Massive Dump of Hacked Salvadorean Headshots and PII Highlights Growing Threat-Actor Interest in Biometric Data
Cyber Threat Intelligence


A threat actor leaked the personally identifiable information (PII) of over five million citizens from El Salvador on the Dark Web, impacting more than 80% of the country’s population. The threat actor, going by the alias ‘CiberinteligenciaSV,’ posted the 144 GB data dump to Breach Forums, writing that the leak included 5,129,518 high-definition photos, each labeled with the corresponding Salvadorian’s document identification (DUI) number. Additionally, the leaked database features Salvadorian citizens’ first names, last names, birthdates, telephone numbers, email addresses, and residential addresses. The most significant aspect of this breach is the biometric element, with the leak offering over five million headshots indexed with the corresponding PII of the victims. This biometric data dump has thus introduced significant fraud and identity theft risks for the majority of El Salvador’s citizens.
Attribution for this attack is uncertain, as the entities that initially posted and later recycled this data leak seem to be insinuating the involvement of an infamous hacking collective. At the same time, the leak posters have previously stated they are not affiliated with the group they continue to promote. For example, the threat actor who posted this data leak invoked the same handle as a Telegram group that originally published the Salvadorean PII dump over a year ago and which superficially appears to be linked to the Guacamaya (Macaw) group. This notorious hacktivist collective targets public and private-sector organizations in Latin America (LATAM). A brief blurb about the group published by the leak and hacktivist resource site Enlance Hacktivista, which has previously published data the Guacamaya have hacked, says that they are “a group of hackers that seeks the liberation of the towns and territory of Abya Yala, until now focusing on hacking extractive companies and repressive forces (police and military)” and that they “will never have accounts on social networks.” This hacktivist group is responsible for a string of high-profile attacks targeting governments and corporations in Mexico, Chile, Colombia, Guatemala, and Peru. Echoing Enlance Hacktivista’s blurb, the Telegram channel alluded to in the handle used by the Breach Forums poster has previously claimed to be unaffiliated with the hacktivist collective, according to an announcement published by the group’s administrators in December 2022.
A translation of the Telegram message, which was written in Spanish, reads: “Heads-up, We are not part of the activist group, we are only forwarding PUBLIC INFORMATION, it has already been published on the internet BY THE GUACAMAYA LEAKS GROUP, so it is PUBLIC INFORMATION.” Despite these explicit denials, the Telegram channel uses the ‘https://t.me/guacamayal’ link to direct people to their group, creating the impression of association with the hacktivist collective. Resecurity nevertheless assumes that the operator(s) behind the Breach Forums account and the Telegram group are the same entities. Based on the channel admin’s past statements and the Enlance Hacktivista blurb, Resecurity assesses that the threat actor behind the CiberinteligenciaSV Breach Forums account is not affiliated with the Guacamaya group either. Also, given that the Guacamaya claim to exclusively target “extractive companies and repressive forces (police and military),” the compromise and dump of everyday Salvadoreans’ PII doesn’t align with the stated mission agenda of the group.
Resecurity assesses that the real intellectual authors of this breach appear to have an interest in obscuring their involvement, using the background specter of the Guacamaya group and its unofficial proxies to form a cloud of uncertainty surrounding the real threat actors and attack chain that caused the data leak. Also uncertain is the ultimate source of the leaked data. After the Breach Forums posting, rumors circulated on Twitter (X) that the data exposed in the dump matches the total userbase and related identifiers associated with the Chivo Wallet, “The official Bitcoin and Dollar wallet of the Government of El Salvador.” However, on April 17, 2024, the Ciberinteligencia SV Telegram channel seemed to dismiss those rumors, writing that “we have not made such statements.”
Ultimately, this data leak is significant because it marks one of the first instances in cybercrime history where virtually the entire population of a country has been affected by a compromise of biometric data. A Federal Trade Commission advisory published last year states, “Biometric information refers to data that depict or describe physical, biological, or behavioral traits, characteristics, or measurements of or relating to an identified or identifiable person’s body.” Beyond the massive scale of Salvadorian PII records, threat actors also obtained a headshot of each victim, which represents a crucial biometric data marker – particularly in the golden age of generative AI. Notably, the vast scale of this biometric and PII data breach places most of El Salvador’s population at significant risk for identity theft and fraud. Armed with modern deep fake technology, threat actors can leverage victim headshots and related PII to stage more convincing frauds across a broad universe of digital-first financial, merchant, and government portals.
