
Intro
The supply-chain cyberattack that targeted Progress Software’s MOVEit Transfer application has compromised over 963 private and public-sector organizations worldwide. The ransomware group, Cl0p, launched this attack campaign over Memorial Day weekend.
Some higher-profile victims of the hack include Maximus, Deloitte, TIAA, Ernst & Young, Shell, Deutsche Bank, PricewaterhouseCoopers, Sony, Siemens, BBC, British Airways, the U.S. Department of Energy, the U.S. Department of Agriculture, the Louisiana Office of Motor Vehicles, the Colorado Department of Health Care Policy and Financing, and other U.S. government agencies. Thus far, the personal data of over 58 million people is believed to have been exposed in this exploit campaign.
Cl0p, also known as TA505, initiated their attack around May 27. The threat group exploited a “previously unknown SQL injection vulnerability (CVE-2023-34362)” in MOVEit Transfer, a managed file transfer (MFT) solution, according to the Cybersecurity & Infrastructure Security Agency. After discovering Cl0p’s campaign, researchers identified two additional SQL injection (SQLi) flaws in MOVEit Transfer, CVE-2023-35036 and CVE-2023-35708, in June.
In July, Progress Software uncovered three additional structured-query-language vulnerabilities in various versions of the MOVEit Transfer application, bringing the total of Cl0p-related SQLi common vulnerabilities and exposures (CVEs) to six. The vulnerabilities flagged by Progress Software include CVE-2023-36934, CVE-2023-36932, and CVE-2023-36933.
- Ransomware gang Cl0p hacked Progress Software’s MOVEit Transfer MFT web application over Memorial Day weekend
- Cl0p weaponized an SQL injection zero day in MOVEit Transfer and never deployed a dedicated ransomware variant in target environments
- This supply-chain attack has compromised over 963 public and private sector organizations
- Roughly 80% of the victims are in the U.S.
- The most impacted sectors are finance, professional
services, and education, which collectively account for over 48% of
reported victims
- Cl0p is anticipated to
generate between $75 mm and $100 mm in primary ransom payouts, making
it the most significant cyberattack of all time
- Progress Software has identified five additional SQLi exploits since Cl0p’s campaign was discovered
SQLi attacks enable hackers to compromise relational databases with arbitrary data requests. Using the zero-day vulnerability in the MOVEit Transfer app, Cl0p could exfiltrate, alter, and potentially corrupt files kept in victim organizations’ MFT repositories.
MOVEit Exploit Mechanics
“Depending on the database engine being used (MySQL, Microsoft SQL Server, or Azure SQL),” noted the National Institute of Standards and Technology (NIST), an attacker using the vulnerability weaponized by Cl0p, “may be able to infer information about the structure and contents of the database, and execute SQL statements that alter or delete database elements.”
More specifically, CISA said that Cl0p infected web-facing, MOVEit Transfer apps with a web shell called LEMURLOOT, which they used to steal data from underlying MFT repositories. LEMURLOOT is a web shell purpose-built for MOVEit Transfer applications and coded in C#. Per CISA, this shell was deployed by Cl0p as a “as a method of persistence, information gathering and data stealing” in the gang’s latest cyberattack campaign.
Persistence is a common capability pursued by threat actors, enabling them to maintain long-term, stealth access to victim systems. This specific type of access is termed “persistent” because it can withstand service interruptions like system restarts, credential changes, and other IT disruptions, all while allowing attackers to maintain their foothold in the victim’s network.
In this context, the LEMURLOOT web shell “interacts with its operators by awaiting HTTP requests containing a header field,” which assigns a value “equal to the password established upon the installation of the web shell,” according to CISA. After authenticating the shell, Cl0p could inject malicious commands into vulnerable MOVEit applications, allowing them to compromise SQL databases in over 963 global organizations.
Cl0p Background
Cl0p is an advanced persistent threat (APT) and ransomware group first identified by cybersecurity researchers in 2019. At the time, Cl0p’s known TTPs included phishing, brute-forcing victim credentials, and exploiting known CVEs. This threat group was initially observed operating out of Russia and Ukraine. Cl0p is believed to be a financially motivated threat actor.
Cl0p is also known to exfiltrate the highest-value victim data before deploying their ransomware binaries. This tactic enables the gang to gain more leverage over compromised organizations in extortion negotiations. Before the MOVEit attack, Cl0p was known for the 2021 hack of the Accellion file transfer appliance (FTA) and Forta’s GoAnywhere MFT exploitation earlier this year.
