Ransomware Attacks against the Energy Sector on the rise - Nuclear and Oil & Gas are Major Targets in 2024
Cyber Threat Intelligence


Resecurity has identified an alarming rise in ransomware operators targeting the energy sector, including nuclear facilities and related research entities. Over the last year, ransomware attackers have targeted energy installations in North America, Asia, and the European Union. In the EU, Handelsblatt reported that ransomware attacks targeting the energy sector more than doubled in 2022 over the previous year, with defenders recording 21 attacks through the past October.
After a brief, sectoral ‘cease-fire’ following the 2021 Colonial Pipeline ransomware attack, cybercriminals are once again homing in on energy-industry targets. Threat actors reason that the seizure of the higher-value Critical Infrastructure (CI) assets handled by these firms will yield more lucrative payouts in ransom negotiations. Factors that make energy firms more vulnerable to ransomware attacks include complexities in converging IT and operational technology (OT) networks, third-party risks, and historic geopolitical fragmentation.
Backdropped by the conflicts in Ukraine and Gaza, Resecurity has also observed suspected cases of state-sponsored espionage activity masquerading as financially motivated ransomware attacks. While Israeli entities have not yet reported any meaningful ransomware attacks, the eruption of war in Gaza in October has fomented a concurrent rise in threat actor activity targeting Israeli energy installations. This activity includes propaganda-oriented hacktivist campaigns, along with more serious threat actors like Storm-1133, a group initially flagged by Microsoft threat researchers.
Resecurity’s research delves deeper into unique ransomware trends cited by the Department of Homeland Security in their recently published Intelligence Enterprise Homeland Threat Assessment. “Between January 2020 and December 2022, the number of known ransomware attacks in the United States increased by 47 percent,” according to the DHS report. The agency also noted that "ransomware attackers extorted at least $449.1 million globally during the first half of 2023 and are expected to have their second most profitable year.”
In the wake of the MOVEit Transfer supply-chain extortion campaign, which has claimed over 2,180 victims so far, 2023 may actually go down in history as the most profitable year ever for ransomware actors. The broader trend driving the ransomware industry’s increasing ROI is the return of “big game hunting,” or the targeting of large organizations, according to the DHS report. Emerging tactics being deployed by ransomware actors in their big-game, extortion ‘safaris' include intermittent encryption, the use of more modern specialized programming languages, and dual ransomware attacks that involve more than one variant.
These dual-variant campaigns typically sequence their attacks over a span of 48 hours, according to the FBI. As Cl0p demonstrated in their MOVEit campaign, there is also rising concern that attackers may be eschewing the in-house development of encryption lockers altogether, in favor of more efficient data theft schemes. By quickly seizing and exfiltrating data, ransomware actors can pivot into the extortion phase of the attack cycle more immediately. Regarding the first two emerging ransomware tactics cited, intermittent encryption enables threat actors to “encrypt systems faster and reduce the chances of being detected,” according to the DHS report.
The enhanced efficiency and evasiveness offered by the above technique are selling points that can help cyber-extortion gangs “entice affiliates to join their Ransomware‑as‑a‑Service operations,” noted the DHS report. The report also said that next-generation programming languages like Rust and Golang, for example, can enhance threat actors’ abilities to “adapt and individualize their attacks.”
Overall, the energy sector was the fourth-most-targeted sector last year, accounting for 10.7% of all cyberattacks. The DHS report warned that "state and non-state cyber actors continue to seek opportunistic access to critical infrastructure sector targets for disruptive and destructive attacks.” Additionally, “malicious cyber activity targeting the United States has increased since the beginning of the Russia‑Ukraine conflict,” noted the DHS report.
With no clear ends to the Israeli-Hamas and Russo-Ukrainian conflicts in sight, Ransomware attacks targeting energy firms are becoming increasingly prevalent in the U.S. and globally. The following white paper will provide a timeline of all significant, energy-sector ransomware attacks over the last year, present HUNTER (HUMINT) research on Dark Web solicitations for energy sector access, and detail findings from our undercover ransom negotiations with threat actor group Black Basta.
Key Takeaways
- Resecurity has identified several Initial Access Brokers (IABs) operating on the Dark Web who are actively seeking out credentials and other unauthorized intrusion methods for the energy sector. Some of these IABs are even promoting unauthorized access to nuclear energy firms. Furthermore, Resecurity has identified numerous posts on major cybercriminal forums, including RAMP (the Russian Anonymous Market Place), where threat actors have profited and continue to profit from illegal network access.
- Per Resecurity investigations, ransomware attacks on the energy sector have significantly increased. Malicious campaigns have been observed in North America, Asia, and the European Union (EU). Cybercriminals target this sector, operating on the assumption that they can command more lucrative ransom payments due to the higher-value data assets involved. These attacks prove that critical infrastructure (CI) data assets are more valuable to ransomware groups than those stored by other economic sectors.
- Resecurity anticipates that criminal entities operating on the Dark Web and professional ransomware gangs will intensify their targeting of the energy industry. These attackers will co-opt independent actors and IABs to help them profit from illicit network intrusions.
- Ransomware operators targeting energy firms will continue to increase their extortion demands beyond $7 million, weaponizing their essentiality to CI operations. One aggravating factor that can justify payouts of this size to victim organizations is the potential for the devastating disruption of industrial processes within their surrounding environment.
- Nuclear energy organizations are high-priority targets for ransomware operators and advanced threat groups seeking to participate in cyber espionage. Leaked data from these entities may serve as a smokescreen for more intricate attacks, planned before any public announcement of these incidents. This tradecraft can make it more challenging for breach investigators to determine the true motives behind a cyberattack.
- Governments and private-sector stakeholders are increasingly concerned about the rise in ransomware attacks targeting the energy sector. This disturbing trend has destabilizing implications for geopolitical relations, capital markets, public safety, and national security.
Analysis of Ransomware Attacks Targeting the Energy Sector (2022-2023)
After analyzing ransomware incidents that impacted the energy sector over the past year, Resecurity has found that extortion demands can vary from tens of thousands to millions of dollars. In the following chart, we have detailed several high-profile attacks on energy firms, with attributions to their corresponding perpetrators.
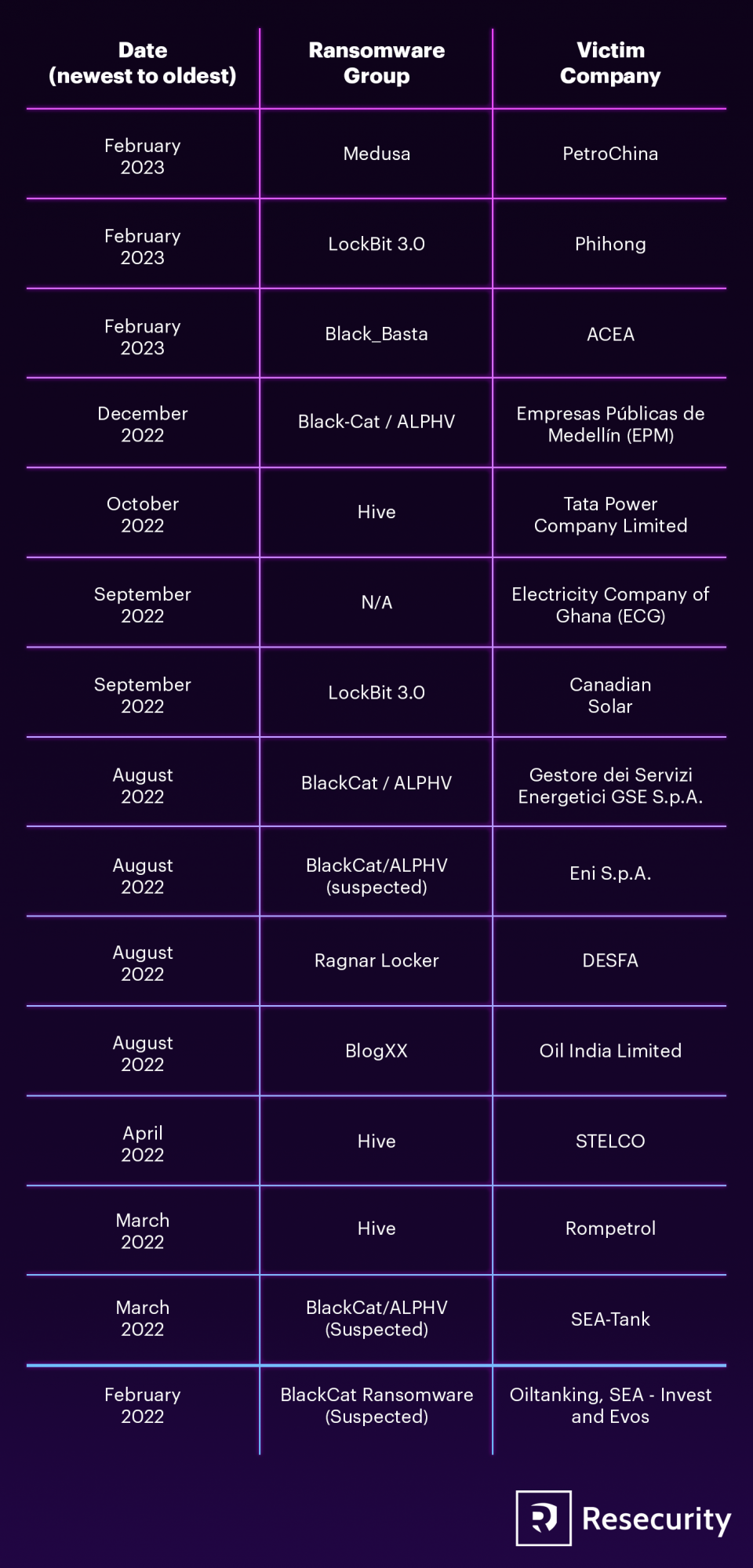
In the context of the Ukraine war, the most geopolitically noteworthy attacks include the steady stream of intrusions by actors like BlackCat/ALPHV, Qilin, and Black Basta targeting energy installations and refining hubs in the Low Countries, Switzerland, Italy and Germany. Germany, once the engine of the European economy, has been particularly hard hit by the transition away from Russian natural gas imports that has resulted from war-related sanctions.
As such, Germany’s energy infrastructure has been especially vulnerable. In this regard, ALPHV’s coordinated attacks on Oiltanking in Germany, Invest-SEA in Belgium, Evos in the Netherlands, and the Amsterdam-Rotterdam-Antwerp oil terminals all in February 2022 are particularly noteworthy. These attacks all immediately coincided with Russian invasion of Ukraine.
It goes without saying that ALPHV, a trail blazer in modern-language-coded ransomware, is considered a Russian-nexus threat group. In the context of Germany, Quilin’s attack on Thornburi Energy Storage Systems (TESM), a Bangkok-based plug-in battery manufacturer, is also significant. Despite being a Thai firm, TESM is a key partner of German auto manufacturer Mercedes-Benz AG, with the latter recently investing €100 million in the battery maker.
As for other energy-related attacks in the EU, ALPHV’s and Black Basta’s attacks on Italian public utilities like Acea the country’s national energy agency, Gestore dei Servizi Energetici S.p.A. (GSE), and multinational oil firm Eni S.p.A. are also significant. These attacks all occurred two months before the Italian general election in 2022, which came earlier than scheduled, to the collapse of former Prime Minister Mario Draghi’s government.
A widely contentious issue leading up to the eventual election of current Prime Minister Girogia Meloni was support for the Ukrainian struggle against Russia. Apart from ransomware attacks, Cl0p’s Memorial Day supply-chain attack campaign compromised at least 2,180 victims, including British multinational oil firm Shell plc, German industrial heating pump manufacturer Siemens AG, and French energy company Schneider Electric, and the U.S. Department of Energy.
Another interesting development noted by HUNTER analysts is the uptick in attacks targeting the Indonesian energy sector this year. This trend is noteworthy given that the country’s presidential election is scheduled for 2024. Russian-nexus groups like Medusa and ALPHV have claimed credit for attacks targeting Indonesian energy firms.
One last development HUNTER analysts noted was the growing alliance between hacktivist groups and ransomware operators, specifically the recently announced alliance between GhostSec and Stormous, respectively.The GhostSec-Stormous alliance has vowed to prioritize attacks on U.S., Ukrainian, Indian, Peruvian, and Vietnamese targets. In July, the duo announced the compromise of data belonging to Cuban Ministry of Energy and Mines.
Date (newest to oldest) |
Ransomware Group |
Victim Company |
Summary |
February, 2023 |
Medusa |
PetroChina |
On February 15, 2023, threat actor group Medusa claimed to have stolen data from PetroChina Indionesia. The hacker group posted some brief information about the oil & gas company on their Dark Web blog and demanded a ransom to delete the victim’s data. Medusa initially gave PetroChina a deadline of seven days and a few hours to respond to the demand. But Medusa extended the deadline for a fee of $10,000/day. Medusa also demanded $400,000 from the victim to prevent Medusa from leaking, and another $400,000 for them to recover it. The group also threatened to sell the data to third parties if their demands were not met. |
February, 2023 |
LockBit 3.0 |
Phihong |
Ransomware gang Lockbit 3.0, claimed credit for hacking Taiwanese battery manufacturer Phihong on their Dark Web blog. The gang claimed that if Phihong did not pay them by February 19, they would release their stolen data online. Phihong is a company that manufactures power supplies and chargers for electronic equipment and electric vehicles. They have clients worldwide and had recently signed a major deal with Shell to supply EV chargers. |
February, 2023 |
Black_Basta |
ACEA |
On February 2, 2023, Black Basta conducted a ransomware attack on Acea, an Italian company that provides waste management, electricity, and water services to the city of Rome. As a result, the company’s official website was mostly unavailable until the next day because incident responders had to implement damage-control measures. |
December, 2022 |
Black-Cat / ALPHV |
Empresas Públicas de Medellín (EPM) |
On December 16, 2022, BlackCat/ALPHV launched a ransomware attack against Empresas Públicas de Medellín (EPM), a Colombian energy company. |
October, 2022 |
Hive |
Tata Power Company Limited |
On October 2022, Tata Power, India’s largest integrated power company and a subsidiary of Tata Group, reported a cyberattack. The Hive ransomware group claimed responsibility for the attack. Data stolen from Tata Power included the personally identifiable information of their employees, |
September, 2022 |
N/A |
Electricity Company of Ghana (ECG) |
The ECG project site near Kwame Nkrumah Circle in Accra experienced ransomware-related disruptions in certain areas. The unidentified hackers altered the source code and gained control over parts of the ECG’s server. Threat actors also encrypted parts of the ECG system, causing it to malfunction. |
September, 2022 |
LockBit 3.0 |
Canadian Solar |
On September 11, 2022, LockBit 3.0 claimed credit for a ransomware attack on Canadian Solar, a manufacturer of solar photovoltaic (PV) modules. LockBit hackers demanded a ransom payment from the company and set a deadline of September 13, 2022. They also offered 24-hour deadline extensions at a cost of $10,000 per day. The attackers threatened to destroy the victim company’s data for a price of around $20,000 and charged an additional $20,000 to download the ransomed data. LockBit affiliates threatened to publish the stolen data on the Dark Web in the even the Canadian Solar declined to pay the ransom. |
August, 2022 |
BlackCat/ALPHV |
Gestore dei Servizi Energetici GSE S.p.A. |
In August 2022, the BlackCat/ALPHV ransomware gang successfully compromised Italy’s national energy agency, Gestore dei Servizi Energetici S.p.A. (GSE). |
August, 2022 |
BlackCat/ALPHV (suspected) |
Eni S.p.A. |
In August 2022, Italian multinational oil company Eni S.p.A disclosed a cyberattack on its computer networks. The attempted ransomware attack only caused minor damage to affected systems. The company’s internal systems identified unauthorized network activity in the days before the attack. |
August, 2022 |
Ragnar Locker |
DESFA |
On August 21, 2022, DESFA, the biggest natural gas distributor in Greece, announced that they experienced a data breach and IT system outage due to a cyberattack. Despite the hackers’ attempts to infiltrate DESFA's network, the company’s IT team was able to act swiftly and prevent a complete takeover of their systems by threat actors. However, threat actors were able to access and leak some data, indicating a limited network intrusion. Ragnar Locker claimed responsibility for the attack. |
April, 2022 |
BlogXX |
Oil India Limited |
In April 2022, Oil India Limited (OIL) was hit by a ransomware attack that caused serious operational disruptions in Assam. BlogXX, an offshoot of REvil claimed credit for this attack on their Tor DLS. In the police report, OIL stated that they received an email from the hackers demanding a ransom of $7,500,000 USD to restore their data. After investigating the attack, incident responders concluded that OIL’s network, server, and client PCs were all impacted by the network disruption. Due to the cyberattack’s impact on the IT systems, both OIL and the Indian government exchequer suffered significant financial losses. |
March, 2022 |
Hive |
STELCO |
In March 2022, State Electric Company Limited (STELCO), an electric utility company in Malé, Maldives, experienced a ransomware attack that affected several of their online services. The Hive ransomware group claimed credit for the attack. STELCO confirmed that they discovered the attack on March 24th, 2022, as their customer-facing operations were knocked offline. |
March, 2022 |
Hive |
Rompetrol |
In March 2022, Hive also compromised the Rompetrol gas station network in Romania. At the time, Rompetrol, a subsidiary of KMG International, stated that it was facing a “complex cyberattack” that led to the closure of its websites and the Fill&Go service at gas stations. The Hive demanded a multi-million-dollar ransom payout. Additionally, the threat actor gained access to the internal IT network of the Petromidia Navodari refinery. However, Rompetrol assured the public that operations at the Petromidia Navodari refinery were not affected. |
February, 2022 |
BlackCat/ALPHV (Suspected) |
SEA-Tank |
In February 2022, oil loading facilities at key terminals in the Amsterdam-Rotterdam-Antwerp (ARA) refining hub suffered a significant ransomware attack. This attack resulted in operational disruptions and energy delivery delays. The attack impacted six terminals owned by various companies in Belgium and the Netherlands, compromising loading operations for multiple affected systems. The attackers demanded a ransom of €10 million to restore the systems, but it is uncertain if any of the companies paid. This cyber-assault was one of the most severe attacks the European energy sector ever experienced, resulting in significant financial losses. |
February, 2022 |
BlackCat Ransomware (Suspected) |
Oiltanking, SEA-Invest and Evos |
In February 2022, several oil storage and transport terminals worldwide—including Oiltanking in Germany, SEA-Invest in Belgium, and Evos in the Netherlands—experienced IT system disruptions. The total number of affected terminals was in the dozens. |
Nuclear Energy Firms Are Becoming Priority Targets
Backdropped by the Russo-Ukrainian conflict, threat actor interest in nuclear-energy firms and related entities has been on the rise. This past January, Reuters reported that a Russian advanced persistent threat (APT) group dubbed ‘Cold River’ by researchers “targeted three nuclear research laboratories in the United States” in the Summer of 2022. This malicious campaign occurred between August and September of last year.
