Cyber Counterintelligence (CCI): When 'Shiny Objects' trick 'Shiny Hunters'
Cyber Threat Intelligence


Introduction
It is worth noting that "Shiny Hunters" (tricked by our team with a honeytrap), or more accurately, their rebranded version involving new members, which calls itself "Scattered Lapsus$ Hunters" (SLH) or "Scattered Lapsus$ Shiny Hunters (SLSH)," is linked to 'The Com' (short for 'The Community'), a predominantly English-speaking cybercriminal ecosystem. In the context of this threat research publication, Resecurity is using the name "Shiny Hunters" as a collaborative alias to illustrate the phenomenon of involving young IT professionals in questionable acts, but more importantly, to prevent others from doing the same.
In fact, the naming of such groups is changing very frequently and intentionally, typically by the actors themselves, who wish to obscure attribution. They use different spellings, sometimes attach themselves to specific group names and detach later, which should not be taken into consideration, as some of them serve as "role players." It is important to note that members present in some online chats, channels and groups associated with these collectives should not necessarily be attributed to them.
This loosely organized network operates more like a cybercrime youth movement, encompassing a broad and constantly shifting range of actors, mainly teenagers. Some announcements of successful data breaches by these actors were published on the associated Telegram channel, "The Comm Leaks," along with many other posts that were created, later deleted, and re-created again under new names. The FBI issued a Public Service Announcement (PSA) last year warning about the risks associated with joining such movements.
Data breaches, intrusions, and ransomware are typically related to one of the key domains of "The Com" — known as "Hacker Com." Besides hacking, derivatives of "The Com" include In Real Life (IRL) Com, which encompasses subgroups that facilitate real-world physical violence, often stemming from online conflicts. Members may start their participation in IRL Com, make friends with other members in Hacker Com, develop the necessary cyber skills, and then begin participating in Hacker Com while maintaining their association with IRL Com. Others may use funds gained through participation in Hacker Com to engage in Extortion (Extort) Com. Extortion primarily involves the exploitation of children. Members may extort minors, typically females, through threats of doxing, swatting, and IRL violence if their demands are not met, forcing them to carry out specific malicious actions.
Connor Riley Moucka and John Erin Binns
Resecurity began tracking such actors well before the industry even started discussing them. This started with Connor Riley Moucka, 25 (aliases: Waifu, Judische, Ellyel8) and John Erin Binns, 24 (aliases: IRDev, IntelSecrets), who were investigated by our HUNTER unit in early 2017—almost 10 years before the DOJ released an indictment against both actors last year:
United States vs. Connor Riley Moucka and John Erin Binns
https://www.justice.gov/usao-wdwa/united-states-vs-connor-riley-moucka-and-john-erin-binns
Before their arrest, Resecurity provided authorities with email communications it had acquired from one of the key actors, John Erin Binns, who used a foreign email account to complicate the investigation. Analyzed messages revealed cloud instances used by the actor, instant messaging (IM) accounts and chat groups, rented dedicated virtual servers and phone numbers, and IP addresses.

In November 2024, Canadian police arrested Moucka on charges tied to the theft of terabytes of data from clients of the cloud-based data warehousing platform Snowflake. The Snowflake data breach refers to a large-scale cybersecurity incident involving unauthorized access to customer cloud environments. The breach affected numerous high-profile clients and has been regarded as one of the most significant data security incidents of the decade.
At least 160 organizations were reportedly targeted through vulnerabilities in the configuration and access to their Snowflake environments. Affected companies included AT&T, Ticketmaster/Live Nation, Santander Bank, LendingTree, Advance Auto Parts, Neiman Marcus, and Bausch Health. The breach resulted in the theft of a wide range of sensitive data, such as:
- Personally Identifiable Information (PII)
- Medical prescriber DEA numbers
- Digital event tickets
- Over 50 billion call records from AT&T
The stolen data was allegedly used for extortion by the group under the umbrella of "ShinyHunters", with hackers demanding ransoms from affected organizations in exchange for not leaking or selling the information.
