StupidFISH from China is Attacking the Digital Identities of Consumers
Cyber Threat Intelligence


Introduction
Resecurity has identified a new phishing kit marketed on the Dark Web by Chinese cybercriminals. The kit, named stupidFISH, targets consumers from Australia, France, Greece, Italy, Malaysia, the US, the UK, and other countries. Initial intelligence about the kit has been received from one of the financial institutions (FIs) in the Middle East that has been affected by its activity. This was after an executive received a targeted malicious message, and the DFIR team was able to triage and attribute it following analysis by our HUNTER team.
The kit is used to orchestrate both phishing and smishing campaigns, supporting customized templates for mobile devices, including smartphones and tablets. StupidFISH is also used to facilitate advanced social engineering for wire fraud, luring the victim into providing access credentials and OTP codes to bypass two-factor authentication (2FA).
Several Telegram groups have been identified where the kit is being offered for sale. Notably, some of these groups have over 3,703 members, which may indicate that the kit is popular within the Chinese cybercriminal underground. Additionally, the information about the kit is provided only in Chinese and is likely intended for Chinese-speaking cybercriminals. There are at least three active groups related to the kit, and many more have been banned or suspended by Telegram due to violations of its Terms of Service (ToS).
However, the actors continue to form new groups to maintain communication and expand their audience. Primarily, their clientele includes Chinese-speaking actors involved in business email compromise (BEC), financial fraud, carding, spam, ad fraud, and account takeover (ATO).
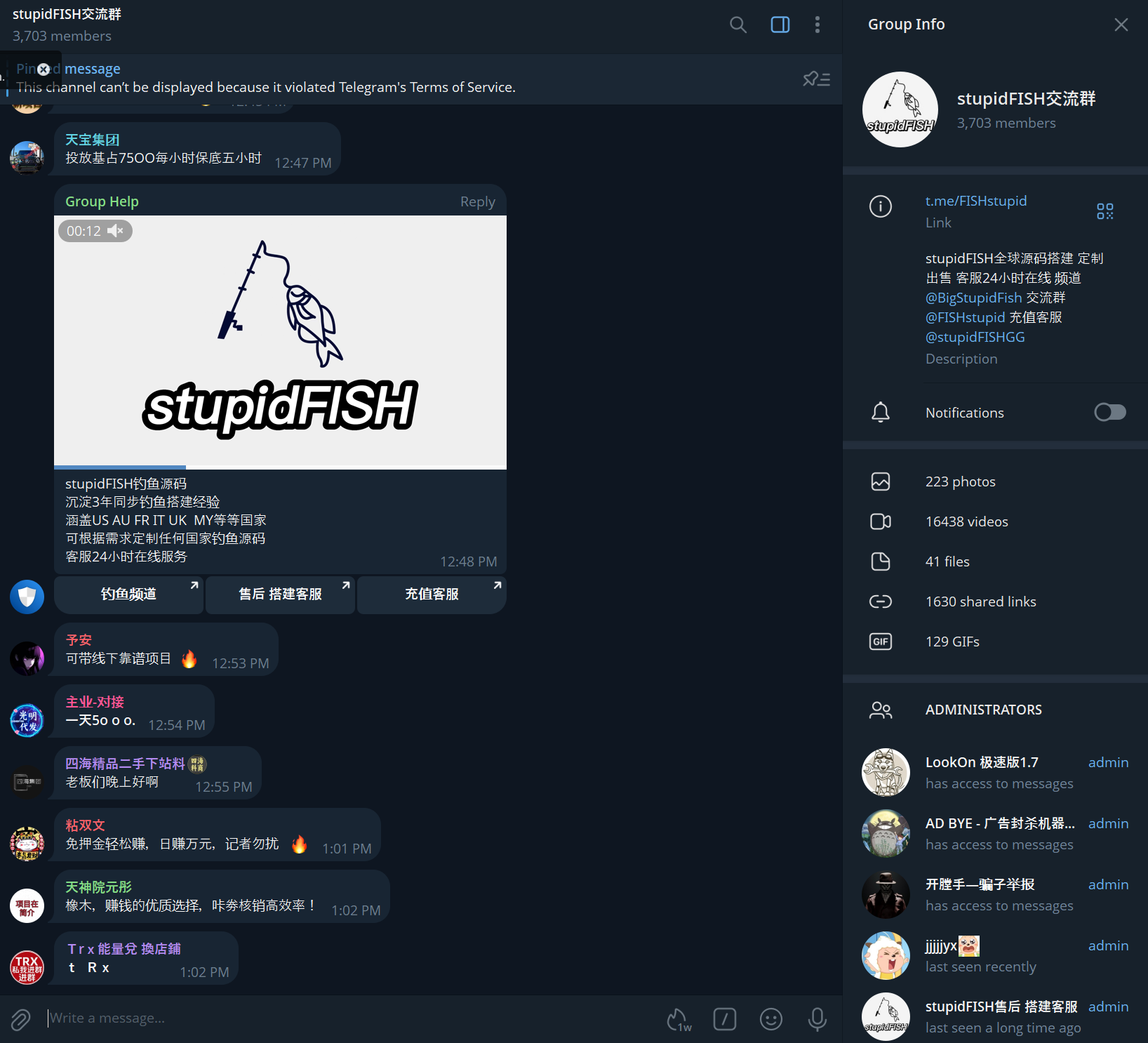
Tive administrators of the Telegram channels associated with stupidFISH were identified. Based on Resecurity's assessment, the kit was developed by a group from China comprising multiple members with varying roles and responsibilities. The group includes many more members, with administrators acting as a "front" to manage payments and service new customers.

Typically, such groups also have developers, phishing template designers, system administrators, and engineers responsible for their network infrastructure and domain name rotation. Some of them also have close relations to the sale of compromised credit cards (CCs) and manage several automated bots to monetize stolen payment data.

One of the key actors responsible for the sales of stupidFISH operates under the alias Ganxingovo. Notably, the actor is not responsive to English-speaking customers and responds only to those who speak Chinese. Resecurity suggests that these actors primarily prefer to deal with Chinese cybercriminals and maintain limited communication with foreigners to improve their OPSEC.

The contact of Ganxingovo was received from jjjjjyx, one of the administrators of the stupidFISH channel on Telegram, whom the first referred to as "the boss."
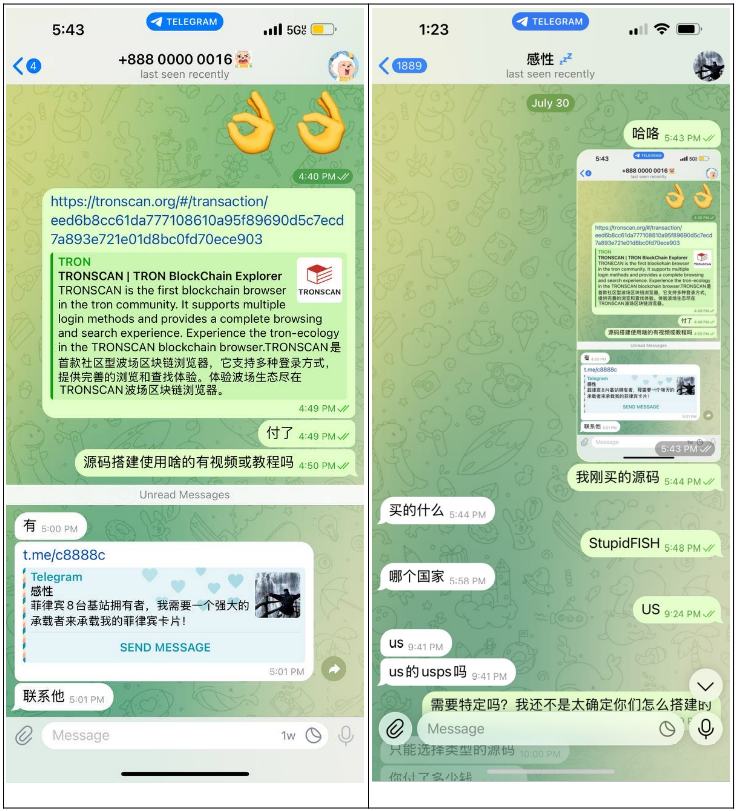
The hierarchy in the Chinese cybercriminal ecosystem is crucial, with the leader of the group assigning tasks to other members and profiting from their activities.
