MongoBleed (CVE-2025-14847): MongoDB Memory Leak Flaw
Vulnerability Assessment and Penetration Testing (VAPT)


Summary
A critical vulnerability, CVE-2025-14847 (MongoBleed), was disclosed right after Christmas, an unwelcome “gift” for the cybersecurity community, impacting MongoDB Server deployments that use zlib network compression. Any internet-facing MongoDB instance, whether cloud-hosted or on-premises, including production, staging, or test environments, with zlib compression enabled is potentially vulnerable.
In practice, this impacts all MongoDB versions from 3.6 onward if they have not been patched. The vulnerability can be exploited remotely and without authentication, meaning an attacker only needs network access to the MongoDB service port. As a result, both internet-exposed databases and internally accessible instances reachable through lateral movement are at risk of leaking sensitive process memory.
What is MongoDB?
MongoDB is a widely used NoSQL database designed to store data in flexible, JSON-like documents rather than traditional tables. It provides high performance, scalability, and ease of development, making it popular for web applications, enterprise software, and cloud services.
How MongoDB Works
MongoDB stores data in collections of documents, which can contain nested fields and arrays. Applications interact with MongoDB through queries and commands using its wire protocol, which can optionally compress data (e.g., with zlib) to optimize network transfer. MongoDB supports replication, sharding, and indexing to improve reliability and performance.
Why Securing MongoDB is Critical