This APT group has historically targeted U.S., Canada, Europe, Latin America, and Asia-Pacific organizations. Cl0p generally hunts large organizations that generate revenues of over USD 5 million annually. In the cybersecurity community, Cl0p is also recognized as one of the more pioneering and innovative APT groups, being one of the first threat actors to practice higher-pressure extortion and victim-shaming tactics.
Some negotiation strategies pioneered by Cl0p include contacting the customers and business partners of their ransomware victims and encouraging these counterparties to apply further payment pressure on victim organizations. Like other elite ransomware groups, they are also practitioners of multi-extortion attacks. Cl0p gained greater infamy for being the first ransomware gang to demand a $20 million ransom payment when they compromised German tech firm Software AG in 2020.
In June 2021, Ukrainian authorities, in cooperation with Interpol and U.S. and South Korean law enforcement agencies, announced the arrests of six individuals accused of aiding and laundering millions of dollars in cryptocurrency for Cl0p. But the gang has persisted. Cl0p has been the second-most active ransomware gang (963+ victims) this year, trailing only LockBit.
Over 90% of Cl0ps victim count this year can reportedly be attributed to the MOVEit hack. Cl0p has also claimed the top spot in terms of average ransomware payment size, pocketing $1,730,486 USD per victim payout, according to mid-year data from blockchain forensics firm Chainalysis.
Significance
Cl0p’s MOVEit exploit campaign is the most significant cyberattack to date. The MOVEit hack is a classic supply-chain attack, one of the most critical types of cyber-threats today. According to recent research, over 60% of U.S. companies were impacted by a supply-chain cyberattack last year. The Identity Theft Research Center, a non-profit provider of identity crime advice and victim assistance, found that over 1,700 entities in the U.S. were targeted in supply-chain attacks last year, compromising the personal data of more than 10 million Americans.
Since the MOVEit cyberattack started, over 963 companies around the world have either publicly announced being hacked by Cl0p or have seen their organizations listed on the ransomware group’s victim leak site. But it remains unclear how many of these organizations were compromised by the MOVEit vulnerability specifically.
More alarming, the 58-million-and-counting tally of individuals compromised by the MOVEit exploit is based on the public confirmation of just several dozen victim organizations. This suggests the broader blast radius of personally identifying information (PII) exposed by the Cl0p campaign is likely far more significant.
Given the deluge of business, employee, and customer data exposed by this hack, security researchers have voiced concerns that the MOVEit breach could be a future catalyst for a particularly tenacious business email compromise (BEC) fraud crimewave.
Assuming only 25%-30% of Cl0p’s reported victims pay the ransom being demanded by the ransom gang, this threat actor is on pace to net an aggregate bounty in the range of $75 million to $100 million, according to recent research. However, given the ease through which Cl0p can monetize non-compliant victim data in Dark Web ‘secondary markets,’ threat actors may stand to generate even more income from the MOVEit attack.
In this light, Resecurity assesses that Cl0p’s MOVEit campaign may signify a transformative event for ransomware tradecraft and one that could influence how future cyber-extortion attacks are staged. The primary theme of Cl0p’s latest crimewave is the threat actor’s execution of a ransomware attack, without ever deploying a dedicated ransomware binary or cryptolocker.
Instead, Cl0p weaponized an SQLi exploit to exfiltrate sensitive corporate data and hold it for ransom. At a high level, Cl0p’s latest cyberattack campaign thus appears to be far more efficient than their usual ransomware modus operandi. With the MOVEit zero-day, which they likely purchased from a third party, the gang bypassed all the fastidious research and development that ransom crews typically must allocate to produce a suitably persistent, evasive, and cryptographically secure malware variant.
While no victims have yet confirmed submitting a ransom payment to Cl0p, Resecurity assesses that Cl0p will likely achieve a result that surpasses even the most prolific ransomware campaigns. Cl0p will also achieve this historic payout, while having used significantly less organizational resources than in any other ransomware gang in a high-grossing ransomware campaign before them. The reasoning for this assessment is that Cl0p is unlikely to have engineered the MOVEit Transfer exploit in-house.
Resecurity believes that the exhaustive level of research, attention to detail, and code-auditing skill required to discover the SQLi flaw in MOVEit Transfer and then tailor an attack kit to exploit it are features that collectively run counter to Cl0p’s established TTPs. While innovative and effective, Cl0p’s previous ransomware campaigns have not exhibited this precision and specialization. Thus, it is more probable that the threat group purchased the MOVEit zero-day from a 0-day broker. This scenario may indicate the growing value of these actors in cybercriminal supply chains.