His accomplice, Binns, was arrested in May 2024 in Turkey, based on a U.S. indictment charging him with hacking T-Mobile in 2021.
The Snowflake breach had grave implications for AT&T, whose call and text message metadata involving nearly all U.S. customers was compromised. The breach prompted an unprecedented request from the U.S. Department of Justice, which asked AT&T to delay public disclosure due to national security and public safety concerns. Reports later confirmed that AT&T paid a $370,000 ransom to have the stolen data deleted.
Both defendants Connor Riley Moucka and John Erin Binns have been charged with conspiracy, computer fraud and abuse, extortion related to computer fraud, wire fraud, and aggravated identity theft in connection with an alleged scheme to hack into at least 10 victim organizations' protected computer networks, steal sensitive information, threaten to leak the stolen data unless the victims paid ransoms, and sell the stolen data online.
Connor Moucka is scheduled for trial on October 19, 2026. John Binns is not currently in U.S. custody.
Security investigations revealed that the attackers accessed customer environments by exploiting stolen credentials obtained via infostealer malware. These credentials, which lacked multi-factor authentication (MFA) in many cases, allowed attackers to log in directly to Snowflake customer instances using only a username and password. Based on that pattern, Resecurity has designed a method to trick
attackers into deliberately creating honeytraps, enabling us to log
actionable network intelligence.
Cameron John Wagenius
Moucka and Binns were also associated with another actor, Cameron John Wagenius, a 20-year-old U.S. Army soldier who went by the online alias "Kiberphant0m." The "trio" met online and allegedly engaged in related cybercrimes, a typical scenario for members of "The Com".
The actors were obsessed with the idea of “mass surveillance,” made possible by compromising telecommunications providers and accessing subscriber records. In one case, an actor sought records tied to a law enforcement officer’s phone number and his network of contacts; in another, the target was an informant involved in an investigation.
Former U.S. Soldier Pleads Guilty to Hacking and Extortion Scheme Involving Telecommunications Companies
https://www.justice.gov/opa/pr/former-us-soldier-pleads-guilty-hacking-and-extortion-scheme-involvin...
Wagenius’ mother, Alicia Roen, stated that he had been associated with Moucka, and worked on radio signals and network communications. Wagenius was stationed at Fort Cavazos in Central Texas and at a U.S. Army base in South Korea between April 2023 and Dec. 18, 2024. He was arrested after infiltrating 15 telecommunications providers while on active military duty.
Wagenius reportedly published the stolen AT&T call logs of high-ranking officials, including President Donald Trump and former Vice President Kamala Harris, on dark web forums.