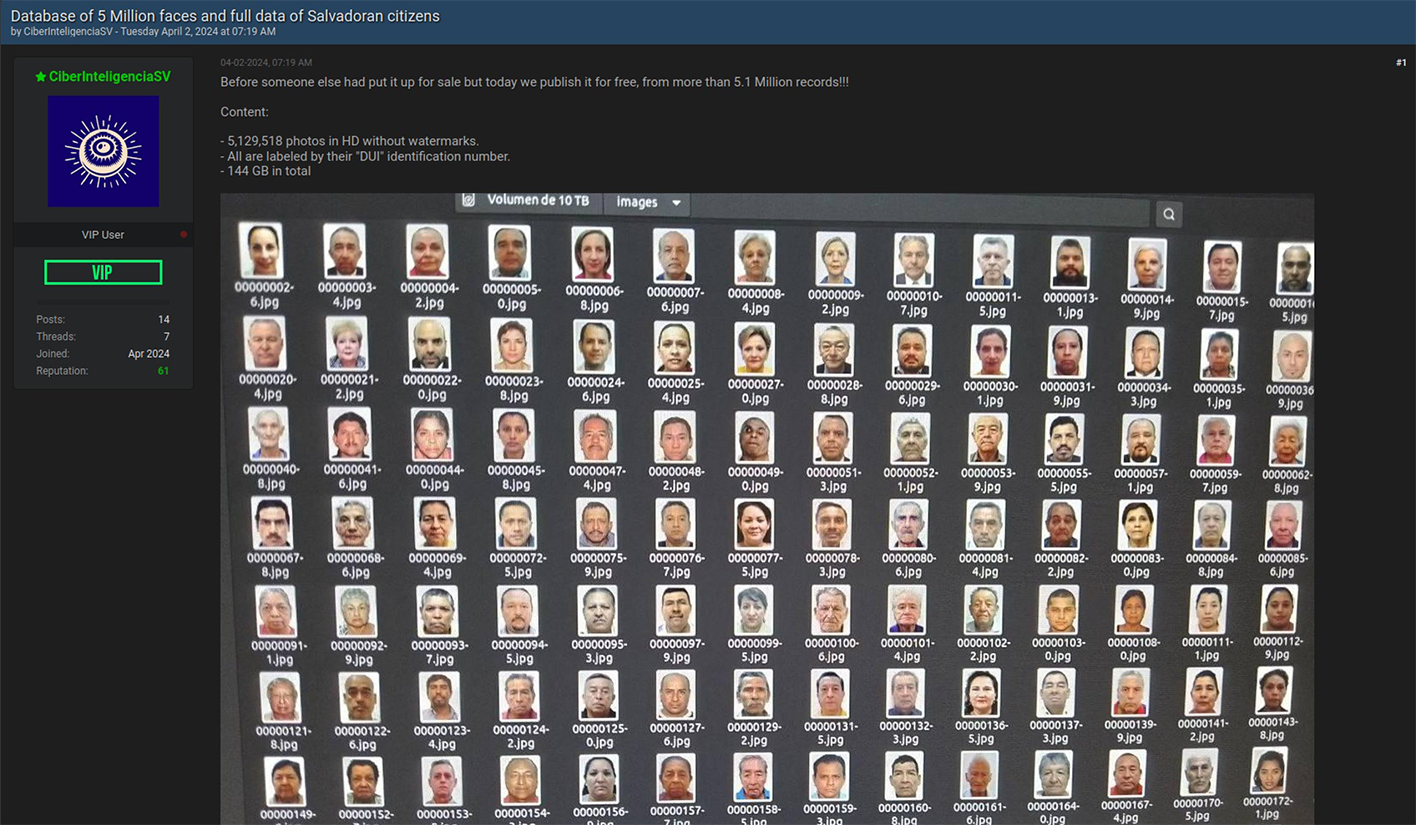
The data dump includes the following fields:
- ID
- Identification document (DUI)
- Names/Last names
- Date of birth
- Telephone
- Email
- Address
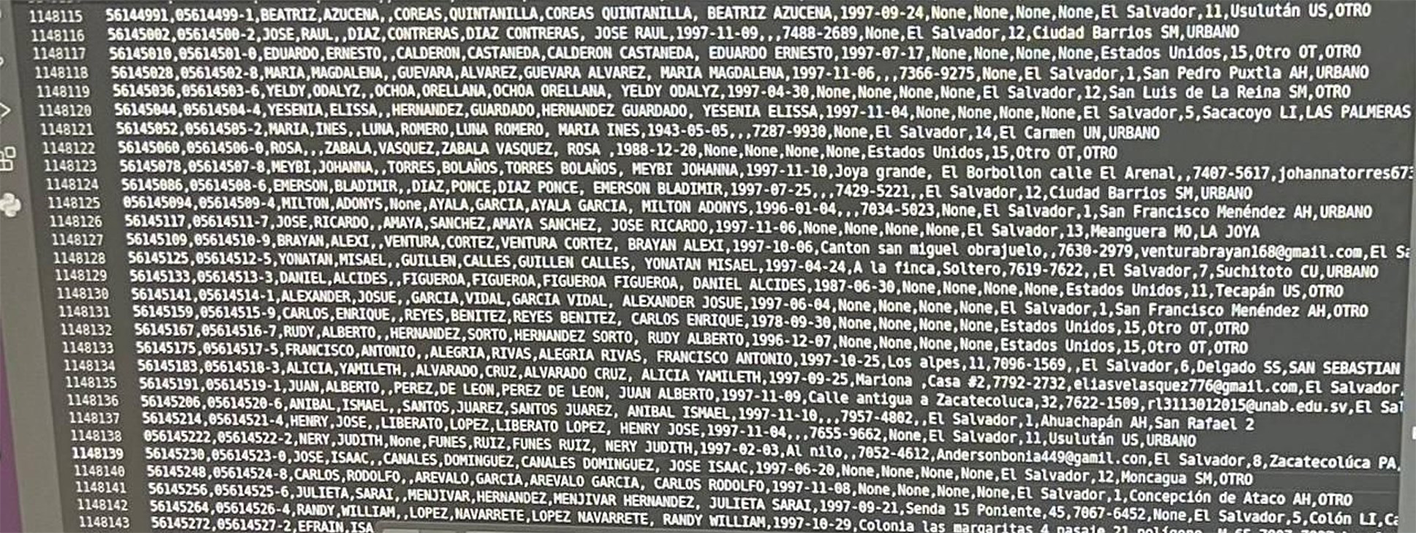
The threat actor CiberinteligenciaSV released a script allowing to match the photo of particular victim, with the related data set containing additional fields including name, national ID, etc.
