API Security: The Importance of Vulnerability Assessment and Penetration Testing (VAPT)
Compliance


In today's digital landscape, the integrity of an organization’s cybersecurity posture is more critical than ever. A recent settlement between the Federal Communications Commission (FCC) and TracFone Wireless, Inc. underscores the dire consequences of inadequate security measures. TracFone, a subsidiary of Verizon Communications Inc., faced a hefty $16 million fine due to severe lapses in protecting customer data. This case highlights a crucial lesson for all organizations: the significance of implementing robust Vulnerability Assessment & Penetration Testing (VAPT) practices to prevent similar breaches.
The TracFone Incident: A Costly Lesson in API Vulnerabilities
The FCC's investigation into TracFone stemmed from three significant data breaches between January 2021 and January 2023. These breaches were a result of malicious actors exploiting vulnerabilities in TracFone's application programming interfaces (APIs), which allowed unauthorized access to sensitive Customer Proprietary Network Information (CPNI) and personal data. This not only led to the unauthorized transfer of customers' mobile numbers to other carriers—a practice known as port-out fraud—but also to the exposure of critical customer information.
The breaches occurred because TracFone failed to implement adequate security measures to protect against unauthorized access, violating multiple sections of the Communications Act and the FCC's CPNI Rules. The repercussions were severe, with TracFone not only facing the financial penalty but also being mandated to overhaul its information security program, particularly concerning API security.
Why VAPT is Essential for Protecting Digital Assets
The TracFone case serves as a stark reminder of why Vulnerability Assessment & Penetration Testing (VAPT) is indispensable in today’s cybersecurity strategy. VAPT involves a comprehensive evaluation of an organization’s digital infrastructure to identify and address vulnerabilities before malicious actors can exploit them. Here’s why VAPT is so critical:
- Identifying and Mitigating Vulnerabilities: VAPT helps in discovering both known and unknown vulnerabilities within your digital ecosystem, including those in APIs, web applications, and networks. By proactively identifying these weaknesses, organizations can address them before they lead to data breaches or other security incidents.
- Simulating Real-World Attacks: Penetration testing, a key component of VAPT, involves simulating real-world cyberattacks on an organization’s systems. This helps in understanding how attackers could potentially exploit vulnerabilities, allowing organizations to strengthen their defenses accordingly.
- Ensuring Compliance with Regulatory Standards: As demonstrated by the TracFone case, failure to comply with regulatory standards can result in severe penalties. Regular VAPT assessments help organizations meet industry regulations and avoid costly fines and legal actions.
- Building Customer Trust: In an era where data breaches are becoming increasingly common, customers expect companies to safeguard their personal information. Regular VAPT assessments demonstrate a commitment to security, helping to build and maintain customer trust.
Resecurity’s Approach to VAPT
At Resecurity, we understand the complexities of modern cybersecurity challenges. Our VAPT services are designed to provide a thorough evaluation of your organization’s security posture, identifying and addressing vulnerabilities across your digital infrastructure.
- Comprehensive Vulnerability Assessments: Our team conducts in-depth assessments to uncover vulnerabilities in your systems, including those in APIs, web applications, networks, and more. We classify these vulnerabilities based on their severity and provide actionable recommendations to mitigate risks.
- Penetration Testing: Resecurity’s penetration testing services simulate sophisticated cyberattacks to test the resilience of your security defenses. This not only helps in identifying potential entry points for attackers but also in evaluating the effectiveness of your existing security measures.
- Continuous Support: Cybersecurity is not a one-time effort. After conducting VAPT assessments, Resecurity offers ongoing support to ensure that your organization maintains a robust security posture. This includes regular reassessments, security updates, and continuous monitoring to address emerging threats.
API Security
In today's interconnected digital landscape, Application Programming Interfaces (APIs) have become the backbone of modern software development. They enable communication between different software systems, allowing them to share data and functionality seamlessly. As organizations increasingly rely on APIs to integrate applications, power mobile apps, and connect to cloud services, the security of these APIs has become a critical concern. With APIs often serving as gateways to sensitive data and essential services, they have become prime targets for cyber attackers. Ensuring the security of APIs is therefore paramount to protecting an organization’s digital assets and maintaining trust with users and partners.
What is API Security ?
API security refers to the practice of protecting the integrity, confidentiality, and availability of APIs. It involves implementing measures to prevent unauthorized access, data breaches, and other malicious activities that can exploit vulnerabilities in an API. API security encompasses various techniques and strategies, such as authentication, authorization, encryption, and monitoring, to ensure that only legitimate users and systems can interact with the API.
