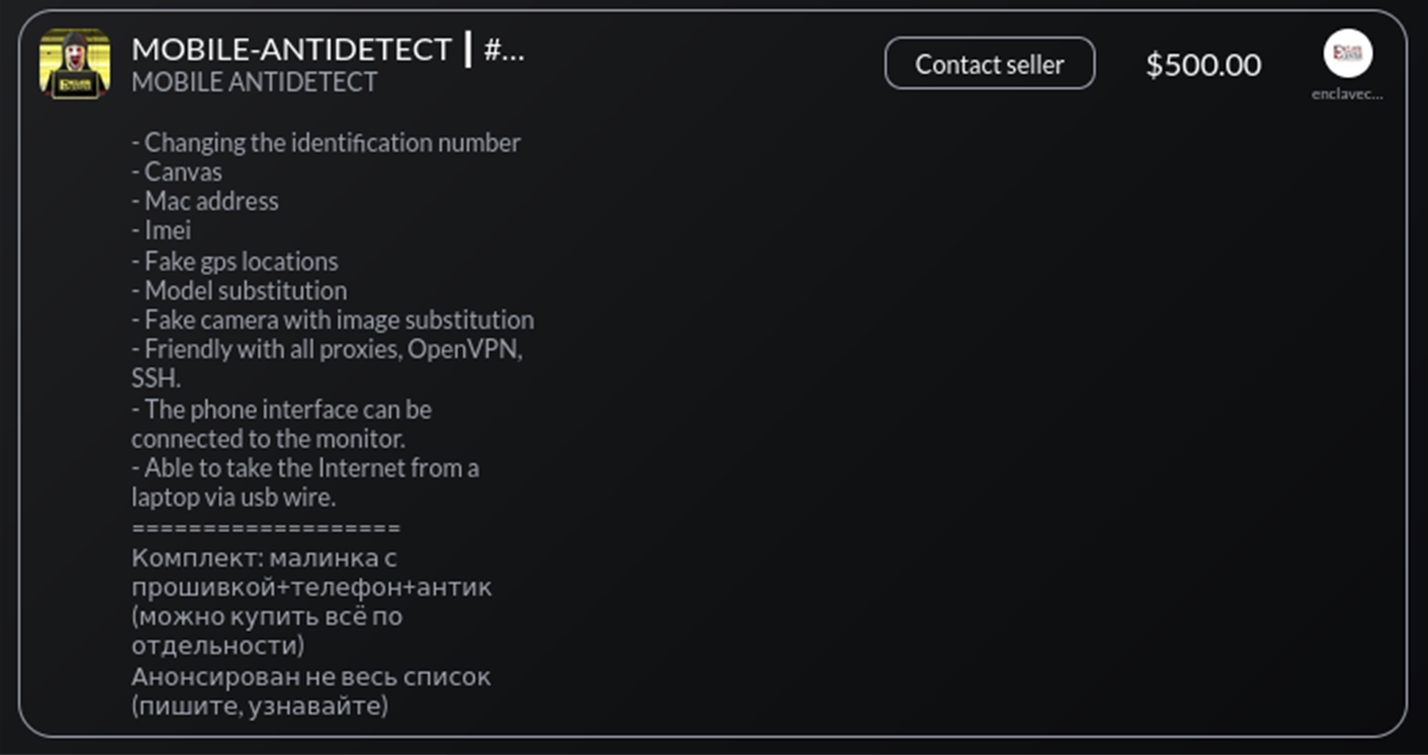
Resecurity acquired Mobile Antidetect by Enclave Service for further field testing and analysis to help FI clients develop enhanced fraud mitigation controls. The threat actor provided covert HUNTER investigators with a password-protected package to be installed on a mobile device.
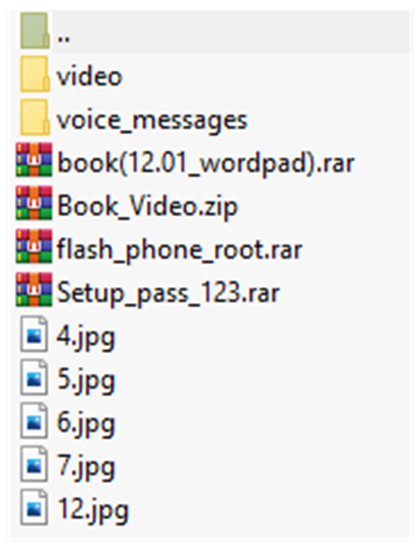
One of the latest updates of the package was released around March 15th, 2023. This update contains some old tutorials from 2020 when Enclave Service first released their antidetection solution to private buyers.
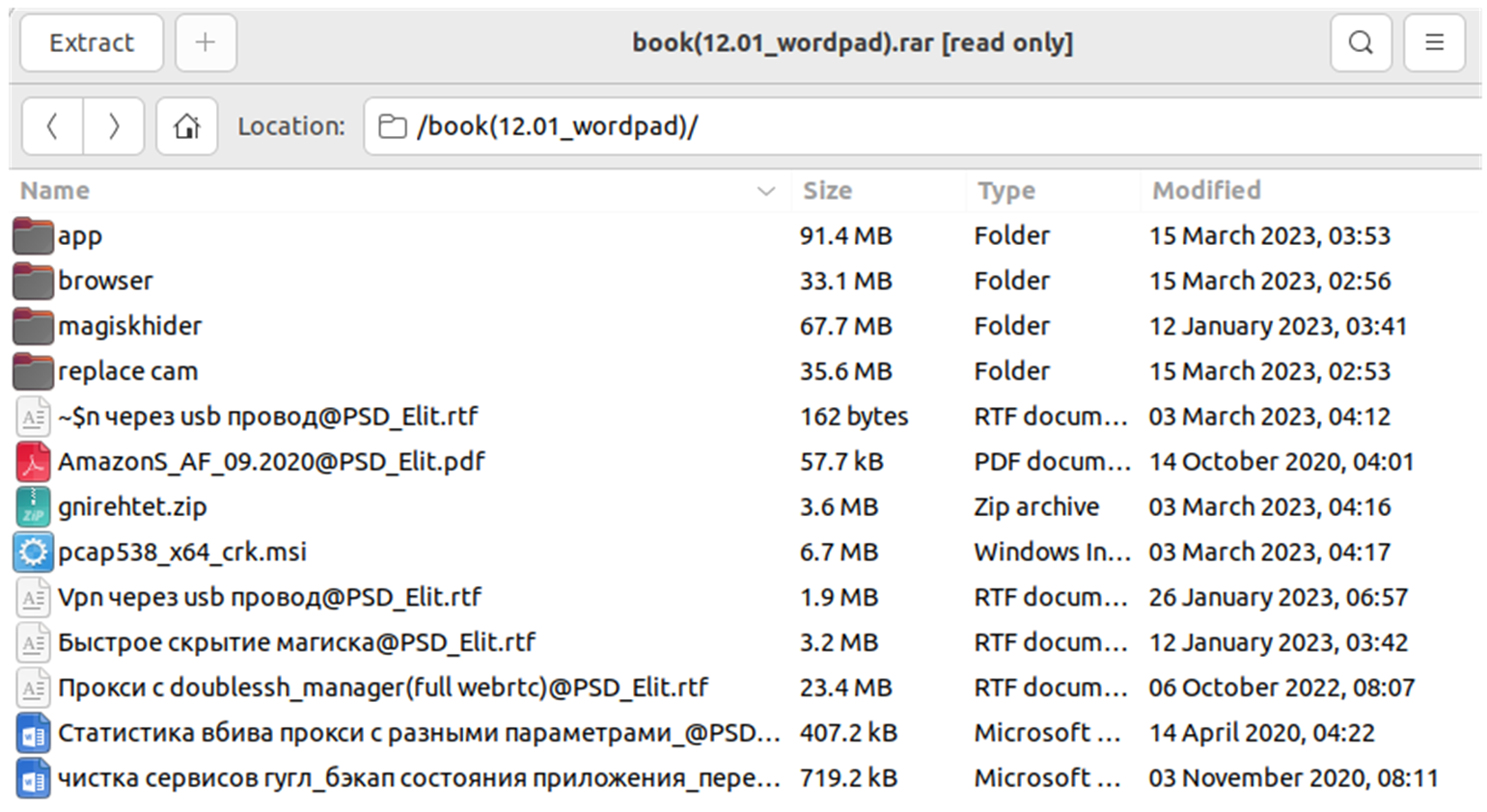
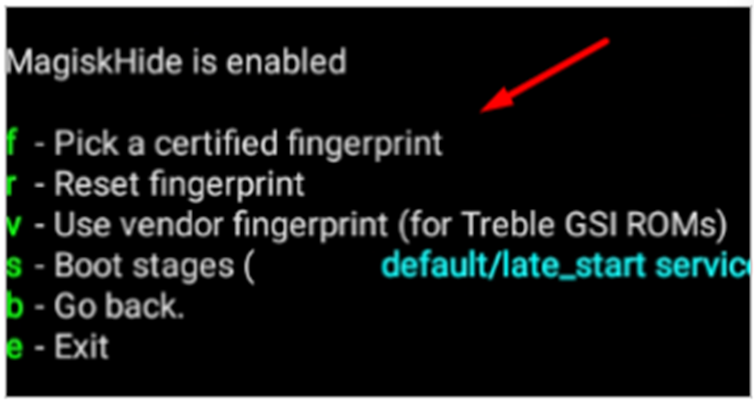
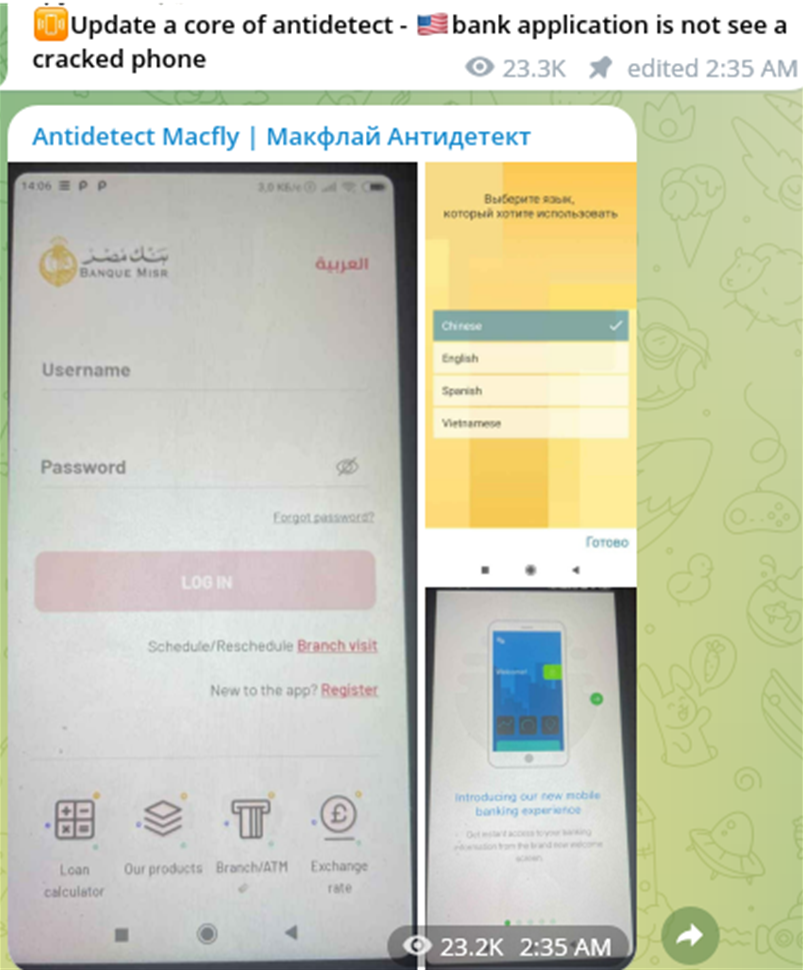
The package includes software for a device firmware upgrade, and customized tools for device fingerprint impersonation, GPS spoofing, and network anonymization. It also has Magisk, a popular utility for rooting and customizing Android phones by installing modules. Regulations in various jurisdictions require that financial applications implement safeguards to prevent installation and execution from “rooted” devices, but bad actors continue to find ways to bypass these controls.
