Hunting Genetics Data - Cyberespionage In The Context Of Geopolitical Conflicts
Cyber Threat Intelligence


The hack and leak of genetic data belonging to direct-to-consumer DNA testing company 23andMe in early October highlights growing threat-actor interest in this biomolecular class of personal information. In December, the company said that the threat actor behind the breach accessed “less than 0.1%, or roughly 14,000 user accounts, of the existing 14 million 23andMe customers through credential stuffing.”
However, the attacker used these compromised accounts to access the information included in a significant number of 23andMe “DNA Relatives profiles (approximately 5.5 million) and Family Tree feature profiles (approximately 1.4 million), each of which were connected to the compromised accounts.” Altogether 6.9 million 23andMe users were impacted by the breach. The threat actor did not manage to exfiltrate DNA records in this intrusion, according to media reports.
Instead, 23andMe explained in a blog post that the DNA Relatives profiles connected to the compromised accounts “consist of information that a customer chooses to make available to their genetic relatives when they opt in to participate in 23andMe’s DNA Relatives feature.” A DNA Relatives profile includes data like “display name, predicted relationships, and percentage of DNA shared with matches.”
The23andMe data leak coincides with the emergence of a modern bioinformatics marketplace where genetic data has become increasingly valuable. Today, Genetic data is more frequently being solicited and operationalized by 23andMe and similar firms to enhance modern medical diagnostic and treatment offerings. Genetic-data-powered research and development thus promises a transformative new era of hyper-personalized medical care. But attackers with varying motivations are also seeking to cash in on or exploit the rising ‘bull’ market for DNA data.
Dark Web Hype
The buzz around the 23andMe breach started on October 1st, when a threat actor using the handle “Golem” leaked 20 million pieces of genetic data on Breach Forums, a leading cybercriminal hub. 23andMe later confirmed the data in this leak belonged to its customers. The original thread, “DNA Data of Celebrities,” was deleted, but another forum member who goes by “Addka72424” reposted it on October 2nd. On October 4th, Golem cited 23andMe as the source of the leak in a since-deleted forum thread.
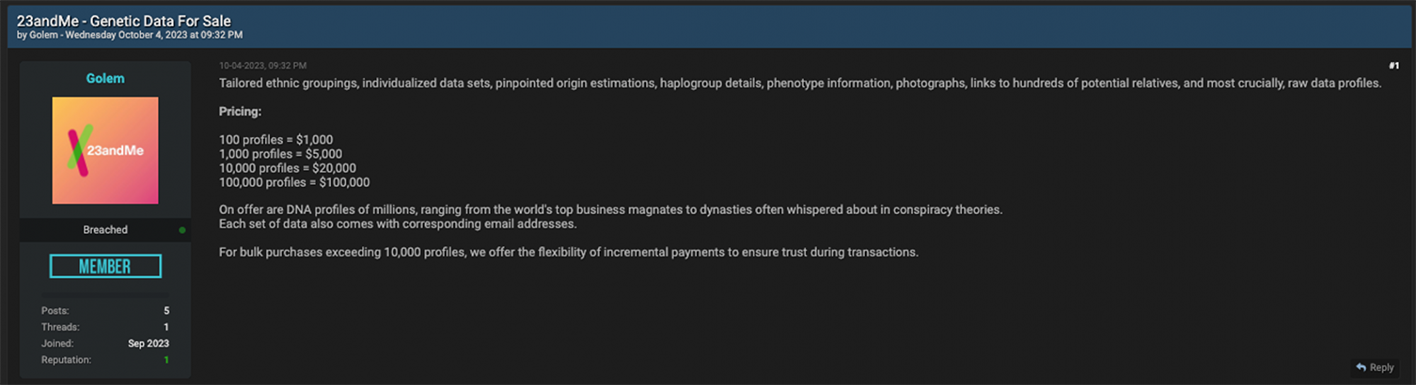
DNA records exposed in this leak include “tailored ethnic groupings, individualized data sets, pinpointed origin estimations, haplogroup details, phenotype information, photographs, links to hundreds of potential relatives, and most crucially, raw data profiles,” according to the thread description. Beyond the record types being promoted, Golem also noted that he could offer access to the “DNA profiles of millions, ranging from the world's top business magnates to dynasties often whispered about in conspiracy theories.”
Golem’s statements appear to be at odds with the company’s statements about the depth of the data stolen. While the threat actor claims to have exfiltrated millions of DNA profiles, BBC reported that “the stolen data does not include DNA records.” Regardless TechCrunch, which broke news on 23andMe's December “blast-radius” update, reported that they “analyzed the months-old leaked data” and “found that some records matched genetic data published online by hobbyists and genealogists.”
TechCrunch noted that the “two sets of information were formatted differently, but contained some of the same unique user and generic data, suggesting the data leaked by the hacker was at least in part authentic 23andMe customer data.” Based on the amount of DNA profiles purchased, Golem’s pricing schedule ranged from $1,000 to $100,000, or $10 per profile.
