

Working with Fortune 500 enterprises globally we’ve realized that one of the top threats CISOs outline as extremely concerning – employees cybersecurity awareness. Even though they have great technology implemented to manage various cyber risks, the human element still remains one of the key gaps to handle.
In order to assist CISOs with determining how well their employees can recognize targeted cybersecurity threats, we initiated multiple exercises based on real-life scenarios aimed towards increasing their awareness of how threat actors may attack them, and what they should consider avoiding in order to prevent breaches or malicious code infections delivered either via e-mail attachments, phishing or “drive-by” download attacks leveraging exploit-kits.
What is Phishing Simulation?
One of the most effective exercises performed on an enterprise scale is a phishing simulation. In the scope of such an exercise, the employees will receive simulated phishing e-mails, potentially focused on the interception of their credentials, or leading them to a potentially malicious site. Such sites may contain “dummy” code or notifications explaining how the employee should refrain from opening such resources in the future and how to inspect URL’s before opening them, otherwise it may lead to a risk of compromise.
Last year, the National Institute for Standards and Technology (NIST) published updated recommendations for phishing simulations in their security awareness training programs:
“Practical exercises include no-notice social engineering attempts to collect information, gain unauthorized access, or simulate the adverse impact of opening malicious email attachments or invoking, via spear-phishing attacks, malicious web links.” – NIST SP 800-53, Rev. 5, Section 5.3 (pg. 60).
Why are Phishing Simulations Useful?
Phishing Simulations are a great component in cybersecurity awareness and training programs, employees learn to be vigilant and careful while working online. It acts as a preventive measure and an educational method which increases their awareness about actual cybersecurity threats.
How to Measure Success Rate?
NIST introduced the Phish Scale which utilizes a rating system based on the content of phishing emails. In fact, the adequate metrics could be based on several criteria:
- Total number of phishing letters opened.
- Total number of clicks on URLs in the emails.
- Total number of attempts to enter credentials (non confirmed victims).
- Total number of successful logins (confirmed victims).
CISO and IT security team may research these metrics to determine the overall cybersecurity awareness level of the staff and to address possible issues individually in order to educate employees why they shouldn't follow instructions from phishing emails.
Technical Aspects to Consider
a) Infrastructure
Making sure proper infrastructure is prepared to host and manage the phishing simulation campaign is imperative to collect further results from the successfully opened e-mails. Such infrastructure should be deployed in an environment you control and are able to audit. At the end of the phishing simulation, it’s good practice to erase all the collected results to prevent the possible leakage or the disclosure of details surrounding your employees.
b) Domain Names
In certain phishing simulation cases, the company may leverage domain names which appear like the official domain. The best results are achieved by leveraging domains with missing letters or punnycode. In some cases, this measure may be unnecessary, however alternative tactics may be used, for example, leveraging e-mail sender spoofing, but in the event the company is using SPF/DKIM, such an approach may not work as expected, and it’s likely the e-mail will go to the junk mail folder thus affecting delivery rates.
c) Phishing Templates
The most effective phishing templates are typically based on well-known applications and services familiar to your employees. This conclusion is based on the successful experience of phishing simulations performed in organizations of various size; the best results were achieved by leveraging the following templates:
- Fake MSFT Teams or Zoom Invitation
Such templates may contain a hyperlink leading to a fake authorization form or a simulated malicious resource. Both applications are widely used in the enterprise sector, typically the users instantly interact with such e-mails.
- Invoices, Financial Documents, SOWs
These templates may contain an e-mail with simulated malicious attachments or external links the user is required to click leading them to a particular document or to sign it. The actual hyperlink may lead to a fake authorization form.
- Communications from Known Sender
The recent campaigns by Trickbot and Oakbot are leveraging Business E-mail Compromise (BEC) which collects the actual communications from the victims, then later used to distribute malicious code. Threat actors include intercepted communications in their phishing attempts, by doing so the victims have no doubt that it has been received from a colleague or an executive. These e-mails have a significantly higher opening rate, this is because the potential victim will treat them as received from known and trusted senders.
