

Introduction
On September 8, 2025, the notorious ransomware group KillSec claimed responsibility for a cyberattack on MedicSolution, a software solutions provider for the healthcare industry in Brazil. The group has threatened to leak sensitive data unless negotiations are initiated promptly.
Healthcare IT Supply Chain as a Target
The attack scenario via a critical supply chain IT vendor may put many healthcare organizations in Brazil at risk, especially their patients, as such systems aggregate massive amounts of sensitive personally identifiable information (PII). Hackers attack supply chain because it allows them to compromise multiple targets efficiently and generate more profit through large-scale data theft, ransom demands, and payment diversion. The trusted relationships between organizations and their suppliers make these attacks both lucrative and difficult to defend against. Supply chain attacks are often difficult to trace and can persist undetected for long periods, allowing hackers to maximize their gains before being discovered. It is not clear whether KillSec Ransomware will pivot to attacking downstream healthcare organizations, but such a scenario is possible considering the trend with victims published on their DLS website on TOR.
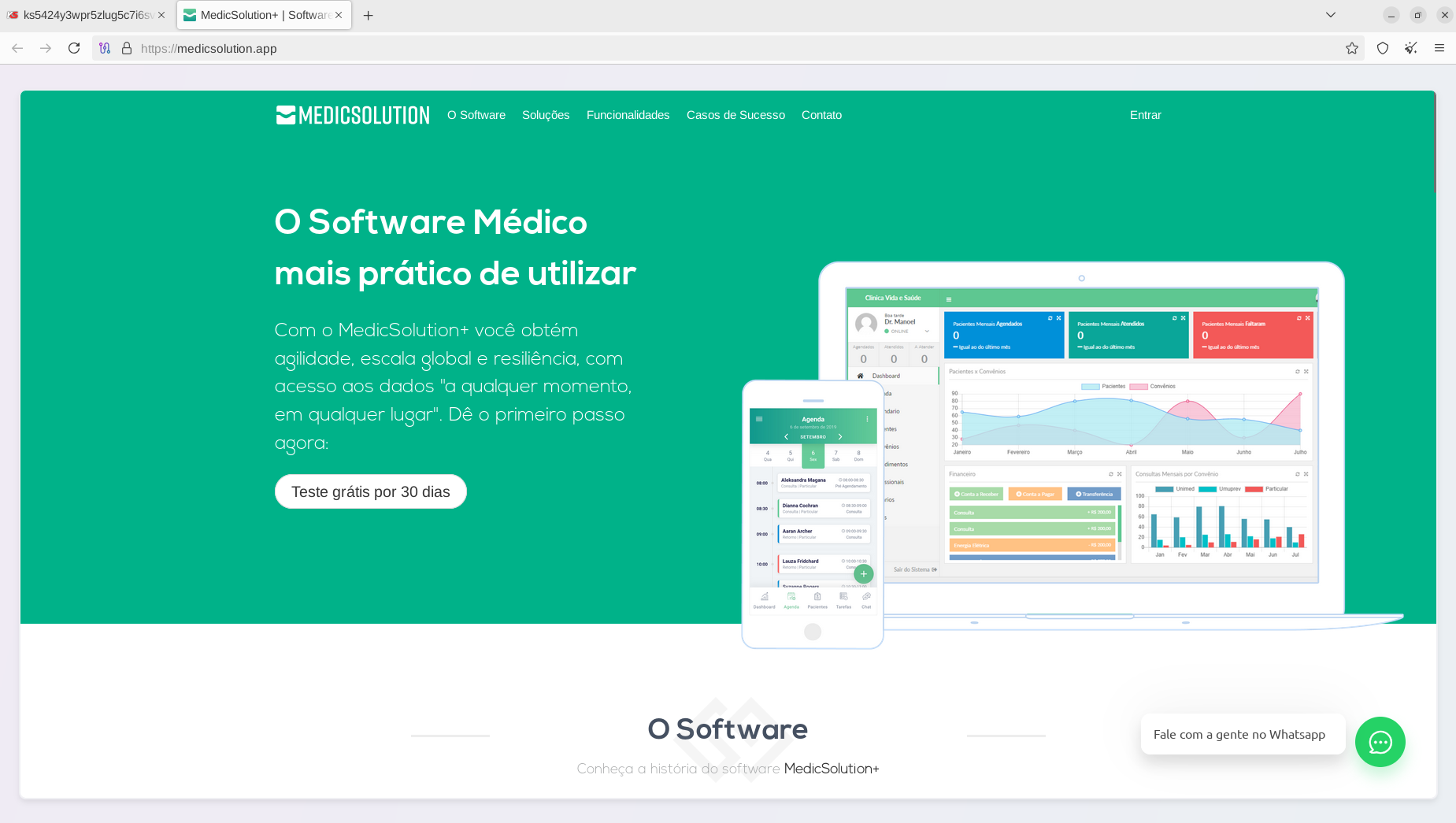
MedicSolution+ delivers intuitive, cloud-based software designed to streamline clinic and practice management. Our platform empowers healthcare professionals with real-time scheduling, multi-platform access, and robust data security, ensuring seamless operations and enhanced patient care. Targeting clinics and medical professionals, MedicSolution+ offers a user-friendly mobile app, intelligent appointment systems, and scalable cloud storage, eliminating the need for costly infrastructure. Trusted by doctors for its simplicity and reliability, MedicSolution+ transforms healthcare management with modern, secure, and accessible solutions.