The Smishing Triad's Successor
The modus operandi (MO) of the group behind stupidFISH exhibits great synergy with another group called Smishing Triad, leveraging Lighthousekit, which Resecurity identified in August 2023. In fact, one of the key differentiators of stupidFISH is that it focuses not only on payment data interception but specifically on personal data and digital identity.
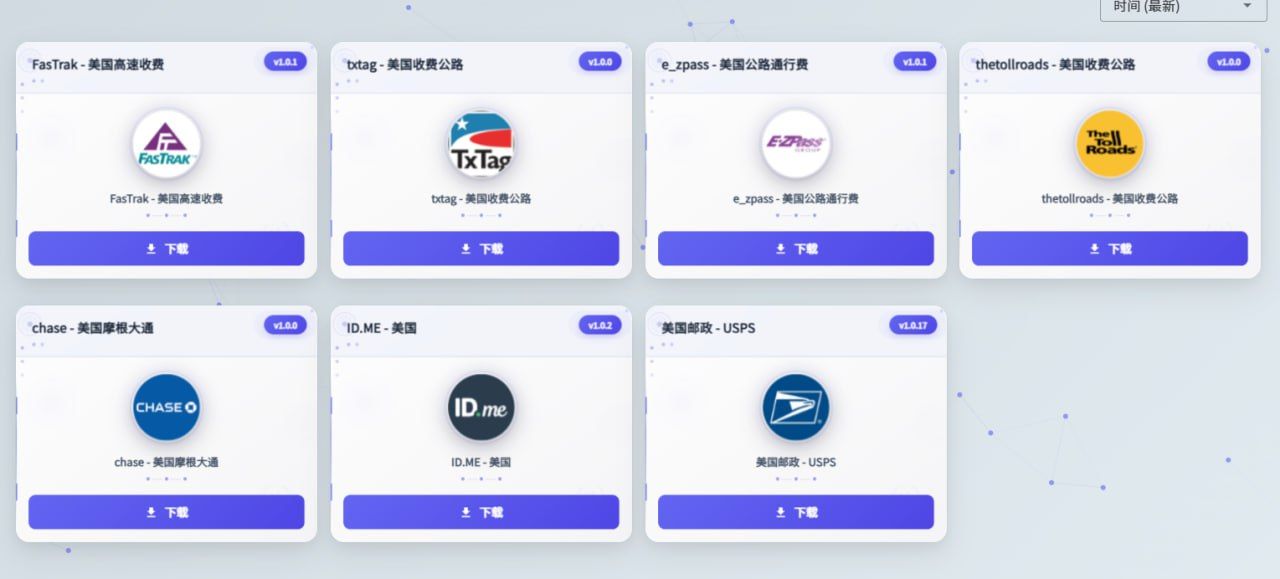
The kit offers a collection of well-designed templates aimed at mimicking popular applications, including toll payment and postal delivery services that Smishing Triad previously targeted on a global scale.
Some of the supported templates are more relevant to traditional smishing tactics. In contrast, others are designed for specific financial institutions, such as JPMorgan Chase, and for identity verification providers like ID.me, which is widely used in the United States as one of the primary authentication providers.
The most popular templates supported by stupidFISH include:
- FasTrak
- TxTag
- EzPass
- TheTollRoads
- Chase
- ID.me
- USPS
The actors also offer a service to develop customized templates tailored to the specific requirements of the customer for an additional fee. Such templates may be handy for language localization or interface modifications.
Initially, Resecurity identified the actors offering USPS smishing templates that have significant similarities to those provided by Smishing Triad in July 2025. It is possible that, after the group's public disclosure, its members could transition, sell the code base, or continue operations under a new umbrella. Our HUNTER team has successfully acquired several licenses of stupidFISH, along with templates designed to defraud various organizations.
Cost-Effective Model
The actors accept cryptocurrency payments in USDT (Tether cryptocurrency) for stupidFISH licenses. The kit is sold without installation or a virtual host, but such options can be purchased for an additional fee. The price depends on the operator's ability to change the domain name where the kit will be deployed. The pricing plans are:
- $58 (USDT)
Per week, with binding to a specific domain name, where the kit will be deployed.