“Cold River targeted the Brookhaven (BNL), Argonne (ANL) and Lawrence Livermore National Laboratories (LLNL), according to internet records that showed the hackers creating fake login pages for each institution and emailing nuclear scientists in a bid to make them reveal their passwords,” reported Reuters.
In this threat environment, Resecurity has noticed growing interest from threat actors soliciting access to nuclear-sector entities. The following images are screenshots of posts Resecurity investigators captured from various cybercrime forums. Specifically, HUNTER analysts mined threat intelligence from RAMP, XSS, Exploit, Breach Forums, and various Telegram channels.
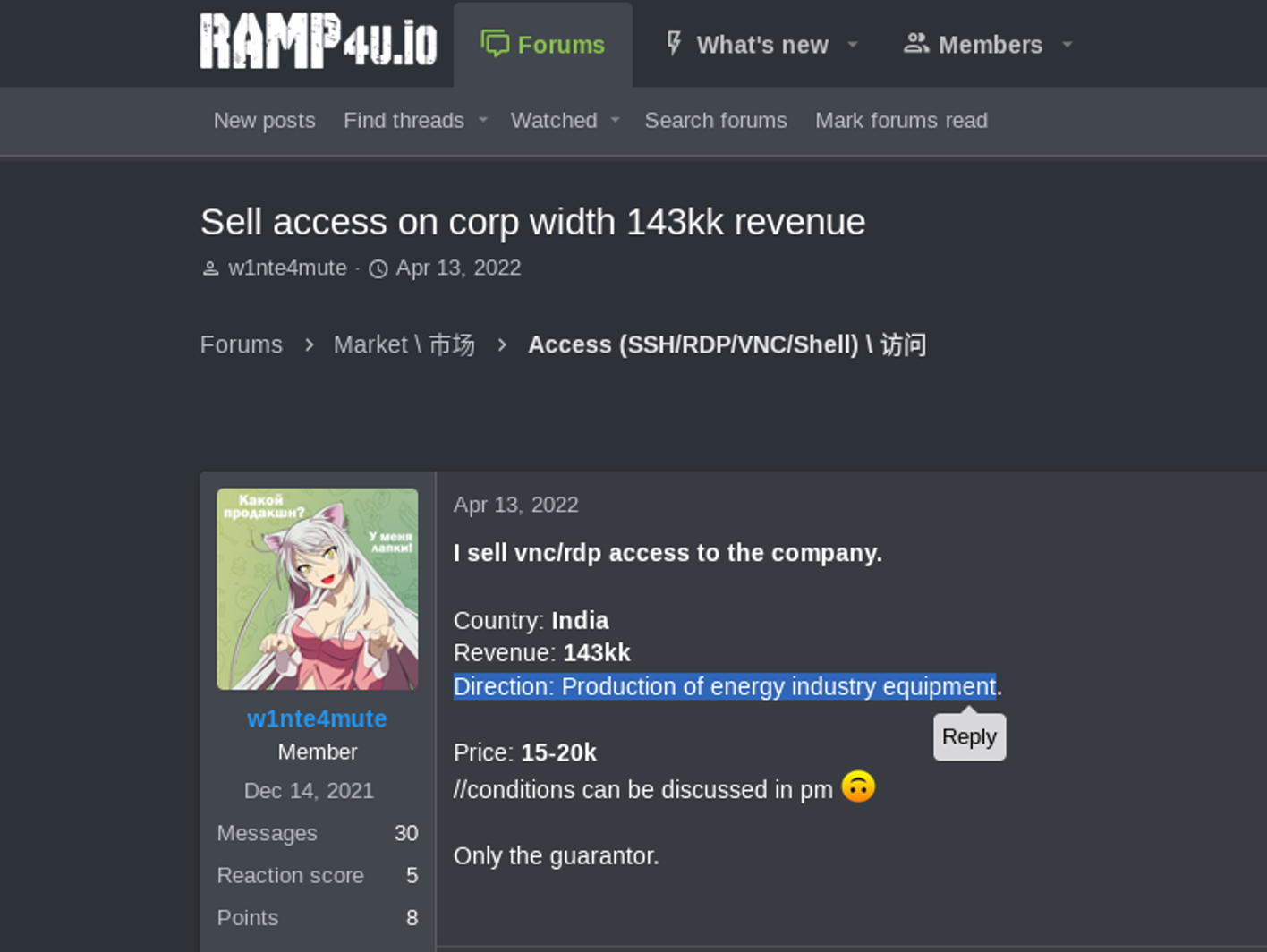
As far as publicly accessible nuclear access listings, Breach Forums proved to be the most fertile hub for open-source intelligence in this regard. The images below depict examples of Initial Access Brokers (IABs) offering access to nuclear energy-sector corporate networks. This first screencap is from the RAMP forum.
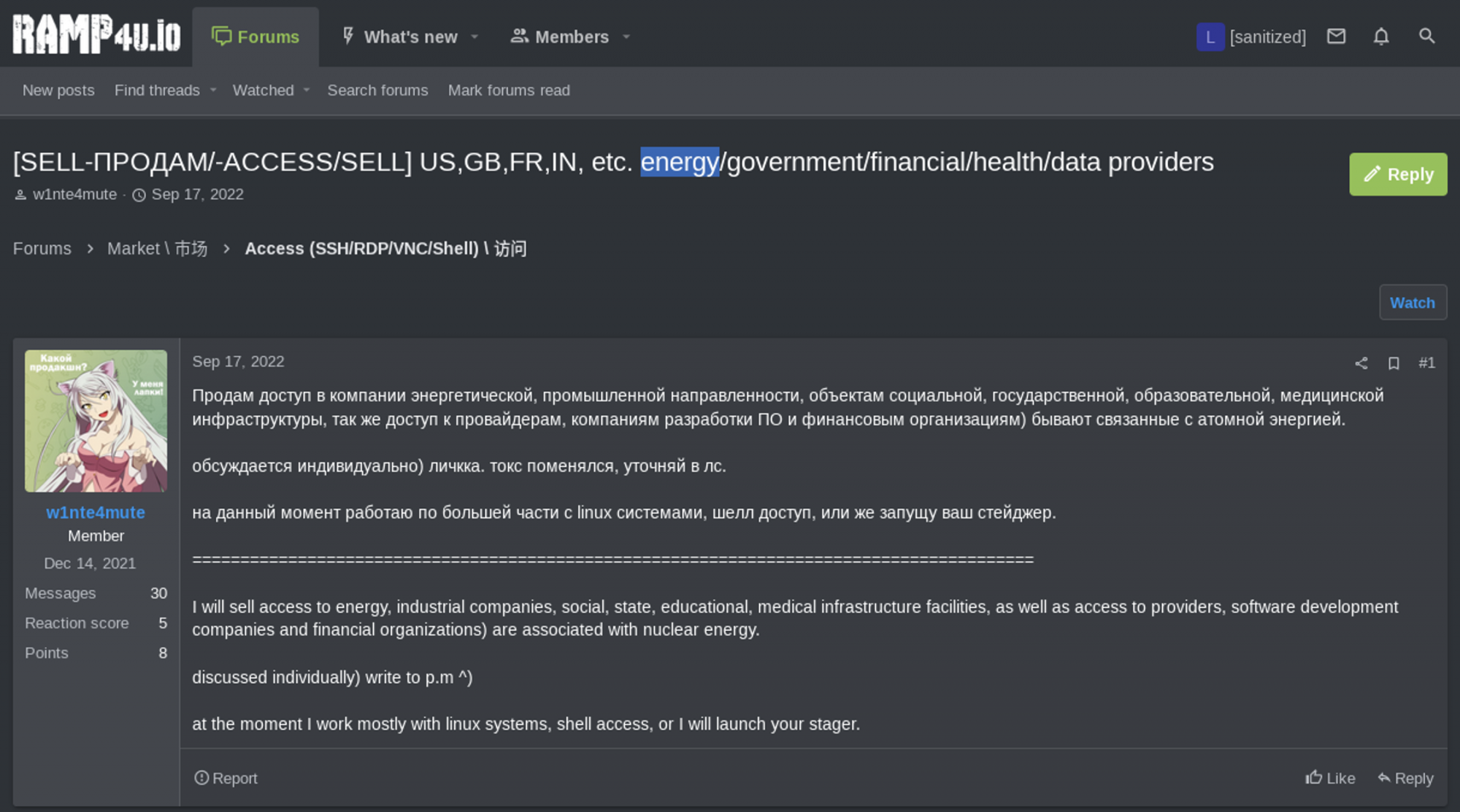
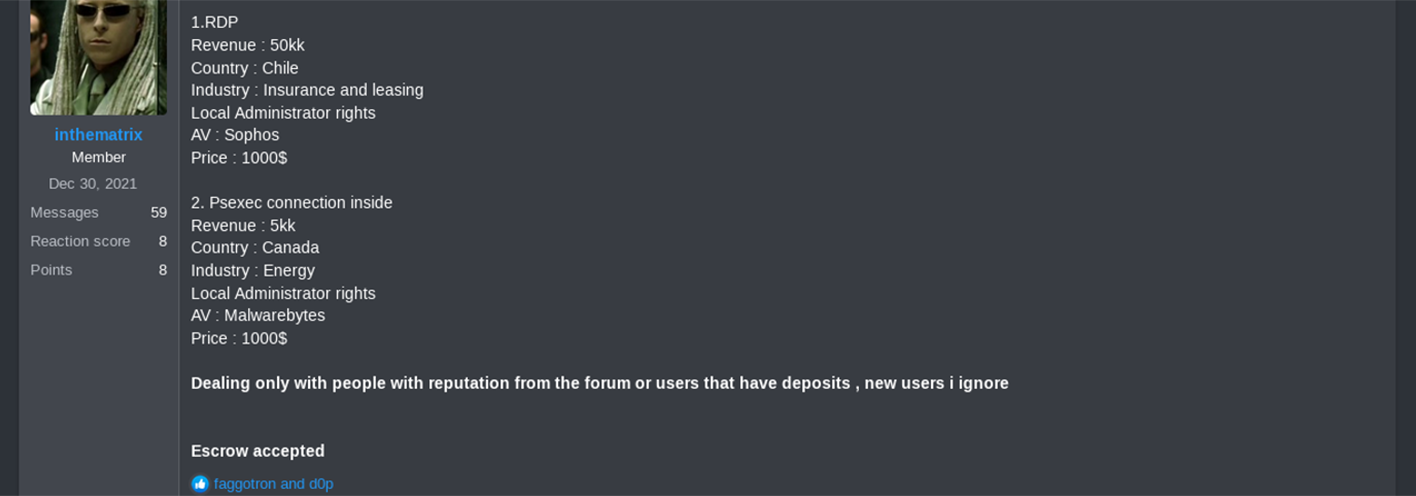
RAMP
In the Ramp post from December 2021 below, threat actor ‘W1nte4mute’ solicits access to energy provider networks, including those that “are associated with nuclear energy."
Resecurity analysts identified similar offerings on the XSS and Exploit cybercriminal forums.
XSS/Exploit
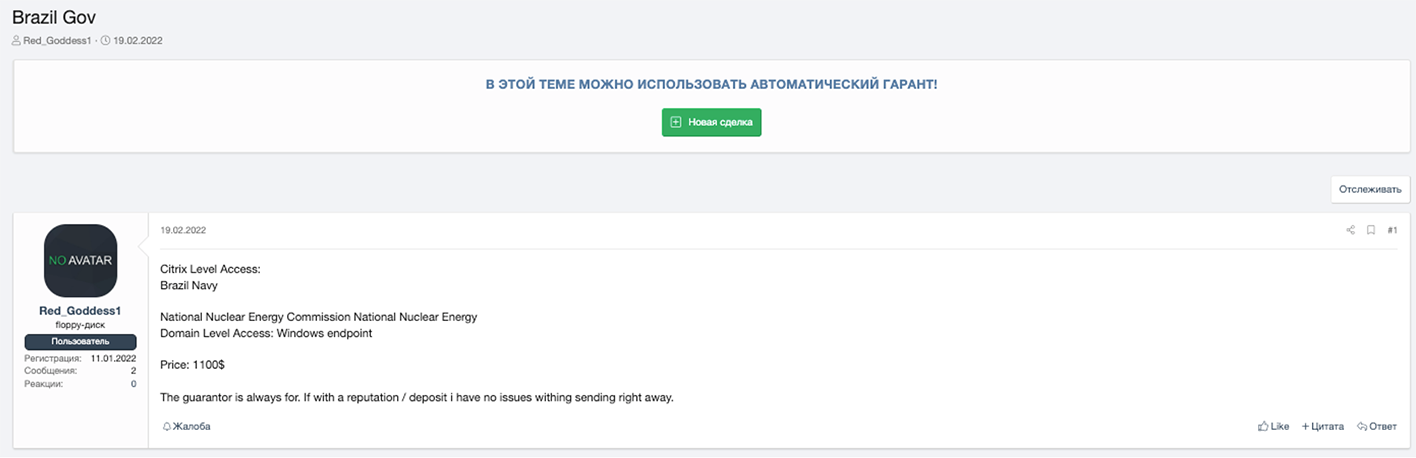
In the below XSS and Exploit forum posts from February of last year, a threat actor Resecurity presumes to be the same individual solicits domain-level access to Brazil’s “National Nuclear Energy Commission National Nuclear Energy” for $1,100. On XSS, the threat actor selling this access goes by the handle ‘Red_Goddess1.’