Notably, it is not the first time the ransomware group has targeted Brazil. Some time ago, the actors leaked personal and business data containing CNPJ/CPF identifiers, transaction amounts, banking information, and other data from government resources in Brazil. At that time, the group did not clarify the full scope of the breach or its possible source. KillSec Ransomware was known for both confirmed incidents and fakes or speculations.
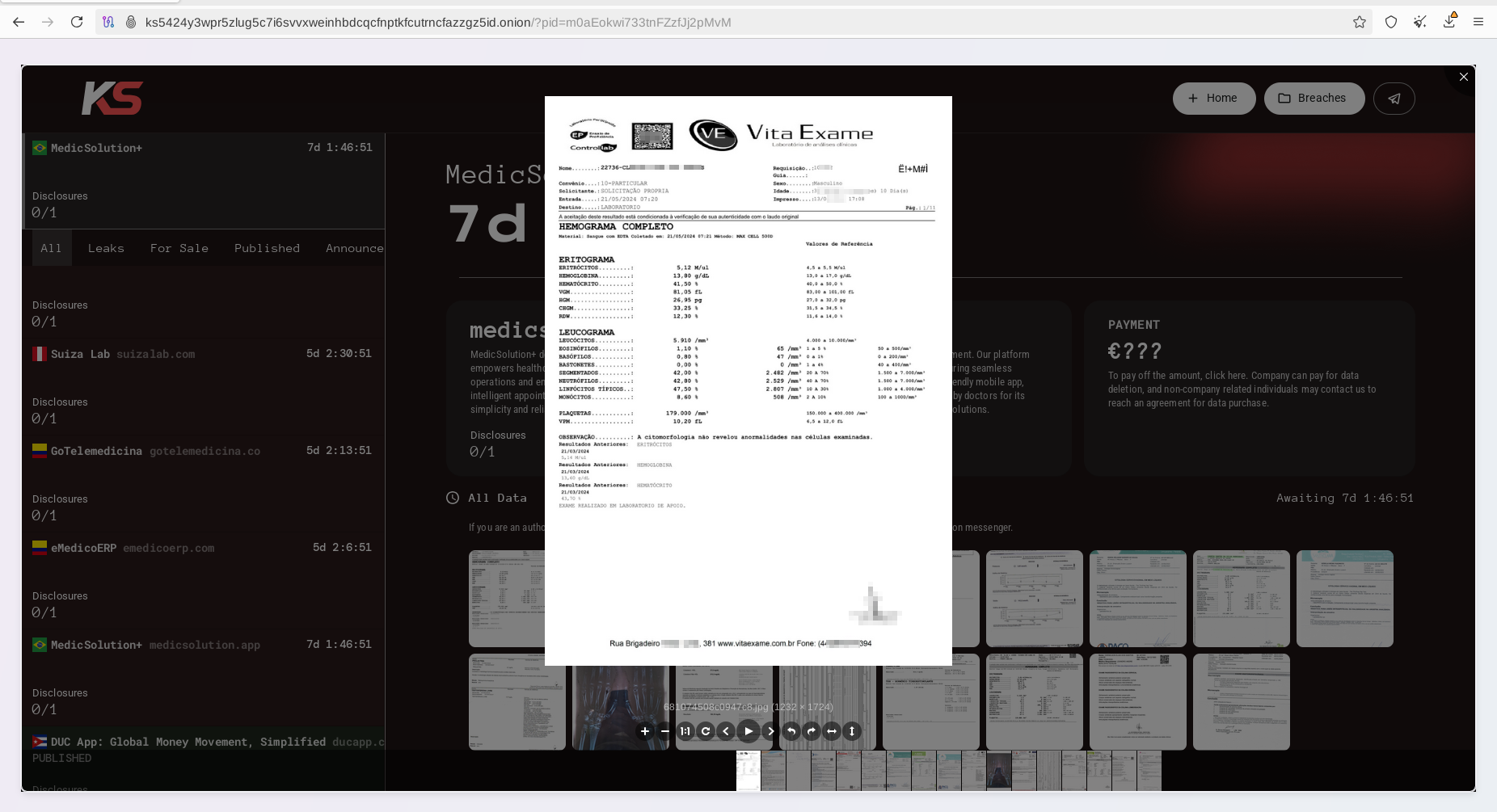
Unfortunately, this time KillSec Ransomware hit Brazil hard. Stolen healthcare data contain sensitive laboratory results reports, medical assessments, and other privacy-sensitive information. Resecurity identified several patients and contacted them - none of whom was aware of this incident as of today.
Cybercriminals use stolen data from healthcare institutions for extortion, understanding that it will cause significant damage not only to the victim organization but also to its end customers, given that numerous patients do not expect their information to be published online.