Latest Developments
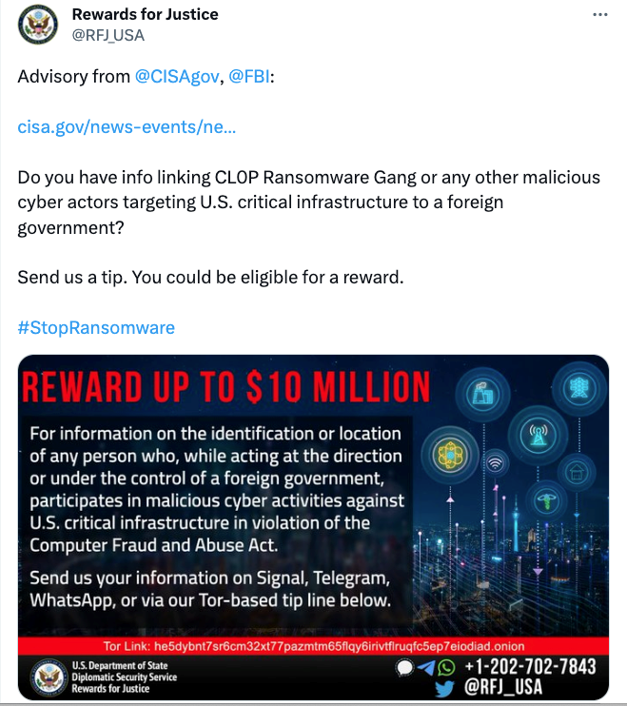
At the time of this writing, none of Cl0p’s reported victims are believed to have submitted a ransom payment. In June, the Rewards for Justice Twitter account, the official online account for the U.S. State Department Rewards for Justice Program, responded to the Cl0p zero-day campaign by offering a $10-million bounty for information about the gang. This is the same sum the RFJ program offered for the Conti ransomware gang last August.
On July 6, Progress Software disclosed that white-hat cybersecurity researchers had discovered three additional SQLi vulnerabilities in its MOVEit Transfer software. While CVE-2023-36934 has been designated as “critical,” CVE-2023-36932 and CVE-2023-36933 have been classified as “high” by the software manufacturer.
Nearly 75% of individuals compromised by the MOVEit hack so far can be attributed to just nine victim organizations. The most impacted entities in terms of PII exposure are government contractor Maximus (11 million), Louisiana Office of Motor Vehicles (6 million), Colorado Department of Health Care Policy and Financing (4 million), Oregon Department of Transportation (3.5 million), and TIAA (2.6 million).
In July, a letter from Pension Benefit Information, LLC surfaced online, indicating that Fidelity Investments had its data compromised by the global MOVEit exploit campaign “that impacted PBI.”
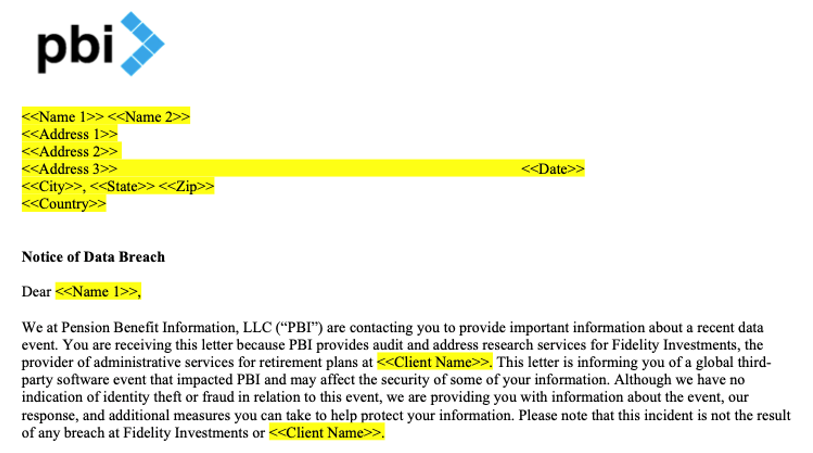
The compromise of Fidelity Investments data brings the total number of entities impacted by the PBI breach to nine. Other high-profile entities impacted by the attack on PBI’s MOVEit stack include pension funds TIAA, CalPERS, and CalSTRS.
The Cl0p spokesperson’s commentary on their ransom discussions with investment firm TD Ameritrade on July 10 highlights the group's antisocial pathology and brazen negotiating style.
