Hundreds of network operators’ credentials found circulating in the Dark Web
Cyber Threat Intelligence


Following a recent and highly disruptive cyberattack on telecom carrier Orange España the cybersecurity community needs to rethink its approach to safeguarding the digital identity of staff involved in network engineering and IT infrastructure management. Orange España is the second-largest mobile operator in Spain. In early January, an attacker going by the alias ‘Snow’ hijacked Orange España’s RIPE Network Coordination Centre (NCC) account. RIPE is Europe’s regional Internet registry. After this initial breach, Snow sabotaged the telecommunications firm’s border gateway protocol (BGP) and resource public key infrastructure (RPKI) configurations.
Snow’s account takeover (ATO) attack and subsequent infrastructure reset caused a three-hour service outage, inconveniencing Orange España’s customers and disrupting the company’s operations. Ultimately, this cyberattack illustrates why network engineering and IT infrastructure management staff represent high-value targets to attackers. By virtue of their job duties, these personnel groups are granted higher levels of privileged access by their enterprises. Resecurity conducted a thorough scan of the Dark Web and identified over 1,572 compromised customers of RIPE, Asia-Pacific Network Information Centre (APNIC), the African Network Information Centre (AFRINIC), and the Latin America and Caribbean Network Information Center (LACNIC), resulting from infostealer infections.
While disruptive cyberattacks on telecom carriers and related network infrastructures are rare there has been a steady increase in attacks targeting this sector, noted Dark Reading last year. The motive behind these attacks is typically espionage. Factors driving the rise in telecom cyberattacks include the proliferation of 5G networks and VoIP services,” according to the Dark Reading report.
Newer telecom services like 5G are particularly vulnerable to cyberattacks because their core technologies are all software designed. According to the Dark Reading report, this means “all the risks associated with software technologies will manifest on carrier networks.” However, Resecurity’s report is more concerned with how the poor digital hygiene of key telecom network personnel can amplify the breach surface for threat actors, potentially setting the stage for more devastating attacks.
Who are the key targets for attack?
- ISP/Telcom engineers
- Data-Center Technicians
- Network Engineers
- IT Infrastructure Managers
- Outsourcing companies (managing networks for their enterprise clients)
Orange España Incident – From Stolen Credentials to BGP hijacking
On January 3, Orange España customers were unable to access the internet for several hours as a result of a cyberattack that appears to have involved credentials that were harvested by an infostealer. The hacker used these stolen credentials to take control of Orange España’s RIPE NCC account. After sabotaging their network settings, Snow taunted Orange España on X, saying “message me to get the new credentials.”
According to Hudson Rock, an Orange employee's computer was infected by the Raccoon Infostealer on September 4th, 2023. Among the corporate credentials identified on the infected machine, the employee had specific credentials for 'https://access.ripe.net', using an email address that was later exposed by the threat actor.
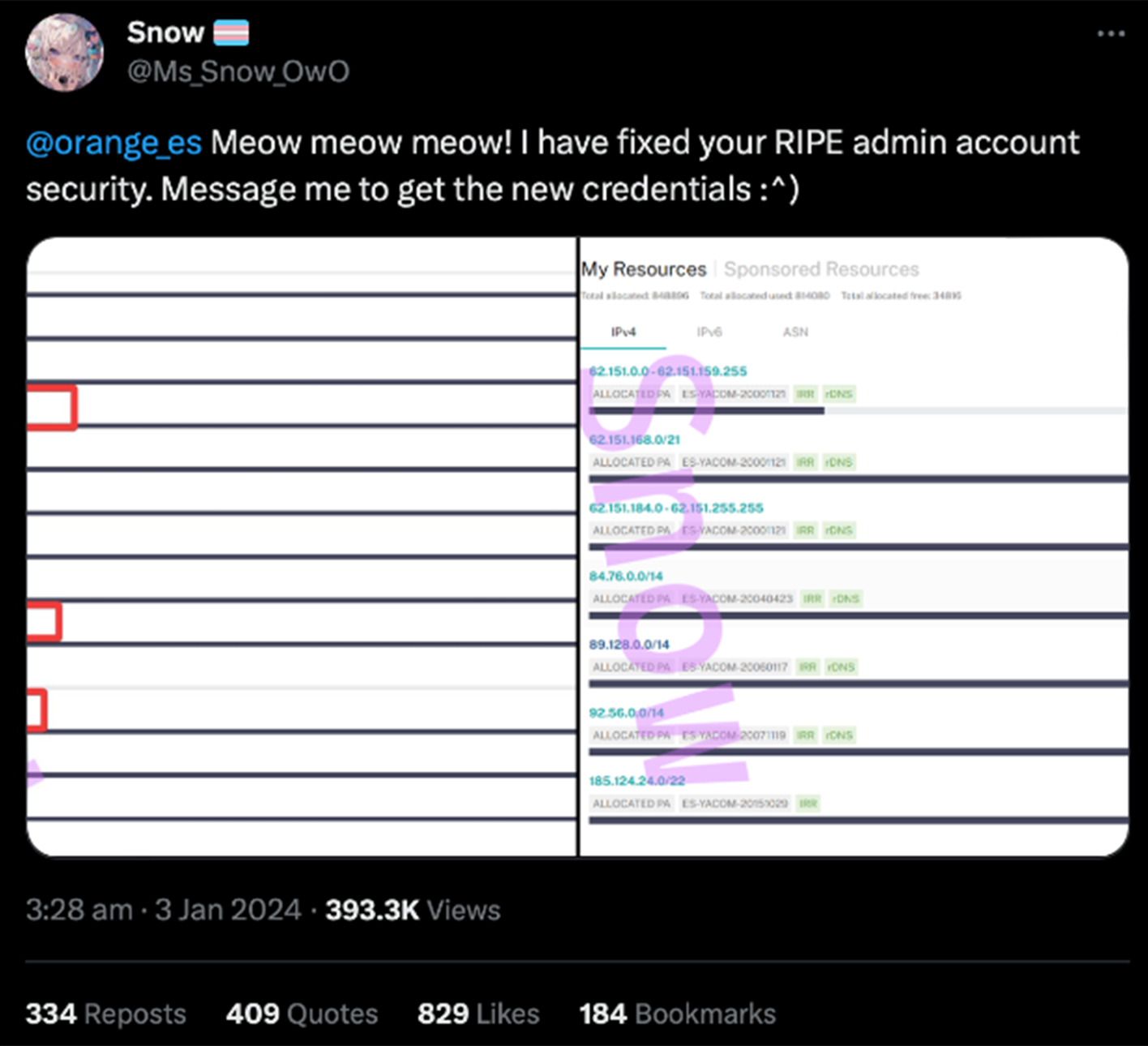
RIPE is a French acronym for Réseaux IP Européens (European IP Networks). The RIPE NCC is the regional internet registry for Europe, the Middle East, and parts of Central Asia. RIPE NCC is responsible for allocating and registering blocks of internet number resources to ISPs and other organizations. The attacker, who goes by‘Snow’, reconfigured Orange’s RIPE account, which led to the disruption in BGP routing and a significant loss in traffic.
Per Bleeping Computer’s description, BGP allows “organizations to associate their IP addresses with autonomous system (AS) numbers and advertise them to other routers they are connected to, known as their peers.” After hijacking Orange’s RIPE account, the hacker manipulated the way the telecom’s Internet addresses were perceived by the BGP. Furthermore, the “attacker modified the AS number associated with the company's IP addresses, and enabled an invalid RPKI configuration on them,” according to Bleeping Computer reports. When properly assigned, AS numbers allow networks to exchange information on the Internet.
Additionally, RPKI is a “cryptographic method of signing records that associate a BGP route announcement with the correct originating AS number.” In this incident, Snow misconfigured Orange’s RPKI settings to sabotage RIPE’s indexing of their correct AS numbers with their network IPs. Snow’s malicious network misconfiguration resulted in widespread outages for Orange España.