APIs can be exposed to several security risks, including injection attacks, broken authentication, excessive data exposure, and inadequate logging and monitoring. To mitigate these risks, organizations must adopt a comprehensive API security strategy that considers both the development and deployment stages of an API. This includes conducting thorough security assessments, implementing robust access controls, and continuously monitoring API activity to detect and respond to threats in real time. API security is not a one-time task but an ongoing process that evolves with the changing threat landscape and the API’s lifecycle.
Examples of API Misconfigurations Discovered by the Resecurity Hunter Team
During our pentesting projects at Resecurity, our Hunter Team has identified a variety of API misconfigurations that expose organizations to risk. These findings highlight the importance of adhering to security best practices throughout the API development and deployment process.
1. Account Takeover Vulnerability in Finance Mobile Application
During our penetration testing of a finance mobile application, we uncovered a critical vulnerability that facilitates account takeover through the password reset functionality. Specifically, the API handling the password reset process inadvertently leaks the verification code within the API request. This flaw allows an attacker to intercept or access the verification code without proper authorization. Consequently, the attacker can reuse the leaked verification code in the subsequent step to successfully reset and change any user's password. This vulnerability poses a significant security risk, as it grants unauthorized access to sensitive user accounts, potentially leading to financial fraud, data breaches, and loss of user trust. To mitigate this issue, it is essential to ensure that verification codes are securely transmitted and not exposed in API requests, implement robust authentication and authorization mechanisms, and enforce strict validation checks during the password reset process.
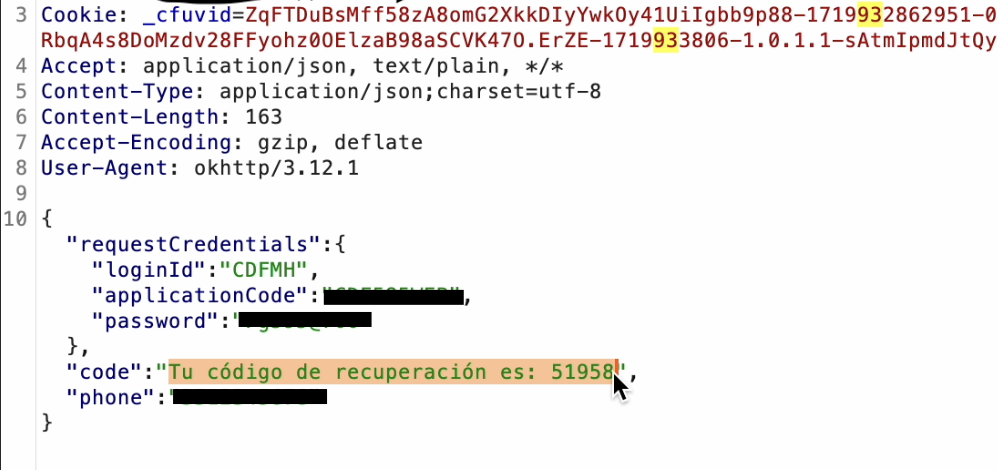
2. PII Data Exposure via Unsecured API Endpoint
In one of our pentest projects, we uncovered a serious vulnerability where an API endpoint was leaking personally identifiable information (PII) of all users. The exposed data included sensitive details such as email addresses, passwords, and other personal information. This API endpoint, which lacked proper access controls, returned this critical data without verifying the identity or authorization of the requester.
This flaw allowed anyone with access to the endpoint to retrieve the complete set of user data, posing a significant privacy risk and opening the door to further attacks, such as identity theft, credential stuffing, and phishing. The exposure of passwords in plaintext is particularly alarming, as it compromises not only the affected accounts but potentially other accounts where users may have reused the same password.
To address this issue, it is essential to implement strict access controls and ensure that only authenticated and authorized requests can retrieve sensitive data. Additionally, sensitive information such as passwords should never be exposed via APIs and must always be stored and transmitted securely using strong encryption methods.
