

Resecurity registered an increase in malicious activity targeting law enforcement agencies at the beginning of Q2 2022.
Threat actors are hacking e-mail accounts belonging to law enforcement officers, their aim is to leverage the accounts for further malicious purposes. Typically, they leverage social engineering tactics, however one of the recent trends is to address fake subpoenas and so called EDR’s (Emergency Data Requests) to major technology companies and online-services such as Apple, Facebook (Meta), Snapchat, Discord to maliciously collect sensitive information about their targets.
Threat actors are looking for billing history, geographical location, phone calls, text history, and other sensitive details which could be used to leverage extortion or cyberespionage purposes. Such incidents have become especially notable in cybercriminal group activities such as LAPSUS$ and Recursion Group.
Resecurity has observed multiple marketplaces in the Dark Web where cybercriminals have monetized accounts and credentials belonging to police officers of various foreign countries (e-mails, VPNs, SSO, etc.). One such email account has previously been used to send fake EDR requests on behalf of the Bangladesh Police which has been recently covered in a Bloomberg article where the CEO of Resecurity Gene Yoo was quoted. The price of such accounts is typically not different from any other compromised accounts and varies in range between $20-$35 but in some cases independent actors with bigger access may sell it in a range of $1,000-$10,000.
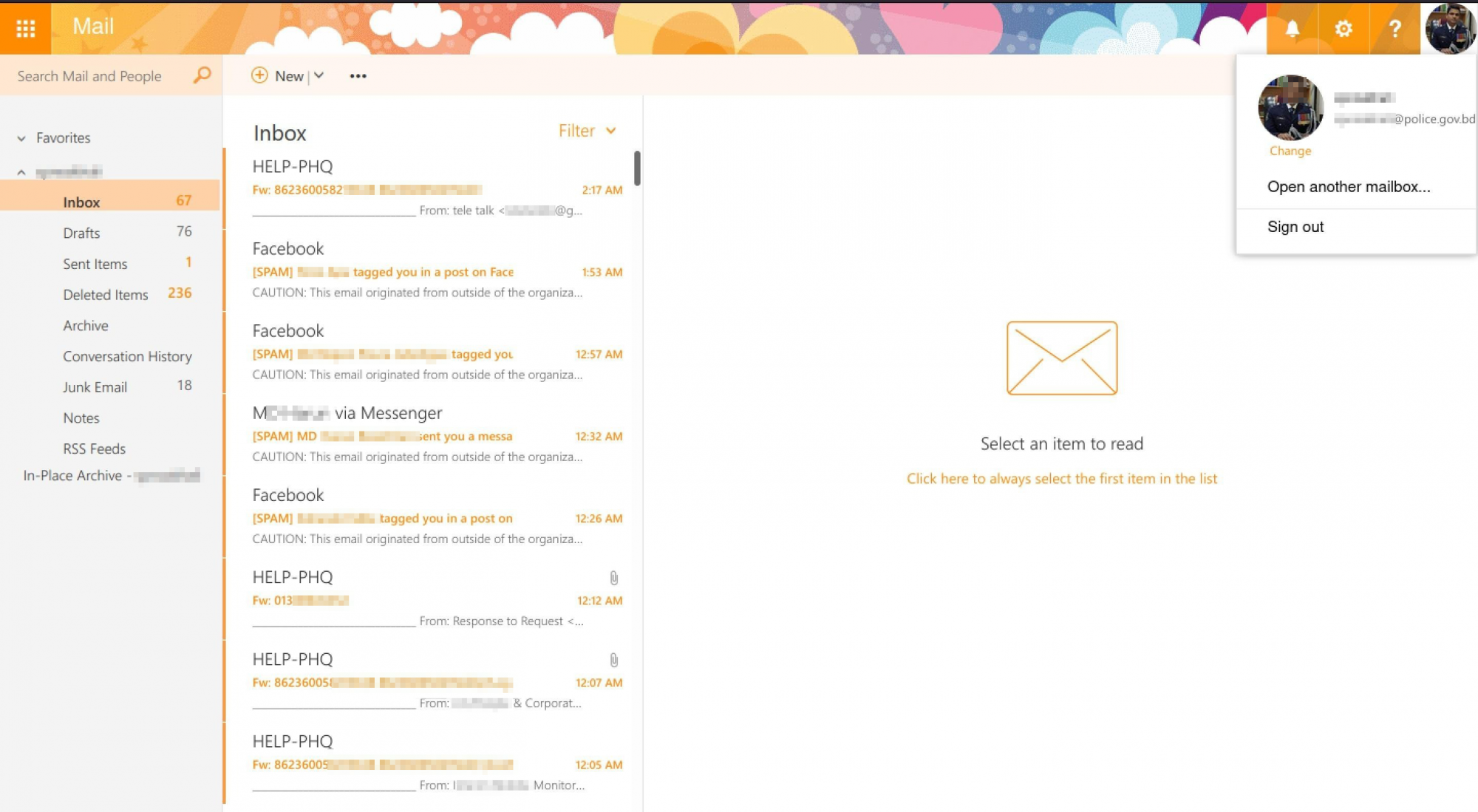

The incident has been timely reported by Resecurity to BGD e-Gov CIRT (Bangladesh e-Government Computer Incident Response Team) and over 5 compromised law enforcement accounts have been successfully recovered for further risk mitigation.