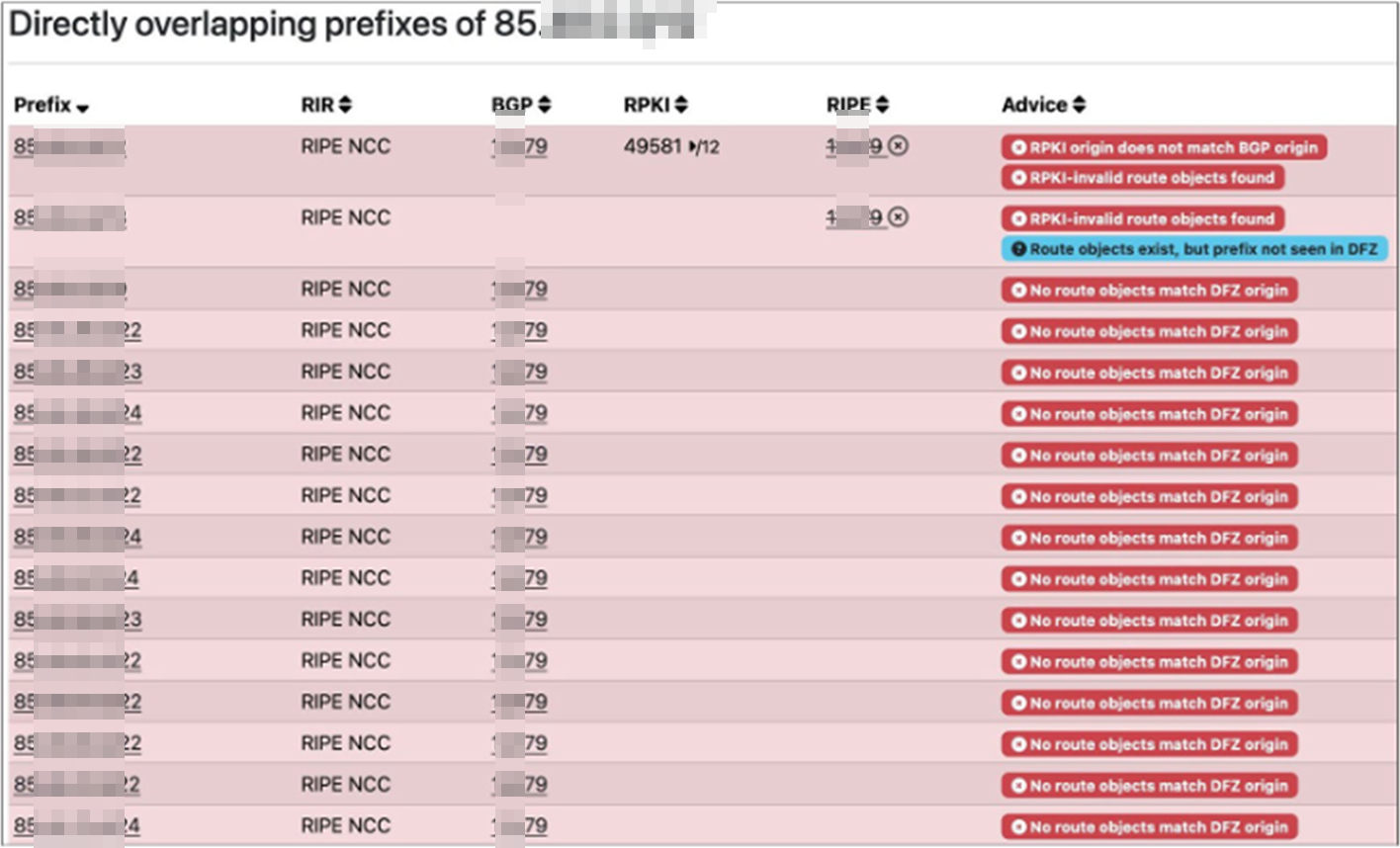
As detailed by APNIC and cybersecurity firm Kentik, the Internet’s RPKI Route Origin Validation (ROV) deployment has reached the point where the propagation of a route is cut in half or more when logged as RPKI-invalid. Normally this is the desired behavior, but when an RPKI setting is intentionally loaded with misconfigured data, it can render address space unreachable, effectively becoming a tool for denial of service (DoS):
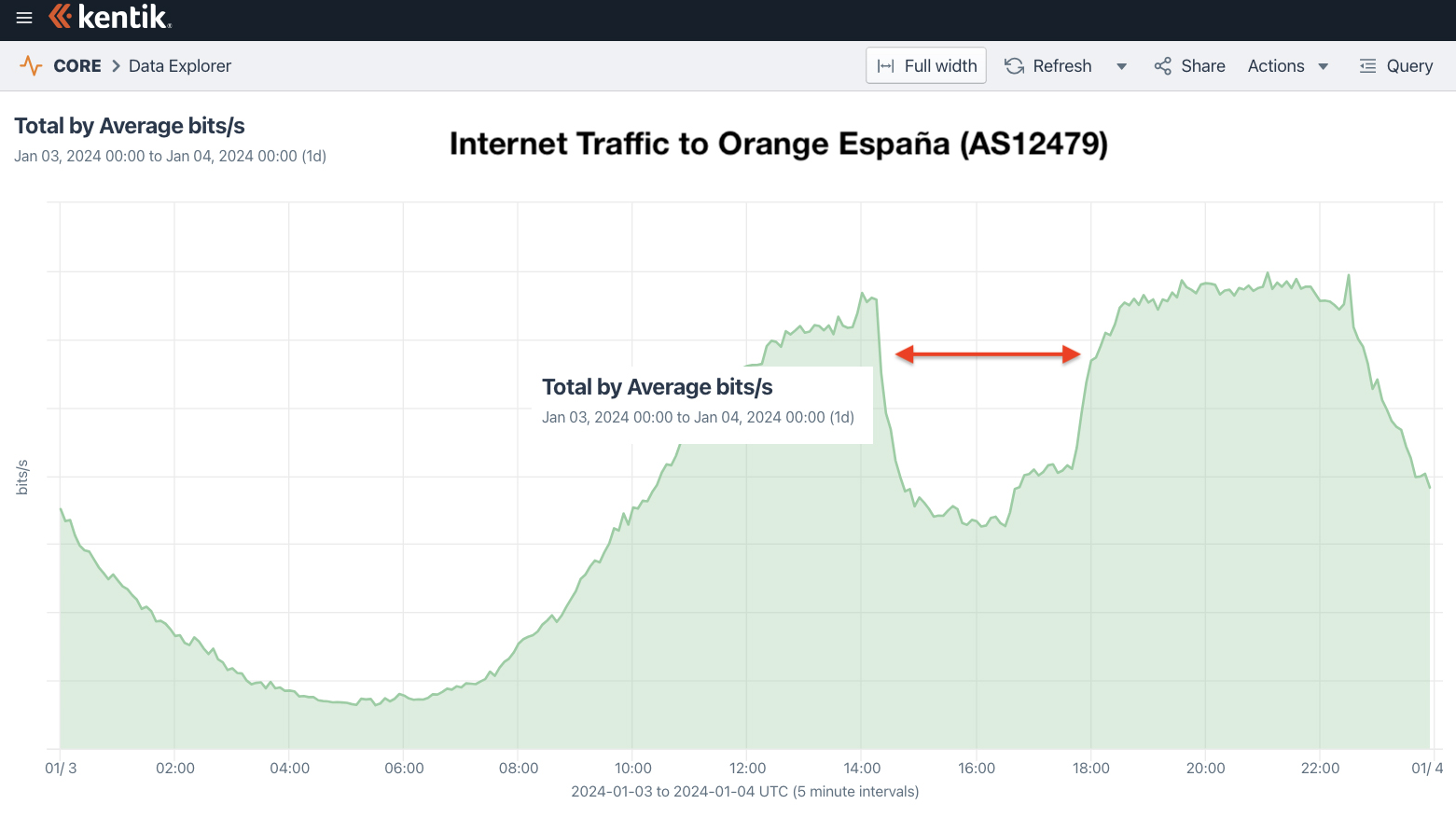
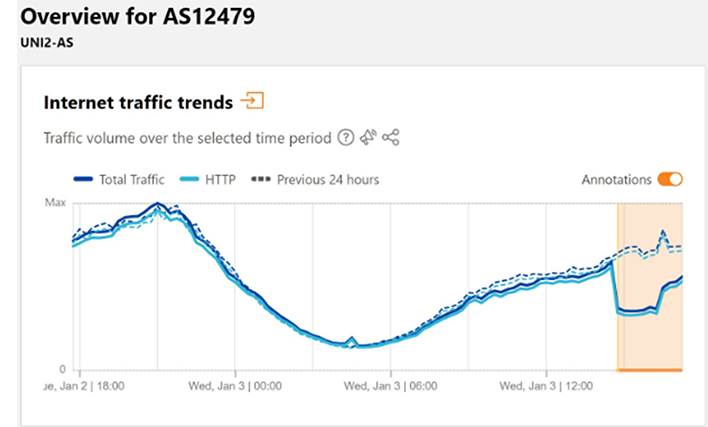
Snow’s attack this resulted in a performance issue on the Orange España network between 14:45 and 16:15 UTC (January 03-04, 2024), which can be seen in the Cloudflare traffic graph for AS12479.
Orange España said on X that there was no compromise of customer data and clarified that the incident only affected the “navigation of some services.”
In response to the situation, RIPE released a statement where they said they were investigating the incident and confirmed that the account compromise resulted in the temporary disruption of some account-holder services. RIPE also noted that they had restored access to Orange España’s account and encouraged registry account holders to update their passwords and to enable multi-factor authentication (MFA).
In response to inquiries regarding the lack of mandatory two-factor authentication, RIPE stated that they were accelerating the implementation of 2FA by making it mandatory for all RIPE NCC Access accounts as soon as possible.
Shopping For Telecom Engineers’ Accounts On The Dark Web – Business & Pleasure
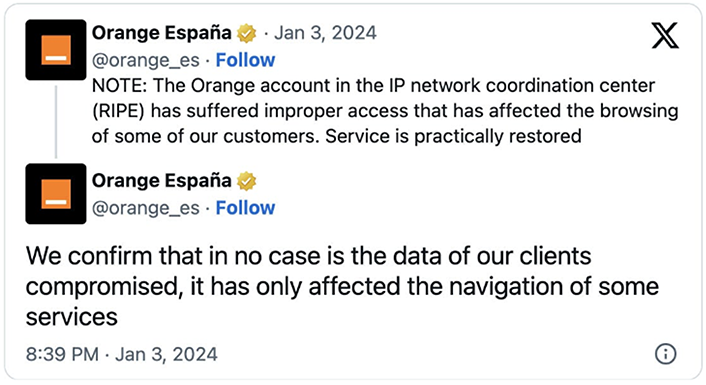
Following the Orange España incident, Resecurity identified multiple postings on the Dark Web that show cybercriminals selling access to credentials belonging to telecom network administrators and engineers from various companies. Likely, Snow’s success encouraged many of these threat actors to start hunting for access to similar credentials. One threat actor going by the handle “aterna” was offering compromised account of a Lebanon-based organization that did not have 2FA enabled.
Based on interactions with this actor by one of Resecurity’s HUNTER (HUMINT) analysts, the portal credentials were valid and didn’t require any 2FA - just as the threat actor advertised in their listing. Notably, as of January 29, the 2FA for this RIPE portal is still optional.
Cybercriminals frequently use underground channels to exchange credentials and botnet data. Individuals or groups of threat actors then purchase the rights to push their infostealers and other malware to the user’s PC or mobile device. The underground markets that commercialize this data are extremely efficient and often automated.