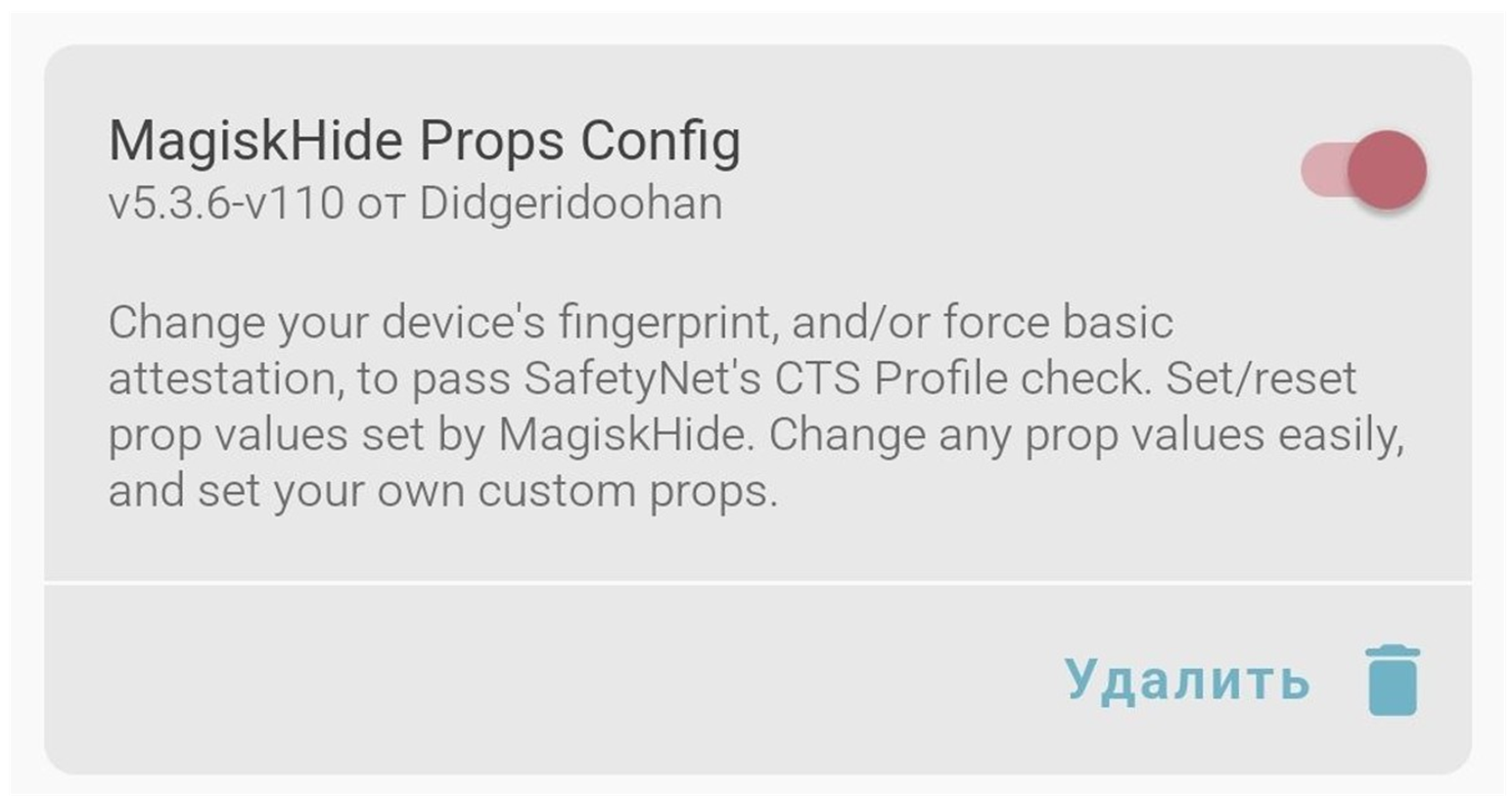
The MagiskHide module, for example, removes the ability of certain Android apps to recognize a device as rooted, successfully obfuscating forensic indicators that its bootloader was unlocked. Certain apps, including banking and mobile payment apps, use Google’s SafetyNet feature to block users from running them on devices that have been modified. However, MagiskHide enables users to continue using those apps on rooted devices since the app is tricked into presuming a legitimate accountholder was the user who decided to tamper with their device.
This project was recently discontinued, but many alternatives emerged to replace it. Some alternative solutions that have emerged in its place include:
- Safetynet Fix
https://github.com/kdrag0n/safetynet-fix
- Shamiko
- ih8sn (an experimental method that doesn’t involve Magisk, but which allows you to spoof prop values to pass SafetyNet checks)
https://github.com/luk1337/ih8sn/releases/tag/latest
Mobile Antidetect by “MacFly”
The MacFly tool first emerged around August 2019. At the time, the eponymous developer of the MacFly tool was building a pre-loaded, antidetect mobile device for sale to private clients. Like EncroChat, Sky ECC, and Omerta, MacFly’s initial idea was to pre-install all software components onto a device and ship clients ready-to-use handsets.
This business model failed to gain traction because many prospective buyers voiced OPSEC concerns, which ultimately proved prescient following the takedowns of three infamous “cryptophone” networks. Later, MacFly modified his business model and started to sell specialized software kits that could be installed on any Android OS smartphone.
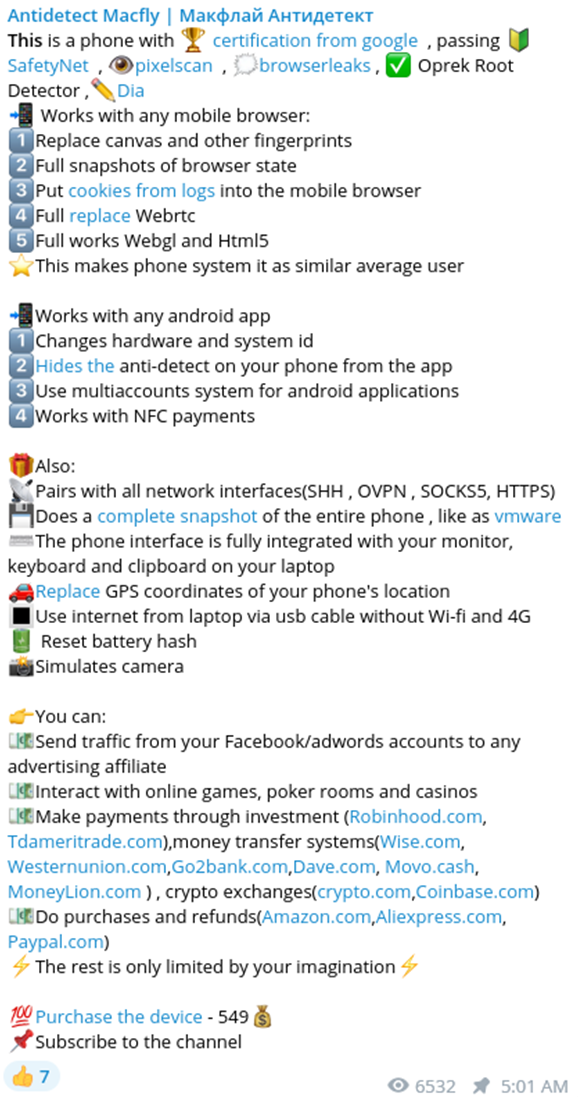
The MacFly tool supports various services, including payment systems, cryptocurrency exchangers, banks, popular online marketplaces, and digital ID/e-government services.

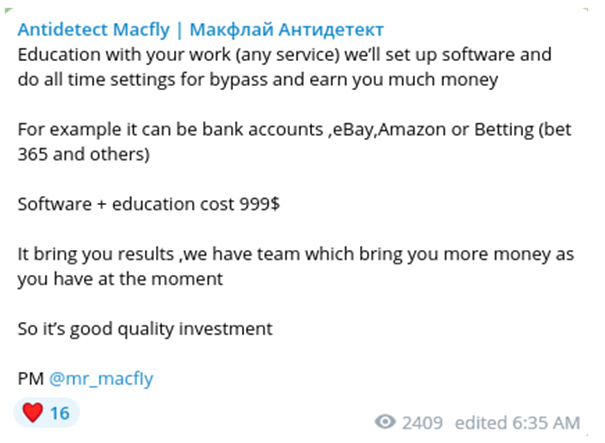
Sold separately from the toolkit, MacFly also offers training courses. For example, the vendor demonstrates how his mobile antidetect can be used to bypass anti-fraud controls on popular online marketplaces and services like online gambling websites. One of these training courses solicited by MacFly is called “Golden Anx.”

Another tutorial instructs users how to defraud Google Pay (Gpay) and Apple Pay, which are increasingly targeted by cybercriminals as exploit kits designed for NFC payment channels become more widely available underground.

Resecurity analysts acquired the MacFly tool and found its components share many similarities with Enclave Service’s mobile antidetect kit. The archive provided by this threat actor contained multiple manuals, tools for mobile device firmware updates, and related software.
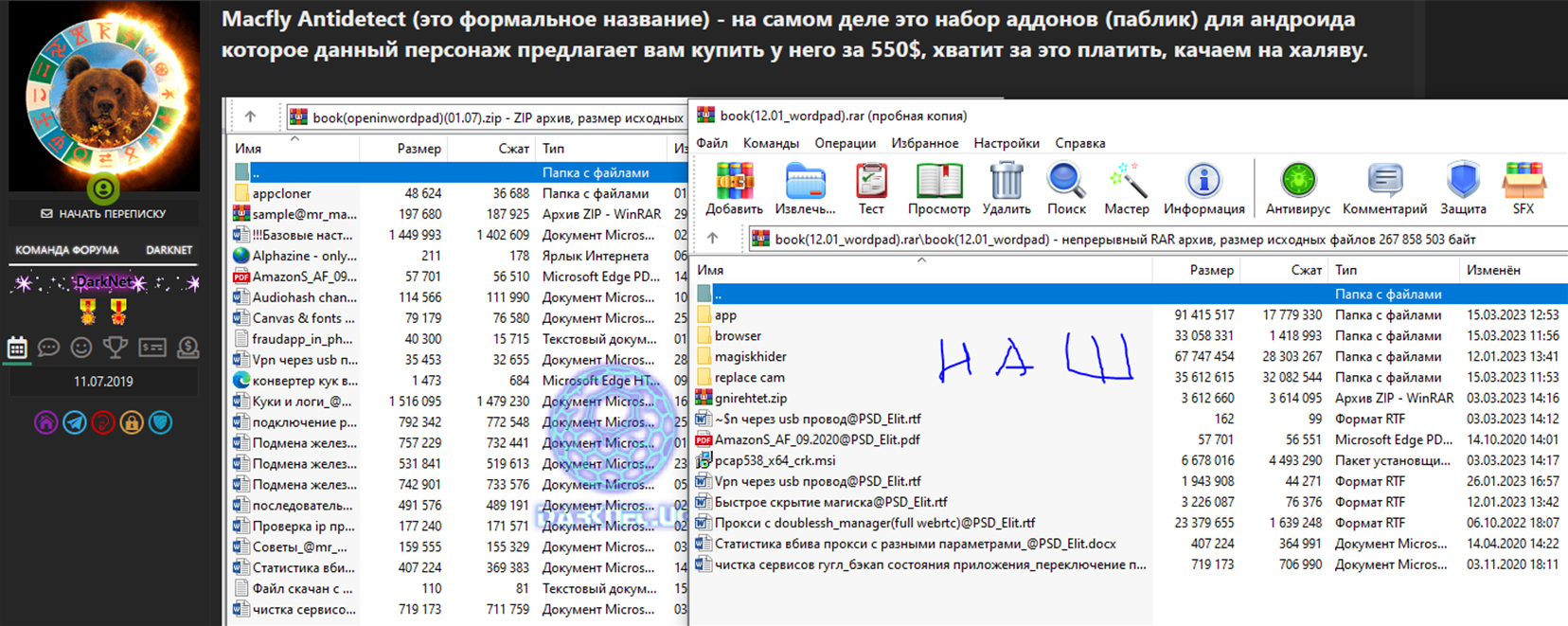
After unpacking and extracting the key tools, Resecurity identified multiple modules prepared with the help of the LSPosed Framework (https://github.com/LSPosed/LSPosed). The following documentation was included:
| A Riru/Zygisk module attempts to provide an Android Runtime (ART) hooking framework, which delivers consistent APIs with the OG Xposed, leveraging the LSPlant hooking framework. Xposed is a framework for modules that can change the behavior of the system and apps without touching any Android packages (APKs). This facilitates effective spoofing because modules can work for different versions and even read-only memories (ROMs), without any modifications (as long as the original code isn’t altered too much). Modifications are also easy to undo. Since all changes are executed in the memory, users just need to deactivate the module and reboot the device to get the original system back. Another key advantage here is that multiple modules can make changes to the same part of the system or app. With modified APKs, on the other hand, users are confined to one choice. There is no way to combine modified APKs, unless the developer builds multiple APKs with different combinations. |
Like to Enclave Service’s mobile antidetect, the process starts with rooting the device and conducting further checks against popular fintech apps. Before rooting, the MacFly developer gives the following instructions for OnePlus phone clients:
| Make sure Developer Options is Enabled and USB debugging is enabled by (Going to “Settings” then “About phone” and then tap on “Build Number” 7 times to enable Developer Options) Open Developer Options Open the app you downloaded (and click the oem_unlock option) Scroll Down to OEM unlock and toggle it on Open Command Prompt and type “adb devices” Make sure it shows your device Type “adb reboot fastboot” Once rebooted into Fastboot mode type “fastboot oem get_unlock_code” Go to this website once you get the code (it will be a string of all uppercase letters and numbers”). Login to your OnePlus account if you haven’t already Enter the following info from your device while it's in fastboot mode (Serial Number, Email and IMEI); you can get the serial from the start screen and the IMEI by clicking the volume rocker so the full text says “Barcode” and press the power button to display it. Wait seven days and OnePlus will send you the Unlock key (you can also use the OnePlus page to check the status and download the token.bin file when it’s available) Use the command prompt and type fastboot flash cust-unlock You should get a “device is unlocked” message now but we still have one more step Type “fastboot oem unlock” and you should get two messages that say “okay” and “finished” Enjoy! |
MacFly continuously releases updates on his Telegram channel about banking apps; he was able to bypass root checks to keep his customers informed about viable fraud vectors.