- Surveys, Events and Gift Cards
From a psychology perspective, phishing simulations should leverage tactics oriented on social engineering, as this is what actual perpetrators will use when they attack your employees. A question to consider is “what would motivate an employee to open and click malicious links contained in e-mails?”. Only subjects of interested will have a high likelihood, for example e-mails containing a link to activate a free gift-card may generate an immediate reaction and lead to a click.
- Expired Accounts and Passwords
In epoch of remote workforce, these vectors remain one of the “champions” in successful phishing simulations. In this case, the employee receives a notification that his password has expired which will then likely cause them to react by modifying it, but by doing so also provides his current password, this is all done without any validation with the IT team.
- Software or Services Updates
Notifications about possible software or service updates provoke employees to click to learn more about it.
d) Tracking
It is critical to generate IDs or tags which allow you to track which user clicked on the phishing URL’s. In certain cases, you will see who forwarded the e-mails to another user, as the recipients may start communicating about the suspicious e-mails.
Ethical Aspects to Consider
- Before the actual phishing simulation campaign, it’s highly recommended to notify employees about the upcoming training exercise and explain how the company is working hard to protect them and the company’s IT infrastructure. It’s also good to explain why security testing will be performed in the upcoming few weeks, by doing so it helps determine cybersecurity awareness and digital identity protection levels within the workforce, and in case they have any questions they may contact their Chief Information Security Officer (CISO) and/or the Data Protection Officer (DPO).
- Make sure, before any engagement with third parties (e.g., penetration testing company or vendor responsible for phishing simulation), there are strictly defined “rules of engagement” to prevent potential miscoordination and miscommunications beforehand, during and after phishing simulation.
- Don’t use and/or re-use malicious code developed by cybercriminals available from the Dark Web, while it may be helpful with testing based on the real signatures, it may create certain legal issues without proper discussion and internal coordination with HR and the Chief Legal Counsel within the company.
- Be strategic and ethical with the use of possible cyber offensive tools used by red teams and penetration testers. A phishing simulation is not a pentest and shouldn’t involve actual malicious payloads which compromise or target the employees. Unless such exercises are also possible within the scope of an actual penetration test leveraging social engineering, they should be properly coordinated internally.
- Don’t practice phishing simulations focused on employee’s personal e-mail accounts registered on public e-mail providers (Gmail, Yahoo!, Hotmail, etc.) as it may directly or indirectly affect their privacy. During the performed tests, facing Board Members, Advisors of the Companies, or Stakeholders which may use domains different from the official corporate domain used by the Client, and in such cases should be discussed in detail.
- Don’t target and/or misrepresent your vendors, partners, or supply chain. While they’re an important component of the day-to-day operations, it may lead to certain legal implications, and cause multiple issues for you as a company.
- Don’t create a problem for your employees when there is no problem. You need to treat the exercise as an exercise, by doing so understanding that your enterprise is dealing with variety of things, and the business hours for your employees are when they actually work. Phishing simulations shouldn’t cause any issues or affect their work schedule during business hours. Different employees have different cybersecurity awareness levels, that’s why your sole goal should be focused on how to increase their awareness in a positive manner.
- Debrief your employees after the phishing simulation is completed. This practice will be helpful to demonstrate the responsibility of the company and how it’s protecting them, as well as the willingness to make them safer and more aware about actual cybersecurity threats. The level of debriefing may vary, but at least include a “thank you” and a brief remark showing which department demonstrated the best awareness level. It’s always good to conclude with the results of the exercise, as well demonstrating team efforts to make the company safer.
Examples Of Phishing emails:
1. The Fake Invoice Scam
Let’s start with arguably the most popular phishing template out there - the fake invoice technique. Like many phishing attacks, this scam relies on fear and urgency, pressuring an end user to submit a payment for goods or services they’ve never even ordered or received.