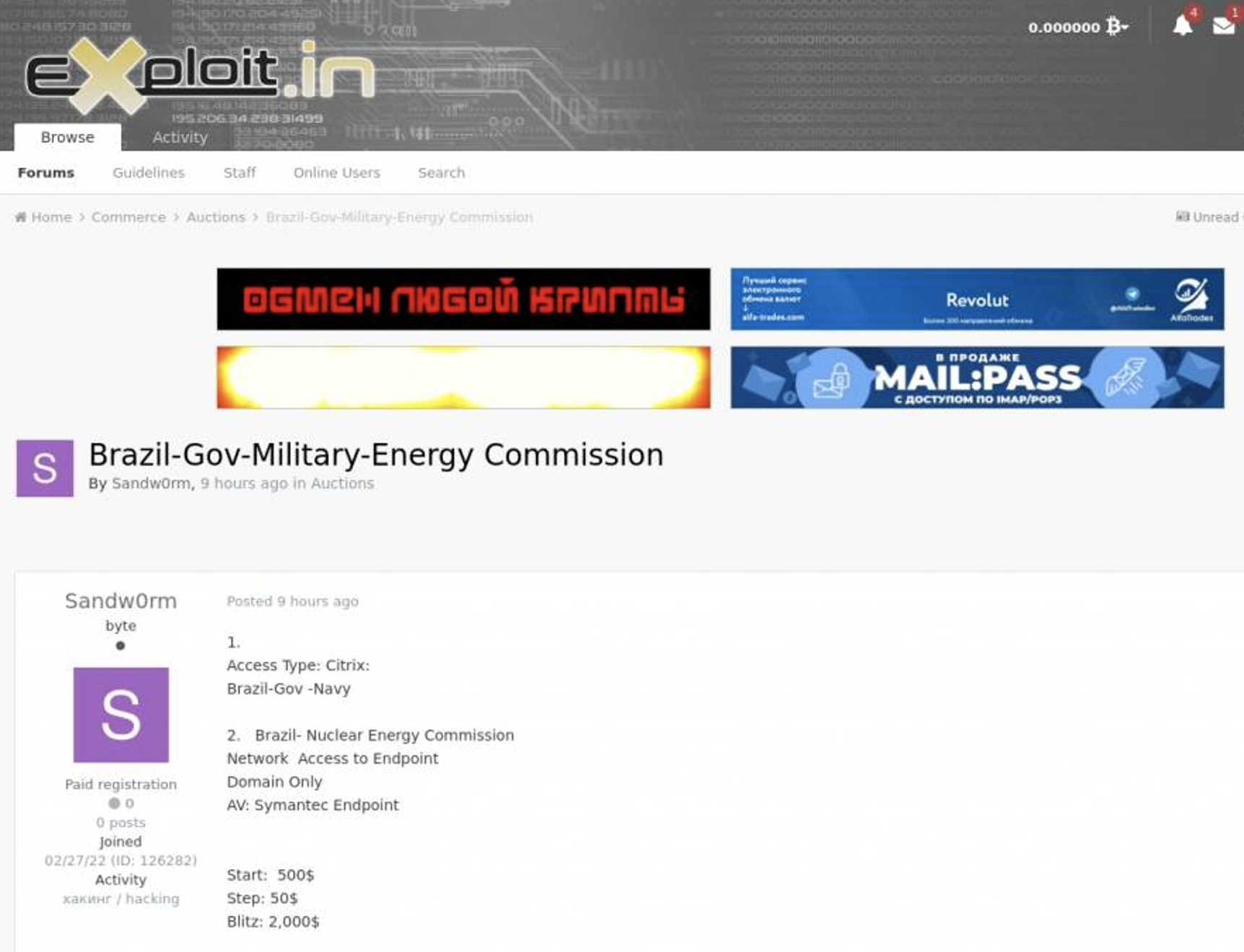
Around the same time, a threat actor using the handle, ‘Sandw0rm,’ who just registered this Exploit.in forum account a week after the initial XSS posting, solicits the same access to Brazil’s NNEC at a starting price of $500, or less than half of the original asking amount. It’s also worth noting that this threat actor probably has no relation with the real Sandworm (nation-state APT group also known as Voodoo Bear), given the relatively low asking price for this access.
Breach Forums
In the below Breach Forums post from August 12, 2023, threat actor ‘WAIL_CRINAL’ solicits access to a database belonging to Israel’s Neve Ne’eman nuclear reactor for the relatively low price of $900. ‘WAIL CRINAL’ claims that this dataset includes: full names with all information about Officials and professors with their residence addresses; 10 GB of confidential documents, including components and materials used in experiments; dimensions, levels and locations of the reactors; emails and ips and passwords for login (ssh smtp servers).
Indonesia’s National Nuclear Energy Agency (Batan)
In March 2023, threat actors leaked data 1.4 GB of data stolen from the National Nuclear Energy Agency of Indonesia (Batan) on Breach Forums. The motive behind this attack may have been hacktivism to protest the Indonesian government and law enforcement during a time of widespread unrest over fuel prices.
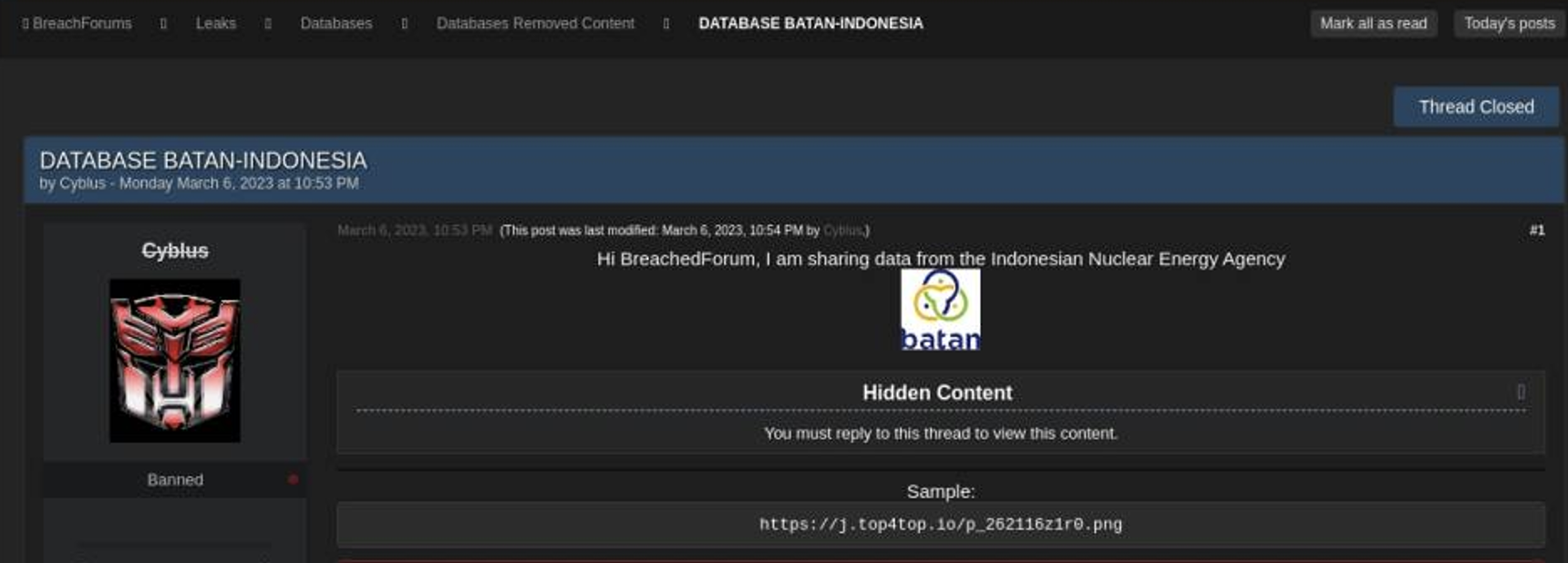
Some advanced cyber-espionage groups intentionally disguise their actions to appear like typical cyber criminals or hacktivists. The 1.4 GB of Batan data was recently re-published on the Telegram channel of “A.I.G.” short for the Atlas Intelligence Group, AKA the Atlantis Cyberarmy. This group offers a variety of illegal services, like distributed denial of service attacks (DDoS) and access to stolen data.
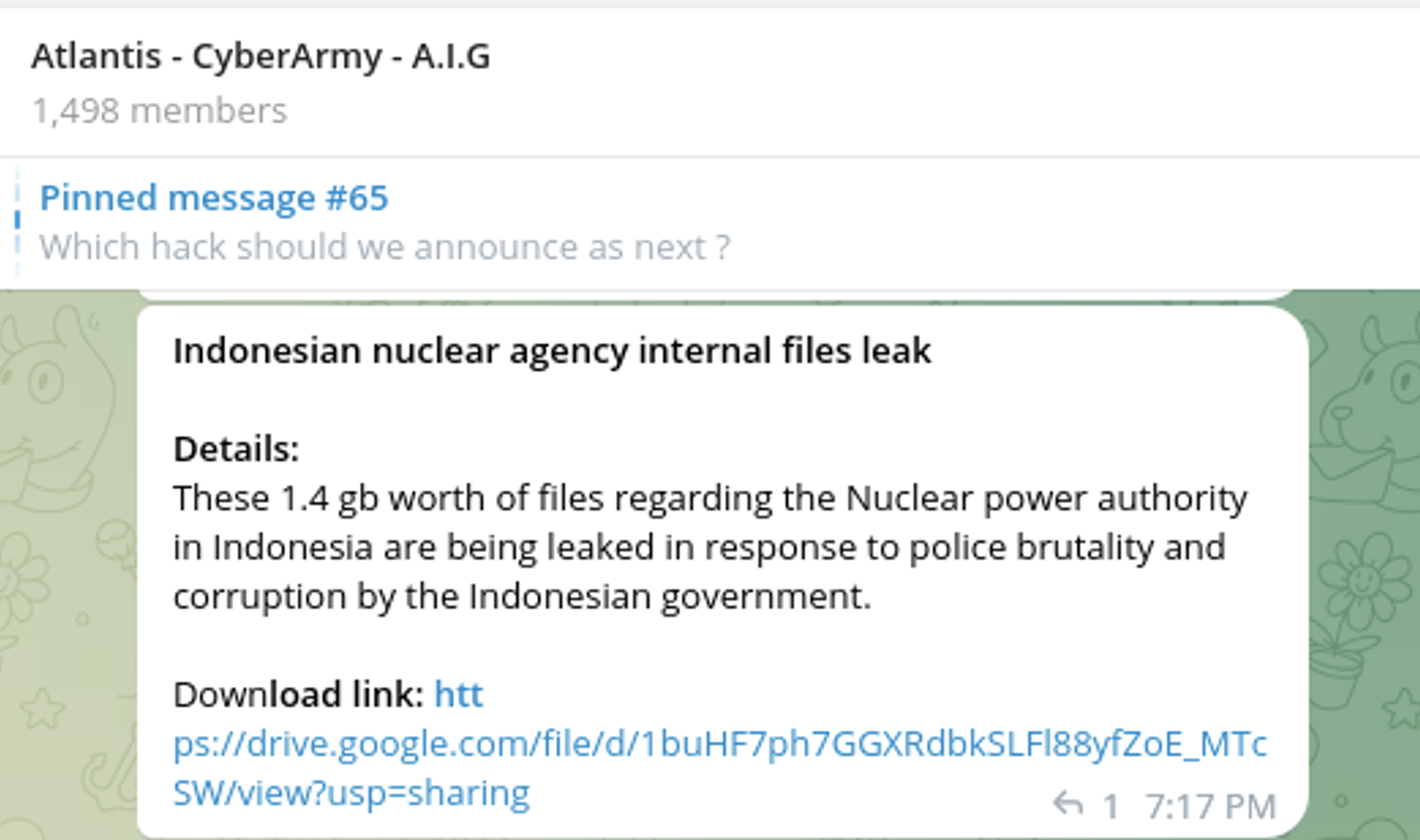
Nuclear Power Production and Development Company of Iran (AEOI)
Around May 2023, threat actors leaked more than 100,000 emails that were stolen from the Nuclear Power Production and Development Company of Iran (AEOI) on Breach Forums. The AEOI is responsible for managing the Bushehr Nuclear Power Plant (BNPP) and leading Iranian research into nuclear fuel cycle development. AEOI’s research initiatives include uranium exploration, mining, and conversion. Attackers exfiltrated 75GB of sensitive Iranian nuclear data.
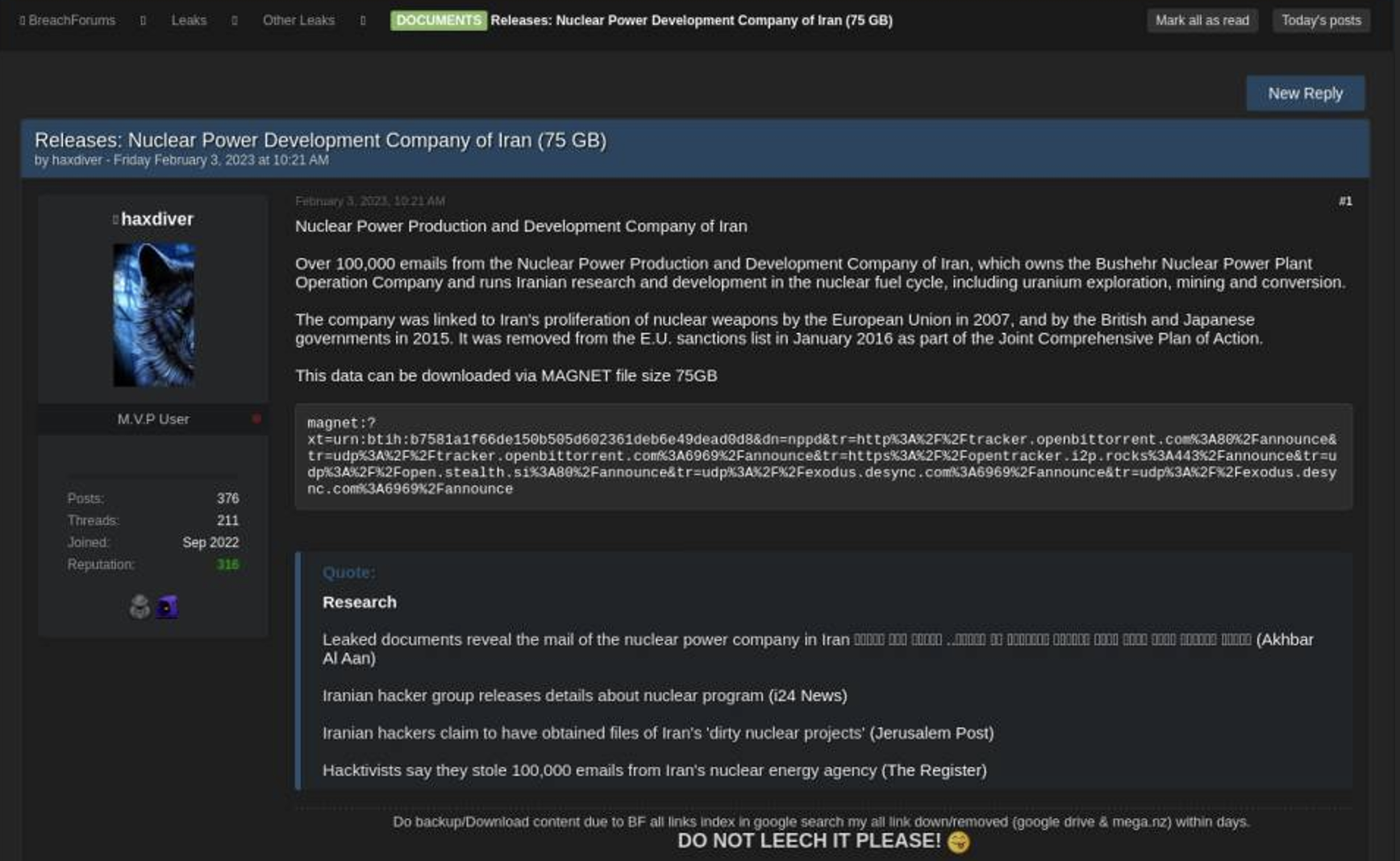
Doosan (South Korea)
One of the first ransomware crews to target the nuclear sector was BlogXX, a sophisticated threat actor group that includes former members ReEvil. Doosan, a Fortune 500 South Korean multinational conglomerate, was one notable victim BlogXX touted on their leak site. This company plays a vital role in supporting critical infrastructure in South Korea, including the nuclear energy sector. Doosan is also the corporate parent to Bobcat and Škoda Power. BlogXX claimed to have stolen over 1.6 TB of sensitive data from Doosan and its business partners. The threat actors also published multiple samples of the ransomed files to prove their claims.
In early December 2020, or approximately 1.5 years before BlogXX’s ransom announcement, Resecurity notified Doosan and the Korean National Computer Emergency Response Team (KN-CERT) about a potential breach impacting their Active Directory. At the time, our team was tracking an IAB who was soliciting access to Doosan and promoting a listing of the company’s Active Directory. Resecurity analysts acquired exclusive access to this listing, which has never been posted publicly on the BlogXX leak site. See the screenshot below.
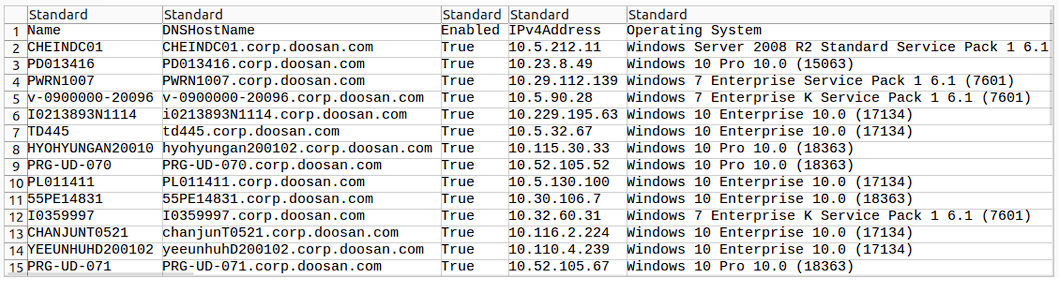
Resecurity assesses that the initial Doosan intrusion likely occurred around 12/3/20, before later evolving into a more serious breach. Around the same time, BlogXX was also targeting major enterprises, government agencies, and organizations involved in nuclear research, including The Institute for Nuclear Research Pitesti (ICN) in Romania. Unlike high-margin private sector firms, research organizations are undesirable for financially motivated cyber-threat actors, as they are less likely to manage significant financial assets.