- $88 (USDT)
Per week, with the opportunity to deploy the kit on any domain and change it later.
- $98 (USDT)
Per month, with binding to a specific domain name, where the kit will be deployed.
- $138 (USDT)
Per month, with the opportunity to deploy the kit on any domain, and change it later.
- $366 (USDT
Lifetime, with binding to a specific domain name, where the kit will be deployed.
- $416 (USDT)
Lifetime, with the opportunity to deploy the kit on any domain and change it later.

Information about the acquisition of the kit is delivered via stupidFISH's Telegram channel and can be confirmed through operators. Discounts are available for license purchases covering many domains. Overall, this pricing makes the kit highly affordable for large-scale deployment by advanced cybercriminals.
Quick Deployment Process
The kit includes SynFishServer, which enables the operator to set up stupidFISH on a dedicated (self-hosted) server. In this case, all collected data from victims will be saved in a local "logs" folder. The actors also offer managed hosting services to deploy the kit if the operator does not have their own server, although cybercriminals prefer this option less due to the risk of theft.
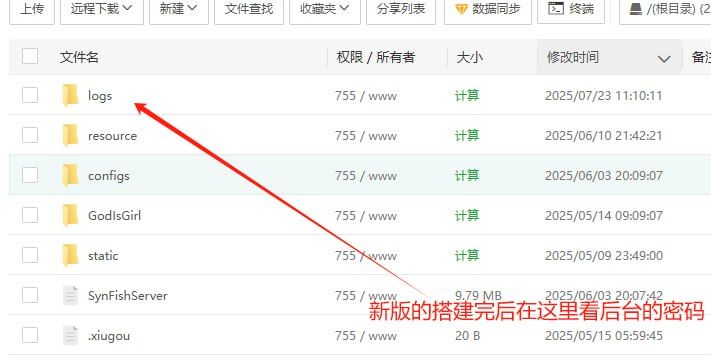
The operator needs to configure the settings for the MySQL/Redis database and the local SynFishServer.
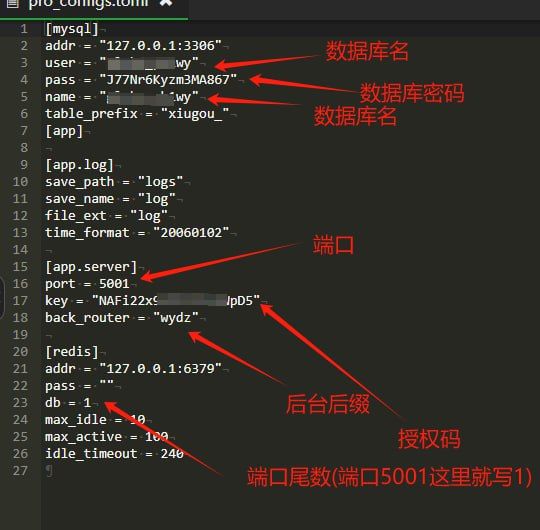
The actors recommend using BT5.ME (https://bt5.me) to deploy the kit, a cracked version of BaoTa Panel that bypasses licensing and server verification.