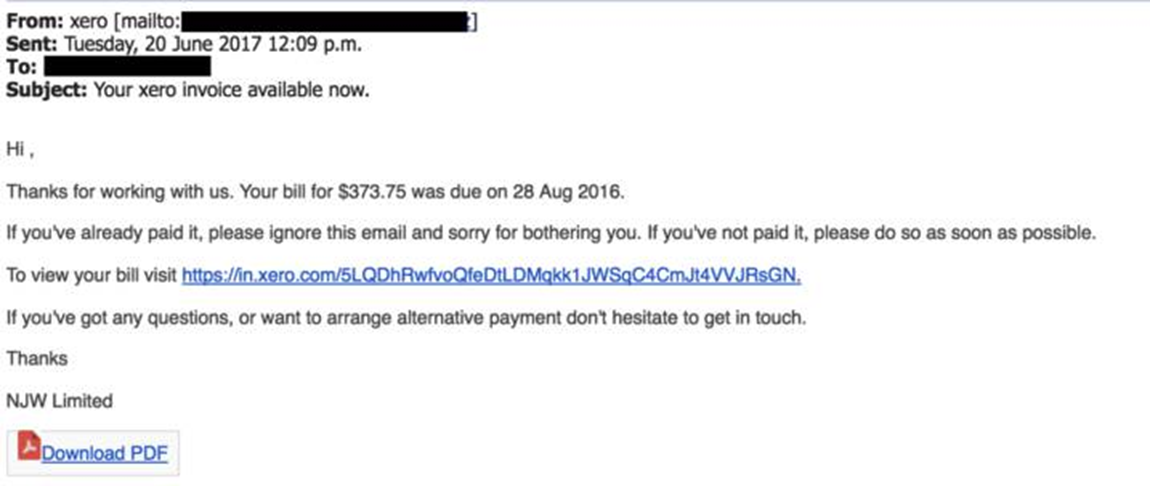
Finance departments are the obvious targets for this sort of attack, although there are plenty of potential victims that could be duped.
2. Email Account Upgrade Scam
Faced with having your account expire unless immediate action is taken, the email account upgrade scam can appear to come from trusted email providers like Microsoft and Google, or simply from your company’s IT department.
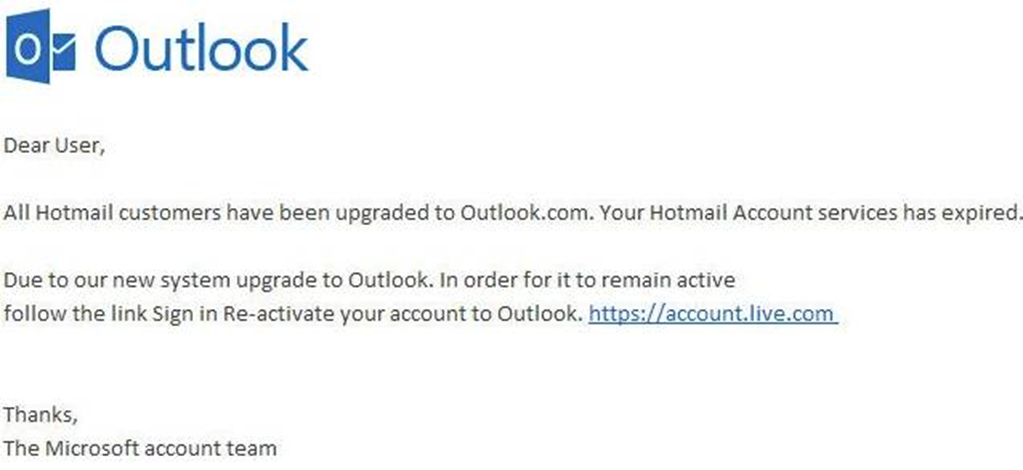
As you can see, nothing harmful stands out from this email. There are no stand-out grammatical errors, no elaborate requests, and the link itself would appear to be direct to a safe “https” web page for an unsuspecting user. A useful tip is to hover over the link itself when being asked to give personal details - as the text itself often doesn’t represent the true destination of the link.
3. Advance-fee Scam
Perhaps receiving an email from a foreigner begging for your help to recover trapped funds with an elaborate story. But don’t be fooled, this scam has been around for a long time, and there’s a good reason for that - it works.