MongoDB often contains sensitive application and business data, including personal information, authentication tokens, and internal service details. Misconfigured or exposed MongoDB instances can be accessed remotely, making them an attractive target for attackers. Critical vulnerabilities like CVE-2025-14847 ("MongoBleed") can leak uninitialized memory without authentication, potentially exposing sensitive data to attackers. Ensuring MongoDB is properly secured, patched, and network-restricted is essential to prevent data breaches, financial loss, and regulatory violations.
How the Vulnerability Works
The issue originates from MongoDB’s handling of zlib-compressed wire protocol messages. By sending a specially crafted compressed request, an attacker can trigger the server to return uninitialized heap memory back to the client.
Technically, the flaw occurs because MongoDB’s zlib decompression logic misreports the size of decompressed data. Instead of returning the actual length of valid decompressed content, the server treats the entire allocated buffer as populated. This allows attackers to:
- Specify an inflated uncompressed size in the request
- Force MongoDB to allocate a large memory buffer
- Receive a response containing residual memory contents beyond the legitimate payload
When the client processes this response, it reads memory until null bytes are encountered, effectively exposing arbitrary chunks of the MongoDB server’s heap.
MongoDB describes the root cause as mismatched length fields in zlib-compressed protocol headers, which results in an unauthenticated memory disclosure at the network layer. No credentials, valid database users, or elevated privileges are required to exploit this issue.
Affected and Fixed Versions
| MongoDB Major Version | Vulnerable Versions | Fixed Version |
|---|---|---|
| 8.2 | 8.2.0 - 8.2.2 | 8.2.3 |
| 8.0 | 8.0.0 - 8.0.16 | 8.0.17 |
| 7.0 | 7.0.0 - 7.0.27 | 7.0.28 |