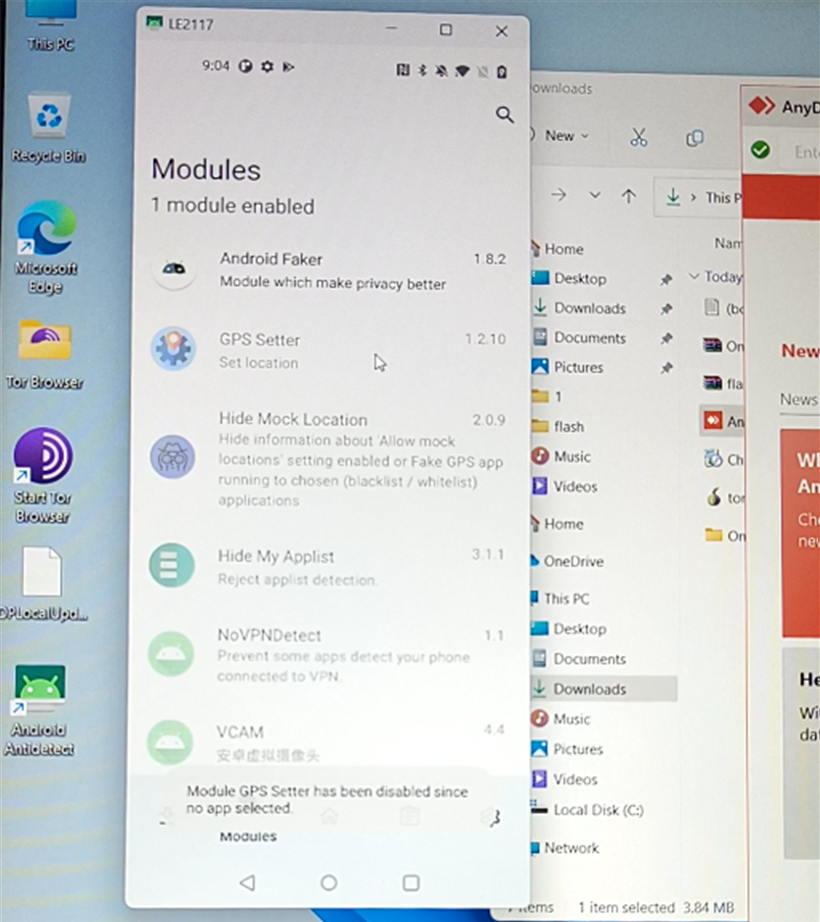
Key Mobile Antidetect Features
Below are some of the key features antidetects offer to their users. These include Device ID changer, Android Faker, Cookie Import, and GPS Spoofing.
Device ID Changer
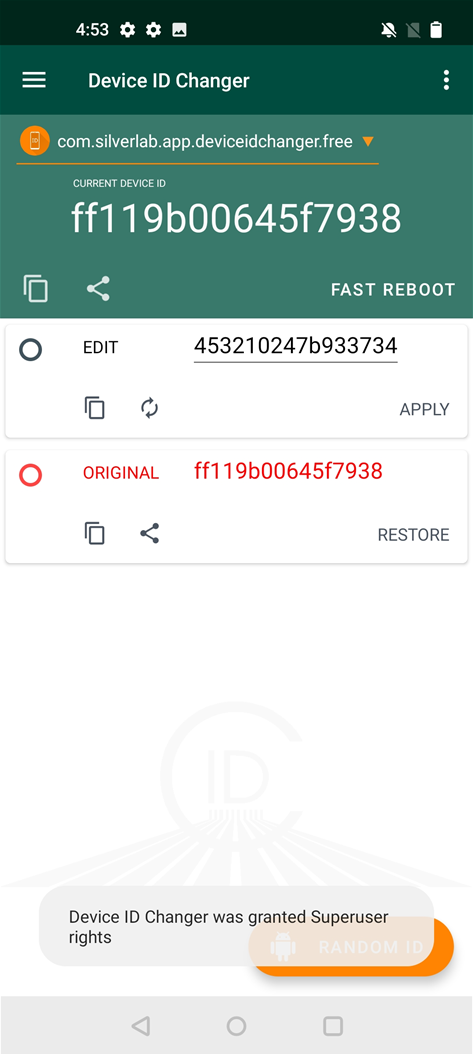 |
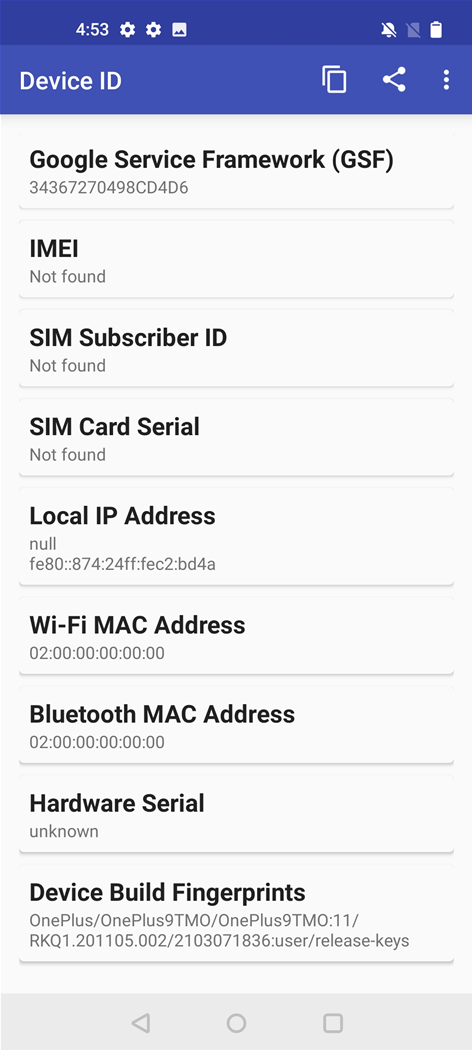 |
Android Faker
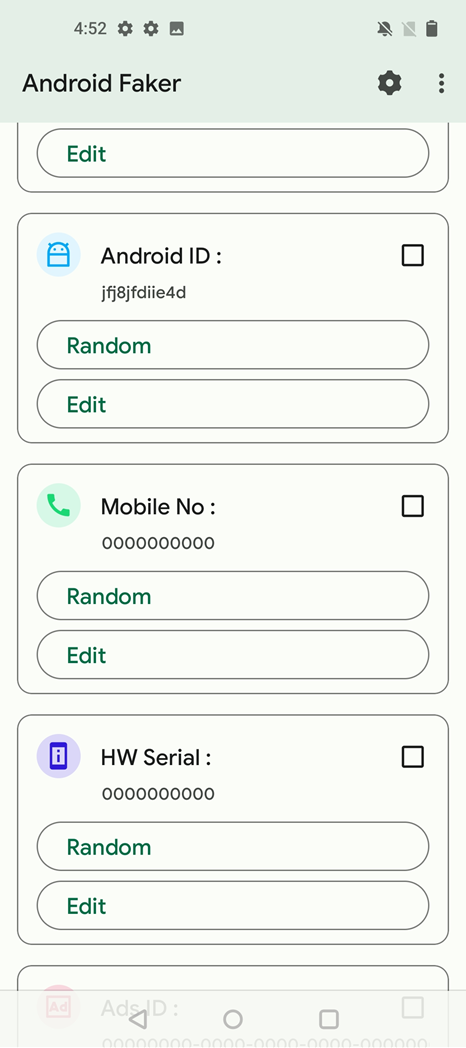 |
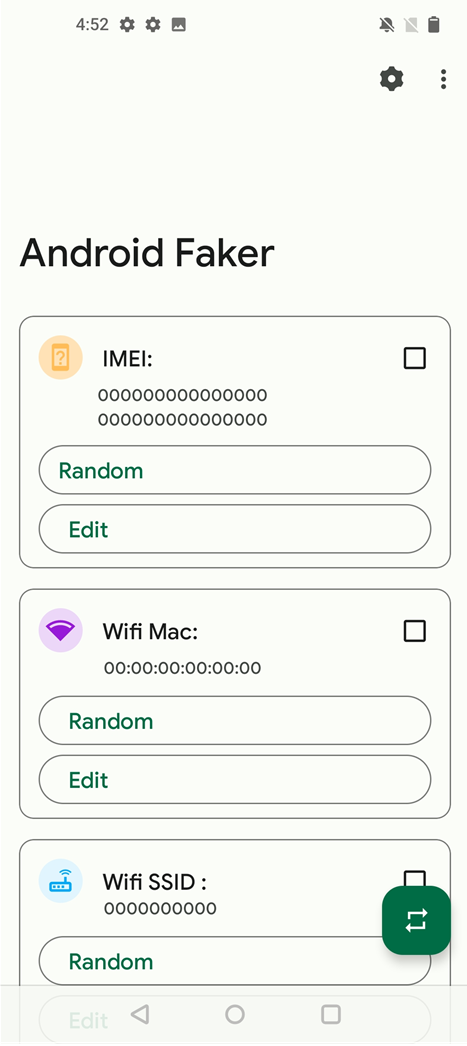 |
Cookie Import
Mobile antidetect developers frequently recommend using alternative browsers like KiwiBrowser for fraudsters exploiting stolen cookie files.
GPS Spoofing
GPS spoofing allows threat actors to modify their location ideogrammatically. Combined with high-quality anonymization services like mobile residential proxies, this feature enables fraudsters to mimic victims’ locations and trick anti-fraud engines into analyzing the geography of previous logins. Several tools may be downloaded separately from antidetects for that. Still, both packages acquired from and MacFly contain the: GPS Setter, GPS Joystick, and Hide Mock Location.
MacFly demonstrated how the tool could be used to spoof the location of a particular modified coordinate, along with a victim’s pre-recorded route, which allows a threat actor to imitate a client in movement (e.g., driving in a taxi).
During installation, HUNTER identified the following modules:
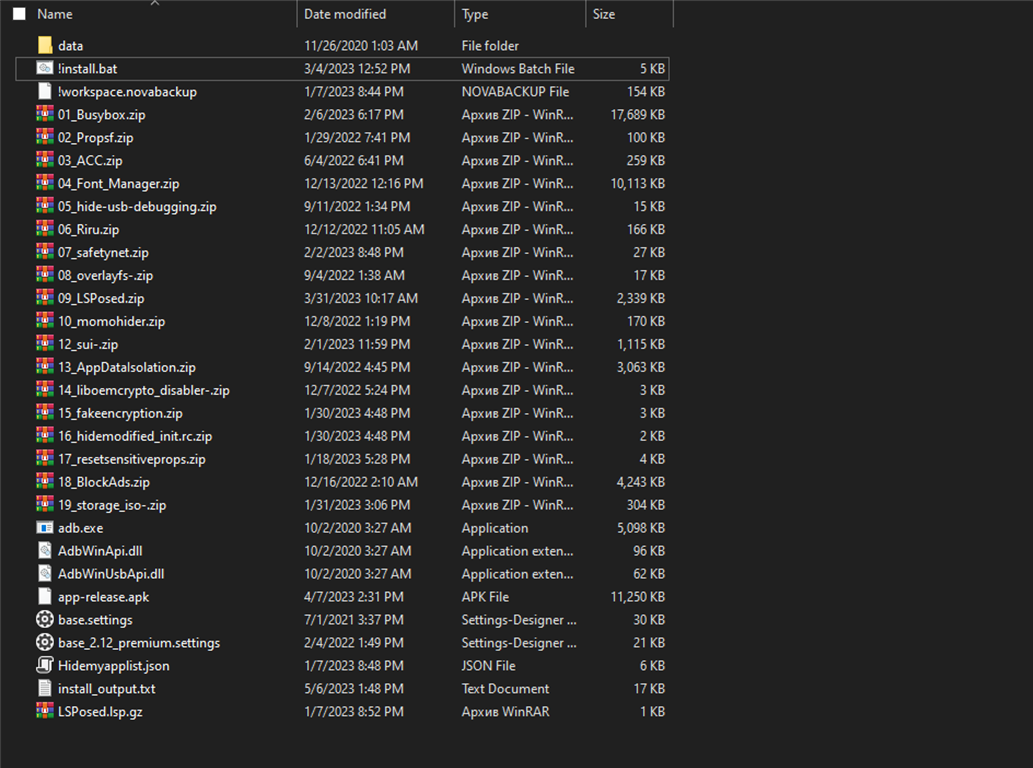
| adb push !workspace.novabackup /storage/emulated/0/ adb push data /storage/emulated/0 adb push 01_Busybox.zip /storage/emulated/0 adb push 02_Propsf.zip /storage/emulated/0/ adb push 03_ACC.zip /storage/emulated/0/ adb push 04_Font_Manager.zip /storage/emulated/0/ adb push 05_hide-usb-debugging.zip /storage/emulated/0/ adb push 06_Riru.zip /storage/emulated/0/ adb push 07_safetynet.zip /storage/emulated/0/ adb push 09_LSPosed.zip /storage/emulated/0/ adb push 10_momohider.zip /storage/emulated/0/ adb push 08_overlayfs.zip /storage/emulated/0/ adb push 11_riru-unshare_a10.zip /storage/emulated/0/ adb push 12_Storage.zip /storage/emulated/0/ adb push 12_sui.zip /storage/emulated/0/ adb push 13_AppDataIsolation.zip /storage/emulated/0/ adb push 14_liboemcrypto_disabler.zip /storage/emulated/0/ adb push 15_fakeencryption.zip /storage/emulated/0/ adb push 16_hidemodified_init.rc.zip /storage/emulated/0/ adb push 17_resetsensitiveprops.zip /storage/emulated/0/ adb push 18_BlockAds.zip /storage/emulated/0/ adb push 19_storage_iso.zip /storage/emulated/0/ adb push app-release.apk /storage/emulated/0/ adb push Hidemyapplist.json /storage/emulated/0/ adb push base.settings /storage/emulated/0/ adb push base_2.12_premium.settings /storage/emulated/0/ adb push LSPosed.lsp.gz /storage/emulated/0/ rem adb shell su -c pm disable com.coloros.phonemanager rem shell su -c pm disable com.oppo.ota rem shell su -c pm disable com.nearme.romupdate rem shell su -c pm disable com.coloros.sau adb shell su -c setenforce 1 adb shell su -c magisk --install-module /storage/emulated/0/01_Busybox.zip adb shell su -c magisk --install-module /storage/emulated/0/02_Propsf.zip adb shell su -c magisk --install-module /storage/emulated/0/03_ACC.zip adb shell su -c magisk --install-module /storage/emulated/0/04_Font_Manager.zip adb shell su -c magisk --install-module /storage/emulated/0/05_hide-usb-debugging.zip adb shell su -c magisk --install-module /storage/emulated/0/06_Riru.zip adb shell su -c magisk --install-module /storage/emulated/0/07_safetynet.zip adb shell su -c magisk --install-module /storage/emulated/0/09_LSPosed.zip adb shell su -c magisk --install-module /storage/emulated/0/10_momohider.zip adb shell su -c magisk --install-module /storage/emulated/0/11_riru-unshare_a10.zip adb shell su -c magisk --install-module /storage/emulated/0/12_Storage.zip adb shell su -c magisk --install-module /storage/emulated/0/08_overlayfs.zip adb shell su -c magisk --install-module /storage/emulated/0/12_sui.zip adb shell su -c magisk --install-module /storage/emulated/0/13_AppDataIsolation.zip adb shell su -c magisk --install-module /storage/emulated/0/14_liboemcrypto_disabler.zip adb shell su -c magisk --install-module /storage/emulated/0/15_fakeencryption.zip adb shell su -c magisk --install-module /storage/emulated/0/16_hidemodified_init.rc.zip adb shell su -c magisk --install-module /storage/emulated/0/17_resetsensitiveprops.zip adb shell su -c magisk --install-module /storage/emulated/0/18_BlockAds.zip adb shell su -c magisk --install-module /storage/emulated/0/19_storage_iso.zip echo press for end install pause adb shell su -c magiskhide add com.google.android.gms adb shell su -c magiskhide add com.google.android.gms.unstable adb shell su -c magiskhide add com.byxiaorun.detector adb shell rm /storage/emulated/0/01_Busybox.zip adb shell rm /storage/emulated/0/02_Propsf.zip adb shell rm /storage/emulated/0/03_ACC.zip adb shell rm /storage/emulated/0/04_Font_Manager.zip adb shell rm /storage/emulated/0/05_hide-usb-debugging.z adb shell rm /storage/emulated/0/06_Riru.zip adb shell rm /storage/emulated/0/07_safetynet.zip adb shell rm /storage/emulated/0/09_LSPosed.zip adb shell rm /storage/emulated/0/10_momohider.zip adb shell rm /storage/emulated/0/11_riru-unshare_a10.zip adb shell rm /storage/emulated/0/12_Storage.zip adb shell rm /storage/emulated/0/05_hide-usb-debugging.zip adb shell rm /storage/emulated/0/!workspace.novabackup adb shell rm /storage/emulated/0/08_overlayfs.zip adb shell rm /storage/emulated/0/12_sui.zip adb shell rm /storage/emulated/0/13_AppDataIsolation.zip adb shell rm /storage/emulated/0/14_liboemcrypto_disabler.zip adb shell rm /storage/emulated/0/15_fakeencryption.zip adb shell rm /storage/emulated/0/16_hidemodified_init.rc.zip adb shell rm /storage/emulated/0/19_storage_iso.zip adb shell rm /storage/emulated/0/18_BlockAds.zip adb shell rm /storage/emulated/0/17_resetsensitiveprops.zip |
The actors deploy LSPosed, and HideMyApp (HMA), with configuration settings defined in the "Hidemyapplist.json" file. In addition to that, the package drops "base.settings" and "base_2.12_premium.settings" in encrypted form.
