Organized North Korean Remote IT Worker Fraud Compels Organizations to Enhance Hiring Verification Controls With Next-Gen CTI
Identity Fraud


An indictment and criminal complaint unsealed on May 16 reveal glaring, malicious-insider risks posed by remote labor and the extreme lengths to which foreign threat actors are willing to go to infiltrate U.S. corporate IT networks. These court documents allege that an Arizona woman, a Ukrainian man, and three unidentified foreign nationals participated in “schemes to place overseas information technology (IT) workers—posing as U.S. citizens and residents—in remote positions at U.S. companies,” according to a Department of Justice press release. Notably, most of the IT workers unlawfully placed in jobs at U.S. companies hail from the rogue state of North Korea.
The DOJ press release said that these schemes “involved defrauding over 300 U.S. companies using U.S. payment platforms and online job site accounts, proxy computers located in the United States, and witting and unwitting U.S. persons and entities.” This probe marks the “largest case ever charged by the Justice Department involving this type of IT workers’ scheme,” according to the DOJ press release. Assistant Director Kevin Vorndran of the FBI’s Counterintelligence Division said these allegations represent a “new high-tech campaign to evade U.S. sanctions, victimize U.S. businesses, and steal U.S. identities,” per the DOJ announcement.
The focal point of this criminal conspiracy is Christina Chapman, a 49-year-old Arizona woman who stands accused by prosecutors of defrauding U.S. companies “across myriad industries, including multiple well-known Fortune 500 companies, U.S. banks, and other financial service providers,” per the announcement. The DOJ said that the identities of over 60 U.S. persons were “compromised and used by IT workers related to Chapman’s cell.”
The overseas IT workers who conspired with Chapman, “many of whom were tied to North Korea, posed as U.S. citizens using the stolen, false, or borrowed identities of U.S. nationals, and applied for positions at U.S companies, causing the transmission of false documentation to the U.S. Department of Homeland Security,” according to the DOJ.
Some Fortune 500 organizations these foreign IT workers were able to infiltrate include a “top-five major television network, a Silicon Valley technology company, an aerospace manufacturer, an American car manufacturer, a luxury retail store, and a U.S.-hallmark media and entertainment company,” according to the DOJ. Additionally, some of the companies defrauded in this conspiracy were “purposely targeted by a group of DPRK IT workers, who maintained postings for companies at which they wanted to insert IT workers," according to the press release.
Once the fraudulent IT workers were hired, the scheme relied on a sprawling “laptop farm,” which was operated by Chapman. Specifically, Chapman hosted the company computers that employers unwittingly sent to impersonated IT workers inside her home, enabling the foreign identity thieves to log into employer networks via unspecified remote access gateways. By hosting these devices in her home, Chapman gave corporate employers the impression that the devices were located in the U.S.
Chapman also “received and forged payroll checks and received direct deposits of the overseas IT workers’ wages from the U.S. companies into her U.S. financial accounts,” per the announcement. Collectively, Chapman’s fraudulent IT workers were paid millions for their work, “much of which was falsely reported to the IRS and the Social Security Administration in the name of the actual U.S. persons whose identities were stolen or borrowed,” according to the press release. Overall, Chapman’s IT employment-fraud racket “created false tax liabilities for more than 35 U.S. persons, and resulted in at least $6.8 million of revenue to be generated for the overseas IT workers,” according to the press release.
IRS Criminal Investigations Chief Guy Ficco said Chapman’s unlawful use of stolen identities to procure employment for foreign nationals with ties to North Korea at hundreds of U.S. companies “compromised the national security” of the United States. Ultimately, this case represents a novel spin on the insider threat typology. The weaponization of identity theft in the furtherance of the fraudulent placement of remote IT workers in roles at Fortune 500 companies may even have a state-sponsored cyber espionage nexus, given the outsized involvement of North Korean threat actors and the backdrop of heavy sanctions against the DPRK. This tradecraft also aligns with activity associated with North Korea’s Lazarus Group, a notorious DPRK-sponsored cyberespionage unit, which has recently leveraged employment recruitment gateways to target the cryptocurrency industry in particular.