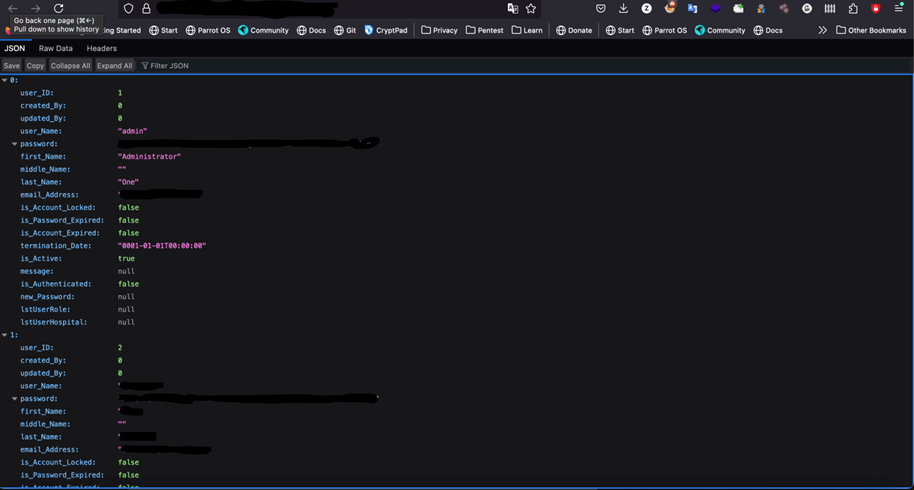
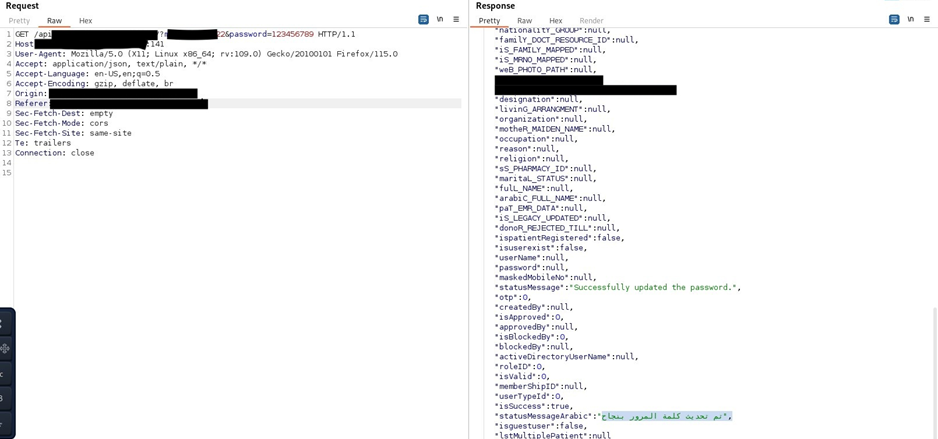
3. IDOR Vulnerability Allowing Password Change via User ID in API Endpoint
In another pentest project, we discovered a significant Insecure Direct Object Reference (IDOR) vulnerability within an API endpoint that allowed unauthorized password changes. The issue arose because the API used a user ID parameter to identify accounts during password reset requests, without properly validating the requesting user's permissions.
An attacker could exploit this vulnerability by manipulating the user ID in the API request, enabling them to change the password of any user in the system. This flaw bypassed the intended security controls, granting attackers the ability to take over accounts simply by altering the user ID in their request.
To mitigate this vulnerability, it is essential to enforce strict access controls and ensure that the API verifies the identity of the requesting user before processing actions that affect other users' accounts. Additionally, using indirect references (e.g., tokens) instead of direct user IDs in API requests can further enhance security and prevent unauthorized access.
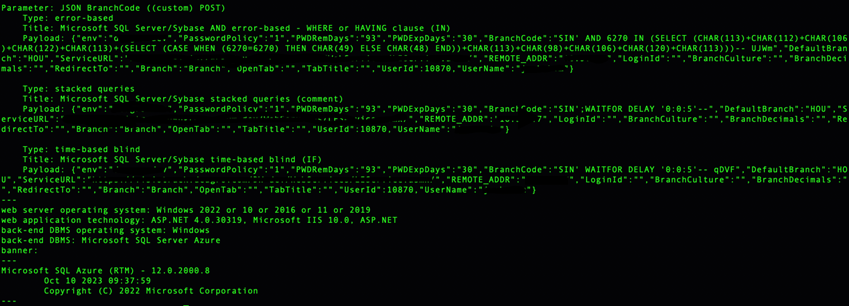
4. SQL Injection in API’s
During our security assessments, we discovered multiple SQL injection vulnerabilities across various API endpoints due to inadequate input sanitization. These flaws allowed attackers to inject malicious SQL code through user inputs, potentially compromising the database by extracting, modifying, or deleting sensitive data. Exploiting these vulnerabilities could lead to unauthorized access to customer information, financial records, or confidential business data. The business impact includes significant financial losses from fraud or remediation efforts, reputational damage due to loss of customer trust, and potential regulatory penalties for failing to protect sensitive information. Addressing these issues is crucial for ensuring data integrity, maintaining operational stability, and upholding regulatory compliance.