For this reason, the motivation for BlogXX’s ransomware attack on the ICN is more likely to be cyber-espionage. Resecurity has also notified Romania’s National Computer Security Incident Response Team (CERT-RO) and passed information about this activity to competent authorities. While Resecurity assesses this activity to be independent from REVil/BlogXX, it’s possible the ransomware operators engaged directly with the broader syndicate(s).
One potential scenario could be that the actor promoting ICN access was operating either as an IAB or one of the group’s affiliates. Another possibility is that the threat actor was conducting reconnaissance for a more powerful attack, which was then disguised as cybercriminal activity. The line between state actors and cybercriminals is often blurred, and these attacks raise concerns about cybersecurity regulation and geopolitical risks.
Geopolitical Contagion
As tensions rise due to Russia’s invasion of Ukraine, there has been a dangerous increase in cyberattacks targeting critical infrastructure sectors, including energy. The situation in Ukraine has escalated to a full-blown war zone, and there have been multiple incidents of cyber-espionage targeting the nuclear industry. In March 2022, Resecurity assessed that the alleged Russian-state nuclear energy corporation ROSATOM hack was likely retaliatory.
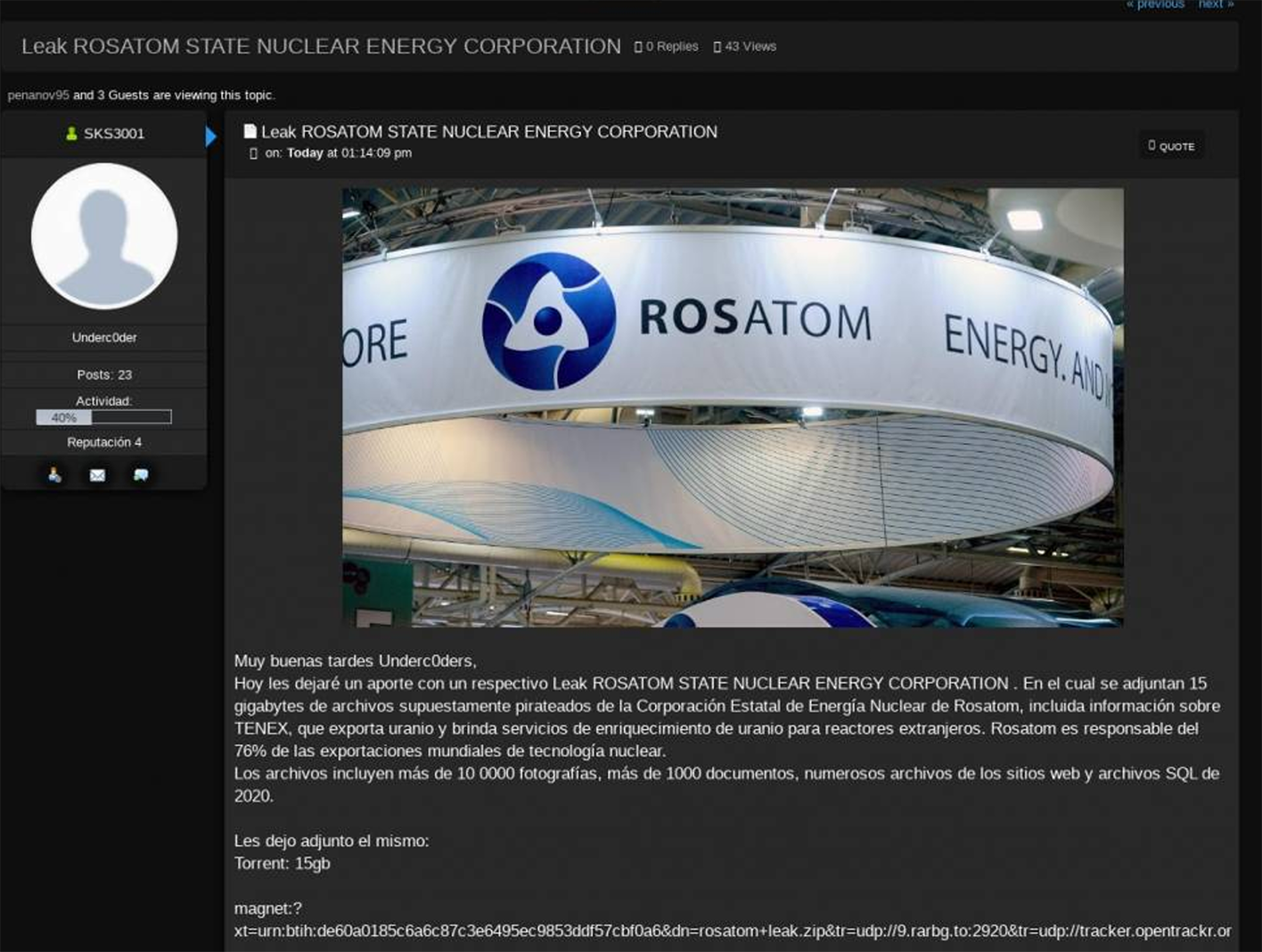
Notably, ‘SKS3001’, the threat actor who posted the 15GB leak of Rosatom data, appears to be a native Spanish speaker, although the posting language could have just been an OPSEC tactic used by the leaker to drop a ‘red herring’ for incident responders. Beyond ROSATOM, this leak also contained documents and data related to Techsnabexport (TENEX), another Russian state-owned company that exports enriched Uranium to global customers.
Taiwan’s Institute Of Nuclear Energy Research (INER)
Resecurity has discovered that an IAB has been selling access to Taiwan’s Institute of Nuclear Energy Research (INER) through a compromised employee’s Office 365 account. The threat actor was monetizing the stolen INER credentials through a trusted network of contacts in the cybercriminal underground. This same IAB was also found to be selling access to other nuclear research organizations in Thailand, Vietnam, Brunei, and Malaysia in 2022. We have shared this information with Taiwanese authorities and our U.S. law enforcement partners.
STORMOUS Announces the Compromise of Petroleum Equipment Assembly & Metal Structure J.S.C (PVC-MS) in Vietnam
On September 7, 2023, the pro-Russian ‘STORMOUS’ ransomware gang announced on their official Telegram channel that they had compromised 300 GB of data belonging to Petroleum Equipment Assembly & Metal Structure J.S.C (PVC-MS). This victim entity is a “member of the PetroVietnam Construction Joint Stock Corporation (PVC) under Vietnam National Oil and Gas Group (PVN), established in 1983 has the main capabilities of constructing, fabricating, installing the Platforms, Tanks, Pipeline for Oil & Gas Field,” according to the victim’s website.
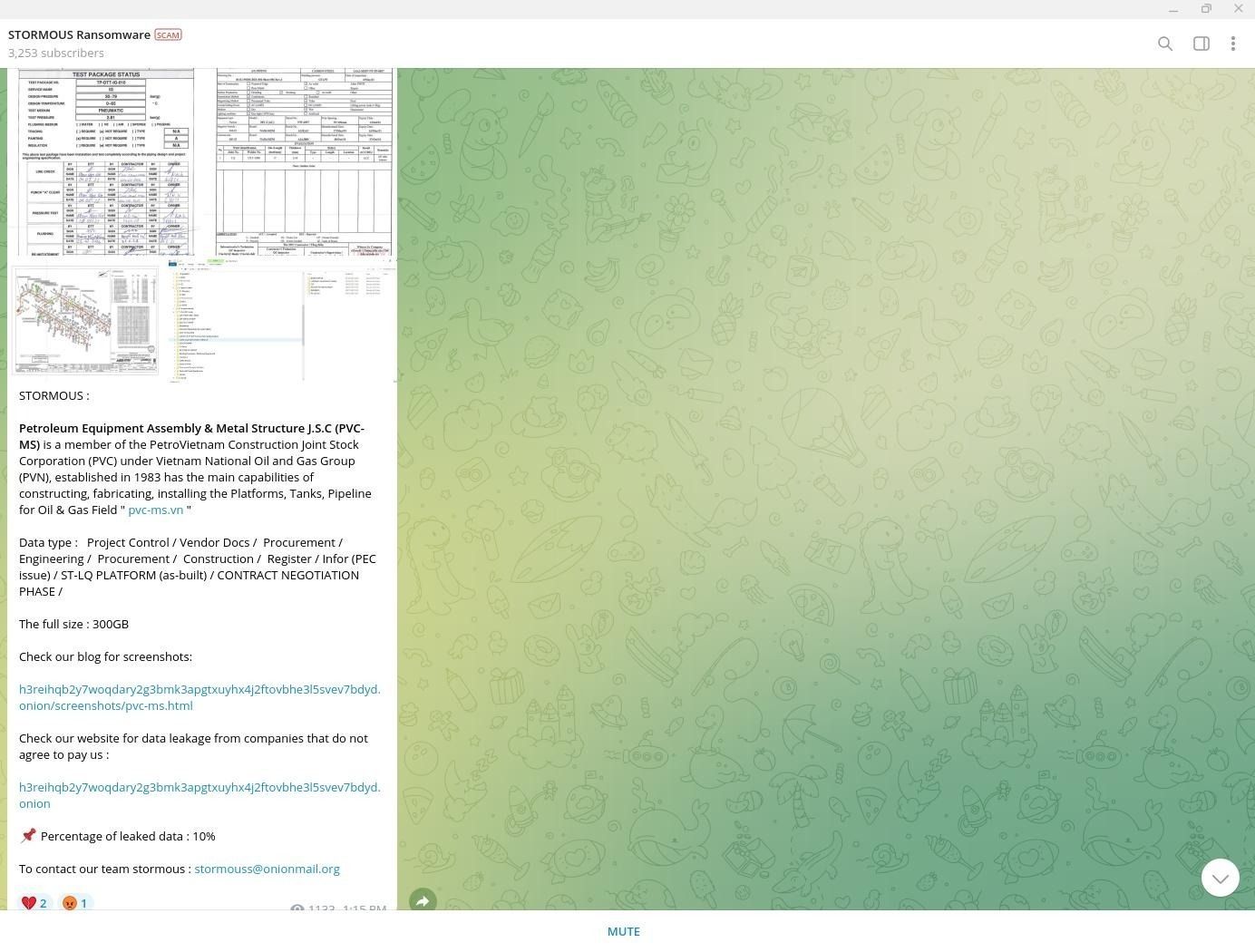
Per STORMOUS’ Telegram posting, data types they stole from PVC-MS include: “Project Control / Vendor Docs / Procurement / Engineering / Procurement / Construction / Register / Infor (PEC issue) / ST-LQ PLATFORM (as-built) / CONTRACT NEGOTIATION PHASE.“ STORMOUS has leaked just 10% of the 300 GB PVC-MS data dump so far.
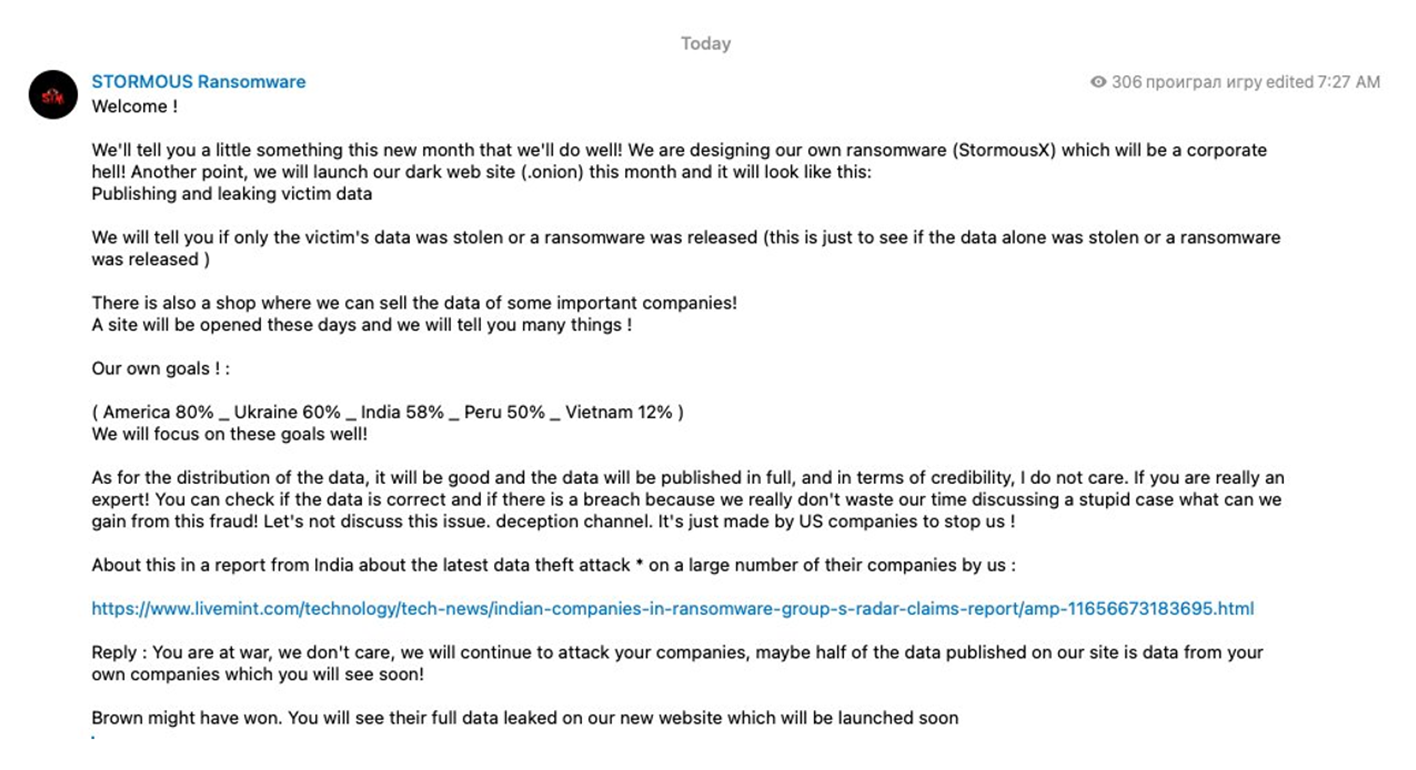
STORMOUS’ attack on PVC-MS is also in line with threats the group made back in May 2022 after returning from a short hiatus. The group published a message on Telegram saying: “We will promise that we will destroy all the different companies in the USA the country of Vietnam and the country of Peru.” See the screenshot below.
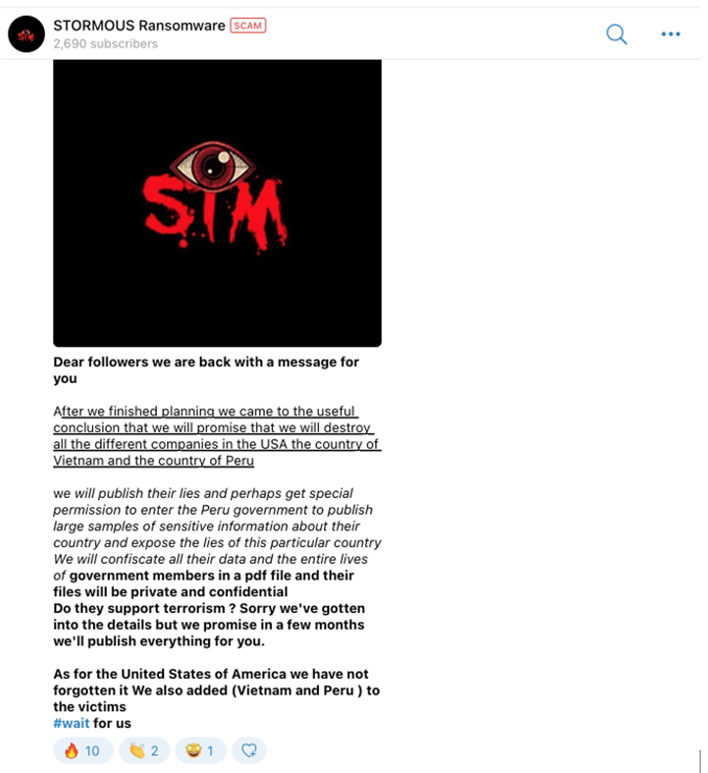
In July 2022, STORMOUS followed up this announcement with another Telegram post, specifying the geopolitical considerations guiding their target selection. They quantified their target criteria as follows: America (80%), Ukraine (60%), India (58%), Peru (50%), and Vietnam (12%). See the screenshot below.
“Big Game” Hunting – Black Basta Targets the Energy Sector
Among active ransomware crews targeting the energy sector, Black Basta is one of the most prolific threat groups operating today. First identified in the wild in 2022, Black Basta is believed to be a splintered ‘rebrand’ of the now-dissolved ransomware syndicate, Conti. The group’s tactics, techniques, and procedures (TTPs) also overlap certain attack signatures observed in breaches attributed to BlackMatter.