While Golem’s October thread catalyzed a media storm surrounding the incident, it should be noted that a threat actor using the alias Dazhbog first leaked 300 terabytes of genetic data allegedly swiped from 23andMe on Hydra Market two months earlier. On August 11, Dazhbog posted a since-deleted threat titled, “23andMe DNA – the world’s most valuable data”, on a relaunched version of the cybercriminal forum Hydra Market.
Dazhbog was offering to sell 300 TB of 23andMe data for $50 million. The threat actor also said that “this company and similar ones are prohibited from operating in our country.” Dazhbog also said that “all data for a buyer living in China will be delivered on 16 disks, each with a capacity of 20 TB.”
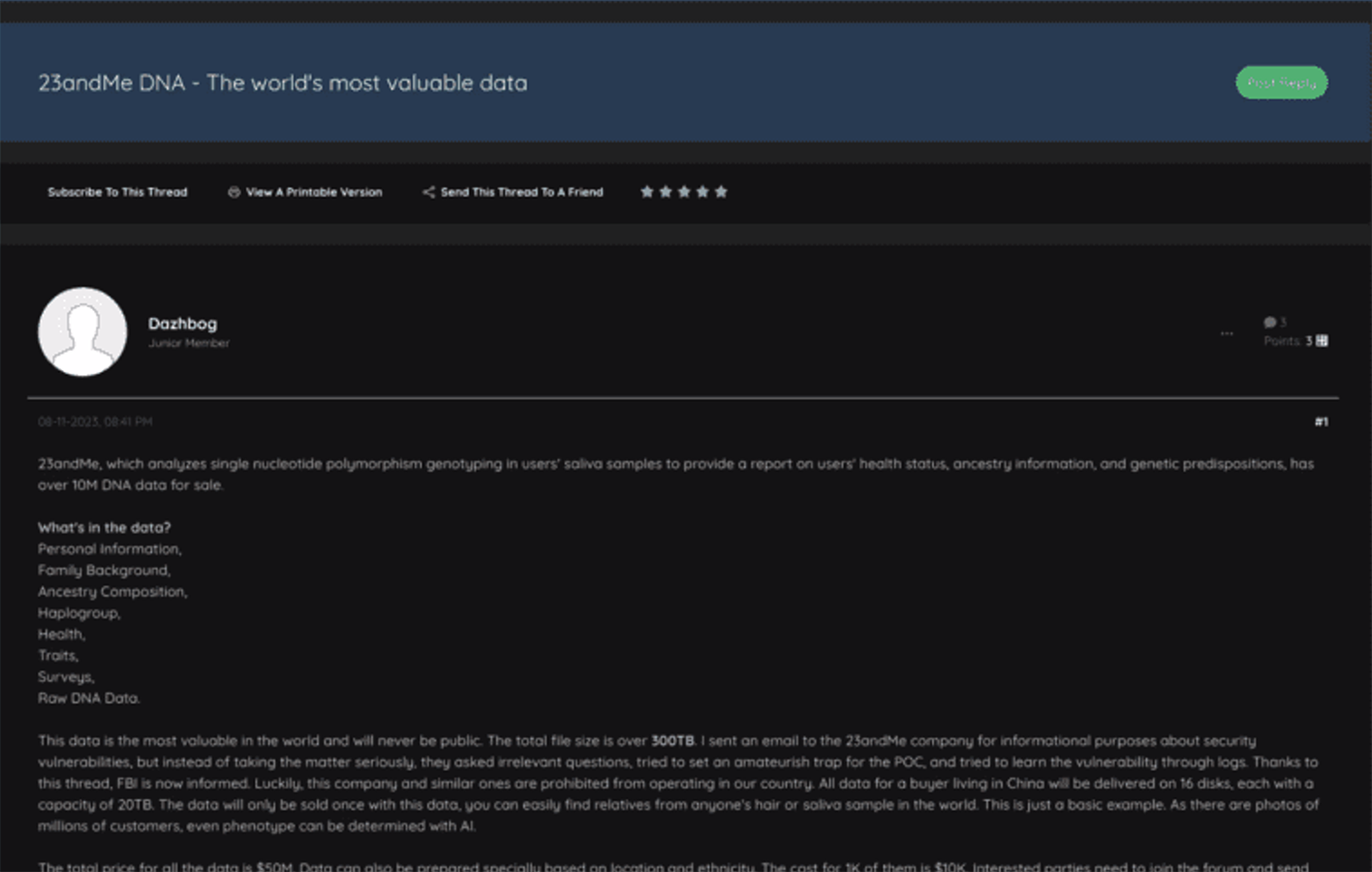
On August 12, Dazhbog also provided a sample of genetic data for one million 23andMe customers in the U.S., noting the leak contained the DNA profiles of 10 million Americans.
The threat actor also claimed the data was swiped via an API service used by pharmaceutical companies. It is not immediately clear what API service Dazhbog was referring to, but in 2019, 23andMe announced it was piloting an initiative to collect more health data beyond DNA profiles from millions of its users. To operationalize this data-collection initiative, 23andMe partnered with a “third-party medical data network called Human API,” according to CNBC reports.