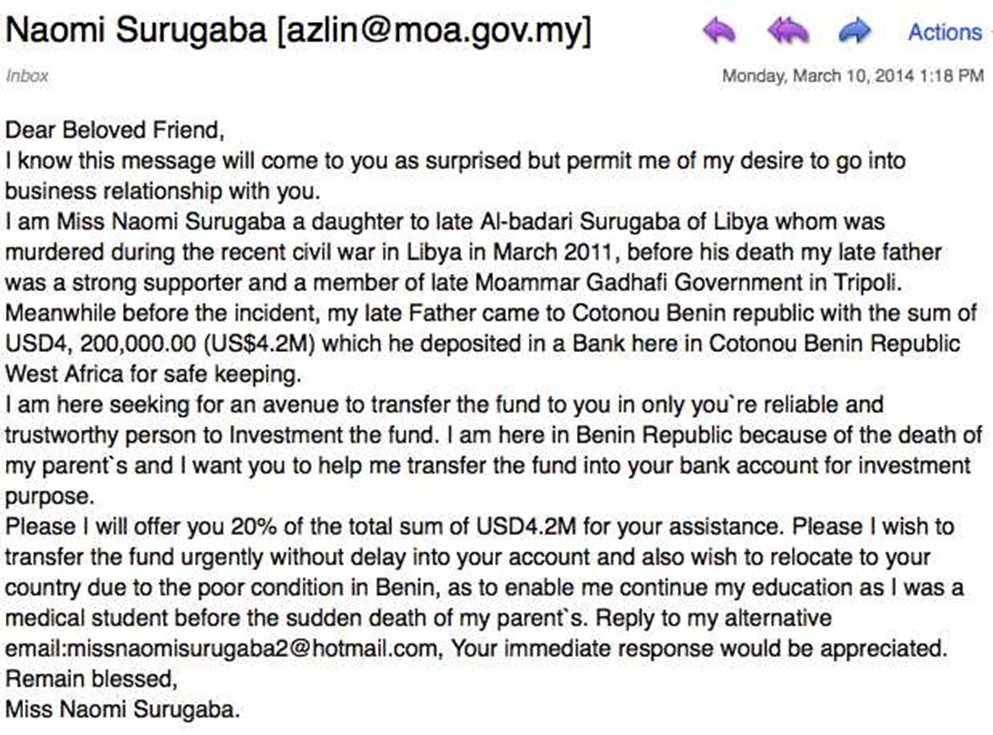
In the email, the scammer will offer you a large sum of money in exchange for your bank details. Not only will you not receive a dime from this kind Prince, but you will also see a chunk of your money go in the opposite direction.
4. Google Docs Scam
One of the most recent high-profile phishing techniques, the Google Docs scam offers an extra sinister twist as the sender can often appear to be someone you know.
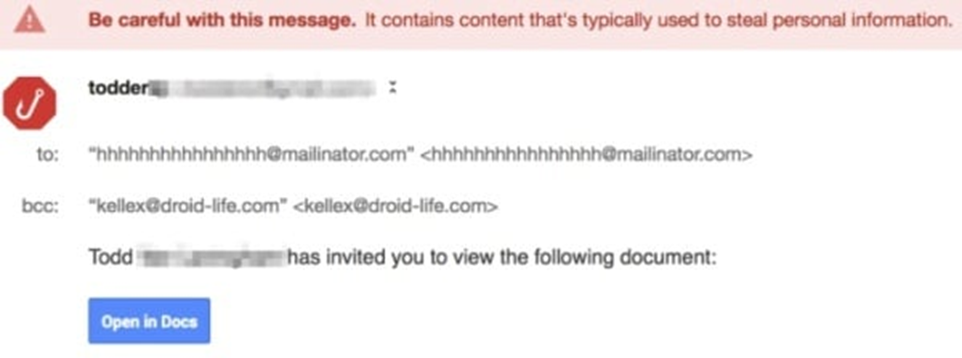
This ultra-sophisticated email encourages you to click on its link to view a ‘document’, which then takes you to an almost identical version of Gmail’s login page. Once an account has been selected, you’re then invited to grant access to your Google account, meaning the attacker has free rein.
5. PayPal Scam
With around 200 million users, PayPal is an incredibly lucrative tool for a cybercriminal. As well as its high volume of accounts, PayPal offers fraudsters the chance to take advantage of the platform linked directly to your credit card or bank account.
