'Blue Locker' Analysis: Ransomware Targeting Oil & Gas Sector in Pakistan
Cyber Threat Intelligence


Introduction
This week Pakistan’s National Cyber Emergency Response Team (NCERT) has issued an advisory to 39 key ministries and institutions and warned them of a “severe risk” posed by the ongoing ‘Blue Locker’ malware attacks, an NCERT spokesperson said on Sunday, confirming that a few Pakistani organizations had been affected by the ransomware. In a rare alert, the recipients include the Cabinet Division, ministries of Interior, Foreign Affairs, Finance, Communications, Privatisation, Religious Affairs, IT and Telecom, Law and Justice, Railways, Commerce, Environment, Industries and Production, and Science and Technology. Other recipients include NECTA, FIA, National Security Division, Establishment Division, Election Commission, National Assembly, National IT Board, PEMRA, NDMA, OGRA, and FBR.
NCERT, which handles cybersecurity threats, alerts and coordination for government ministries and institutions, advisory came after the ransomware targeted some organizations in the South Asian country, according NCERT spokesman Imran Haider. “Pakistan Petroleum has been impacted severely and some other organizations were also attacked, but our deployed system is detecting and blocking it continuously,” he told Arab News.
Notably, the malicious cyber activity took place in close proximity to the celebration of Pakistan's Independence Day, one of the key national holidays, which is celebrated annually on August 14. This ransomware attack could be considered significant, as it targeted major enterprise in the country's oil and gas sector (Pakistan Petroleum Limited), which is critically important to the economy. The motive behind these events may vary, but it is unlikely that a traditional cybercriminal organization is responsible; instead, it is more probable that a nation-state group is attacking critical infrastructure. Very often, advanced actors operate under the guise of cybercrime to blur attribution and avoid geopolitical context. The actors have been actively targeting organizations across multiple sectors, including Technology, Government Services and Oil and Gas specifically. The attacks have affected confirmed victims across Pakistan and various parts of Asia.
Resecurity has acquired binary samples of the "Blue Locker" ransomware and provided a detailed reverse engineering analysis in this report to raise awareness within the cybersecurity community and to equip network defenders with additional insights about this activity due to limited information about it for today.
Overview of Blue Locker Ransomware
"Blue Locker" ransomware is a type of malicious software designed to encrypt files on infected systems and demand ransom payments in exchange for the decryption key. Like many ransomware strains, "Blue Locker" is distributed via a PowerShell-based loader that attempts to disable security defenses, escalate privileges, and load its ransomware payload.
This ransomware family typically appends a ".blue" or ".bulock16" (or similar) extension to encrypted files and leaves a ransom note titled HOW_TO_BACK_FILES.html, threatening to leak or sell exfiltrated data if the ransom is not paid.
As the delivery channel, "Blue Locker" is leveraging phishing emails, malicious attachments, drive-by downloads, insecure remote access, and can propagate across local networks and removable storage devices. Detection is possible with antivirus solutions, but decryption without the attackers’ key is generally not feasible, making regular backups and robust cybersecurity hygiene essential for prevention and recovery.
CERT Notification and Response
- The National Computer Emergency Response Team (CERT) of Pakistan has recently issued warnings to 39 ministries regarding the threat posed by "Blue Locker" ransomware. This alert underscores the seriousness of the threat, highlighting the potential for significant data loss and operational disruption within governmental organizations.
- The advisory places organizations in Pakistan on high alert, indicating that "Blue Locker" is actively targeting critical infrastructure and government bodies in the country. This reflects a broader trend of increasing ransomware attacks globally, with Pakistan now being a specific target for such campaigns.