| 6.0 | 6.0.0 - 6.0.26 | 6.0.27 |
| 5.0 | 5.0.0 - 5.0.31 | 5.0.32 |
| 4.4 | 4.4.0 - 4.4.29 | 4.4.30 |
| 4.2 | All versions | ❌ No fix (EOL) |
| 4.0 | All versions | ❌ No fix (EOL) |
| 3.6 | All versions | ❌ No fix (EOL) |
Shodan Exposure Analysis
Shodan Search Query
The following Shodan query was used to identify internet-exposed MongoDB instances running versions vulnerable to CVE-2025-14847:
product:MongoDB version:8.2.0,8.2.1,8.2.2,8.0.0,8.0.1,8.0.2,8.0.3,8.0.4,8.0.5,8.0.6,8.0.7,8.0.8,8.0.9,8.0.10,8.0.11,8.0.12,8.0.13,8.0.14,8.0.15,8.0.16,7.0.0,7.0.1,7.0.2,7.0.3,7.0.4,7.0.5,7.0.6,7.0.7,7.0.8,7.0.9,7.0.10,7.0.11,7.0.12,7.0.13,7.0.14,7.0.15,7.0.16,7.0.17,7.0.18,7.0.19,7.0.20,7.0.21,7.0.22,7.0.23,7.0.24,7.0.25,7.0.26,7.0.27,6.0.0,6.0.1,6.0.2,6.0.3,6.0.4,6.0.5,6.0.6,6.0.7,6.0.8,6.0.9,6.0.10,6.0.11,6.0.12,6.0.13,6.0.14,6.0.15,6.0.16,6.0.17,6.0.18,6.0.19,6.0.20,6.0.21,6.0.22,6.0.23,6.0.24,6.0.25,6.0.26,5.0.0,5.0.1,5.0.2,5.0.3,5.0.4,5.0.5,5.0.6,5.0.7,5.0.8,5.0.9,5.0.10,5.0.11,5.0.12,5.0.13,5.0.14,5.0.15,5.0.16,5.0.17,5.0.18,5.0.19,5.0.20,5.0.21,5.0.22,5.0.23,5.0.24,5.0.25,5.0.26,5.0.27,5.0.28,5.0.29,5.0.30,5.0.31,4.4.0,4.4.1,4.4.2,4.4.3,4.4.4,4.4.5,4.4.6,4.4.7,4.4.8,4.4.9,4.4.10,4.4.11,4.4.12,4.4.13,4.4.14,4.4.15,4.4.16,4.4.17,4.4.18,4.4.19,4.4.20,4.4.21,4.4.22,4.4.23,4.4.24,4.4.25,4.4.26,4.4.27,4.4.28,4.4.29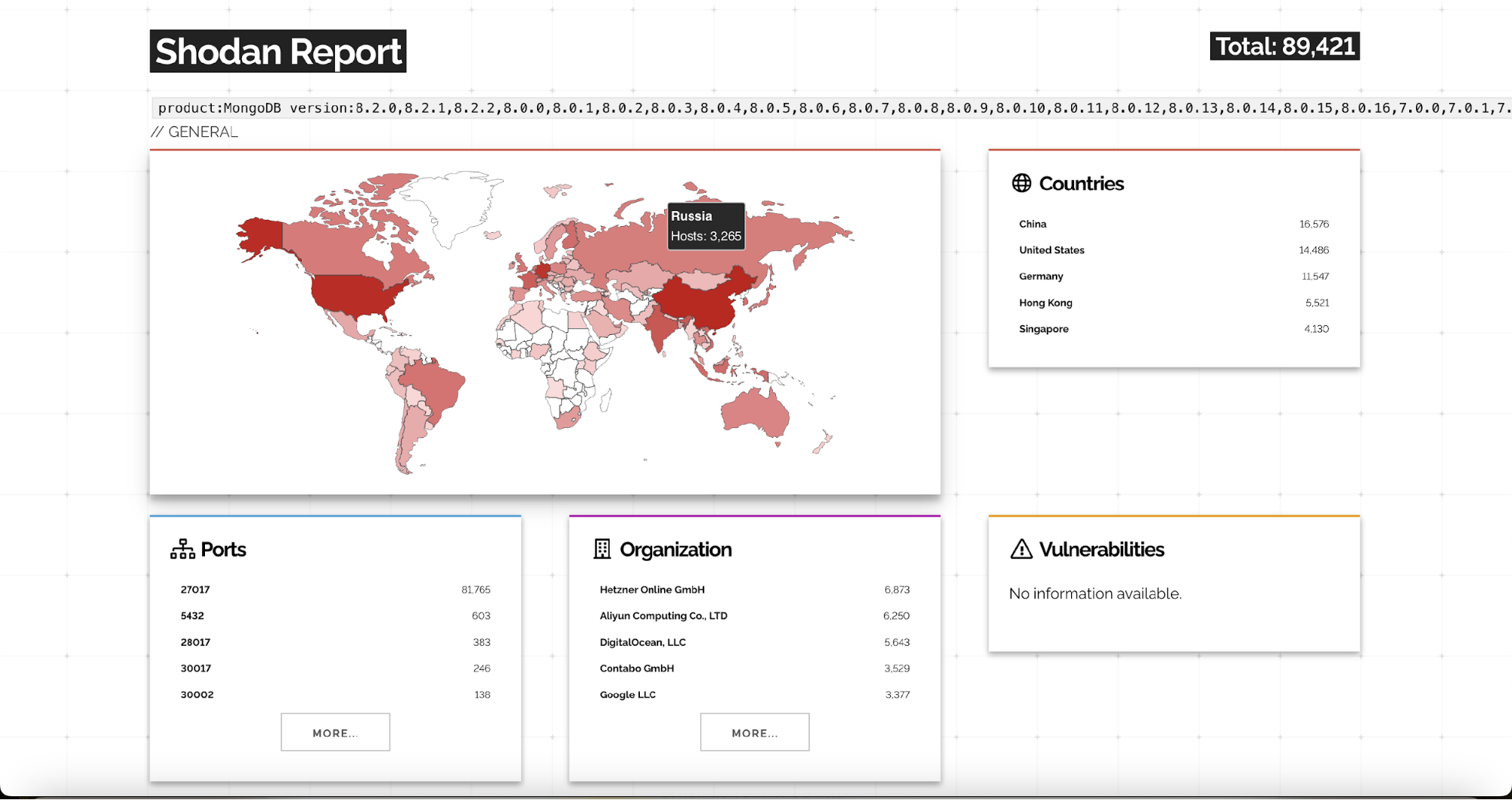
This query specifically targets MongoDB services exposed on the default MongoDB port (27017) that disclose a version string known to be vulnerable to the MongoBleed memory-disclosure vulnerability.
Internet-Exposed MongoDB Instances
The statistics indicates a large global attack surface consisting of MongoDB servers running vulnerable versions and directly accessible from the internet. Because CVE-2025-14847 is exploitable remotely and without authentication, every exposed instance identified via external mapping services is immediately at risk.