Employee Verification Gaps in the Remote Work Era
The U.S. government has been warning about these types of DPRK-dominated IT remote work scams for the last two years. Recently the FBI, the U.S. Department of State, and the Treasury issued a new joint warning that said the North Korean government has “dispatched thousands of tech-savvy workers to China, Russia, and other countries in Eastern Europe, Southeast Asia, and Africa to infiltrate freelance networks and find jobs where they have access to sensitive data and systems,” per Dark Reading reporting.
The key takeaway from the Chapman case and the related criminal complaint involving Ukrainian national Oleksandr Didenko is that these investigations may only be the tip of the iceberg. There may be many more organizations unaware that they have been infiltrated by these types of threat actors, North Korean and otherwise. The freelancer markets in North America, Europe and East Asia, for example, are particularly vulnerable to malicious North Korean IT workers. Further complicating matters, “many of these North Korean IT workers have also been ex-pats that are based in China and Russia,” according to Axios reporting.
The proliferation of these schemes dovetails with legacy of the COVID-19 pandemic, namely the enterprise-wide normalization of remote labour. According to recent data published by the U.S. Career Institute, 21.7% of employers offer fully remote work opportunities today. The U.S. Career Institute also found that employees aged between 25 and 39 comprise the majority of remote workers, or 36.5%. Another factor driving organizations to look for remote IT talent is the growing “tech talent shortage,” with Bureau of Labor statistics revealing that there will be a deficit of 1.2 million IT employees by 2026 in the U.S. alone.
But as the Chapman case reveals, the mass adoption of remote- friendly policies by U.S. employers has significantly amplified the attack surface for would-be malicious insiders. As noted by Axios, it’s much easier for threat actors to “bypass traditional identity verification tactics when interviewing for a job through video and phone calls.” Furthermore, it can be difficult for companies to identify malicious online activity, “especially if they're a freelancer who is only with the company for short periods of time,” per Axios. Employee verification has been further stymied by the rapid rise of generative AI.
Today, rogue job applicants can use large language models (LLMs) to craft more convincing resumes and even weaponize deep fakes to impersonate the voices or video presence of IT workers they have targeted for identity theft. Given these emergent remote insider threat risks, employers need to assess their verification controls for their work-from-home (WFH) employees and ensure they have the tools in place to authenticate the identities of new hires.
Underground Market of Stolen IDs
One of the main catalysts for the identified DPRK activity is the use of forged and stolen identification documents, which can be reused by bad actors to falsify their identity.
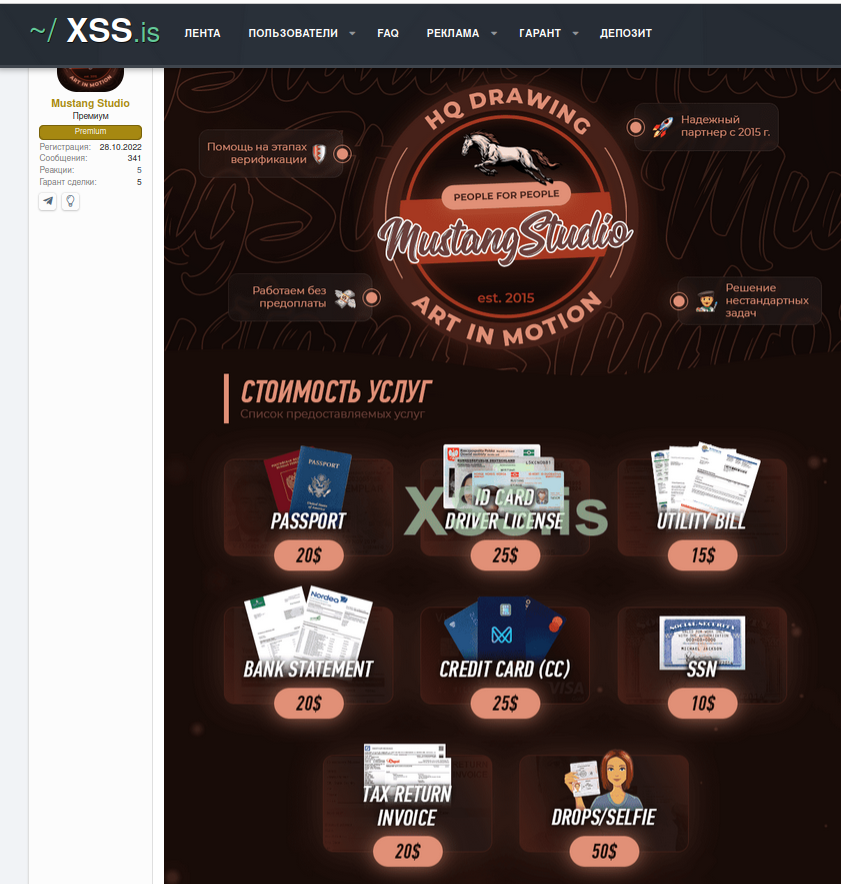
The dark web is known for being a marketplace where cybercriminals sell or trade leaked personal information and forged documents, including stolen ID documents. These documents can include passports, driver's licenses, and other forms of identification. The prices for these stolen identities can vary, but they can sell for as little as $2 and the going rate for a stolen identity is about twenty bucks.
