How Interlock Ransomware Affects the Defense Industrial Base Supply Chain
Cyber Threat Intelligence


Introduction
Kinetic events, such as the Russia-Ukraine, Israel-Hamas, and Pakistan-India situations, along with non-kinetic or political turmoil events, have both a direct effect (participant 1 targeting participant 2) and an indirect effect (social sympathizer group targeting the participant they deem the aggressor), which drive ransomware and similar cyberattacks. The motivation behind these attacks can be to support an official action or to justify a criminal attack on a victim. However, it may also leverage the event as political cover for a cyberattack motivated by industrial or state espionage.
The situation is clear. Cyberattacks, especially ransomware attacks on defense contractors and their supply chains, have significant and far-reaching impacts. These consequences affect the targeted organizations, their supply chain, and potentially national security.
In previous threat intelligence reporting, Resecurity highlighted the cyber risks targeting the defense industrial base, specifically using the example of UAVs. Adversaries purposely target the manufacturers of technologies in that field to acquire sensitive information about the intellectual property behind them, but they also target engineers. Defense contractors are also perceived as having substantial financial resources, making them attractive targets for large ransom payments.
Resecurity is tracking the activity of Interlock Ransomware, which recently attacked National Defense Corporation (NDC) and its subsidiaries such as AMTEC. The stolen (exfiltrated) data has been published at the group's Data Leak Site (DLS) in TOR network. Its parent corporation, National Presto Industries, filed a report with the Securities and Exchange Commission (SEC) on March 6 that stated "a system outage caused by a cybersecurity incident". The DataBreaches.net tracking the latest data breaches shared some additional context on the background of these events. AMTEC is a manufacturer of lethal and non-lethal ammunition, explosives, and cartridges for military and law enforcement use.
Interlock Background - Rapid Shift in Targeting
Interlock first appeared in public in September 2024 and has been observed launching big-game hunting and double extortion attacks. According to the data leak site disclosure, the group has notably targeted businesses in various sectors, including healthcare, technology, government in the U.S., and manufacturing in Europe. This indicates that their targeting is opportunistic.