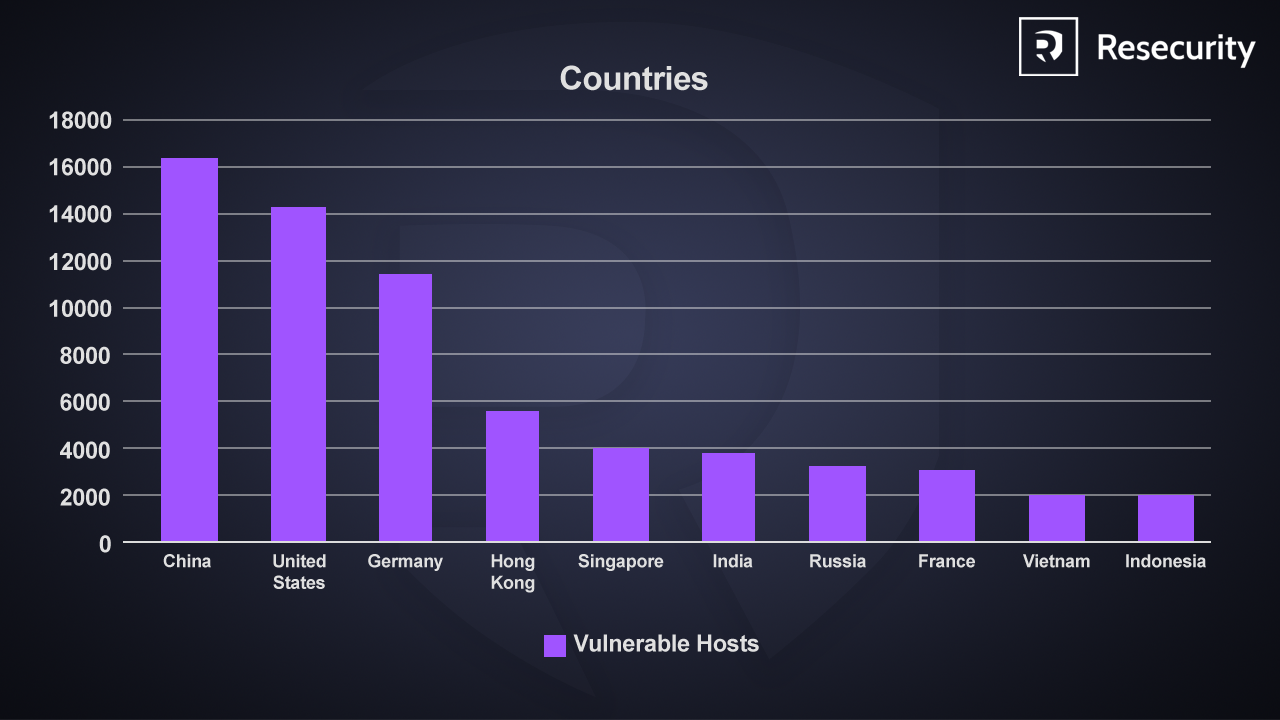
Geographic Distribution
Based on the available telemetry, the highest number of exposed vulnerable MongoDB instances were observed in the following countries:
- China: 16,576 exposed instances
- United States: 14,486 exposed instances
- Germany: 11,547 exposed instances
- Hong Kong: 5,521 exposed instances
- Singapore: 4,130 exposed instances
According to our HUNTER team, additional exposures were observed in India, Russia, France, Vietnam, and Indonesia, suggesting the issue is globally distributed rather than regionally isolated.
The chart below illustrates the geographic distribution of exposed vulnerable MongoDB instances by country. It highlights regions with the highest concentration of affected systems, providing insight into potential risk hotspots.
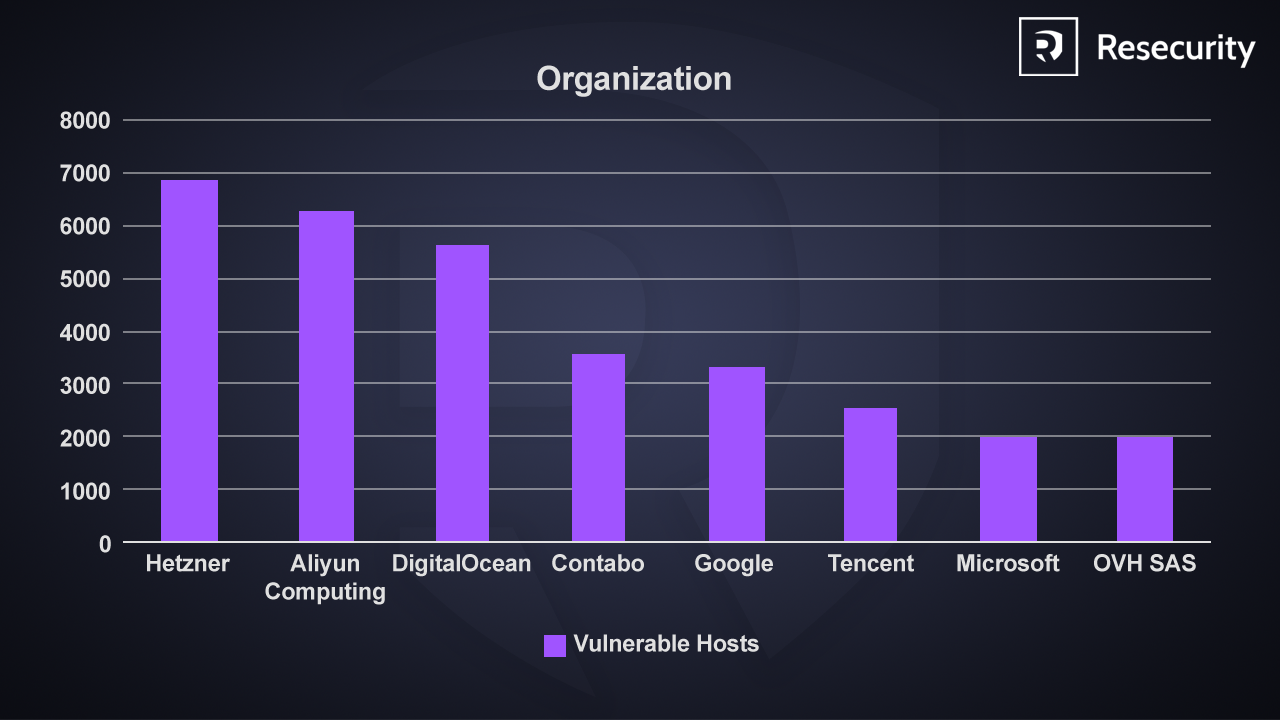
Infrastructure Provider Distribution
The available telemetry shows that a significant portion of exposed and vulnerable MongoDB instances are hosted on major cloud and infrastructure providers. The highest concentrations were observed on the following providers:
- Hetzner Online GmbH: 6,828 exposed instances
- Alibaba Cloud (Aliyun): 6,226 exposed instances
- DigitalOcean, LLC: 5,594 exposed instances
- Contabo GmbH: 3,509 exposed instances
- Google LLC: 3,364 exposed instances
- Tencent Cloud: 2,551 exposed instances
- Microsoft Corporation: 1,952 exposed instances
- OVH SAS: 1,935 exposed instances