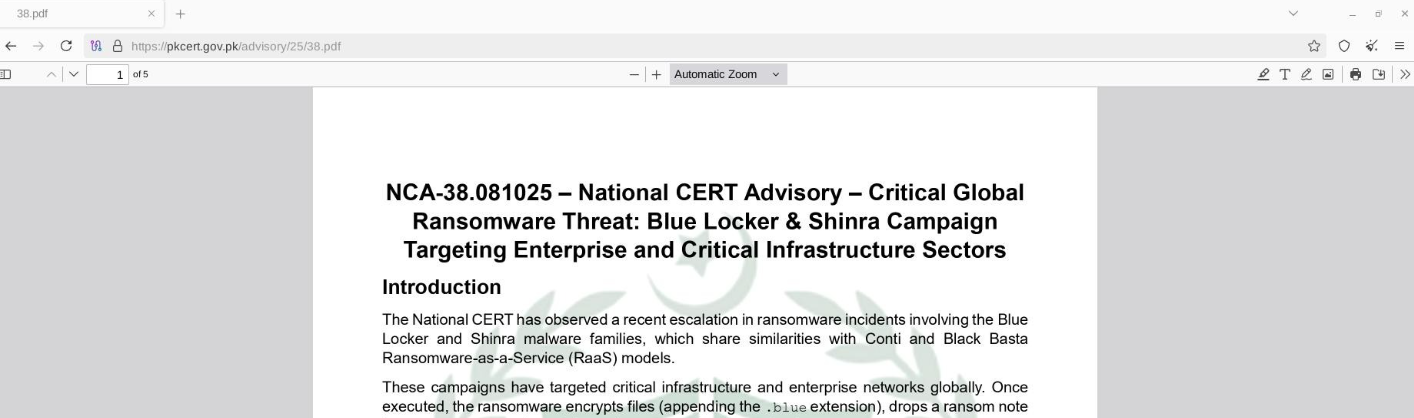
The notification also included a list of IOCs and network infrastructure details. As of the date of reporting, the indicated domain names are no longer available and have likely been blocked. It is possible that these domains were used for a short period during the ongoing campaign.
The reference to Shinra (in fact, another ransomware strain, discovered variant from the Proton malware family) is of interest, which was first detected in the wild around April 2024. According to an analysis by Fortinet, the Shinra ransomware contained several strings, such as "ZhuDongFangYu," which may indicate a possible relation to China or, at least, Asia as a potential region of origin.
The inclusion of such strings could also be used as a "false flag" tactic - widely employed by actors to confuse attribution. Interestingly, in May 2024, the Israeli National Cyber Directorate (INCD) received a report of a ransomware attack against an Israeli victim, with the ransomware identifying itself as "Shinra." Through independent research and OSINT verification, the INCD assessed that that ransomware was part of the Proton ransomware family, which has been known to operate since early 2023 with probable Iranian origins. The advisory also noted several other variants, including Limba, targeting Chinese victims, and Zola, as well as other names such as Cipher and Trust.
Resecurity confirms the connection between Limba, Zola and Shinra (as one of the latest variants of the Proton ransomware family known prior to incident in Pakistan), and it is likely that this connection can be explained by shared authorship or a possible delegation of source codes between the actors. It is common for cybercriminal actors to hire various ransomware developers, who later transfer or monetize source codes of specific products on the Dark Web, often making slight adjustments - such as modifying the ransomware note template or adding new functions - without changing the original code base.
"Blue Locker" appears to inherit the best features of Proton-like ransomware instances and could be interpreted as one of the most recent modifications in this regard observed in the confirmed cybersecurity incident. It would be incorrect to attribute responsibility for the past attack solely based on its historical context - actors from any other geography could easily reuse and reproduce its samples. Resecurity also received credible insights regarding the sale of Proton ransomware source codes on the Dark Web. Considering that both Iran and China maintain stable diplomatic relationships with Pakistan, it is unlikely that the threat could be influenced from there. On the contrary, it is more likely that a foreign third party is involved in this activity.