Chat with the threat actor sharing compromised credentials to RIPE portal:
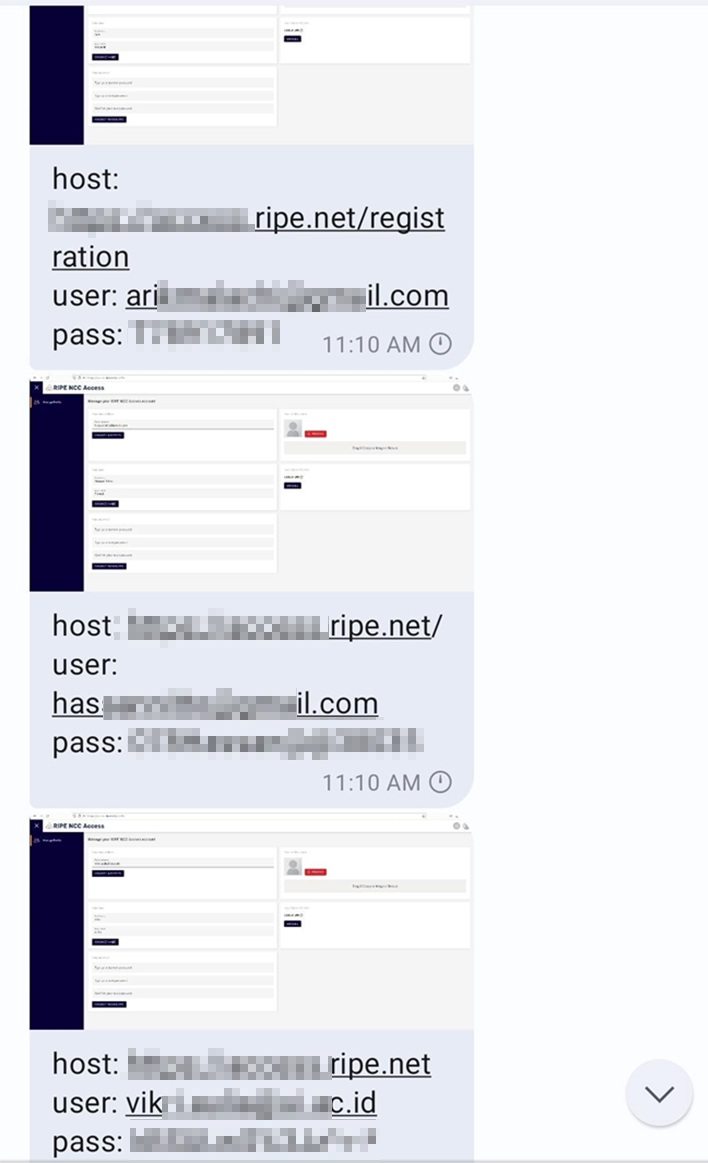
Resecurity identified multiple underground markets and acquired 1,572 compromised access credentials to RIPE customer portals. This number includes historical records and artifacts that were identified in January 2024 as a result of analyzing Command and Control (C2) servers. Resecurity promptly shared this threat intelligence with the RIPE Security Team and related victims for further risk mitigation. Please, note, the identified compromised credentials have nothing to do with any vulnerability, data breach, or security incident on RIPE’s side. The issue is purely related to the network hygiene of RIPE customers impacted by password stealers (or other types of Dark Web exposure).
According to The Hacker News, infostealers are a “type of malware that targets its victim by stealing sensitive information that can include passwords, login credentials, and other personal data. After collecting such data, the stealer sends it to the threat actor's command and control (C2) system.” Infostealers are a rapidly growing threat and one of the leading compromise vectors behind the leak of user credentials on the Dark Web – if not the foremost one.
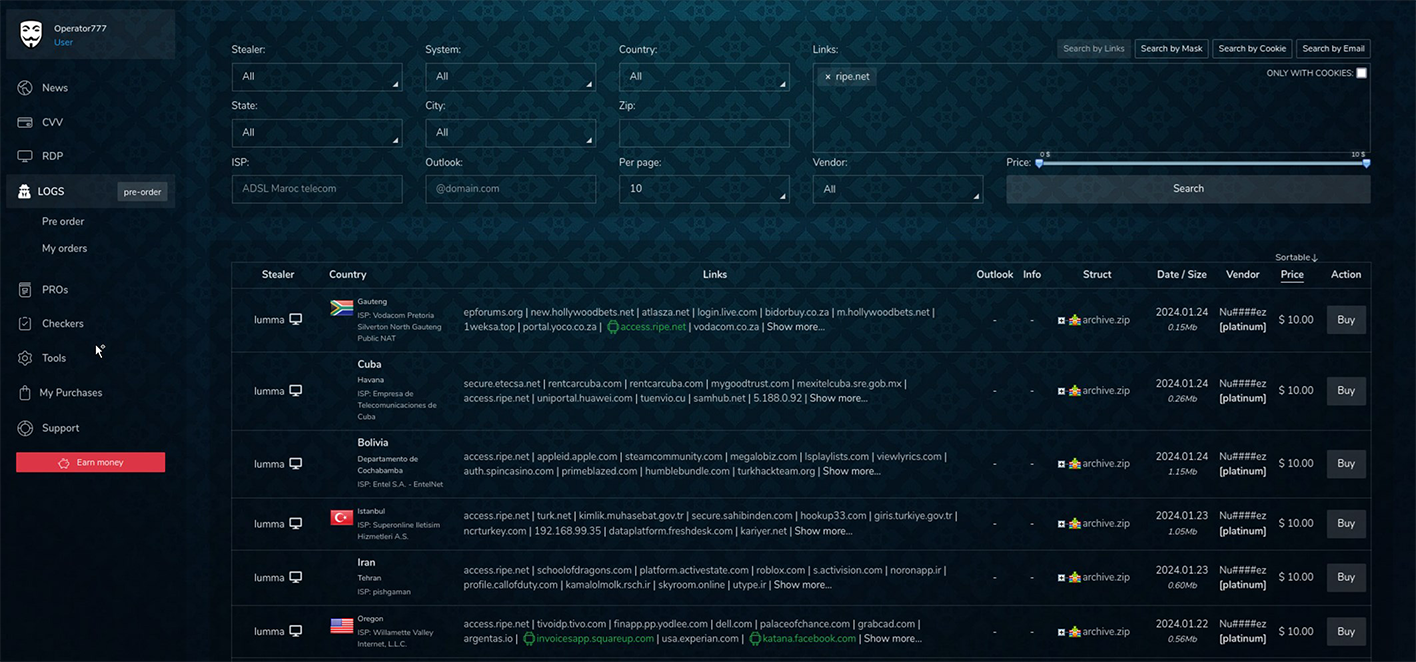
Notably, in some cases, credentials on underground markets were offered for just $10. An example of a critical risk that could arise from this niche market could manifest via the collaboration between initial access brokers (IABs) and ransomware groups. The former could enable the latter to acquire the credentials of a compromised network engineer from one of the Indonesian ISPs and later use it to stage a more devastating attack inspired by the Orange España breach.
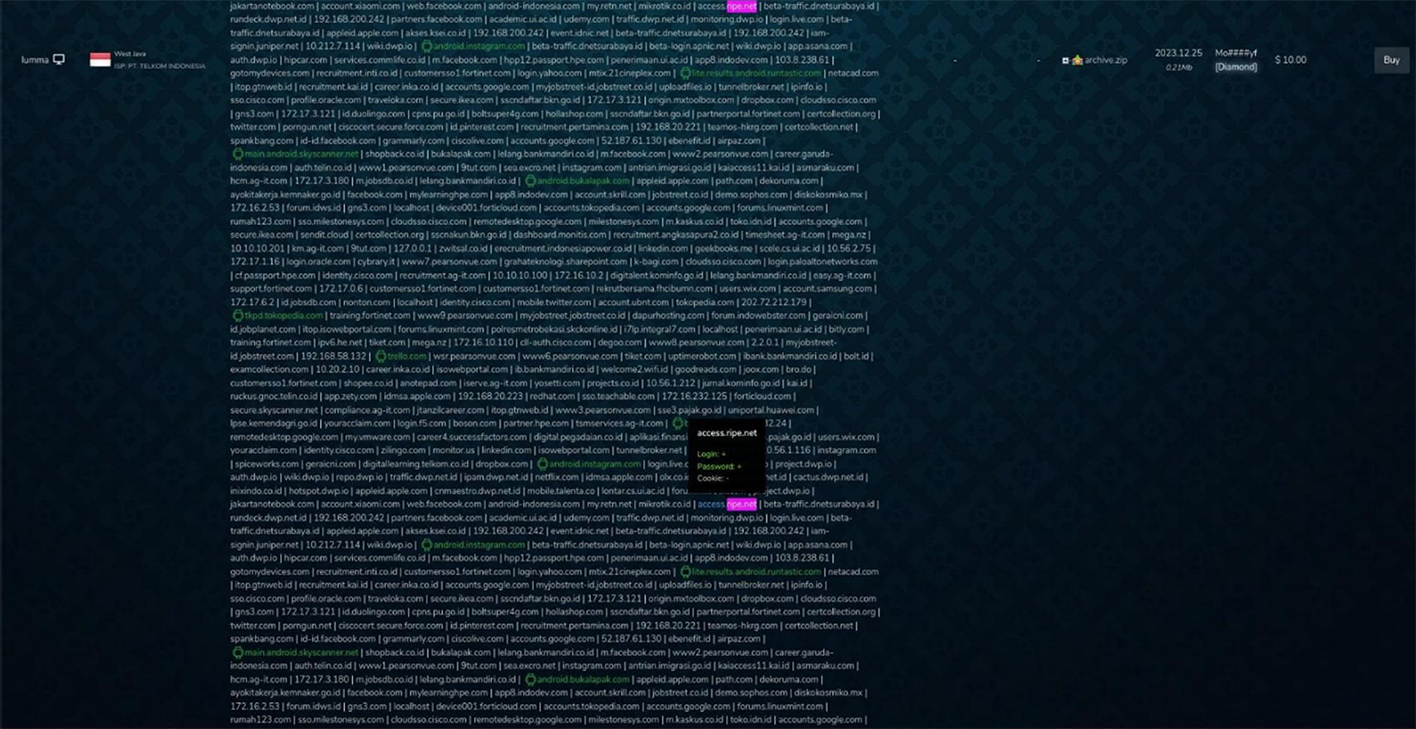
Notably, some of the independent actors were also offering higher-priced RIPE credentials. These higher value credentials included cookies, proxy, or remote access that could be activated via the deployment of malicious code onto the victim’s device. Resecurity acquired one of these offerings. Depending on the privileges available to the compromised user, the threat actor may leverage tactics similar to Orange España scenario, but to greater effect.