However, this appears to have changed with an incident impacting a defense contractor of AMTEC's size. Based on Resecurity's assessment, the group specifically targeted the victim companies. It is possible that the cyber-attack targeting was received from a nation-state actor. It is common for state and near-state actors to use cybercriminals as a method of geopolitical influence and as a tool for espionage. Ransomware attacks often serve as a cover for data theft and espionage activities. Attacking defense contractors allows adversaries to collect sensitive information about logistics, warehouse locations, and key personnel involved in the defense industrial base supply chain.
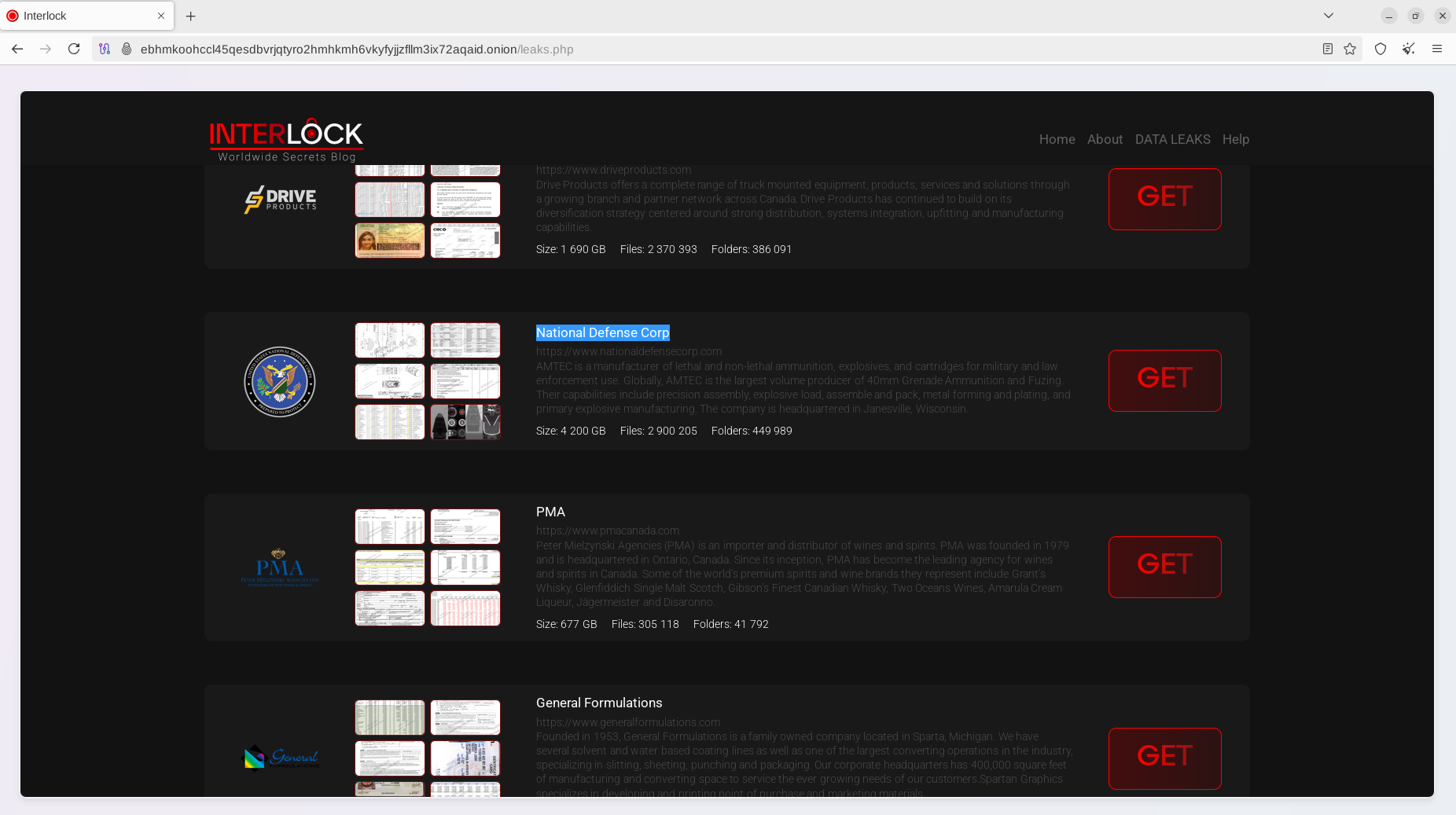
Like other ransomware players in the big-game hunting space, Interlock also operates a data leak site called “Worldwide Secrets Blog,” which provides links to victims’ leaked data, chat support for victims' communications, and the email address “interlock@2mail[.]co.”
Interlock calls itself "a relentless collective that exposes the recklessness of companies failing to protect their most critical assets: customer data and intellectual property."
Cascading Effects on the Defense Supply Chain