Mitigation Strategies and Recommendations
To counter the threat, National CERT has recommended that organizations immediately strengthen their cybersecurity posture. Measures include adopting multi-factor authentication, enhancing email filtering to detect suspicious links and attachments, and isolating backups from shared networks. In the event of an attack, it advises disconnecting shared drives and offline storage to prevent further spread. Institutions are urged to preserve forensic evidence to aid investigations and support possible legal action against attackers.
The advisory also calls for increased employee awareness and training, emphasizing the importance of recognizing and avoiding suspicious emails, attachments, and download links. Keeping all systems updated with the latest security patches and maintaining robust institutional vigilance are considered essential steps to reduce vulnerability. Organizations are warned not to download files from unverified sources or open questionable attachments, as these remain the most common entry points for ransomware infections. Ransomware mitigation strategies include:
- Patch Management: Ensure all operating systems and software are up to date with the latest security patches to close vulnerabilities that ransomware might exploit.
- Multi-Factor Authentication (MFA): Enforce MFA to add an extra layer of security for accessing sensitive systems and data.
- Data Backups: Regularly back up critical data and ensure backups are stored offline or otherwise not accessible from the main network, to prevent them from being encrypted during an attack.
- Employee Training: Educate staff about phishing and social engineering tactics, as these are common vectors for ransomware delivery.
- Network Segmentation and Access Controls: Limit user privileges and segment networks to contain the spread of ransomware if an infection occurs.
- Incident Response Planning: Develop and regularly update incident response plans to ensure rapid and coordinated action in the event of a ransomware attack.
PsyOp Context
Around the time the official NCERT notification was released, several actors were identified attempting to socialize a possible breach originating from Pakistan Petroleum via the Dark Web. Based on our assessment, these claims were likely false or used to amplify the narrative surrounding the consequences of a cyberattack involving the "Blue Locker" ransomware. Such tactics could be interpreted as part of a psyop (psychological operation) aimed at generating fear, panic, and increased attention.
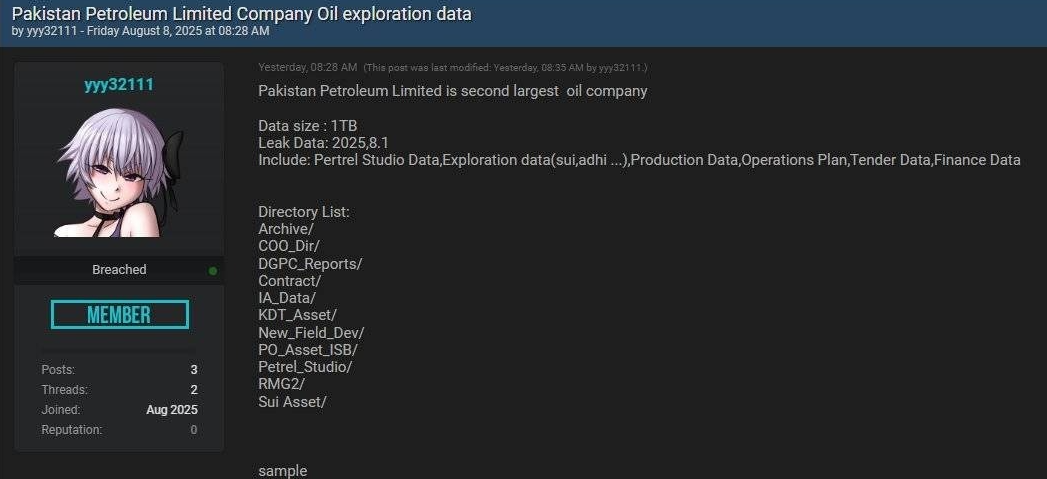
At this stage, there is no confirmation that the data has ever been leaked, but the compromise of an endpoint within Pakistan Petroleum Limited (PPL), where a ransom note was found, was acknowledged by the company spokesperson.
A PPL spokesperson said the attack occurred on August 6, prompting the immediate activation of the company’s internal cybersecurity protocols. PPL has also initiated a comprehensive forensic analysis to assess the scope of the incident and to further strengthen its cyber defence capabilities. “We are committed to complete transparency and to restoring full system functionality in a safe and phased manner,” the spokesperson said.