# instrucciones:
# 1- covertir la db de texto plano a formato de db
# 2- descargar (PyQt5)
# 3- colocar las rutas de lo que pide
# 4- darse un tiro en la cien
import os
import sys
import sqlite3
from PyQt5.QtWidgets import QApplication, QMainWindow, QLabel
from PyQt5.QtGui import QPixmap
class DUIs(QMainWindow):
def __init__(self, n_DUI):
super().__init__()
self.setWindowTitle(f"{n_DUI}.jpg")
img = QPixmap(f"<carpeta donde estan las fotos>/{n_DUI}.jpg")
lb_img = QLabel(self)
lb_img.setPixmap(img)
self.setCentralWidget(lb_img)
def Searth(
DUI=None,
Nombres=None,
Apellidos=None,
Ciudad=None,
Cumpleaños=None,
Telefono=None,
):
# filtro SQL
query = "SELECT * FROM <nombre de la tabla> WHERE 1=1"
if DUI:
query += f" AND DUI like '%{DUI}%'"
if Nombres:
query += f" AND Nombres like '%{Nombres}%'"
if Apellidos:
query += f" AND Apellidos like '%{Apellidos}%'"
if Ciudad:
query += f" AND Ciudad like '%{Ciudad}%'"
if Cumpleaños:
query += f" AND Cumpleaños like '%{Cumpleaños}%'"
if Telefono:
query += f" AND Telefono like '%{Telefono}%'"
conn = sqlite3.connect("<ruta de la db>")
cursor = conn.cursor()
cursor.execute(query)
result = cursor.fetchall()
cursor.close()
conn.close()
if result[0] == "":
print("*** No se encontro la persona")
else:
return ResultDB(result)
def ResultDB(data):
for i in range(len(data)):
dataOne = data[i]
print("####################################################################")
print(f"# Personas Encontradas: {i+1}/{len(data)}")
print(f"# Nombre Completo: {dataOne[8]} {dataOne[7]}")
print(f"# DUI: {dataOne[1]}")
print(f"# Fecha de Nacimiento: {dataOne[9]}")
print(f"# Telefono: {dataOne[12]}")
print(f"# Dirección: {dataOne[10]}")
print(f"# Ciudad: {dataOne[16]}")
print(f"# Pais: {dataOne[14]}")
print("####################################################################")
if len(data) == 1:
if os.path.exists(f"<carpeta donde estan las fotos>/{dataOne[1]}.jpg"):
app = QApplication(sys.argv)
ventana = DUIs(n_DUI=f"{dataOne[1]}")
ventana.show()
sys.exit(app.exec())
else:
print("*** La fotografia no existe")
print("*** Si no sabes un dato, dejalo en blanco")
Searth(
DUI=input("(1/6) Ingresa el DUI (12345678-9): "),
Nombres=input("(2/6) Ingresa los nombres (Jorge Armando): "),
Apellidos=input("(3/6) Ingresa los apellidos (Perez Diaz): "),
Ciudad=input("(4/6) Ingresa la ciudad (San Salvador SS): "),
Cumpleaños=input("(5/6) Ingresa la fecha de nacimiento (1999-12-31): "),
Telefono=input("(6/6) Ingresa el numero de telefono (1234-5678): ")
)
# LiLa :)
Biometric Data in the Crosshairs
Headlined by last year’s sweeping 23andMe hack and leak operation, the mass publication of Salvadorean facial data on the Dark Web coincides with growing threat actor interest in acquiring and monetizing biometric data. Biometric data is particularly valuable to attackers because these digital identifiers are immutable, unlike passwords and pin codes. As previously noted by NordVPN, “the biometrics of your fingerprints or face aren’t supposed to change, so in case of an attack, your identity might be compromised forever.” The FTC advisory warned that the “increasing use of consumers’ biometric information and related technologies, including those powered by machine learning, raises significant consumer privacy and data security concerns and the potential for bias and discrimination.”
The FTC issued this advisory in the wake of a modern information economy that has birthed a proliferation of biometric identity and analytics technologies. Across the public and private sectors, organizations worldwide are increasingly adopting facial, iris, and fingerprint recognition technologies to collect, process, and verify customer, employee, and citizen identities. Other biometric information technologies claim that they can determine a wide array of characteristics specific to a person based on a single biomarker, ranging from a subject’s age, gender, or race to their personality traits, health, aptitudes, or emotional disposition at the point of data capture. Modern use cases for biometric verification and analysis include medical screens, hiring, travel, Know Your Customer (KYC) verification in financial services, and general security checks.
However, consumers face growing risks associated with the institutional collection and use of biometric information. For example, using biometric information technologies to identify consumers in certain locations could reveal sensitive personal information about them, such as the type of medical treatments they received, any religious services they attended, jobs they interviewed for, or their participation in political or labor union meetings. A recent class action lawsuit filed by an Illinois woman against the retailer Target illustrates the growing climate of distrust surrounding biometric data collection. According to Fox Business
reporting, the plaintiff’s suit accuses the “retail giant of collecting and storing her biometric data, including face and fingerprint scans, without her consent in violation of state law.” Growing legal and regulatory risks for organizations that collect biometric data only serve to amplify the appeal of these unique identity records for threat actors. Beyond the higher lifetime value of immutable identity markers, growing regulatory scrutiny over biometric data governance offers another potential pressure point for ransomware actors, which have already weaponized data and privacy protection regulations against victims in the U.S. and Europe.