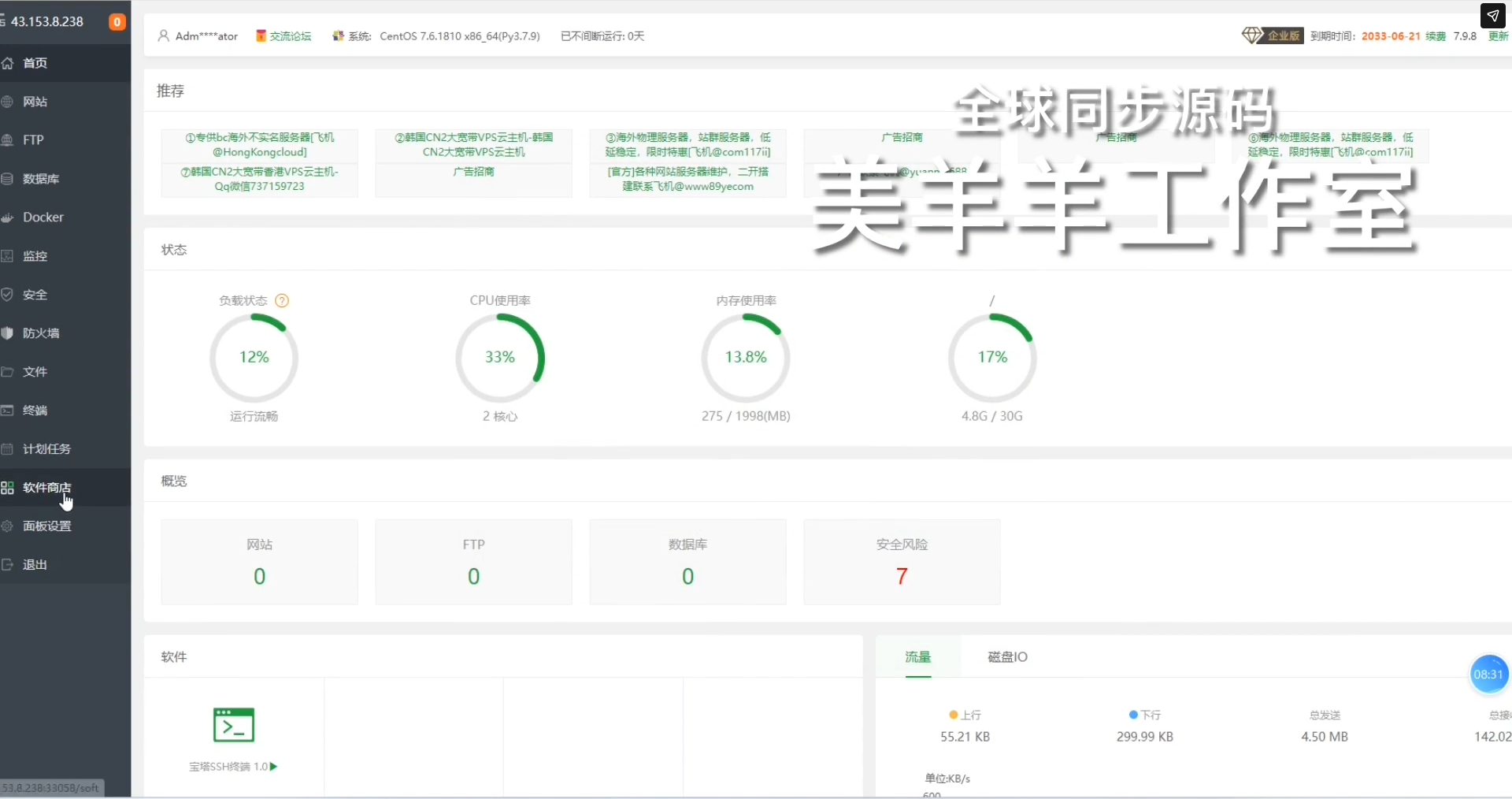
Typically, the actors deploy nginx on one of the external IPs, acting as a publicly facing proxy, to protect the real location of the kit.
Installation of the kit is fully automated.
D2 Panel VS Lighthouse
Like Lighthouse, used by the Smishing Triad, stupidFish provides an interactive GUI in the form of an administration panel to review intercepted data from victims. The structure of the frontend is very similar to Lighthouse and even copies some of its key components.