The partnership between 23andMe persisted until at least October 2020, according to media reports published at that time. But a reference document on Human API’s website currently notes that the “genotypes endpoint has been deprecated by 23andMe,” meaning new data “will not be retrievable.” However, users of this service “who provided access to their 23andMe account and had genetic data available via Human API will still have that data available through genetic/traits,” according to the reference document.
On the same day Dazhbog posted their 23andMe thread, they wrote a follow-up comment saying, “I realized that the most crucial part of the data is invalid(false positive). That's why I can't make any sales. I thought it would be better to update the post since some users wrote it.”
Yet on August 14, Dazhbog authored another post on their thread claiming that they sold the 23andMe data to an Iranian national. The threat actor also requested that their post be deleted from the forum. Notably, it is unusual for threat actors to publicize the nationality of their buyers. Furthermore, the alias Dazhbog, is a curious choice for a threat actor. The name is a reference to an obscure pre-Christian Slavic sun God. It is also noteworthy that both Dazhbog and Golem invoked mythological references in their username registrations. However, it is not known with any degree of certainty whether these threat actors are the same person.
Technically not a Security Breach?
the Northern District of California, plaintiffs are suing 23andMe for “negligence, breach of implied contract, invasion of privacy and unjust enrichment,” according to the court filing. The lawsuit says that victims’ following personally identifying information (PII) and personal health information (PHI) are now in the “hands of criminal hackers”: Names, sex, date of birth, genetic ancestry results, profile photos, and geographical location.
Meanwhile, the most significant regulatory development to emerge from this breach, is the October 30 letter Connecticut Attorney General William Tong wrote to 23andMe’s general counsel. “We understand that the 23andMe breach has resulted in the targeted exfiltration and sale on the black market of at least one million data profiles pertaining to individuals with Ashkenazi Jewish heritage,” said the letter.
The letter also noted that a “subsequent leak has revealed the data of hundreds of thousands of individuals with Chinese ancestry, also for sale on the dark web as a result of this hack. The increased frequency of antisemitic and anti-Asian rhetoric and violence in recent years means that this may be a particularly dangerous time for such targeted information to be released to the public.”
For 23andMe the most legally problematic charge made in the Connecticut AG’s letter is that the company has not yet “submitted a breach notification pursuant to Connecticut’s breach notification statute, Conn. Gen. Stat. § 36a-701b.” “While we understand that this breach may
have been the result of a “credential stuffing” attack, the notice triggers in our breach notification statute expressly include email address and password information,” noted the letter.
Fortunately, for the company Connecticut breach notification law affords compromised organizations 60 days to file a report with the state regulator after an identified cyber incident where customer data is exposed. But the breach also “calls into question 23andMe’s compliance with the Connecticut Data Privacy Act (“CTDPA”), Conn. Gen. Stat. § 42-515 et seq.,” according to the letter.
The letter notes that the “CTDPA provides Connecticut consumers with important rights over their personal data and imposes corresponding privacy and data security obligations on controllers and processors of personal data.” This leak of genetic data thus “raises questions about the processes used by 23andMe to obtain consent from users, as well as the measures taken by 23andMe to protect the confidentiality of sensitive personal information,” according to the letter.
The Connecticut Attorney General’s office has given 23andMe a November 13 deadline to answer 14 detailed questions about the breach and their policies and procedures as they pertain to security, user privacy, and user consent. Regardless, this regulatory development is a bellwether for the rising enforcement power being sought out and exercised by a growing number of state regulators.
While state-level enforcement power has most frequently been leveraged by cybersecurity regimes like the California Consumer Privacy Act (CCPA), the New York Department of Financial Services' (NYDFS) Cybersecurity Regulation, and the New York’s Stop Hacks and Improve Electronic Data Security (SHIELD) Act, the California Attorney General’s bold entrance into this fracas is likely a harbinger of things to come. The 23andMe incident may be a seminal event for balkanized multi-state regulatory inquires into breaches.