Resecurity has recently identified an updated Black Basta ransomware variant that has targeted multiple entities operating in the European energy sector. Black Basta distributed the new attack variant to their affiliates sometime in February and then released a version update around March 10. Around this time, Black Basta operators were demanding $6 million from one energy company victim in the EU and another $3.5 million from a logistics company in the Nordic region that provides transport services for the oil & gas industry.
The identities of these victims have not been disclosed on Black Basta’s DLS.
One of the most significant upgrades to the previous Black Basta ransomware version is the new variant’s optimized encryption library. Black Basta developers replaced the Mini-GMP code library used in the older versions (https://github.com/idris-lang/Idris-dev/blob/ master/rts/ mini-gmp.c) with the Cryptoapp (https://github.com/weidai11/cryptopp) library. Another enhancement observed in one variant update distributed to a specific affiliate is the inclusion of a customized package containing a ‘cryptor’ malware obfuscation tool, as well as several .bat files used for anti-virus evasion/deactivation.
https://twitter.com/FalconFeedsio/status/1630091991810801666
This BlackBasta ransomware strain was written in the C++ language and compiled for Win32.
Files:
- av.bat – performs a hidden deletion of an application with the given GUID:
{7E4BEC2F-7D16-4A7D-9174-BE810D60A187} - av1.bat – performs a hidden deletion of an application with the given GUID:
{C8902761-479E-4590-A707-6623FCC66FA6} - sym.bat – runs smc.exe with the -stop parameter (Looks like Symantec Endpoint Protection is disabled)
- TI_c.exe – a cryptor that hides as the Symantec Norton Security with Backup Portable Restore Utility.
- TI_c.dll – a library version of the TI_c.exe cryptor.
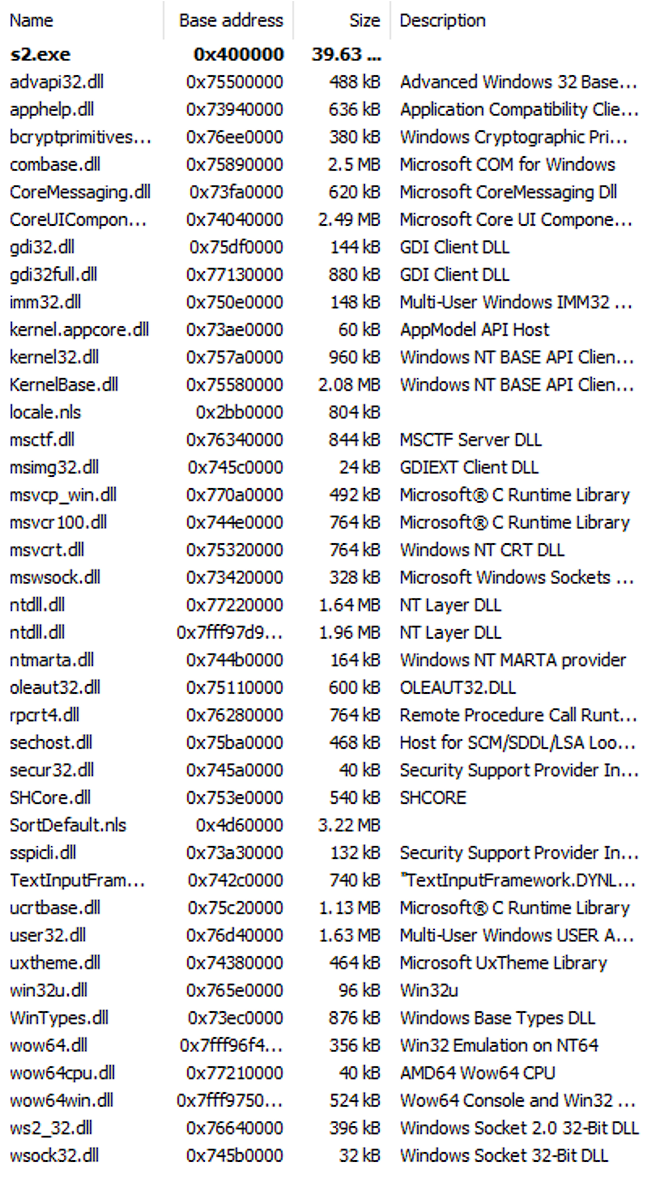
- S2.exe – knocks via TCP by the address from files list_x…
Algorithm Functionality
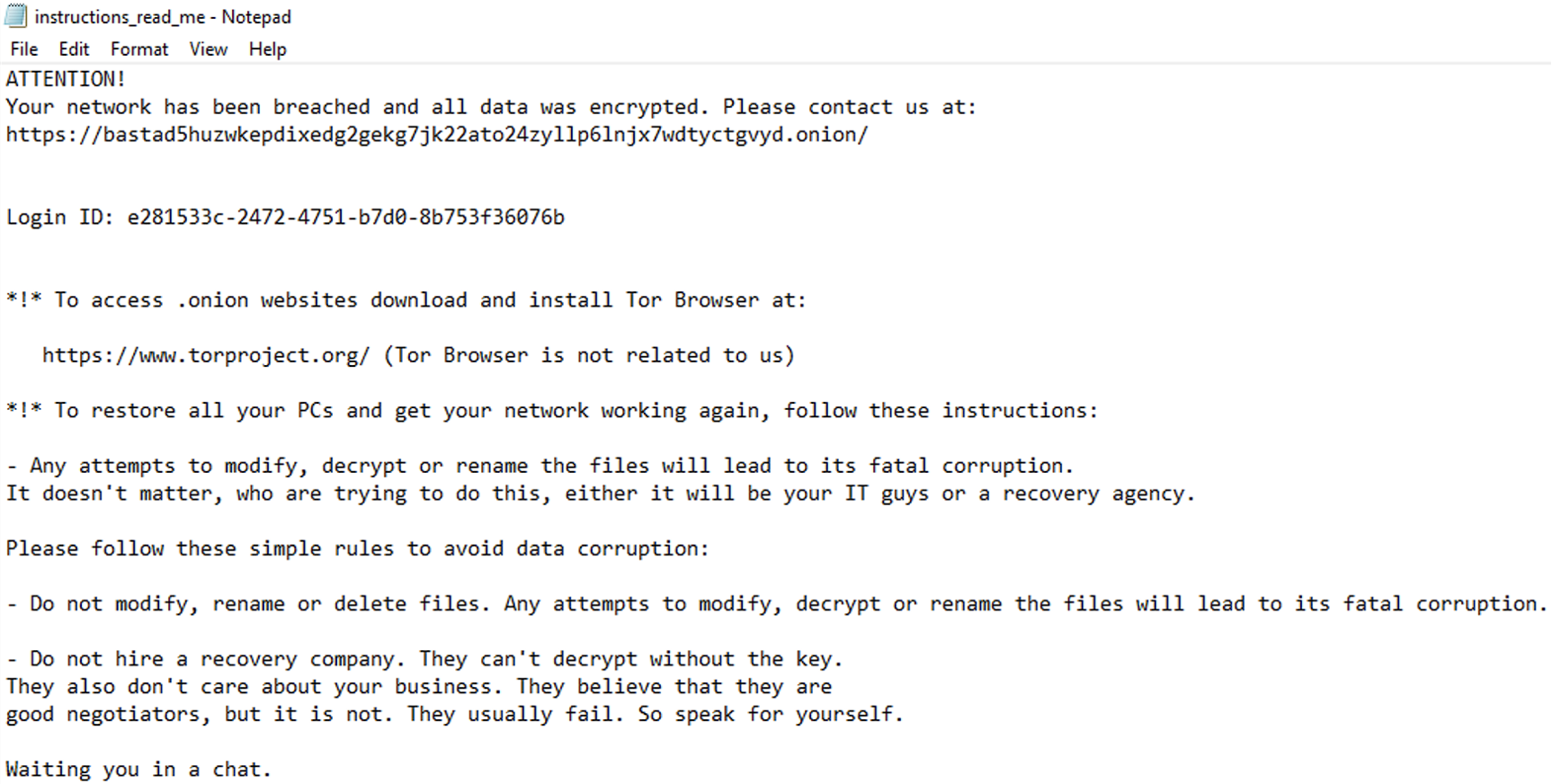
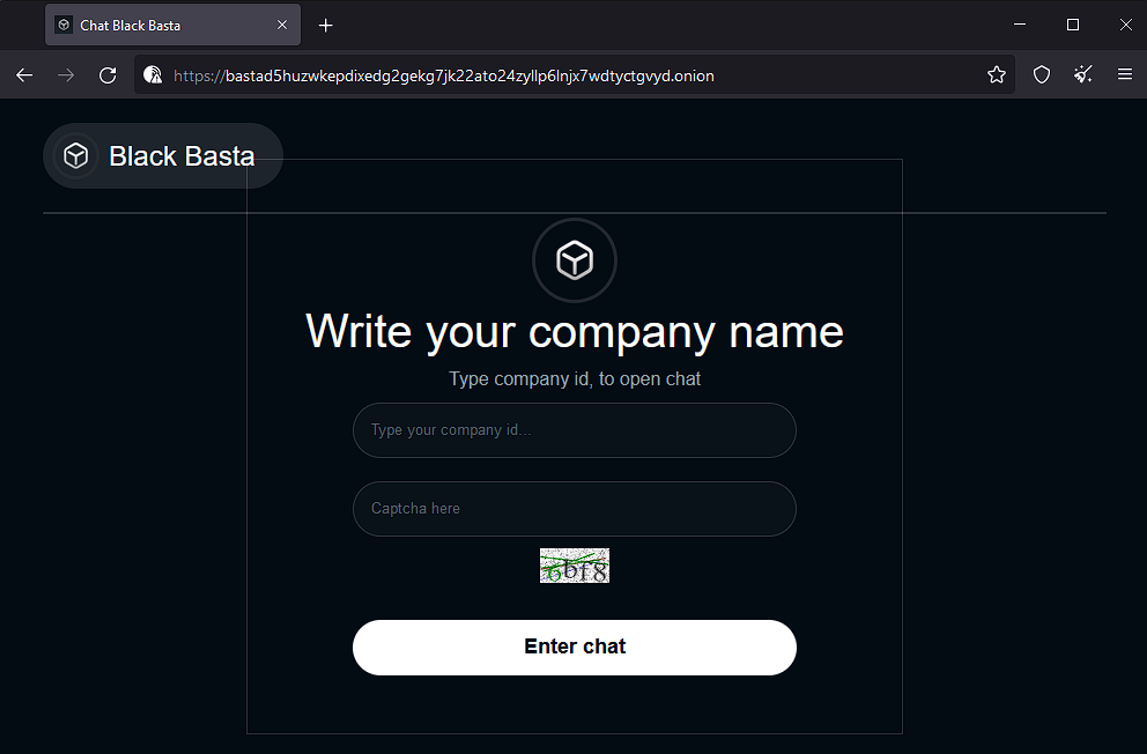
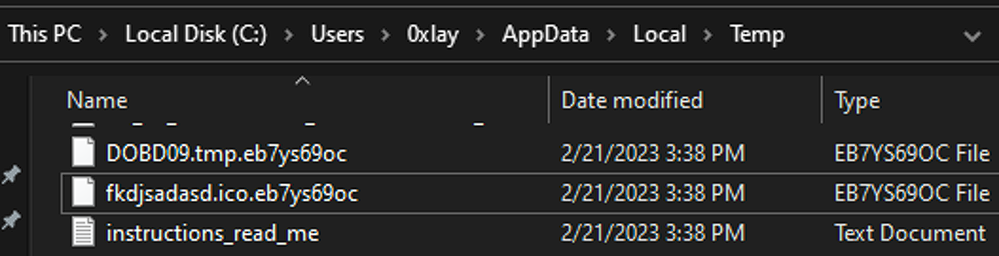
When we ran the TI_c.exe, the encryption process started. The encrypted files have the “.eb7ys69oc” extension (see Figure 0). Once the data is encrypted, this strain generates a “read-me” file in each folder (see Figure 1). This file includes a link to Black Basta’s dark web chat site (see Figure 2 and Figure 3).