Below are examples of compromised RIPE accounts belonging to a major data center and one of the largest vendors of international-scale network connectivity to governmental and national telecom providers in Africa:
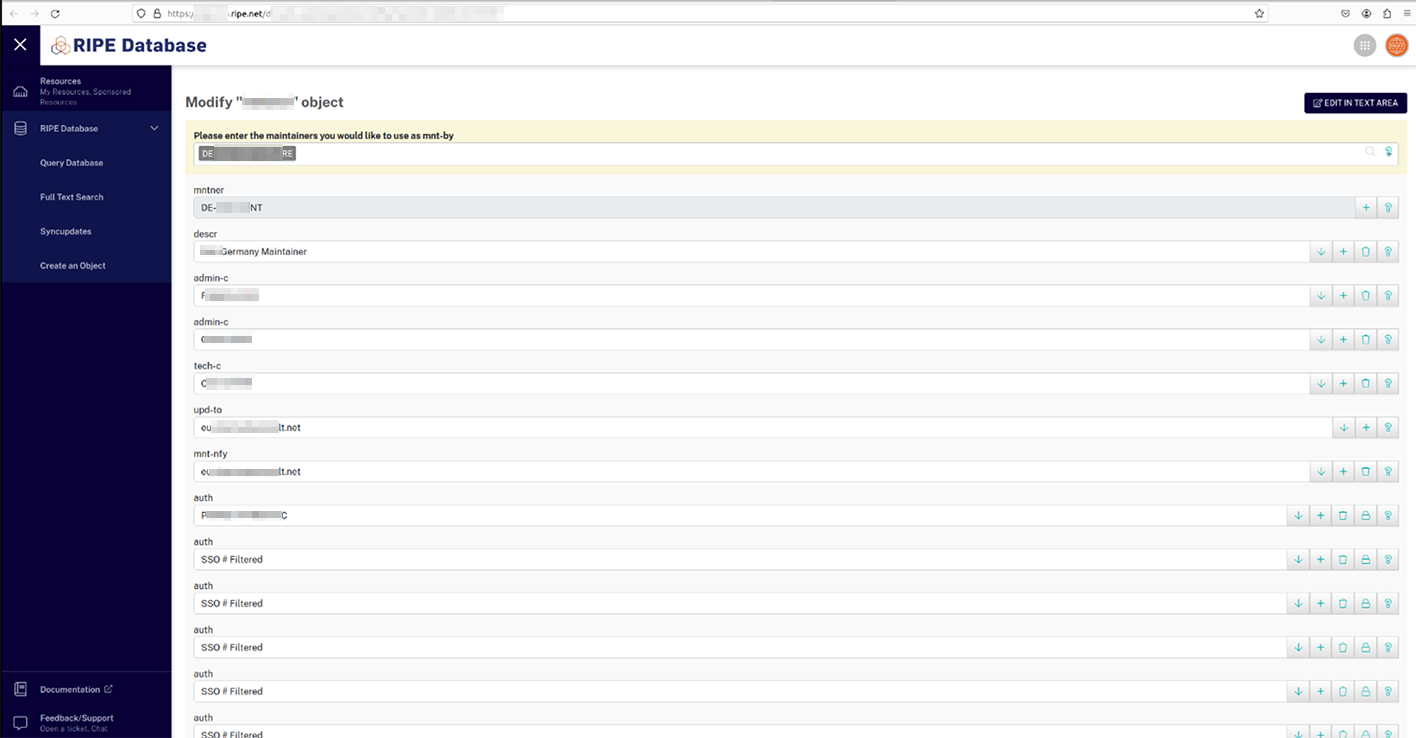
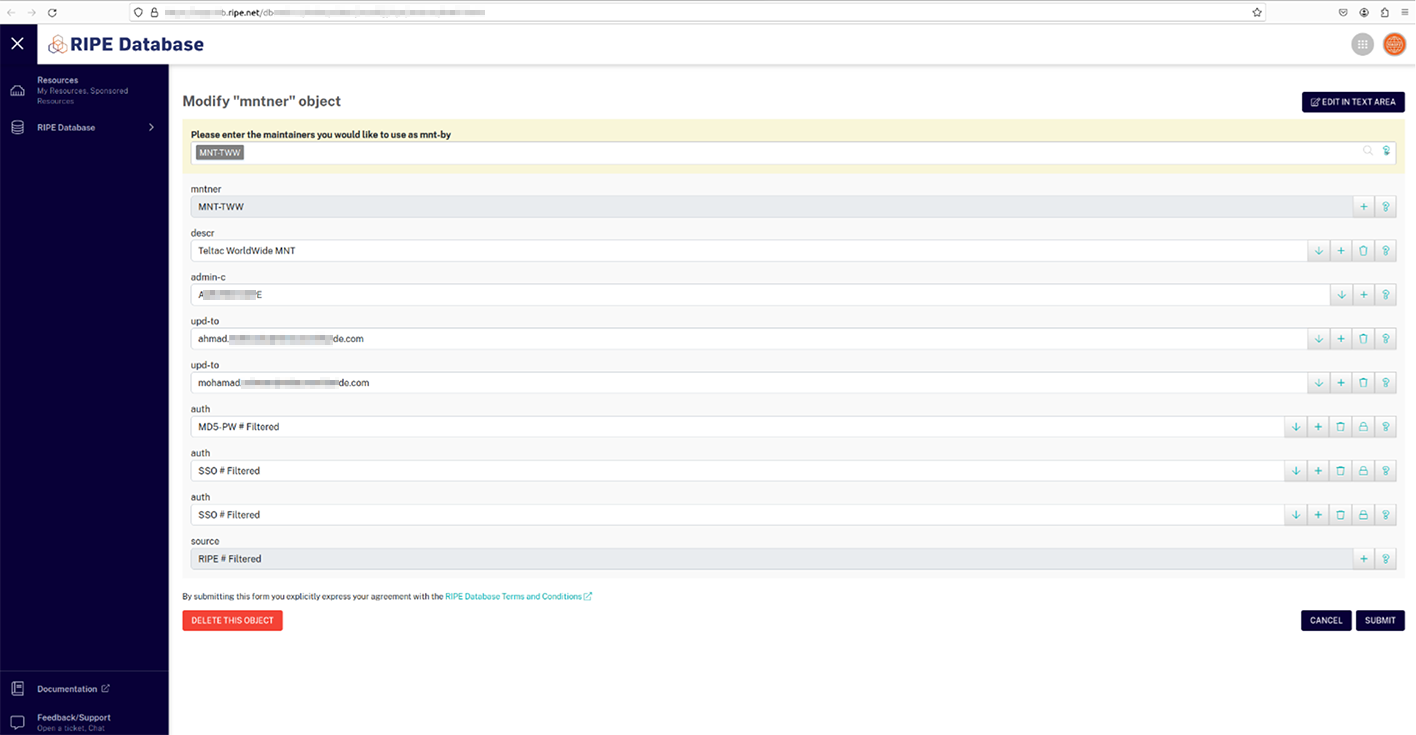
Other identified victims were associated with significant organizations, including:
- Scientific research organization from Iran;
- Major financial organization from Kenya;
- One of the largest IT consulting firms in Azerbaijan, known for offering services like telecommunications, integrated network, and cloud solutions to enterprises and government entities;
- A major financial organization in Spain;
- One of the largest gambling providers in EU;
- ICT technology provider based in Saudi Arabia;
- An Israeli communications satellite operator;
- A government agency from Iraq;
- A nonprofit Internet Exchange (IXP), established in Riffa, located in the Southern Governorate of Bahrain.
The potential for malicious activity in this sector surpasses simple credential theft. With access to network settings, threat actors can also alter existing configurations or introduce deceptive elements, potentially creating havoc on enterprise network infrastructures. These types of unauthorized modifications can lead to severe disruptions in telecom service and security, underscoring the critical need for heightened vigilance in safeguarding digital assets and the credentials of privileged IT personnel.
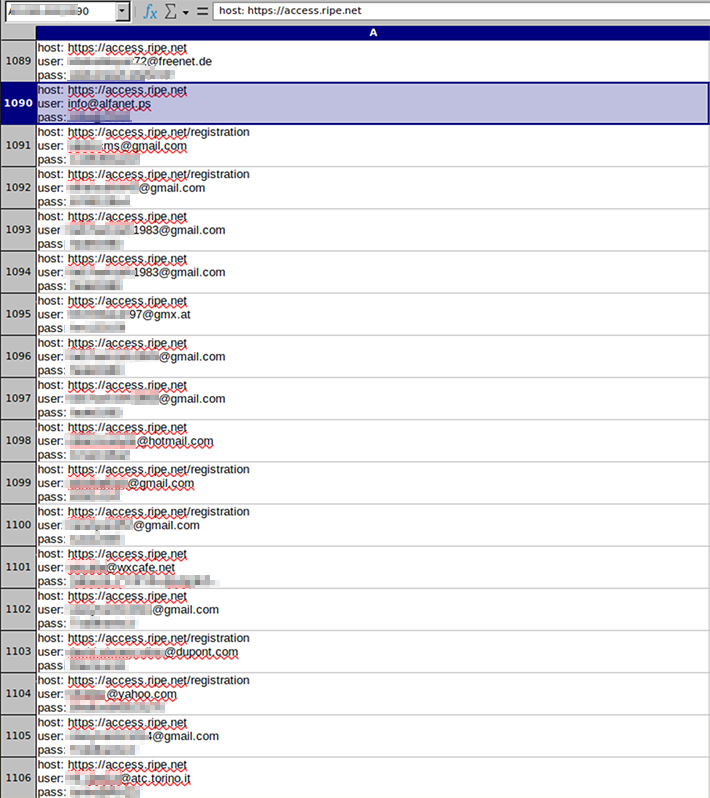
Notably, some of the records identified in the data sets acquired by Resecurity have been previously observed in major cybersecurity incidents. For example, Gaza-based ISP AlfaNet was significantly impacted by outages at the peak of Israel-Gaza conflict in October. At the time, attackers were leveraging multiple tactics including DDoS attacks. In the wake of the Orange España incident, however, these types of intrusions could be repurposed to inflict more severe, if not catastrophic, levels of network disruption.