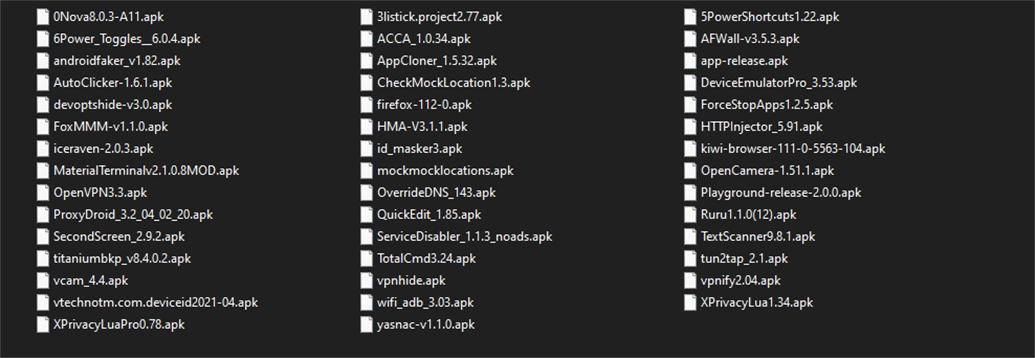
Recovered "Hidemyapplist.json" by our reverse engineers contains the following list of supported applications from major online services and mobile banking:
"configVersion": 90, "detailLog": false, "maxLogSize": 512, "forceMountData": true, "templates": { "mr_macfly": { "isWhitelist": false, "appList": [ "com.tsng.applistdetector", "eu.faircode.xlua.pro", "com.newtoolsworks.tun2tap", "zone.bytesreverser.xposeddeviceidmaskerlite", "io.github.huskydg.magisk", "eu.chylek.adam.fakewifi", "ru.yedcxjps.ljvzfgvsn", "ru.ptktpqhy.iatvdqdor", "ru.rqcztpka.ngzmyvigb", "de.blinkt.openvpn", "com.fox2code.mmm", "eu.faircode.xlua", "com.device.emulator.pro", "com.evozi.deviceid", "dev.ukanth.ufirewall", "net.mx17.overridedns", "com.applisto.appcloner", "com.ttxapps.wifiadb", "com.android1500.androidfaker", "com.farmerbb.secondscreen.free", "project.listick.fakegps", "x.vpk", "io.github.vvb2060.mahoshojo", "ru.andr7e.deviceinfohw", "com.coderstory.toolkit", "com.github.kolacbb.ids", "com.brandonnalls.mockmocklocations", "com.tsng.hidemyapplist", "com.godevelopers.OprekCek", "io.github.vvb2060.magisk", "com.evozi.injector", "com.applisto.appcloneR", "moe.shizuku.redirectstorage", "com.genymobile.gnirehtet", "com.ytheekshana.deviceinfo", "net.accelf.devoptshide", "com.vpn.free.hotspot.secure.vpnify", "com.theappninjas.fakegpsjoystick", "com.example.vcam", "com.topjohnwu.magisk", "me.hoshino.novpndetect", "com.kunkunsoft.rootservicedisabler", "org.proxydroid", "com.finalwire.aida64", "com.truedevelopersstudio.automatictap.autoclicker", "com.varuns2002.disable_flag_secure", "mattecarra.accapp" ] } }, "scope": { "com.tsng.applistdetector": { "useWhitelist": false, "excludeSystemApps": true, "applyTemplates": [ "mr_macfly" ], "extraAppList": [] }, "com.BanqueMisr.MobileBanking": { "useWhitelist": true, "excludeSystemApps": true, "applyTemplates": [], "extraAppList": [] }, "uk.co.santander.spendlytics": { "useWhitelist": true, "excludeSystemApps": true, "applyTemplates": [], "extraAppList": [] }, "com.godevelopers.OprekCek": { "useWhitelist": false, "excludeSystemApps": false, "applyTemplates": [ "mr_macfly" ], "extraAppList": [] }, "com.starfinanz.mobile.android.pushtan": { "useWhitelist": false, "excludeSystemApps": true, "applyTemplates": [ "mr_macfly" ], "extraAppList": [] }, "com.axis.mobile": { "useWhitelist": true, "excludeSystemApps": true, "applyTemplates": [], "extraAppList": [] }, "com.binance.dev": { "useWhitelist": false, "excludeSystemApps": false, "applyTemplates": [], "extraAppList": [] }, "com.finalwire.aida64": { "useWhitelist": true, "excludeSystemApps": false, "applyTemplates": [], "extraAppList": [ "org.mozilla.firefox" ] }, "ru.app.paycoinchecker": { "useWhitelist": true, "excludeSystemApps": false, "applyTemplates": [], "extraAppList": [] }, "io.github.vvb2060.mahoshojo": { "useWhitelist": false, "excludeSystemApps": false, "applyTemplates": [ "mr_macfly" ], "extraAppList": [] }, "vn.com.techcombank.bb.app": { "useWhitelist": false, "excludeSystemApps": false, "applyTemplates": [ "mr_macfly" ], "extraAppList": [] }, "de.fiduciagad.securego.wl": { "useWhitelist": true, "excludeSystemApps": true, "applyTemplates": [], "extraAppList": [] }, "de.fiduciagad.securego.vr": { "useWhitelist": true, "excludeSystemApps": true, "applyTemplates": [], "extraAppList": [] }, "cz.rb.app.smartphonebanking": { "useWhitelist": false, "excludeSystemApps": false, "applyTemplates": [ "mr_macfly" ], "extraAppList": [] }, "com.csam.icici.bank.imobile": { "useWhitelist": false, "excludeSystemApps": false, "applyTemplates": [ "mr_macfly" ], "extraAppList": [] }, "com.starfinanz.mobile.android.bwpushtan": { "useWhitelist": false, "excludeSystemApps": false, "applyTemplates": [ "mr_macfly" ], "extraAppList": [] }, "com.napsternetlabs.napsternetv": { "useWhitelist": false, "excludeSystemApps": false, "applyTemplates": [ "mr_macfly" ], "extraAppList": [] }, "com.pubg.newstate": { "useWhitelist": false, "excludeSystemApps": false, "applyTemplates": [ "mr_macfly" ], "extraAppList": [] }, "ru.nspk.mirpay": { "useWhitelist": false, "excludeSystemApps": false, "applyTemplates": [ "mr_macfly" ], "extraAppList": [] }, "com.byxiaorun.detector": { "useWhitelist": false, "excludeSystemApps": false, "applyTemplates": [ "mr_macfly" ], "extraAppList": [] }, "pl.creditagricole.nmobi": { "useWhitelist": false, "excludeSystemApps": false, "applyTemplates": [ "mr_macfly" ], "extraAppList": [] }, "com.citibank.mobile.uk": { "useWhitelist": false, "excludeSystemApps": false, "applyTemplates": [ "mr_macfly" ], "extraAppList": [] }, "com.citibank.mobile.tw": { "useWhitelist": false, "excludeSystemApps": false, "applyTemplates": [ "mr_macfly" ], "extraAppList": [] }, "hr.asseco.android.kaspibusiness": { "useWhitelist": false, "excludeSystemApps": false, "applyTemplates": [ "mr_macfly" ], "extraAppList": [] }, "com.wirebarley.android": { "useWhitelist": false, "excludeSystemApps": false, "applyTemplates": [ "mr_macfly" ], "extraAppList": [] }, "id.bmri.livin": { "useWhitelist": false, "excludeSystemApps": false, "applyTemplates": [ "mr_macfly" ], "extraAppList": [] }, "com.square_enix.android_googleplay.octopathw": { "useWhitelist": false, "excludeSystemApps": false, "applyTemplates": [ "mr_macfly" ], "extraAppList": [] }, "ru.m4bank.softpos.halykg": { "useWhitelist": false, "excludeSystemApps": false, "applyTemplates": [ "mr_macfly" ], "extraAppList": [] }, "icu.nullptr.nativetest": { "useWhitelist": false, "excludeSystemApps": false, "applyTemplates": [ "mr_macfly" ], "extraAppList": [] }, "com.bet365.authenticator": { "useWhitelist": true, "excludeSystemApps": true, "applyTemplates": [], "extraAppList": [] }, "com.godevelopers.mockinfo": { "useWhitelist": false, "excludeSystemApps": false, "applyTemplates": [ "mr_macfly" ], "extraAppList": [] } } } |
Notable independent mobile software developers have previously described some of these tactics.
The archive provided by the actor, adb run.exe, contains four folders:
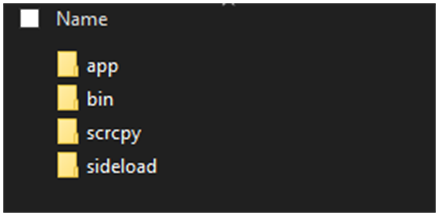
bin and scrcpy are tools to work with Android devices.
https://developer.android.com/tools/releases/platform-tools
Sideload: Magisk fork (Magisk delta) with additional modules and scenarios to upload them onto a device.
app: additional software
Architecture
The architecture of this mobile antidetect phone is based on Magisk and LSPosed and additional software (folder app).
https://github.com/HuskyDG/magisk-files
https://github.com/topjohnwu/Magisk
LSPosed (previously - Xposed) - unofficial Android framework made for changing codes of system apps (https://github.com/LSPosed/LSPosed).
