Millions of Undetectable Malicious URLs Generated Via the Abuse of Public Cloud and Web 3.0 Services
Cyber Threat Intelligence


Cybercriminals continue to evolve their arsenal of tools and find new ways to scale global phishing campaigns. Building on our 2022 research into the ‘EvilProxy’ Phishing-as-a-Service (PhaaS) attack kit, Resecurity recently observed an evolution in phishing tooling that leverages Fully Undetectable (FUD) Links. The rise of this PhaaS technique is a novel byproduct of leading cyberattack trends, namely the growing exploitation of public cloud services like GitHub and Web 3.0 data-hosting platforms built on the InterPlanetary File System (IPFS) protocol. Unfortunately, these services enable attackers to host and automate phishing kits and other malicious activity by harvesting URLs generated by cloud platforms en masse, rendering their infectious links undetectable by leading email providers.
Resecurity estimates that underground “FUD Links” services collectively generate a minimum of 25,000 – 30,000 malicious URLs per month (per service), totaling 0.5M - 0.7M per quarter. Of course, this number could be much higher, considering adversaries regularly use FUD Links in their day-to-day operations, ranging from phishing and spam campaigns to scams and online fraud.
Beyond phishing, FUD Links can also be operationalized for malicious payload delivery (as the emerging GitHub attack campaign illustrates), surveillance, spam, and Black Hat SEO (the exploitation of search engine guidelines to generate higher search rankings). Victims of these attacks do not easily recognize these public cloud-harvested URLs as suspicious due to the prevailing whitelist controls implemented by most email providers. Existing anti-spam and anti-phishing solutions fail to flag public cloud-generated domains as malicious, instead relying on domain reputation data. The problem is that URLs generated on widely used cloud platforms are inherently scored as low risk by most email security filters.
Ultimately, these phishing kits manipulate the programmatic risk-scoring controls of anti-spam and anti-phishing firewalls to drive phishing campaigns on an unparalleled scale. The hyper-scalability of these malicious campaigns enables attackers to increase the delivery rate of phishing emails and malware campaigns. In addition to the high volume of malicious emails, the use of cloud provider-generated URLs helps attackers avoid detection. In cybercriminal slang, threat actors call these types of URLs “FUD Links.” The FUD feature has traditionally been associated with malware that can evade recognition by prevailing anti-virus solutions. The abuse of public cloud services to automate the mass generation of maliciously forged, high-authority domain URLs represents a new development in adversarial tradecraft.
In the past, threat actors leveraged URL shortening services, a technique that was most notably used in the phishing attack against Hillary Clinton’s campaign chairman John Podesta in 2016. It’s important to note that malicious URL shortening still falls under the broader FUD Link typology. However, network operators and enterprise security teams quickly caught on to these schemes and started to flag these URLs as potentially risky. Threat actors adapted to this defensive pivot and implemented a creative approach leveraging so-called “infinite subdomain misuse,” a term coined by Microsoft in a 2021 report.
In their report, Microsoft described this technique as an attack that occurs when threat actors “compromise a website’s DNS or when a compromised site is configured with a DNS that allows wildcard subdomains. “Infinite subdomains” allow attackers to use a unique URL for each recipient while only having to purchase or compromise one domain for weeks on end.” Microsoft cited the activity of a threat-actor group called BulletproofLink that generated over 300,000 URLs for phishing campaigns hosted on the hacked websites of victim companies and individuals oblivious to the malicious activity emanating from their infrastructures.
BulletproofLink provided this PhaaS capability to over 1,618 Dark Web actors, serving as a launch pad for their phishing campaigns. Unfortunately, the infinite-subdomain approach requires significant effort from threat actors in terms of acquiring access, reconfiguring DNS settings, maintaining the infrastructure, and managing the phishing kit. In some cases, more sophisticated actors employed Domain Generation Algorithms (DGAs) to reduce the burden of maintaining adversarial infrastructures. Both the infinite subdomain and the DGA scenarios have remained extremely popular with threat actors, as these methods are still effective in making phishing URLs less detectable.
But FUD Links represent the next step in PhaaS and malware-deployment innovation. As an example of the latter attack scenario, one recent malicious campaign, which leveraged the Rhadamanthys Stealer to target the oil & gas sector, used an embedded URL that exploited an open redirect on legitimate domains, primarily Google Maps and Google Images. This domain-nesting technique makes malicious URLs less noticeable and more likely to entrap victims.

Challenge for Enterprise Security Teams – Would you rather ban Azure, AWS, and Dropbox?
Threat actors have found stealthier ways to generate “FUD Links,” presenting a greater challenge to enterprise security teams. Resecurity has observed a spike in Dark Web actors offering “FUD Links” that actively abuse popular public cloud and data-hosting platforms such as GitHub, Azure, Amazon Web Services (AWS), Dropbox, along with related Content Delivery Networks (CDNs). The URLs generated by these underground services are widely used in the infection chains of major malware and ransomware campaigns and phishing operations.
Trust & Safety teams are having a hard time tracking this relentless wave of malicious activity. Besides phishing, attackers weaponize platforms like Github, for example, to deploy malware payloads. In fact, threat intelligence data collected by Resecurity revealed that GitHub is the most frequently abused data-hosting platform. These findings dovetail with a wave of emerging news reports detailing an ongoing attack campaign that is flooding GitHub with millions of malicious forked code repositories.
According to Ars Technica, “these repositories contain obfuscated malware that steals passwords and cryptocurrency from developer devices.” The news outlet also said that these “malicious repositories are clones of legitimate ones, making them hard to distinguish to the casual eye.” An unknown party has automated this forgery process, enabling the campaign to scale to the extent that it has overwhelmed GitHub’s ability to detect the malicious automation of repository forks.
Beyond GitHub, the domain names of the other providers noted above are typically ‘whitelisted’ by default, as their cloud services are widely used by enterprises worldwide. By exploiting cloud provider’s domain reputation, threat actors effectively spread malicious content and evade detection by network security solutions. Attackers employ the same approach with other prominent cloud-based services and resources associated with leading domain names, as indicated by their rankings on Alexa, the comprehensive list of the world's most-visited websites. Threat intelligence and domain reputation-based feeds typically exclude these web resources from their malicious infrastructure feeds.