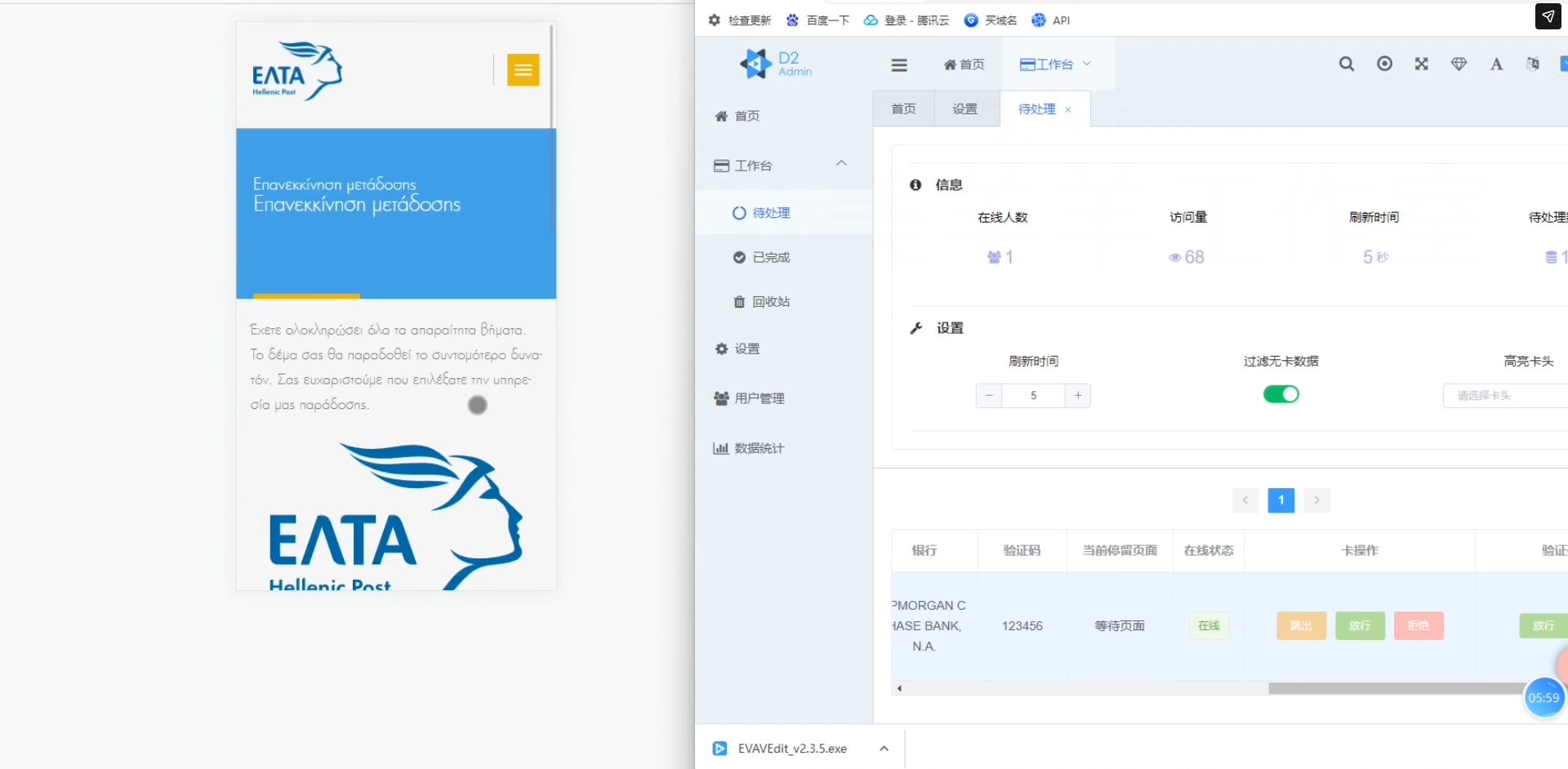
The kit also includes a network filtering module, enabling the operator to block visits from potential crawlers, bots, and hosts that could be controlled by cybersecurity researchers using TOR, VPN, or proxy services to research such kits and their infrastructure.