Reference: https://bastad5huzwkepdixedg2gekg7jk22ato24zyllp6lnjx7wdtyctgvyd.onion/
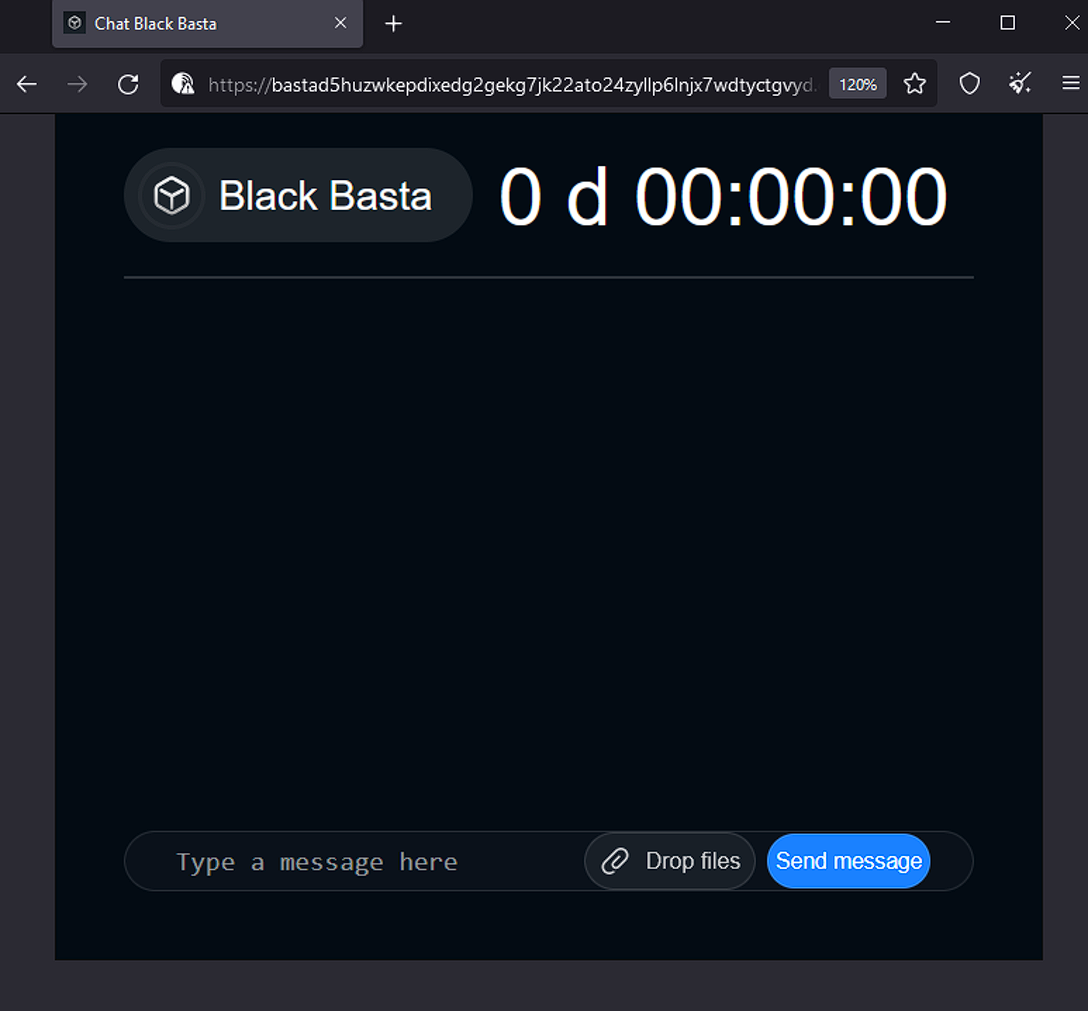
Cybercriminal Negotiations
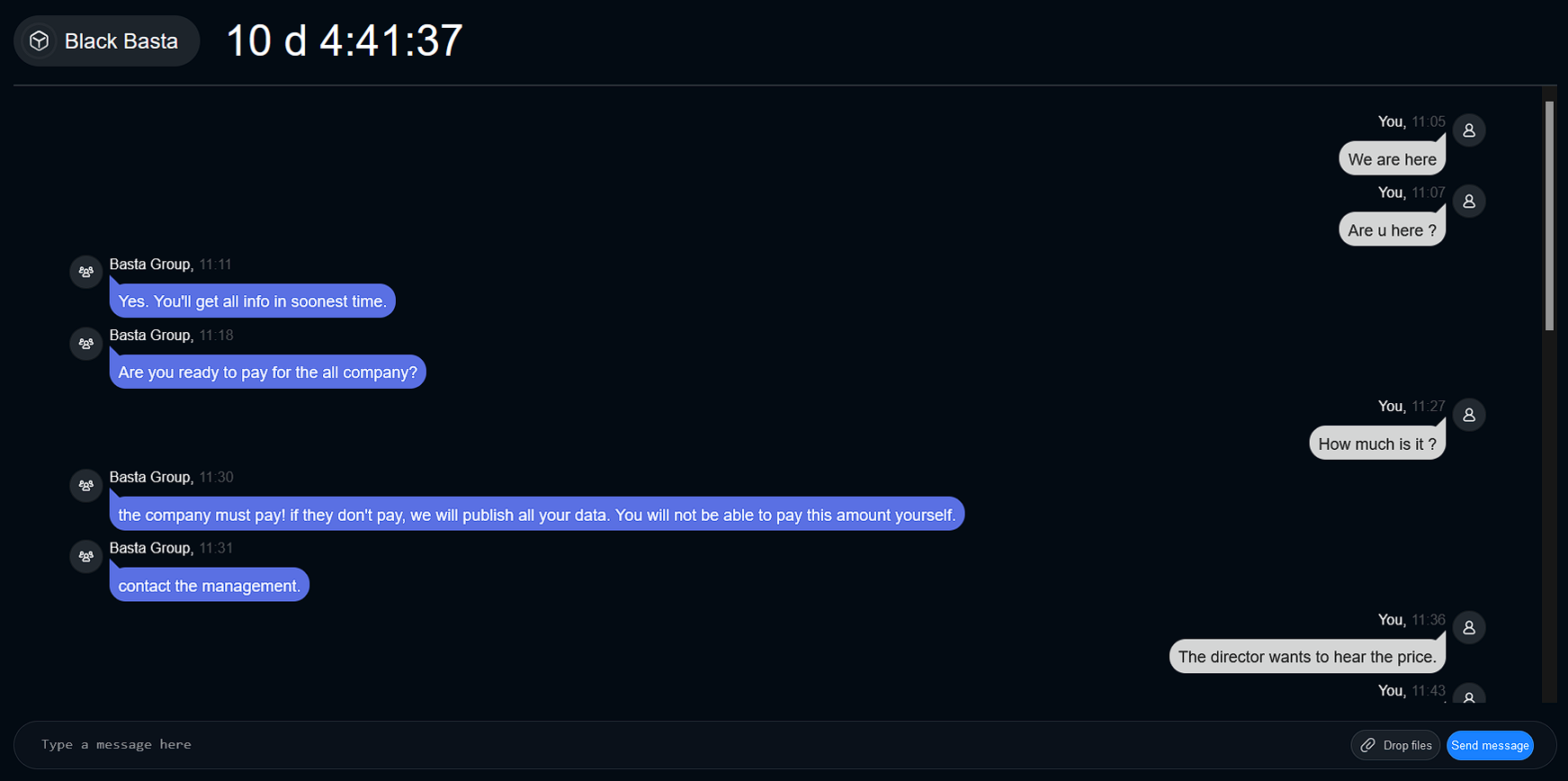
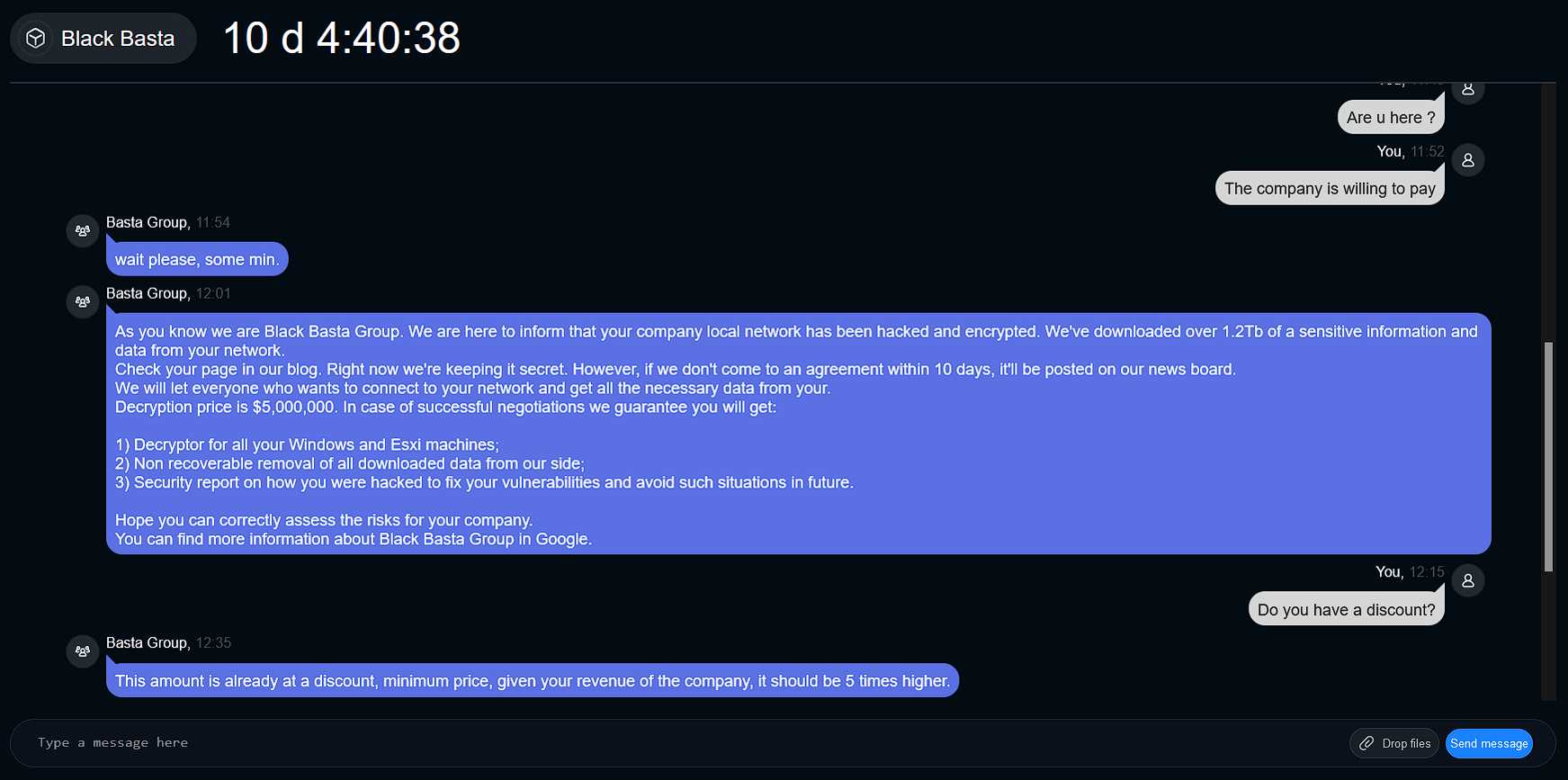
In Figure 4, Resecurity investigators pretended to be a regular employee whose laptop data had been encrypted. They contacted Black Basta’s customer support team to inquire about the cost of decrypting the ransomed files.
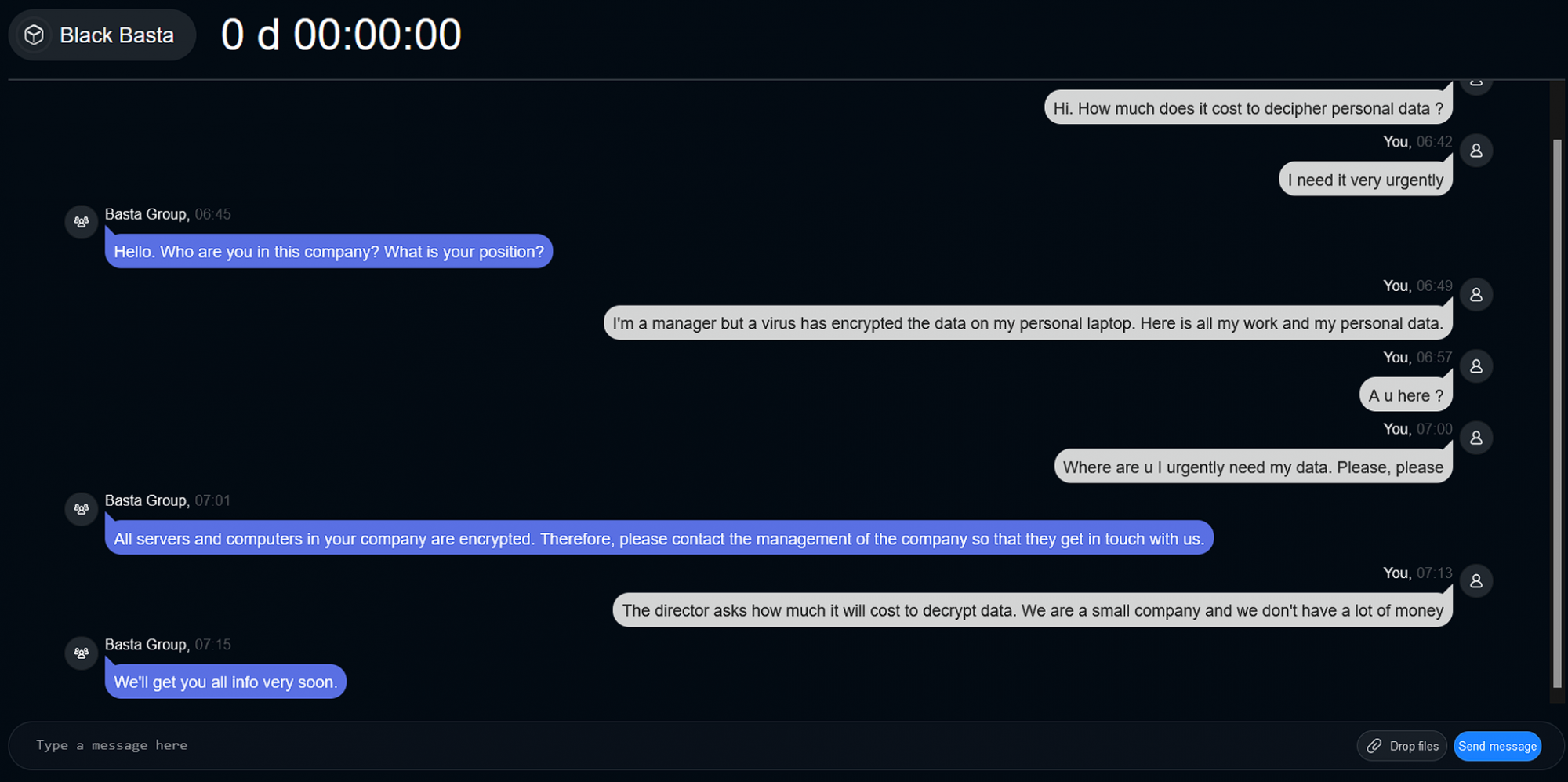
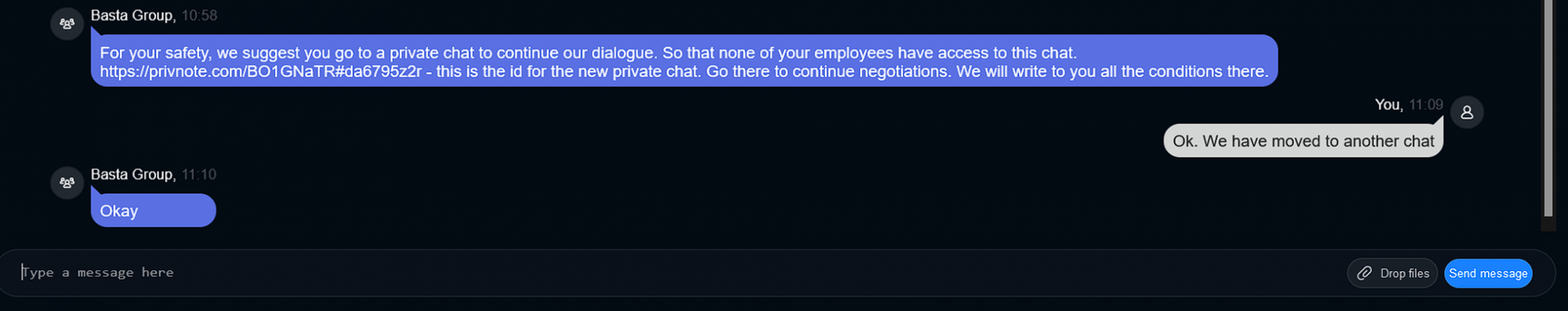
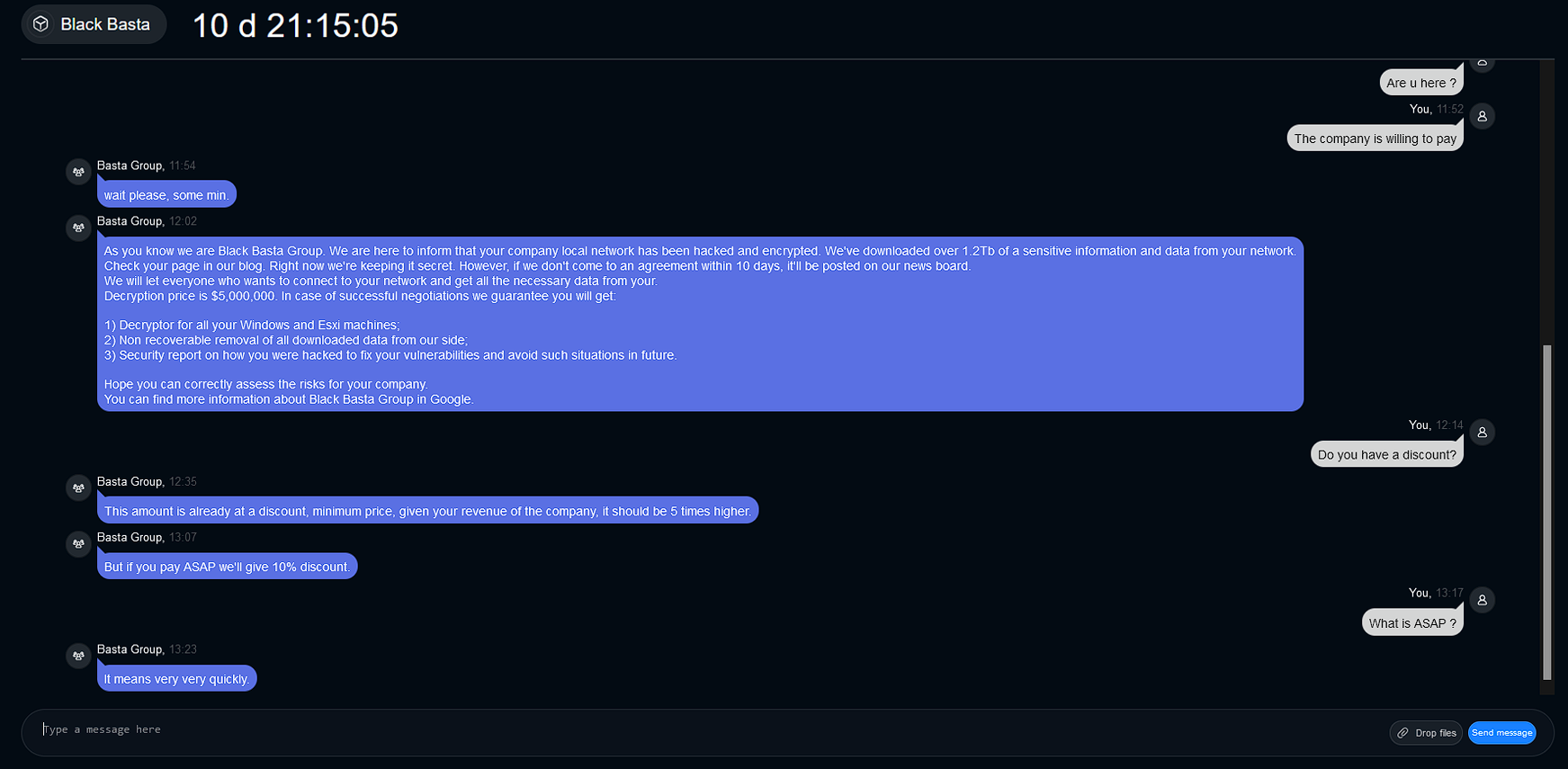
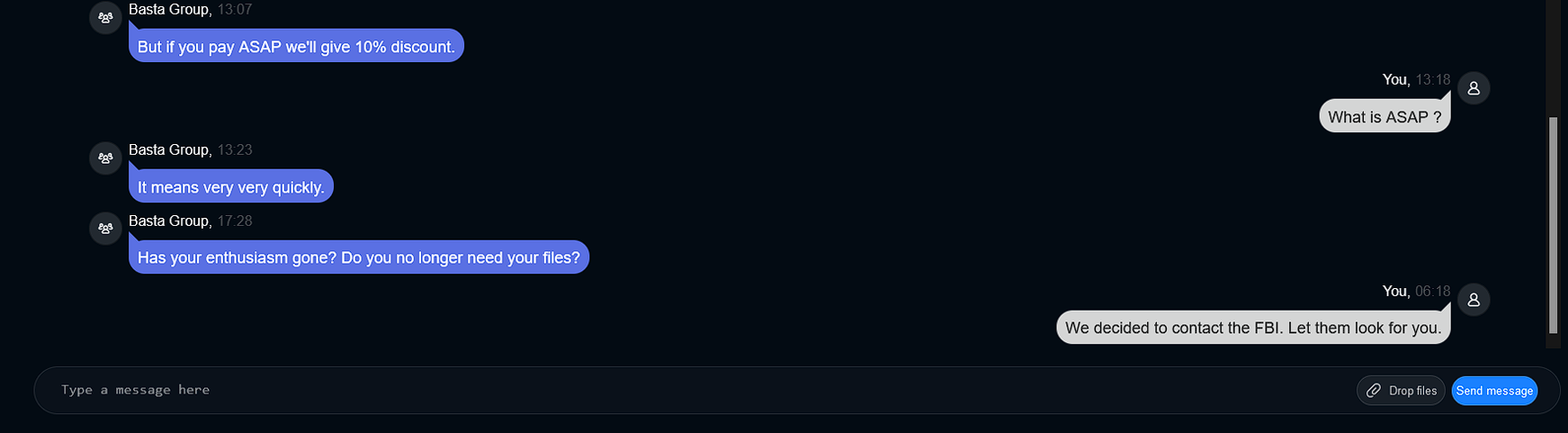
Afterward, Black Basta instructed our investigator to go to another chat by copying the Chat ID from a Privnote message. Privnote is a self-destroying messaging app popular in the cybercriminal underground (see Figure 5). When our investigator resumed the chat, a timer began, and Black Basta’s support team instructed them to make a ransom payment of $5 million (refer to Figure 6.1 and Figure 6.2).