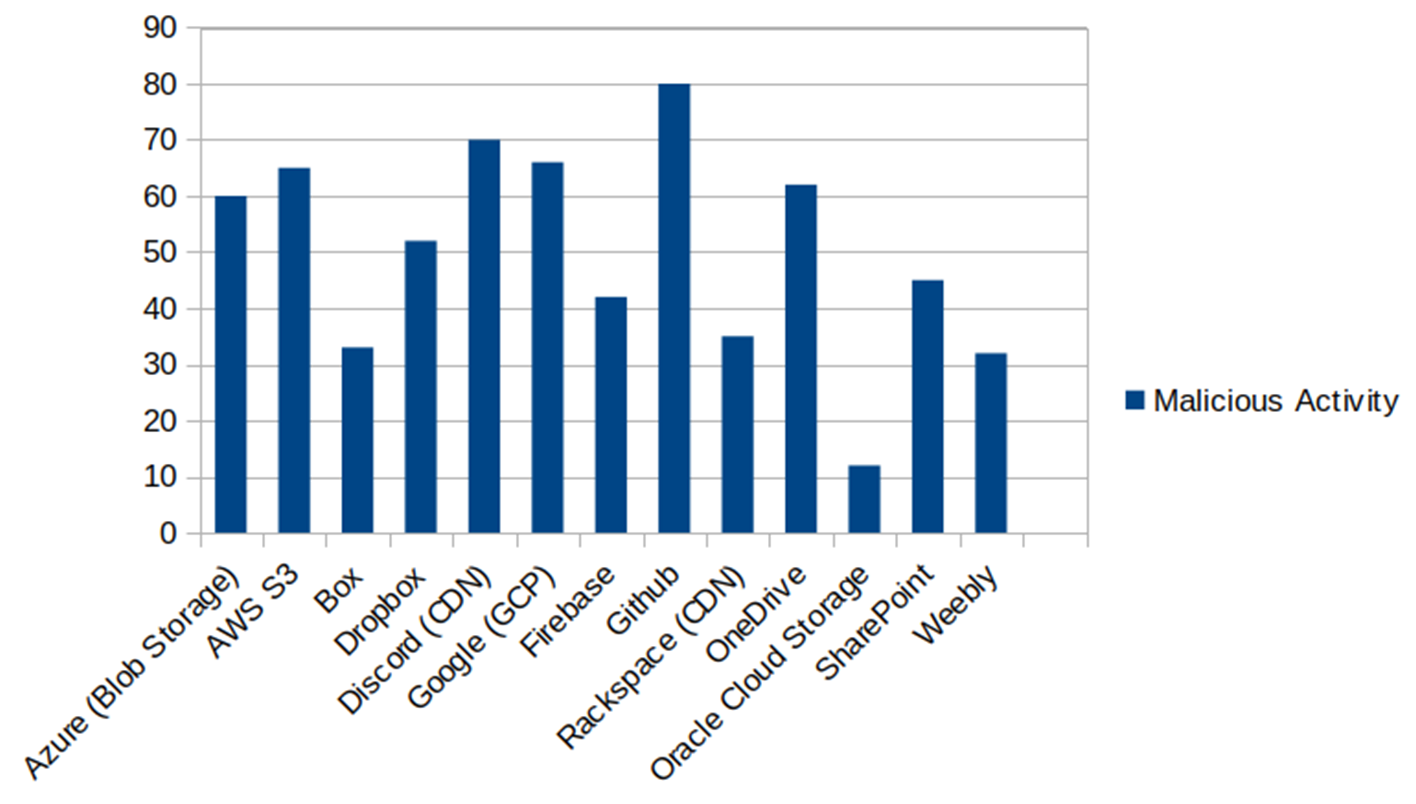
Attackers pounce on this loophole, repurposing high-reputation infrastructure for malicious use-cases. While cybersecurity researchers attempt to track these malicious URLs, the massive scale of FUD Link campaigns creates a latency loop that makes it difficult to neutralize adversarial campaigns in a timely fashion. The rapidly unfolding GitHub campaign is a prime example of how detection systems can be overwhelmed by malicious mass-automated campaigns. Based on the investigation of multiple incidents, Resecurity’s threat intelligence team has acquired over 101,743 URLs (in Q1) generated by underground services that specialize in providing FUD Links.
According to data compiled by Resecurity the most abused cloud platforms are:
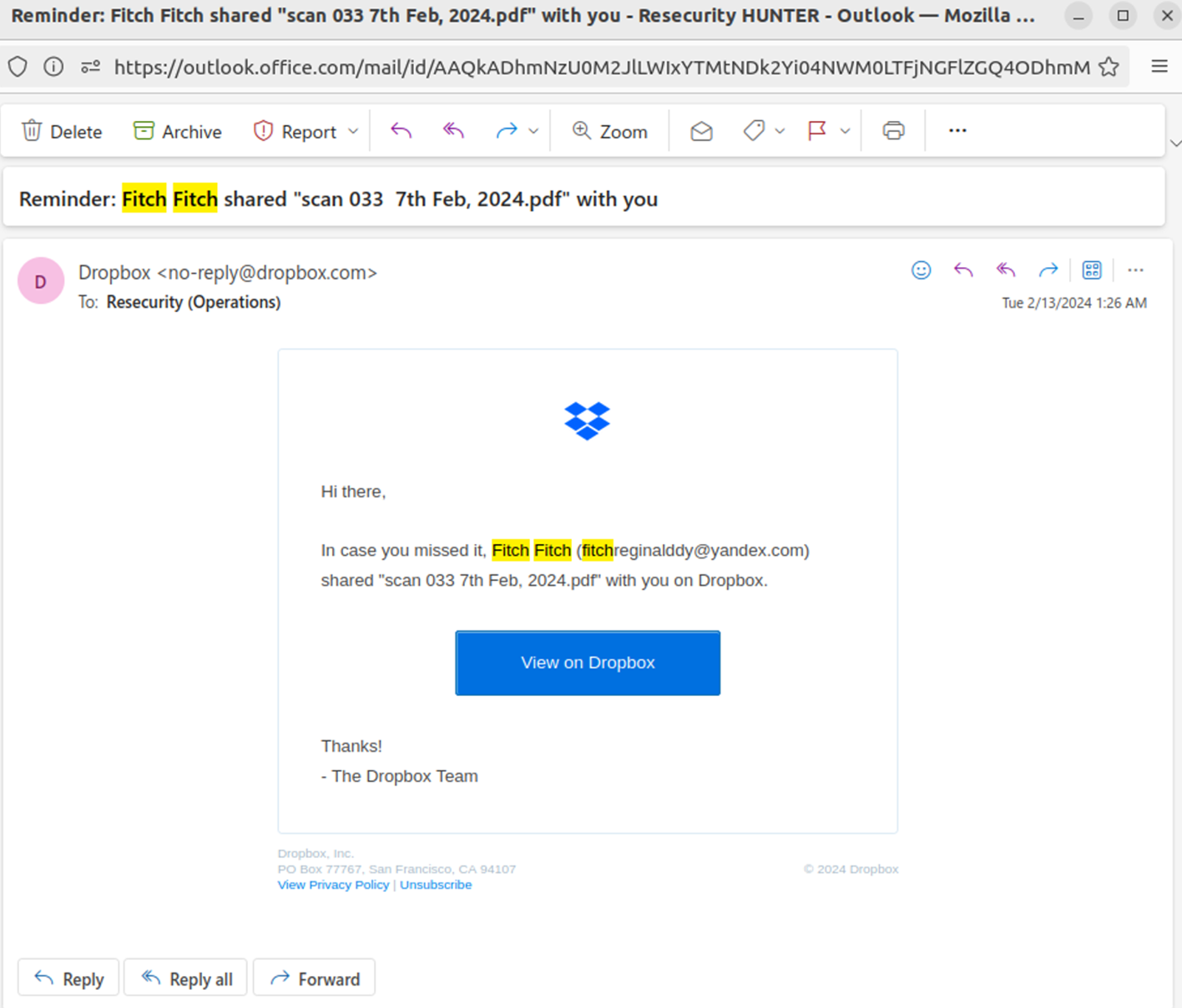
In one of Resecurity’s recent Digital Forensics & Incident Response (DFIR) engagements with a Fortune 100 company, we investigated the account compromise of their Chief Financial Officer (CFO) and multiple employees of the firm’s accounting team. During this probe , Resecurity identified a notable PDF decoy received by the victims that mimicked a document sent by a legitimate investment bank. Attackers shared the document via Dropbox and successfully delivered it to the victim’s inbox, bypassing anti-spam filters and other e-mail security guardrails used by the company. Threat actors employed these tactics to create a more effective phishing lure that would be more likely to dupe the victim into interacting with the sham business document tripwired with a malicious URL.