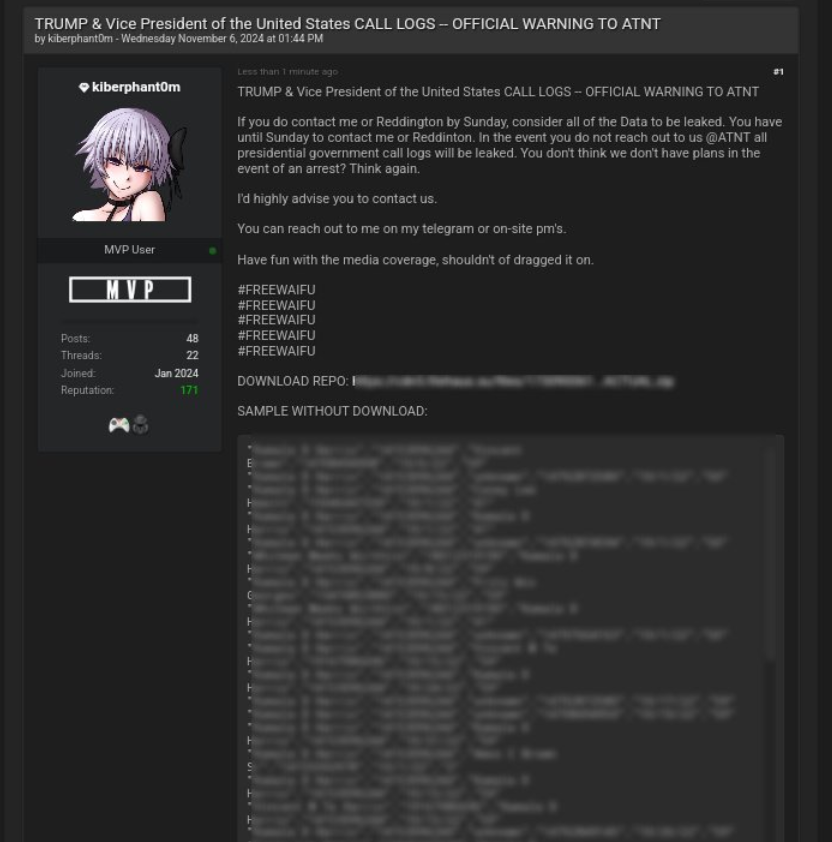
It is unknown whether the actor was acting on behalf of a foreign government or if the idea of targeting a high-ranking U.S. government officials was initially generated by him independently. In November 2024, Wagenius communicated via email from an address he believed belonged to an unidentified foreign country's military intelligence service, attempting to sell the stolen information.
Court filings reveal that before his arrest in December 2024, Wagenius made several highly incriminating searches over multiple weeks, including:
"can hacking be treason"
"where can i defect the u.s government military, which country will not hand me over"
"U.S. military personnel defecting to Russia"
"Embassy of Russia - Washington, D.C."
Such cases have a significant counterintelligence component, as they may also pose a threat to national security, beyond cybercrime.
Notably, Wagenius and Binns leveraged foreign infrastructure and online services to avoid tracking and prosecution, with the latter residing abroad.
Based on available intelligence, a female individual previously linked to Moucka is currently residing in Turkey. Our team sends her a 'warm hello,' along with another individual whom we will call 'S.M.' for today.
Offense is the Best Defense
With this publication, Resecurity is releasing 105 pages containing over 1,000 messages related to John Erin Binns (aliases: IRDev, IntelSecrets). Due to sensitivity, we are publishing only the titles of his communications obtained from a foreign email server.
Resecurity will not disclose how it obtained this data, but it can confirm its authenticity, which can be independently verified by examining the contacts and titles in the acquired messages. Such data could occasionally be left on the Dark Web or other open sources that are readily available for collection. The communications include attempts to harass U.S. government personnel, State Department officials, and FBI staff, along with multiple instances of misinformation and deceptive tactics.
Notably, "Scattered LAPSUS$ Hunters" (SLH) continued this outrageous trend by posting phone numbers and addresses of hundreds of government officials, including nearly 700 from DHS, in October last year.
Why is Binns important in the context of “ShinyHunters”-like collectives (or “The Com” phenomenon)? John Binns is not currently in U.S. custody. According to Resecurity’s research, "The Com" actors could be involved in wrongdoing, which may be conducted on behalf of malicious parties working against American interests. "The Com" actors have repeatedly attempted to harass U.S. government employees, including law enforcement personnel, one of whom worked for the Federal Bureau of Investigation (FBI).

The actors recently mentioned the alias of Binns when their malicious attempt was successfully identified by the honeytrap account we deployed.