By attacking a defense contractor of this size, Interlock Ransomware uncovered the details about the supply chains of many other top defense contractors globally who use their products, including their end customers. The systems companies use in the defense sector may also hold classified information. Such information will be of special interest to foreign intelligence, nation-state actors, and advanced espionage groups, especially during local conflicts and ongoing wars.
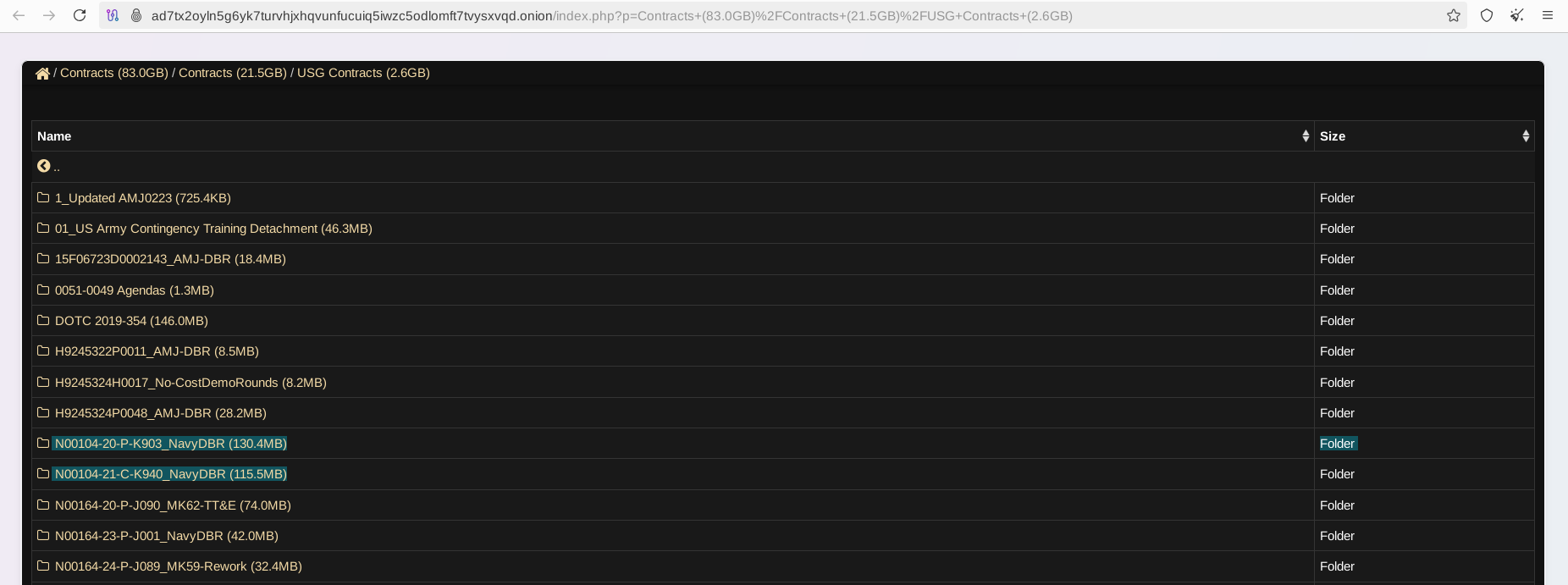
Numerous documents referencing top global defense corporations were found in the leaked dataset, including but not limited to:
- German Aerospace
- Hanwha
- Simmel Difesa
- Leonardo
- PW Defence
- Raytheon
- SpaceX
- SE Corporation
- Thales
- Talley Defense
- QinetiQ
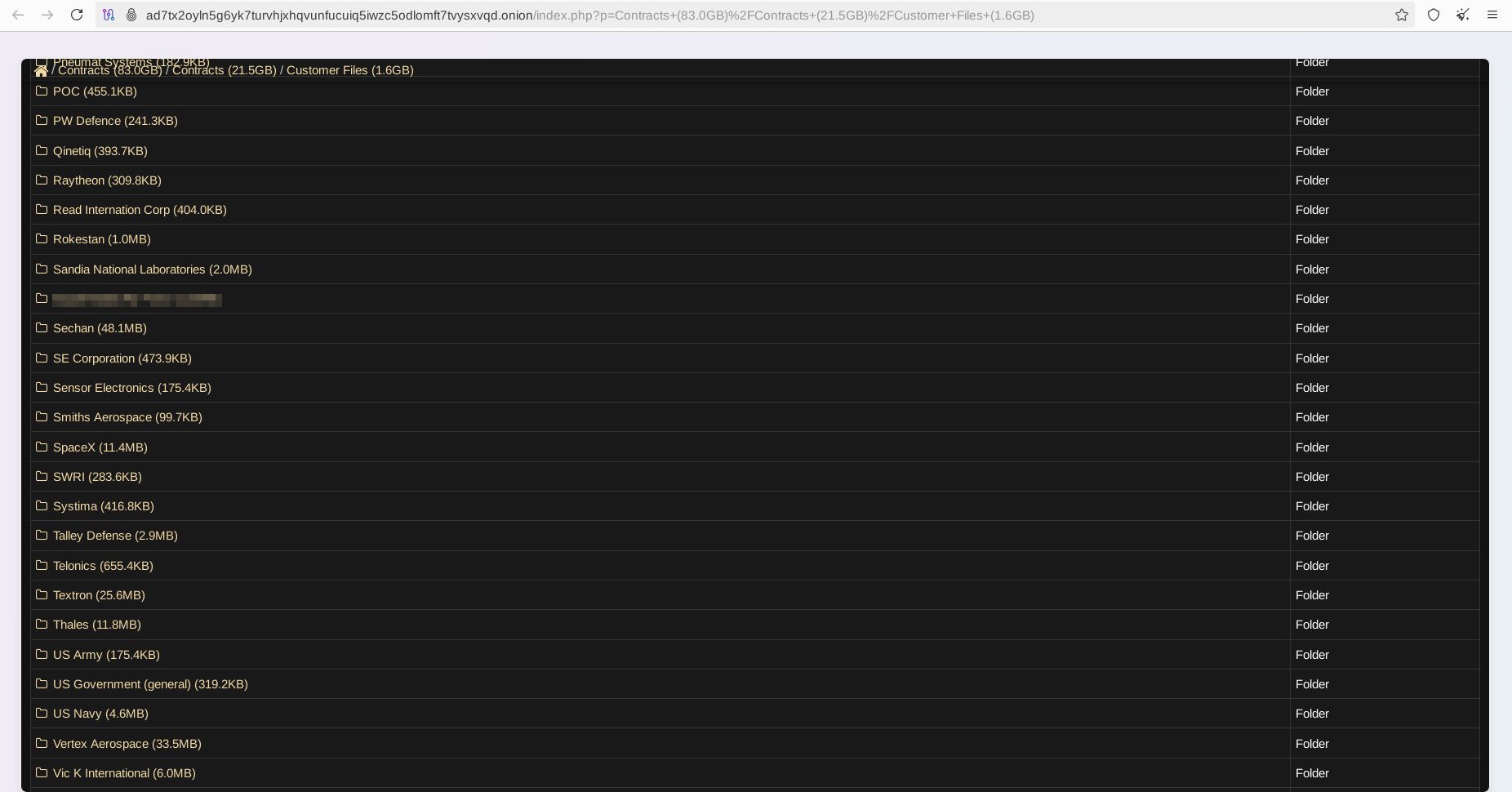
The distribution of explosives and ammunition is primarily an export-controlled and licensed business regulated by relevant defense authorities and government agencies. Information about such exports is typically not public and may contain a significant level of sensitivity, which is always of interest to foreign military intelligence.
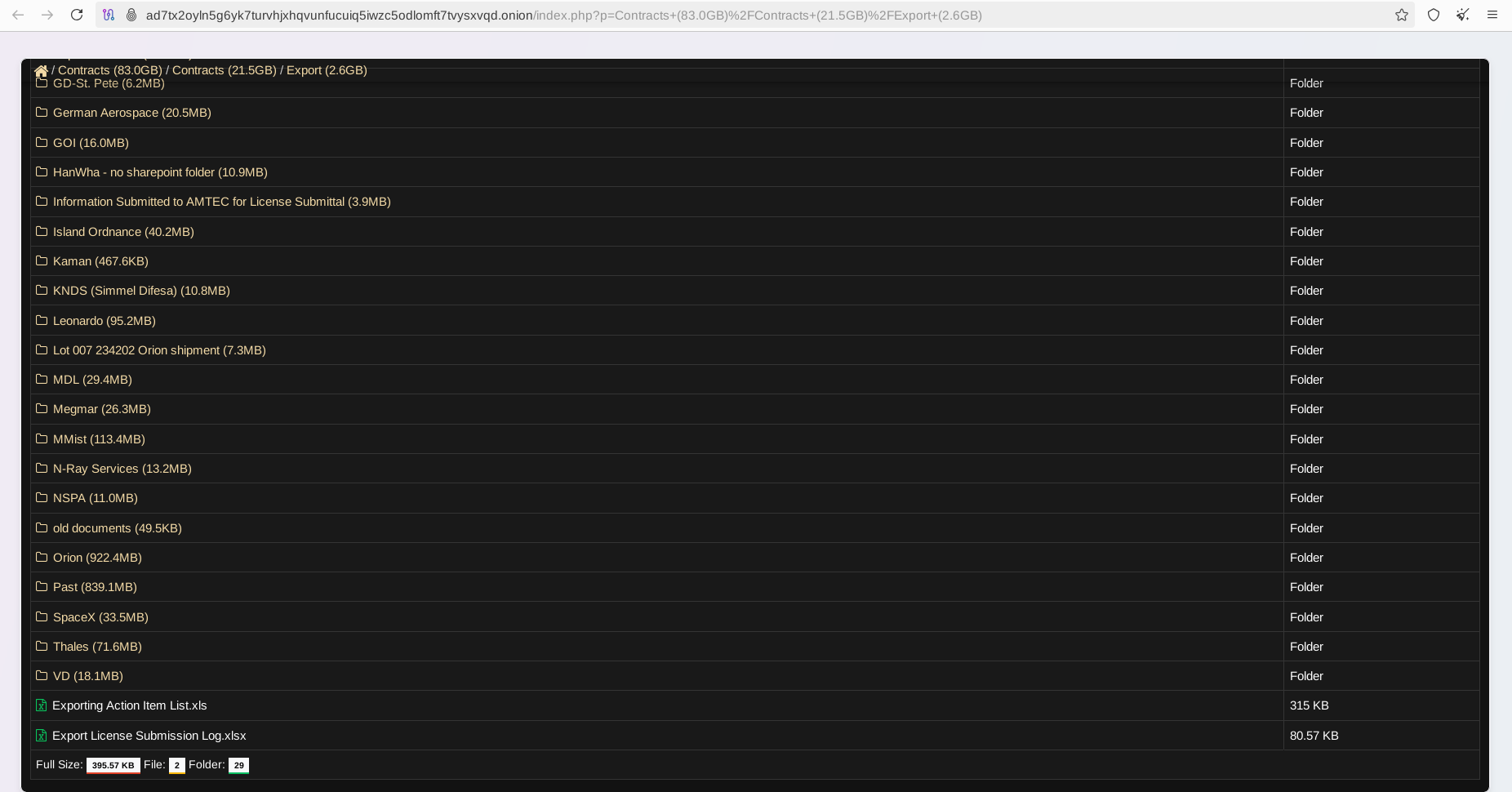
Ransomware Will Impact Military Operations