The dark web provides a platform for cybercriminals to exploit stolen data for financial gain. However, it's worth mentioning that the dark web is not the only source of stolen identities. Data breaches, impersonation scams, and leaks from data brokers can also contribute to the availability of personal information on the dark web.
Recently, Resecurity detected a massive dump of stolen identity documents on the Dark Web, containing thousands of records including passports, driver's licenses, and other identification documents. This data is highly sought after by cybercriminals and nation-state actors who can use it to impersonate innocent individuals before job interviews, facilitating illegal activities such as financial fraud and espionage.
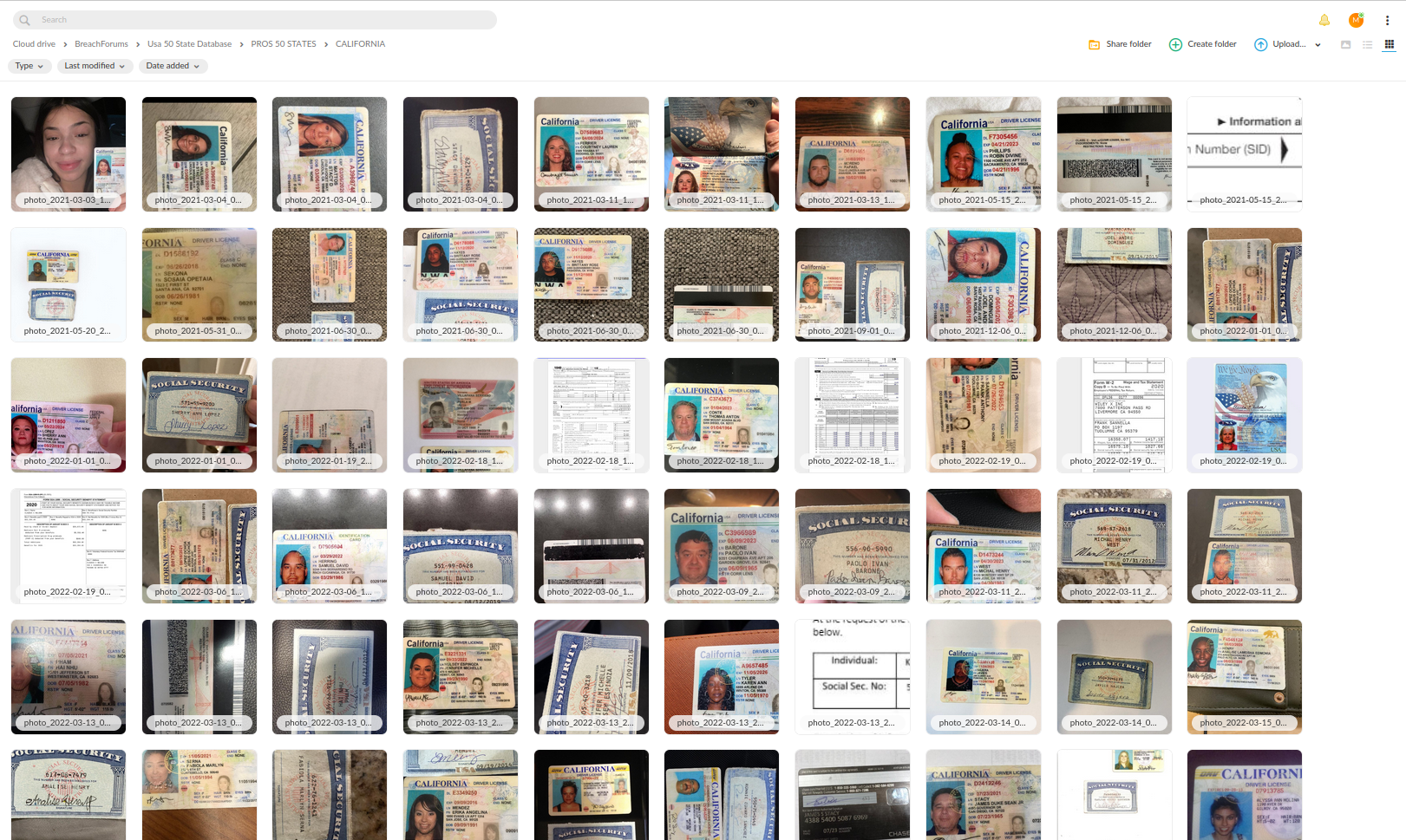
Additional drivers facilitating DPRK-related malicious activity include:
- proliferation of underground Deep Fake services, which use AI to modify facial and other information on ID
documents, making it difficult to verify identities;
- availability of high-quality counterfeit documents for sale on the Dark Web, which can be used to create fake identities;
- advanced verification services available on the Dark Web enable actors to build a proper "history" and profile for new accounts, leveraging stolen identities;
- compromise of job portals and recruiting services to collect sensitive information, including CVs and personally identifiable information (PII), as well as other details such as employment history, education, and contact information. This stolen data enables the actors to perform sophisticated impersonation attacks, allowing them to create fake identities that are convincing enough to deceive even the most vigilant organizations.
- infiltration by external vendors and staffing agencies, which can compromise sensitive information and disrupt operations. This risk is particularly high when these vendors and agencies lack thorough vetting or have inadequate security measures in place.
Nation-state actors may engage with cybercriminal services, such as those that provide forged identification documents, which can cost between $10 to $50 per document. These services are often used for KYC verification of new identities.
Resecurity ID Protect for Employee Verification and Enhanced Due Diligence
In the modern employee-onboarding threat landscape, organizations must be vigilant about vetting their remote workers. By harnessing the power of modern cyber-threat intelligence (CTI), enterprises can cross-reference job candidate data with a broad universe of compromised identity records. This way organizations can conduct enhanced verification and diligence checks on candidates who present a higher risk of impersonation.