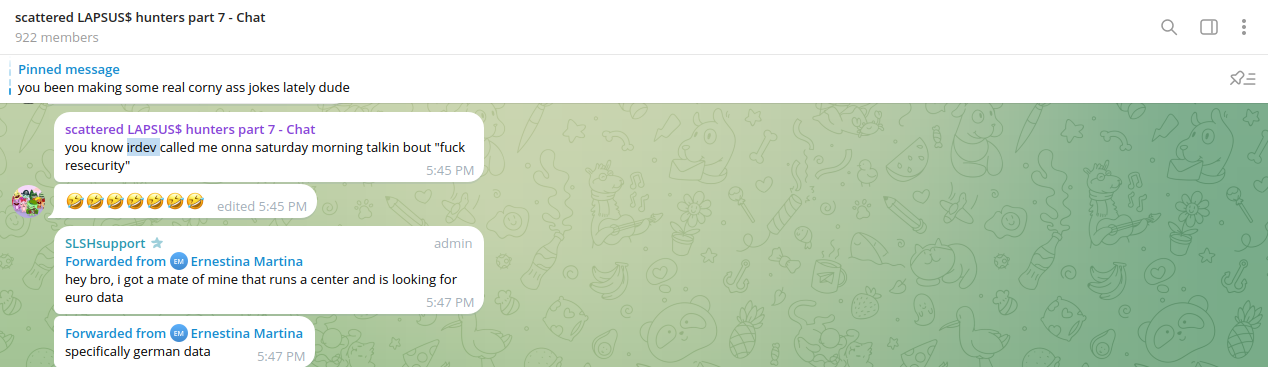
In the past, Binns also created a website where he leaked information and attempted to harass representatives of the U.S. Intelligence Community (IC), including high-ranking government officials:
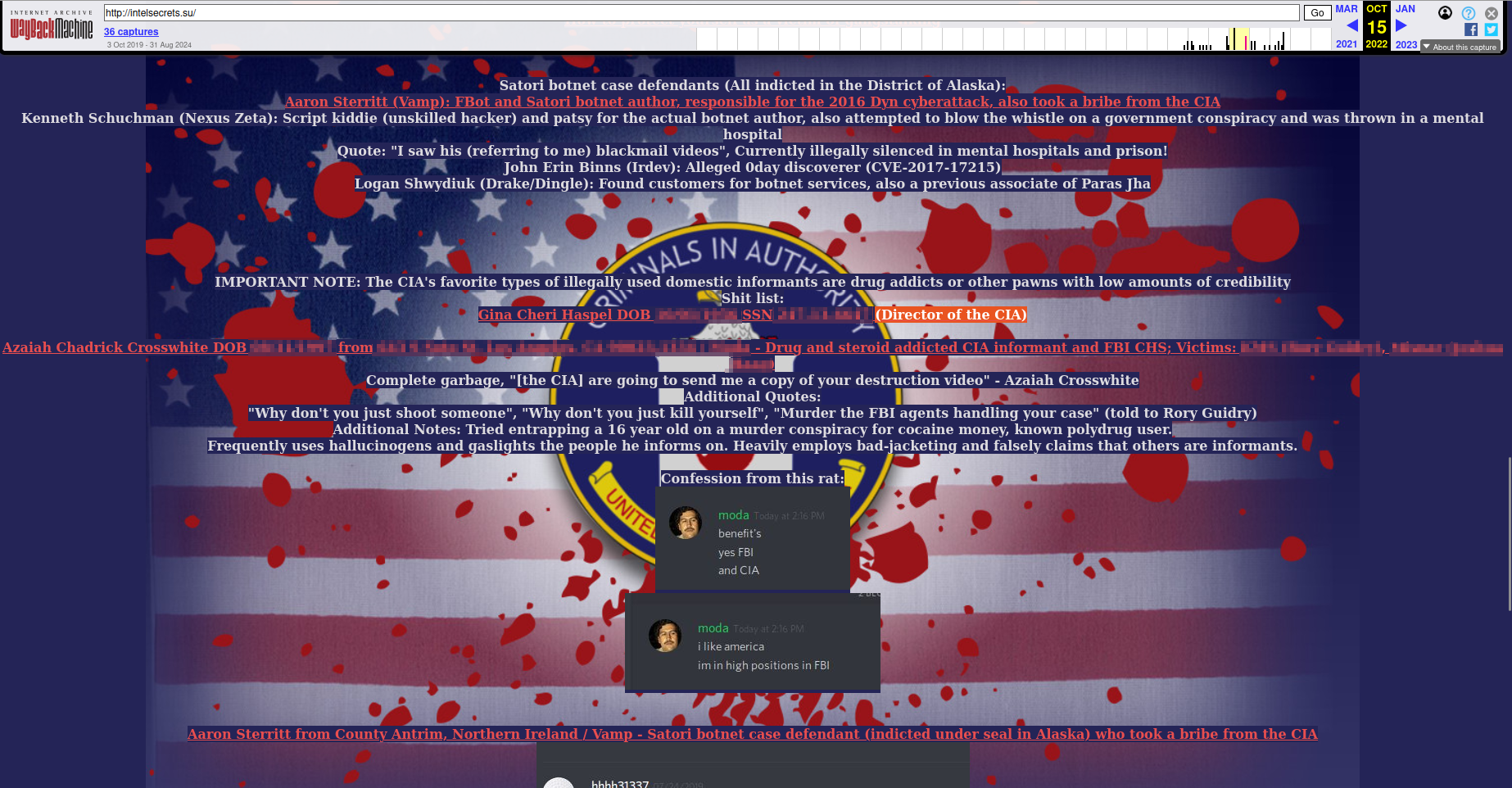
Notably, all domains registered by the actor have been configured through foreign domain registrars and hosting providers, which pose challenges for U.S. law enforcement to obtain data via traditional cooperation channels.
Why Honeytraps and Deception Are Needed?
In most network intrusions, hacking attacks, and data breaches conducted by these actors, infostealer data has been widely exploited. By planting honeytrap accounts — based on possibly compromised or targeted accounts — network defenders can create counterintelligence traps to track potential attackers and gain insights into their motives and tactics.
Notably, all the actors from "The Com" have something in common. They target big brands and government agencies to gain fame and express themselves within their community. In many cases, this motive drives their interest in attacking enterprises.
A secondary motive is financial gain and domination; through extortion, they attempt to obtain new sources of income that can be substantial and political power within their groups. By exploring actors' profiles, Resecurity was able to infiltrate their circles and gather valuable insights through Human Intelligence (HUMINT).
Enterprises should plan and implement counterintelligence (CI) programs to protect their environments against sophisticated actors. Such measures can be applied at both organizational and technical levels. They may include deception technologies, honeytraps, emulated environments, and fake information, all of which could attract malicious actors to engage in illegal activities.
Given that actors like "Shiny Hunters" (and their derivatives) and/or other members of "The Com" phenomenon often leverage insiders recruited for cooperation, CI will play a critical role in modern cybersecurity operations.