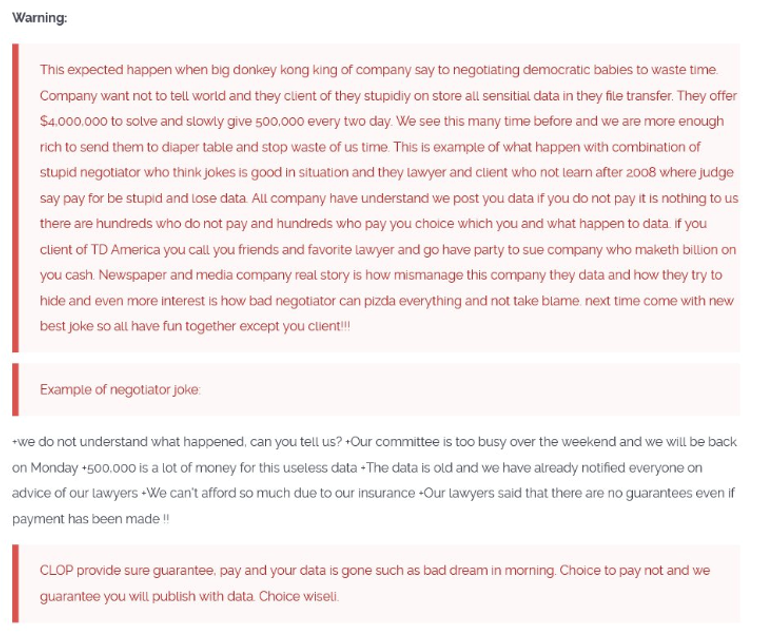
In this thread, Cl0p refers to the victim organization as a “big donkey kong.” Also, the gang showcases one of the high-pressure negotiation techniques they pioneered, as they urge TD Ameritrade clients to “call you[sic] friends and favorite lawyer and go have a party to sue company who maketh[sic] billions on you[sic] cash.”
Cl0p eventually published some of TD Ameritrade’s “SECRET INFORMATION FILES,” along with portions of PWC, K&L Gates, United Bank, and Cadence Bank data on their dark web leak site.
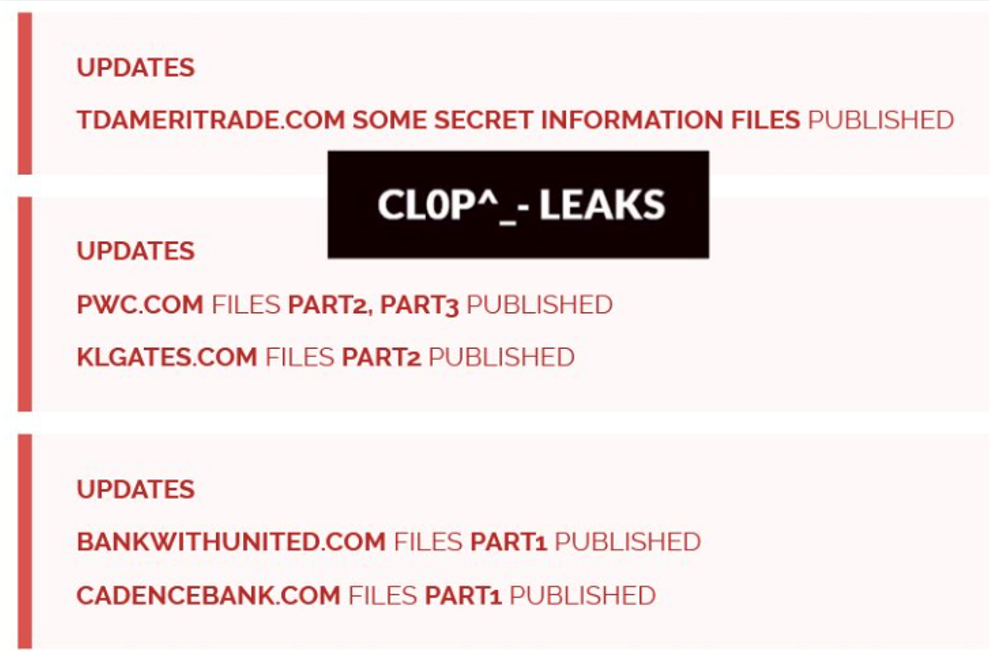
Concurrently, ING Bank confirmed to CyberNews that some of their customer data was impacted by the MOVEit hack. But the bank stressed that their customer data was compromised via an attack initially stage on a Luxembourg-based, account-switching service provider, only affecting a customer count numbering in the low thousands.