For example, by analyzing leaked shipment information and artifacts revealing the logistics chain, foreign adversaries may quickly identify the end customers and understand the purpose and aims of the weapons supply, especially during periods of ongoing geopolitical tensions.
- Information about suppliers, logistics, and distribution networks
- Details of contracts with government and military clients
- Production capacities and delivery schedules
- When a commercial carrier transports such mutations, those actors can redirect shipments during transit, thereby providing mutations to unintended third parties.
Some ransomware groups have connections to state actors, using attacks as cover for espionage or strategic disruption attacks can be used to:
- Gain strategic advantages in international conflicts
- Disrupt military supply chains
- Weaken national defense capabilities
In one such document, an order placed through a US-based entity by a major EU-based defense contractor led to the supply of defense-related products to Turkmenistan, an ex-USSR country. The end buyer was the Ministry of Defense of Turkmenistan.
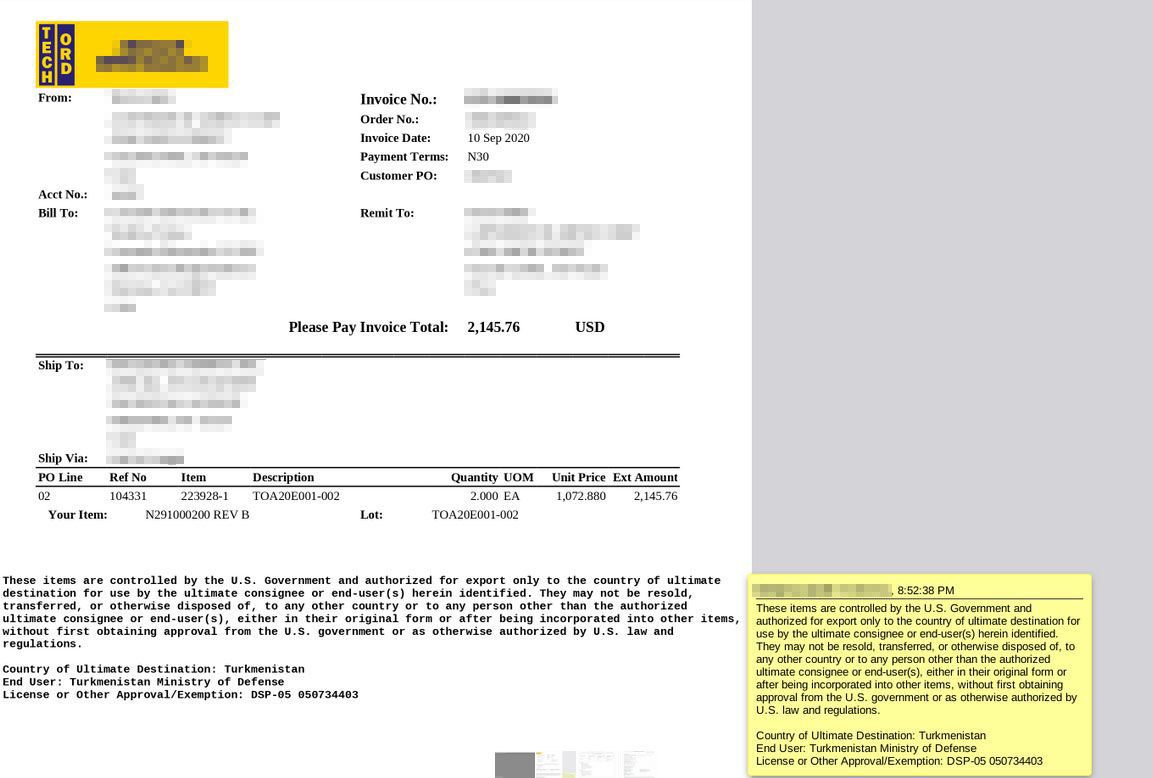
The data leak also contains multiple documents referencing contracts with the U.S. Department of Defense (DoD), disclosing the transportation codes, destinations, as well as personnel involved in handling those matters, along with intermediary contractors involved.