One of the biggest concerns – the visible security of the law enforcement IT infrastructure, which may create a significant risk to our society not just in cyberspace, but in real life too. Terrorists and extremist groups may leverage such access for malicious purposes.
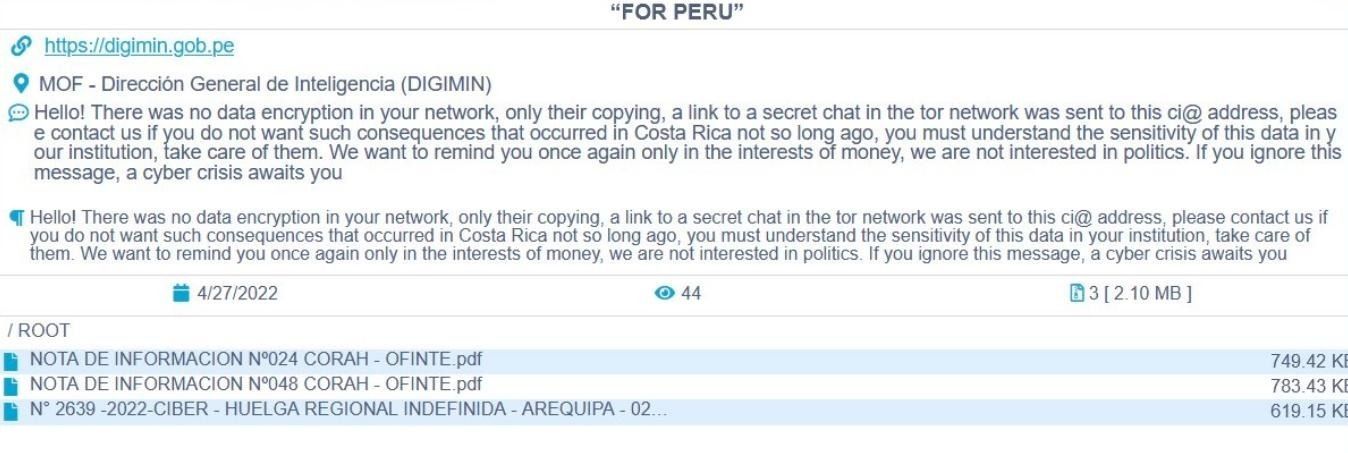
The trend is continuing, and more law enforcement organizations have been impacted by cyberattacks this month. Just recently, the Conti ransomware group attacked the Intelligence Agency in Peru and leaked their data which created a significant precedent in the security community. Cybercriminals were extorting DIGIMIN, one of the national agencies, asking for payment in cryptocurrency.
DDOS Secrets - another notable group of threat actors, has released 285,635 leaked emails from Nauru Police. The motivation of actors was different - hacktivists attempted to highlight possible abuses endured by asylum-seekers and refugees based on the island and to make them public.
