

Resecurity notified several data center organizations about malicious cyber activity targeting them and their customers. The initial early-warning threat notification about this activity was sent around September 2021 with further updates during 2022 and January, 2023. Recent cyber-attacks on cloud service providers (CSPs) and managed services providers (MSPs) saw bad actors attempt to leverage a weakness in their cybersecurity supply chain with the goal of stealing sensitive data from their target enterprises and government organizations. Data centers are meaningful targets for attackers and an important element of the enterprise supply chain.
Following the note-worthy attacks on SolarWinds and Kaseya, the threat actors continue to upgrade their tradecraft and tactics to a new sophisticated level - where data center organizations are becoming one of their major targets. While Resecurity continues to investigate malicious cyber activity related to the data center organizations, the following advisory aims to provide awareness into the cybersecurity community and network defenders. These activities remain significant for further research due to the potential of scale and where the impact affecting multiple organizations simultaneously. It is not possible to estimate the full impact of the activity observed 2021-2023 Q1, but the sharing of this advisory may facilitate further awareness.
Just recently, the credentials to presumably related data center organizations have been published to "Breached.to", an underground forum - [post 1] [post 2], successor to the notorious "Raidforums" which was seized by The Department of Justice. One such publication was identified around February 20, 2023, in the Dark Web. The information observed in the publication is almost consistent with artifacts acquired at the beginning of the campaign. Notably, February 21, 2023 the posting with one of the data centers has been removed from Dark Web forum (likely, by the bad actor), but has been indexed by our Cyber Threat Intelligence Platform and its historical copy is available in Google Cache. It is not clear how many independent actors were able to download the leaked data during this timeframe. Some fragments of this data have been also found in Telegram IM shared by various actors.
The information about this malicious activity has been shared with the affected parties and national computer emergency response teams (CERTs) in China and Singapore respectfully for further analysis and risk mitigation - CNCERT/CC, CSA SingCERT and IMDA ISG CERT. The information has also been shared with U.S. Law Enforcement due to significant major Fortune 500 corporations presence in the observed data sets - likely these organizations leverage foreign data centers for business and compliance purposes. Some of those organizations are the customers of Resecurity and were notified at the early stage of the campaign development. Many of them interpreted it as a significant risk to their supply chain and initiated further incident response. Unfortunately, such incidents remain complicated to address with proper transparency due to cross-border privacy and data protection acts, as well as the sensitive nature of the events.
Resecurity identified several actors in the Dark Web potentially originating from Asia, they managed acquired access to the “customer” records and exfiltrated them from one or multiple databases related to specific applications and systems which are leveraged by several data-center organizations. In one of the cases reported to CNCERT/CC, it’s likely the initial access was gained via a vulnerable helpdesk or ticket management module having integration with other applications and systems, and based on our assessment could allow them to perform lateral movement in one of the observed episodes.
The actor was able to extract a list of CCTV cameras with associated video stream identifiers used to monitor data center environments, as well as credential information related to operators (IT staff at the data center) and customers. Once the customer credentials were collected, the actor performed active probing to the customer panels aiming to collect information about the representatives of the enterprise customers who manage operations at the data center, list of purchased services, and deployed equipment. Besides that, the actor applied effort to research the availability of the "Remote Hands Service" (RHS) feature provided by data centers to enable customers to manage their servers remotely and troubleshooting them as and when needed. The artifacts related to CCTV cameras have been acquired via Human Intelligence (HUMINT) engagement with the actor. Each device had its own ID and reference "DC_ID" (likely, from “data center”) with relatively simple passwords. In addition, "camera_code" field had enumeration such as "C-097", "C-098" and etc.
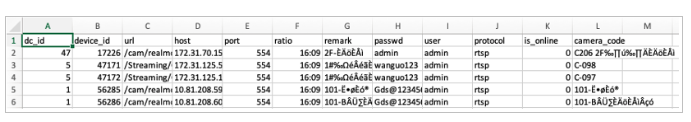
Moreover, additional acquired artifacts having references to "iot_atis" and "sys_camera" as well as possible helpdesk / ticket management system which was likely attacked. Such configurations could be used to video monitor clients' equipment deployed in the data center. Unfortunately, we haven't received any feedback in this regard from the affected parties.

More detailed information about available flags is provided below. The names of the fields are consistent with names of record structure published on "Breached.to" forum.

During the 1st episode of the identified campaign, the actor was also able to collect various records (according to our assessment, with moderate level of confidence, over 2,000) - presumably credentials, e-mail, cellphone, and ID card references, likely to be used for certain client verification mechanisms. After communication with CNCERT/CC around January 24, 2023, the affected organization forced customers to change their passwords.