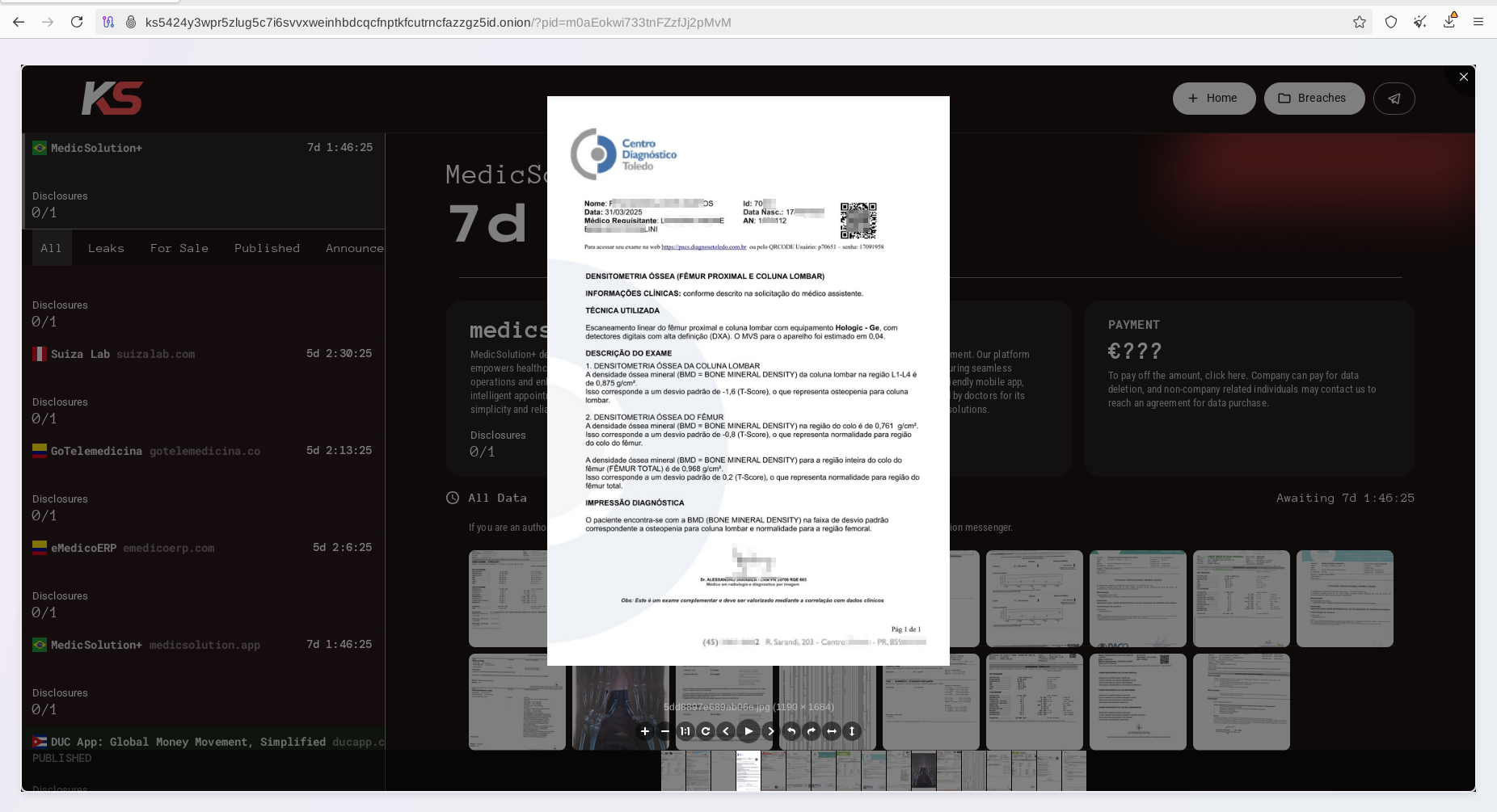
By attacking a major element of the healthcare IT supply chain, KillSec ransomware actors quadrupled their results compared to an attack against an individual target. By compromising a software vendor, they affected other healthcare institutions at scale. Resecurity observed documents belonging to local healthcare institutions and medical labs in Brazil, including, but not limited to, Vita Exame, Clinica Especo Vida, Centro Diagnostico Toledo, Labclinic, Laboratório Alvaro, and many others.
Data Breach Scope
The total volume of stolen data exceeds 34 GB, containing over 94,818 files. The compromised data include:
- Medical evaluations
- Medical lab results
- X-rays
- Unredacted patient pictures, including those showing body parts
- Records related to minors
Critical Timing
Notably, KillSec ransomware actors also targeted healthcare institutions in Colombia, Peru, and the United States a few days before Brazil. Such timing demonstrates the increasing interest of cybercriminals in the healthcare field.