The concentration of vulnerable MongoDB instances on large cloud and hosting providers highlights the risk of misconfiguration at scale. Attackers can rapidly enumerate and target these environments using internet-wide scanning platforms, enabling automated exploitation, data exposure, and service compromise across multiple tenants.
The infrastructure and cloud providers hosting the highest number of affected systems.
Who is impacted
This vulnerability impacts organizations running self-managed MongoDB servers on affected versions where:
- The MongoDB service is reachable over the network
- zlib compression is enabled
This includes MongoDB deployed on:
- Virtual machines
- Containers
- Kubernetes clusters
- Cloud environments with misconfigured networking
Proof of Concept
The vulnerability was validated using the publicly available MongoBleed proof-of-concept exploit developed by Joe DeSimone:
https://github.com/joe-desimone/mongobleed/blob/main/mongobleed.py
This script demonstrates unauthenticated memory disclosure in vulnerable MongoDB servers by sending a malformed MongoDB wire-protocol message using zlib compression.
PoC Execution Command
The following command was used to trigger the vulnerability against a target MongoDB instance:
python3 mongobleed.py --host 10.10.10.10 --port 27017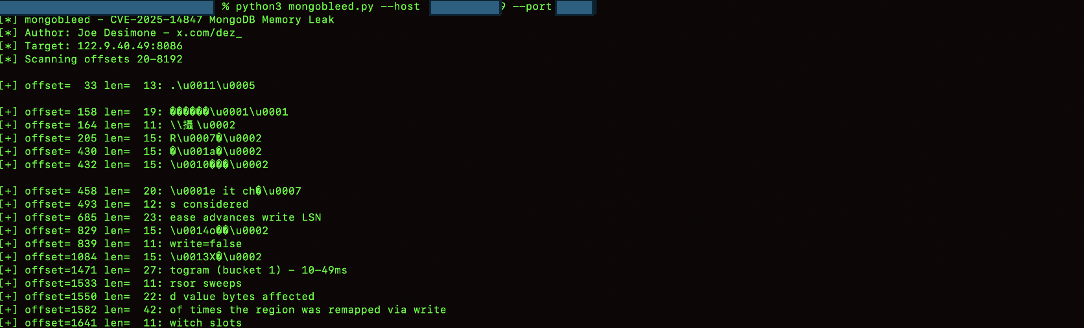
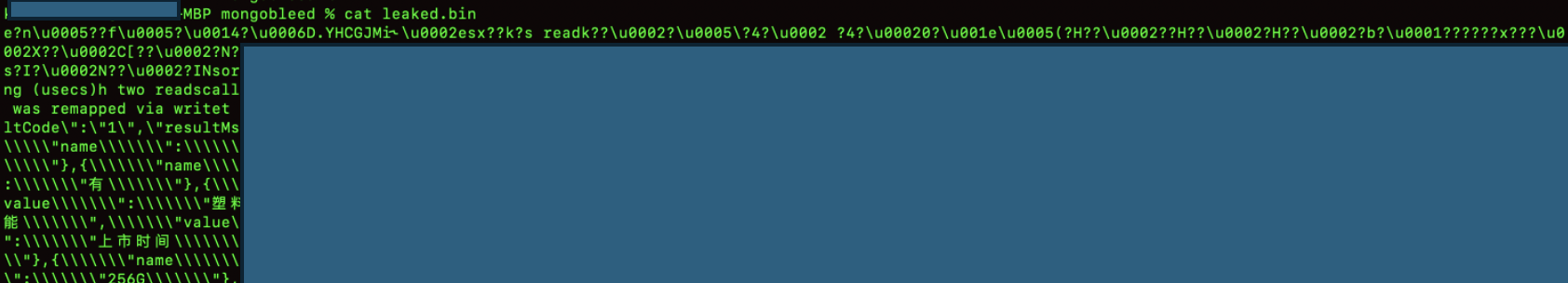
The screenshot shows the raw response returned by the MongoDB server after sending a malformed compressed request.
Upon successful exploitation, the leaked memory contents are written to a file named leaked.bin, which is dumped locally by the exploit once execution completes.
No authentication credentials or valid MongoDB user accounts are required for exploitation.
The exploit is based on the public MongoBleed research and confirms that a remote attacker can retrieve arbitrary MongoDB server memory without valid credentials.
PoC Methodology