In conjunction with that, the actor was able to compromise one of the internal email accounts used to register visitors - which could then be used for cyber espionage or other malicious purposes. Information about visitors may disclose important information about the exact staff responsible for data center operations from the client side. This information with related artifacts has been also shared with CNCERT/CC.
During the 2nd episode of the same campaign, the actor was able to exfiltrate a customer database presumably containing 1,210 records from another data center organization which has an HQ in Singapore. The actor acquired customer records in 2021 presumably via a similar scenario - customer service portal / helpdesk / ticket management system, and likely continued to leverage exfiltrated credentials for further access probing of available portals and apps. Based on our assessment, the activity was successfully detected by the affected party.
In January 2023, several additional artifacts were acquired which may confirm the access attempts to customer portals of 10 different organizations, some of which were based in India. It is not clear if such access was possible simply because multiple customers didn't change their passwords after the incident in 2021, lack of awareness or response, or the episode may have been interpreted as “new”. Notably, the observed customer portals included several (typical for data center organizations) features including Remote Hands Service (RHS), access permission and material movement. The information about this incident has been shared with CSA SingCERT.
After prompt communication it was determined the issue observed may be related to an episode from 2021, but the details about these findings remained foggy as well as the window of exposure (WoE). Resecurity has reached out to multiple parties (clients under protection and partner organizations) in order to collect feedback about the origin of those credentials - some contacts confirming the use of the credentials have been utilized by them and their IT staff, and that data center was used either for disaster recovery or active operations in the APAC region. Notably, some of the interviewed organizations stated how they never received any notification about any possible incidents resulting in their credential leakage and were not aware about it. Some organizations confirmed the opposite, and they received certain communications about the need to change passwords. Obviously, the incident response on such activity requires time and coordination, and at this stage we do believe the potentially impacted parties made significant efforts to contain this activity successfully.
January 28, 2023 - the actor published the stolen data for sale on one of the underground communities in the Dark Web called RAMP - often used by Initial Access Brokers (IABs) and Ransomware groups. Likely, the reason behind this step was in an unexpected, forced password change by the data centers organization dating back to the 1st episode. The actor most likely realized his activity could be detected and the value of the data may drop over time, that's why the idea of immediate monetization was an expected step. Another possible reason could be the intended publication to imitate the profile of financially driven actor once the incident was detected. Such tactics are often used by nation-state actors to mask their activity, typically to blur the attack motive. A version like this is possible due to the low activity of the actor, who was creating a new persona in Dark Web and remained low key.
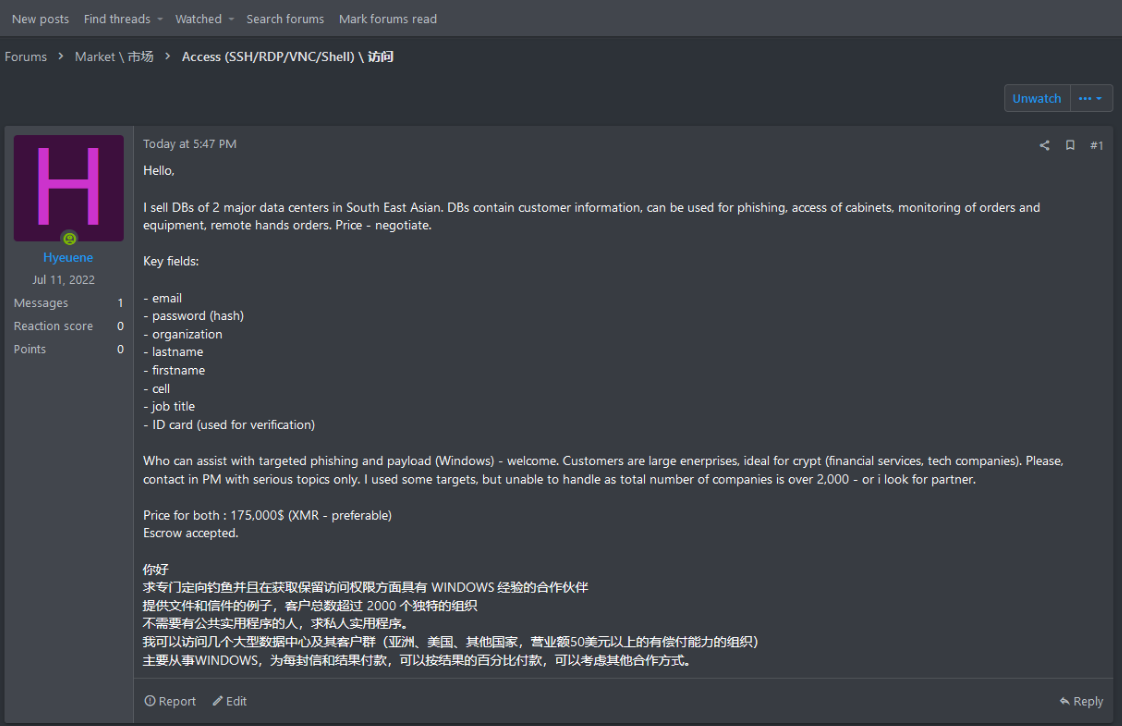
The choice of marketplace to offer this data is interesting. Some time ago, RAMP added support for Chinese language and welcomed Chinese-speaking hackers to join. The majority of forum sections have Chinese translation, and it is there where we could identify multiple actors originating from China and countries based in South-East Asia.