According to Pakistan Today, an alarming email was sent to PPL employees to extort the company: “Your computers and servers are encrypted, backups are deleted from your network and copied. We have stolen some of your business data and employee information, including but not limited to TMC Data (Sui, Adhi, etc.) and contracts… If you don’t contact us with a quote, we will report the hack to mainstream media and release your data to social media and competitors.”
Reverse Engineering
This ransomware follows the general structure of most modern ransomware but comes with unique characteristics and behaviors. Below is a step-by-step breakdown of how "Blue Locker" operates:
- Initial Infection and Delivery
"Blue Locker" ransomware is commonly spread through targeted emails. The email might appear legitimate, pretending to be a legitimate business or service, and includes an attachment or a malicious link.
Once the victim opens the attachment or clicks the malicious link, the malware uses social engineering techniques to convince the target to trigger the malware’s execution.
- Execution and Payload Deployment
Once executed, victims discover a ransom note (restore_file.txt) in multiple directories, along with encrypted files that have been appended with the '.Blue' extension.
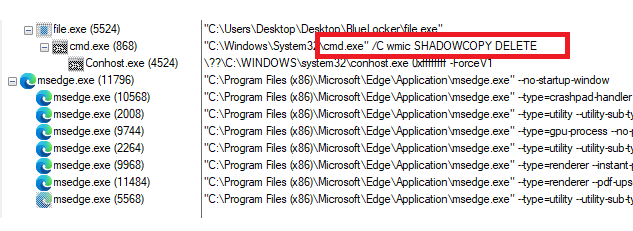
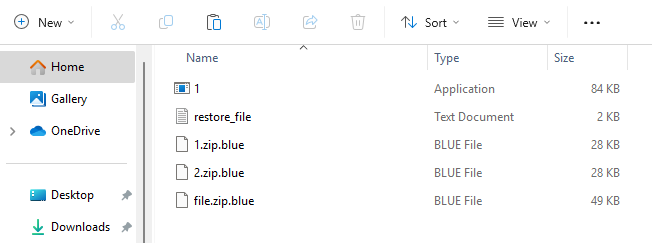
The ransomware inserts itself into KEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Run.
This registry key allows the ransomware to achieve persistence, silently execute, and maintain control over compromised systems.
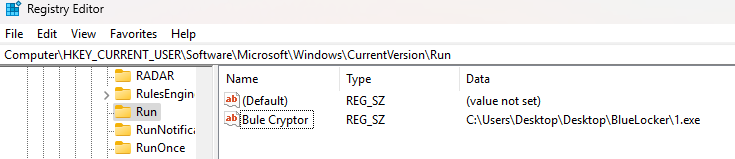
It also uses ShellExecuteW to run wmic SHADOWCOPY DELETE to remove backup snapshots that could help restore files.
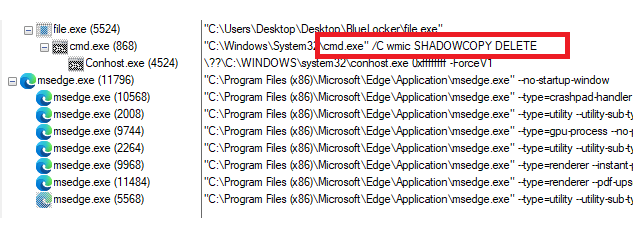
The "Blue Locker" includes a list of folder names that are deliberately skipped during the encryption process. By excluding these directories, the malware avoids encrypting files that are critical to the operating system. This could potentially prevent immediate system instability, thereby making it easier for the malware to maintain persistence and evade detection.