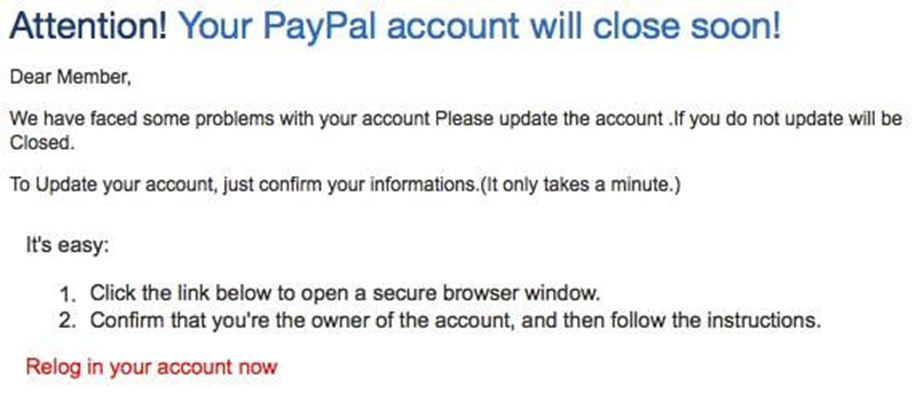
These emails often include the PayPal logo, plus a convincing chunk of fine print at the bottom of the email. Again, this scam tries to induce panic mode for its victims, often with a “There’s a problem with your account, please click here to fix it” kind of message. Beware, they also contain legitimate-looking fine print.
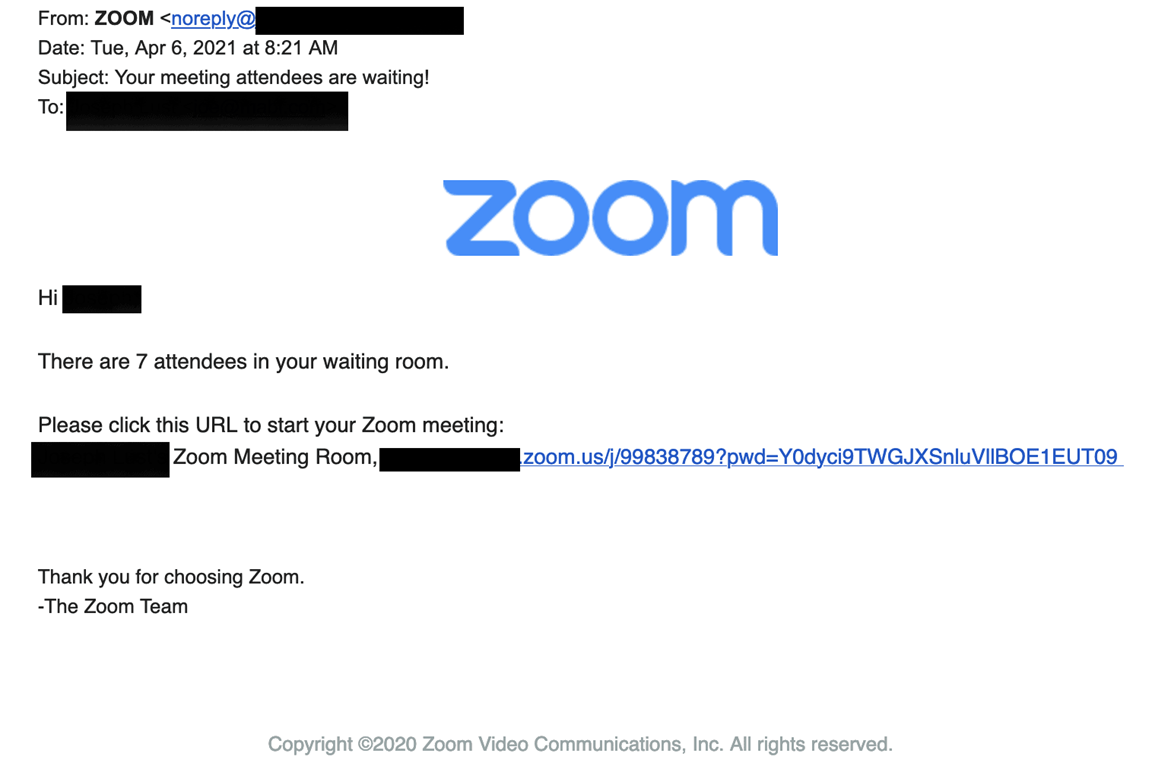
6. Fake Zoom Invitations Stealing Credentials
Available for Your Termination Meeting in a few Minutes?