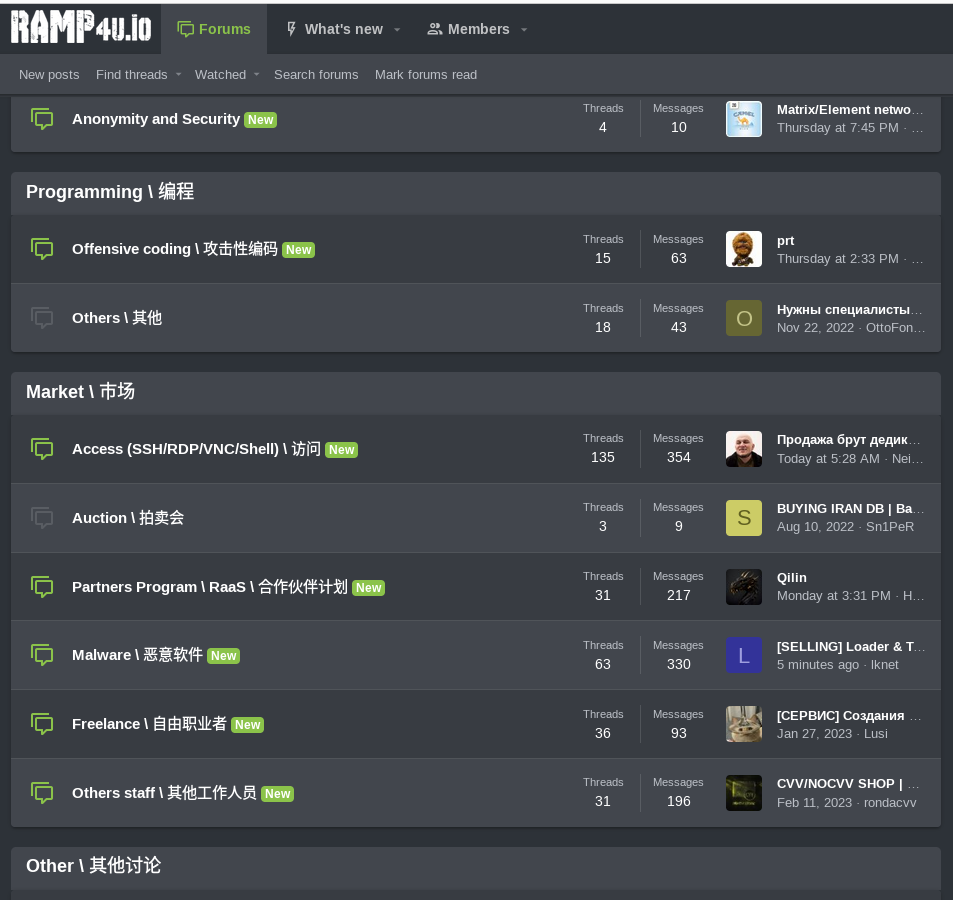
In the beginning of 2023 RAMP performed rebranding ("RAMP" vs "RAMP4U") but remained to be an underground marketplace with strong focus on ransomware operations.

The 3rd episode of the campaign was related to a U.S. based organization - operating in carrier neutral data center field. Notably, the organization was a client of one of the previously impacted data centers abroad. The information about this episode remains limited compared to the 2 previous episodes, but Resecurity was able to collect several credentials used by the IT staff which granted access to the customer portal in another data center, and also several screenshots of their client’s successful authorizations.