Other victims identified by Resecurity in these data sets include Fortune 500 companies, major universities, wireless / mobile operators, and regional ISPs. Significantly, most of the network administrators (identified as compromised) managing networks used emails registered with free providers, including Gmail, GMX, Yahoo. These details could be highly valuable to cyberespionage groups that are laser-focused on specific targets, such as network administrators and their circle of contacts. Acquiring information about this target group’s personal emails could enhance the likelihood of successful reconnaissance, and lead to more sophisticated campaigns.
Looking at the Bigger Picture – Network Operators in Danger
Resecurity analyzed the precursors of possible breaches for four major regional Internet service registries that serve enterprise customers.
- RIPE (access.ripe.net)
- APNIC (my.apnic.net)
- LACNIC (milacnic.lacnic.net/lacnic/login)
- AFRINIC (my.afrinic.net/login)
These organizations provide Internet number resources and registration services that support the global operation of the web.
As of Q1 2024, Resecurity found that the largest number of compromised customer accounts originated from the RIPE registry. As the largest registry, it makes sense that RIPE would have the largest victim pool. Therefore, it’s difficult to say whether this registry has been targeted more deliberately than its global peers.
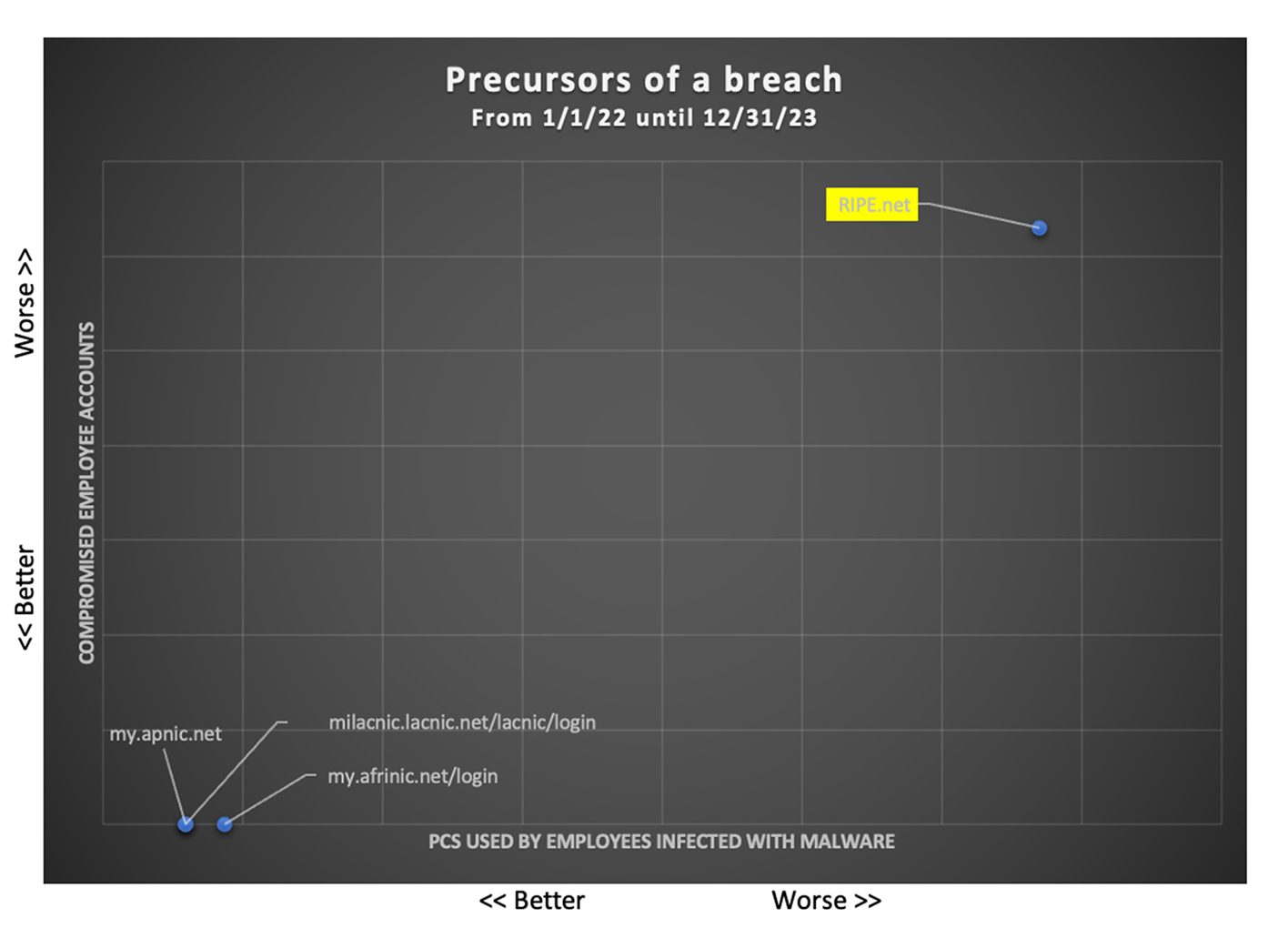
However, there is a concerning trend of increasing infostealer infections impacting users of all four organizations. This aligns with a broader macro trend of proliferating infostealer infections.
This analysis shows the number of accounts associated with the above URL/domain(s) that were compromised when the PC they were using was infected with malicious code or infostealers like Redline, Vidar, Lumma, Azorult, Taurus, etc. It is common for malware like this to collect all the usernames and passwords, along with the devices and services that can be exploited by threat actors. All the user’s cookies, security tokens, and more are also often stolen by these malware types.
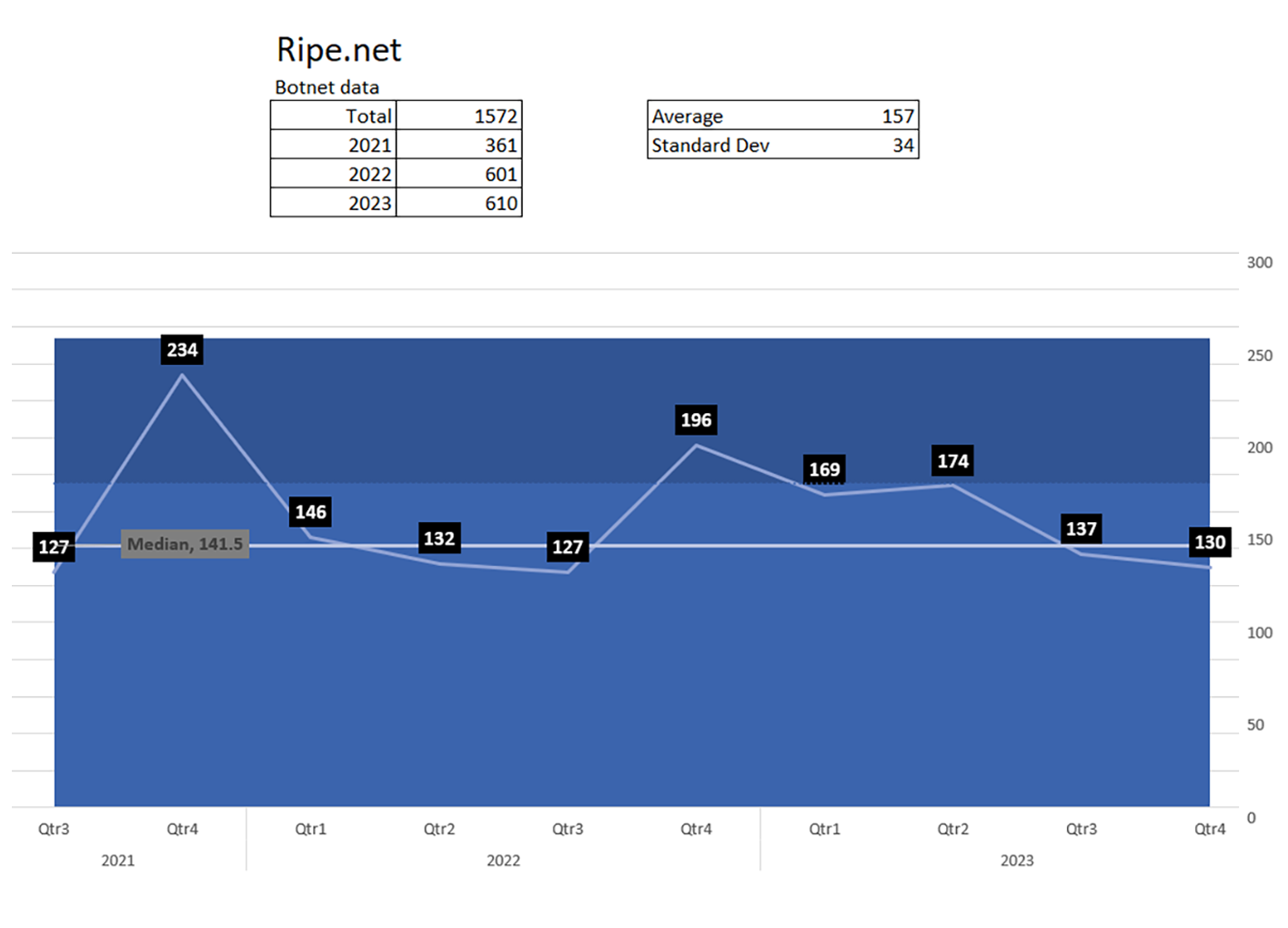
RIPE NCC
Compromised RIPE NCC customers identified (infected with malware or leaked credentials in Dark Web).
Total: 1572
1211 in 2022/23
361 in 2021
There was a concerning spike in Q3 2022 and since Q2 2023. 856 accounts have been also acquired from underground marketplaces.