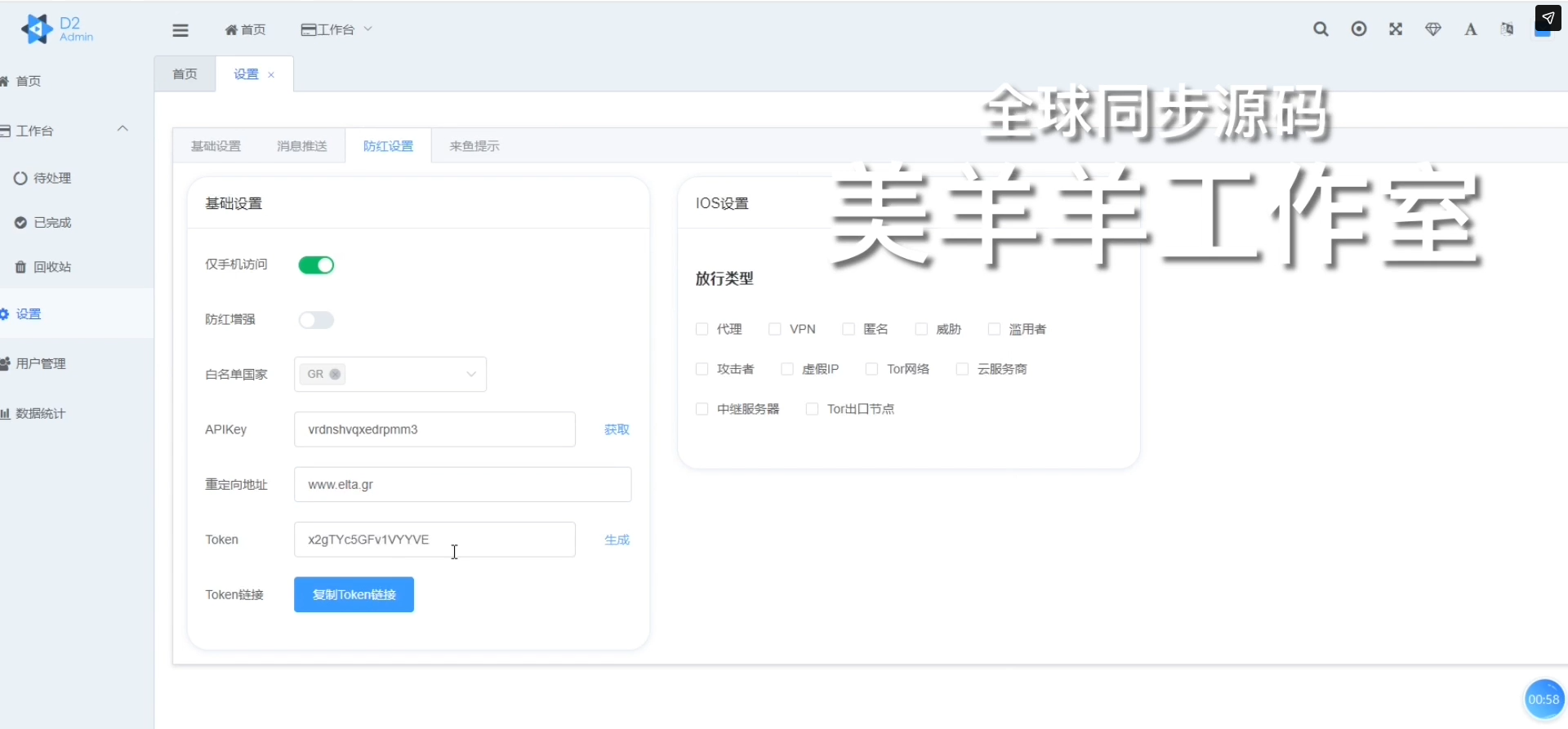
Sike Smishing Triad's TTPs, the group is also targeting popular postal services. One of the most recent targets was ELTA (Ελληνικά Ταχυδρομεία, Hellenic Post), the state-owned postal service provider in Greece, which succeeded the former government postal service founded in 1828.
Resecurity identified hundreds of fake domain names registered by stupidFISH actors in alternative TLD zones, such as ".icu".

Examples of fake domains:
- eltaegr[.]icu
- fetcio[.]icu
- govte[.]icu
- feetco[.]icu
- postuffico[.]icu
- nzpostr[.]icu
- aurspost[.]icu
- aupostr[.]icu
- auvpost[.]icu
- aoupost[.]icu
- auosposte[.]icu
- feoetc[.]icu
- poeston[.]icu
- nexcv[.]icu
- aufpest[.]icu
Notably, most of them were registered last year and protected by Cloudflare. Most fake domains have been registered through GNAME, a Singapore-based domain registrar that is frequently abused by Chinese cybercriminals.