Golem Refutes 23andMe’s Breach Narrative
While all threat actors’ post-breach commentary should be taken with a grain of salt, Golem shredded the company’s initial narrative about the intrusion. On October 18th, Golem responded to a new, related thread they posted the previous day, writing the following:
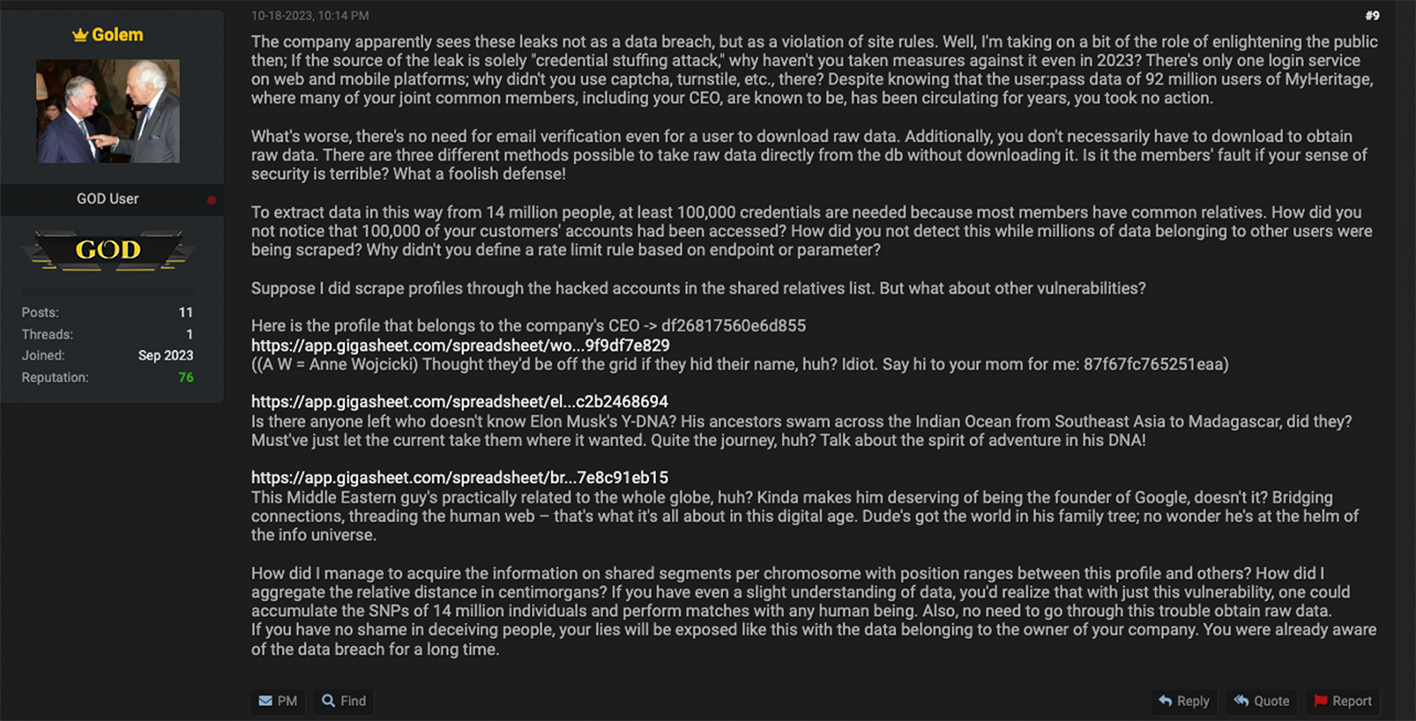
“The company apparently sees these leaks not as a data breach, but as a violation of site rules. Well, I’m taking on a bit of the role of enlightening the public then; If the source of the leak is solely “credential stuffing attack,” why haven’t you taken measures against it even in 2023? There’s only one login service on web and mobile platforms; why didn’t you use captcha, turnstile, etc., there? Despite knowing that the user:pass data of 92 million users of MyHeritage, where many of your joint common members, including your CEO, are known to be, has been circulating for years, you took no action.”
Golem further elaborated on why they believe the company is misrepresenting the truth, writing:
“What's worse, there's no need for email verification even for a user to download raw data. Additionally, you don't necessarily have to download to obtain raw data. There are three different methods possible to take raw data directly from the db without downloading it. Is it the members' fault if your sense of security is terrible? What a foolish defense!
To extract data in this way from 14 million people, at least 100,000 credentials are needed because most members have common relatives. How did you not notice that 100,000 of your customers' accounts had been accessed? How did you not detect this while millions of data belonging to other users were being scraped? Why didn't you define a rate limit rule based on endpoint or parameter?”
After claims of doxing genetic profiles related to Google CEO Sergei Brin, Tesla and SpaceX CEO Elon Musk, and 23andMe CEO Anne Wojcicki, Golem concluded their comment thread with the following legally inconvenient analysis of the DNA-testing company’s security’s practices:
“How did I manage to acquire the information on shared segments per chromosome with position ranges between this profile and others? How did I aggregate the relative distance in centimorgans? If you have even a slight understanding of data, you'd realize that with just this vulnerability, one could accumulate the SNPs of 14 million individuals and perform matches with any human being. Also, no need to go through this trouble obtain raw data.
If you have no shame in deceiving people, your lies will be exposed like this with the data belonging to the owner of your company. You were already aware of the data breach for a long time.”
While Golem’s provocative comments project an air of credibility that will likely be weaponized by the plaintiffs’ attorneys suing 23andMe, cybercriminals are not good-faith actors. As such, the cybersecurity community should approach Golem’s hot legal takes with caution until a professional third-party investigation of the 23andMe breach has been completed.
In the backdrop of the escalating war between Israel and Hamas, Golem’s initial 23andMe thread, posted on October 1st, also exploits related geopolitical hostilities with an explicit antisemitic bias. Golem vociferously promoted DNA data particular to Ashkenazi Jews in their seminal Breach Forums thread.