https://www.dropbox.com/l/scl/AAAC0LXEoSjvFO3CDpKfxvbGPftiOGbSuFs
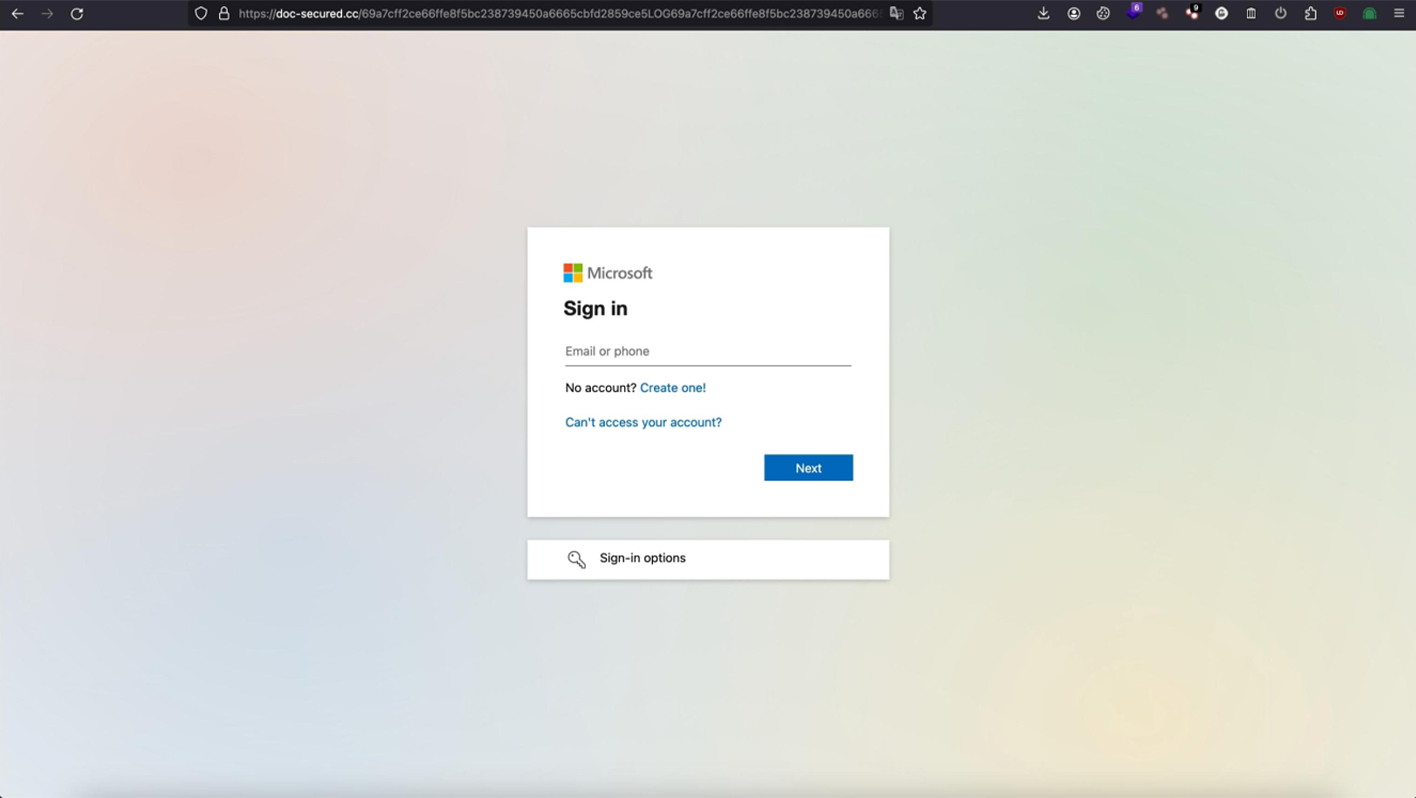
The decoy document contains an “Access File” button that leads to a phishing kit hosted on a “doc-secured[.]cc” domain protected by Cloudflare.

The phishing kit is designed to intercept Office 365 authorization credentials, which are purportedly required to view the decoy file.
Notably, after some time, a related malicious domain involved in the delivery chain, cklproducts[.]com, was blocked and the phishing kit started to display an “expired license” warning with a reference to an “ONNX SUPPORT” signature. The warning was related to a previously expired API key provided for phishing kit licensing by one of the underground services.
Resecurity crossreferenced the HTML content with artifacts available in our Cyber Threat Intelligence (CTI) Platform (Resecurity® Context). This query led to the identification of over 510 domain names linked to the same host with IP 104.21.87.47. Cloudflare-protected domains added some complication to our investigation, but Resecurity generated matches for most of the phishing kit resources in the .tk, .gq, .cf, .top, and .ga domains with previously indexed malicious activity.

ONNX is recognized as one of the major underground vendors offering Phishing-as-a-Service (PhaaS) using a subscription model, with prices starting at $200 per month.
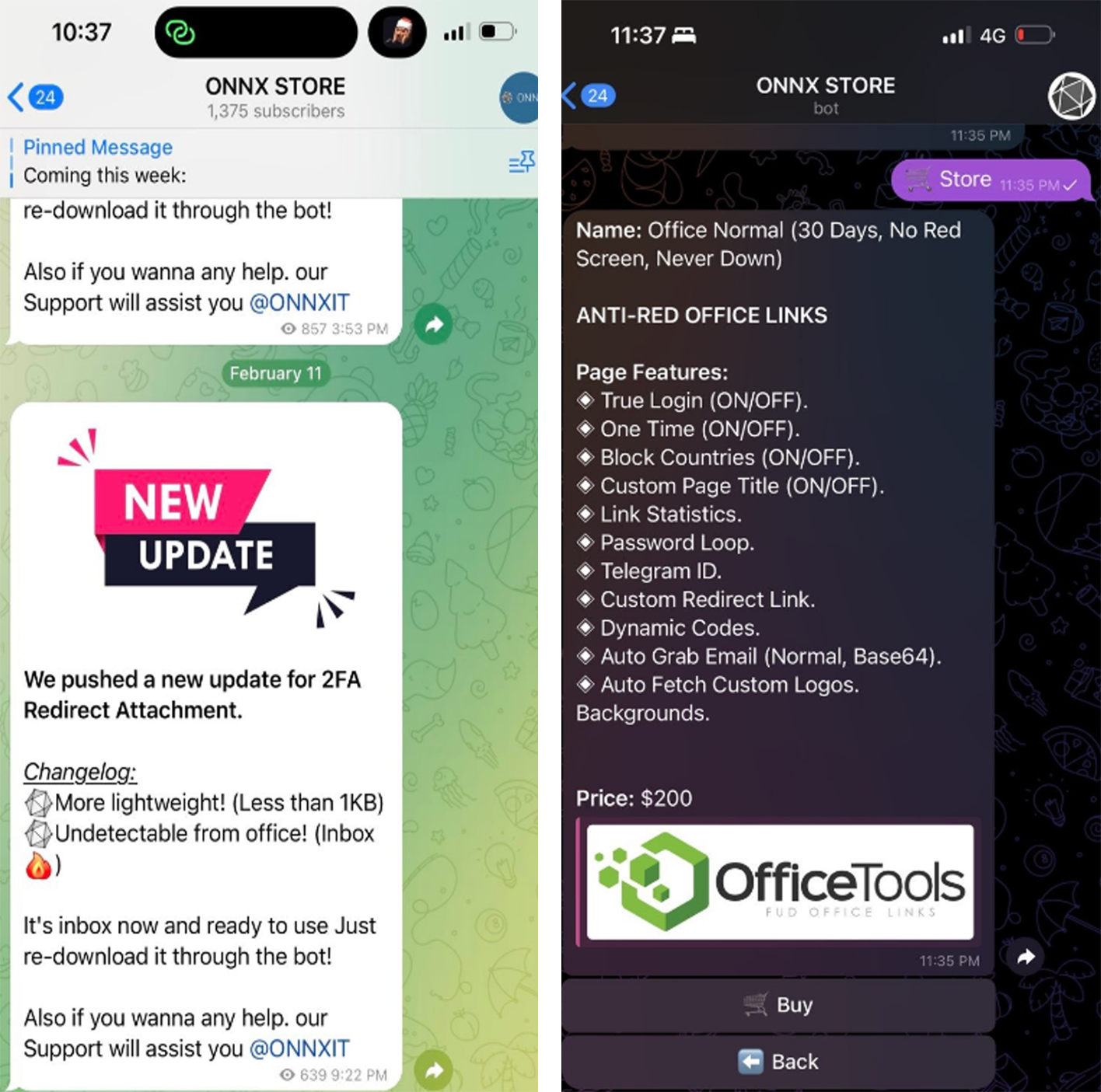
Besides the actual phishing kit known as “Office Tools”, one of ONNX’s key offerings is FUD Links.