Modern CTI and identity protection solutions leverage bleeding edge counter-deep fake and anti-document-forgery computer vision (CV) technologies. For new hires, this technology can be purposed at the onboarding stage to scan candidate identity documents. The combination of CV technologies like optical character recognition (OCR) and facial recognition can be applied to analyze candidate IDs with planetary-scaled databases of compromised identity records to mitigate the risk of impersonator onboarding.
As the Chapman case illustrates, the remote IT work ecosystem has been infiltrated by untold numbers of foreign malicious insiders. As authorities race to map out the full scale of the problem, organizations need to start taking enhanced measures to mitigate risk and verify the integrity of candidate identities. To learn more about how your organization can leverage CTI to prevent malicious insiders from corrupting your remote workforce, Resecurity can help.
To protect against advanced threats from cybercriminals, fraudsters, and nation-state actors who leverage stolen identities, Resecurity offers a comprehensive range of solutions and services designed to accelerate identity verification and background checks.
Our portfolio includes:
- enhanced due diligence;
- insider threat investigations;
- computer vision filters to verify identification documents;
- deep background checks;
- on-demand investigations;
- tracking of high-risk individuals and sanctioned organizations.
When recruiting remote contractors or employees in foreign jurisdictions, organizations may face increased risk due to the complexity of background checks, which can lead to blind spots that can be exploited by nation-state actors and groups. These blind spots can be leveraged to compromise identities and facilitate fraud, making it essential to implement robust risk mitigation measures. For instance, enhanced due diligence and timely insider threat assessment (before the incident) can help identify potential vulnerabilities, prevent fraudulent activities, sensitive data and intellectual property theft.
It's critical to implement robust digital identity protection measures to minimize the risk of identity theft. To achieve this, Resecurity launched a digital identity protection solution that safeguards citizens' national ID documents. As a pioneer in this field, Resecurity successfully launched its solution for multiple regions, providing a critical layer of protection against identity theft and fraud.