Implications
The combination of high financial rewards, access to sensitive data, and potential for strategic impact makes defense contractors in the explosives and ammunition sector particularly attractive targets for ransomware groups. The critical nature of their operations and the pressure to maintain continuous production create additional leverage for attackers. At the same time, the potential for state-sponsored involvement adds another layer of complexity and seriousness to these threats.
National Security Risks
Ransomware attacks on defense contractors can compromise sensitive military and defense-related information, directly threatening national security. Defense contractors often handle classified or sensitive data, including:
- Military technologies
- Weapons systems
- Intelligence operations
When this data is stolen or encrypted, it can fall into the hands of adversaries, including nation-state actors. For example, research shows that cybercriminals and state-sponsored groups increasingly target critical infrastructure and defense contractors, with each attack having a more substantial impact on national security.
Disruption of Defense Operations
Ransomware attacks can disrupt defense contractors' operations and supply chains, delaying critical projects and services. This is particularly concerning in the defense sector, where delays can hinder military readiness and the timely delivery of essential equipment or services to armed forces. Supply chain vulnerabilities exacerbate this issue, as attackers can exploit weaker links to spread malware and disrupt operations on a larger scale.
Ransomware attacks on one contractor can have ripple effects throughout the defense supply chain. Many small and medium-sized businesses (SMBs) in the defense industry lack robust cybersecurity measures, making them vulnerable to attackers. Robust cybersecurity measures are paramount to prevent such attacks and their potential spread to larger contractors or even government networks.
Loss of Intellectual Property (IP)
Defense contractors often work on cutting-edge technologies and innovations. Ransomware attacks can result in the theft of intellectual property (IP), which can then be sold on the dark web or used by adversaries to replicate or counteract U.S. military advancements. This loss of IP undermines the competitive edge of the U.S. defense industry and can have long-term strategic consequences.
What CMMC Says About Ransomware Protection
As ransomware attacks become more frequent and impactful, governments and regulatory bodies impose stricter cybersecurity requirements on defense contractors.
The Cybersecurity Maturity Model Certification (CMMC) is a framework developed by the U.S. Department of Defense (DoD) to ensure that contractors and organizations handling Federal Contract Information (FCI) and Controlled Unclassified Information (CUI) implement robust cybersecurity measures. While CMMC does not explicitly focus on ransomware alone, its requirements and practices are designed to mitigate the risks of ransomware attacks as part of a broader cybersecurity strategy. CMMC is being implemented to ensure that defense contractors meet specific cybersecurity standards. Contractors must continuously monitor and improve their cybersecurity posture to remain compliant and avoid penalties.
Key Points on Ransomware Protection and CMMC:
- Focus on Safeguarding Sensitive Information:
CMMC protects sensitive information, such as FCI and CUI,
from cyber threats, including ransomware. By requiring contractors to
implement specific security controls, CMMC helps reduce vulnerabilities
that ransomware attackers could exploit
- Alignment with NIST 800-171:
CMMC incorporates practices from the NIST 800-171 framework,
which includes controls for access management, data encryption, and
incident response. These measures are critical for preventing and
responding to ransomware attacks.