The underground service has an automated phishing bot used for actual links generation – supporting templates for 2FA (and without).
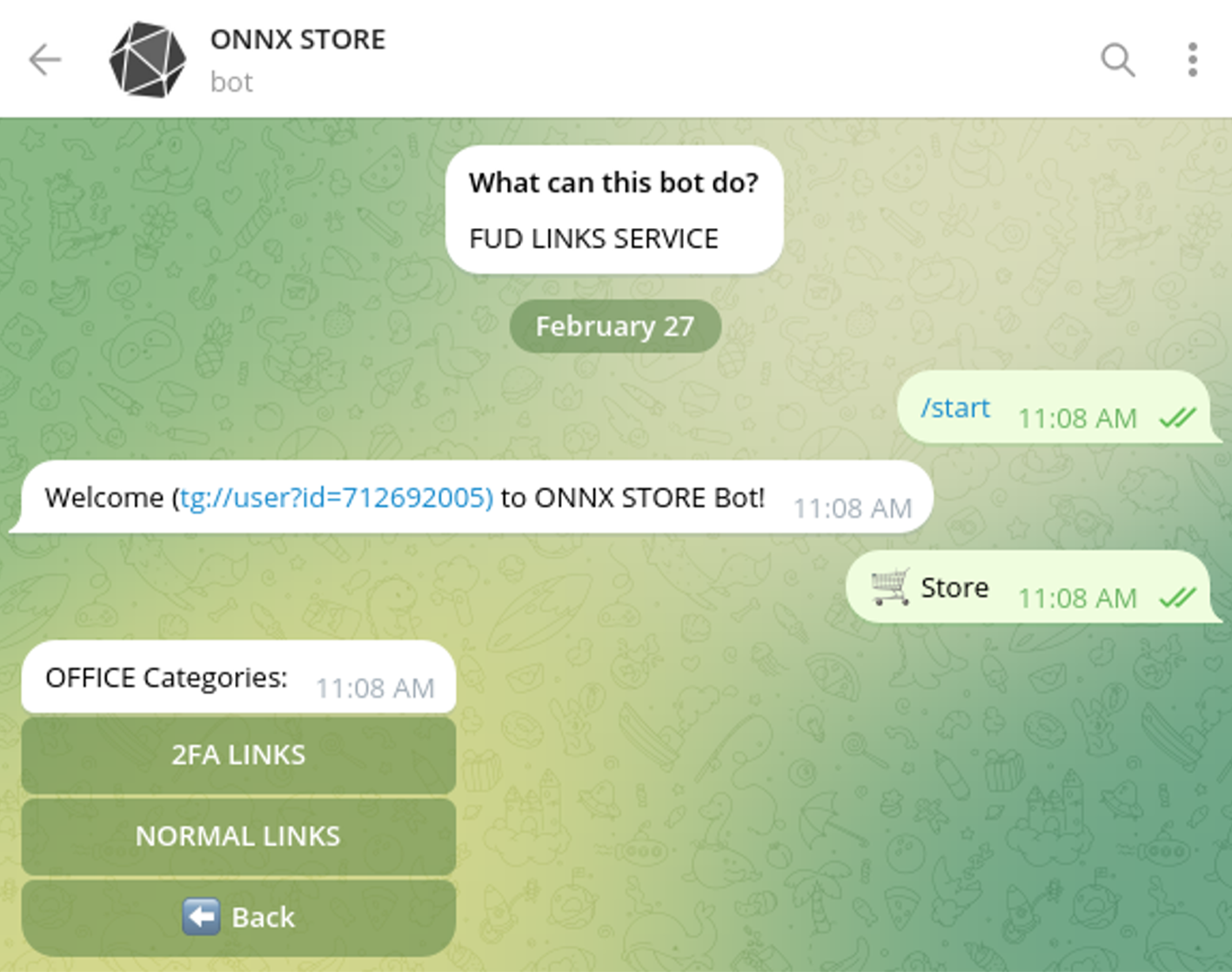
Driving Public Cloud Abuse
Besides “ONNX Store”, Resecurity identified several other underground services offering FUD Links, such as:
- FUDSENDER
https://fudsender.com/product/fudlink-service/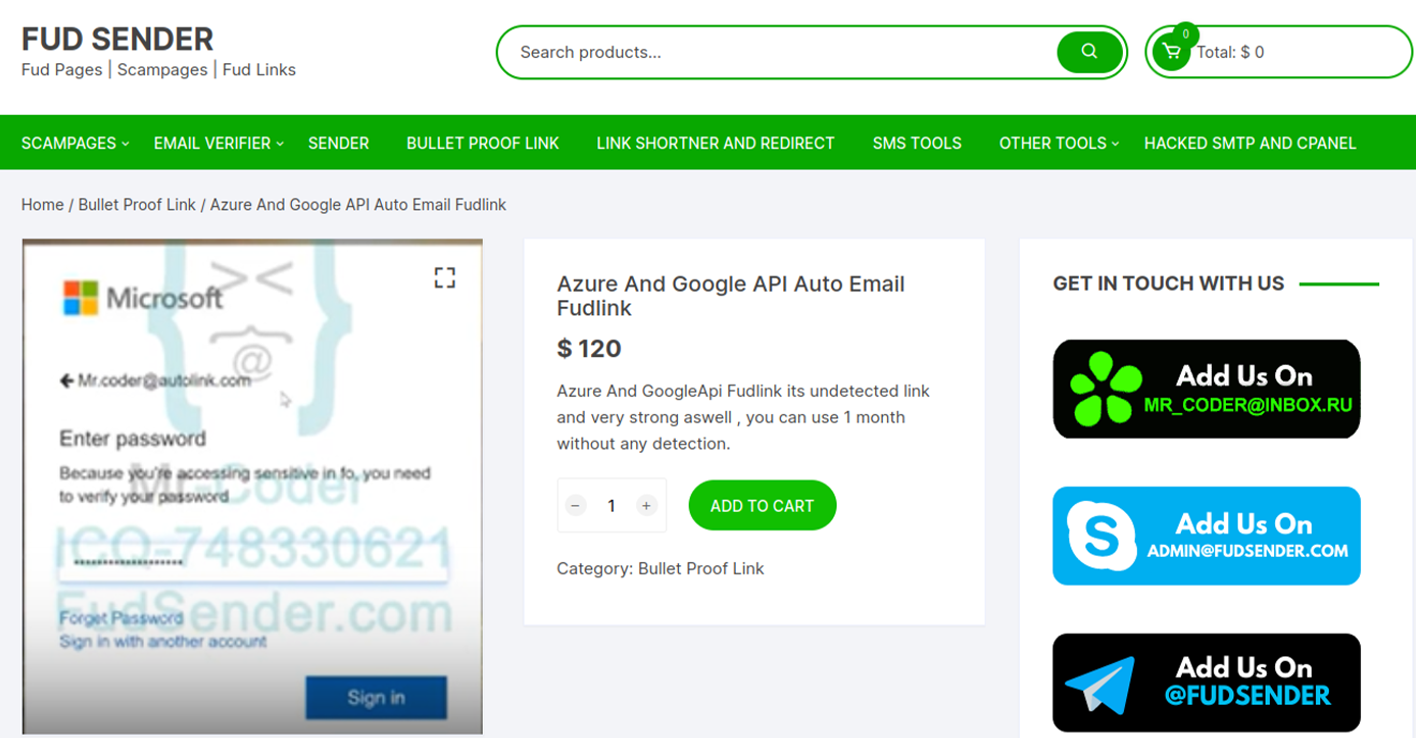