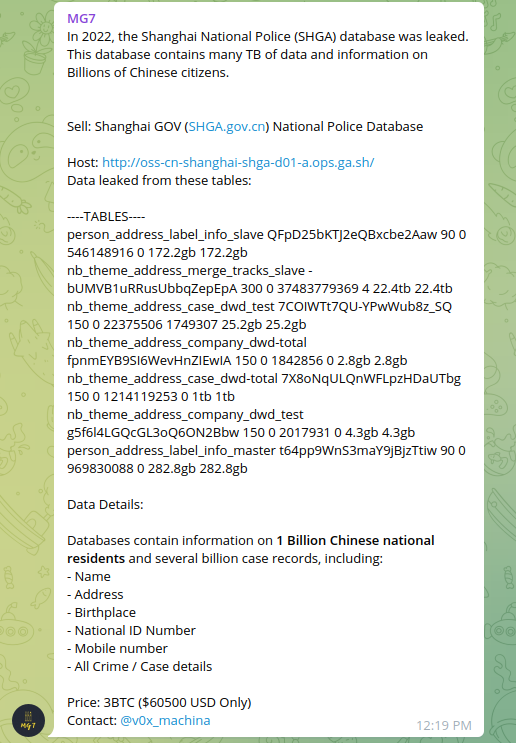
The bad actor in Dark Web offered for sale Shanghai Police database including 1B+ records about Chinese citizens. Multiple postings have been identified around July 2 with reference to actor "ChinaDan". According to several sources, the actor was offering 23 Terabytes of data for sale.

Later, this information has been offered by other independent actors for 3 BTC ($60,500). Using anonymous channels and IM like Telegram the actors were looking to monetize the stolen data in Dark Web.
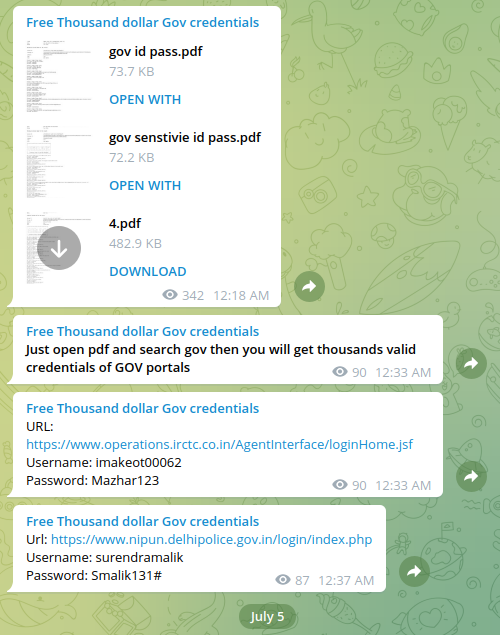
July 5, 2022 - the bad actor was offering access to Indian law enforcement portal and government resources in India. Based on further analysis, the credentials and associated data offered by the actor were likely compromised by password stealers such as Mars Stealer, X-Files Stealer or Azorult.
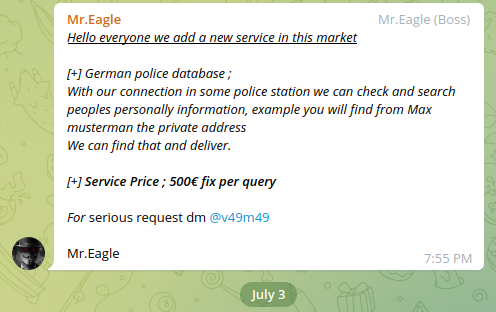
Cybercriminals abuse law enforcement databases and offer various illegal services in Dark Web creating significant risk for users' privacy. Using unauthorized access or insider contacts they're able to extract sensitive information and to monetize it in the underground. July 3, 2022 - there was identified an actor Mr.Eagle selling a "look-up" service for 500 euro (per query / per person).