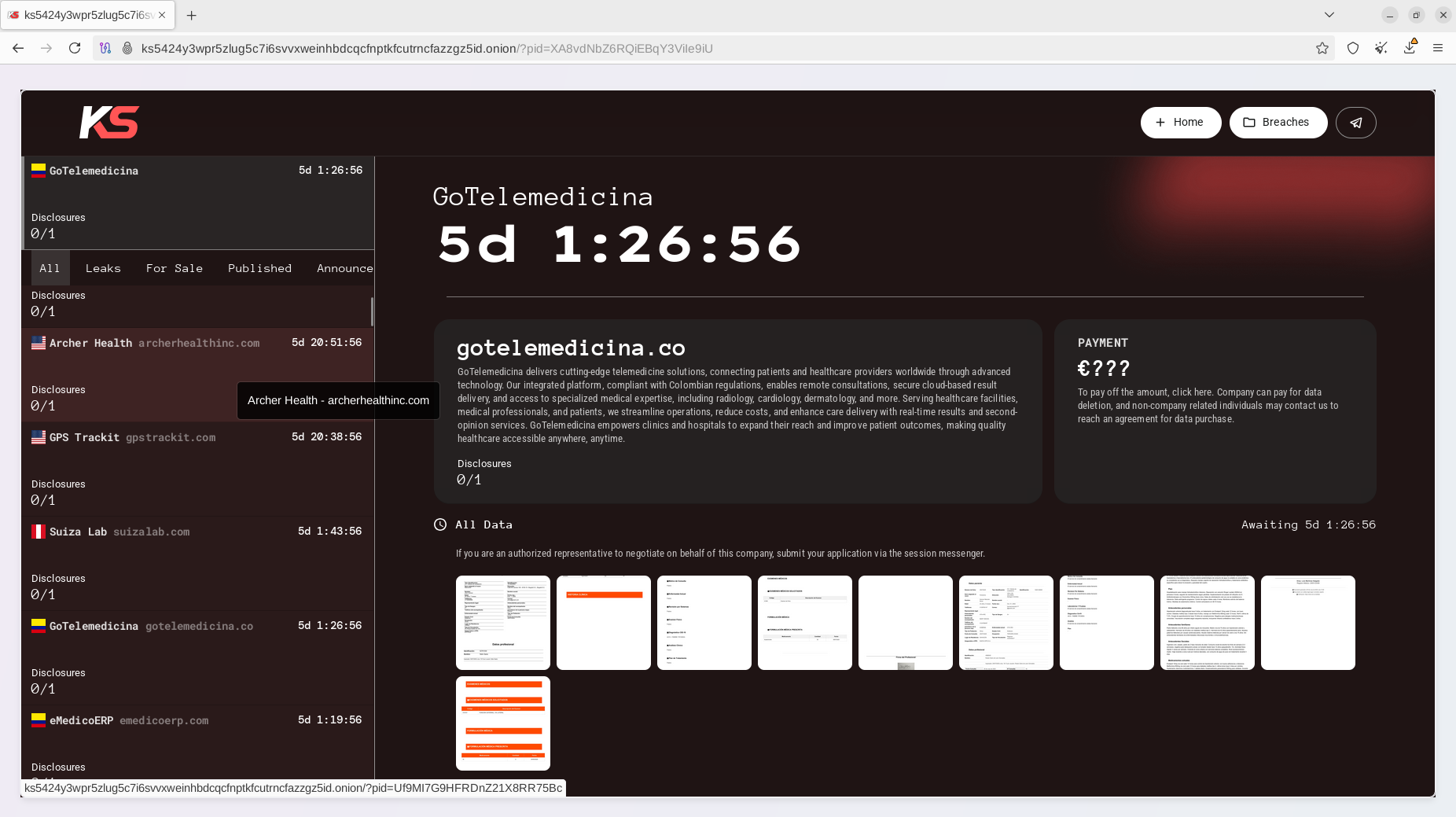
Two days ago, actors announced the successful compromise of several notable healthcare organizations:
- Archer Health (USA)
- Suiza Lab (Peru)
- GoTelemedicina (Colombia)
- eMedicoERP (Colombia)
One month ago, the actors leaked data from Doctocliq, a prominent healthcare software platform in Peru that serves over 3,500 doctors across more than 20 countries. The platform is designed for medical and dental professionals. In the past, the group also targeted the Royal Saudi Air Force (RSAF) and released several new leaks from sectors outside healthcare, including the compromise of Nathan and Nathan (UAE), an HR, staffing, and technology solutions provider, as well as Ava Senior Connect (USA), a communication platform designed for senior living communities.