- A compressed MongoDB message is sent to the server
- The message declares an inflated uncompressed size
- MongoDB allocates a larger memory buffer than needed
- Due to incorrect length handling, MongoDB returns:
- Valid response data
- Residual heap memory contents
- The client receives and parses leaked memory until null bytes are encountered
This behavior confirms a successful exploitation of the vulnerability.
Analysis of the Leaked Output
The leaked output consists of a mix of binary data and readable plaintext, which is expected behavior when dumping uninitialized heap memory.
The following examples illustrate the types of data observed in leaked MongoDB server memory during exploitation of CVE-2025-14847.
All values shown are anonymized and non-sensitive.
Indicators of Successful Exploitation
- Presence of non-UTF binary characters (\u0005, ??, corrupted bytes)
- Cleartext application and business data
- Tokens and secrets appearing outside any legitimate query context
- Internal system strings unrelated to the attacker’s request
This confirms that memory beyond the intended response buffer was returned.
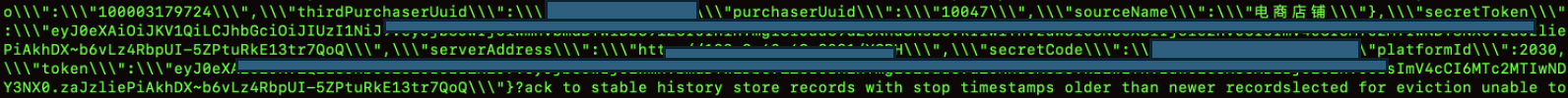
Authentication & Secrets
Leaked authentication tokens and secret values can be reused by attackers to impersonate users or services.
This may lead to unauthorized API access, session hijacking, and full account compromise.
{
"token": "eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.REDACTED",
"secretToken": "REDACTED_SECRET_VALUE",
"secretCode": "REDACTED_CODE"
}
Internal Infrastructure Data
Exposure of internal service URLs, platform identifiers, and UUIDs reveals internal network topology.
This information enables attackers to perform lateral movement and target internal systems more precisely.