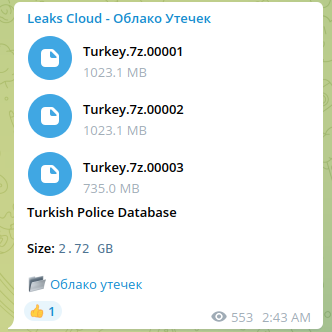
Last year, the bad actor released a dump of data presumably originating from an unnamed law enforcement system in Turkey. Notably, 6 years ago a hacker going by the online alias ROR[RG] has released a large amount of data that belonged to a Turkish National Police database and it's thought to contain large amounts of sensitive private information. ROR[RG] is aligned with the Anonymous hacktivist group and has leaked the data that was supposedly stolen from Turkish General Directorate of Security (EGM) onto a number of peer-to-peer sites for anyone to download and examine. The data was released through The Cthulu website, which has been a host of a number of leaks by members of Anonymous in the past, including a serious hack against a US Police union.
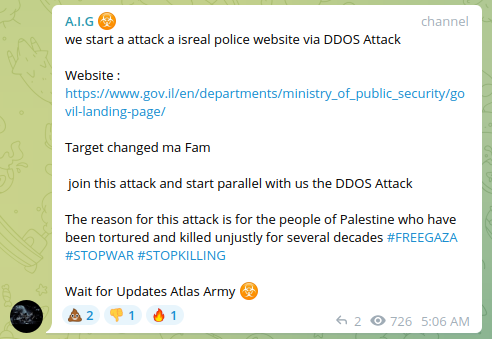
In context of ongoing geopolitical tensions, bad actors are actively attacking law enforcement WEB-sites leveraging various types of DDoS activity to create protest narratives.
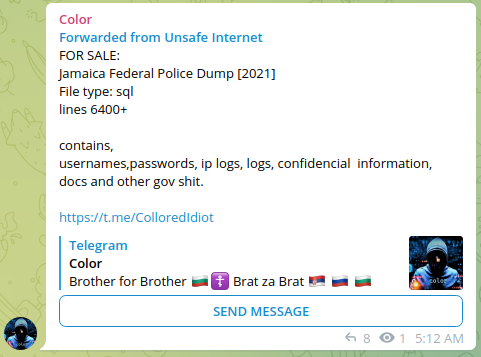
The bad actor was offering a dump of hacked law enforcement portals in Jamaica. Based on further assessment, he was able to exploit a MySQL injection vulnerability in one of the insecure modules of the official Jamaica Federal Police WEB-site.
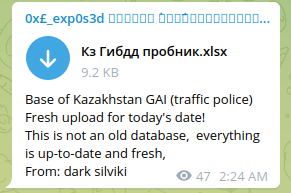
Bad actors released a road traffic & vehicle database of Kazakhstan presumably acquired from a law enforcement system. Such access allows to check car numbers, vehicles registration, and other PII related to citizens. Such offerings are also available commercially in Dark Web covering different geographical regions. The cost of "look-up" varies from $50 to $250.
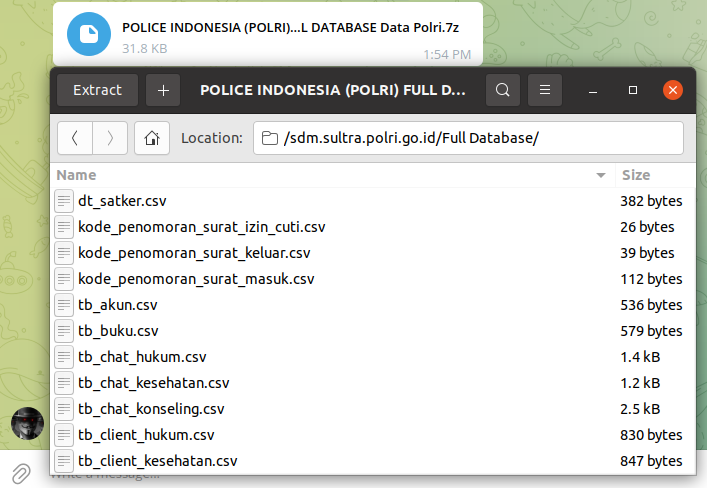
The bad actor was selling compromised database of WEB-application presumably belonging to a law enforcement in Indonesia. The stolen data also included internal communications and law enforcement employee information.