Ashkenazis in the Crosshairs
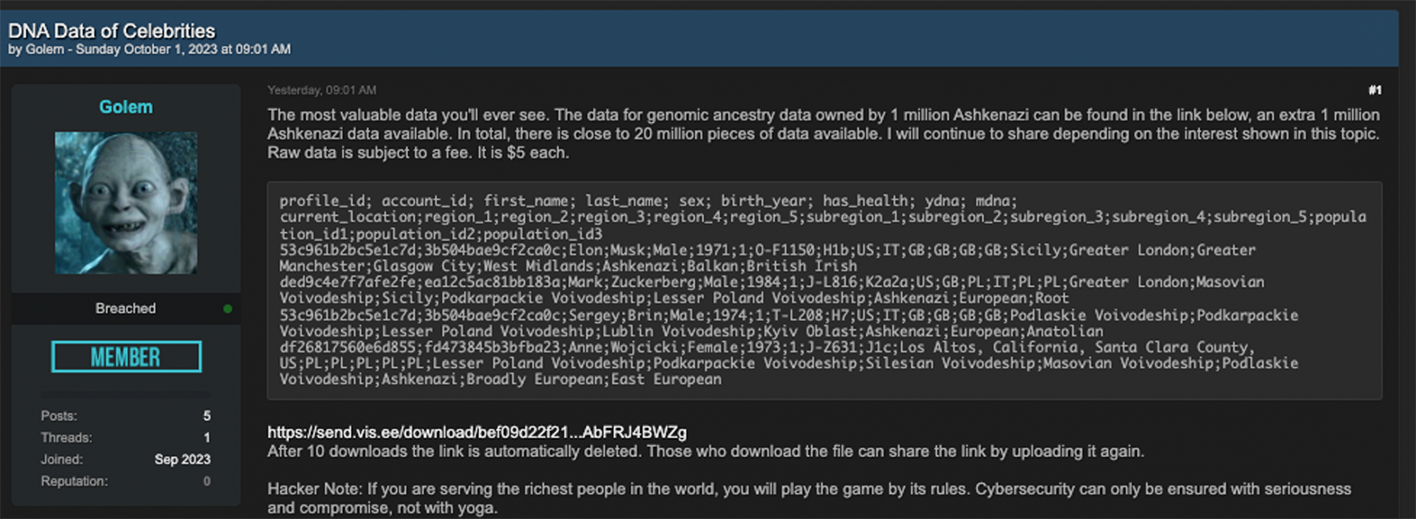
“The most valuable data you'll ever see. The data for genomic ancestry data owned by 1 million Ashkenazi can be found in the link below, an extra 1 million Ashkenazi data available. In total, there is close to 20 million pieces of data available. I will continue to share depending on the interest shown in this topic. Raw data is subject to a fee. It is $5 each.”
Ashkenazis are a subset of the Jewish diaspora who trace their ancestry back to Central or Eastern Europe. In Israel, Ashkenazi Jews are often framed as the most elite caste of the country’s society, a stereotype that was even officialized by the Central Intelligence Agency in a 1982 intelligence assessment.
According to the CIA report, “the dominance of Israel’s government and economy by Ashkenazi Jews is largely attributable to their early sizeable immigration to Palestine and their organization and leadership of all the major prestate public and private institutions.” The leading catalysts for this early sizeable migration of Ashkenazi Jews to pre-state Israel, were a series of violent Russian pogroms. Pogrom is a term that was used to describe the wave of “anti-Jewish riots that swept the southern and western provinces of the Russian Empire in 1881–1884, following the assassination of Tsar Alexander II.”
Regardless, Golem’s explicit and prejudicial targeting of Ashkenazi 23andMe users is further conveyed by the threat actor’s use of “The Lord of the Rings” motion-picture Golem’s hideous face as their profile photo. The antisemitic animus is noteworthy given the recent outbreak of war in Gaza. The vicious Hamas invasion and civilian massacres transpired just six days after Golem publicized the DNA data leak on Breach Forums.
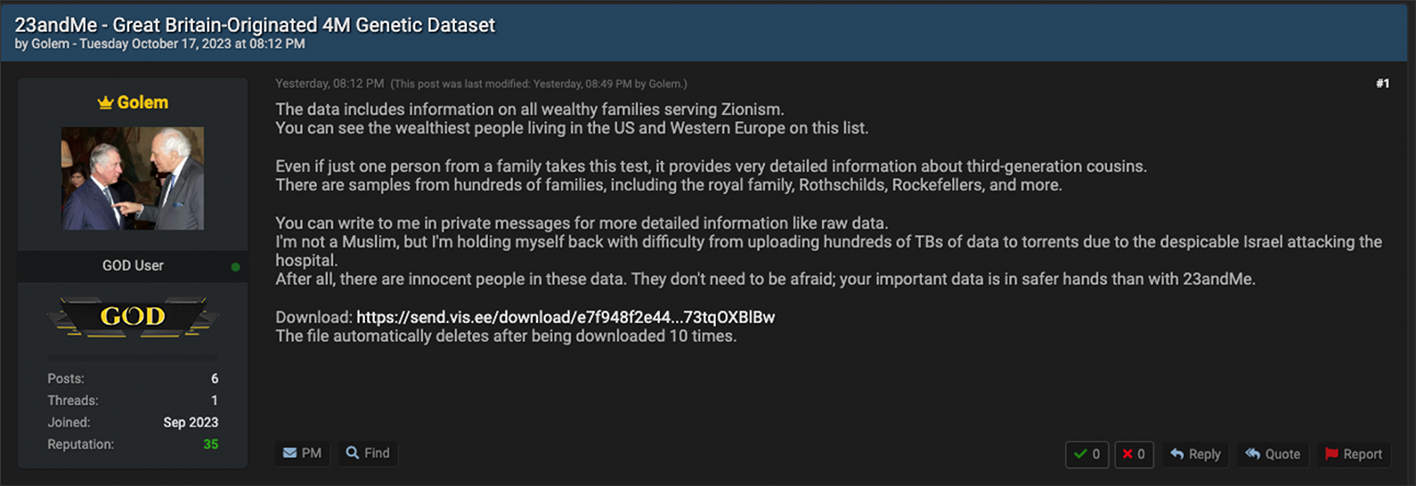
On October 17, Golem posted another thread titled “23andMe – Great Britain-Originated 4M Genetic Dataset” that expounded on their apparent antisemitic mission agenda. In the thread description, Golem writes: “The data includes information on all wealthy families serving Zionism. You can see the wealthiest people living in the US and Western Europe on this list.”