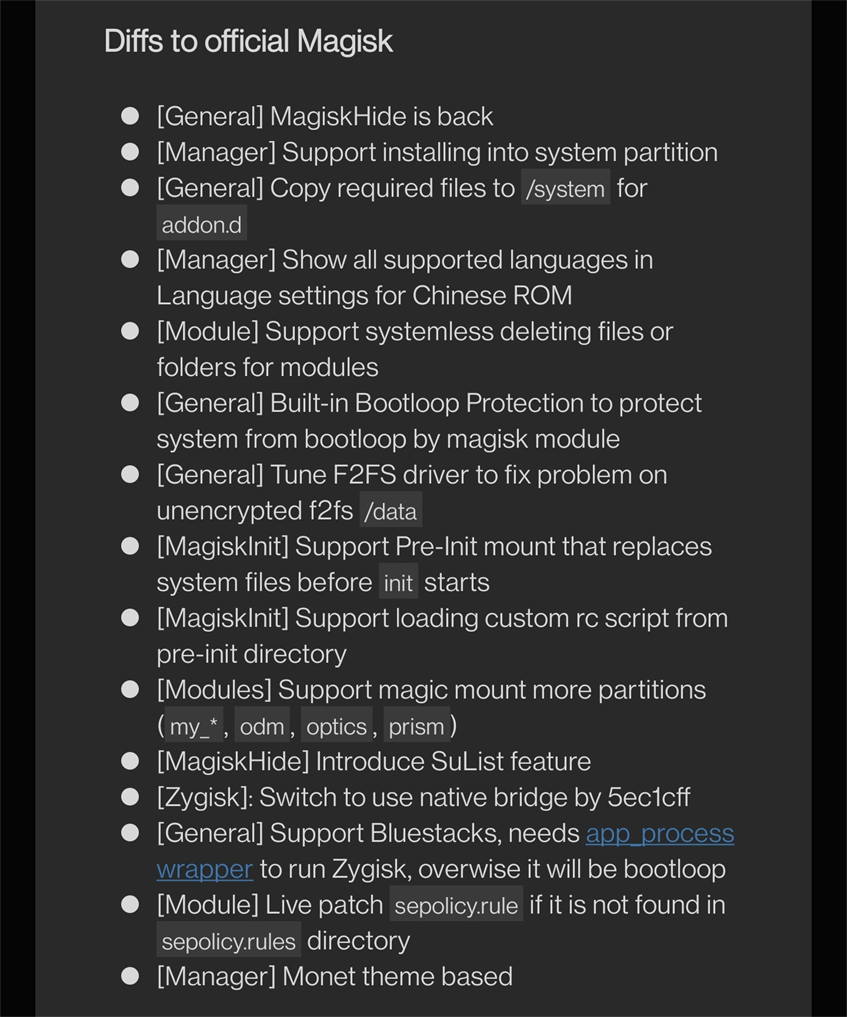
Notably, the author of mobile antidetects uses fork Magisk Delta from HuskyDG - https://github.com/HuskyDG/Magisk/tree/delta. Magisk Delta contains a magiskhide module allowing to hide root from selected apps (which doesn't exist in the official package).
The main differences between Magisk Delta from the official version of Magisk are provided below:
Installation
To install the solution on the device, you must first unlock the bootloader and install the driver to connect the device to the PC. Check the connection with the adb devices command.
Go to the folder sideload
Install MagiskDelta: app-release.apk, to get the root root. Подробнее https://www.xda-developers.com/how-to-install-magisk/
Check that Magisk has been successfully installed and has the status Installed:
Launch batch script !install.bat
Content of !install.bat:
| @echo off adb push !workspace.novabackup /storage/emulated/0/ adb push data /storage/emulated/0 adb push 01_Busybox.zip /storage/emulated/0 adb push 02_Propsf.zip /storage/emulated/0/ adb push 03_ACC.zip /storage/emulated/0/ adb push 04_Font_Manager.zip /storage/emulated/0/ adb push 05_hide-usb-debugging.zip /storage/emulated/0/ adb push 06_Riru.zip /storage/emulated/0/ adb push 07_safetynet.zip /storage/emulated/0/ adb push 09_LSPosed.zip /storage/emulated/0/ adb push 10_momohider.zip /storage/emulated/0/ adb push 08_overlayfs.zip /storage/emulated/0/ adb push 11_riru-unshare_a10.zip /storage/emulated/0/ adb push 12_Storage.zip /storage/emulated/0/ adb push 12_sui.zip /storage/emulated/0/ adb push 13_AppDataIsolation.zip /storage/emulated/0/ adb push 14_liboemcrypto_disabler.zip /storage/emulated/0/ adb push 15_fakeencryption.zip /storage/emulated/0/ adb push 16_hidemodified_init.rc.zip /storage/emulated/0/ adb push 17_resetsensitiveprops.zip /storage/emulated/0/ adb push 18_BlockAds.zip /storage/emulated/0/ adb push 19_storage_iso.zip /storage/emulated/0/ adb push app-release.apk /storage/emulated/0/ adb push Hidemyapplist.json /storage/emulated/0/ adb push base.settings /storage/emulated/0/ adb push base_2.12_premium.settings /storage/emulated/0/ adb push LSPosed.lsp.gz /storage/emulated/0/ rem adb shell su -c pm disable com.coloros.phonemanager rem shell su -c pm disable com.oppo.ota rem shell su -c pm disable com.nearme.romupdate rem shell su -c pm disable com.coloros.sau adb shell su -c setenforce 1 adb shell su -c magisk --install-module /storage/emulated/0/01_Busybox.zip adb shell su -c magisk --install-module /storage/emulated/0/02_Propsf.zip adb shell su -c magisk --install-module /storage/emulated/0/03_ACC.zip adb shell su -c magisk --install-module /storage/emulated/0/04_Font_Manager.zip adb shell su -c magisk --install-module /storage/emulated/0/05_hide-usb-debugging.zip adb shell su -c magisk --install-module /storage/emulated/0/06_Riru.zip adb shell su -c magisk --install-module /storage/emulated/0/07_safetynet.zip adb shell su -c magisk --install-module /storage/emulated/0/09_LSPosed.zip adb shell su -c magisk --install-module /storage/emulated/0/10_momohider.zip adb shell su -c magisk --install-module /storage/emulated/0/11_riru-unshare_a10.zip adb shell su -c magisk --install-module /storage/emulated/0/12_Storage.zip adb shell su -c magisk --install-module /storage/emulated/0/08_overlayfs.zip adb shell su -c magisk --install-module /storage/emulated/0/12_sui.zip adb shell su -c magisk --install-module /storage/emulated/0/13_AppDataIsolation.zip adb shell su -c magisk --install-module /storage/emulated/0/14_liboemcrypto_disabler.zip adb shell su -c magisk --install-module /storage/emulated/0/15_fakeencryption.zip adb shell su -c magisk --install-module /storage/emulated/0/16_hidemodified_init.rc.zip adb shell su -c magisk --install-module /storage/emulated/0/17_resetsensitiveprops.zip adb shell su -c magisk --install-module /storage/emulated/0/18_BlockAds.zip adb shell su -c magisk --install-module /storage/emulated/0/19_storage_iso.zip