- XPLOITRVERIFIER
https://xploiterverifier.com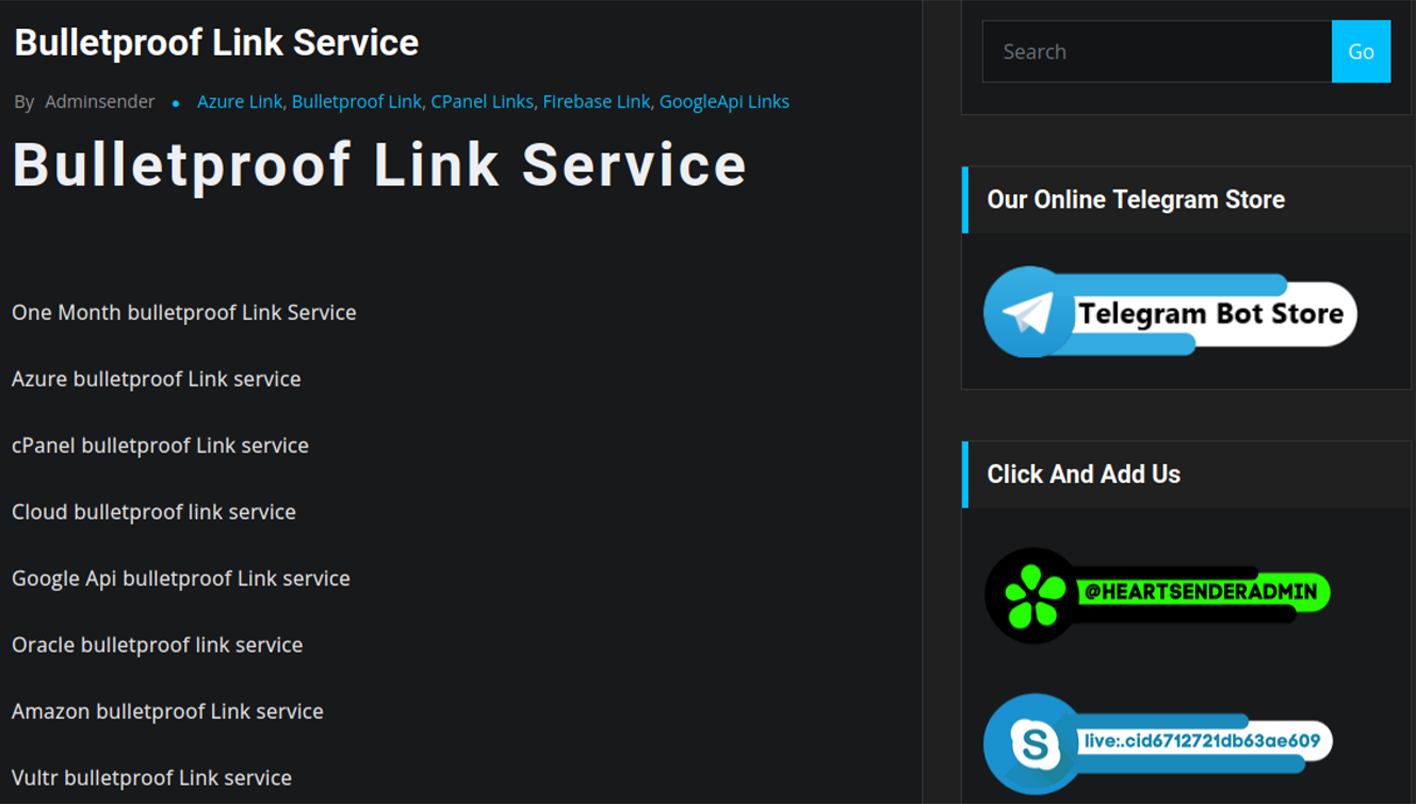
- FUDLINKSHOP
https://fudlinkshop.com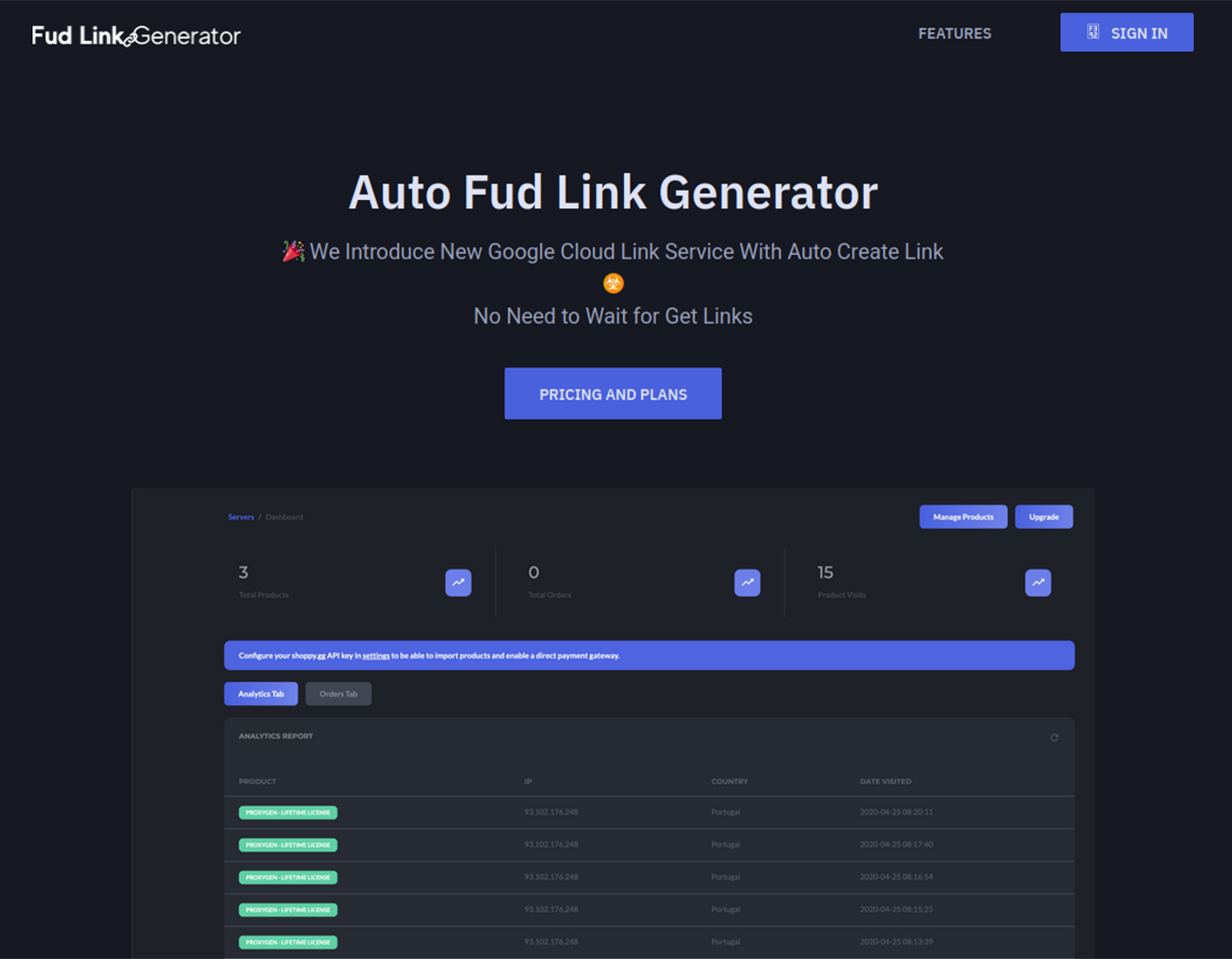
- BulletProftLink
https://bulletproftlink.org
Based on the product descriptions, these FUD Link vendors use services including but not limited to Google Cloud to host phishing.