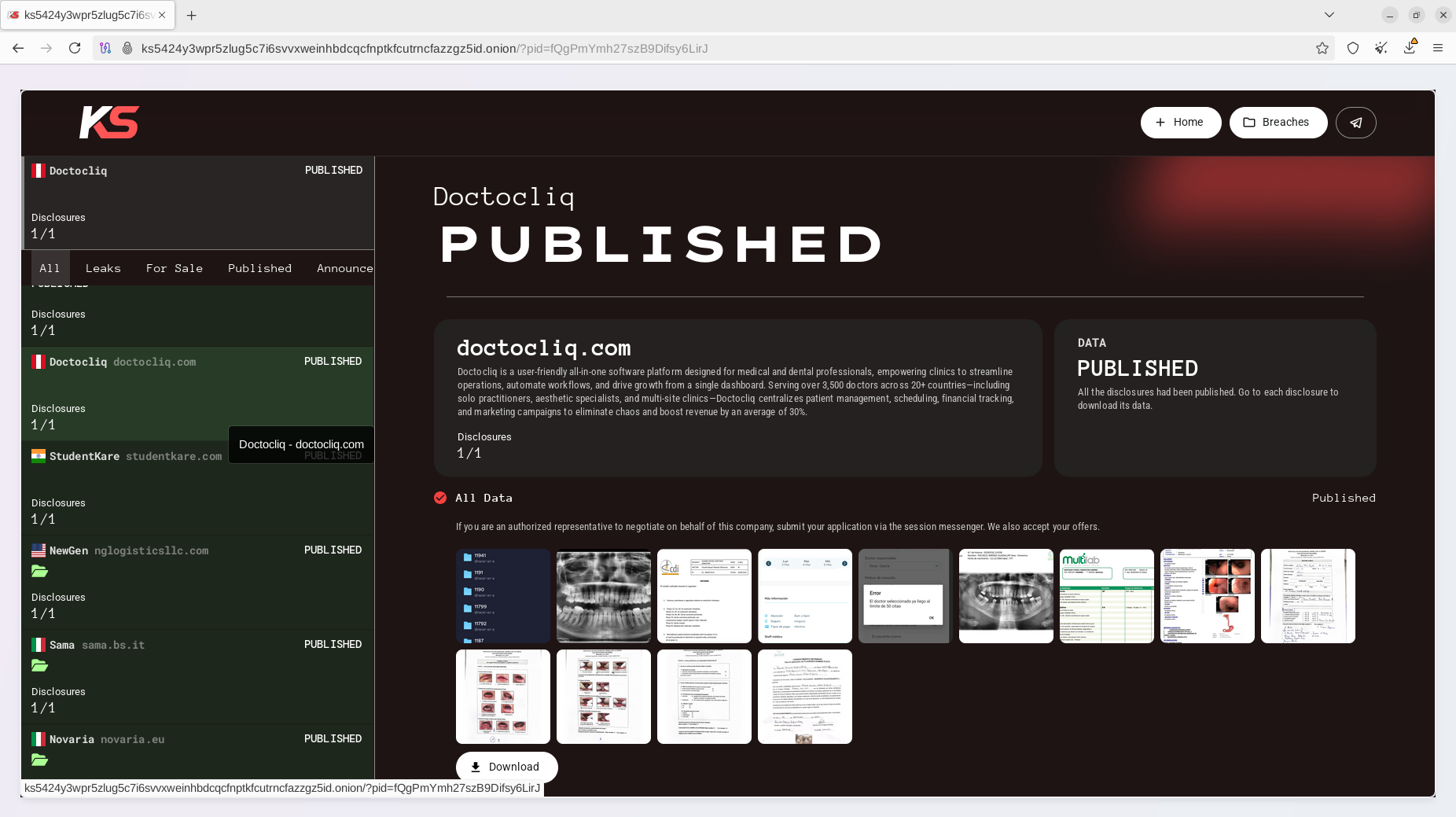
Unfortunately, Brazil is the latest target of KillSec ransomware, resulting in significant privacy damage to its citizens.
Root Cause of the Breach
What do all these data breaches affecting healthcare organizations have in common? Resecurity was able to conduct an investigation based on available artifacts and locate stolen files stored in exposed AWS cloud buckets. Our specialists from the HUNTER team were able to map the stolen data to specific S3 storage locations, and they had a listing of all exposed files in plaintext.
Notably, at the time of the ransomware claims, the issue had not been contained and the data remained vulnerable