“Even if just one person from a family takes this test, it provides very detailed information about third-generation cousins. There are samples from hundreds of families, including the royal family, Rothschilds, Rockefellers, and more,” continues Golem’s thread.
Likely, besides the antisemitic bias, the bad actor tried to generate attention to significance of the data leak by leveraging names of world-recognized business elites and leaders.
Golem also concluded his thread writing the following disclosure: “I'm not a Muslim, but I'm holding myself back with difficulty from uploading hundreds of TBs of data to torrents due to the despicable Israel attacking the hospital. After all, there are innocent people in these data. They don't need to be afraid; your important data is in safer hands than with 23andMe.” In this comment, Golem is referring to the October 17 hospital blast in Gaza that killed 500 Palestinians.
The hospital strike has been variously attributed to an Israeli airstrike by many in the Arab world, or to a “failed rocket launch
by the Palestinian Islamic Jihad militant group” Hamas by Western leaders. Hamas has denied that they were responsible for the hospital bombing. Meanwhile, President Joe Biden pledged solidarity with Israel and their account of the hospital strike.
Adding to the geopolitical intrigue is another comment posted by Golem on October 18th where they say that German Chancellor “Olaf Scholz is darkening the future of Germans by serving Zionism.”
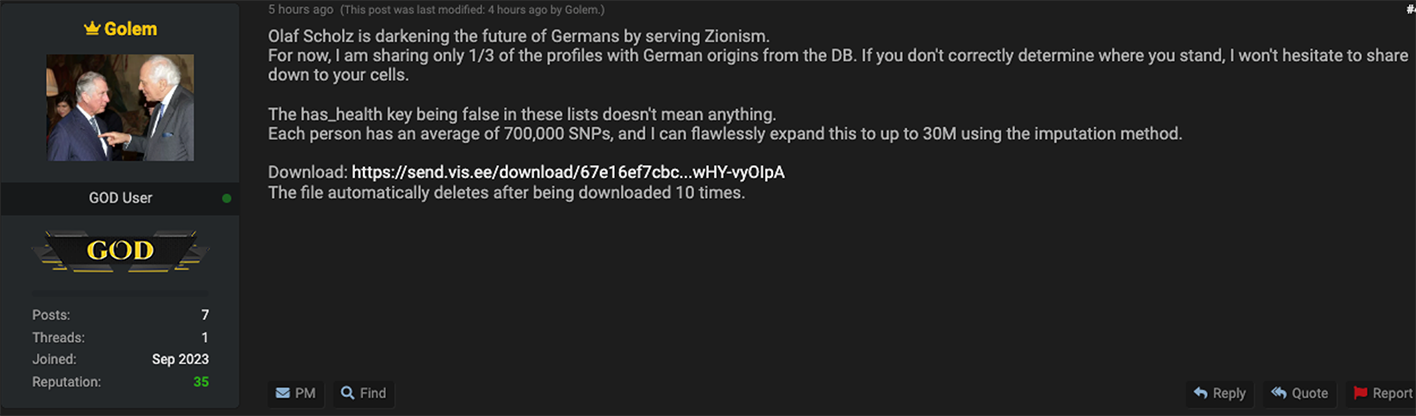
It is notable that Golem authored this comment one day after Chancellor Scholz visited Tel Aviv and held a press conference
with Israeli Prime Minister Benjamin Netanyahu.
Also worth highlighting is the registration date of the Golem account. This threat actor registered the Golem Breach Forums account on September 30, a day before they leaked the 23andMe data. In the context of the escalating war in Gaza, the account registration date is significant as it overlaps with the execution date for the #OpIsrael and #FreePalestine hacktivist propaganda campaigns flagged by Resecurity in an earlier report.