The following folder names are excluded from encryption:
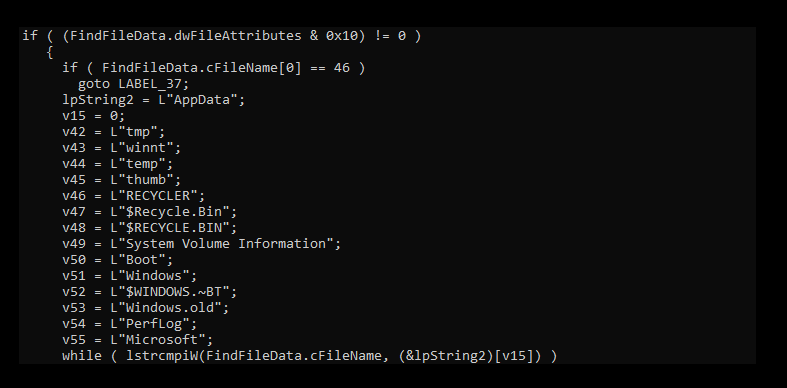
During our analysis, we observed that "Blue Locker" searches for a unique obfuscated string: “锗빔爡⳹凑销빉爣ⲻ凛锊빉牑”. This string, rendered in what appears to be Chinese characters, is in fact an XOR-encoded variant of “Chrome.exe”.Upon locating this target process, "Blue Locker" forcibly terminates it to bypass file locks and gain access to Chrome’s local password database. The malware then proceeds to encrypt the password files, ensuring they are rendered inaccessible to the victim.
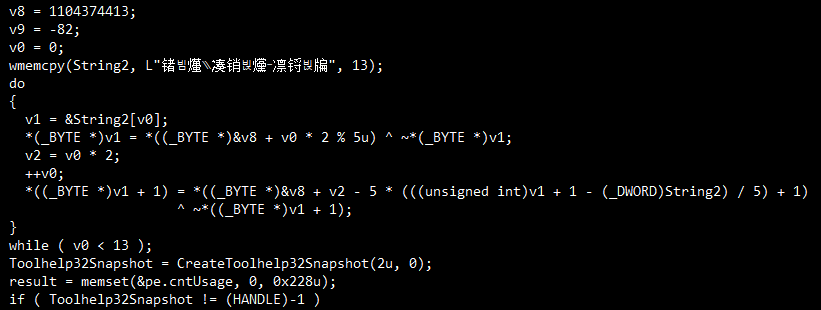
- Encryption Process
"Blue Locker" ransomware uses a combination of AES and RSA encryption algorithms to lock files. It targets common file types while deliberately avoiding system-critical or executable files.
The ransomware filters out extensions such as .cat, .bat, .cmd, .ps1, and .vbs, among others, to prevent interference with system operations or detection.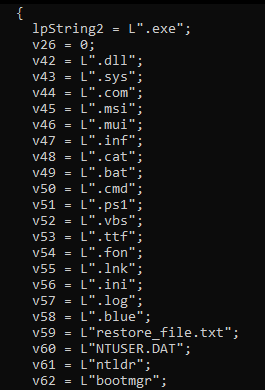
After generating the unique key, the malware searches for a new file path and a corresponding public RSA key. It then encrypts the file’s contents and appends .Blue to the filename.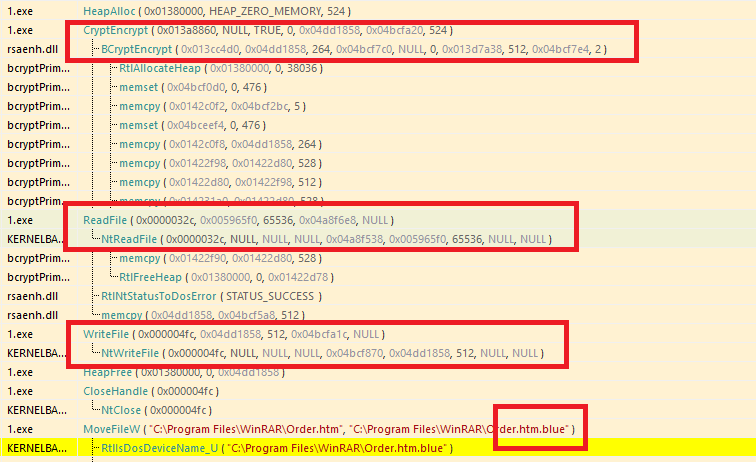