Fud Link Shop is one vendor who actively promotes their ability to exploit Google Cloud’s domain infrastructure. To simplify the management of adversarial URLs, the threat actors behind the Fud Link Shop service integrate a proprietary management panel modeled after the legitimate Google product G-Cloud Panel into their phishing kits. This panel allows FUD Link customers to track the status of their phishing links (in case they are reported as malicious) and request new ones if they are blocked.
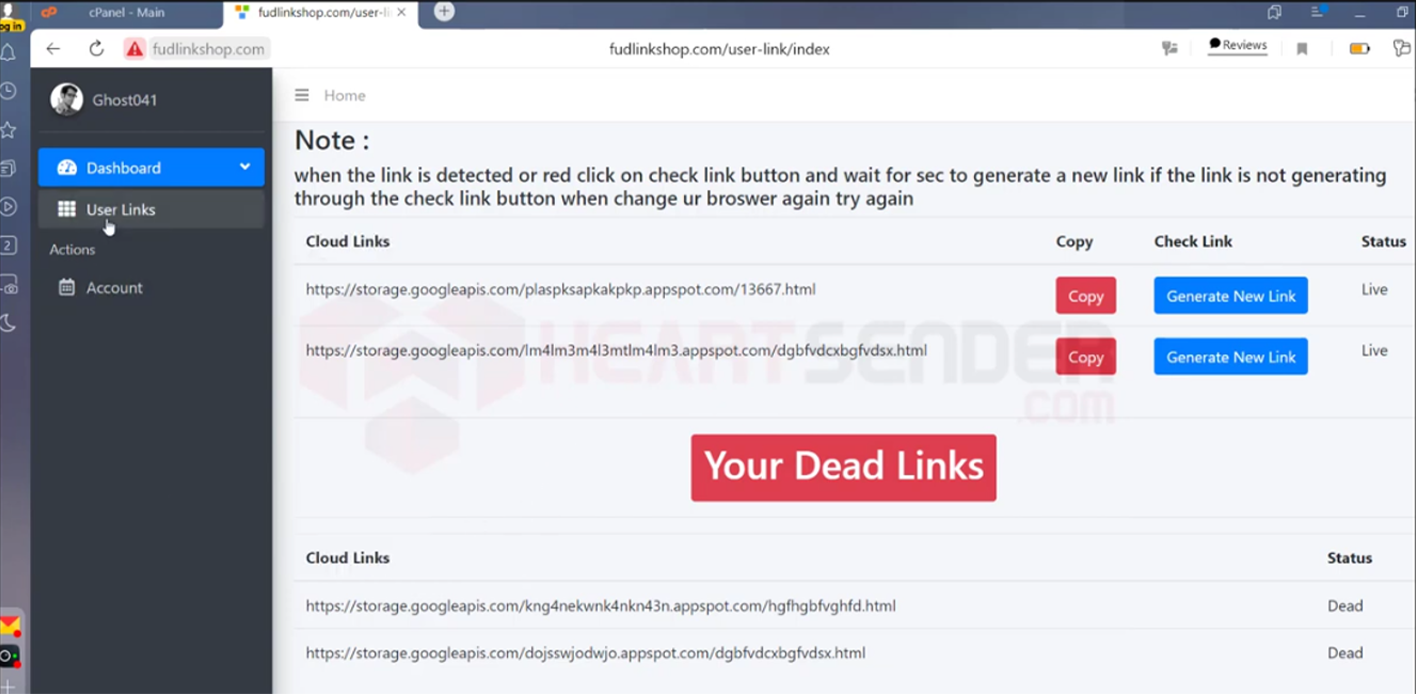
Threat actors behind this FUD Links service diligently monitor the scam URLs they generate to ensure they remain operational and actively replenish malicious URL inventories in the event cloud providers detect any links as malicious.
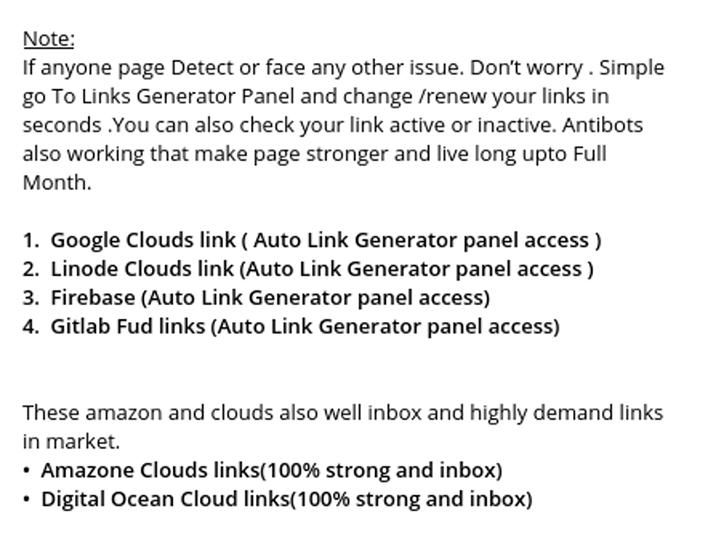
In order to protect their FUD Links, threat actor employ so-called “bot detectors” or “antibots.” In the context of adversarial activity, these antibot modules are deployed on web servers controlled by cybercriminals to filter incoming traffic which may originate from malware tracking tools, domain reputation and antivirus scanners, and cybersecurity researchers hunting malicious online infrastructures. One underground vendor lists their antibot tool for $300 per month. Threat actors use this tool to filter out all traffic that is not related to prospective victims. This tactic helps extend the longevity of the FUD Links used in their malicious campaigns.