Analysis of S2.exe
MD5: 6f20f5aa2eb7a0c53a39b49024d938ee
SHA256: a9dd4eae8612729957bfeac53b764aba6243c749c7b7666e21acec1504efde84
SHA512: 188b46145135c5f850ac811975cc87f07a5493ee4d6c41db6ec361da5445b4e3b00964c7a691e4ab520dd2b88ed0a60969c43599a0d22b2b9f645f7250bc7e98
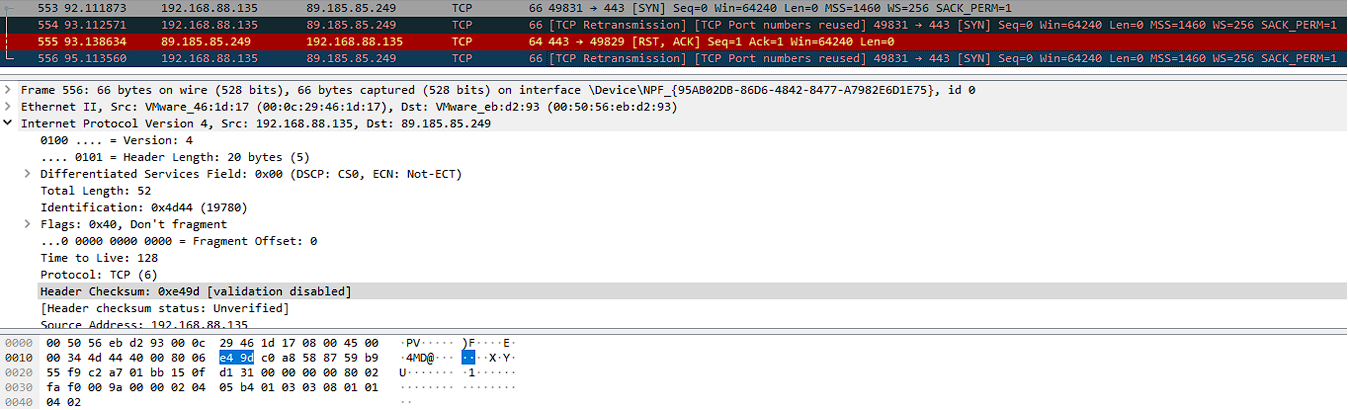
This module, called s2.exe, is encrypted and uses an anti-debugging technique. After unpacking it, we found that it sends a signal via TCP to the addresses listed in files list_0, list_1, and so on (see Figures 9 and 10). However, the way that this module executes needs to be clarified since the cryptor process does not activate it. See Figure 7 and Figure 8 for more details.
Analysis of TI_c.exe
MD5: 2f4acd97542131cda5f26249176348e3
SHA256: b0e43793c527802856bfa3a81b02b3f10e29d74fc60d8b233247a42f0cbc78eb
SHA512: f0ed9685e85f0e8d8ce7324f7a5813db2bf08021e102b758dd88dbf5b450fb139f3116db5029bf11f2b548f17be89e42e2a3d84c07ca64ffbc3cab2a1fb04c43
The TI_c.exe executable is a cryptor. First, it collects file information and then starts the encryption process. After the files have been encrypted, this image is unloaded from memory.
The cryptor ignores the following folders: C:\Windows, C:\Program Files, C:\Program Files (x86), and $Recycle Bin.
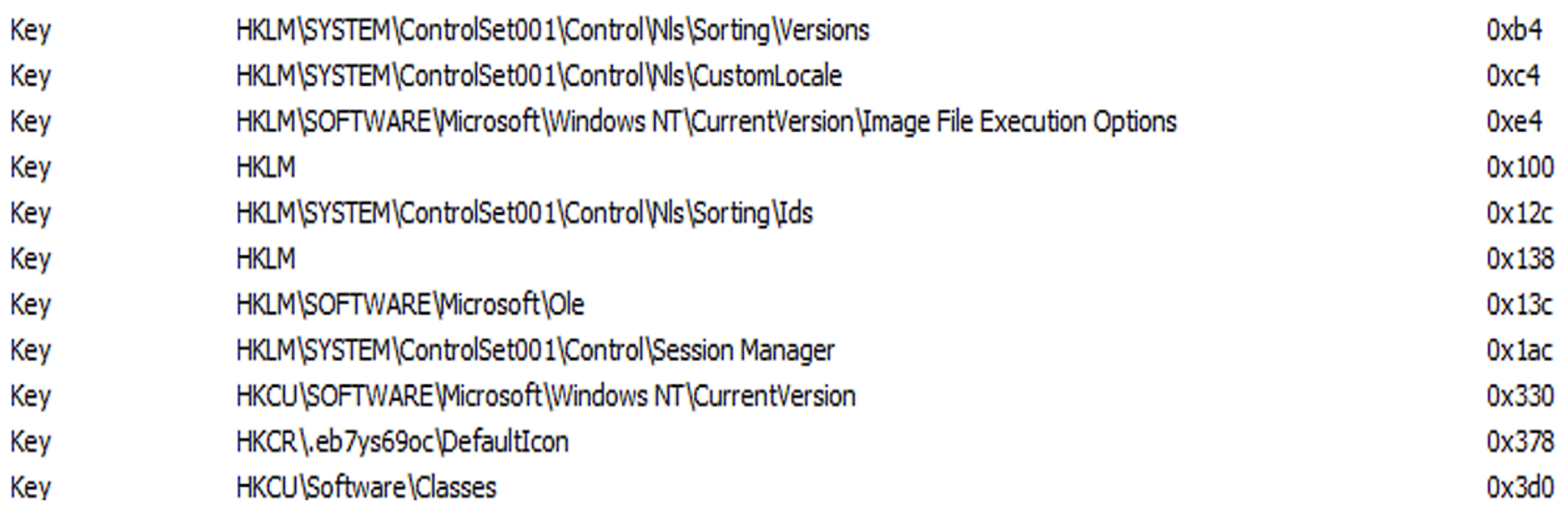
The cryptor works with the registry to create the registry key: “HKCR\.eb7ys69oc\”. (See Figure 11).
The cryptor has a bug that sometimes encrypts its own icon (See Figure 12).
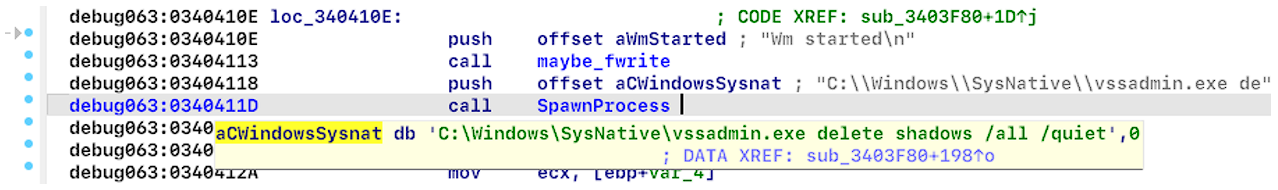
The cryptor spawns the process “vssadmin.exe” to delete snapshots (see Figure 13). The “vssadmin.exe” is a command-line utility found in all Microsoft Windows operating systems after Windows XP. This utility manages the Volume Shadow Copy Service (VSS), which is a Windows service that allows users to create and manage snapshots of volumes for backup and restore purposes.
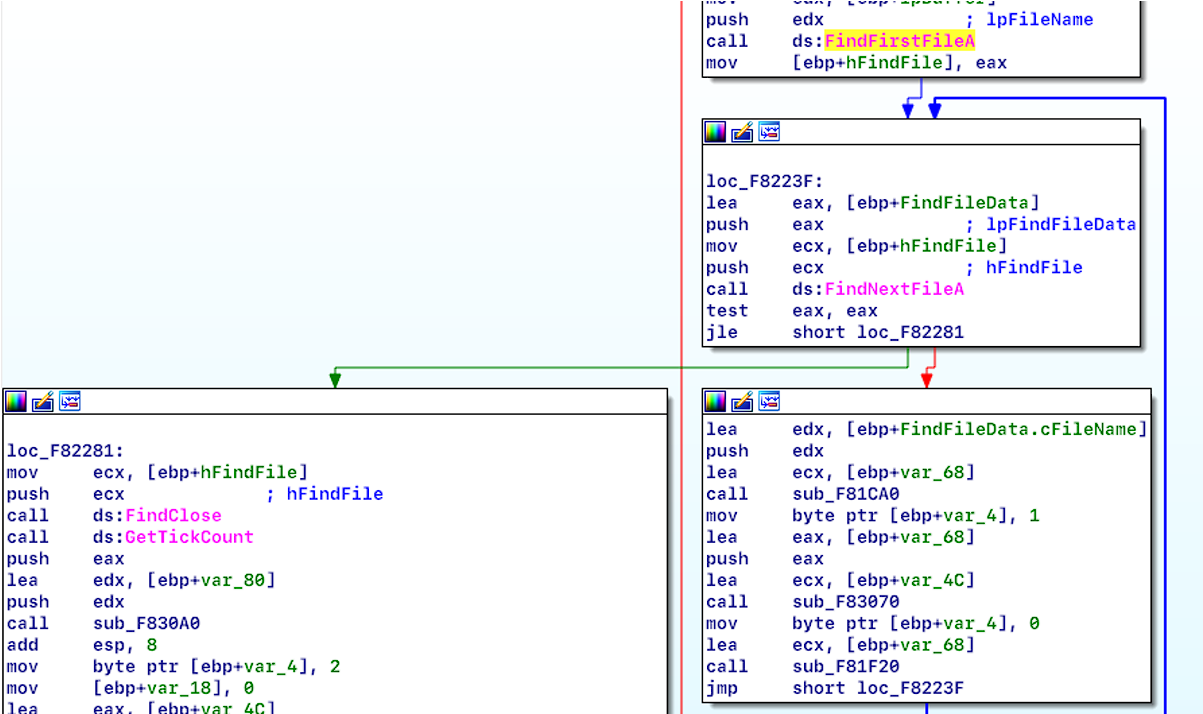
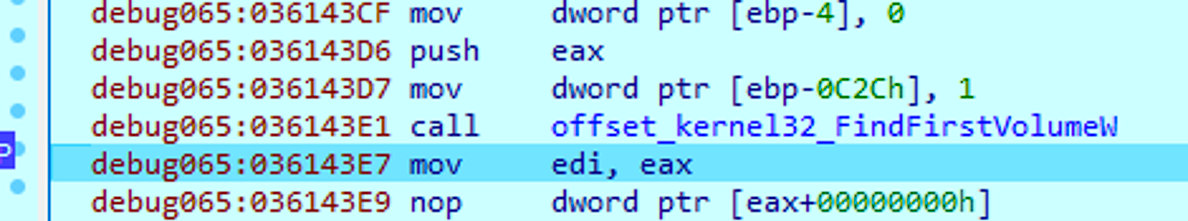
The cryptor acquires data on files by utilizing the FindFirstFileA and FindNextFileA APIs (see Figure 14) as well as FindFirstVolumeW and FindNextVolumeW functions, which are Windows APIs that provide handles for volumes on a computer (see Figure 15).
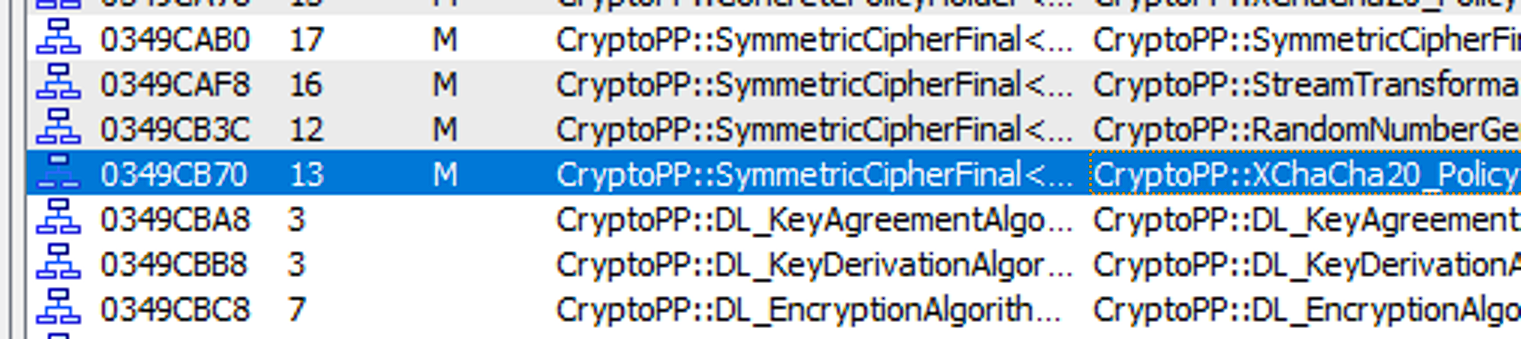
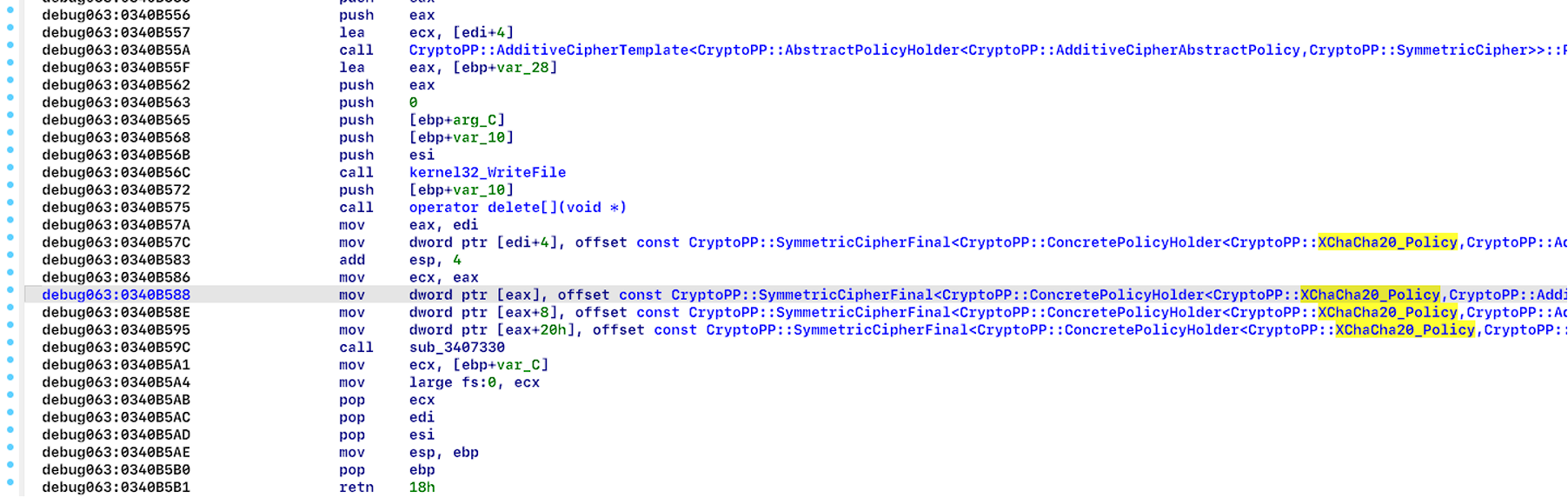
After unpacking, Resecurity investigators found that the cryptor was using the CryptoPP library (see Figure 16) (https://github.com/weidai11/cryptopp). Next, we found that the chacha20 algorithm was used for encryption (see Figure 17).