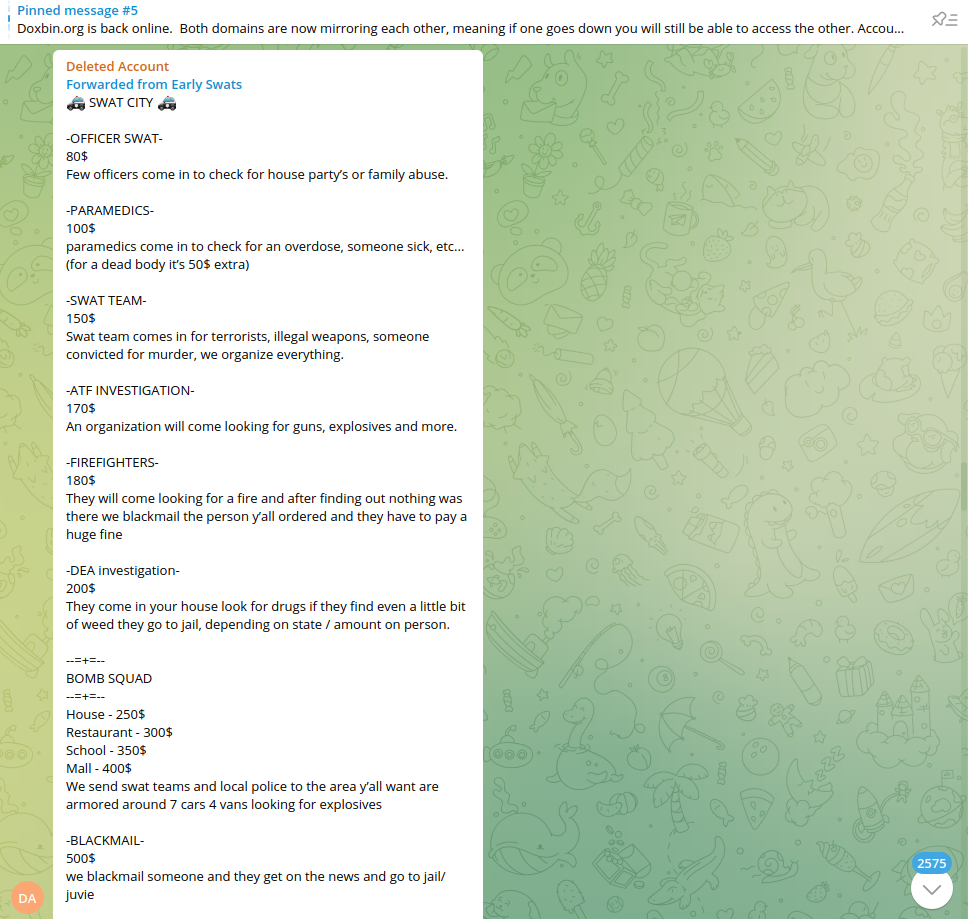
The bad actors are also offering abuse service of law enforcement agencies, technically leading to fake incidents notifications and other types of malicious activity. While some of such tactics may look primitive, unfortunately, they may generate serious damage to innocent people on practice.
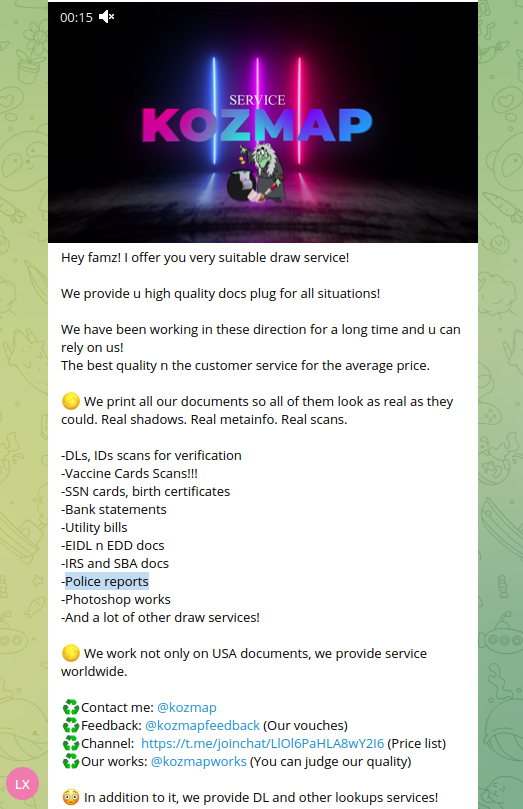
Resecurity identified multiple underground services selling police reports about individuals what allows bad actors to collect sensitive information. Such services can be widely used by foreign intelligence and organized crime to target individuals and organizations of interest.