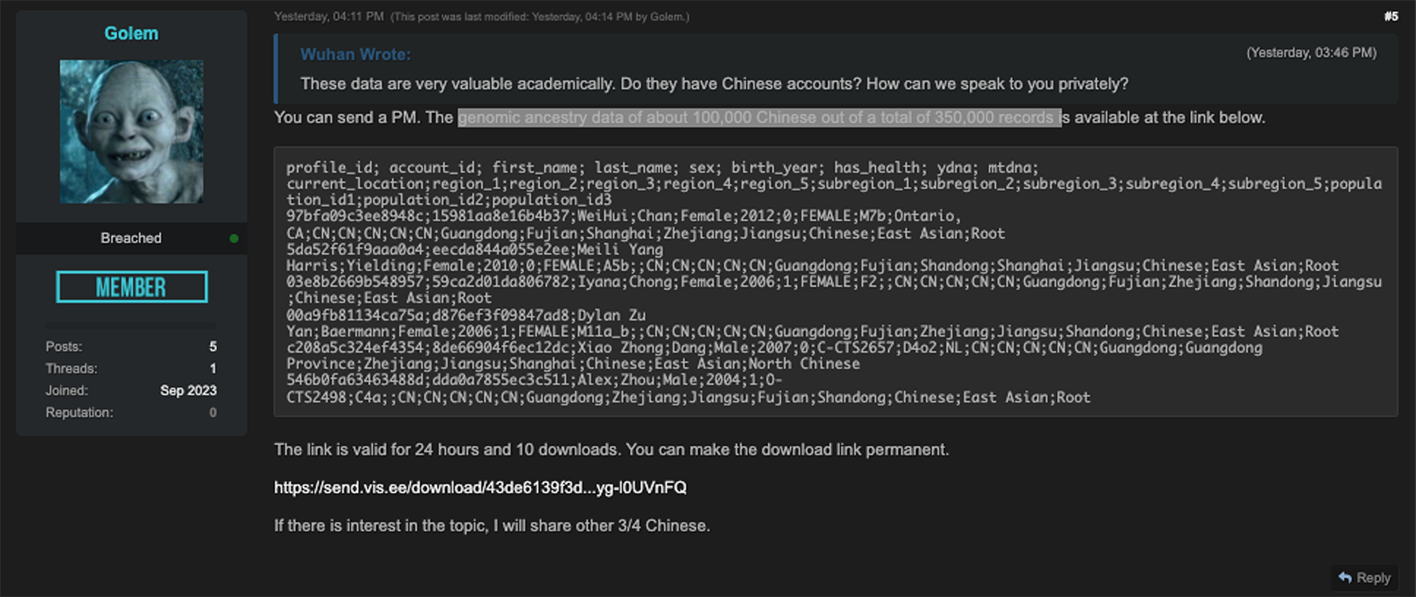
However, Resecurity has not confirmed any coordination or cooperation between the Golem account and other related malicious cyber-activity related to the evolving war in Gaza. At this stage, these events can only be described as coincidental, despite their shared geopolitical significance. Beyond Ashkenazi 23andMe users, Golem also claimed to have access to the “genomic ancestry data of about 100,000 Chinese out of a total of 350,000 records.” Golem made this claim following an inquiry about Chinese data made by Breach Forums user ‘Wuhan.’
More Gaza-Nexus DNA Hacks
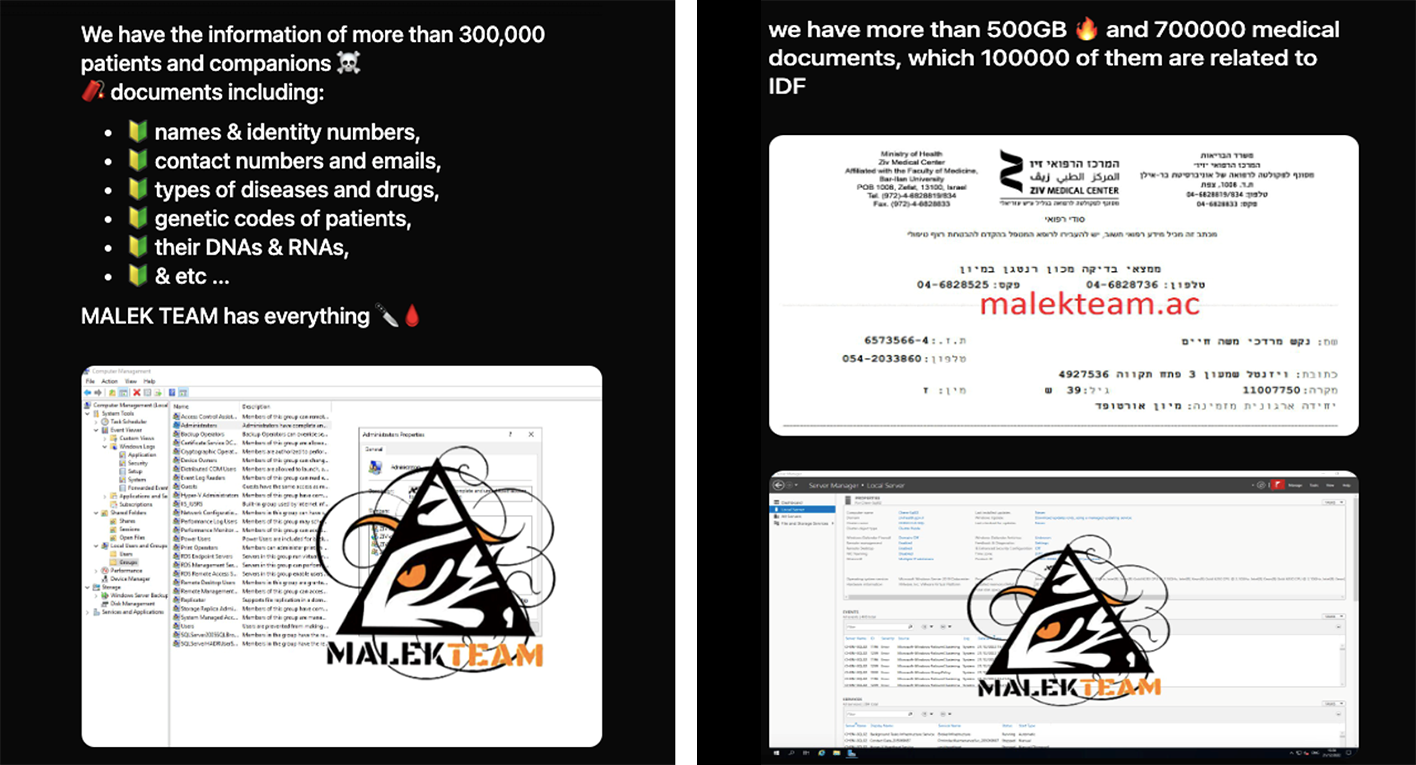
As the news cycle surrounding the 23andMe hack has slowed down, Iran-linked hackers Malek Team recently made headlines with their compromise of Ziv Medical Center in Safed, Israel on December 3rd. On their clear-web leak site, the threat actors announced that they had stolen the “information of more than 300,000 patients and companions.”

Included in this data seizure are “more than 500GB and 700000 medical documents, which 100,000 of them are related to IDF.” The IDF are the Israel Defense Forces, the country’s national military. Notably, Malek Team claims that among the data assets they stole are the “genetic codes of patients,” including their DNAs and RNAs.
In the backdrop of the Israel-Hamas war, it is significant that threat actors are focusing their efforts on the theft of genetic data.
Significance
The 23andMe data leak is an unprecedented breach that represents the most significant hack of DNA-related data ever. The explicit ethnic bias targeting Ashkenazi Jews expressed by the leaker – and its overlap with a historic eruption of military conflict in Israel and Gaza – is too big of a coincidence for the international Intelligence Community (IC) to ignore. This concurrence, combined with similarities in the execution date of related anti-Israel hacktivist propaganda campaigns and the account registration date for the Golem account, also merit further investigation.
These coincidences have been thrust into even sharper focus by the recent theft of Israeli patient DNA data from Ziv Medical Center by Iran-nexus hacktivists Malek Team. Thus, the theft and potential manipulation or weaponization of genetic data has rapidly evolved into a new dimension of warfare in the 21st Century. The 23andMe and Ziv Medical Center cyberattacks have collectively pried open a Pandora’s box of DNA-enabled attack scenarios.