Significance
Notably, many members of "The Com" remain at large and are not under arrest. One of the challenges is the complications with law enforcement collaboration and in coordinating timely efforts to disrupt their activities in foreign jurisdictions that are not easily accessible to U.S. law enforcement agencies. Another aspect is the complexity of cases involving advanced actors and victims previously targeted by them, who are forced to cooperate and carry out malicious activity due to extortion and/or prior exploitation.
During the investigation into "The Com" activity and John Binns, one of the key actors, Resecurity observed some foreign organizations' lack of cooperation. This highlights the necessity for improved cross-border law enforcement cooperation and a greater emphasis on Public-Private Partnerships (PPPs) to exchange vital intelligence and address threats effectively.
Our Commitment
These efforts demonstrate Resecurity’s strong commitment to protecting our customers, U.S. law enforcement interests, and individuals working for the benefit of our nation, regardless of where threat actors are, who they are, or what "hat" they wear.
Remarks
Shortly after the publication of this threat intelligence research, the Telegram channel associated with one of the "Shiny Hunters" (and variations) groups was deleted. More interestingly, after being documented via honeytrap infrastructure, the actors began repeatedly contacting media to remove the name "Shiny Hunters". Such delicate requests have been sent to several journalists.
Resecurity documented this outreach, which is a well-known tactic. As explained in the introduction to this research and by independent sources, including CyberScoop, the actors described in this publication are associated with “The Com,” an ecosystem of groups and individuals who engage in or are involved (by other actors) in cybercrime and other illegal activities.