- Layered Cybersecurity Approach:
CMMC emphasizes a layered defense strategy, which is
essential for ransomware protection. This includes practices like
regular system monitoring, multi-factor authentication, and data backups
to ensure resilience against ransomware.
- Incident Response and Recovery:
Organizations certified under CMMC are required to have incident
response plans in place. These plans include steps for detecting,
responding to, and recovering from cyber incidents, such as ransomware
attacks.
- Proactive Risk Management:
CMMC encourages organizations to proactively identify and mitigate
risks, which includes implementing anti-malware and ransomware-specific
protections. This aligns with broader industry best practices for
ransomware defense.
However,
it is also important to note that this effort must expand beyond a
company’s firewall and extend to suppliers (third parties) and
suppliers of suppliers (fourth parties). For example, Resecurity’s
Risk CTI service provides both.
The National Institute of Standards and Technology (NIST) released a specialized cybersecurity framework for ransomware risk management. The “Ransomware Profile” identifies actions organizations can take to prevent, respond to, and recover from ransomware events. NIST states that “the Ransomware Profile aims to help organizations identify opportunities for improving their security and resilience against ransomware attacks.” They encourage organizations to use the document as a guide for profiling their current readiness.
How CMMC Helps Combat Ransomware:
By requiring organizations to adopt stringent cybersecurity measures, CMMC indirectly addresses ransomware threats. For example:
- Access Controls: Limiting access to sensitive data reduces the risk of ransomware spreading across systems.
- Data Encryption: Encrypting data ensures that attackers cannot access the underlying information, even if ransomware encrypts files.
- Regular Backups: CMMC-compliant organizations are expected to maintain secure backups, critical for recovering from ransomware attacks without paying ransoms.
Key Penalties for CMMC Non-Compliance:
- Loss of Eligibility for DoD Contracts:
Non-compliance
with the Cybersecurity Maturity Model Certification (CMMC) can have
significant consequences for organizations working with the
Department of Defense (DoD). While there are no direct monetary fines
for failing to comply, the penalties are primarily tied to the
inability to secure or maintain DoD contracts and potential legal and
reputational risks. The most immediate and impactful penalty for
non-compliance is the inability to bid on or win DoD contracts. The
DoD will only award contracts to organizations that meet the required
CMMC level for the specific contract. This effectively means
non-compliance can result in a complete loss of business
opportunities with the DoD.
- Legal Risks Under the False Claims Act (FCA):
If an organization falsely claims compliance with CMMC requirements, it could face legal action under the False Claims Act. This could result in significant financial penalties and legal liabilities. For
example, organizations that misrepresent their compliance status to
win contracts could be subject to lawsuits and fines.
Significance
Ransomware attacks on defense contractors and their supply chains have profound implications for national security, operational efficiency, financial stability, trust and brand reputation. These attacks highlight the urgent need for robust cybersecurity measures, continuous monitoring, and collaboration between the public and private sectors to mitigate risks and protect critical assets.
Data Leak Site (DLS)
http://ebhmkoohccl45qesdbvrjqtyro2hmhkmh6vkyfyjjzfllm3ix72aqaid[.]onion
To access a .onion website (a website on the Tor network), you generally need to have the Tor Browser installed and running. The Tor Browser is designed to interact with the Tor network, which is necessary for accessing .onion sites. You can download the Tor Browser from the official Tor Project website.
Indicators of Attacks (IOAs)
Interlock Ransomware is practicing double extortion, but their latest incidents have primarily focused on hack-and-leak operations without planting ransomware binaries. Resecurity may outline the following IOAs to assist network defenders with tracking and detecting ransomware groups:
23.95.182[.]59
195.201.21[.]34
159.223.46[.]184
23.227.203[.]162
65.109.226[.]176
65.38.120[.]47
216.245.184[.]181
212.237.217[.]182
168.119.96[.]41
216.245.184[.]170
65.108.80[.]58
84.200.24[.]41
206.206.123[.]65
49.12.102[.]206
193.149.180[.]158
85.239.52[.]252
5.252.177[.]228
80.87.206[.]189
65.108.80[.]58
212.104.133[.]72
140.82.14[.]117
64.94.84[.]85
49.12.69[.]80
96.62.214[.]11
177.136.225[.]153
188.34.195[.]44
45.61.136[.]202