In the emerging era of genetically personalized health care and mRNA vaccines, IC and military leaders must consider antithetical scenarios where threat actors might weaponize DNA traits specific to an ethnic group to target them with bioengineered microbes. Specifically, the open-sourcing of ethno-specific genetic profiles could enable certain threat actors, especially those backed by rogue nation-states, to produce gain of function (GoF) viruses or bacteria targeting a defined group.
A blueprint for this attack vector is illustrated by a 2020 National Library of Medicine research paper titled “New insights into genetic susceptibility of COVID-19: an ACE2 and TMPRSS2 polymorphism analysis.” Less harmful than ethno-specific GoF pathogens are scenarios where hostile intelligence services mine genetic data to identify a target’s unknown or willfully hidden relatives.
By unearthing a target’s full family tree threat actors of this nature can plot peripheral attacks to harm or otherwise compromise the person they are pursuing. This attack scenario could also be useful for asset seizure purposes. For example, adversaries could use genetic data to identify an unknown relative who is sheltering a target’s assets in their name.
Other forms of state-sponsored or private-sector espionage involving genetic data might entail attackers discovering a hereditary disorder or a predisposition to that condition that disqualifies a target from employment. For example, say two candidates are competing for a high-powered job. If one of those candidates were to mine the genetic data of their rival and discover a predisposition to an early-onset gene disease, they could find a way to get that person disqualified from consideration. A similar tactic could be used to undermine candidates in political races.
One additional attack vector genetic data creates just by the mere virtue of its existence, and now its mass exposure in the cybercriminal underground, is misrepresentation via deep fakes.
Take the attack vectors discussed in the previous paragraph, for example, and imagine threat actors faking their target’s genetic profile data with the aim of disqualifying them from employment or otherwise harming them.
Golem and Malek Team have pioneered a new era of data compromise. In the wake of the 23andMe and Ziv Medical Centers breaches, Resecurity anticipates that threat actor interest in this specialized class of personally identifying information (PII) will increase significantly.