- Ransom Note Creation
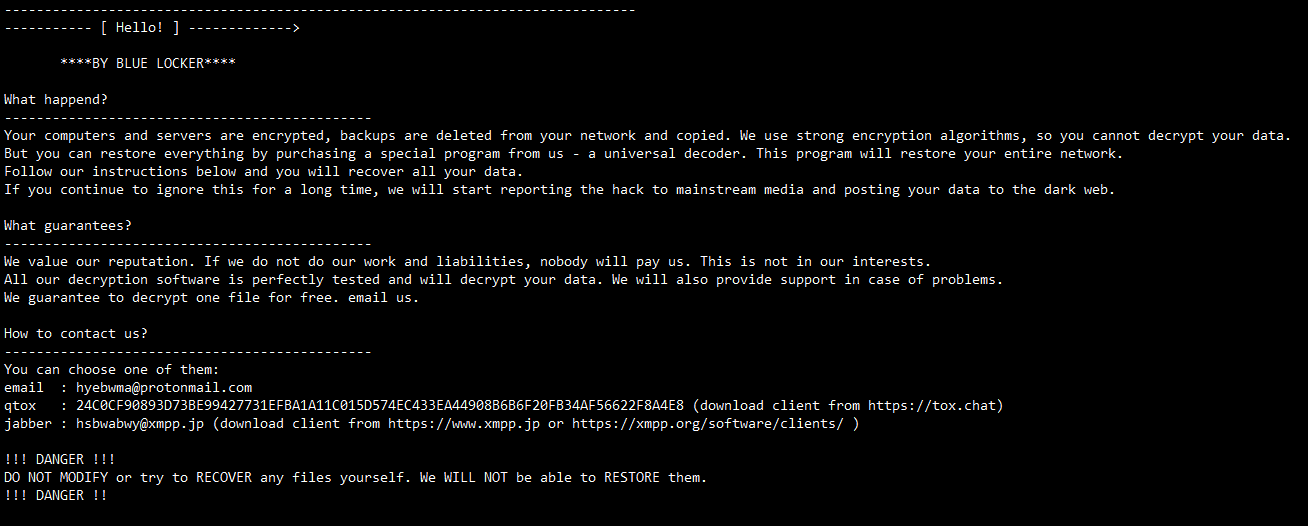
Once the encryption is complete, "Blue Locker" drops a ransom note, usually named restore_file.txt, on the victim’s desktop and in the directories where files were encrypted.
The ransom note instructs the victim to submit payment via email or IM Messengers. The note includes the following:
- Indicator of Compromise (IOC)
Besides the IOCs shared by NCERT, Resecurity acquired additional artifacts, which may be useful in "Blue Locker" ransomware detection.
d3cc6cc4538d57f2d1f8a9d46a3e8be73ed849f7fe37d1d969c0377cf1d0fadc
e6bd4ed287d1336206f5b4b65011e570267418799eb60c2d0d7496d5d9e95a33
6eeb20cc709a18bf8845f7b678967b7f0ff96475cf51a261da87244886bbfd2e
515bd71a8b3c2bce7b40b89ddfe2e94d332b0779d569c58117f8dcdcb8a91ed9
Resecurity was able to recover the contact information mentioned in the ransom note left by attackers. Notably, it included a Protonmail (hyebwma@protonmail.com), Jabber IM (hsbwabwy@xmpp.jp) and TOX IM account for anonymous secure communications with the victim.