5. BOLA (Broken Object Level Authorization) IDOR Vulnerability
During our security assessments, we identified numerous BOLA (Broken Object Level Authorization) IDOR (Insecure Direct Object Reference) vulnerabilities across several API endpoints. These vulnerabilities arose because the APIs lacked proper authorization checks, allowing unauthorized users to manipulate object identifiers in their requests. As a result, users could access or modify data that belonged to other users, such as personal details, account settings, or confidential information.
The impact of these vulnerabilities includes severe privacy breaches, where sensitive user data is exposed or tampered with. This can lead to significant legal and regulatory repercussions, damage to the organization’s reputation, and a loss of user trust. Addressing these BOLA IDOR vulnerabilities is crucial to ensure that access controls are correctly enforced and to protect the integrity and confidentiality of user data.
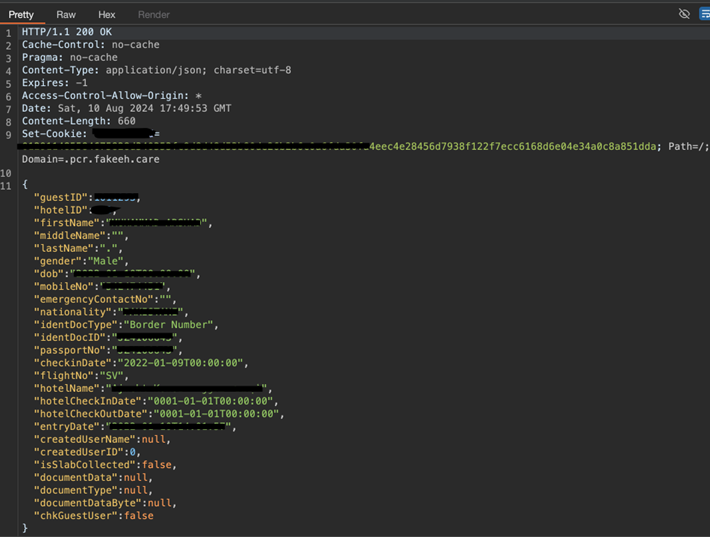
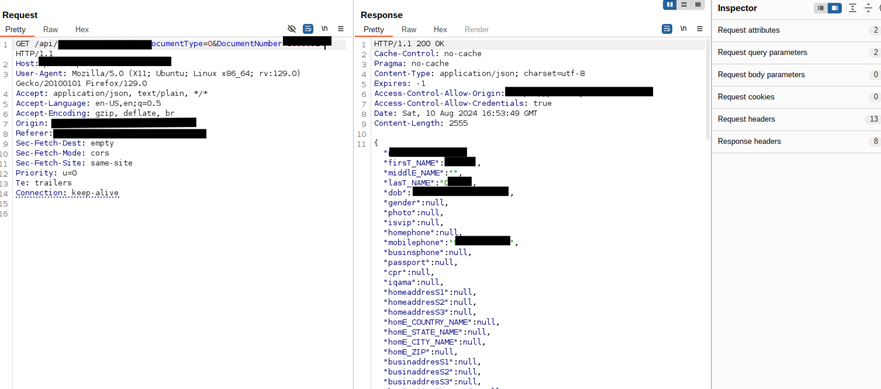
6. Lack of Rate Limiting in Mobile App API Leading to User Enumeration
During our security assessments, we identified a significant issue with the mobile app's API due to the lack of rate limiting controls. This vulnerability allowed attackers to send an excessive number of requests to the API fuzzing users ID's, enabling them to enumerate mobile app users and access personally identifiable information (PII). Without rate limits, attackers could systematically probe the API to retrieve sensitive user data, such as email addresses, names, and other personal details.
The ability to enumerate users and access their PII poses serious risks, including privacy breaches and identity theft. This vulnerability can be exploited for further attacks, such as credential stuffing, phishing, or social engineering. The business impact includes compromised user privacy, potential regulatory penalties, and damage to the organization's reputation. Implementing robust rate limiting and monitoring mechanisms is crucial to prevent such enumeration attacks and safeguard user data from unauthorized access.