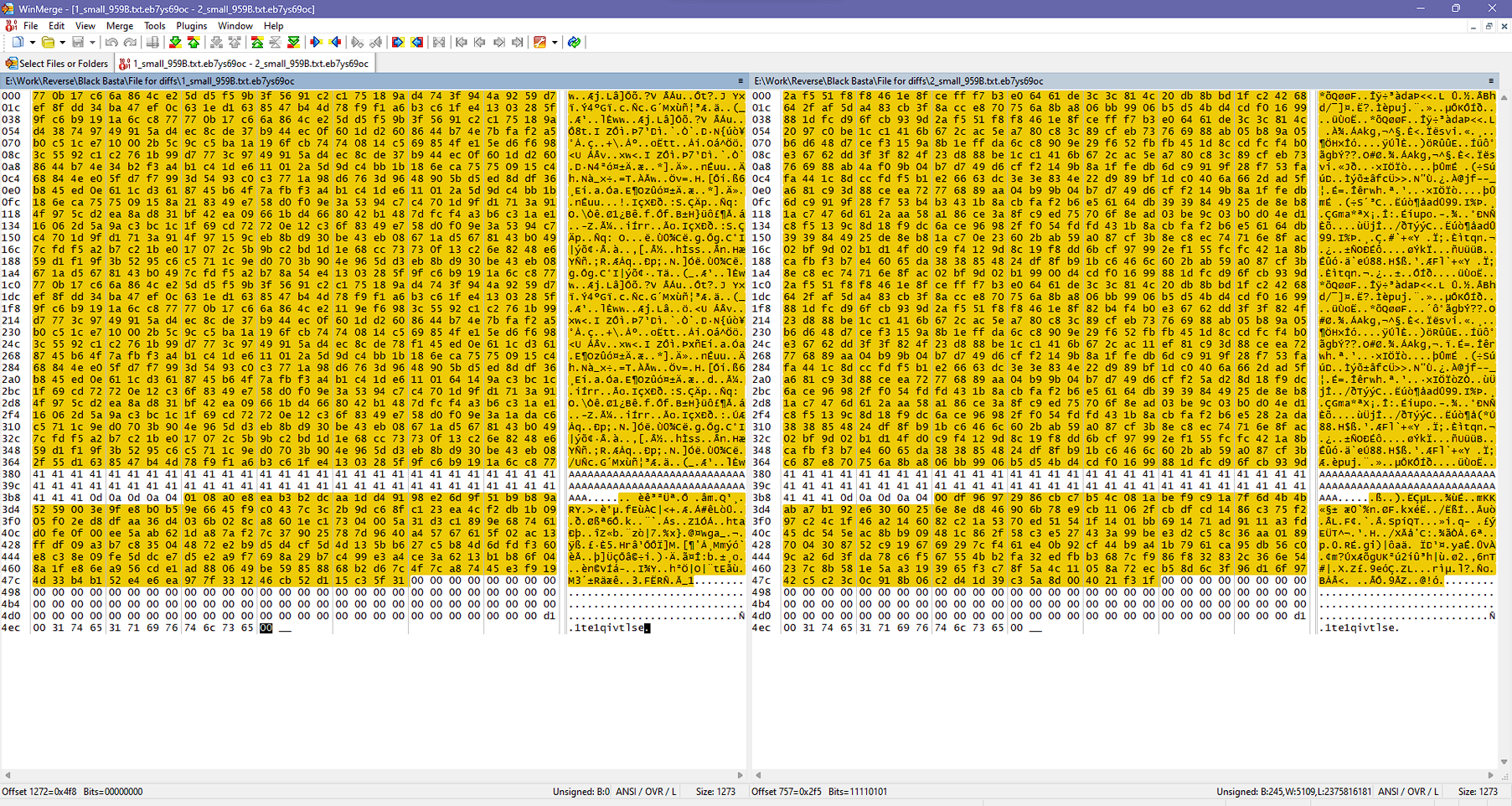
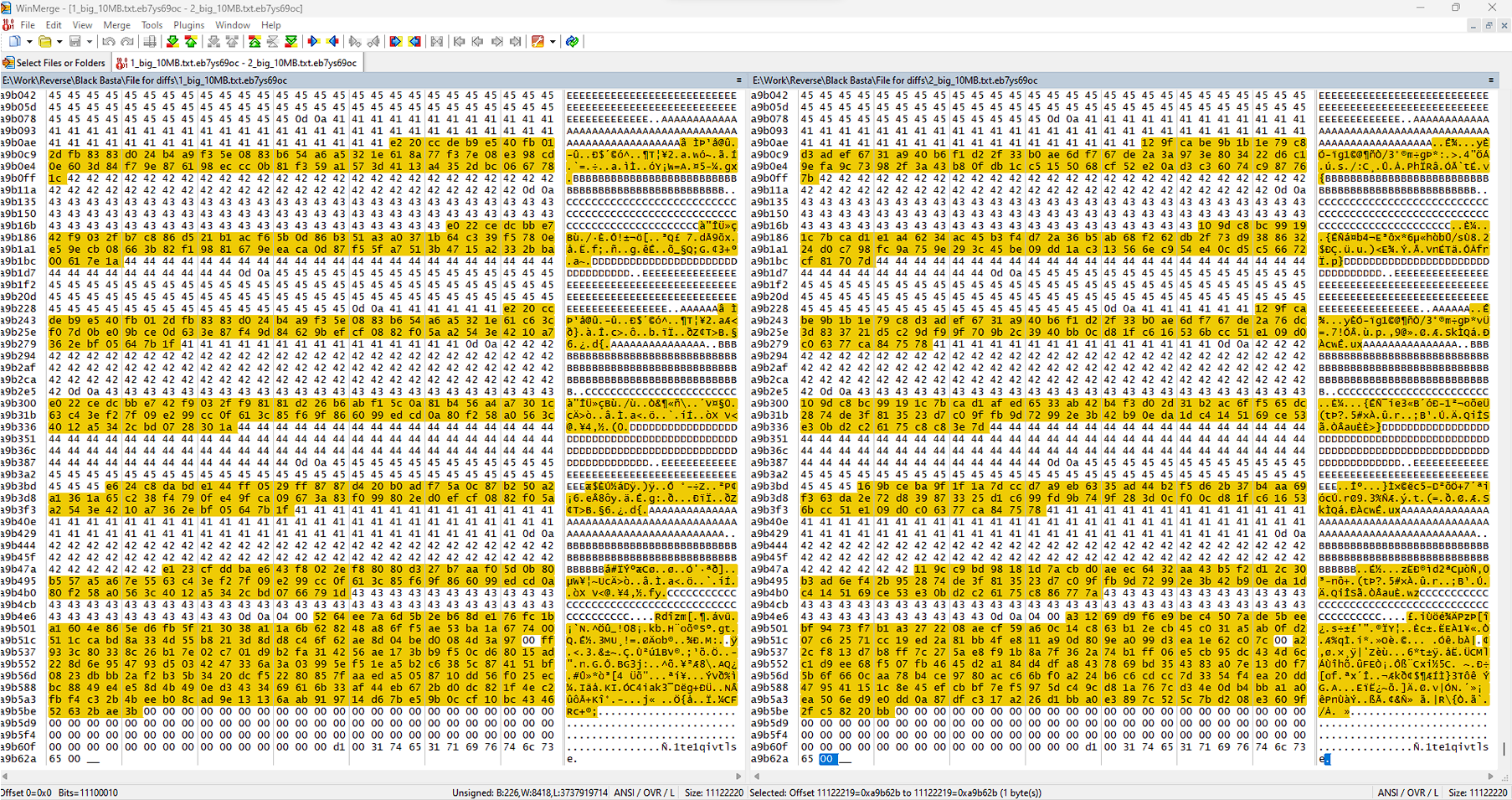
Each encrypted file stores the string “1te1qivtlse” at the end of the cipher. (See Figure 18)
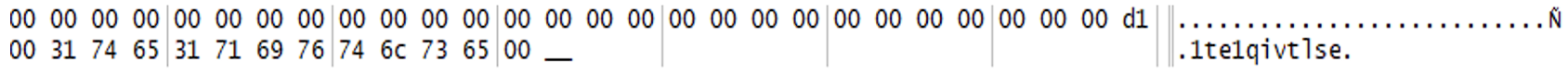
We encrypted a file that was 959B in size and found that 64B were skipped while 896B were successfully encrypted, as shown in Figure 19. However, when the file was larger than 4KB, we noticed that 64B were encrypted while 128B were skipped, as depicted in Figure 20.
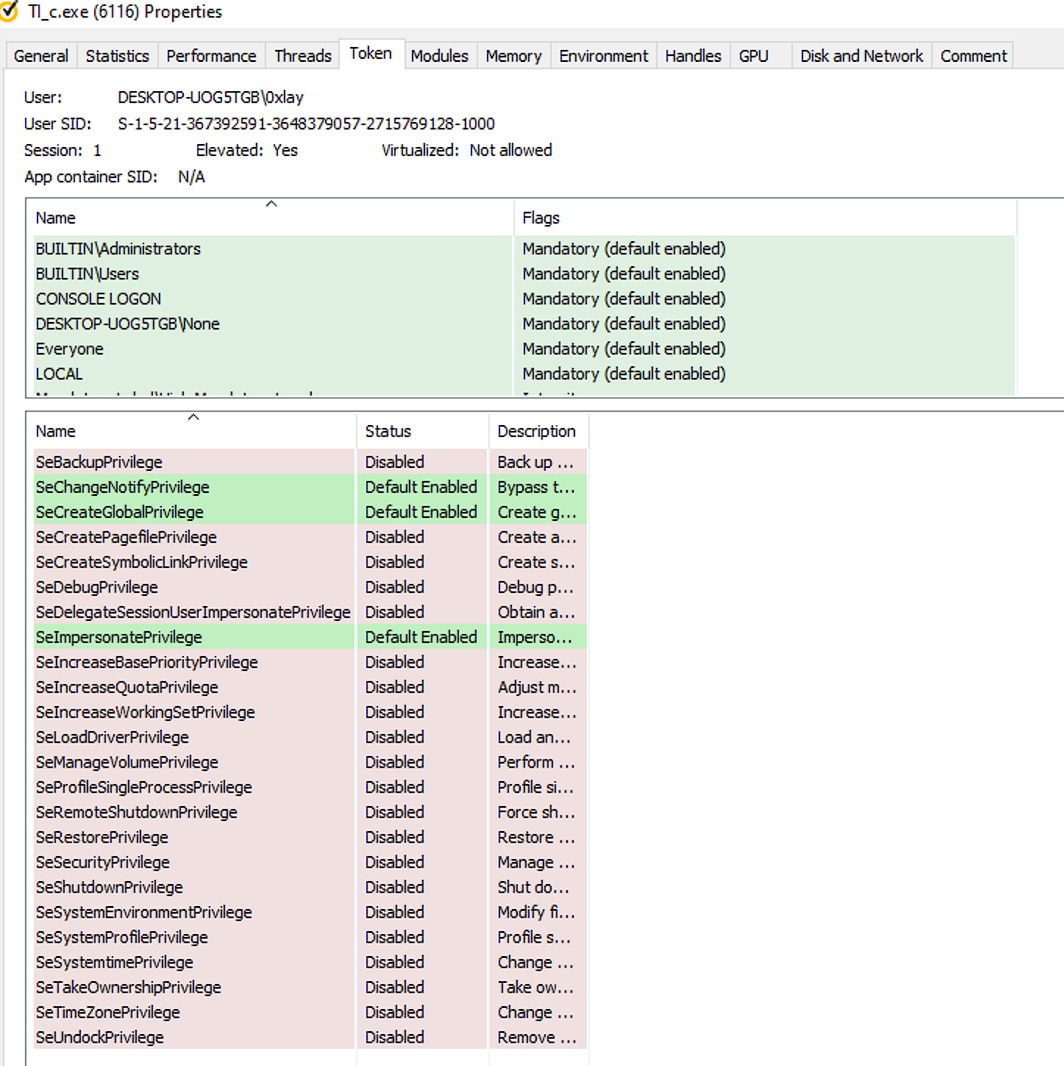
The cryptor uses the following privileges and modules (see Figure 21 and Figure 22).
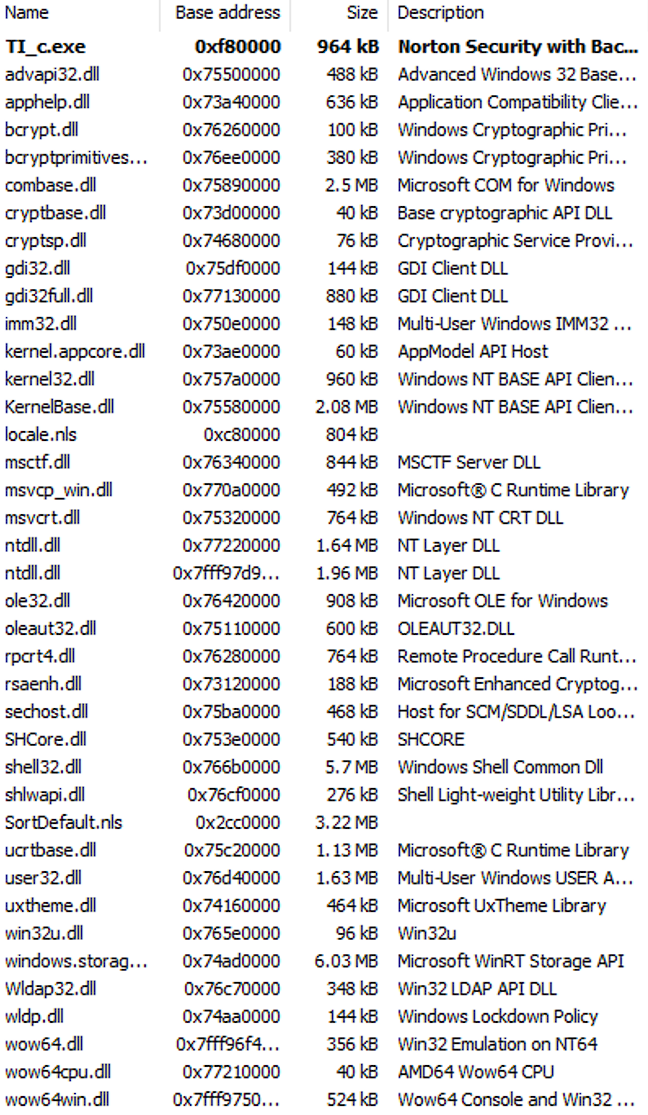
Analyze TI_c.dll
MD5: ca6b2fbb87c4abbbc8202387b1dfc173
SHA256: da6800063764aa4f39998d4aa069ca380ce6bcbe70099e16ece946c1754423cc
SHA512: 0ea3b49bacd9d2b7fbedf0296fdc6cd06c005c54d822a7e9041305c01a01c30a6604fbd17f43aea68716e3fd0639e7f25d76e703843c18d470bdc6930d54ef00
After carefully analyzing both files, we have determined that the TI_c.dll is a version of the TI_c.exe cryptor library (refer to Figure 23 and Figure 24). This library can start the encryption of files by injecting it into a process.
Summary
The alarming escalation of ransomware attacks against the energy sector and critical infrastructure is a trend that cannot be ignored. With at least a dozen sophisticated groups such as BlackCat/ALPHV, Medusa, and LockBit 3.0, among others, intensifying their focus on these high-stakes targets, the threat landscape is becoming increasingly dangerous. These threat actors are not acting in isolation; they are supported by a flourishing ecosystem of access brokers and tool developers who provide the necessary leverage to infiltrate and exploit these essential systems. The collaboration between these groups and individual actors is a clear indicator of the strategic importance placed on the energy sector, which is perceived as a goldmine for high-value data and maximum ransom payouts exceeding $5,000,000 (million) in some cases.
Looking ahead to 2024, we envision a significant growth in cyber threats, particularly with ransomware groups increasingly prioritizing high-value targets within the energy sector. This includes a specific focus on the nuclear energy sector, as well as oil and gas providers, both in their downstream and upstream operations. As digitalization in these areas continues to advance, the attack surface for malicious actors expands, offering more opportunities for exploitation. The sector's growing reliance on interconnected technologies, while beneficial for operational efficiency, also presents lucrative opportunities for cybercriminals. The potential for substantial ransom payments, driven by the critical nature of these energy services, further heightens the appeal for these bad actors. It is therefore imperative for organizations within these specific areas of the energy sector to significantly bolster their cyber defenses and prepare for the sophisticated and potentially devastating cyber campaigns that are likely to emerge in the coming year.