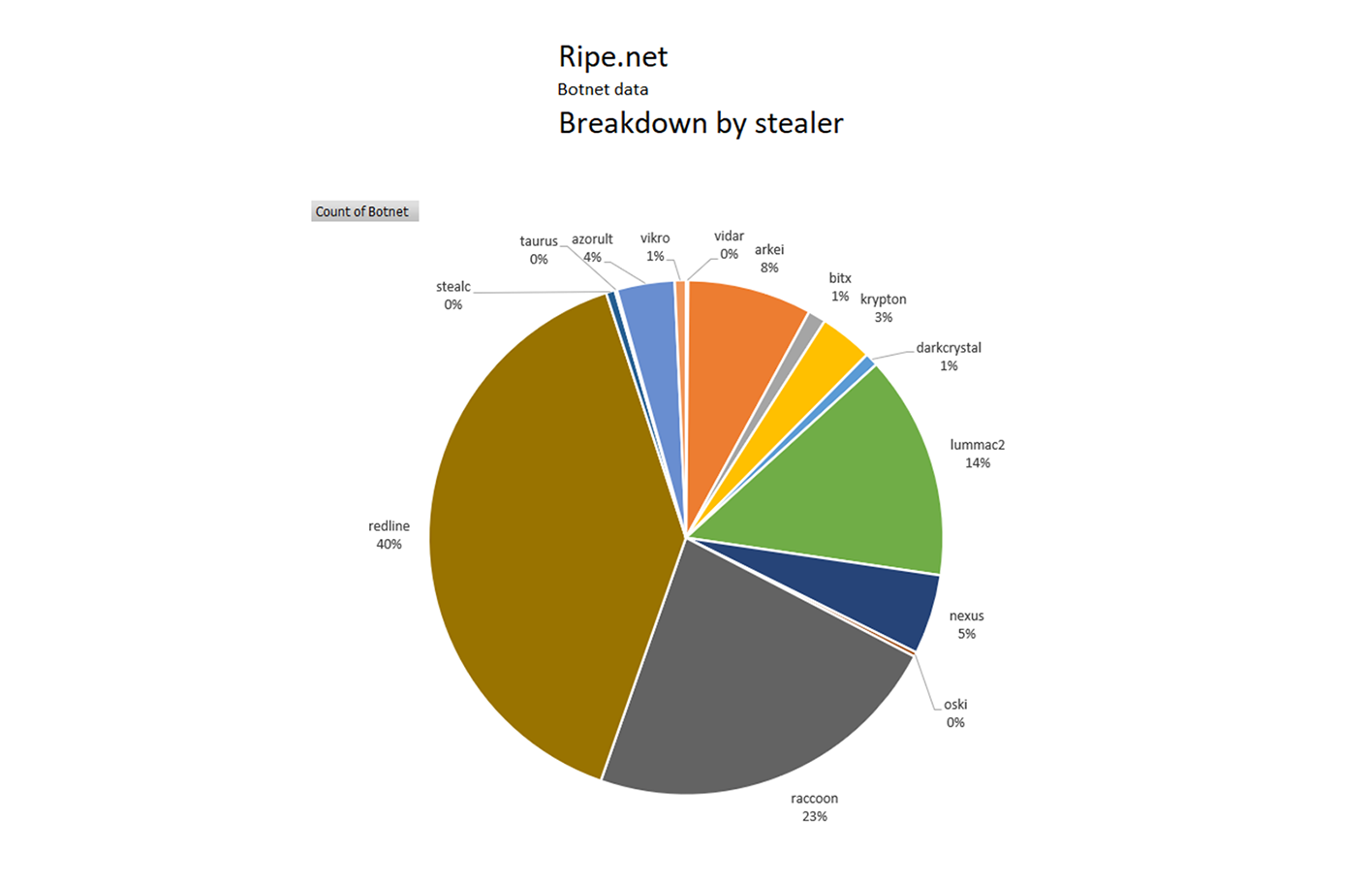
The distribution among stealers is an indicator that multiple threat actors are infecting PCs used by account holders logging into this domain.
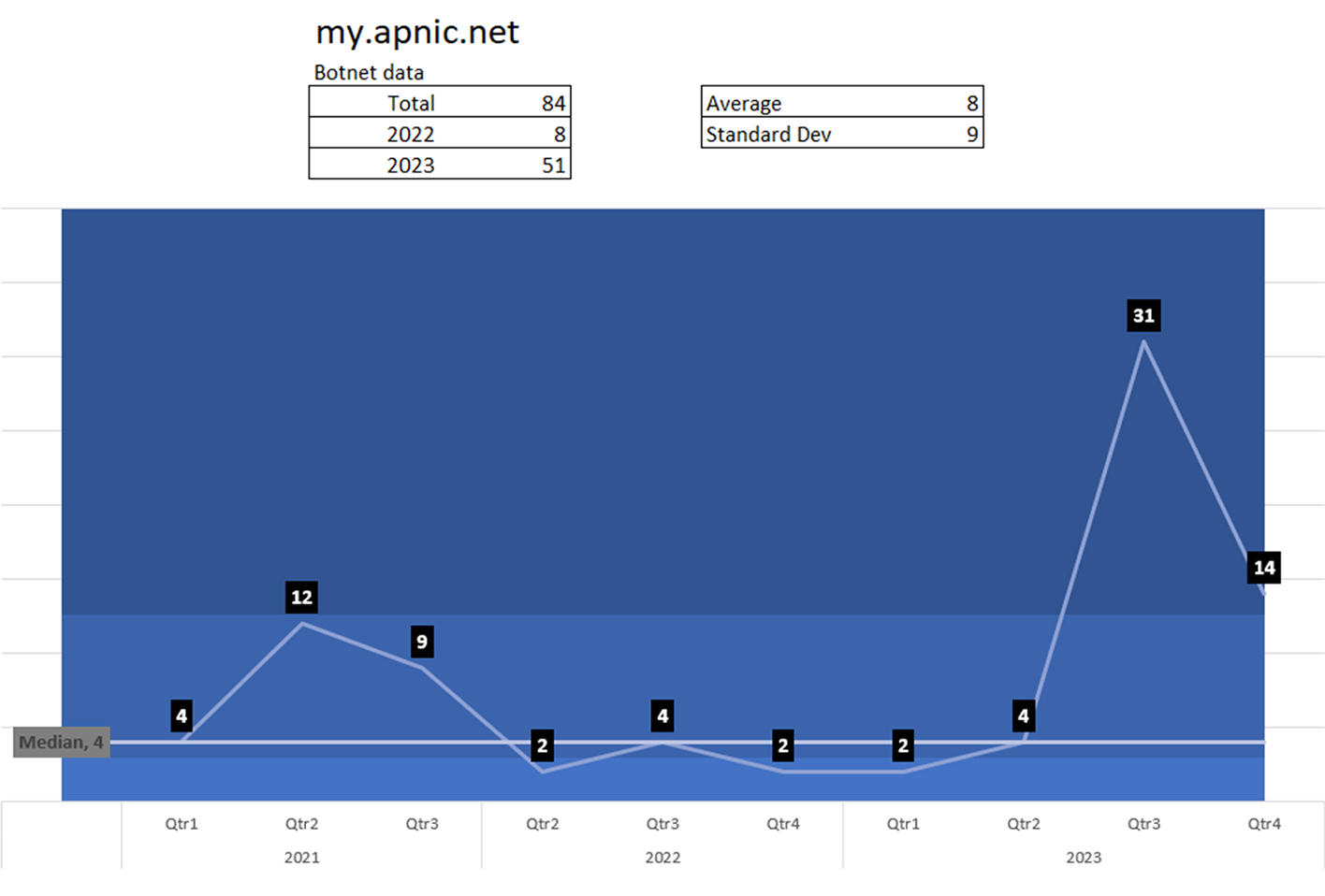
APNIC
APNIC is the regional Internet address registry for the Asia-Pacific region. Compromised customers identified (infected with malware or leaked credentials in Dark Web).
Total: 84
59 in 2022/23
25 in 2021
There was a concerning spike since Q3 2023.
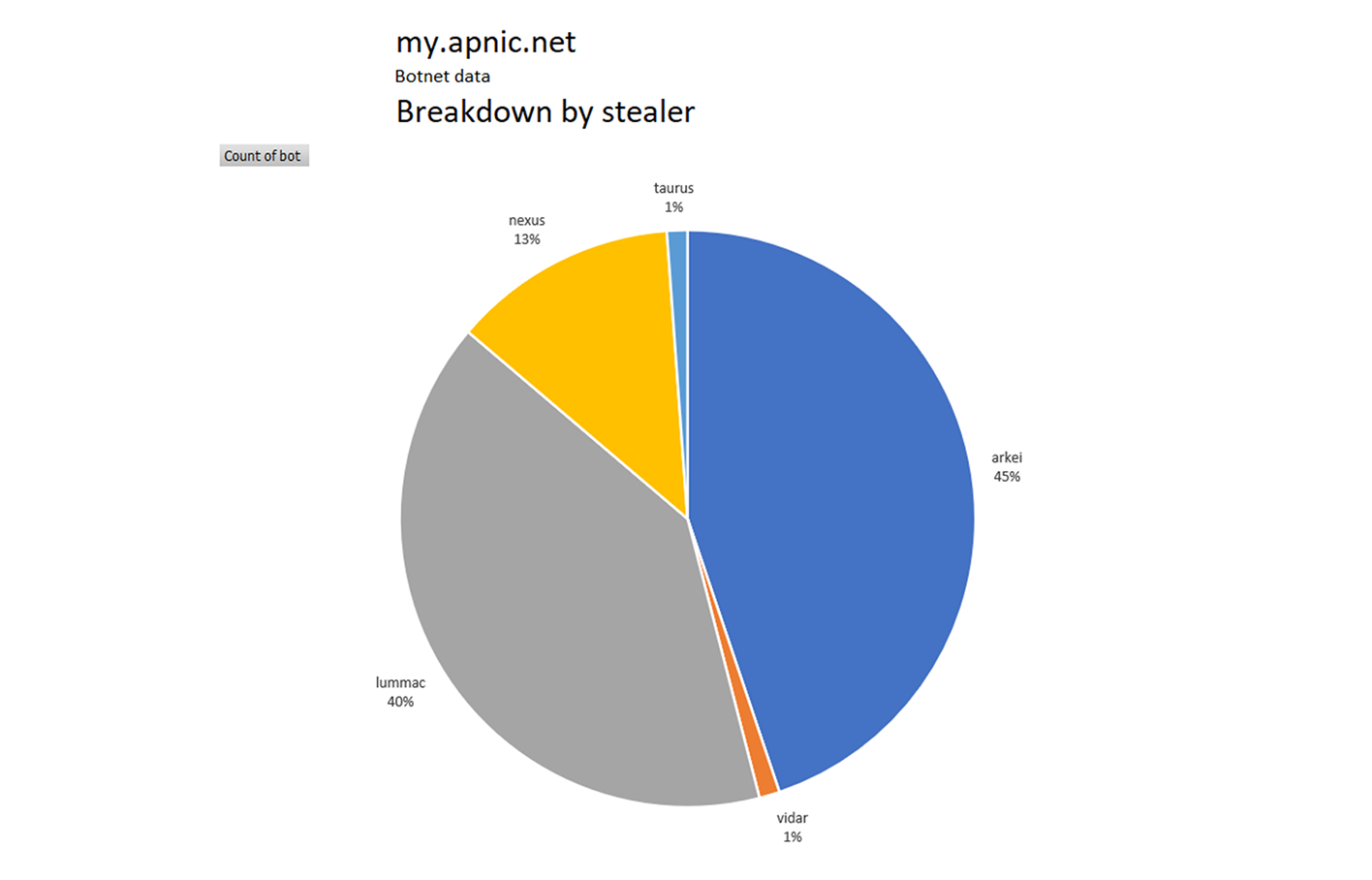
The distribution among stealers indicates that several threat actors infect PCs used by account holders logging into this domain.