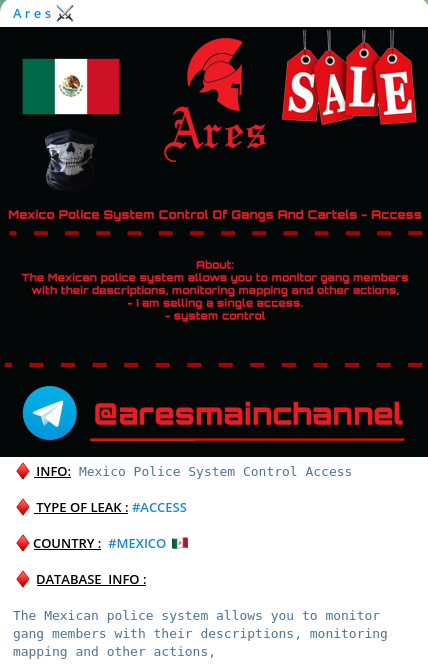
Bad actors have recently breached a law enforcement database in Mexico. The database belongs to the Mexican Police, and it's being sold in the Dark Web by threat actors who claim access to data such as gang members, action mapping, systems control and more is accessible. The bad actors states "The Mexican police system allows you to monitor gang member with their descriptions, monitoring mapping and other actions, - I am selling a single access. – System control".
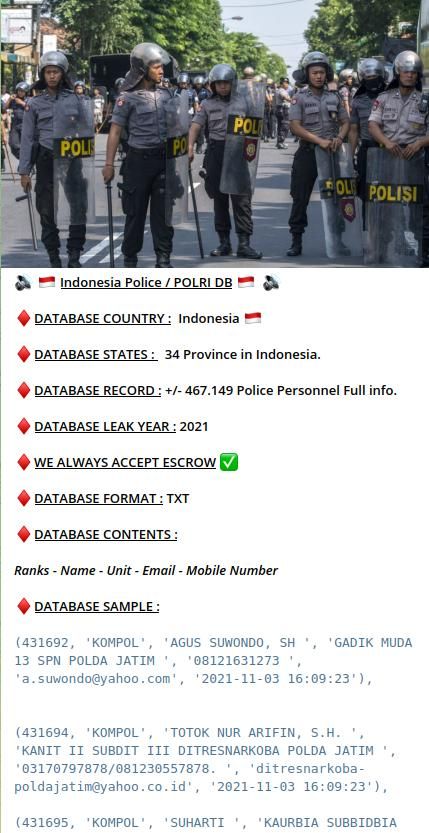
Indonesia Police / POLRI DB
DATABASE COUNTRY : Indonesia
DATABASE STATES: 34 Province in Indonesia.
DATABASE RECORD : +/- 467.149 Police Personnel Full info.
DATABASE LEAK YEAR: 2021
WE ALWAYS ACCEPT ESCROW
DATABASE FORMAT: TXT
DATABASE CONTENTS:
Ranks - Name - Unit - Email - Mobile Number
DATABASE SAMPLE:
(431692, 'KOMPOL', AGUS SUWONDO, SH', 'GADIK MUDA 13 SPN POLDA JATIM , 08121631273, 'a.suwondo@yahoo.com', '2021-11-03 16:09:23'),
(431694, "KOMPOL', 'TOTOK NUR ARIFIN, S.H. KANIT II SUBDIT III DITRESNARKOBA POLDA JATIM '03170797878/081230557878. ', 'ditresnarkobapoldajatim@yahoo.co.id', '2021-11-03 16:09:23'),
(431695, 'KOMPOL', SUHARTI, KAURBIA SUBBIDBIA
Resecurity® is committed to protecting consumers and enterprises all over the globe, and is actively involved in public-private partnerships to share actionable cyber threat intelligence (CTI) with financial institutions, technology companies and law enforcement to ultimately minimize the risk of credentials being compromised and data breaches being executed.