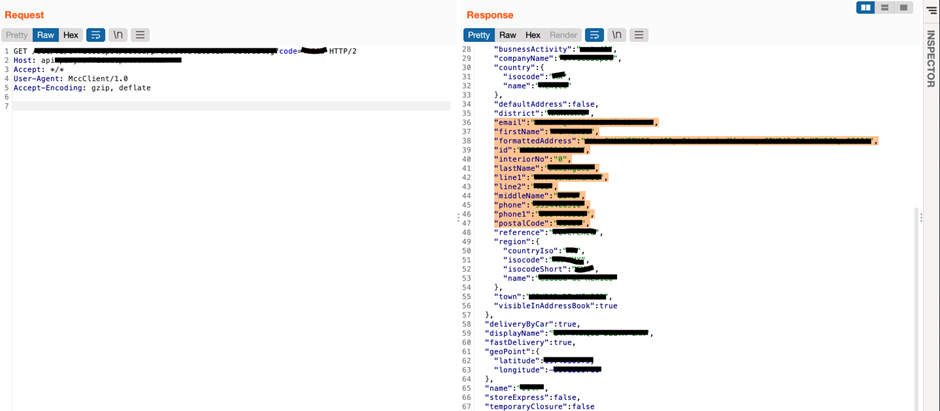
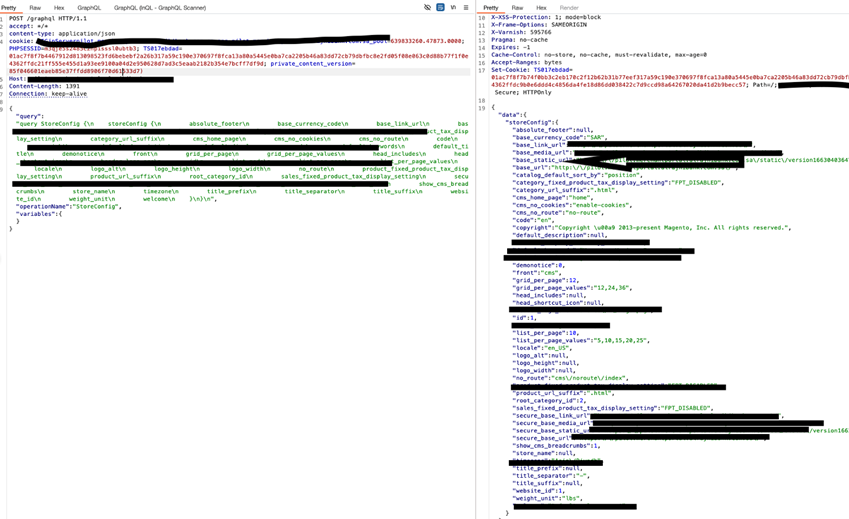
7. Multiple GraphQL Vulnerabilities Due to Enabled Introspection
During our security assessment, we uncovered numerous GraphQL vulnerabilities, primarily due to introspection being enabled in the production environment. This allowed attackers to view the entire schema, including all queries and mutations, revealing sensitive internal functions. With this information, attackers could craft targeted queries to extract internal data that should have been restricted, such as system configurations, sensitive user information, and operational details.
The impact of these vulnerabilities is severe, as exposing the API’s internal structure increases the risk of data leaks, unauthorized access to core functionalities, and further exploitation. Disabling introspection in production and implementing strict access controls are critical to securing GraphQL APIs and protecting sensitive data.
Conclusion
API security is a critical aspect of modern cybersecurity, especially as organizations increasingly rely on APIs to connect services, share data, and facilitate digital transformation. The examples of vulnerabilities discovered by the Resecurity Hunter Team highlight the importance of thorough security assessments and the need to follow best practices when developing and deploying APIs. From account takeover risks to sensitive data leaks and unauthorized access, the potential impact of insecure APIs can be severe, leading to financial losses, reputational damage, and regulatory penalties.
By understanding these risks and implementing robust security measures, organizations can better protect their APIs from exploitation and ensure the integrity, confidentiality, and availability of their systems. This research underscores the importance of continuous vigilance in API security and serves as a reminder that securing APIs is an ongoing process that requires regular updates, monitoring, and testing.
Contact Us
Do you have questions regarding the security assessment of your API’s ? Please, don't hesitate to contact our team who are certified information security and application security professionals holding the following industry certifications:
- Certified Ethical Hacker (CEH)
- Offensive Security Certified Professional (OSCP)
- GIAC Web Application Penetration Tester (GWAPT)
- Certified Penetration Tester eXtreme (eCPTX)
- Web Application Penetration Tester (eWPT)
- Web Application Penetration Tester Extreme (eWPTXv2)
- Certified Professional Penetration Tester (eCPPTv2)
- Attify Certified IoT Security Pentester (ACIP)
- Mobile Application Penetration Tester (eMAPT)
- Certified Red Team Professional (CRTP)
- CREST Registered Penetration Tester (CRT)
- CREST Practitioner Security Analyst (CPSA)