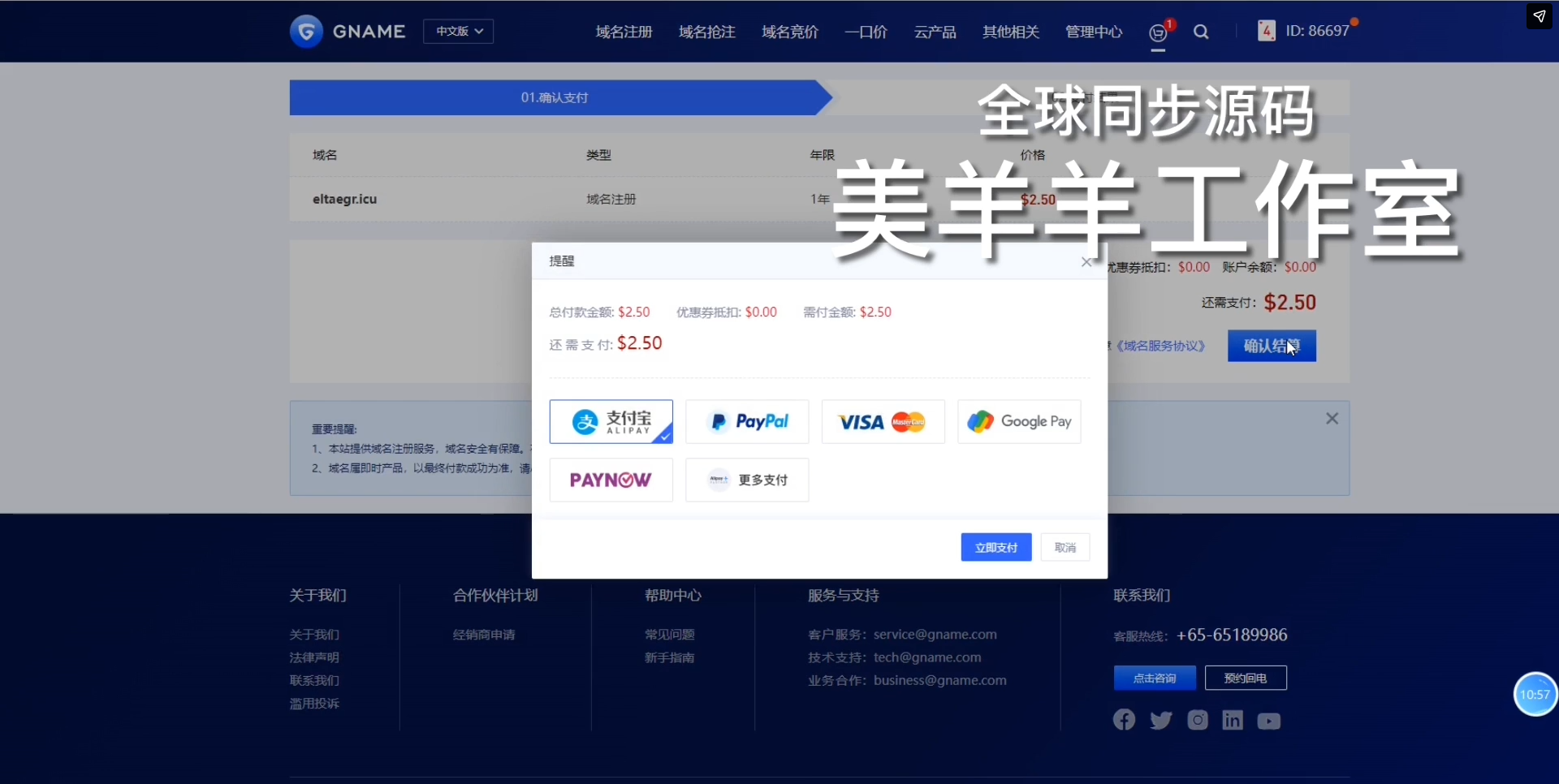
This is not the first instance of GNAME being widely abused by cybercriminals. For example, Smishing Triad also registered fake domains at scale through GNAME when targeting Emirates Post to defraud UAE citizens and other organizations.
Video Demonstration
Resecurity acquired a video demonstration of the stupidFish deployment.
Resecurity warns consumers and businesses about the increased activity by Chinese actors, considering the upcoming winter holidays, and encourages victims to report smishing and phishing campaigns, as well as to exchange threat intelligence information to help disrupt their malicious operations.