to remote exfiltration, which demonstrates substantial gaps in incident response and a lack of awareness among victim organizations operating in the healthcare field. Resecurity reached out to the victim but received no response. To facilitate incident containment, our team has shared available findings with CERT.br (Computer Emergency Response Team Brazil) and the Autoridade Nacional de Proteção de Dados (ANPD), which oversees LGPD compliance, investigates breaches, and imposes sanctions.
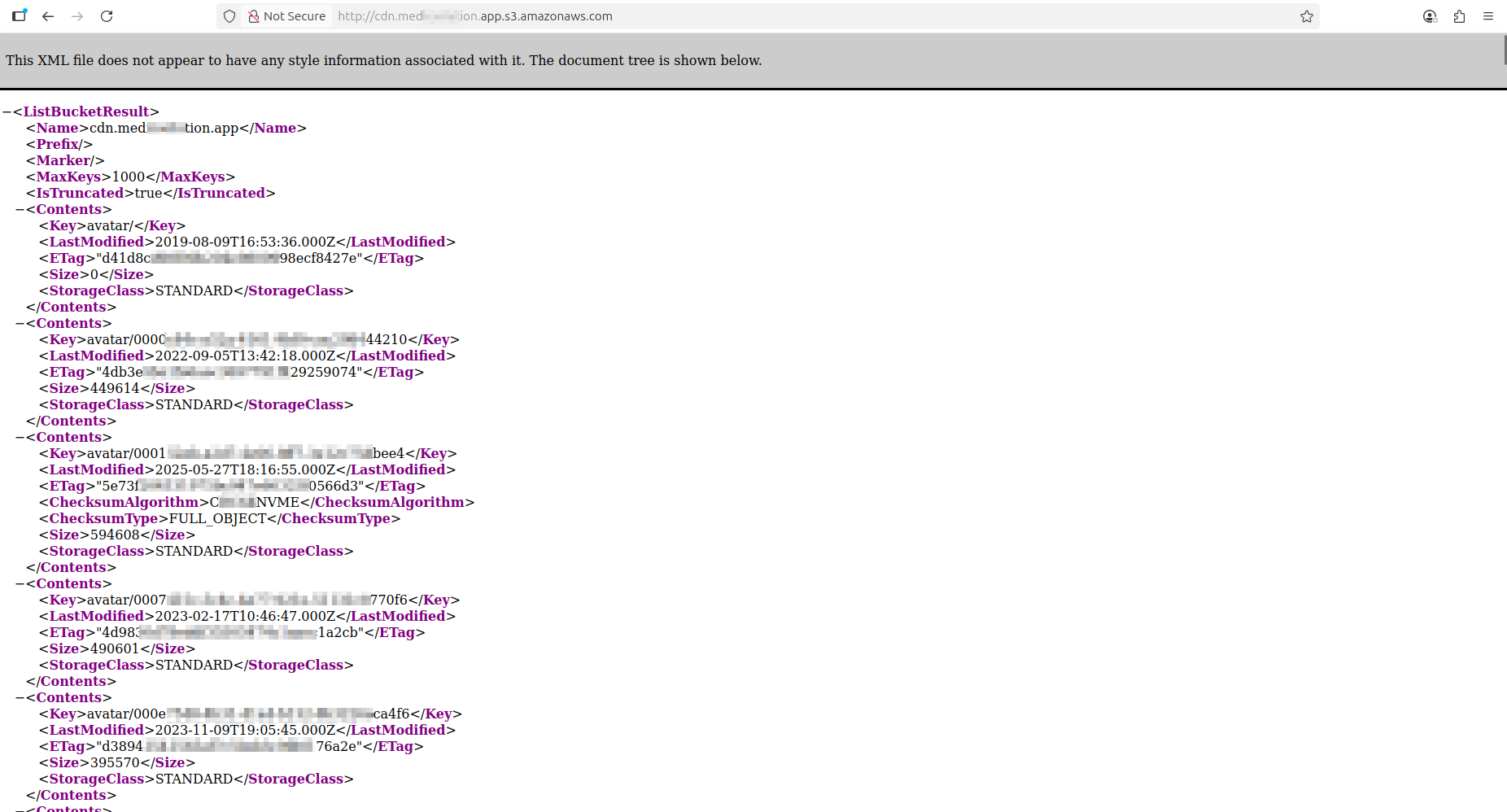
KillSec Ransomware exploited 'low-hanging fruit' to steal data without actual hacking or penetration into the IT environment. Based on their recent victim history, this vector appears to be frequently leveraged by them.