{
"internalServiceUrl": "http://10.0.12.5:8080/api",
"platformId": "PLATFORM-XXXX-1234",
"supplierUuid": "SUP-UUID-XXXX"
}Business & Transaction Data
Order numbers, invoices, payment types, and financial totals may be exposed in cleartext memory.
This results in leakage of confidential business operations and sensitive financial workflows.
{
"orderNumber": "ORD-2024-XXXX",
"invoiceNumber": "INV-XXXX-7890",
"paymentType": "BANK_TRANSFER",
"totalAmount": 1450.75
}
Product / SKU Information
Leaked product identifiers, quantities, and pricing details expose inventory and procurement data.
Attackers can use this information for competitive intelligence or financial fraud.
{
"skuId": "SKU-XXXX-001",
"productName": "Product A",
"quantity": 25,
"unitPrice": 58.00
}Personally Identifiable Information (PII)
Organizational names, employee identifiers, tax numbers, and banking metadata may be disclosed.
This creates serious privacy, regulatory, and legal risks under data protection laws.
{
"purchaserName": "Employee X",
"organizationName": "Company A",
"taxNumber": "TAX-XXXX-9999",
"bankAccount": "BANK-ACCOUNT-REDACTED"
}Application Runtime & Internal Logs
Internal runtime states, thread information, and performance metrics can be recovered from memory.
Such data helps attackers understand application behavior and chain further targeted attacks.
{
"threadState": "WAITING",
"cursorReadLatencyMs": 32,
"writeLatencyMs": 18
}Impact
- Sensitive Data Disclosure
Attackers can retrieve uninitialized MongoDB server memory containing credentials, API keys, tokens, and confidential business data. - Authentication Bypass
Because exploitation requires no authentication, attackers can extract sensitive information without valid MongoDB users or permissions. - Account and Service Compromise
Leaked authentication tokens and secrets can be reused to impersonate users or backend services, leading to unauthorized access and privilege escalation. - Lateral Movement Enablement
Exposure of internal URLs, service identifiers, and infrastructure metadata allows attackers to map internal networks and pivot to additional systems. - Regulatory and Compliance Violations
Disclosure of personally identifiable information (PII) and financial data may trigger violations of GDPR, PCI-DSS, and other data protection regulations. - High Risk of Mass Exploitation
Publicly exposed MongoDB instances can be discovered and exploited at scale using Shodan and automated tools, significantly increasing the likelihood of widespread data breaches.
How to Prevent It
- Apply Security Patches Immediately
Upgrade MongoDB to fixed versions (8.2.3, 8.0.17, 7.0.28, 6.0.27, 5.0.32, or 4.4.30) to fully remediate the vulnerability. - Migrate End-of-Life Versions
Replace unsupported MongoDB releases (3.6, 4.0, and 4.2) with actively supported versions that receive security updates. - Disable zlib Compression as a Temporary Mitigation
If immediate patching is not possible, disable zlib network compression or switch to an alternative compression method to prevent exploitation. - Restrict Network Exposure
Limit access to MongoDB port 27017 using firewalls, security groups, or VPNs, ensuring the database is not publicly accessible. - Implement Monitoring and Detection Controls
Monitor for malformed compressed requests, abnormal response sizes, and unusual protocol behavior indicative of exploitation attempts. - Strengthen Long-Term Database Security
Enforce regular patch management, network segmentation, and database activity monitoring to reduce the attack surface and prevent future exploitation.
Conclusion
CVE-2025-14847 ("MongoBleed") represents a severe threat to MongoDB deployments worldwide. With easy remote exploitation, no authentication requirements, and significant data leakage potential, organizations must treat this vulnerability with utmost urgency. Exposed instances should be assumed compromised until verified otherwise, and immediate action - such as applying patches or disabling zlib compression - is critical. Organizations are advised to conduct forensic analysis for signs of exploitation and comprehensively strengthen database security postures. The window for remediation is rapidly closing as attackers actively scan for and exploit vulnerable systems, making proactive MongoDB vulnerability management an essential component of overall database security strategy.