echo press for end install pause adb shell su -c magiskhide add com.google.android.gms adb shell su -c magiskhide add com.google.android.gms.unstable adb shell su -c magiskhide add com.byxiaorun.detector adb shell rm /storage/emulated/0/01_Busybox.zip adb shell rm /storage/emulated/0/02_Propsf.zip adb shell rm /storage/emulated/0/03_ACC.zip adb shell rm /storage/emulated/0/04_Font_Manager.zip adb shell rm /storage/emulated/0/05_hide-usb-debugging.z adb shell rm /storage/emulated/0/06_Riru.zip adb shell rm /storage/emulated/0/07_safetynet.zip adb shell rm /storage/emulated/0/09_LSPosed.zip adb shell rm /storage/emulated/0/10_momohider.zip adb shell rm /storage/emulated/0/11_riru-unshare_a10.zip adb shell rm /storage/emulated/0/12_Storage.zip adb shell rm /storage/emulated/0/05_hide-usb-debugging.zip adb shell rm /storage/emulated/0/!workspace.novabackup adb shell rm /storage/emulated/0/08_overlayfs.zip adb shell rm /storage/emulated/0/12_sui.zip adb shell rm /storage/emulated/0/13_AppDataIsolation.zip adb shell rm /storage/emulated/0/14_liboemcrypto_disabler.zip adb shell rm /storage/emulated/0/15_fakeencryption.zip adb shell rm /storage/emulated/0/16_hidemodified_init.rc.zip adb shell rm /storage/emulated/0/19_storage_iso.zip adb shell rm /storage/emulated/0/18_BlockAds.zip adb shell rm /storage/emulated/0/17_resetsensitiveprops.zip |
This script will install all the necessary Magisk modules to the device. Note that not all paths used in the script correspond to the data in the sideload directory. Some are missing; others have changed their name, with a “-” (dash symbol) added at the end. For example:
| Script !install.bat | Folder sideload |
| adb push 08_overlayfs.zip /storage/emulated/0/ | 08_overlayfs-.zip |
| adb push 11_riru-unshare_a10.zip /storage/emulated/0 | - |
| adb push 12_Storage.zip /storage/emulated/0/ | - |
| adb push 12_sui.zip /storage/emulated/0/ | - |
| adb push 14_liboemcrypto_disabler.zip /storage/emulated/0/ | 14_liboemcrypto_disabler-.zip |
| adb push 19_storage_iso.zip /storage/emulated/0/ | 19_storage_iso-.zip |
The program will upload app-release.apk and execute the following commands:
adb shell su -c magisk --install-module ...
...
adb shell su -c magiskhide add ...
The operator needs to copy software packages from the "app" folder to the device and install them.
Before to that, the author recommends checking the proper functionating of Magisk and the successful enablement of the LSPosed module:
As described earlier, the core of the mobile antidetect is based on MagiskHide – a module that allows you to hide the root on the device from applications.
https://github.com/HuskyDG/MagiskHide
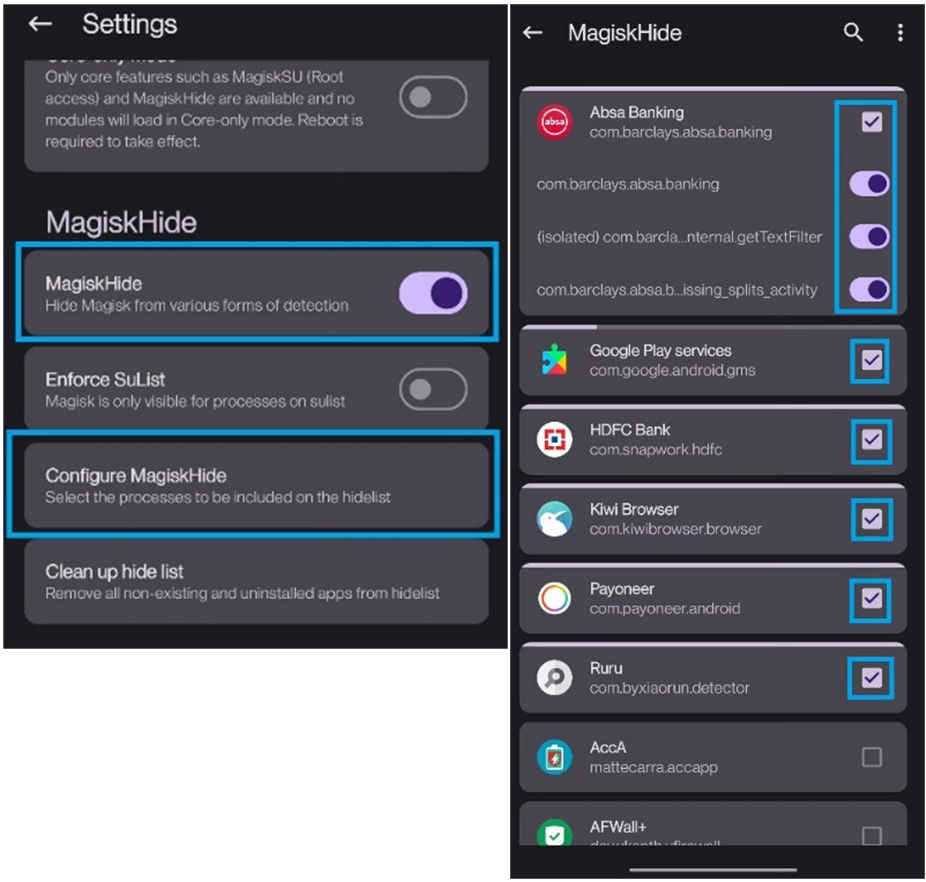
Applications hiding:
HMA (Hide My Applist) – The LSPosed module allows users to hide some applications from others (attacking from target). The config for the HMA module is at the root /Hidemyapplist.json (after running the !install.bat script). In LSPosed, the HMA module is activated and the config is loaded:
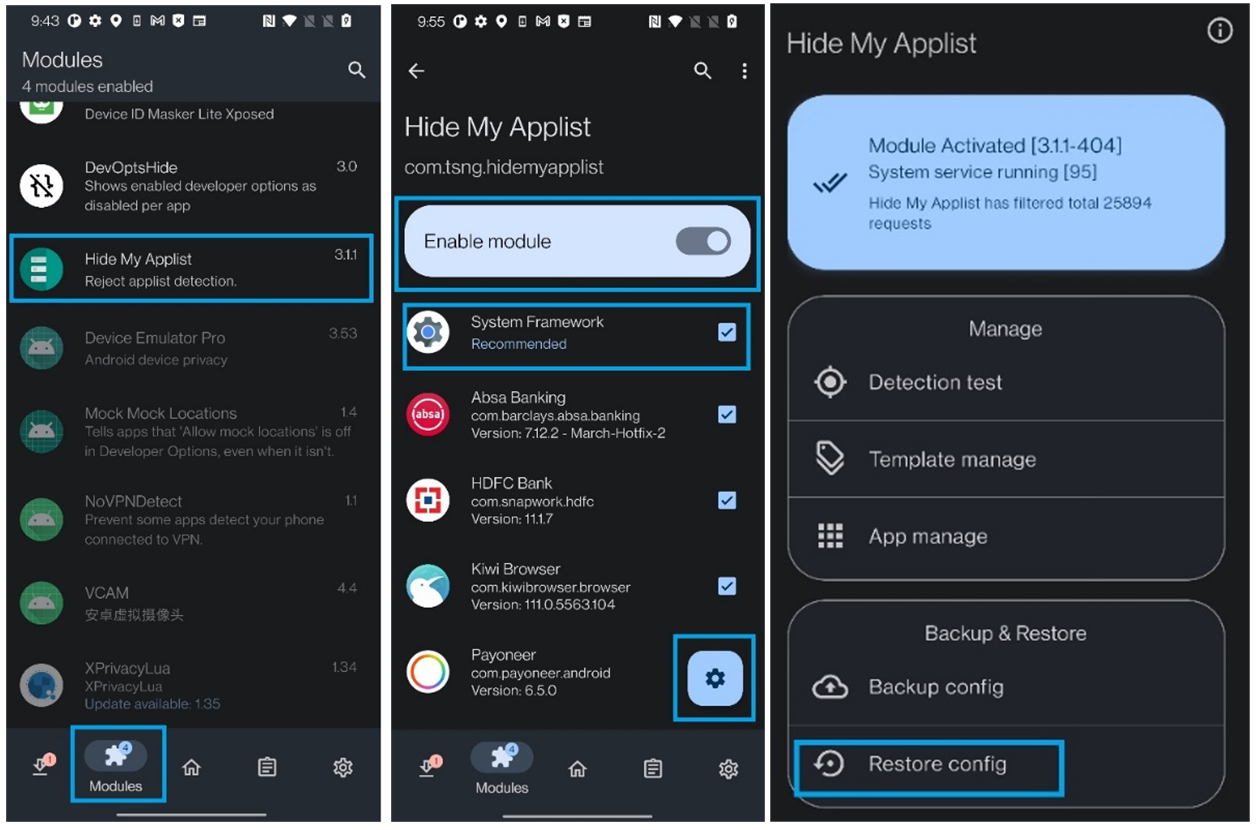
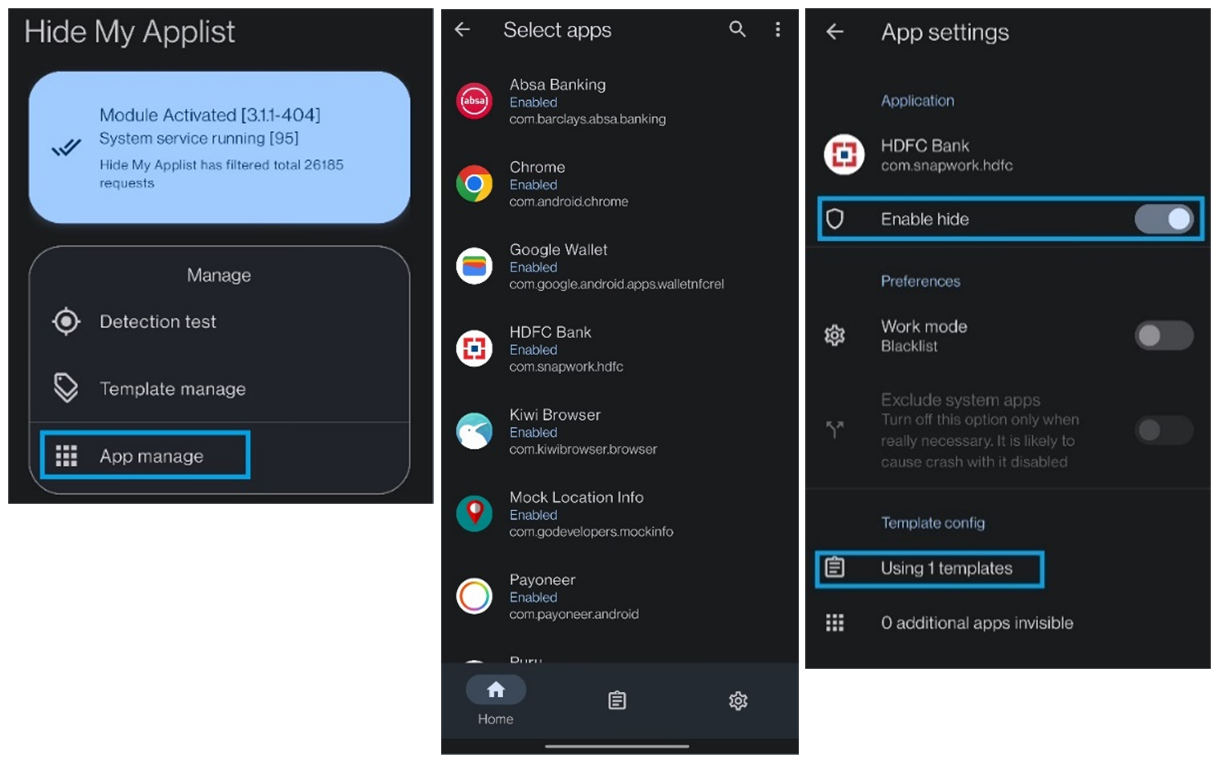
https://github.com/adrianmmiller/Hide-My-Applist-Guide
Hiding the GPS spoof:
Mock Mock Location - ready-to-use module available for location spoofing.
https://www.tenorshare.com/change-location/mock-mock-location.html
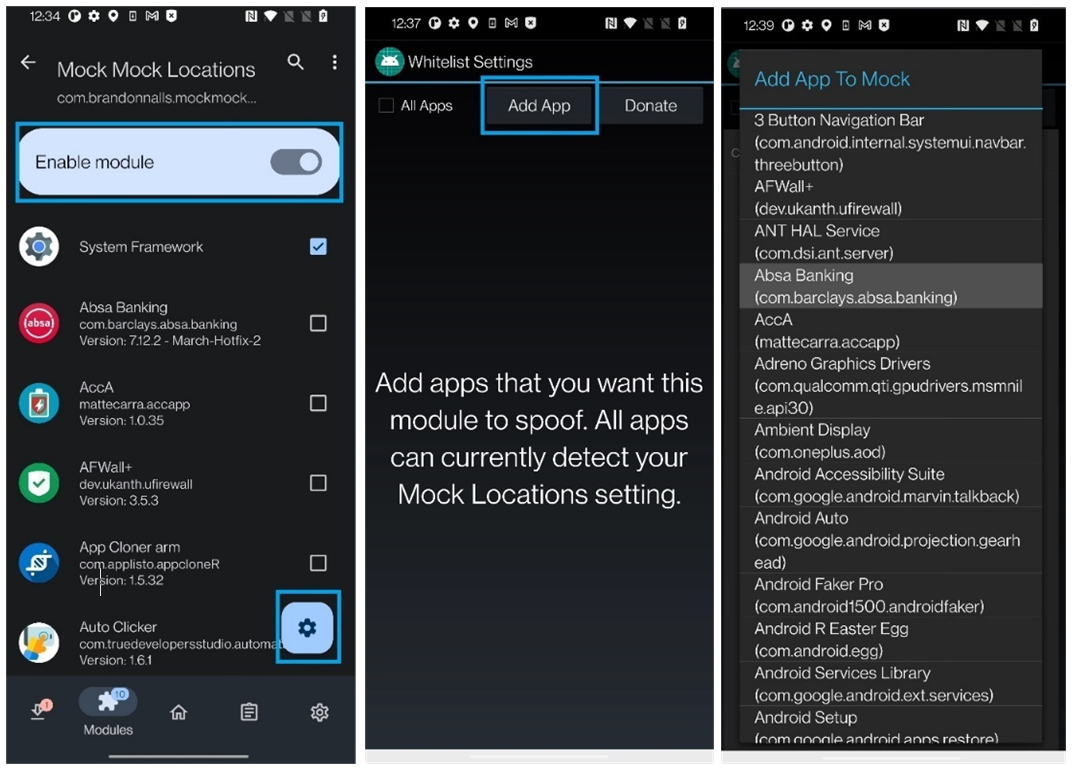
Hiding VPN:
NoVPNDetect - another useful module delivered via LSPosed allowing to hide the fact of VPN usage (on application level).
https://github.com/Xposed-Modules-Repo/me.hoshino.novpndetect
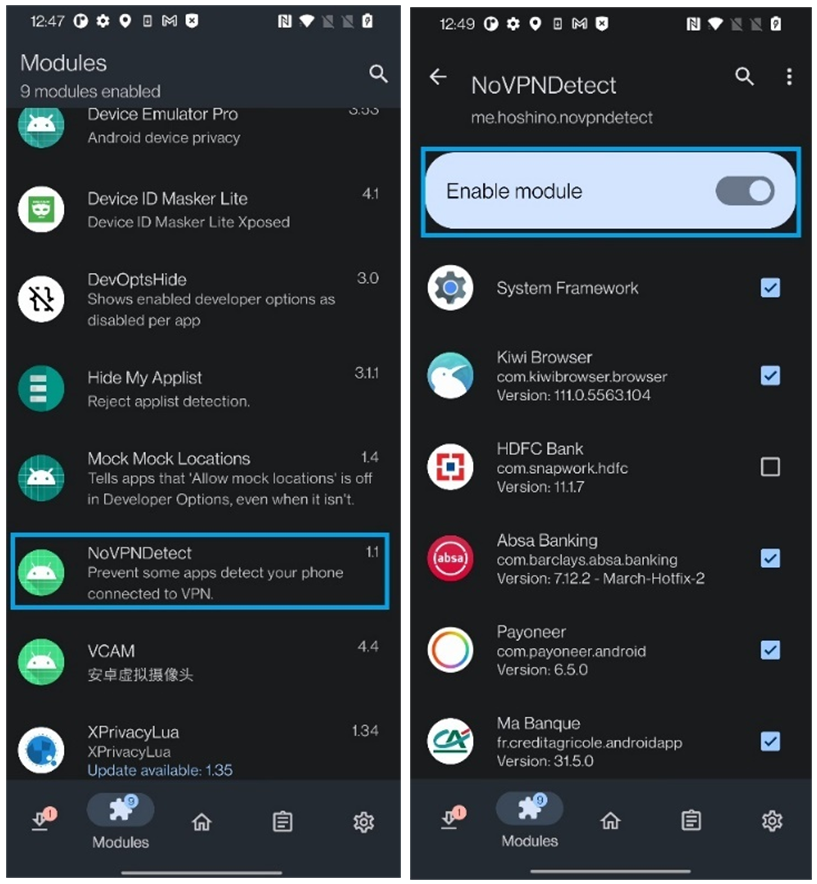
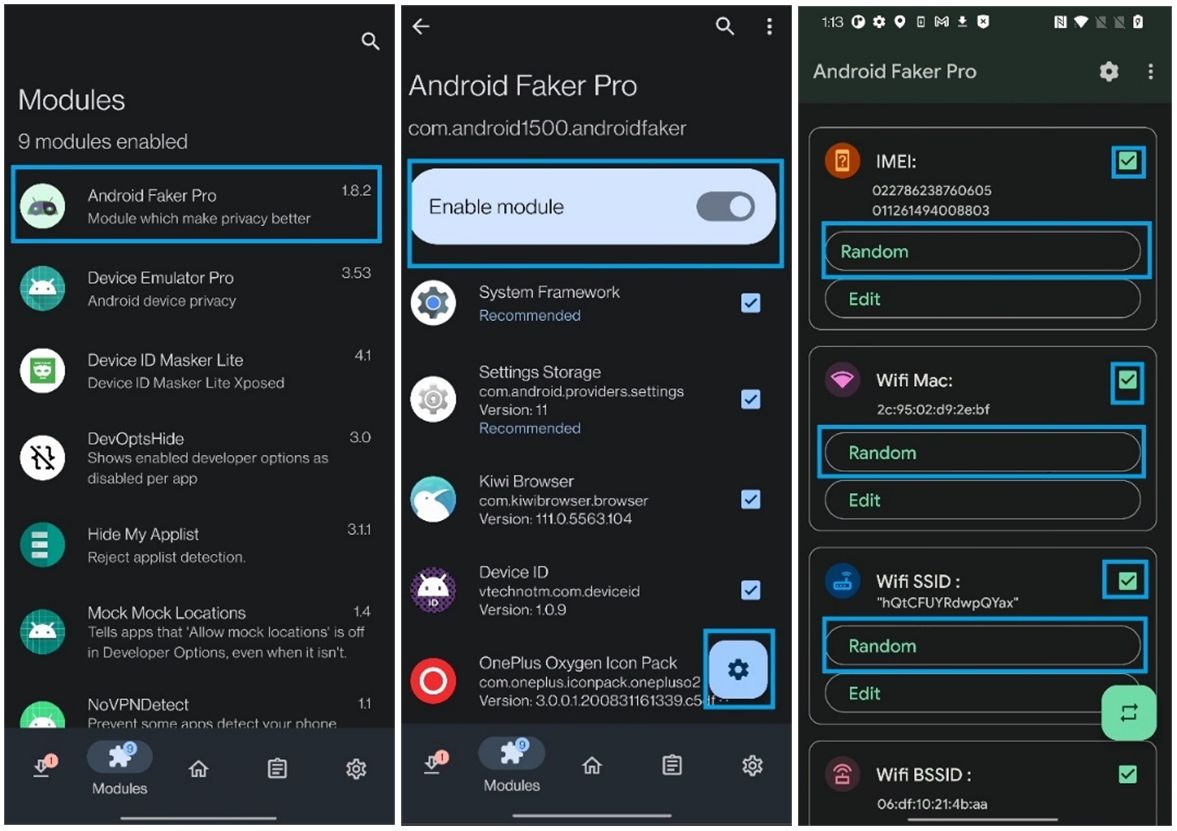
Hiding identifiers spoofers (IMEI, WiFi Mac, Bluetooth ID, SimSerial. Android ID, итд):
Android Faker Pro - another useful module of LSPOSED allowing to customize Android settings. The module enables spoofing of IMEI, WiFi Mac, Bluetooth ID, SimSerial—Android ID, and data artifacts related to Contacts, History, Calls, etc.