Employees are receiving fake Zoom meeting invitations with words like “suspension” and “termination” with the meeting scheduled in only a few minutes. They hastily click the invitation link to join the meeting, are prompted to login to Zoom, and accidentally hand over their credentials to an attacker.
This attack is particularly nasty because it preys on our emotional response. Most people who get a meeting invitation regarding a performance review and potential termination are going to get panicky, especially when the meeting is starting soon, so they may not be thinking clearly. Then before they can realize it, they’ve just become the victim of a phishing attack.
For these emails, it is important to verify the sender’s email address and domain are recognizable and trusted. If you feel it’s safe to click on the link, ensure the URL directs you to the official zoom.us website before entering any personal information or credentials, it is at this point where an attacker would steal your information, so you must remain vigilant and confirm the web address is correct.
7. Microsoft Teams Phishing Attack Targets Office 365 Users
Like other collaboration and communications platforms, the popularity of Microsoft Teams has risen since the beginning of the Covid-19 pandemic because a growing number of organizations started using the remote working model.
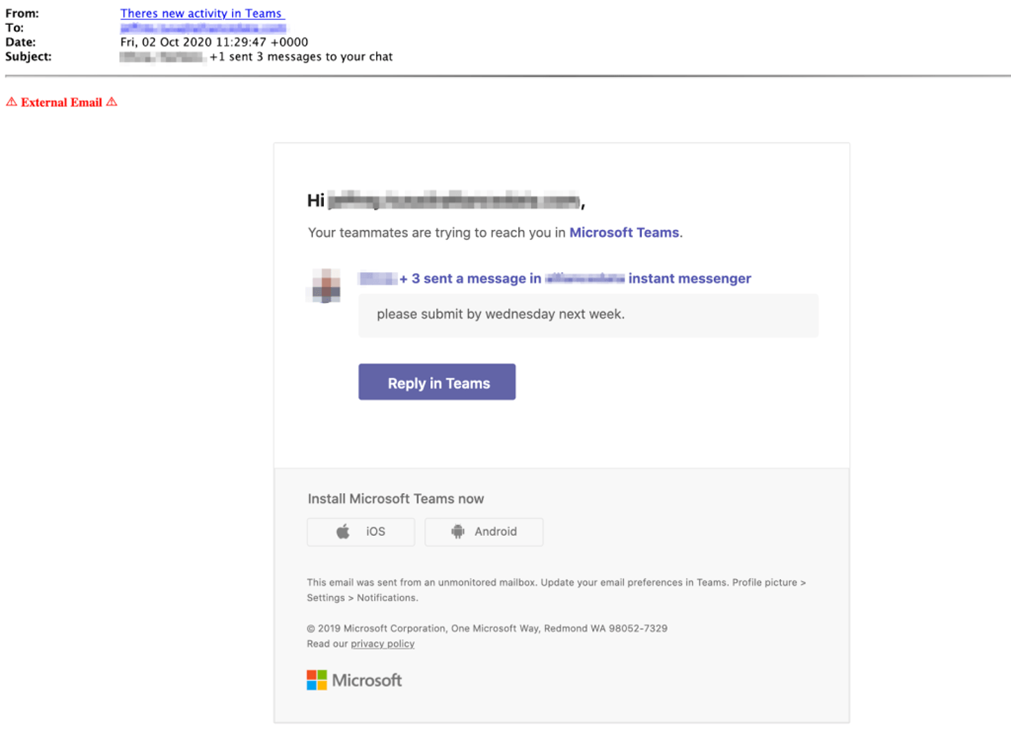
The bait email displays the name “There’s new activity in Teams” to trick the victims into believing it’s an automated notification from Microsoft Teams. The email tells the recipient they’ve missed Microsoft Team chats and show an example of a teammate chat that asks them to submit something by Wednesday of next week. Recipient could respond to the email by clicking on the “Reply in Teams” button that is present in the message content, but because of this action, the victim is redirected to a phishing page. The phishing landing page looks like a Microsoft login page, its URL begins with the “microsftteams” to appear as legitimate.
If you are interested in executing a* phishing simulation, please, contact us via the WEB-form or use our email (contact@resecurity.com).