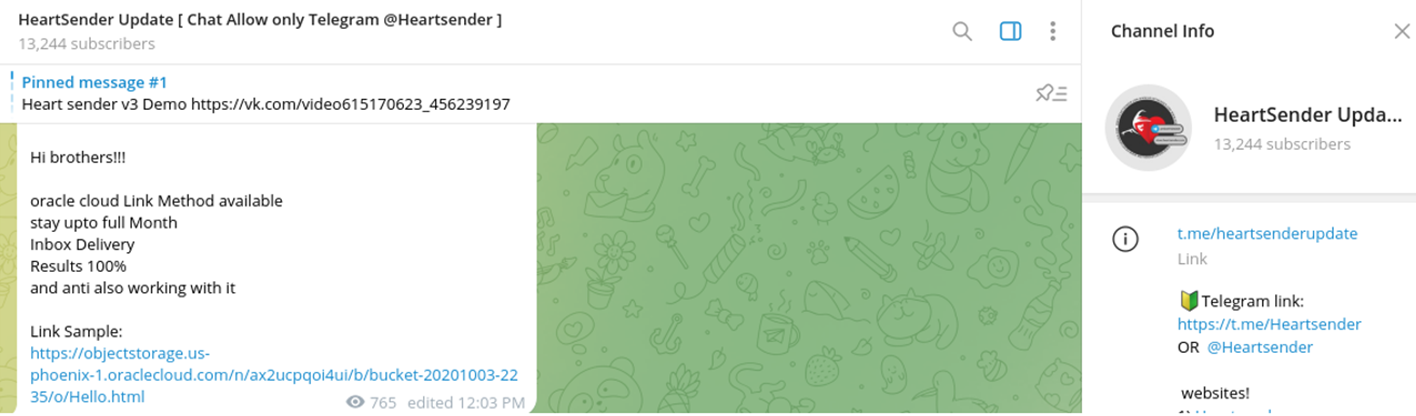
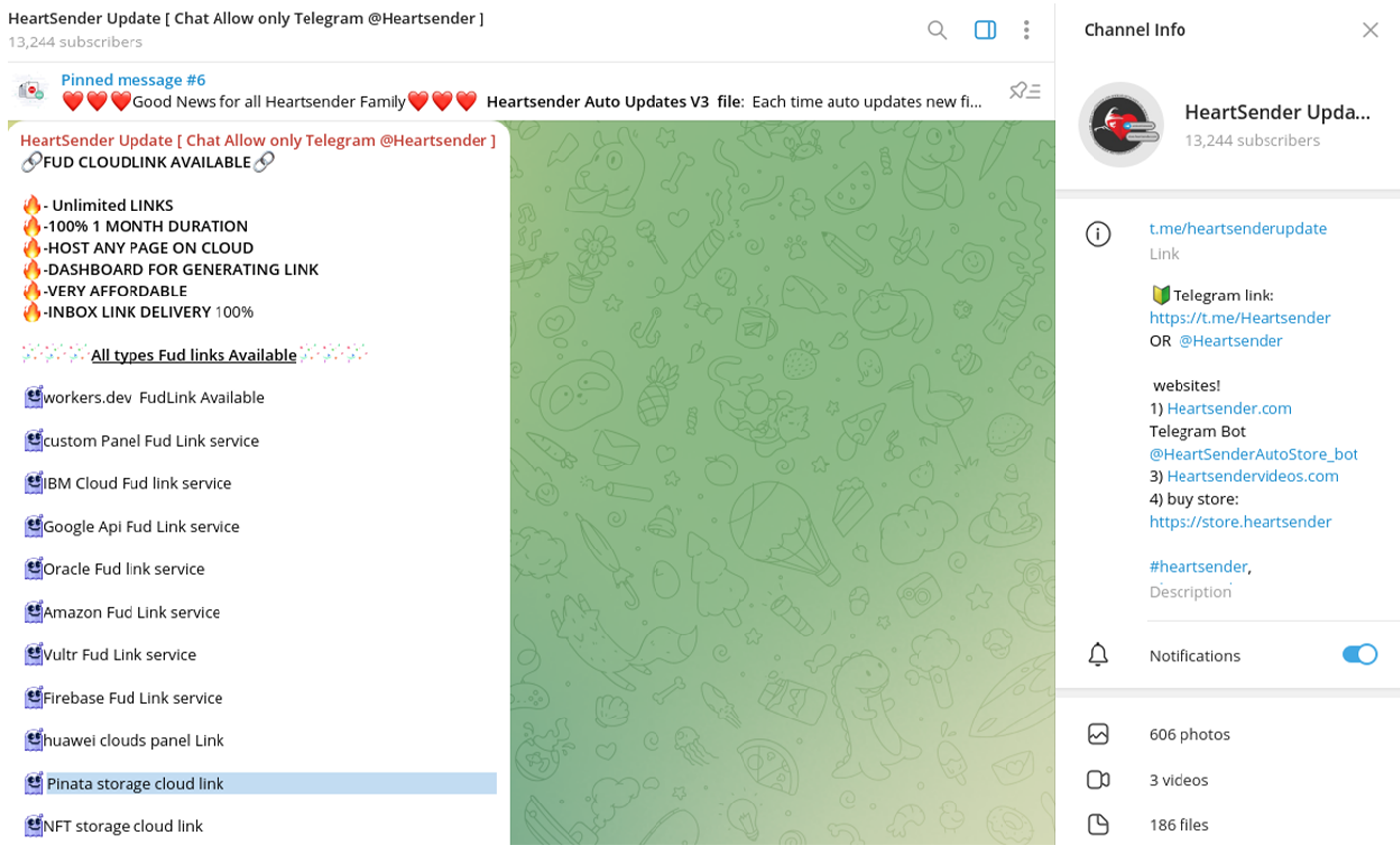
To distribute FUD Links at scale, cybercriminals use tools like HeartSender. In one of the sale listings Resecurity observed on a threat actor-operated Telegram channel, the vendors mentioned Oracle Cloud Storage as one of the platforms that could be abused to host malicious content.
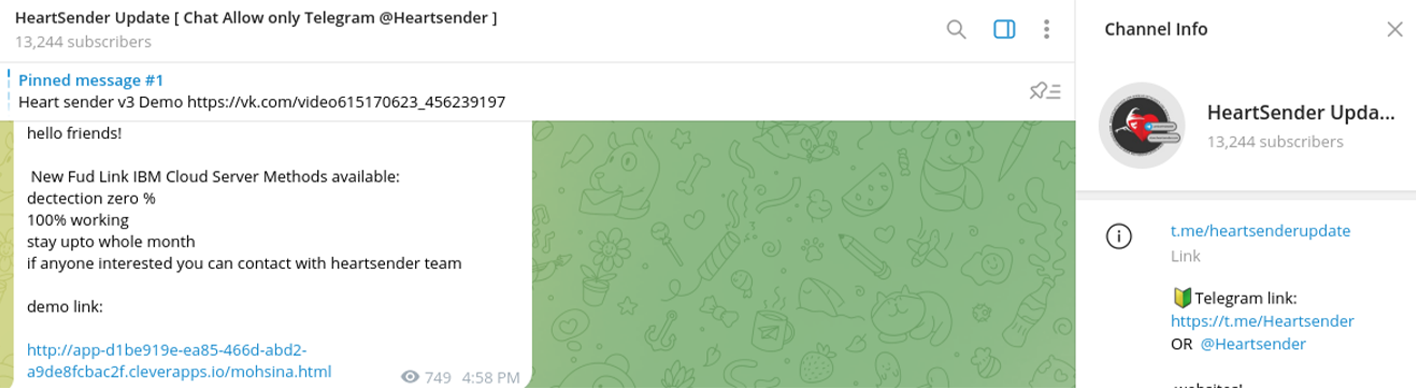
Another widely used cloud platform abused by attackers is IBM Cloud.