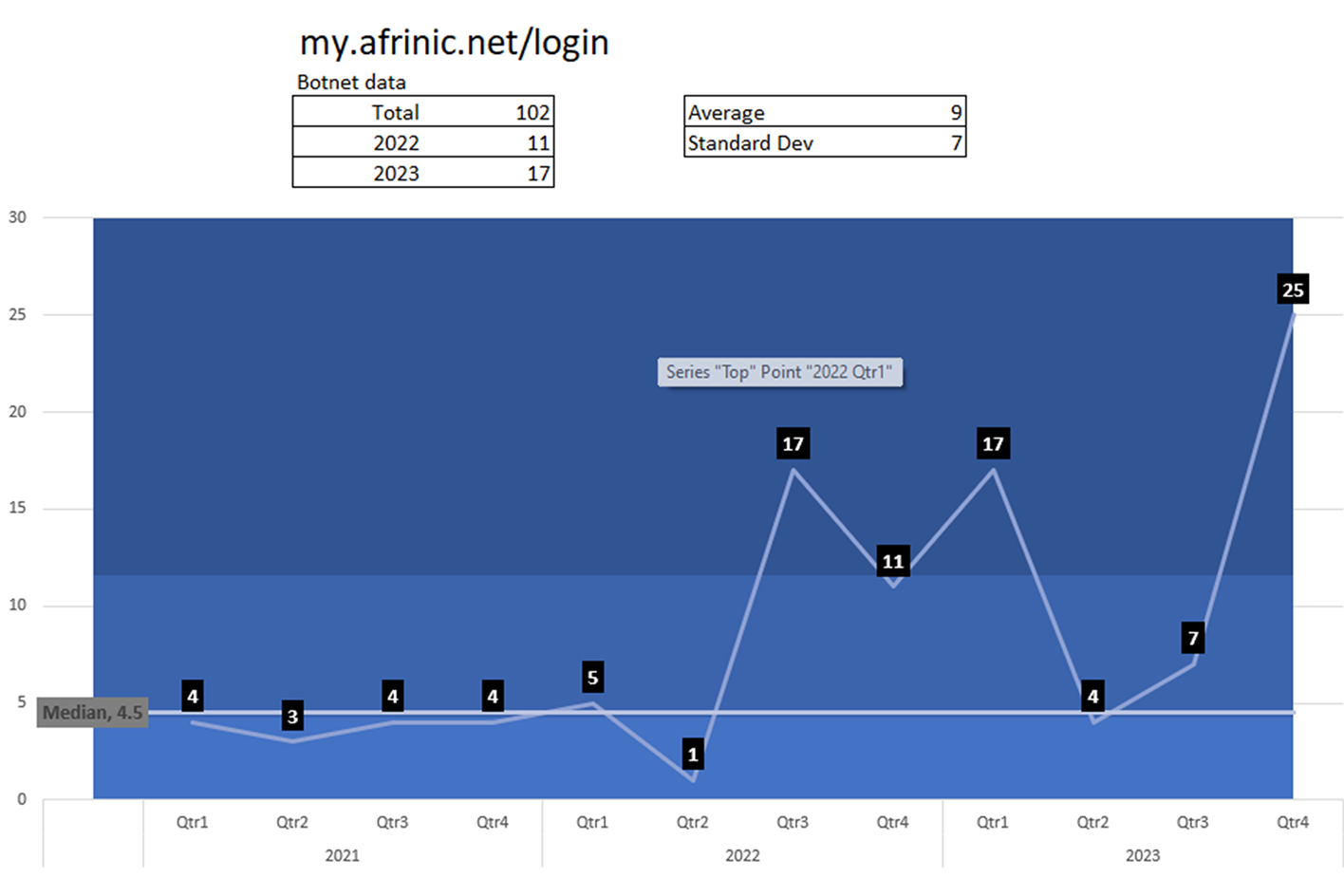
AFRINIC
AFRINIC is the regional Internet registry for Africa. Before AFRINIC was formed, IP addresses for Africa were distributed by the Asia-Pacific Network Information Centre, the American Registry for Internet Numbers, and the RIPE NCC. Compromised customers identified (infected with malware or leaked credentials in Dark Web).
Total: 102
89 in 2022/23
12 in 2021
There are two concerning spikes. Once from Q3 2022 through Q1 2023 and once starting Q4 2023.
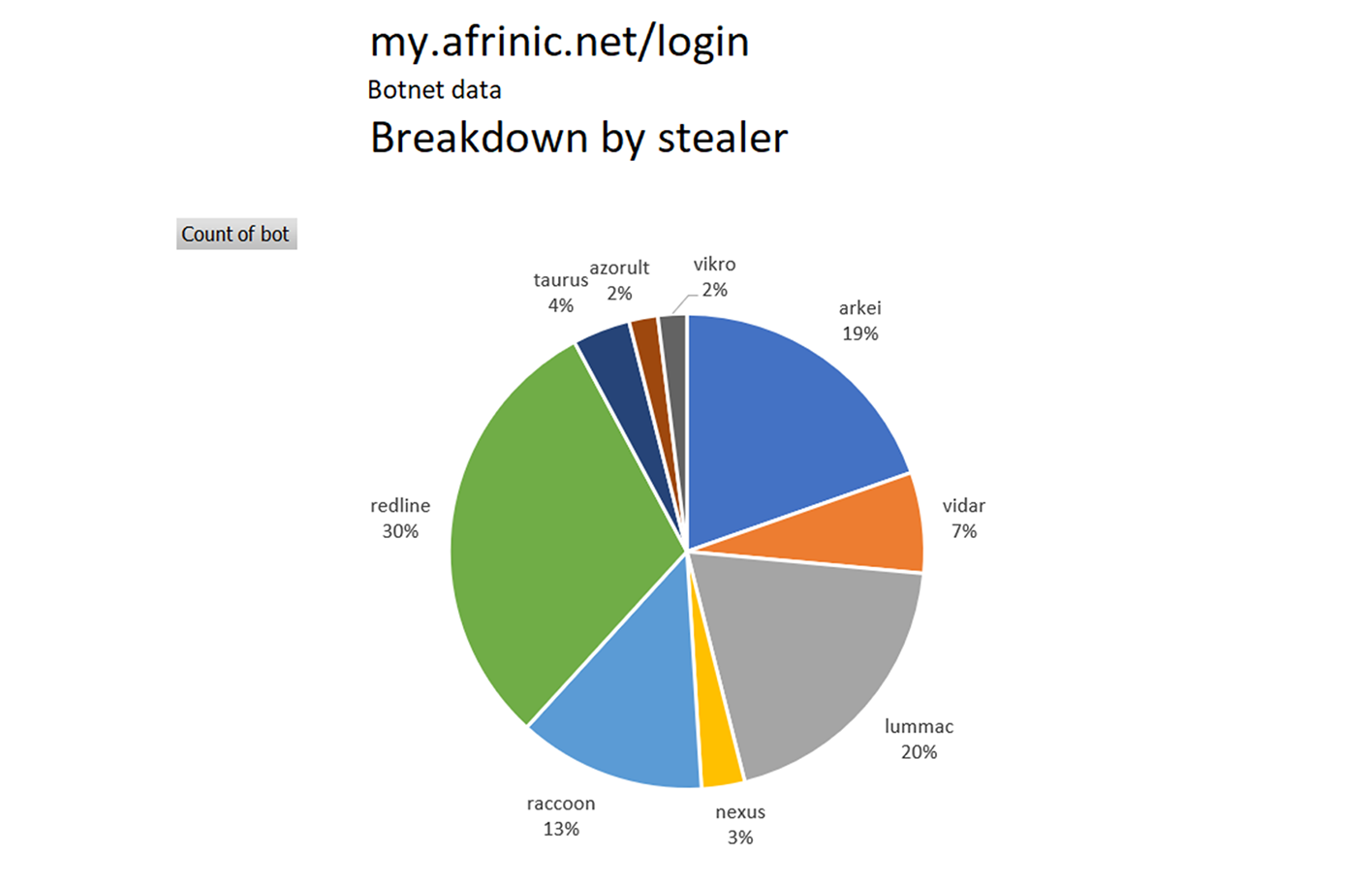
The distribution among stealers indicates that multiple threat actors infect PCs used by users logging into this URL.