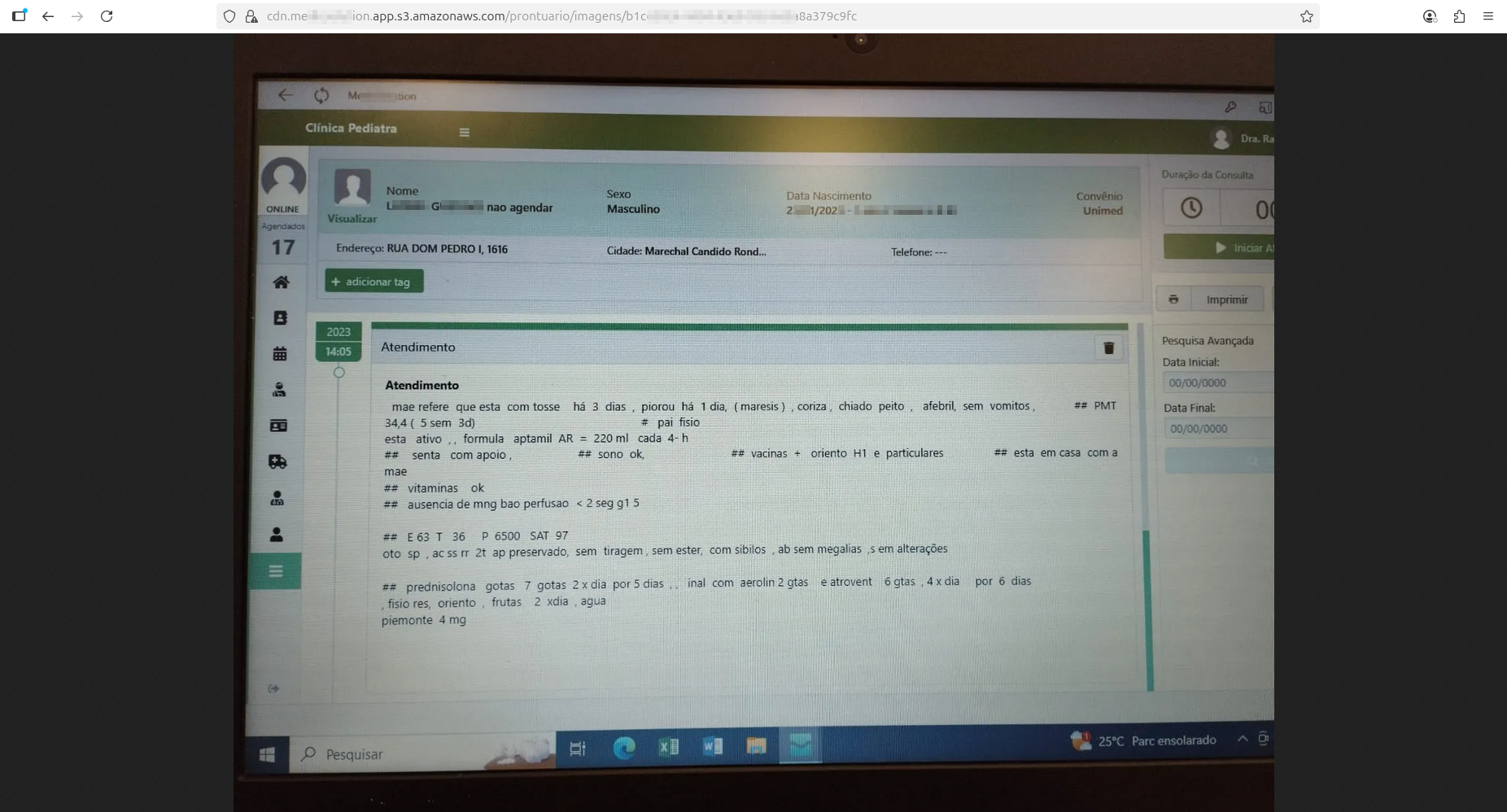
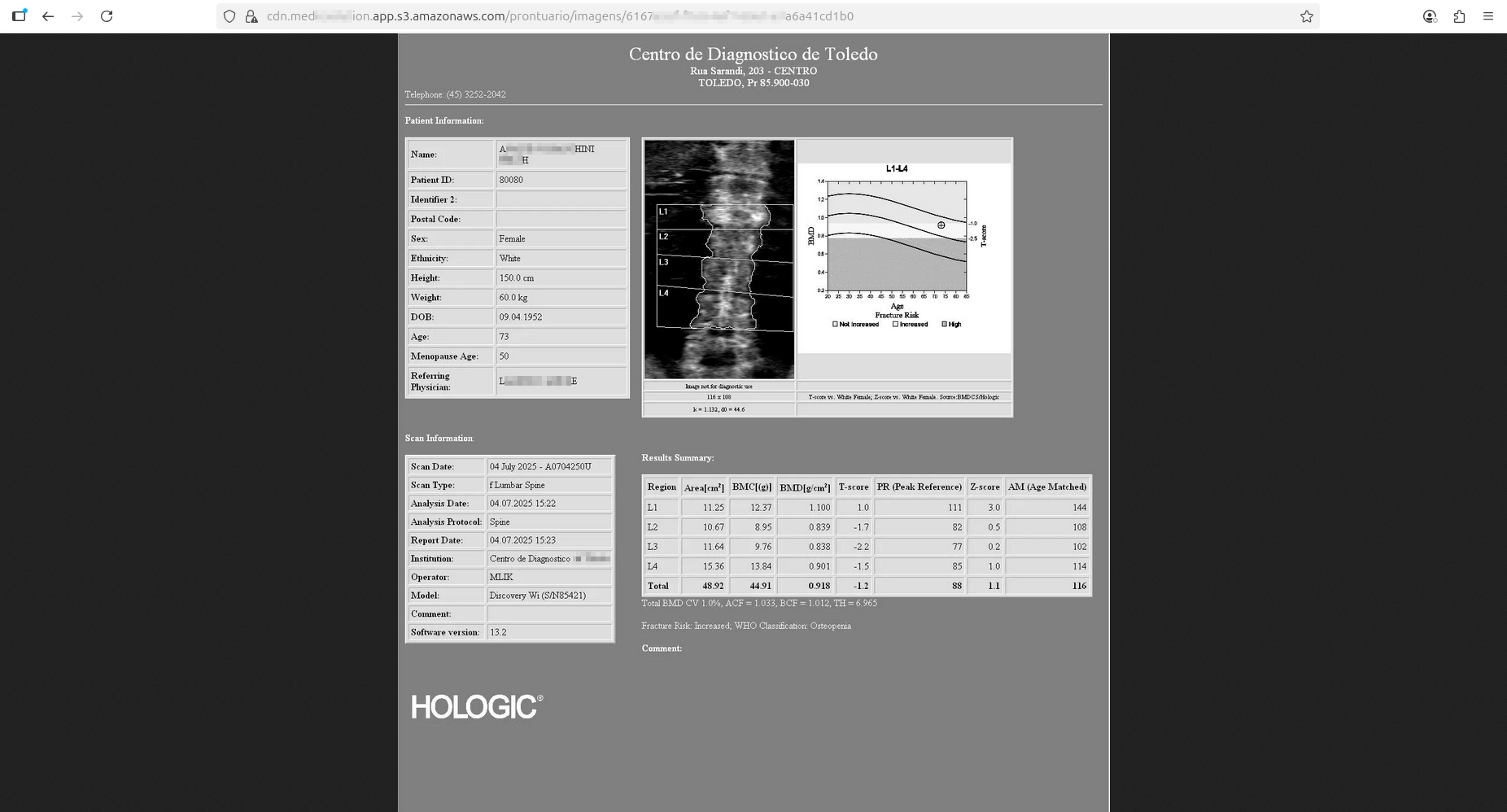

Significance
Resecurity is aware of one more victim from the healthcare sector in Brazil, which has not been disclosed today by KillSec Ransomware yet. The group may be developing a compromise and delaying publication to ensure the current victims can be properly monetized. Notably, at the beginning of September 2025, the actors released a record-breaking lineup of hacks into healthcare organizations in the US and Latin America - by intensity and the number of affected victims, compared to their previous activities.