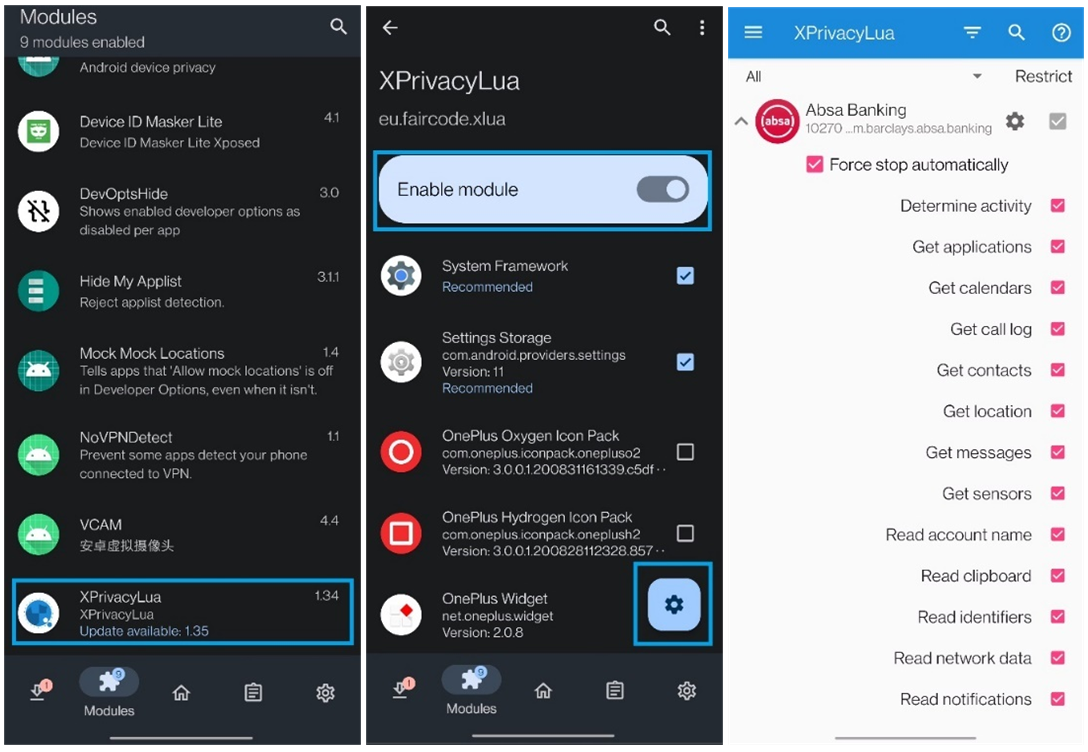
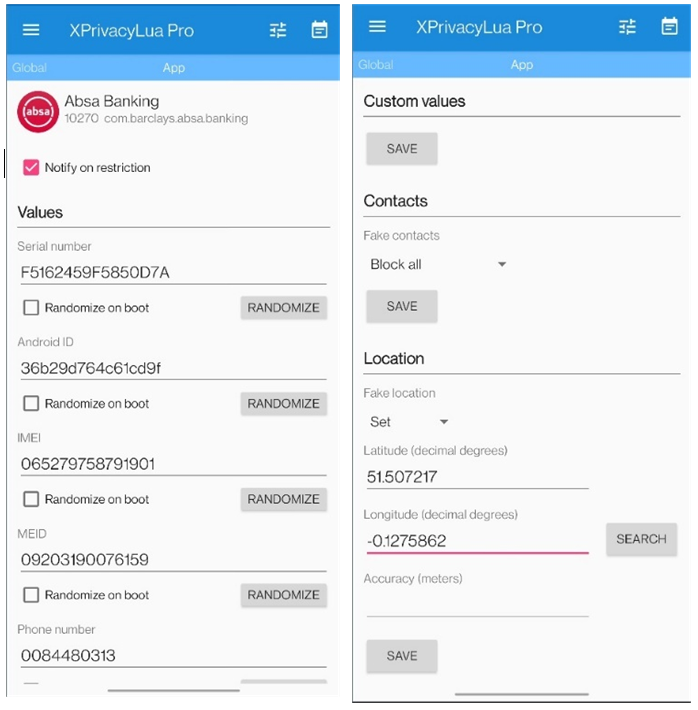
The authors are using it in combination with XPrivacyLua:
https://github.com/M66B/XPrivacyLua
Fingerprint Spoofing
MagiskHide Props Config - delivered as module in Magisk
https://github.com/Magisk-Modules-Repo/MagiskHidePropsConf
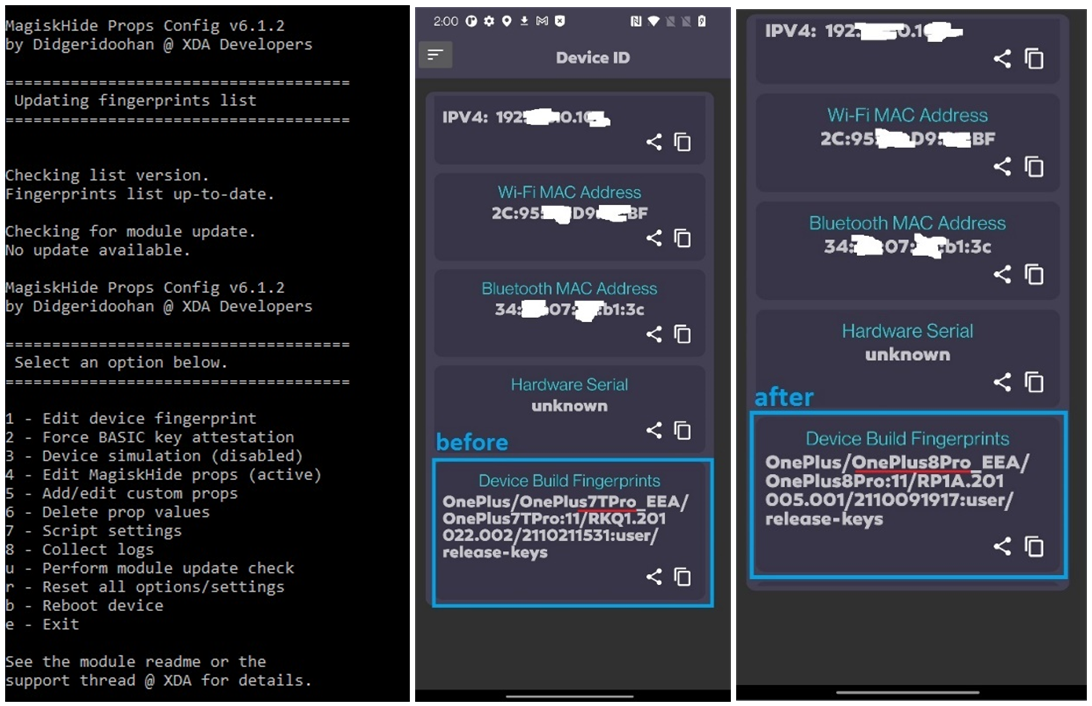
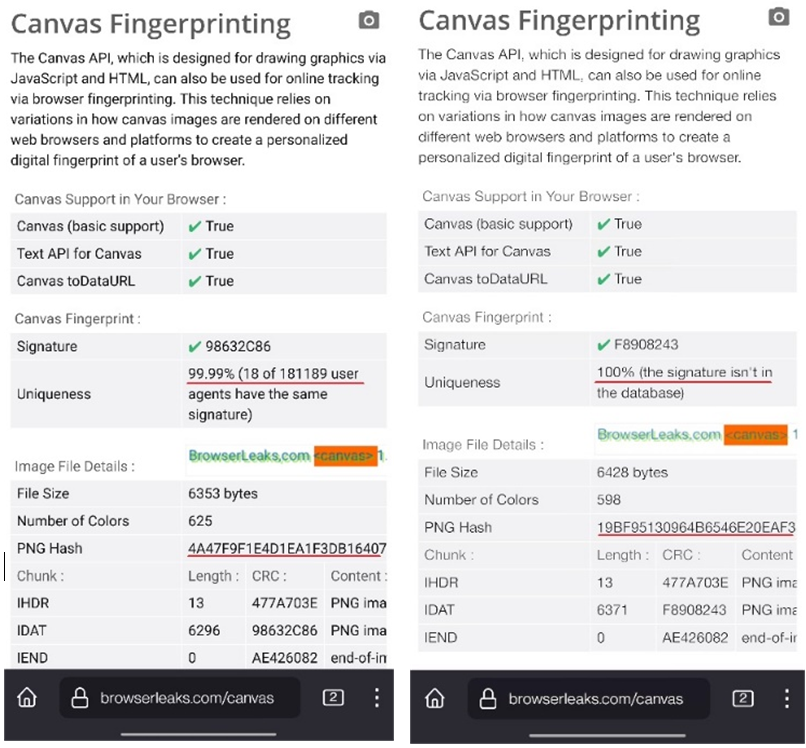
Canvas fingerprint spoofing
Font Manager - delivered as module in Magisk (https://www.androidacy.com/tag/font-manager/).
https://forum.xda-developers.com/t/magisk-module-font-manager-for-emojis-and-fonts.4194631/
https://browserleaks.com/canvas/ - The Canvas API, designed for drawing graphics via JavaScript and HTML, can also be used for online tracking via browser fingerprinting. This technique relies on variations in how canvas images are rendered on different web browsers and platforms to create a personalized digital fingerprint of a user's browser.
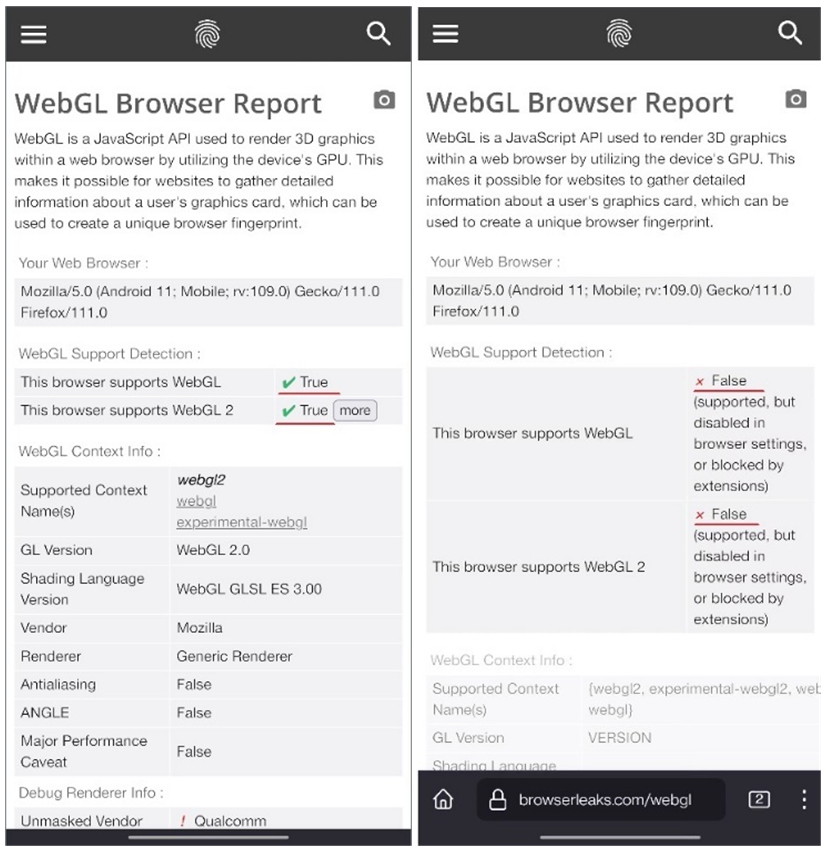
WebGL
The package includes Iceraven Browser (Mozilla-based):
https://github.com/fork-maintainers/iceraven-browser
about:config -> webgl.disabled -> true
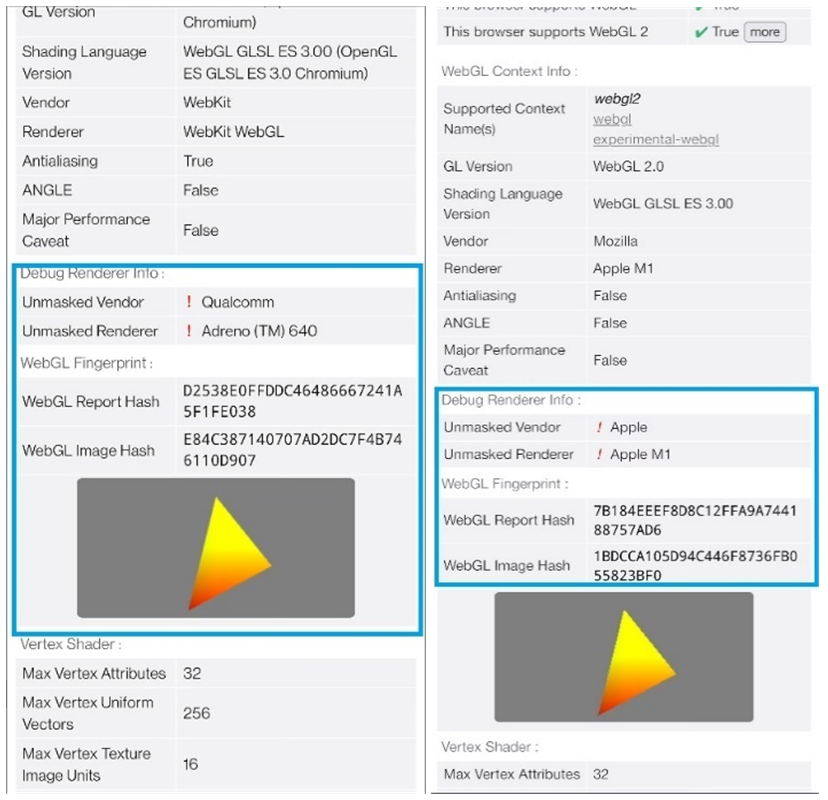
WebGL hash may be changed on the browser level:
about:
config -> webgl.override-unmasked-renderer -> webgl.override-unmasked-vendor
WebRTC
Can be disabled on browser level in Iceraven Browser (Mozilla-based)
https://browserleaks.com/webgl
about:config -> media.peerconnection.enabled -> false
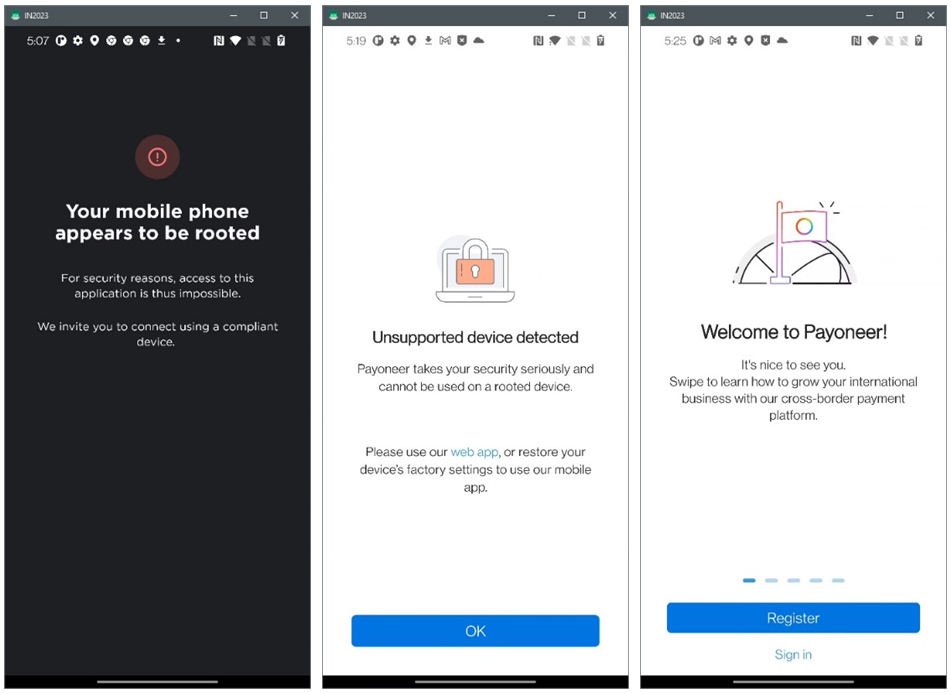
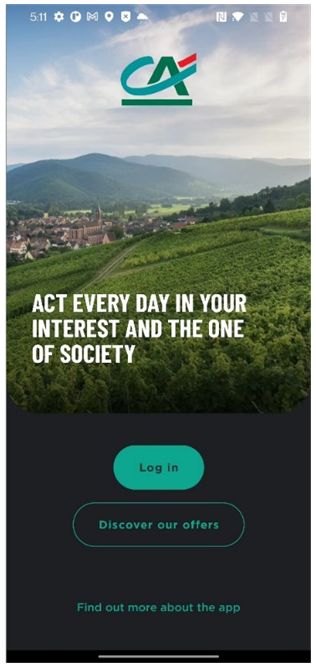
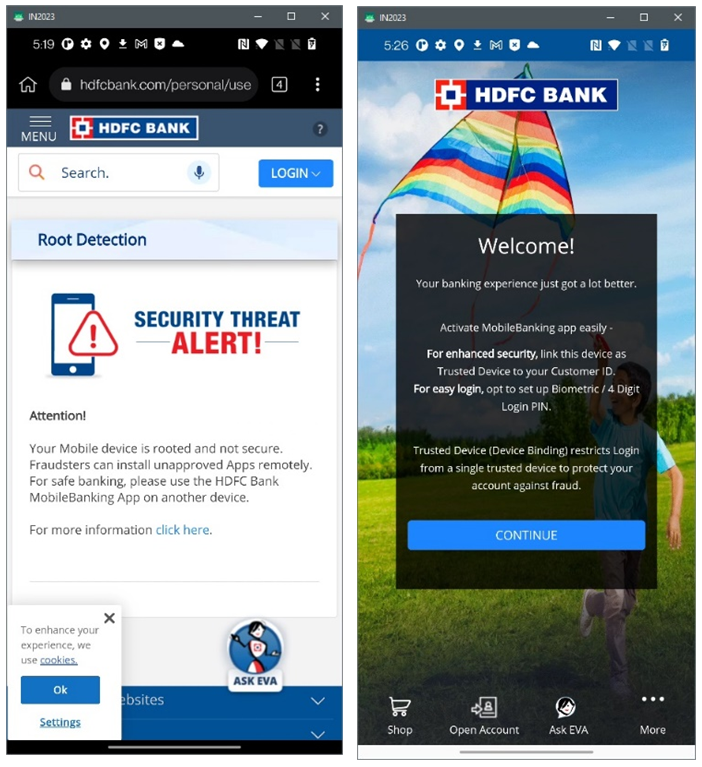
Based on Resecurity's assessment, both mobile anti-detects analyzed by our team are not that sophisticated by way of design, but rather act as a successful combination of tools and built-in Android mechanisms which successfully change the software environment. We’ve also detected how the authors of mobile anti-detects cherry pick elements from other products, or re-use publicly available components. To their compliment, successfully configuring packages based on those tools and modules allows them to create a “Swiss Army Knife” which fraudster’s can then utilize with other tools (including mobile malware, customized WEB-injects, residential IP proxies, etc.) to attack mobile banking and payment services.
Demonstration of hiding root on the example of random banking applications
Payoneer:
Credit Agricole:
HDFC Bank:
Absa Banking:
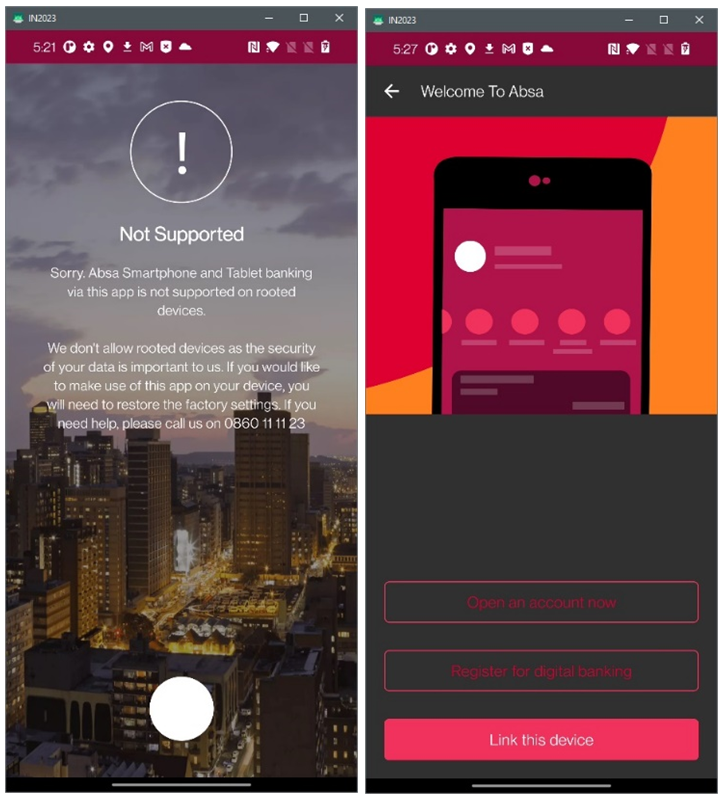
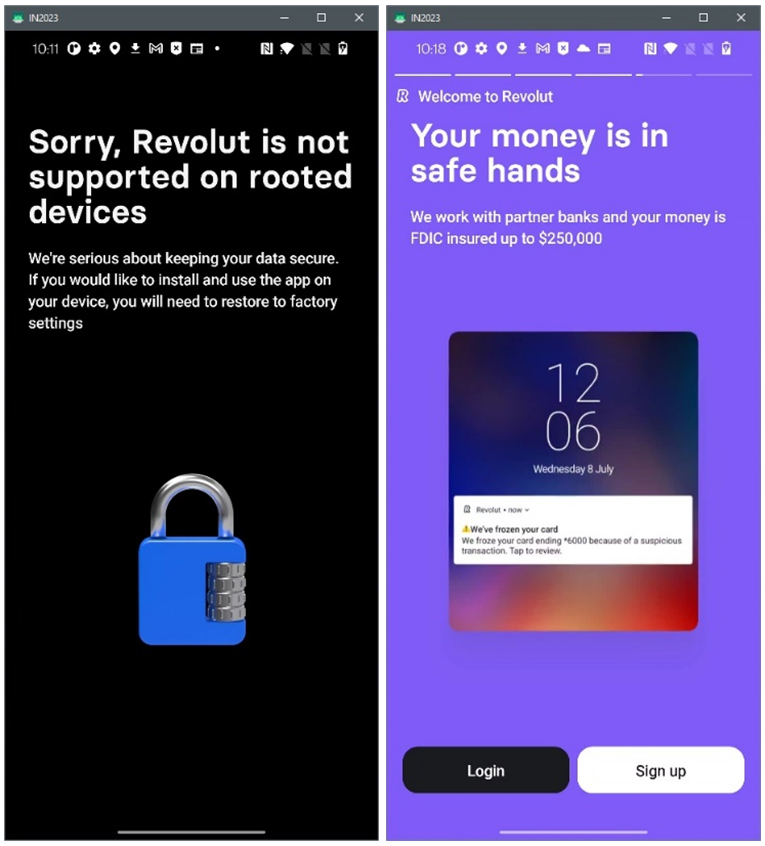
Revolut:
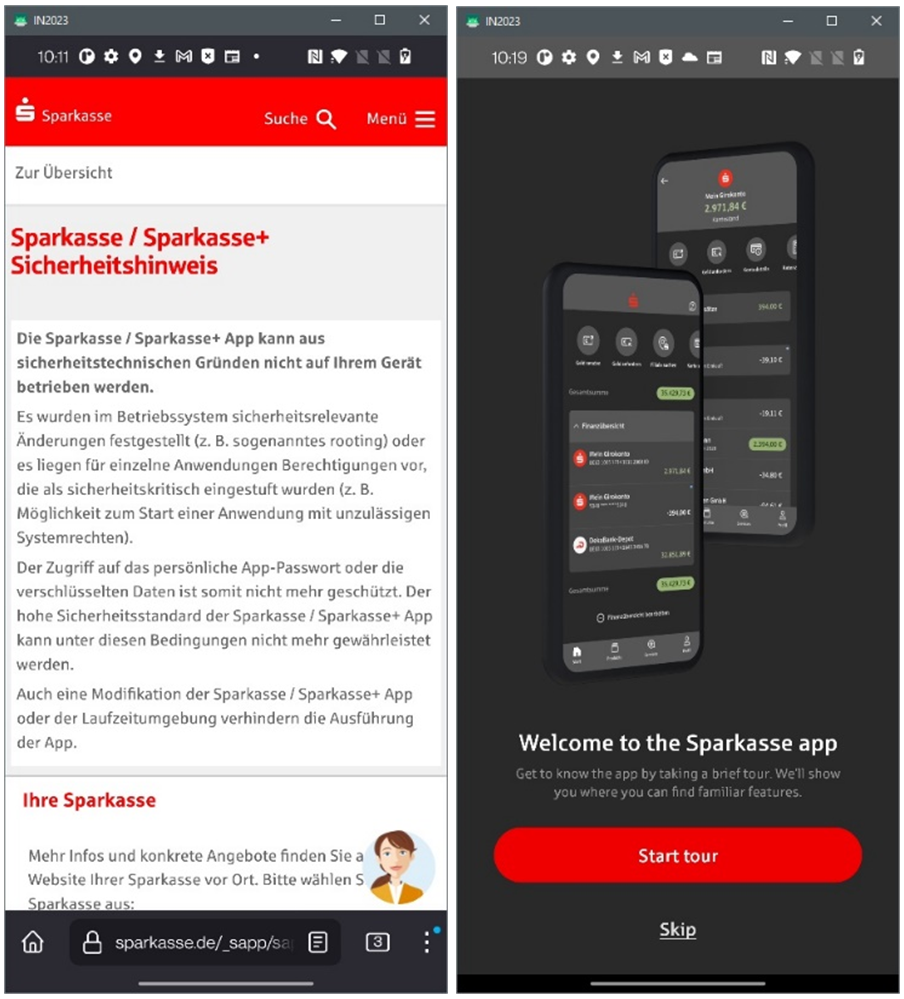
Parkasse:
Disclaimer
The identified findings and opportunity to execute payment mobile apps on "rooted" devices is not a vulnerability, rather a successful manipulation of the software environment on mobile devices. This emerging tactic will be widely used by bad actors to perform fraudulent and other malicious activity.
Significance
Mobile clients are a known “blind spot” for most anti-fraud providers. Financial Institutions (FIs) are trying to balance security and user-friendliness for their customers, ultimately enabling them to use various payment services and investment offerings without being blocked. Typically, mobile device customers access their bank website portal or mobile app via Wi-Fi, LTE, or 4G/5G. Based on user experience considerations, FIs thus design their mobile access terminals to minimize the risk of false positives that flag IP addresses and network activity as unusual, especially if there are no anomalies in a user’s geolocation and device information.
Threat actors weaponize this knowledge and look to use an IP address near a victim’s previously known location, mining this data from the network pools of frequently used ISP providers. Banking industry compliance and risk units are typically reluctant to apply aggressive fraud detection checks to mobile clients because the added friction runs the risk of excessive blocks on legitimate customer activity. As online banking customers increasingly seek faster and more convenient offerings, customer loyalty and retention are thus jeopardized by more stringent mobile fraud-prevention controls.
Adversaries exploit this prioritization of user experience by FIs and e-commerce firms by engineering smartphone-based attack kits like Mobile Antidetect by Enclave Service and Mobile Antidetect by MacFly. According to the Pew Research Center, with the rise of Generation Z and the continued growth of the online payments and e-commerce industries, mobile transactions have already emerged as the preferred method of sending money to friends and relatives and making purchases online. For these reasons, stakeholders at FIs, payment firms, and online retailers should stay up to date on the latest fraud trends and look to develop better risk-based mitigation controls that enhance fraud prevention and consumer protection.