Majorel, the primary victim in the ING breach, was also the source of the compromise that impacted customer data for Deutsche Bank, Postbank, and Comdirect, according to CyberNews reporting. Another point worth raising is the publication of K&L Gates data, as it is one of three major U.S. law firms that Cl0p claimed as victims during this attack cycle. The other legal victims include Kirkland & Ellis and Proskauer Rose.
Frustrated with the state of their negotiations with victims, Cl0p even created clearweb leak sites for PwC, EY, Aon, and other firms. Most recently, Cl0p announced on their leak site that they had compromised the consulting firm, Deloitte. This means the gang compromised data belonging to three of the ‘big four’ consulting firms.
Delayed by slow clear-web download speeds, Cl0p pivoted to releasing data via torrents to enable faster peer-to-peer transfer. Cl0p has created torrents for over 20 victims, including Aon, K & L Gates, Putnam, Delaware Life, and Zurich Brazil.
On August 10, Cl0p threatened to leak the data of victim organizations that neglected to contact them. “YOU NOT HIDING MORE,” concluded the menacing note
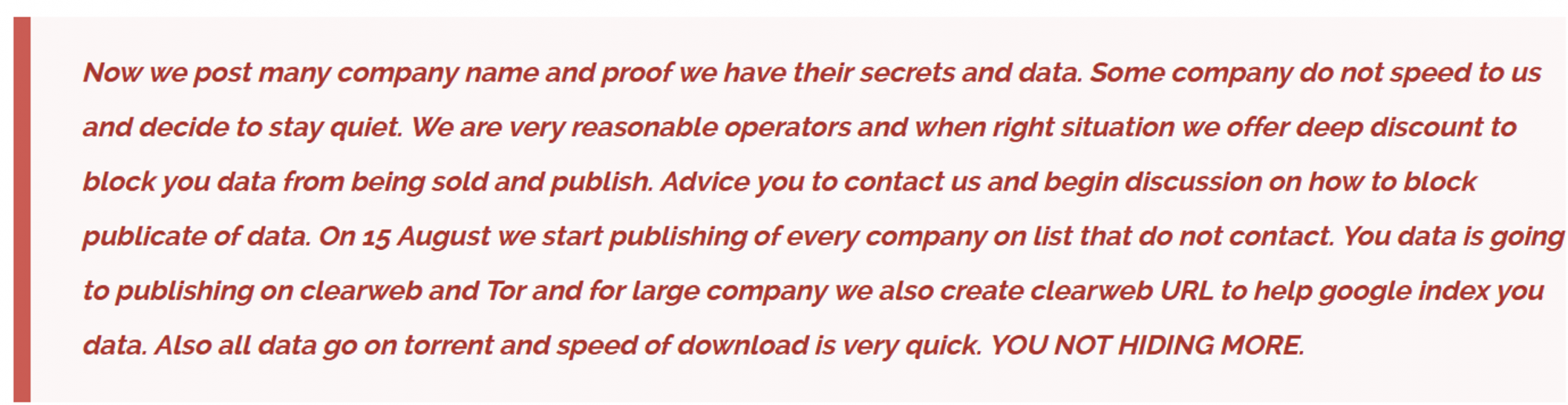
On August 14 and 15, Cl0p made good on their threat. The group released clear-web torrents for 16 more companies, exposing over 947 gigabytes of victim data to the public.

Some of the more notable victims of this data dump include UCLA, Siemens Energy, Norton Lifelock, Cognizant, and Netscout. There are also numerous financial institutions (FIs) included in the torrent dump.
Key Takeaways
This Cl0p cyberattack campaign is particularly alarming due to the number of major FIs, law firms, and professional services firms impacted by the MOVEit exploit. The reason for this concern is that these organizational targets typically handle and store significantly higher-value data than the average enterprise.
As fallout from Cl0p’s latest cybercrime offensive continues, organizations must be attuned to supply-chain risks. Enterprises and public institutions must also regularly update and patch their software applications, while continuously evaluating critical IT stacks for potential vulnerabilities.
A critical lesson from the MOVEit exploit campaign is that outdated enterprise technology stacks can be a significant vulnerability for organizations. To improve cybersecurity, organizations can seek professional assessments of their technical debt exposures and take measures to mitigate the risks of ransomware and supply-chain exploits.
At Resecurity, we offer a variety of products and services to help companies protect their business, staff, and clients. We aim to improve security measures and provide in-depth insights into present and future threats. This helps companies prioritize their defenses and prevent attackers from accessing their networks and data.