MITRE ATT&CK techniques
| Tactic | ID | Description |
|---|---|---|
| Persistence & Privilege Escalation | T1547.001 | Achieves persistence through Registry Run Keys, ensuring execution after system reboot. |
| Persistence & Privilege Escalation | T1543 | Modifies system services for persistence and privilege escalation. |
| Persistence & Privilege Escalation | T1548.002 | Bypasses UAC via registry manipulation, elevating privileges without user consent. |
| Defense Evasion | T1140 | Implements obfuscation and deobfuscation to evade detection by security tools and analysts. |
| Defense Evasion | T1070.006 | Timestomping technique is used to alter file timestamps, making it difficult to detect during forensic analysis. |
| Defense Evasion | T1562.001 | Disables UAC to avoid detection and remain persistent without being interrupted by security controls. |
| Discovery | T1012 | Performs registry queries to gather system configuration and installed software information. |
| Discovery | T1057 | Enumerates running processes to identify which processes to target for exploitation or injection. |
| Process Injection | T1087 | Discovers user accounts for credential harvesting or lateral movement across systems. |
| Discovery | T1497 | Detects virtualized or sandboxed environments to avoid detection during dynamic analysis. |
| Discovery | T1083 | Explores file and directory structures to find valuable files for encryption or exfiltration. |
| Collection | T1074 | Prepares collected data in temporary or known directories before exfiltration or further exploitation. |
| Collection | T1056 | Uses raw input capture to steal user credentials or session data during active sessions. |
| Impact | T1490 | Inhibits system recovery by disabling or deleting backup systems, ensuring that victims cannot restore their encrypted files. |
| Impact | T1489 | Stops system services to ensure the encryption process is not interrupted and maximizes the damage. |
Conclusion
"Blue Locker" ransomware is a sophisticated and highly dangerous threat. It demonstrates typical ransomware behavior, such as file encryption and ransom demands. However, it also exhibits advanced evasion techniques like obfuscation, anti-analysis, and potential data exfiltration, which makes it a significant threat to both individual users and enterprises.
Organizations are strongly advised to implement a multi-layered defense strategy involving:
- Regular updates and patch management.
- Network monitoring for unusual activity.
- Comprehensive backup and recovery plans.
Given the evolving nature of ransomware, continuous monitoring and adaptation of defense strategies are critical in combating ransomware like "Blue Locker".
Cyber Threat Intelligence (CTI) is also a critical enabler for both the detection and prevention of ransomware attacks. By providing actionable intelligence on adversaries, attack methods, and vulnerabilities, CTI empowers organizations to:
- Anticipate and detect ransomware threats early
- Respond rapidly to incidents
- Prevent the spread and impact of ransomware
- Continuously improve their security posture
The integration of CTI into cybersecurity strategies is a proven method for reducing the risk and impact of ransomware attacks across all sectors.
In summary, "Blue Locker" ransomware represents a significant and immediate threat to organizations in Pakistan, particularly government ministries, as highlighted by the recent CERT notification. The ransomware’s advanced capabilities and double extortion tactics make it a formidable adversary.
Pakistani authorities have responded by issuing high-alert advisories and recommending a suite of preventive and mitigation measures to safeguard critical data and infrastructure. Organizations are urged to remain vigilant, implement robust cybersecurity practices, and stay informed through official CERT communications.
Ransomware attacks have surged globally, with a 350% increase since 2018, and Pakistan is not immune to this trend. The targeting of oil and gas organizations by "Blue Locker" ransomware is consistent with the global pattern of threat actors focusing on critical infrastructure and public sector organizations.
Cybersecurity experts say the threat highlights deeper vulnerabilities in Pakistan’s government IT infrastructure. Tariq Malik, former Chief Technology Officer for Pakistan’s army, noted that most ministries and departments are ill-equipped to handle sophisticated cyberattacks. “There is a lack of structured policies and cybersecurity frameworks,” shared the expert. Ammar Jaffri, President of the Pakistan Information Security Association (PISA), emphasized the need for a shift from a reactive to a proactive cybersecurity posture. “Cybersecurity is no longer a one-time effort. Threats evolve daily, and so must our defenses,” he said.