The Deepfake Threat
In the context of the El Salvador data leak, the vast exposure of facial identity records poses unprecedented fraud and identity theft risks for the country’s citizenry. The key accelerant in this budding fraud onslaught is the rapidly evolving criminal deepfake economy on the Dark Web. In 2022, Resecurity noted the rise of threat actors specializing in the creation of crypto-influencer deepfakes, which could be used to scam members of the Web 3.0 community. At the time, threat actors were focused on using generative AI to forge the likeness of Elon Musk, Vitalik Buterin, and various crypto executives. Since then, there has been a rapid rise in deepfake video-enabled corporate and romance frauds, the most notable being the $25 million business email compromise (BEC) heist in Hong Kong, where a finance worker there was duped by a scammer who skillfully impersonated his employer’s chief financial officer. More concerning than these bulge-bracket corporate fraud scenarios is the rapid pace of innovation and mass accessibility of deepfake and KYC-bypass tooling presented by cybercriminal services like OnlyFake.
First reported by 404 Media earlier this year, OnlyFake was a service that claimed to use ““neural networks” to generate realistic looking photos of fake IDs for just $15, radically disrupting the marketplace for fake identities and cybersecurity more generally.” Joseph Cox, the reporter who broke the story, was able to use an OnlyFake-generated ID to “successfully step through the identity verification process on OKX,” a cryptocurrency exchange. The operator of the OnlyFake service, which shut down after 404 Media’s reporting, also “claimed the generated identity cards could be used on other exchanges, such as Binance and Coinbase.” While subsequent cyber-intelligence vendor research determined that the OnlyFake service was not using generative AI, Resecurity has noted an explosion of adversarial KYC-bypass services that claim to offer the capability hyped by the now-defunct vendor. Thus, the key takeaway from the massive dump of Salvadorean citizens’ headshots is that these facial biomarkers are now at risk of fraudulent misuse in an era transformed by the democratization of access to cybercriminal deepfake services. Over 80% of El Salvador’s population now faces significant risks in the form of biometric identity theft in the furtherance of financial fraud and more diffuse money-mule or laundering conspiracies.
Significance
The massive leak of Salvadorean PII on the Dark Web aligns with a broader geographic trend that has seen cyberattacks targeting LATAM surge to an “all-time high,” according to vendor research. Driving this attack wave is the rapid expansion of digital connectivity throughout the region. According to the International Telecommunication Union, 77.9% of the population in LATAM and the Caribbean used the Internet, “up from 74.8% the year before and above the global rate of 66.3%.” Reuters also reported that nearly “half of Latin American internet users spend an average of six hours a day on social media.”
The LATAM population’s deep online connectivity has significantly amplified their exposure to data theft and cybercrime. Reuters also reported that institutions and governments in LATAM are also more vulnerable than in other parts of the world, citing a survey from fraud prevention firm SEON that found that nine of 10 Latin American countries were ranked in the bottom half of cyber-readiness out of 93 countries they evaluated globally. LATAM also had the “highest share of unprotected data in the world in 2022,” according to Reuters reporting.
In this regional threat landscape, organizations and everyday consumers in LATAM must be vigilant about their digital hygiene and rapidly increasing cyber risks. By harnessing the power of modern cyber-threat intelligence (CTI), Salvadoreans and broader LATAM consumer populations can mitigate malicious risks associated with their PII and biometric data falling into the hands of cybercriminals. The use of a robust CTI tool can empower people in the LATAM region with a 360-degree view of their Dark Web data footprint, arming them with the knowledge they need to avoid becoming victims of financial fraud and identity theft. To learn more about how enterprise and retail customers in LATAM can protect their digital identities, Resecurity can help.
References
- FTC Warns About Misuses of Biometric Information and Harm to Consumers
- The politics and power of Latin American hacktivists Guacamaya
https://cyberscoop.com/guacamaya-hacktivist-group-latin-america-interview/