Unless the root cause of the incident becomes clear, the unfortunate side is that the ransomware group has already exfiltrated data and will likely use it in a hack-and-leak operation to extort patience and related organizations. This issue highlights the importance of cybersecurity audits aimed at uncovering possible vulnerabilities that could lead to data leakage and prevent potential damage at an early stage.
Based on Resecurity's analysis, KillSec Ransomware has found a sweet spot targeting healthcare organizations. Healthcare organizations store vast amounts of sensitive and valuable data, including personal identification, medical histories, insurance details, and payment information. Hackers target these organizations because stolen medical records can be sold on the black market for significant sums. This makes healthcare data breaches highly lucrative for cybercriminals.
Compliance and Preventative Measures
Healthcare organizations are required to:
- Implement robust data protection policies and technical safeguards.
- Obtain explicit consent for processing sensitive health data.
- Limit access to authorized personnel.
- Report breaches to the ANPD and affected individuals within three business days.
- Regularly train staff and conduct security audits
Resecurity also recommends implementing ongoing Cyber Threat Intelligence gathering and Digital Risk Monitoring, especially aimed at detecting possible threats originating from third parties and the supply chain.
The rapid digital transformation in healthcare - such as the adoption of electronic medical records, connected medical devices, and cloud services - has expanded the attack surface. Many healthcare systems have legacy infrastructure and may lack robust cybersecurity defenses, making them easier targets for hackers.
Attack surface management (ASM) enables organizations to identify and mitigate vulnerabilities before attackers can exploit them. By continuously monitoring all digital assets - such as servers, applications, and cloud services - security teams can spot weaknesses early and address them, reducing the risk of cyberattacks.
Resecurity is aware of the significant cyber threats facing companies in the healthcare industry worldwide. All companies in this sector face more significant threats than nearly any other industry. This risk is compounded by the fact that many healthcare organizations are under financial distress. Although Resecurity’s Risk platform is a cost-effective solution for companies and governments globally, some organizations lack the budget to enhance their security posture. Therefore, in Brazil, Resecurity is offering grants to healthcare companies that cannot typically afford robust CTI services like Risk. In some cases, these grants can cover 100% of the cost, enabling healthcare providers to better protect their company, staff, and patients from being victimized by breaches like the one described in this blog.
Litigation Practice
The litigation and enforcement landscape for data breaches in Brazil’s healthcare sector is shaped primarily by the Lei Geral de Proteção de Dados (LGPD), Brazil’s General Data Protection Law, which came into full effect in 2020. The LGPD applies to all organizations processing personal data in Brazil, with health data classified as “sensitive personal data” and subject to heightened protection and stricter processing requirements.
The main regulatory authority for data protection enforcement is the Autoridade Nacional de Proteção de Dados (ANPD), which oversees LGPD compliance, investigates breaches, and imposes sanctions. Sector-specific regulators, such as the Agência Nacional de Vigilância Sanitária (ANVISA) and the Conselho Federal de Medicina (CFM), also play roles in enforcing data security and confidentiality in healthcare in Brazil.
Brazilian courts have generally sided with claimants in healthcare data breach cases, especially when fundamental rights to privacy are at stake. Courts often recognize the violation of privacy and emotional distress, awarding moral damages. Courts frequently apply a strict liability standard to healthcare providers and insurers, holding them responsible for breaches regardless of intent, due to the sensitivity of health data.
Notable Litigation Outcomes:
Hospital Ransomware Case (2021): A major São Paulo hospital was found liable for failing to implement adequate security measures after a ransomware attack. The court ordered compensation ranging from R$5,000 to R$20,000 per claimant, depending on the extent of exposure and emotional distress.
Health Insurance Data Leak (2022): A large insurer was ordered to pay collective moral damages and implement a comprehensive data protection compliance program, monitored by the ANPD.
Public Health System (SUS) Data Exposure (2023): A breach affecting millions led to a court order for the Ministry of Health to enhance security protocols and pay collective damages to be distributed through public health initiatives.
Documented Fines in the Healthcare Sector:
The ANPD fined 15 healthcare institutions a total of BRL 12 million (~$2.4 million USD) for lacking encryption and breach response plans as a result of the 2024 Healthcare Sector Audit. Additional corrective measures included mandatory penetration testing and staff training. Since 2023, the ANPD has imposed over BRL 98 million (~$20 million USD) in fines across all sectors, with healthcare representing a significant portion due to repeated vulnerabilities and sector-wide audits.
The ANPD’s enforcement is robust and proactive, with a clear focus on healthcare due to the high risk and sensitivity of medical data. The risk of financial penalties, operational sanctions, and reputational harm is substantial for non-compliant organizations. In conclusion, litigation and regulatory enforcement for healthcare data breaches in Brazil are active and evolving, with courts and the ANPD imposing both financial and operational penalties to ensure compliance and protect patient privacy.