This channel also provides various educational manuals on how these cloud services can be exploited to target customers of major e-commerce marketplaces and financial institutions, including Amazon, Barclays, PayPal.
Abuse of Cloud CDN Services
In the Summer of 2022, Resecurity detailed how cybercriminals abuse Azure Front Door, a popular cloud CDN service provided by Microsoft, to stage phishing attacks. According to a Cloudflare explainer, CDNs are geographically distributed groups of servers that cache content close to end users. “A CDN allows for the quick transfer of assets needed for loading Internet content, including HTML pages, JavaScript files, stylesheets, images, and videos.”
Cloudflare also noted that the “popularity of CDN services continues to grow, and today the majority of web traffic is served through CDNs, including traffic from major sites like Facebook, Netflix, and Amazon.” However, the increased use of CDNs has made them a more desirable target for attackers. Since our previous research, CDN-based attacks have intensified, as threat actors are increasingly hosting Cobalt Strike command-and-control (C2) servers and payloads on Azure Front Door and other networks. Cobalt Strike is a commercial penetration testing tool that has also been adopted by cybercriminals to conduct spear-phishing attacks, gain unauthorized access to IT networks, and launch a wide variety of malicious campaigns.
Establishing Cobalt Strike C2 severs on Azure and other CDNs enables a type of attack known as Domain Fronting. Domain fronting is a technique where threat actors host different domain names on the same HTTPS connection. This tactic helps attackers hide their traffic when connecting to a target website. Domain-fronted traffic ultimately routes the connection through a larger platform, obfuscating the true destination in the process. This is the foundational attack vector enabling the unfolding malicious repository-cloning campaign on GitHub, for example.
In addition to this Azure service, Resecurity identified multiple campaigns that abused Discord CDN to host malicious files, and to host C2 communication s. Notable campaigns that abused Discord CDN include Epsilon Ransomware, Azorult, Lumma Stealer, and other popular malware families.
In one video demonstration of FUD Links, a threat actor representing the underground FUDSENDER service also shared an example of a phishing kit that exploited Rackspace CDN’s infrastructure:
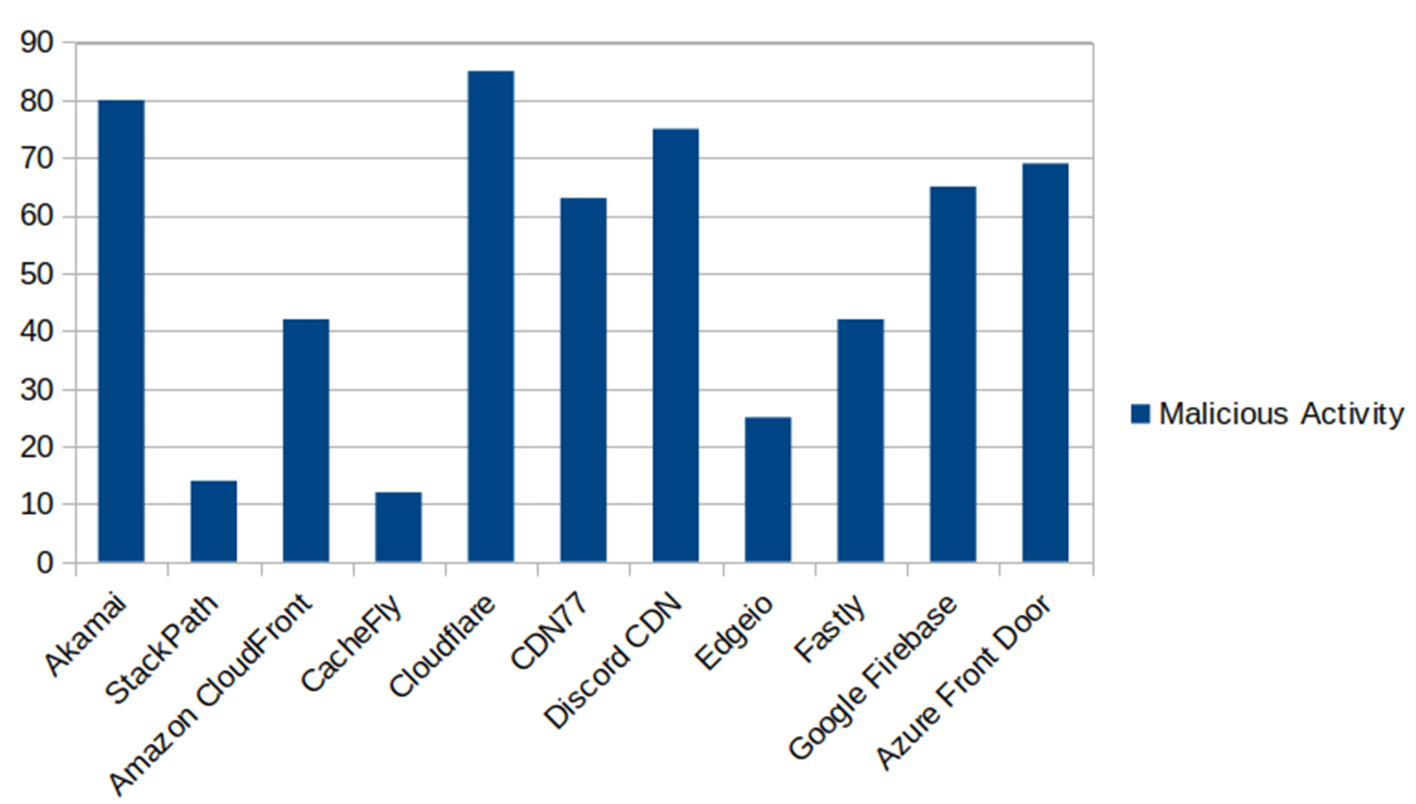
The majority of these CDN abuse scenarios involve Domain Fronting. Out of all the CDN abuse data compiled by Resecurity, Akamai and Cloudflare were the distribution networks most targeted by threat actors.
According to data compiled by Resecurity, the most abused cloud CDNs are:
Abuse of IPFS – Web 3.0 Hosting on Cybercriminals’ Radar
Notably, threat actors also cited the exploitation of decentralized IPFS-based cloud platforms like Pinata to generate FUD Links. IPFS is a decentralized, data-hosting protocol that is popular with many DeFi industry operators.
Two other popular IPFS-based platforms abused by threat actors are IPFS.IO and Infura. Resecurity identified multiple infostealers delivered via these hosting platforms, including Azorult, Vidar, and Racoon. In some cases, adversaries use DNS Link modules to connect to IPFS environments with custom domain names.
Such services may generate links having the following structure to deliver malicious payload:
hxxps[://]ipfs[.]io/ipfs/QmQBPuPxy3nZjK2yVspsUJVhutajAfRQpnjc58RAcUJFrh?filename=INV-SCL0093-05-22pdf.exe
hxxps[://]ipfs.infura[.]io/ipfs/QmejguEysvXLMaAYmXe3EXmjfnoAqMdVfn4ojto1yLTGhK
Conclusion
Public cloud platforms and popular CDNs are integral nodes in the infection chains of global malware and phishing campaigns. By abusing these services, attackers inflict significant damage on millions of Internet users and create substantial challenges for network defenders overwhelmed with the flood of FUD Links. The significant time gap between the generation of these public cloud and CDN-nested links and their detection by hosting providers or defenders places enterprise personnel at substantial risk of being compromised by malicious FUD Link-powered campaigns.