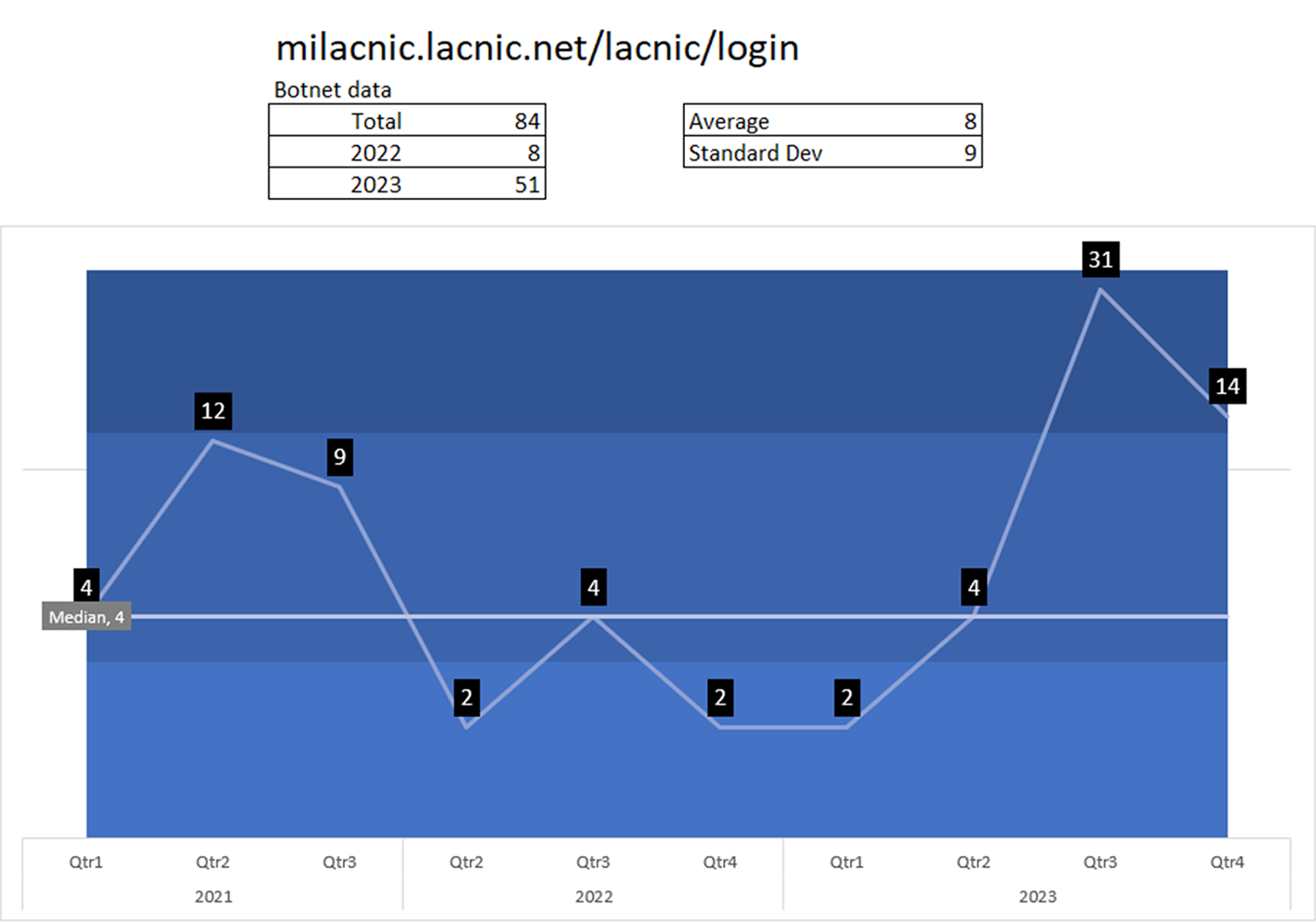
LACNIC
LACNIC is the regional Internet registry for the Latin American and Caribbean regions. Compromised customers identified (infected with malware or leaked credentials in Dark Web).
Total: 84
59 in 2022/23
25 in 2021
There are two concerning spikes - one from Q2 2021 through Q2 2021 and one starting Q3 2023.
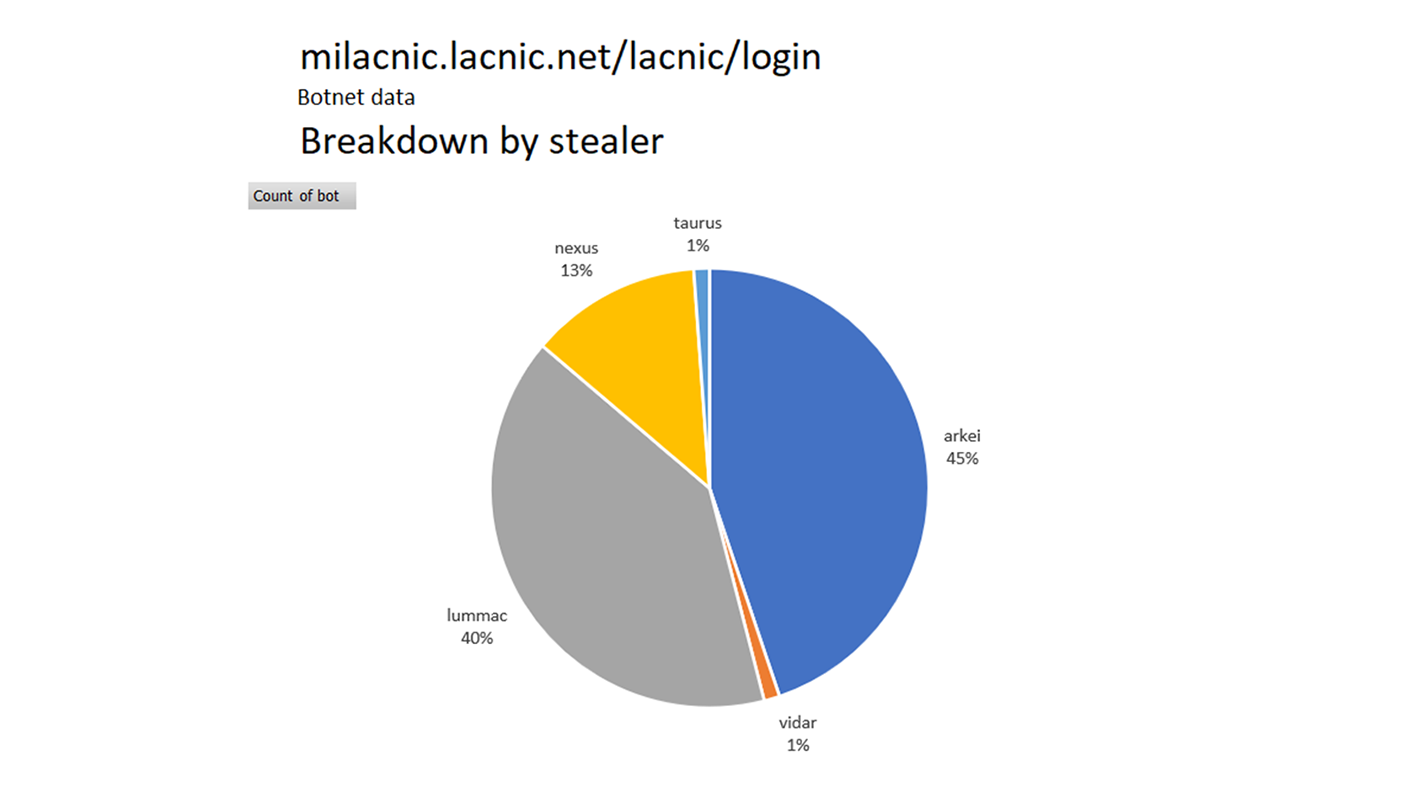
The distribution among infostealers indicates that several threat actors are infecting used by users logging into this URL.
Conclusion:
Protecting digital identity remains a key pillar of cybersecurity in the telecom industry. It's important to emphasize that cybercriminals are increasingly targeting the credentials of network engineers and telecommunications specialists. Such credentials provide direct access to infrastructure, making them valuable for conducting sophisticated cyberattacks and cyberespionage campaigns. Therefore, maintaining robust security measures and conducting constant Dark Web monitoring are crucial to protect these digital gateways and prevent unauthorized access to telecom networks.
Resecurity has notified over 1,572 victims whose credentials for RIPE, APNIC, AFRINIC and LACNIC were compromised by infostealers and exposed on the Dark Web. Based on the collected feedback, our team was able to build the following statistics:
- 45% were not aware about the identified compromised credentials and acknowledged successful password change and enabled 2FA;
- 16% were already aware about the identified compromised credentials as a result of infection by malicious code and made necessary password changes and enabled 2FA on their accounts;
- 14% were aware about the compromised credentials, but enabled 2FA only after notification (written statement received);
- 20% acknowledged the need to perform deeper investigation of the incident leading to credential compromise; for example, some of the recipients acknowledged 2FA enabled, but had a lack of knowledge around how and when exactly the compromise has happened, and what credentials (to other apps and systems) could be exfiltrated by password stealer from the victim;
- 5% of recipients were not able to provide any feedback and/or aim to identify a relevant point of contact in their organization to review this issue.
The collected statistics may confirm the staff involved in network engineering and mission critical IT management operations can also be victimized by malicious code. Their accounts (when compromised) have the potential to act as "low-hanging fruit" for massive cyberattacks. As such, this employee category represents a high-value target for sophisticated threat actors. Highlighting the risk landscape, Resecurity’s Dark Web analysis identified multiple compromised credentials belonging to network engineers that could grant threat actors access to gateways like: enterprise identity and access management (IAM), virtualization systems, various cloud providers, and backup and disaster recovery systems.
References
- The major cyberattacks on the telecommunications sector in 2023 (January 2024, Inna Serdiuk and Olga Nasibulina)
- Infostealer infection of an Orange employee results in BGP disruptions (Hudson Rock)
- How 50% of telco Orange Spain’s traffic got hijacked^H^H^H^H^H^Hnull routed — a weak password (Kevin Beaumont)
- Digging into the Orange España Hack
https://blog.apnic.net/2024/01/26/digging-into-the-orange-espana-hack/
- How to Enable Two Step Verification on a RIPE NCC Access account
https://www.ripe.net/membership/member-support/ripe-ncc-access/two-step-verification/