Most organizations identified in the leaked data sets relate to financial institutions (FIs) with a global presence, investment funds, biomedical research companies, technology vendors, e-commerce, online marketplaces, cloud services, ISPs and CDN providers with HQs in the U.S, the U.K, Canada, Australia, Switzerland, New Zealand, and China. The identified campaign may highlight the importance of the international cooperation and proactive threat intelligence sharing due to significant interconnection between data centers which are based in different parts of the world similar to their customers.
Timeline
The initial indicators of this activity were identified in September 2021 - proper early-warning threat intelligence notifications have been disseminated to two data center organizations based in China and Singapore. Additional intelligence was acquired at the end of 2022 related to the same activity and addressed for further incident response (IR) to the appropriate parties. The most recent update was received in January 2023 and shared in a timely manner. Around that time both data center organizations began forcing their clients to change their passwords and released a notification of a security policy update.
Modus Operandi
Unless such incidents are interpreted as novel by target, the attack vectors around them remain unextraordinary. Based on the observed actors' activity, most probable targets of interest for them remain as follows:
- Helpdesk systems, customer service, ticket management and support portals.
- Devices which may be potentially probed remotely including but not limited to CCTV equipment, watchdogs, etc.
- Data center visitors' management systems.
- Email accounts belonging to data center IT staff and their customers.
- Remote management and device monitoring solutions.
- Integrated Lights-Out, or ILO, a proprietary embedded server management or similar related technology such as OpenBMC, FreeIPMI and iDRAC.
Attribution
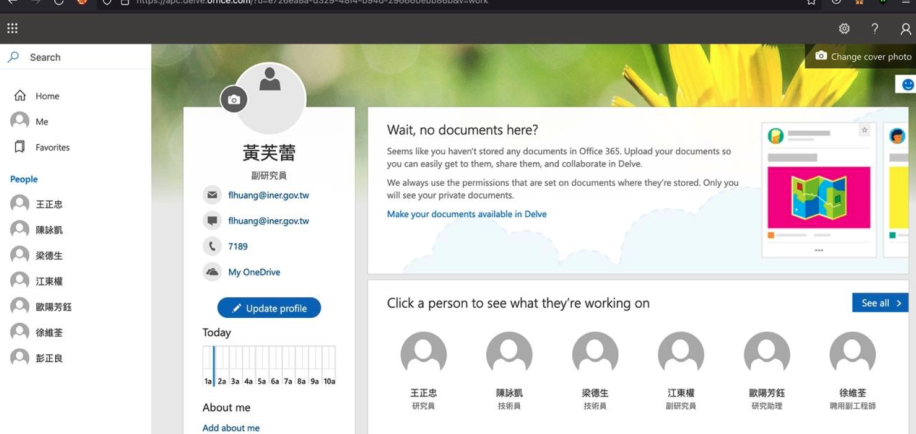
Attribution in such cases may be complicated. At this stage, Resecurity hasn't identified any notable hits with known APT groups. Typically, such groups are constantly changing their infrastructure and tooling in order to avoid detection by patterns. It is possible the victims could be compromised by multiple (different) actors. One of the notable artifacts collected from the actor was a compromised Office 365 account related to the Institute of Nuclear Energy Research (INER) based in Taiwan around September 7, 2021. The actor attempted to monetize this data in the underground via a trusted circle of contacts. Similar accounts have been offered for sale from organizations based in Thailand, Vietnam, Brunei, and Malaysia in 2022. The information about this incident has been shared with authorities in Taiwan as well as domestic law enforcement partners.
Significance
Malicious cyber activity targeting data center organizations creates a significant precedent in the context of supply chain cybersecurity. Resecurity expects attackers to increase malicious cyber activity related to data centers and their customers. Network defenders should evaluate proper measures to mitigate such vectors from both OT and IT supply chain cybersecurity. It’s also crucial to have a transparent communication with suppliers regarding possible cybersecurity incidents which may involve client accounts and related data.
Disclaimer
The information about this campaign and related incidents provides awareness into the cybersecurity community. Resecurity has addressed the identified incidents voluntarily with a goal to facilitate timely risk mitigation and investigation. Data breaches related to supply chain cybersecurity remain significant to public interest due to the involvement of advanced threat actors, including nation states and sophisticated cybercriminal and espionage groups. As described in this advisory, Resecurity expects an increase of targeted attacks on data center organizations. We appreciate a timely response and attention to our findings by CNCERT/CC and CSA SingCERT, and facilitation of timely information sharing with the affected parties.

